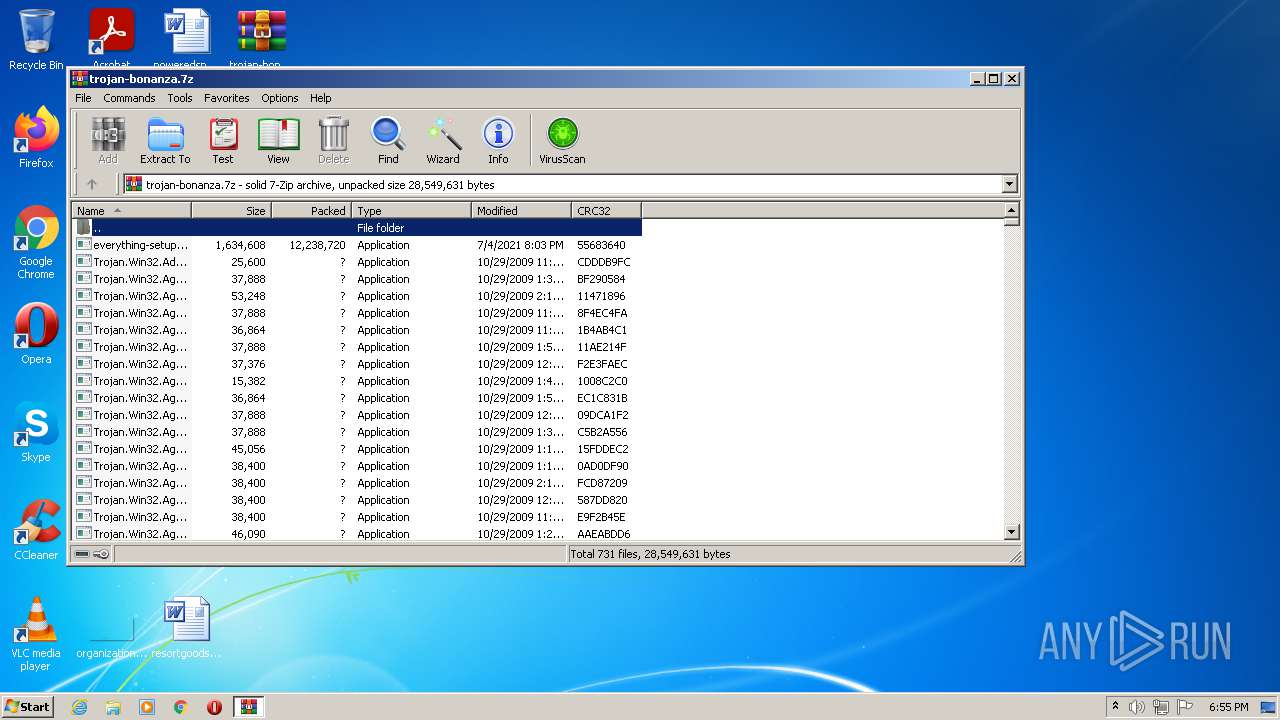
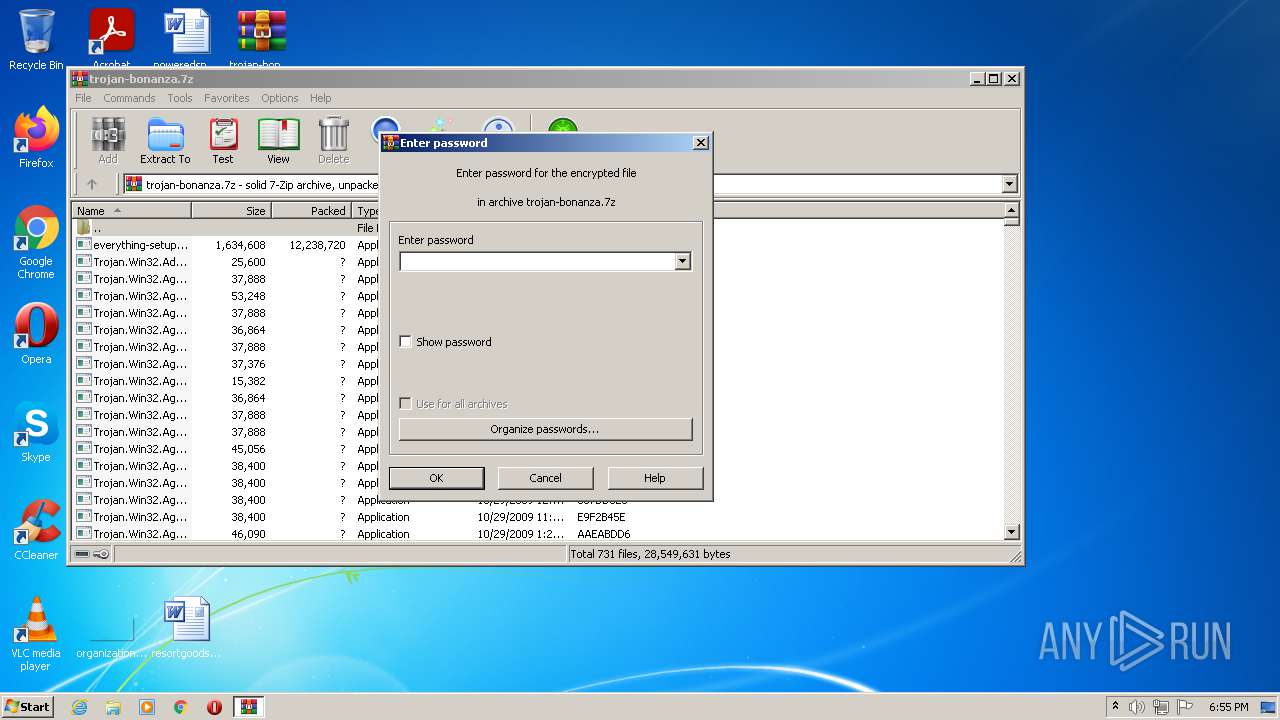
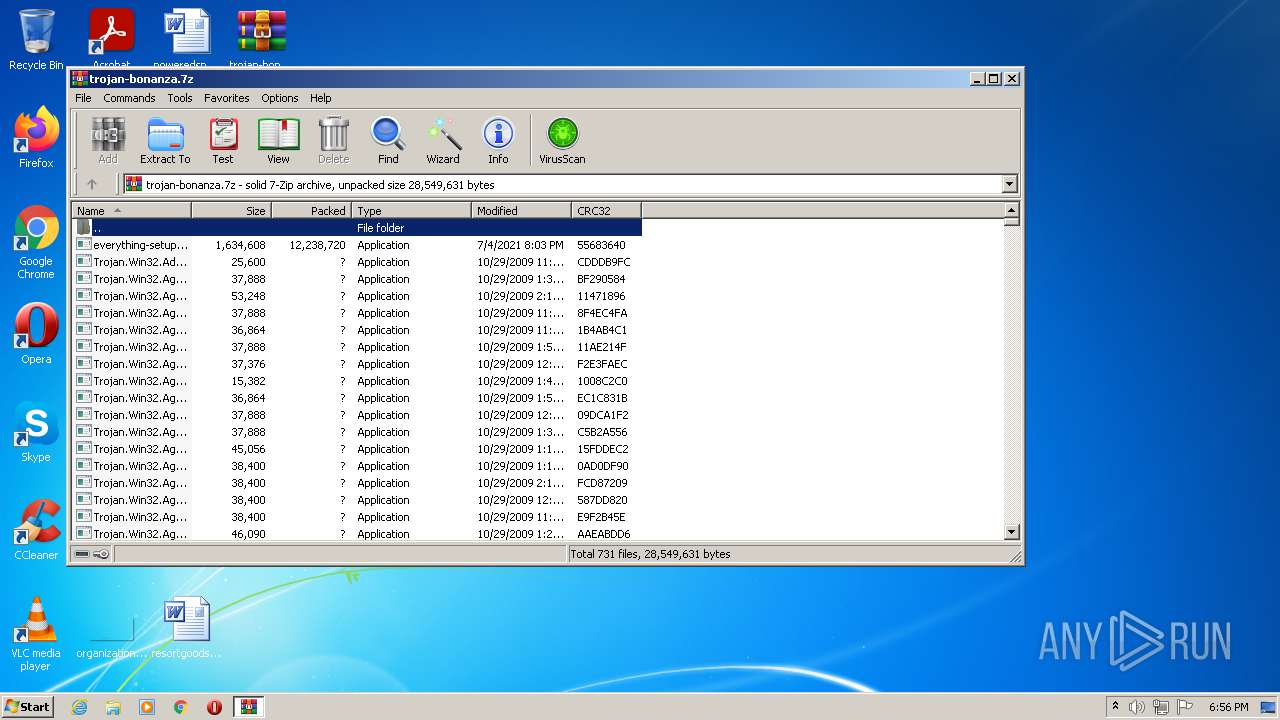
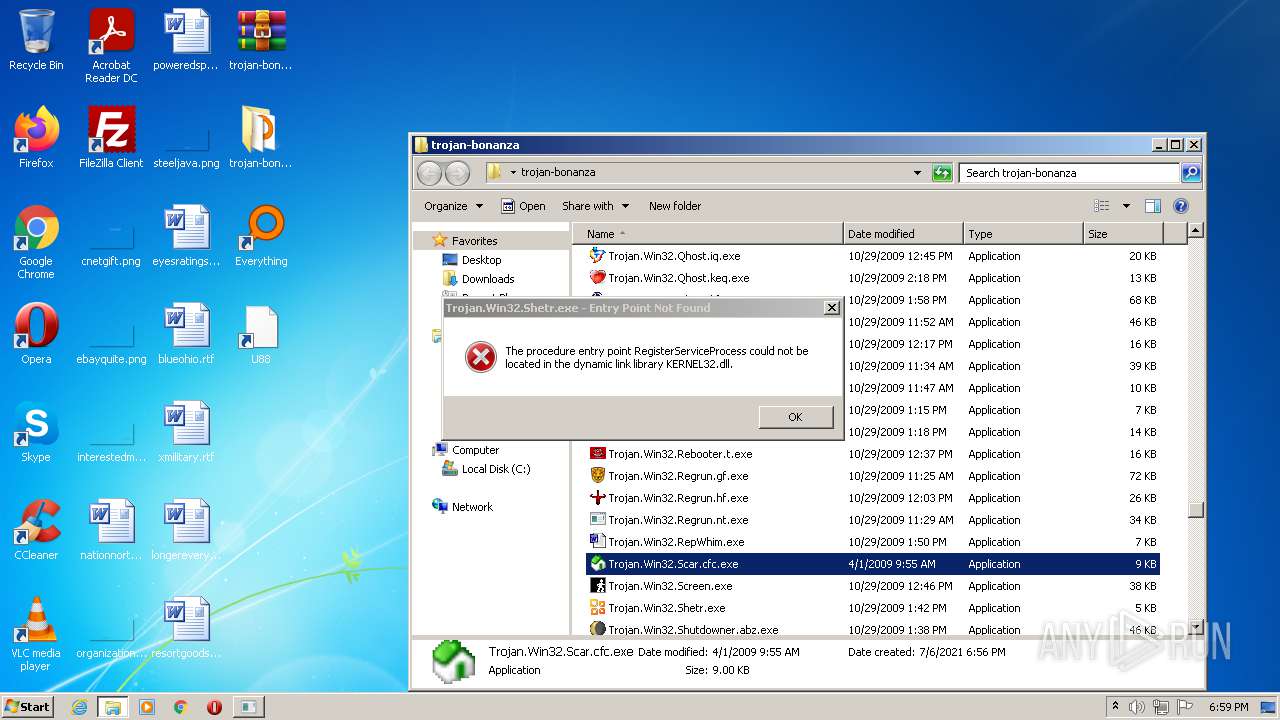
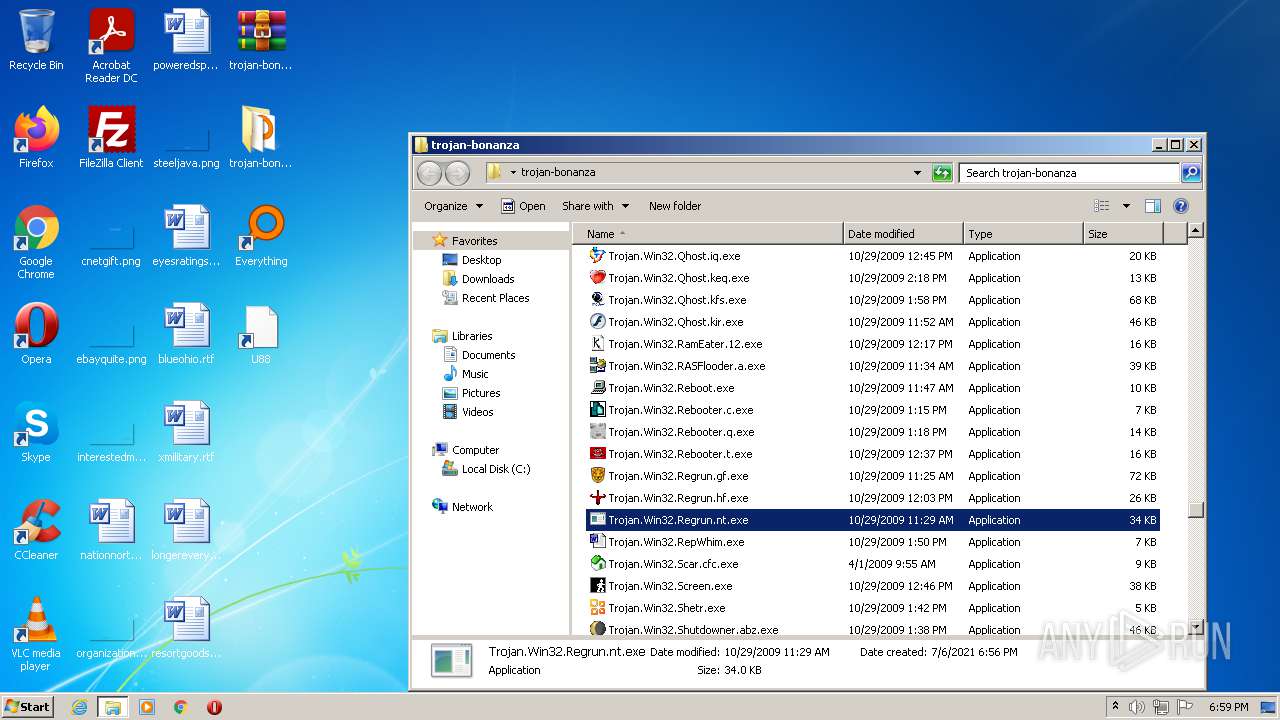
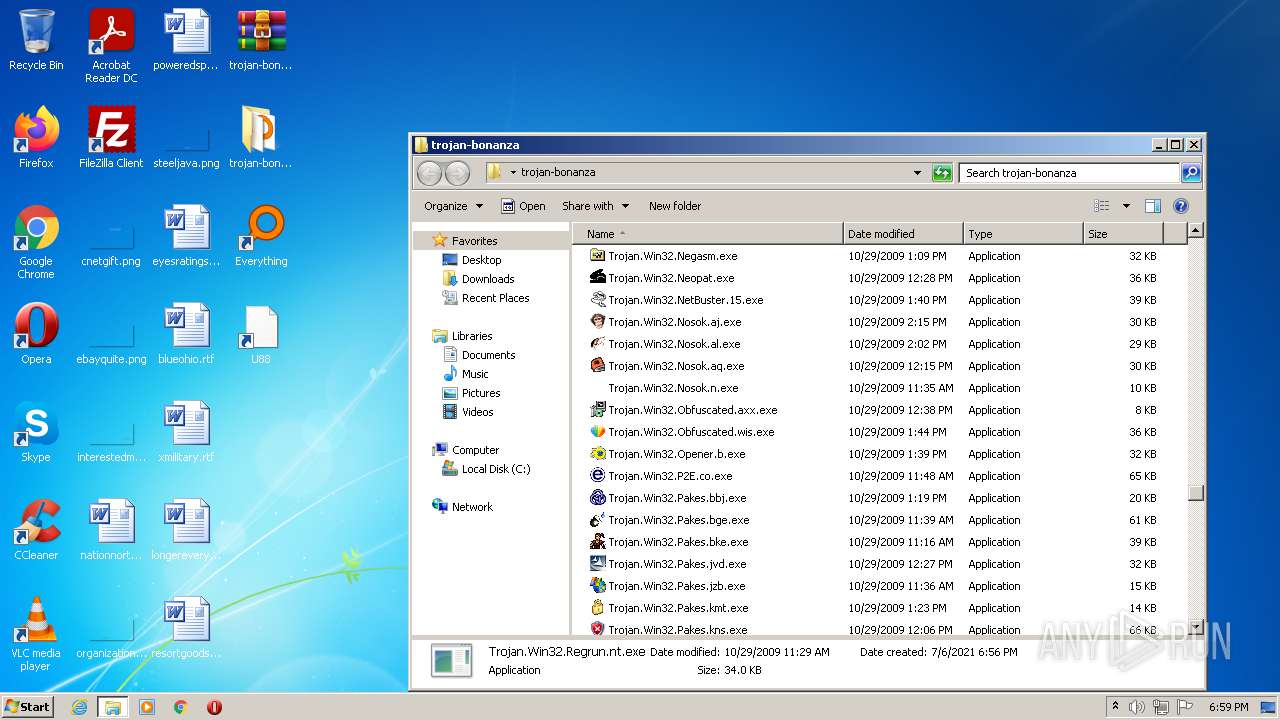
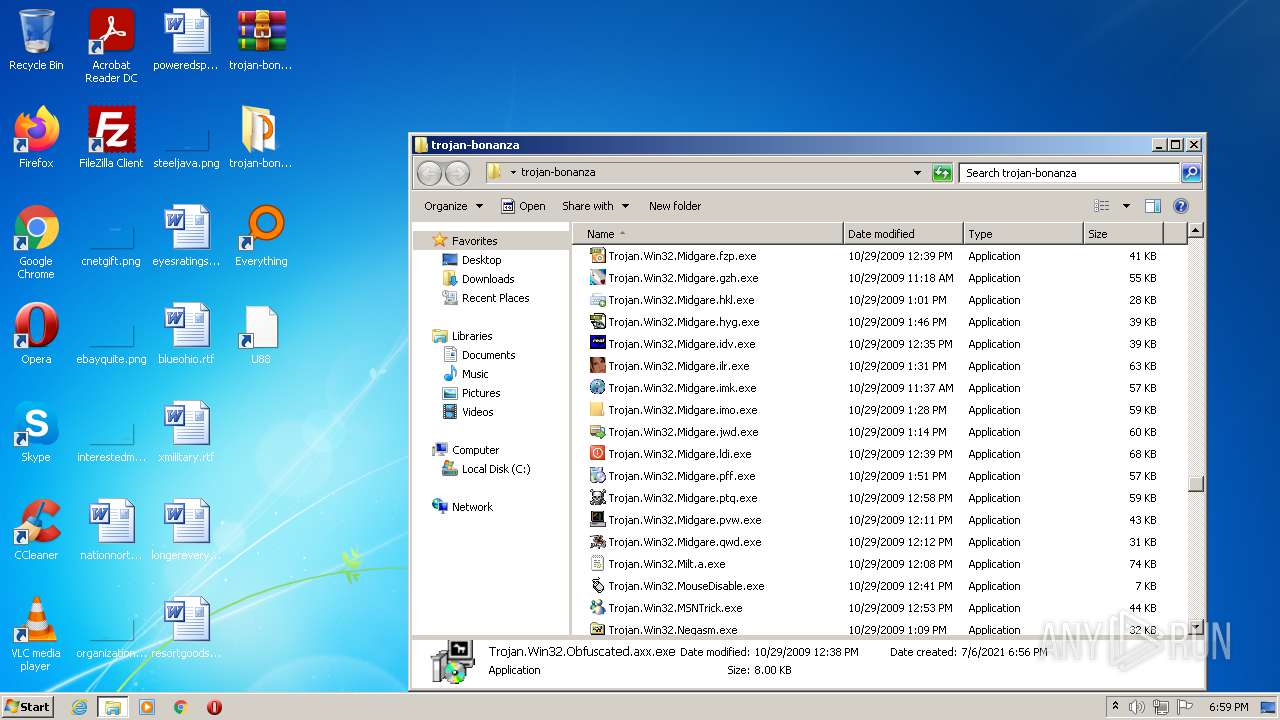
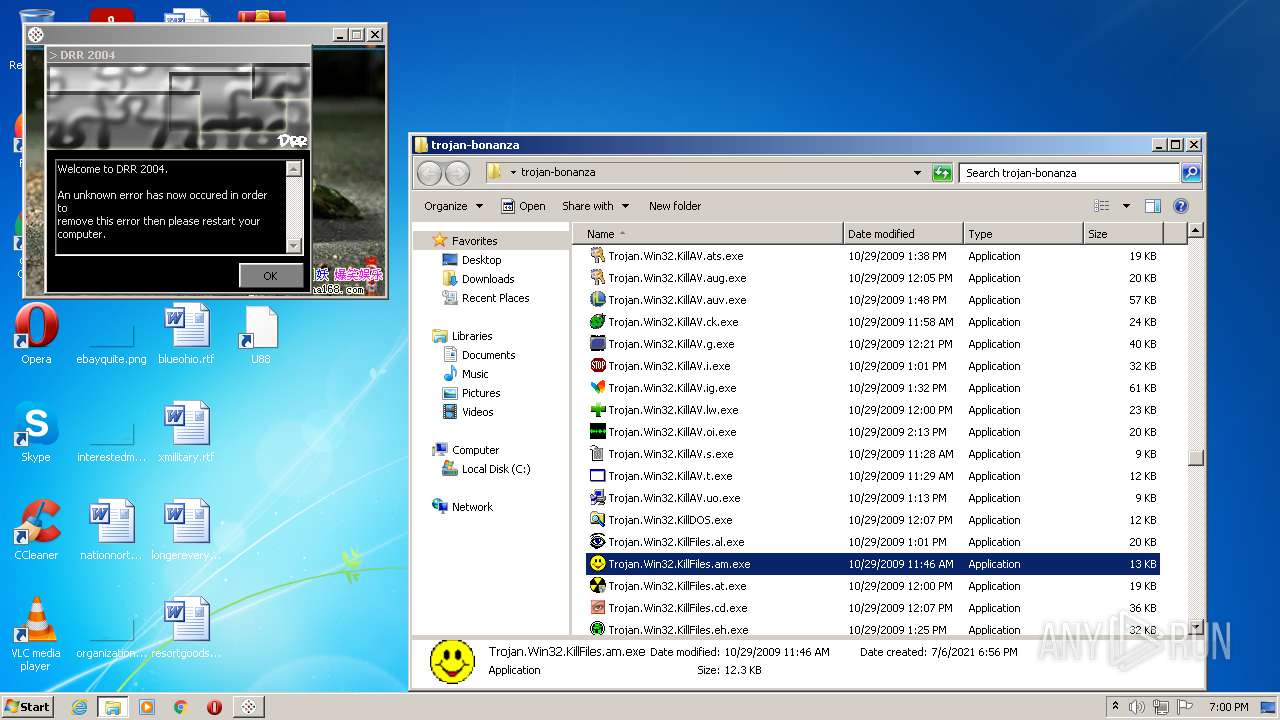
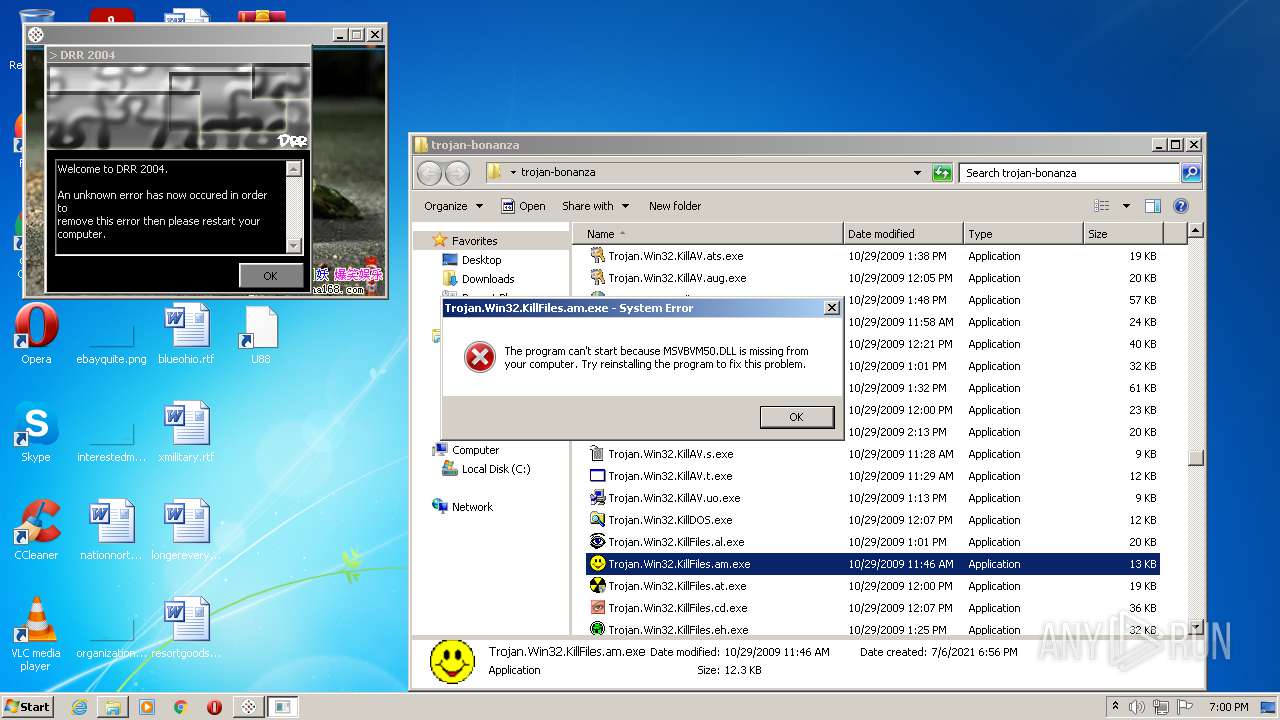
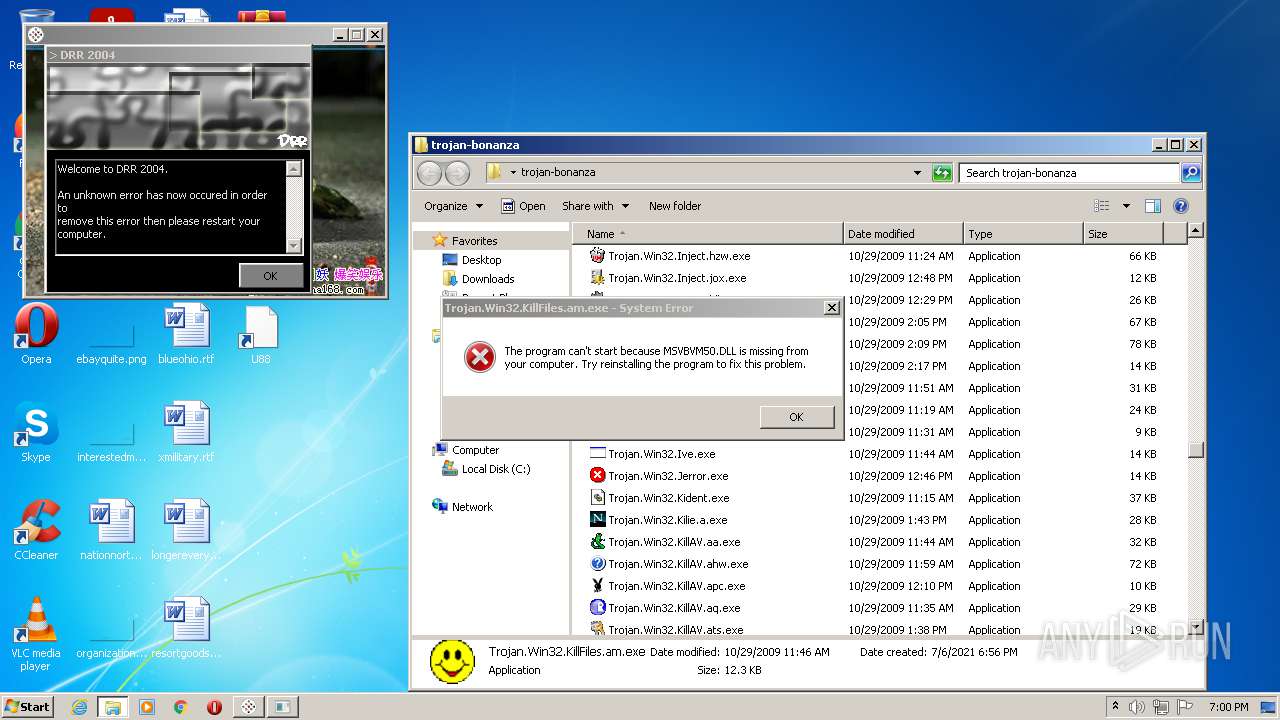
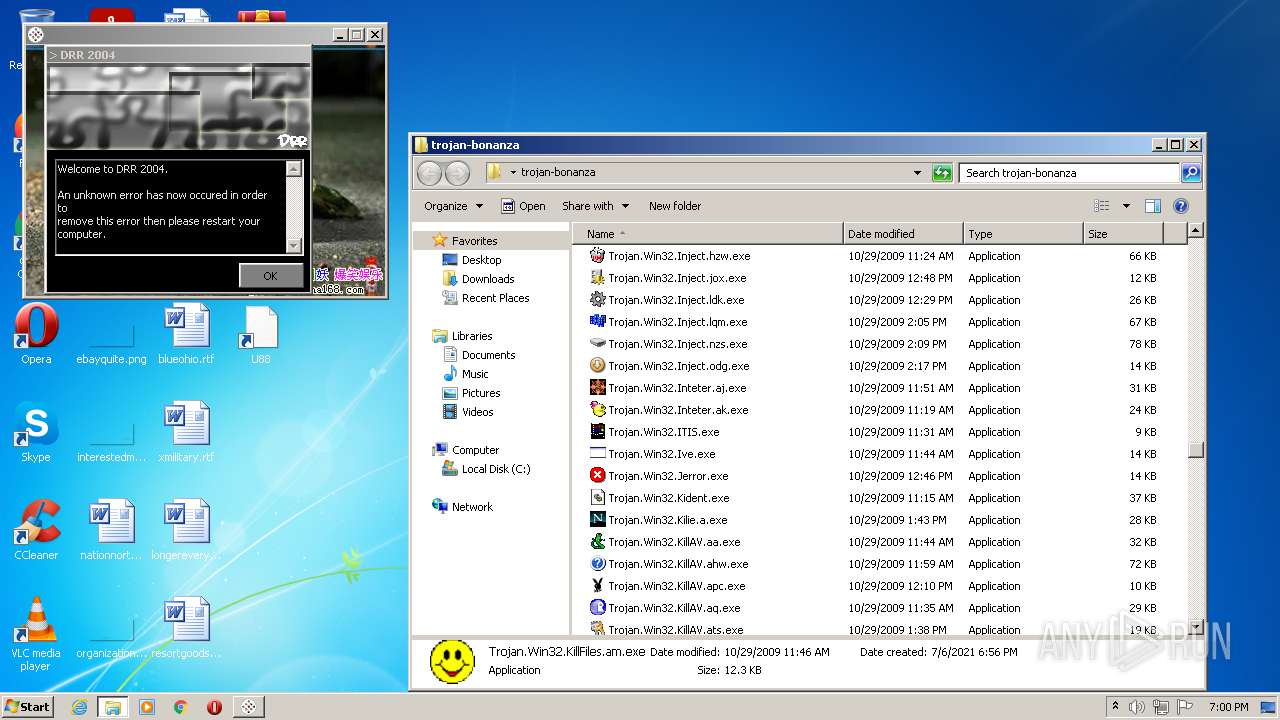
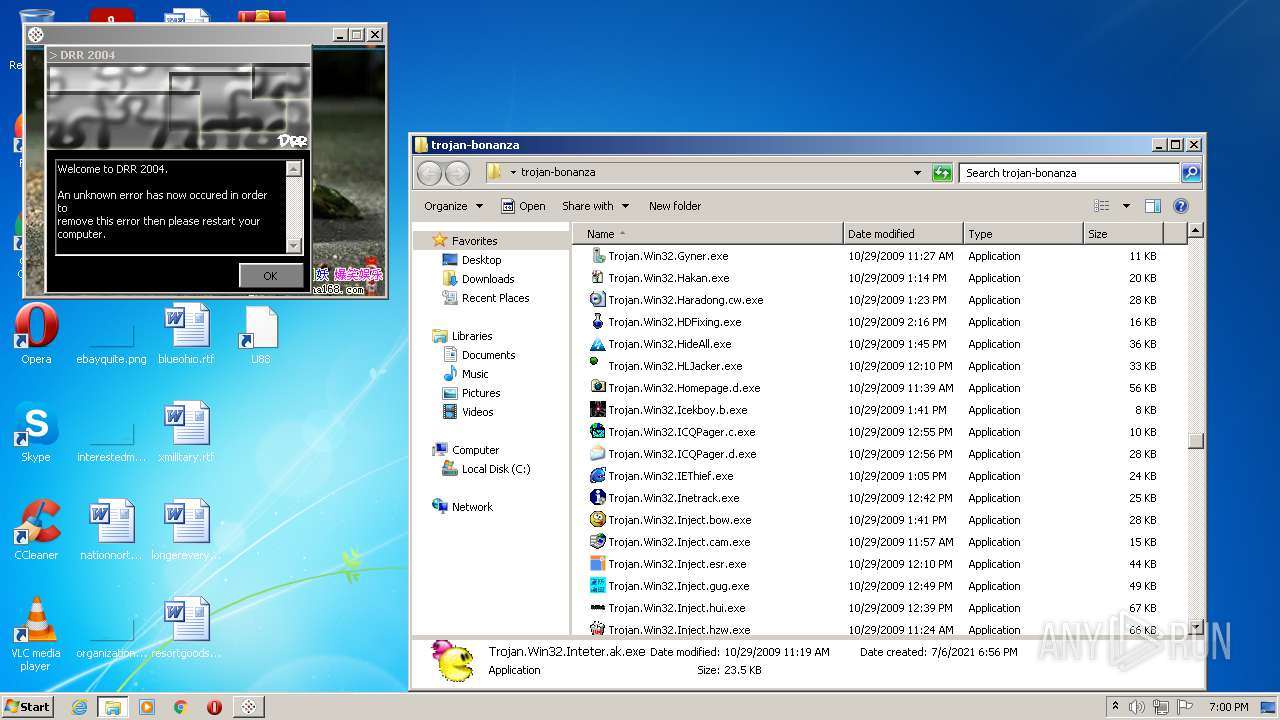
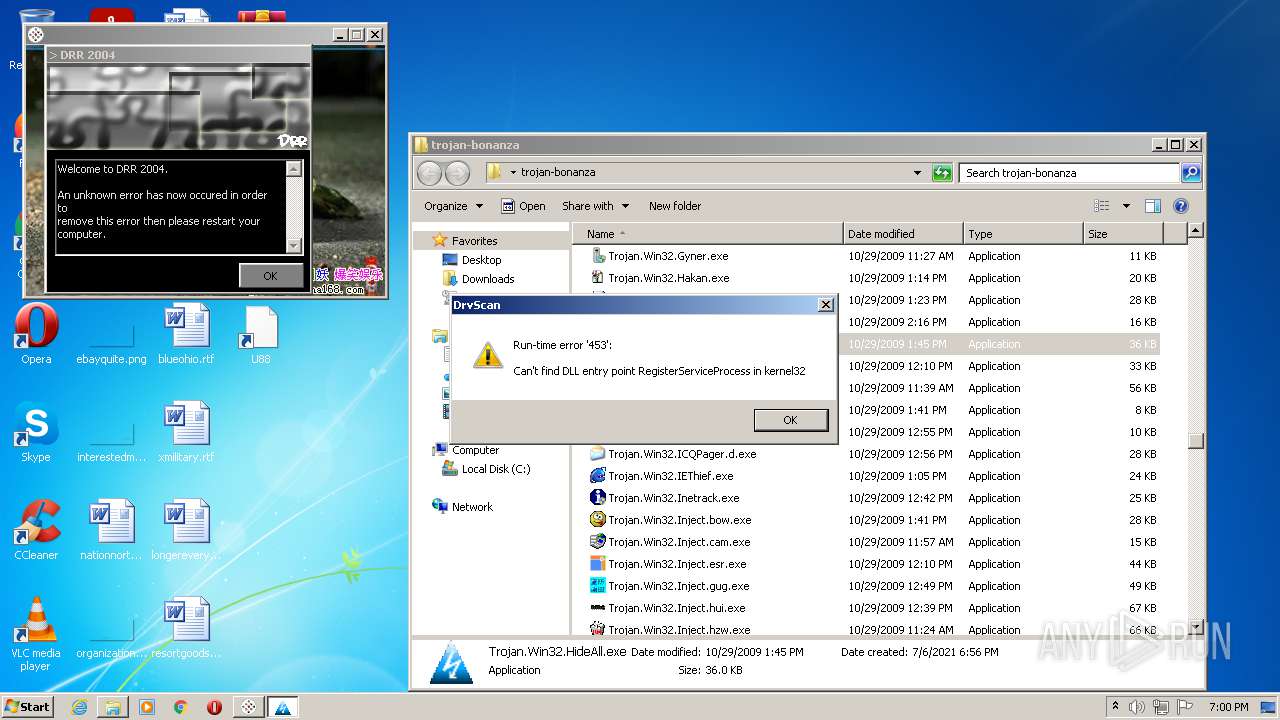
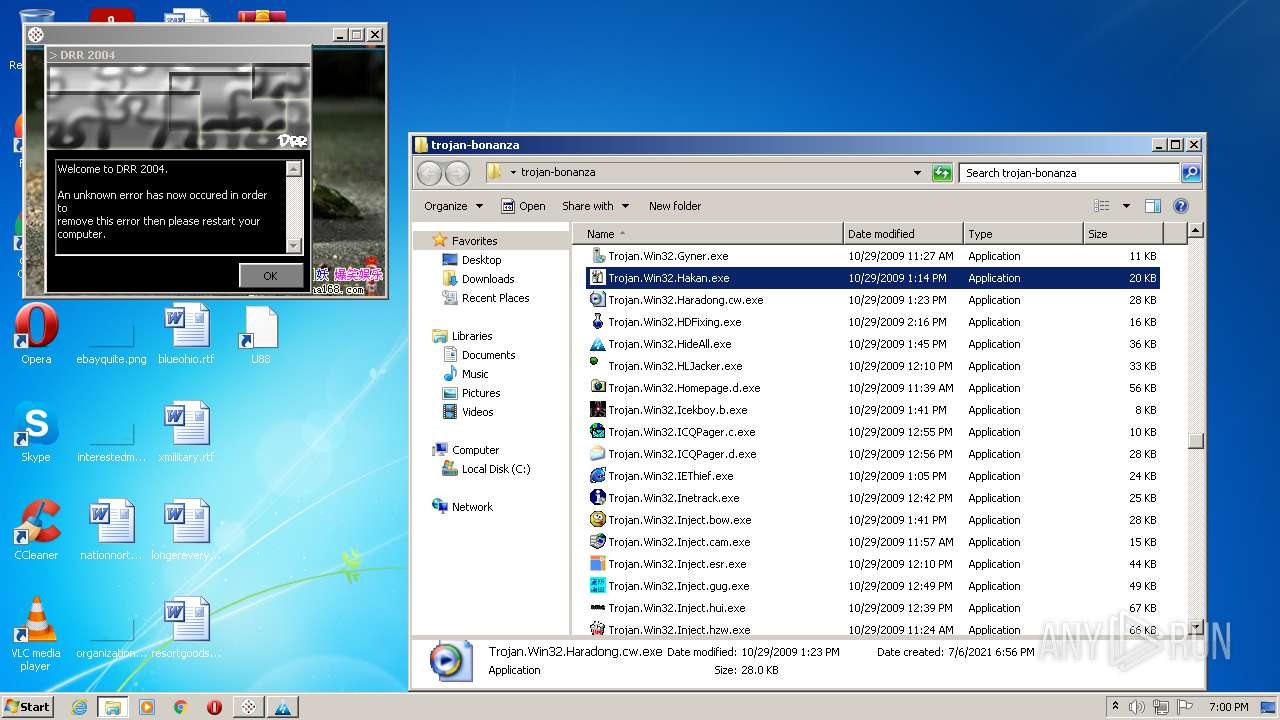
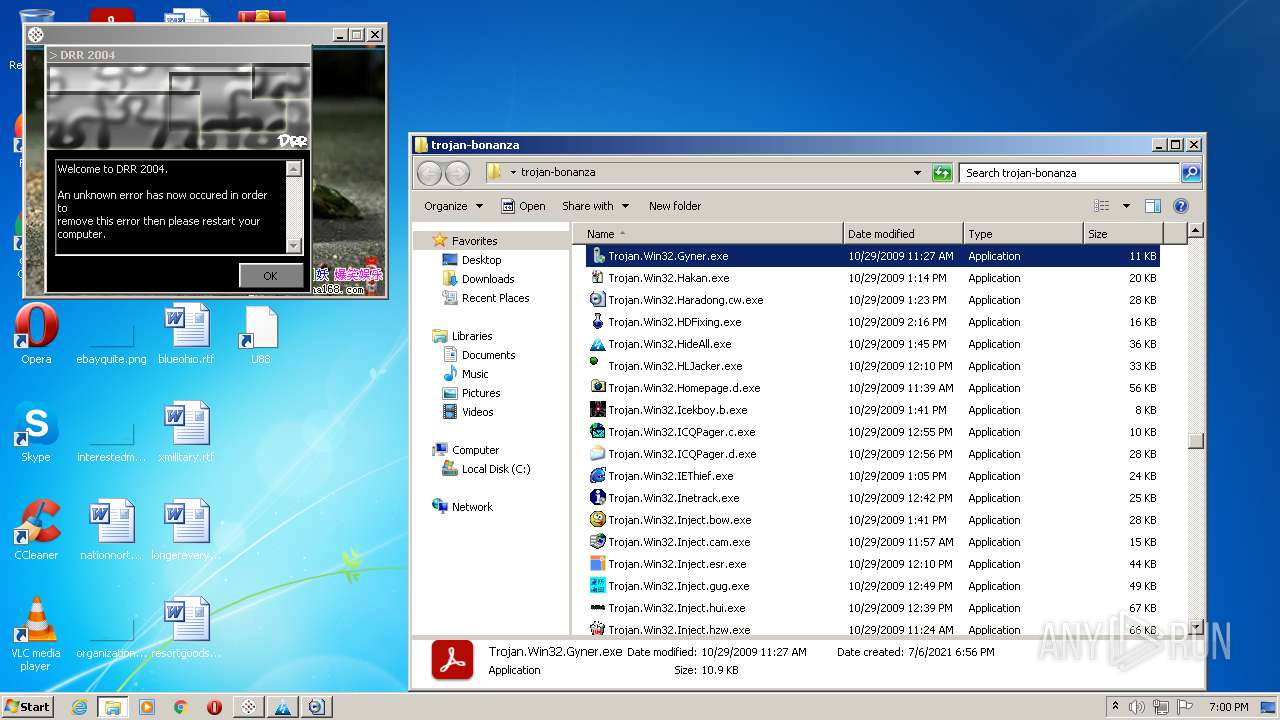
| File name: | trojan-bonanza.7z |
| Full analysis: | https://app.any.run/tasks/31806ae5-4f40-496f-afdd-c59155ee4467 |
| Verdict: | Malicious activity |
| Analysis date: | July 06, 2021, 17:55:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 3DA139109E56EFE7D47676DFD2744DB3 |
| SHA1: | D64E68E1692C963CB640EACF9252DDB277F3CD82 |
| SHA256: | 1CDB88BF3DB4D9FEA34A421C903035216C2EE069D7ECCFD1735CC8DCBD0EF6EE |
| SSDEEP: | 196608:8/oDkrpZSkHIs0VbbZ0m5URubuwb5lGeukS0qEVSqHh0oMBPD3MUKnnYLREtLDM1:6oDk7PY/fC6uO5lmkTRVlh0oMBPDcUKY |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3396)
- everything-setup.exe (PID: 1604)
- Everything.exe (PID: 2348)
- Explorer.EXE (PID: 1072)
- svchost.exe (PID: 880)
Application was dropped or rewritten from another process
- everything-setup.exe (PID: 1604)
- Everything.exe (PID: 692)
- Everything.exe (PID: 2892)
- Everything.exe (PID: 3772)
- Everything.exe (PID: 2540)
- Everything.exe (PID: 2348)
- Trojan.Win32.Pakes.bge.exe (PID: 1128)
- Trojan.Win32.Pakes.bke.exe (PID: 2272)
- Trojan.Win32.Pakes.jvd.exe (PID: 2576)
- Trojan.Win32.Pakes.jzb.exe (PID: 3232)
- Trojan.Win32.Pakes.jzb.exe (PID: 3432)
- Trojan.Win32.Pakes.kmt.exe (PID: 3308)
- Trojan.Win32.Pakes.kns.exe (PID: 1840)
- Trojan.Win32.Pakes.kmt.exe (PID: 2804)
- Trojan.Win32.Opener.b.exe (PID: 3052)
- Trojan.Win32.Obfuscated.wis.exe (PID: 2000)
- Trojan.Win32.Nosok.n.exe (PID: 2576)
- Everything.exe (PID: 3308)
- Trojan.Win32.Nosok.aj.exe (PID: 3072)
- Trojan.Win32.Neopat.exe (PID: 3324)
- Trojan.Win32.NetBuster.15.exe (PID: 3084)
- Trojan.Win32.Negasm.exe (PID: 2544)
- Trojan.Win32.MSNTrick.exe (PID: 1796)
- Trojan.Win32.MouseDisable.exe (PID: 952)
- Trojan.Win32.Milt.a.exe (PID: 2524)
- Trojan.Win32.Nosok.al.exe (PID: 304)
- Trojan.Win32.Midgare.qwd.exe (PID: 3880)
- Trojan.Win32.LoveYou.exe (PID: 1356)
- Trojan.Win32.Nosok.aq.exe (PID: 2652)
- Trojan.Win32.Looper.exe (PID: 1668)
- Trojan.Win32.Linkre.exe (PID: 2356)
