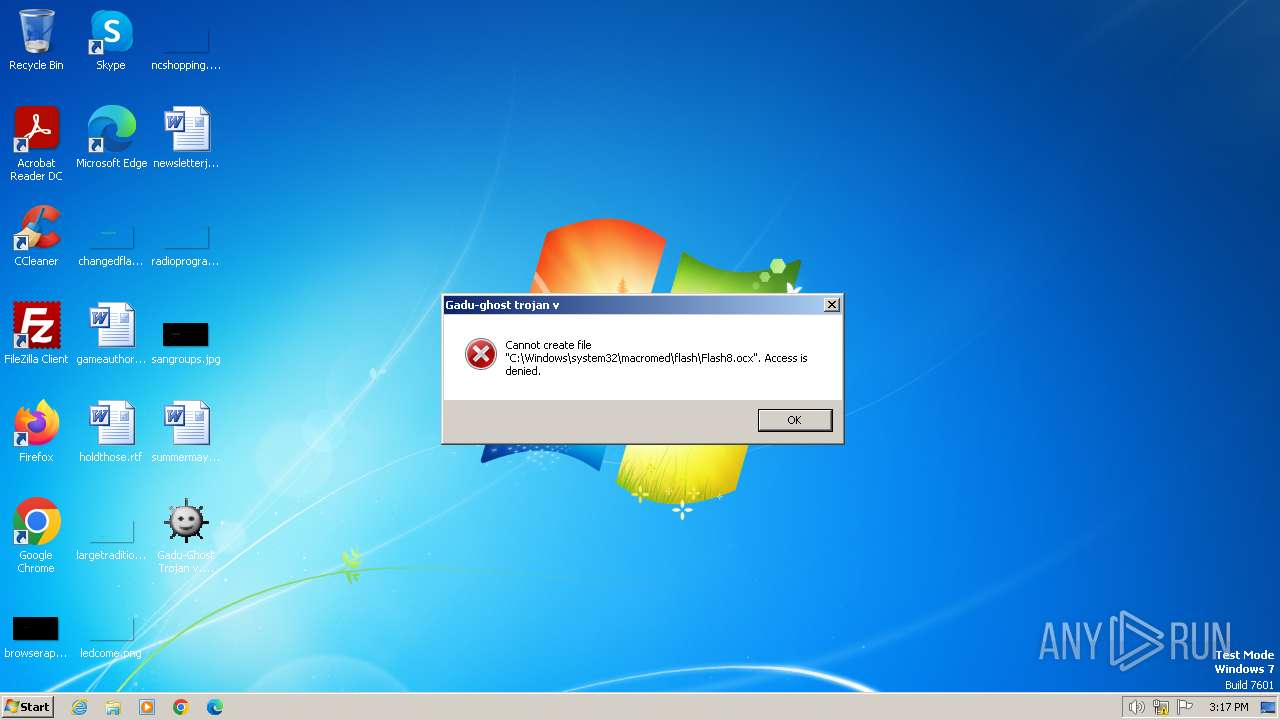
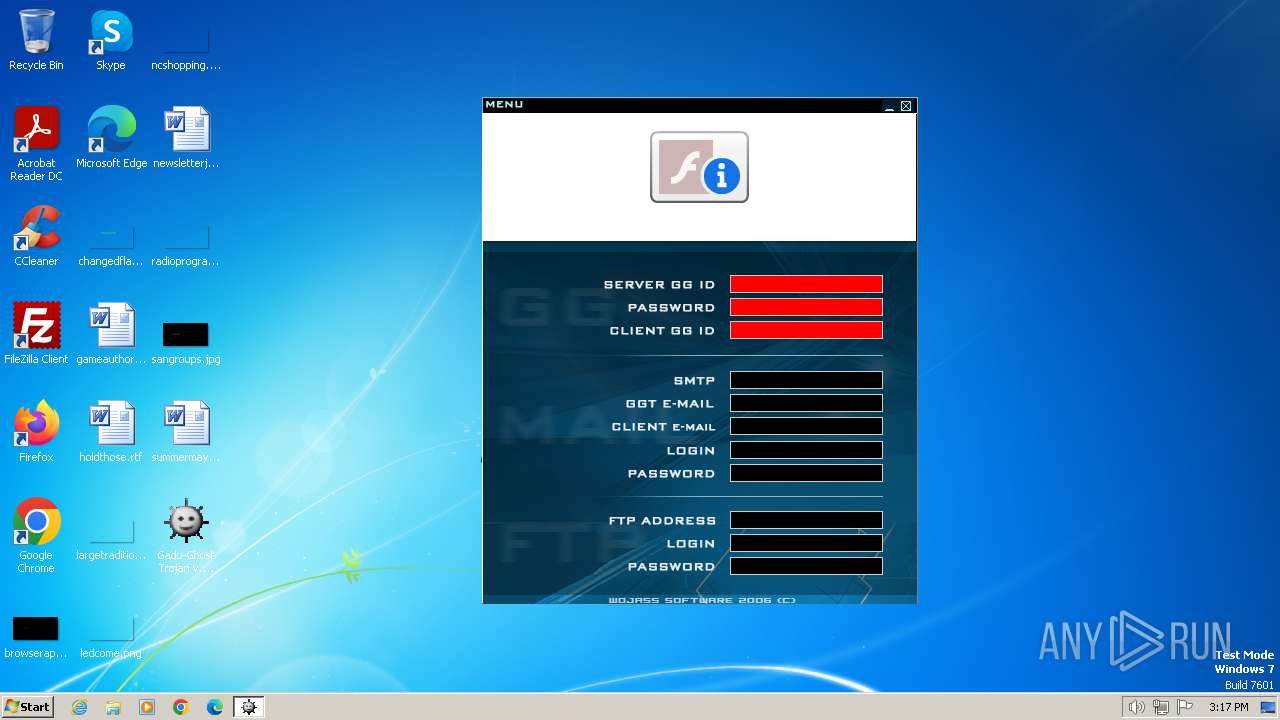
| File name: | Gadu-Ghost Trojan v.2.3 pb.exe |
| Full analysis: | https://app.any.run/tasks/6250f4c1-6f4d-4fe4-a6ee-133ca17b21ab |
| Verdict: | Malicious activity |
| Analysis date: | August 03, 2024, 14:16:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | MS-DOS executable PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | A23BCD6FC4D2AF04C66BDCB5A3D7F449 |
| SHA1: | DDF29316EFDD89D718B4D1266641607AFDAC7B59 |
| SHA256: | 1CB371A602F6DC3A856027CBDA881549AF56F4DE0C43FBFA54DCE9DBA9FF3B3F |
| SSDEEP: | 49152:fo9xIWrJ1b+y8cB4YDe38ftZpukHGsmwCam3VLZz3SepndlrdZHdTjVSCt2dXM+5:f4xHrTb38t0ZpukmsmwCagLd3pdjnVSL |
MALICIOUS
Drops the executable file immediately after the start
- Gadu-Ghost Trojan v.2.3 pb.exe (PID: 2992)
- Gadu-Ghost Trojan v.2.3 pb.exe (PID: 3468)
Registers / Runs the DLL via REGSVR32.EXE
- Gadu-Ghost Trojan v.2.3 pb.exe (PID: 3468)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- Gadu-Ghost Trojan v.2.3 pb.exe (PID: 2992)
- Gadu-Ghost Trojan v.2.3 pb.exe (PID: 3468)
There is functionality for communication over UDP network (YARA)
- Gadu-Ghost Trojan v.2.3 pb.exe (PID: 2992)
- Gadu-Ghost Trojan v.2.3 pb.exe (PID: 3468)
Executable content was dropped or overwritten
- Gadu-Ghost Trojan v.2.3 pb.exe (PID: 3468)
Reads settings of System Certificates
- Gadu-Ghost Trojan v.2.3 pb.exe (PID: 3468)
INFO
Reads the computer name
- Gadu-Ghost Trojan v.2.3 pb.exe (PID: 2992)
- wmpnscfg.exe (PID: 3452)
- Gadu-Ghost Trojan v.2.3 pb.exe (PID: 3468)
Checks supported languages
- Gadu-Ghost Trojan v.2.3 pb.exe (PID: 2992)
- wmpnscfg.exe (PID: 3452)
- Gadu-Ghost Trojan v.2.3 pb.exe (PID: 3468)
Reads the machine GUID from the registry
- Gadu-Ghost Trojan v.2.3 pb.exe (PID: 2992)
- Gadu-Ghost Trojan v.2.3 pb.exe (PID: 3468)
Reads CPU info
- Gadu-Ghost Trojan v.2.3 pb.exe (PID: 2992)
- Gadu-Ghost Trojan v.2.3 pb.exe (PID: 3468)
UPX packer has been detected
- Gadu-Ghost Trojan v.2.3 pb.exe (PID: 2992)
- Gadu-Ghost Trojan v.2.3 pb.exe (PID: 3468)
Manual execution by a user
- wmpnscfg.exe (PID: 3452)
- Gadu-Ghost Trojan v.2.3 pb.exe (PID: 3468)
Create files in a temporary directory
- Gadu-Ghost Trojan v.2.3 pb.exe (PID: 3468)
Creates files or folders in the user directory
- Gadu-Ghost Trojan v.2.3 pb.exe (PID: 3468)