- Trojan.Win32.Laoshen.d.exe (PID: 3260)
- Trojan.Win32.Laoshen.c.exe (PID: 2468)
- Trojan.Win32.Lame.exe (PID: 2192)
- Trojan.Win32.Koska.exe (PID: 2064)
- Trojan.Win32.Snatch.edit.exe (PID: 3524)
- Trojan.Win32.Small.xya.exe (PID: 620)
- Trojan.Win32.Small.yfq.exe (PID: 2748)
- Trojan.Win32.Small.xtb.exe (PID: 2268)
- Trojan.Win32.Small.u.exe (PID: 2472)
- Trojan.Win32.Small.me.exe (PID: 2584)
- Trojan.Win32.Small.lf.exe (PID: 4008)
- Trojan.Win32.SwapMouse.exe (PID: 3636)
- Trojan.Win32.StartPage.wc.exe (PID: 3556)
- Trojan.Win32.StartPage.i.exe (PID: 2304)
- Trojan.Win32.StartPage.bfx.exe (PID: 3568)
- Trojan.Win32.StartPage.aym.exe (PID: 3360)
- Trojan.Win32.StartPage.bey.exe (PID: 2516)
- Trojan.Win32.StartPage.bey.exe (PID: 2532)
- Trojan.Win32.LaSta.exe (PID: 2632)
- everything-setup.exe (PID: 3360)
- Trojan.Win32.LastTime.exe (PID: 900)
- Everything.exe (PID: 2836)
- Trojan.Win32.VB.dek.exe (PID: 1692)
- Trojan.Win32.Slefdel.awr.exe (PID: 296)
- Trojan.Win32.Small.adw.exe (PID: 3340)
- Trojan.Win32.Slefdel.bvk.exe (PID: 3860)
- Trojan.Win32.RepWhim.exe (PID: 3092)
- Trojan.Win32.Small.bam.exe (PID: 2804)
- Trojan.Win32.Sith.exe (PID: 4080)
- Trojan.Win32.Regrun.nt.exe (PID: 3856)
- Trojan.Win32.RASFlooder.a.exe (PID: 2340)
- Trojan.Win32.Regrun.hf.exe (PID: 2320)
- Trojan.Win32.Qhost.kir.exe (PID: 3952)
- Trojan.Win32.Small.biq.exe (PID: 2464)
- Trojan.Win32.Regrun.hf.exe (PID: 2544)
- Trojan.Win32.Qhost.kfs.exe (PID: 964)
- Trojan.Win32.Qhost.keq.exe (PID: 3888)
- Trojan.Win32.Qhost.keq.exe (PID: 1328)
- Trojan.Win32.Qhost.iq.exe (PID: 2252)
- Trojan.Win32.RamEater.12.exe (PID: 2800)
- Trojan.Win32.Qhost.kir.exe (PID: 2684)
- Trojan.Win32.Shetr.exe (PID: 328)
- Trojan.Win32.Scar.cfc.exe (PID: 1144)
- Trojan.Win32.Regrun.nt.exe (PID: 544)
- Trojan.Win32.KillWin.k.exe (PID: 2692)
- Trojan.Win32.Screen.exe (PID: 3284)
- Trojan.Win32.KillWin.gi.exe (PID: 1940)
- Trojan.Win32.KillWin.d.exe (PID: 3764)
- Trojan.Win32.KillWin.d.exe (PID: 3976)
- Trojan.Win32.KillFiles.h.exe (PID: 2268)
- Trojan.Win32.KillFiles.am.exe (PID: 3696)
- Trojan.Win32.Homepage.d.exe (PID: 1004)
- Trojan.Win32.HideAll.exe (PID: 3380)
- Trojan.Win32.KillFiles.er.exe (PID: 3416)
- Trojan.Win32.Haradong.cw.exe (PID: 2744)
- Trojan.Win32.Inject.gug.exe (PID: 2884)
- Trojan.Win32.Inject.gug.exe (PID: 3084)
- Trojan.Win32.Inject.cam.exe (PID: 824)
- Trojan.Win32.Inject.cam.exe (PID: 2160)
- Trojan.Win32.Inject.hui.exe (PID: 3620)
- Trojan.Win32.Inject.bow.exe (PID: 1388)
- Trojan.Win32.KillWin.gt.exe (PID: 2176)
- Trojan.Win32.Inetrack.exe (PID: 3864)
- Trojan.Win32.IEThief.exe (PID: 772)
- 1979343.exe (PID: 2084)
- Trojan.Win32.Inetrack.exe (PID: 4092)
Drops executable file immediately after starts
- everything-setup.exe (PID: 1604)
- Everything.exe (PID: 2892)
- Explorer.EXE (PID: 1072)
- Trojan.Win32.KillWin.gt.exe (PID: 2176)
- Trojan.Win32.Inject.bow.exe (PID: 1388)
- 1979343.exe (PID: 2084)
Changes the autorun value in the registry
- Everything.exe (PID: 3308)
- Trojan.Win32.Pakes.bke.exe (PID: 2272)
- Trojan.Win32.Neopat.exe (PID: 3324)
- Trojan.Win32.MouseDisable.exe (PID: 952)
- Trojan.Win32.Milt.a.exe (PID: 2524)
- Trojan.Win32.Looper.exe (PID: 1668)
- Explorer.EXE (PID: 1072)
- Trojan.Win32.Small.yfq.exe (PID: 2748)
- Trojan.Win32.Nosok.n.exe (PID: 2576)
- Trojan.Win32.Small.xya.exe (PID: 620)
- Trojan.Win32.Small.lf.exe (PID: 4008)
- Trojan.Win32.StartPage.wc.exe (PID: 3556)
- Trojan.Win32.StartPage.bfx.exe (PID: 3568)
- Trojan.Win32.StartPage.i.exe (PID: 2304)
- Trojan.Win32.KillWin.gt.exe (PID: 2176)
Runs injected code in another process
- Trojan.Win32.Midgare.qwd.exe (PID: 3880)
Application was injected by another process
- Explorer.EXE (PID: 1072)
Changes internet zones settings
- Trojan.Win32.Small.yfq.exe (PID: 2748)
Writes to a start menu file
- Trojan.Win32.Nosok.n.exe (PID: 2576)
Changes the login/logoff helper path in the registry
- Trojan.Win32.Nosok.n.exe (PID: 2576)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 284)
- everything-setup.exe (PID: 1604)
- Everything.exe (PID: 692)
- Everything.exe (PID: 2892)
- Everything.exe (PID: 3772)
- Everything.exe (PID: 2540)
- Everything.exe (PID: 2348)
- Trojan.Win32.Pakes.bke.exe (PID: 2272)
- Trojan.Win32.Pakes.bge.exe (PID: 1128)
- Trojan.Win32.Pakes.jvd.exe (PID: 2576)
- Trojan.Win32.Pakes.jzb.exe (PID: 3432)
- Trojan.Win32.Pakes.kns.exe (PID: 1840)
- Trojan.Win32.Opener.b.exe (PID: 3052)
- Trojan.Win32.Obfuscated.wis.exe (PID: 2000)
- Trojan.Win32.Nosok.n.exe (PID: 2576)
- Everything.exe (PID: 3308)
- Trojan.Win32.Nosok.aq.exe (PID: 2652)
- Trojan.Win32.Nosok.aj.exe (PID: 3072)
- Trojan.Win32.Nosok.al.exe (PID: 304)
- Trojan.Win32.Neopat.exe (PID: 3324)
- Trojan.Win32.Negasm.exe (PID: 2544)
- Trojan.Win32.MSNTrick.exe (PID: 1796)
- Trojan.Win32.Milt.a.exe (PID: 2524)
- Trojan.Win32.MouseDisable.exe (PID: 952)
- wscript.exe (PID: 3032)
- Trojan.Win32.Looper.exe (PID: 1668)
- Trojan.Win32.Midgare.qwd.exe (PID: 3880)
- Trojan.Win32.Koska.exe (PID: 2064)
- Trojan.Win32.Laoshen.c.exe (PID: 2468)
- Trojan.Win32.Laoshen.d.exe (PID: 3260)
- Trojan.Win32.Snatch.edit.exe (PID: 3524)