- Gadu-Ghost Trojan v.2.3 pb.exe (PID: 2992)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Mew compressed Win32 Executable (88.8) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (5.9) |
| .exe | | | Generic Win/DOS Executable (2.6) |
| .exe | | | DOS Executable Generic (2.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | - |
| CodeSize: | 512 |
| InitializedDataSize: | - |
| UninitializedDataSize: | - |
| EntryPoint: | 0x7e2143 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
43
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2992 | "C:\Users\admin\Desktop\Gadu-Ghost Trojan v.2.3 pb.exe" | C:\Users\admin\Desktop\Gadu-Ghost Trojan v.2.3 pb.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3228 | regsvr32 /s C:\Windows\system32\macromed\flash\Flash8.ocx | C:\Windows\System32\regsvr32.exe | — | Gadu-Ghost Trojan v.2.3 pb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 5 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3452 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3468 | "C:\Users\admin\Desktop\Gadu-Ghost Trojan v.2.3 pb.exe" | C:\Users\admin\Desktop\Gadu-Ghost Trojan v.2.3 pb.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
1 914
Read events
1 912
Write events
0
Delete events
2
Modification events
| (PID) Process: | (3228) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\MacromediaFlashPaper.MacromediaFlashPaper\CLSID |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3228) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\MacromediaFlashPaper.MacromediaFlashPaper |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
1
Suspicious files
44
Text files
0
Unknown types
39
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2992 | Gadu-Ghost Trojan v.2.3 pb.exe | C:\Users\admin\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\settings.sol | sol | |
MD5:4E442C66F85325FE25C83EE8855432CA | SHA256:C1F7F9394B37899EC9EFE36DD2C26C80837F357D86F20F67DC13F6491F0CFEA9 | |||
| 3468 | Gadu-Ghost Trojan v.2.3 pb.exe | C:\Users\admin\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\settings.sxx | binary | |
MD5:42792AF9048950059A515744EEE118CA | SHA256:F872DCB3753C49266F144FCB8F7D0111C507D42B4ED5D57A3A786E845B762B8E | |||
| 3468 | Gadu-Ghost Trojan v.2.3 pb.exe | C:\Windows\System32\Macromed\Flash\Flash8.ocx | executable | |