- Trojan.Win32.Small.yfq.exe (PID: 2748)
- Trojan.Win32.Small.xtb.exe (PID: 2268)
- Trojan.Win32.Small.u.exe (PID: 2472)
- Trojan.Win32.Small.me.exe (PID: 2584)
- Trojan.Win32.Small.xya.exe (PID: 620)
- Trojan.Win32.Small.lf.exe (PID: 4008)
- Trojan.Win32.StartPage.wc.exe (PID: 3556)
- Trojan.Win32.SwapMouse.exe (PID: 3636)
- Trojan.Win32.Linkre.exe (PID: 2356)
- Trojan.Win32.StartPage.aym.exe (PID: 3360)
- Trojan.Win32.StartPage.i.exe (PID: 2304)
- Trojan.Win32.StartPage.bfx.exe (PID: 3568)
- Trojan.Win32.VB.dek.exe (PID: 1692)
- everything-setup.exe (PID: 3360)
- Trojan.Win32.LastTime.exe (PID: 900)
- Trojan.Win32.LaSta.exe (PID: 2632)
- Trojan.Win32.StartPage.bey.exe (PID: 2532)
- Trojan.Win32.Slefdel.awr.exe (PID: 296)
- Trojan.Win32.Small.biq.exe (PID: 2464)
- Trojan.Win32.Regrun.hf.exe (PID: 2544)
- Trojan.Win32.Regrun.nt.exe (PID: 3856)
- Trojan.Win32.Qhost.kir.exe (PID: 3952)
- Trojan.Win32.RamEater.12.exe (PID: 2800)
- Trojan.Win32.Qhost.kir.exe (PID: 2684)
- Trojan.Win32.Qhost.keq.exe (PID: 1328)
- Trojan.Win32.Regrun.nt.exe (PID: 544)
- Trojan.Win32.KillWin.gt.exe (PID: 2176)
- Trojan.Win32.KillWin.d.exe (PID: 3976)
- Trojan.Win32.KillFiles.er.exe (PID: 3416)
- Trojan.Win32.Homepage.d.exe (PID: 1004)
- Trojan.Win32.Sith.exe (PID: 4080)
- Trojan.Win32.HideAll.exe (PID: 3380)
- Trojan.Win32.Haradong.cw.exe (PID: 2744)
- Trojan.Win32.Inject.hui.exe (PID: 3620)
- Trojan.Win32.Inject.gug.exe (PID: 2884)
- Trojan.Win32.Inject.gug.exe (PID: 3084)
- Trojan.Win32.Inject.cam.exe (PID: 824)
- Trojan.Win32.Inject.bow.exe (PID: 1388)
- 1979343.exe (PID: 2084)
- Trojan.Win32.IEThief.exe (PID: 772)
Creates files in the user directory
- Explorer.EXE (PID: 1072)
- Everything.exe (PID: 2540)
- Trojan.Win32.Linkre.exe (PID: 2356)
- Trojan.Win32.Nosok.n.exe (PID: 2576)
Executable content was dropped or overwritten
- everything-setup.exe (PID: 1604)
- Everything.exe (PID: 2892)
- WinRAR.exe (PID: 284)
- Explorer.EXE (PID: 1072)
- Trojan.Win32.Nosok.n.exe (PID: 2576)
- Trojan.Win32.KillWin.gt.exe (PID: 2176)
- Trojan.Win32.Inject.bow.exe (PID: 1388)
- 1979343.exe (PID: 2084)
Reads the computer name
- Everything.exe (PID: 692)
- everything-setup.exe (PID: 1604)
- WinRAR.exe (PID: 284)
- Everything.exe (PID: 2892)
- Everything.exe (PID: 3772)
- Everything.exe (PID: 2540)
- Everything.exe (PID: 3308)
- Everything.exe (PID: 2348)
- Trojan.Win32.Pakes.bke.exe (PID: 2272)
- Trojan.Win32.Obfuscated.wis.exe (PID: 2000)
- Trojan.Win32.Nosok.n.exe (PID: 2576)
- wscript.exe (PID: 3032)
- Trojan.Win32.Negasm.exe (PID: 2544)
- Trojan.Win32.MSNTrick.exe (PID: 1796)
- Trojan.Win32.Milt.a.exe (PID: 2524)
- Trojan.Win32.Small.yfq.exe (PID: 2748)
- Trojan.Win32.StartPage.wc.exe (PID: 3556)
- Trojan.Win32.VB.dek.exe (PID: 1692)
- Trojan.Win32.Linkre.exe (PID: 2356)
- Trojan.Win32.Slefdel.awr.exe (PID: 296)
- Trojan.Win32.Inject.gug.exe (PID: 3084)
- 1979343.exe (PID: 2084)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 284)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 284)
- Explorer.EXE (PID: 1072)
Application launched itself
- Everything.exe (PID: 692)
- Trojan.Win32.Pakes.kmt.exe (PID: 2804)
- Trojan.Win32.Inject.cam.exe (PID: 824)
- Trojan.Win32.Inject.gug.exe (PID: 2884)
Creates a directory in Program Files
- Everything.exe (PID: 2892)
- Trojan.Win32.Pakes.bge.exe (PID: 1128)
Drops a file with too old compile date
- WinRAR.exe (PID: 284)
- Explorer.EXE (PID: 1072)
- Trojan.Win32.Nosok.n.exe (PID: 2576)
- Trojan.Win32.KillWin.gt.exe (PID: 2176)
- Trojan.Win32.Inject.bow.exe (PID: 1388)
- 1979343.exe (PID: 2084)
Starts itself from another location
- Everything.exe (PID: 2892)
Executed as Windows Service
- Everything.exe (PID: 3772)
Changes default file association
- Everything.exe (PID: 3308)
Reads default file associations for system extensions
- Explorer.EXE (PID: 1072)
Executes scripts
- Trojan.Win32.Nosok.n.exe (PID: 2576)
Uses NETSH.EXE for network configuration
- Trojan.Win32.Nosok.n.exe (PID: 2576)
Creates files in the program directory
- Everything.exe (PID: 2892)
- Everything.exe (PID: 3308)
- Trojan.Win32.KillWin.d.exe (PID: 3976)
Creates a software uninstall entry
- Everything.exe (PID: 2892)
Changes the started page of IE
- Trojan.Win32.Milt.a.exe (PID: 2524)
- Trojan.Win32.StartPage.bfx.exe (PID: 3568)
- Trojan.Win32.StartPage.i.exe (PID: 2304)
- Trojan.Win32.StartPage.aym.exe (PID: 3360)
- Trojan.Win32.StartPage.bey.exe (PID: 2532)
Reads Environment values
- netsh.exe (PID: 3764)
Starts Internet Explorer
- Explorer.EXE (PID: 1072)
Executes application which crashes
- Trojan.Win32.LaSta.exe (PID: 2632)
Creates executable files which already exist in Windows
- Trojan.Win32.Nosok.n.exe (PID: 2576)
Reads the date of Windows installation
- Everything.exe (PID: 2348)
Reads Microsoft Outlook installation path
- Trojan.Win32.StartPage.wc.exe (PID: 3556)
Reads internet explorer settings
- Trojan.Win32.StartPage.wc.exe (PID: 3556)
Creates files in the Windows directory
- Trojan.Win32.KillWin.gt.exe (PID: 2176)
- Trojan.Win32.KillWin.d.exe (PID: 3976)
Executed via COM
- DllHost.exe (PID: 1824)