MD5:900373C059C2B51CA91BF110DBDECB33 | SHA256:31453FD8F743C19E27F8FA04EE88DFEBE95A7884CDFBC15AB0EB8994829AAD61 | |||
| 3468 | Gadu-Ghost Trojan v.2.3 pb.exe | C:\Users\admin\AppData\Local\Temp\dsgnggtmenu | binary | |
MD5:1D4DA921130A08E7309FA83201507450 | SHA256:3307A0F45B4DBC7E025AF104EFCCB1F2739EB1093ADC47CDDC5700B364714B27 | |||
| 2992 | Gadu-Ghost Trojan v.2.3 pb.exe | C:\Users\admin\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\settings.sxx | sol | |
MD5:4E442C66F85325FE25C83EE8855432CA | SHA256:C1F7F9394B37899EC9EFE36DD2C26C80837F357D86F20F67DC13F6491F0CFEA9 | |||
| 3468 | Gadu-Ghost Trojan v.2.3 pb.exe | C:\Users\admin\AppData\Local\Temp\dsgnggttop | binary | |
MD5:1F40DBFB144B04824E8B213465A1A038 | SHA256:55CD8D4BC348F4D8E802DB8150E9E423C5E625D28E69257C384B56C82B2833A0 | |||
| 3468 | Gadu-Ghost Trojan v.2.3 pb.exe | C:\Users\admin\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\settings.sol | binary | |
MD5:42792AF9048950059A515744EEE118CA | SHA256:F872DCB3753C49266F144FCB8F7D0111C507D42B4ED5D57A3A786E845B762B8E | |||
| 3468 | Gadu-Ghost Trojan v.2.3 pb.exe | C:\Users\admin\AppData\Roaming\Macromedia\Flash Player\openssl\cache\RevocationCacheFile.dat | binary | |
MD5:0F343B0931126A20F133D67C2B018A3B | SHA256:5F70BF18A086007016E948B04AED3B82103A36BEA41755B6CDDFAF10ACE3C6EF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
18
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 23.50.131.216:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 23.48.23.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3468 | Gadu-Ghost Trojan v.2.3 pb.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | — | — | unknown |
3468 | Gadu-Ghost Trojan v.2.3 pb.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | — | — | unknown |
3468 | Gadu-Ghost Trojan v.2.3 pb.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 87.248.202.1:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5445ebff82c5850f | unknown | — | — | whitelisted |
3468 | Gadu-Ghost Trojan v.2.3 pb.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
— | — | 239.255.255.250:3702 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1372 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1372 | svchost.exe | 23.50.131.216:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 23.48.23.190:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fpdownload.macromedia.com |
| whitelisted |