Writes to a desktop.ini file (may be used to cloak folders)
- Trojan.Win32.KillWin.d.exe (PID: 3976)
Removes files from Windows directory
- Trojan.Win32.KillWin.d.exe (PID: 3976)
INFO
Manual execution by user
- everything-setup.exe (PID: 1604)
- iexplore.exe (PID: 1832)
- everything-setup.exe (PID: 3360)
- Everything.exe (PID: 2836)
- Trojan.Win32.Sith.exe (PID: 4080)
- Trojan.Win32.Slefdel.awr.exe (PID: 296)
- Trojan.Win32.Slefdel.bvk.exe (PID: 3860)
- Trojan.Win32.Small.adw.exe (PID: 3340)
- Trojan.Win32.Small.biq.exe (PID: 2464)
- Trojan.Win32.Small.bam.exe (PID: 2804)
- Trojan.Win32.RepWhim.exe (PID: 3092)
- Trojan.Win32.Regrun.nt.exe (PID: 3856)
- Trojan.Win32.Regrun.hf.exe (PID: 2544)
- Trojan.Win32.Qhost.kir.exe (PID: 3952)
- Trojan.Win32.Regrun.hf.exe (PID: 2320)
- Trojan.Win32.RASFlooder.a.exe (PID: 2340)
- Trojan.Win32.Qhost.kir.exe (PID: 2684)
- Trojan.Win32.Qhost.kfs.exe (PID: 964)
- Trojan.Win32.Qhost.keq.exe (PID: 3888)
- Trojan.Win32.Qhost.keq.exe (PID: 1328)
- Trojan.Win32.Qhost.iq.exe (PID: 2252)
- Trojan.Win32.Screen.exe (PID: 3284)
- Trojan.Win32.RamEater.12.exe (PID: 2800)
- Trojan.Win32.Shetr.exe (PID: 328)
- Trojan.Win32.Scar.cfc.exe (PID: 1144)
- Trojan.Win32.Regrun.nt.exe (PID: 544)
- Trojan.Win32.KillWin.k.exe (PID: 2692)
- Trojan.Win32.KillWin.gt.exe (PID: 2176)
- Trojan.Win32.KillWin.gi.exe (PID: 1940)
- Trojan.Win32.KillWin.d.exe (PID: 3764)
- Trojan.Win32.KillWin.d.exe (PID: 3976)
- Trojan.Win32.Homepage.d.exe (PID: 1004)
- Trojan.Win32.HideAll.exe (PID: 3380)
- Trojan.Win32.KillFiles.er.exe (PID: 3416)
- Trojan.Win32.KillFiles.am.exe (PID: 3696)
- Trojan.Win32.KillFiles.h.exe (PID: 2268)
- Trojan.Win32.Inject.hui.exe (PID: 3620)
- Trojan.Win32.Inject.gug.exe (PID: 2884)
- Trojan.Win32.Inject.cam.exe (PID: 824)
- Trojan.Win32.Haradong.cw.exe (PID: 2744)
- Trojan.Win32.Inetrack.exe (PID: 3864)
- Trojan.Win32.Inject.bow.exe (PID: 1388)
- Trojan.Win32.Inetrack.exe (PID: 4092)
- Trojan.Win32.IEThief.exe (PID: 772)
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 284)
Checks supported languages
- netsh.exe (PID: 3764)
- ntvdm.exe (PID: 1284)
- iexplore.exe (PID: 1832)
- ftp.exe (PID: 2044)
- consent.exe (PID: 3764)
- consent.exe (PID: 3284)
- DllHost.exe (PID: 1824)
- consent.exe (PID: 2932)
- consent.exe (PID: 2856)
- consent.exe (PID: 2292)
- consent.exe (PID: 2656)
Reads the computer name
- netsh.exe (PID: 3764)
- iexplore.exe (PID: 1832)
- ftp.exe (PID: 2044)
- consent.exe (PID: 3764)
- consent.exe (PID: 3284)
- consent.exe (PID: 2932)
- consent.exe (PID: 2856)
- consent.exe (PID: 2292)
- consent.exe (PID: 2656)
Reads security settings of IE
- Trojan.Win32.StartPage.wc.exe (PID: 3556)
Checks Windows Trust Settings
- consent.exe (PID: 3764)
- consent.exe (PID: 3284)
- consent.exe (PID: 2932)
- consent.exe (PID: 2292)
- consent.exe (PID: 2856)
- consent.exe (PID: 2656)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
222
Monitored processes
115
Malicious processes
86
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\trojan-bonanza.7z" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 296 | "C:\Users\admin\Desktop\trojan-bonanza\Trojan.Win32.Slefdel.awr.exe" | C:\Users\admin\Desktop\trojan-bonanza\Trojan.Win32.Slefdel.awr.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 304 | "C:\Users\admin\Desktop\trojan-bonanza\Trojan.Win32.Nosok.al.exe" | C:\Users\admin\Desktop\trojan-bonanza\Trojan.Win32.Nosok.al.exe | Everything.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 328 | "C:\Users\admin\Desktop\trojan-bonanza\Trojan.Win32.Shetr.exe" | C:\Users\admin\Desktop\trojan-bonanza\Trojan.Win32.Shetr.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 544 | "C:\Users\admin\Desktop\trojan-bonanza\Trojan.Win32.Regrun.nt.exe" | C:\Users\admin\Desktop\trojan-bonanza\Trojan.Win32.Regrun.nt.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsotf Corption. Integrity Level: MEDIUM Exit code: 0 Version: 1.00.0001 Modules
| |||||||||||||||
| 620 | "C:\Users\admin\Desktop\trojan-bonanza\Trojan.Win32.Small.xya.exe" | C:\Users\admin\Desktop\trojan-bonanza\Trojan.Win32.Small.xya.exe | Everything.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 692 | "C:\Users\admin\AppData\Local\Temp\nsg8A90.tmp\Everything\Everything.exe" -install "C:\Program Files\Everything" -install-options " -app-data -install-run-on-system-startup -install-service -disable-run-as-admin -uninstall-folder-context-menu -install-start-menu-shortcuts -install-desktop-shortcut -uninstall-url-protocol -install-efu-association -install-language 1033 -save-install-options 0" | C:\Users\admin\AppData\Local\Temp\nsg8A90.tmp\Everything\Everything.exe | — | everything-setup.exe | |||||||||||
User: admin Company: voidtools Integrity Level: MEDIUM Description: Everything Exit code: 0 Version: 1.4.1.1009 Modules
| |||||||||||||||
| 772 | "C:\Users\admin\Desktop\trojan-bonanza\Trojan.Win32.IEThief.exe" | C:\Users\admin\Desktop\trojan-bonanza\Trojan.Win32.IEThief.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: IEthief Microsoft ??????? Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 824 | "C:\Users\admin\Desktop\trojan-bonanza\Trojan.Win32.Inject.cam.exe" | C:\Users\admin\Desktop\trojan-bonanza\Trojan.Win32.Inject.cam.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: wizard MFC Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 880 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\system32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
90 025
Read events
88 235
Write events
1 745
Delete events
45
Modification events
| (PID) Process: | (284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (284) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\trojan-bonanza.7z | |||
| (PID) Process: | (284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1072) Explorer.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.7z\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
Executable files
744
Suspicious files
18
Text files
19
Unknown types
1 372
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1072 | Explorer.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\290532160612e071.automaticDestinations-ms | automaticdestinations-ms | |
MD5:— | SHA256:— | |||
| 1072 | Explorer.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\1b4dd67f29cb1962.automaticDestinations-ms | automaticdestinations-ms | |
MD5:— | SHA256:— | |||
| 284 | WinRAR.exe | C:\Users\admin\Desktop\trojan-bonanza\Trojan.Win32.Agent.aabv.exe | executable | |
MD5:— | SHA256:— | |||
| 284 | WinRAR.exe | C:\Users\admin\Desktop\trojan-bonanza\Trojan.Win32.Agent.aalt.exe | executable | |
MD5:— | SHA256:— | |||
| 284 | WinRAR.exe | C:\Users\admin\Desktop\trojan-bonanza\Trojan.Win32.Agent.aajf.exe | executable | |
MD5:— | SHA256:— | |||
| 284 | WinRAR.exe | C:\Users\admin\Desktop\trojan-bonanza\Trojan.Win32.Adut.exe | executable | |
MD5:— | SHA256:— | |||
| 284 | WinRAR.exe | C:\Users\admin\Desktop\trojan-bonanza\Trojan.Win32.Agent.abai.exe | executable | |
MD5:— | SHA256:— | |||
| 284 | WinRAR.exe | C:\Users\admin\Desktop\trojan-bonanza\Trojan.Win32.Agent.aalw.exe | executable | |
MD5:— | SHA256:— | |||
| 1072 | Explorer.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\trojan-bonanza.7z.lnk | lnk | |
MD5:— | SHA256:— | |||
| 284 | WinRAR.exe | C:\Users\admin\Desktop\trojan-bonanza\Trojan.Win32.Agent.abav.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
5
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Domain | IP | Reputation |
|---|---|---|
r7.no-ip.biz |
| unknown |
gurmanonline.com |
| unknown |
www.zhaol.com |
| unknown |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a Suspicious no-ip Domain |
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |