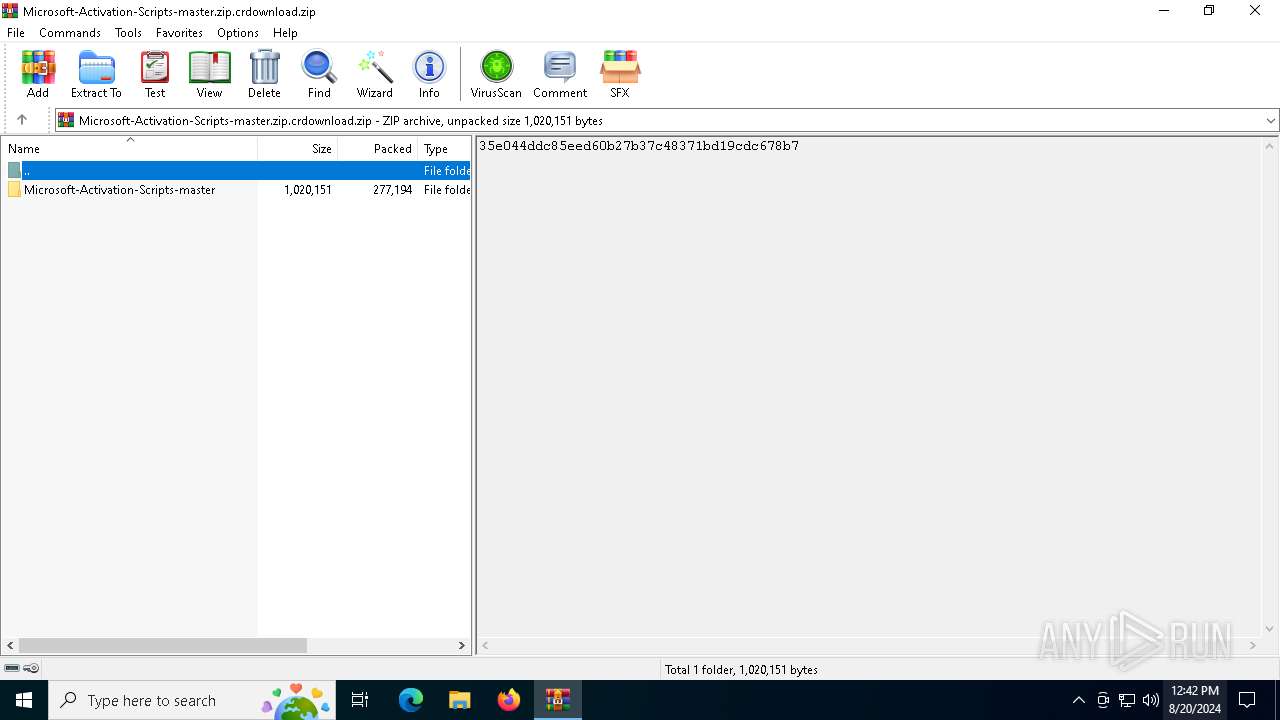
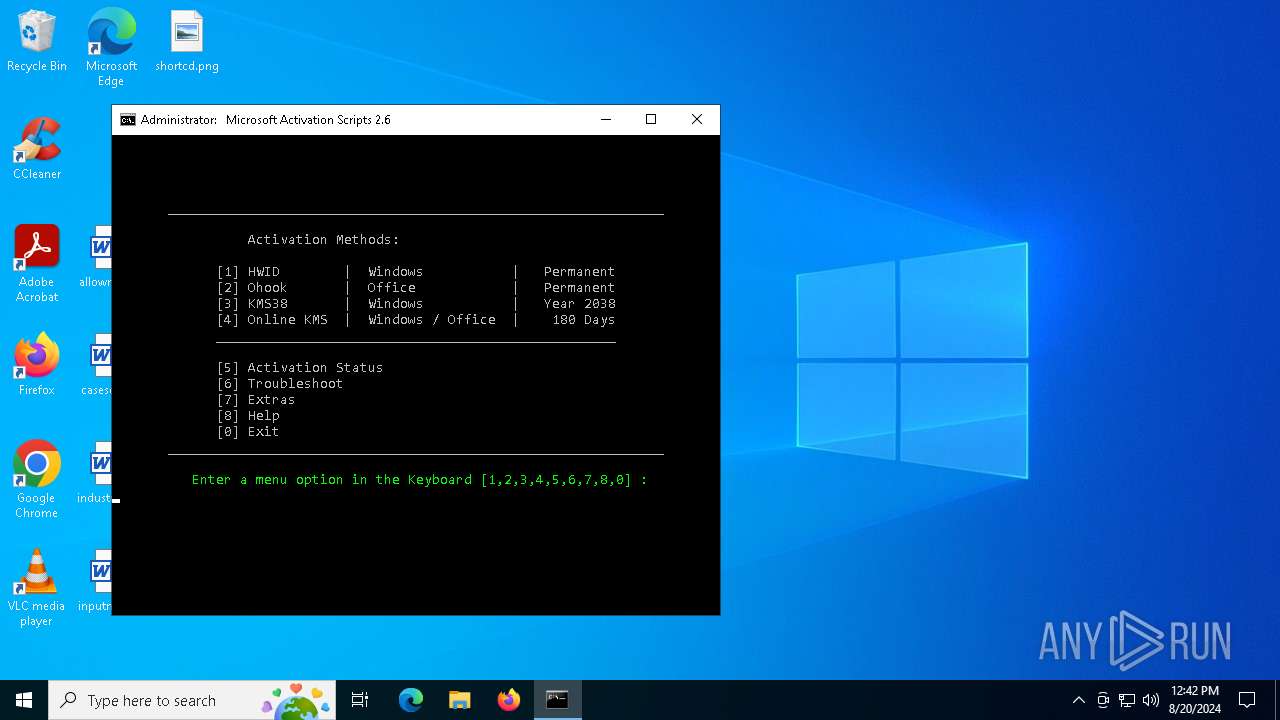
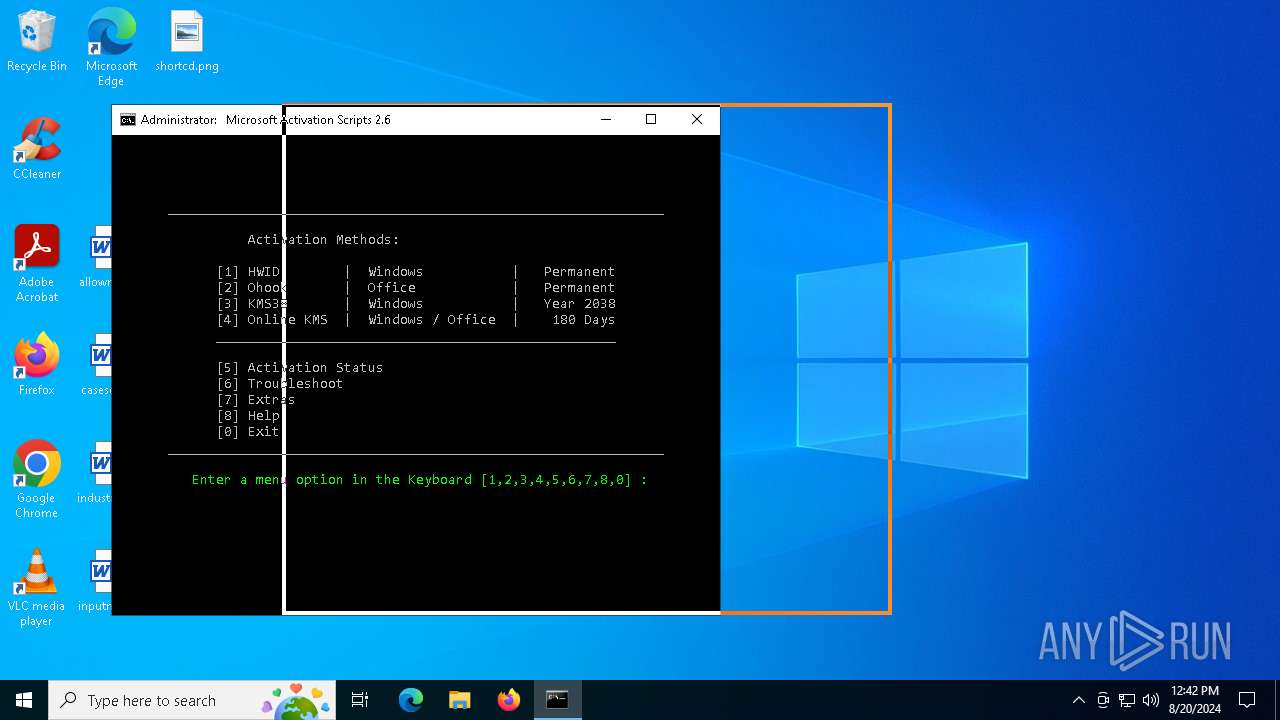
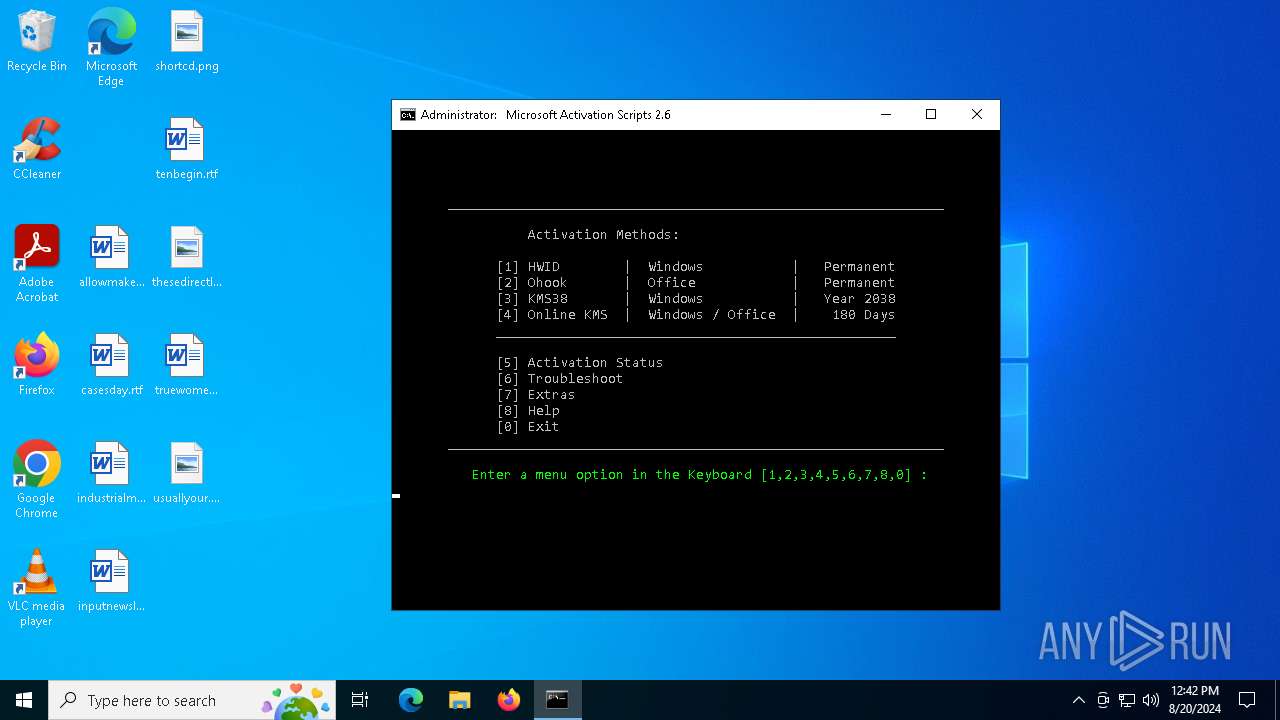
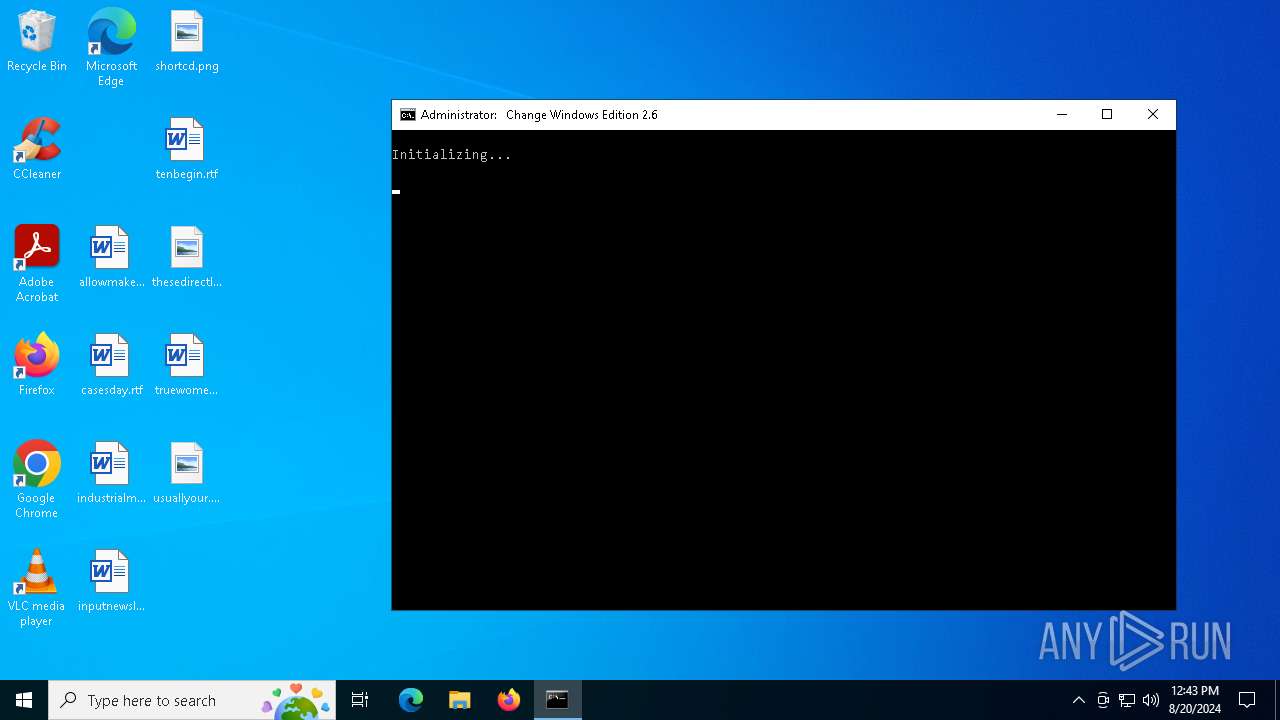
| File name: | Microsoft-Activation-Scripts-master.zip.crdownload |
| Full analysis: | https://app.any.run/tasks/2e99f97b-f969-408f-9fb2-77cab3020ab8 |
| Verdict: | Malicious activity |
| Analysis date: | August 20, 2024, 12:42:04 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | DE09BA441A8B0405274E954CAA22B9A0 |
| SHA1: | 8FF98BF0A0C783B3E64049C09DA21900F94CF43B |
| SHA256: | 1C99F1DAADBA3308396326E39021363322B881612A5123D36DB1EE2B33BD25A9 |
| SSDEEP: | 12288:sa69I/osqUIyT6CWEzxkMvKiaZOn2n4ccj:s/9GosqUIyT6JEz2MiiaZOn2n4z |
MALICIOUS
No malicious indicators.SUSPICIOUS
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 252)
- cmd.exe (PID: 6640)
- cmd.exe (PID: 3980)
Starts SC.EXE for service management
- cmd.exe (PID: 252)
- cmd.exe (PID: 6640)
Application launched itself
- cmd.exe (PID: 252)
- cmd.exe (PID: 6396)
- cmd.exe (PID: 6640)
- cmd.exe (PID: 3784)
- cmd.exe (PID: 6396)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 252)
- cmd.exe (PID: 6396)
- cmd.exe (PID: 6640)
- cmd.exe (PID: 3784)
- cmd.exe (PID: 6396)
Executing commands from ".cmd" file
- cmd.exe (PID: 252)
- cmd.exe (PID: 6640)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 252)
- cmd.exe (PID: 6640)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1344)
- cmd.exe (PID: 3964)
- cmd.exe (PID: 6640)
- cmd.exe (PID: 3268)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 6640)
Hides command output
- cmd.exe (PID: 2868)
- cmd.exe (PID: 4680)
- cmd.exe (PID: 3356)
- cmd.exe (PID: 5180)
- cmd.exe (PID: 5556)
- cmd.exe (PID: 6028)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 2868)
- cmd.exe (PID: 6028)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 3356)
Executable content was dropped or overwritten
- Dism.exe (PID: 5096)
- Dism.exe (PID: 6452)
Process drops legitimate windows executable
- Dism.exe (PID: 5096)
- Dism.exe (PID: 6452)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 6296)
- DismHost.exe (PID: 4824)
The process creates files with name similar to system file names
- Dism.exe (PID: 6452)
- Dism.exe (PID: 5096)
INFO
Manual execution by a user
- WinRAR.exe (PID: 6272)
- cmd.exe (PID: 252)
Checks operating system version
- cmd.exe (PID: 252)
- cmd.exe (PID: 6640)
Checks supported languages
- mode.com (PID: 6788)
- mode.com (PID: 6684)
- mode.com (PID: 6988)
- DismHost.exe (PID: 6296)
- DismHost.exe (PID: 4824)
- mode.com (PID: 6876)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 1744)
- WMIC.exe (PID: 6512)
- WMIC.exe (PID: 2396)
- WMIC.exe (PID: 6692)
Reads the computer name
- DismHost.exe (PID: 6296)
- DismHost.exe (PID: 4824)
Reads Environment values
- DismHost.exe (PID: 6296)
- DismHost.exe (PID: 4824)
Create files in a temporary directory
- Dism.exe (PID: 6452)
- Dism.exe (PID: 5096)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:08:11 17:04:06 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Microsoft-Activation-Scripts-master/ |
Total processes
328
Monitored processes
199
Malicious processes
6
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 8 | find /i "computersystem" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 32 | reg query "HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders" /v Desktop | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | find /i " ServerRdsh " | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 240 | reg query "HKCU\Console" /v ForceV2 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 252 | "C:\WINDOWS\System32\cmd.exe" /C "C:\Users\admin\Desktop\MAS_AIO-CRC32_8C3AA7E0.cmd" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 252 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo " ProfessionalEducation ProfessionalWorkstation Education ProfessionalCountrySpecific ProfessionalSingleLanguage ServerRdsh IoTEnterprise Enterprise " " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 508 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo " ProfessionalEducation ProfessionalWorkstation Education ProfessionalCountrySpecific ProfessionalSingleLanguage ServerRdsh IoTEnterprise Enterprise " " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1060 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo " ProfessionalEducation ProfessionalWorkstation Education ProfessionalCountrySpecific ProfessionalSingleLanguage ServerRdsh IoTEnterprise Enterprise " " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1168 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo prompt $E " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1280 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo " ProfessionalEducation ProfessionalWorkstation Education ProfessionalCountrySpecific ProfessionalSingleLanguage ServerRdsh IoTEnterprise Enterprise " " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
32 499
Read events
32 466
Write events
33
Delete events
0
Modification events
| (PID) Process: | (7152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (7152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (7152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (7152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master.zip.crdownload.zip | |||
| (PID) Process: | (7152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000200000003000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (7152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
100
Suspicious files
1
Text files
25
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6272 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\MAS\Separate-Files-Version\Activators\HWID_Activation.cmd | text | |
MD5:28312C7DAAFDE6AAC9F829513715C69F | SHA256:00836E3642F9D4E027BBBE8BDB206284E817EE60553FD1340B50C7EEF77DA847 | |||
| 6272 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\.gitattributes | text | |
MD5:F9F25F50652FBF7E61039A620BE51FA6 | SHA256:42708C4FE8A9F14722BF6C2BA13BC7218C4E2ECCEB8A87C0FFBBD62D2D7CBB74 | |||
| 6272 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\MAS\Separate-Files-Version\Change_Edition.cmd | text | |
MD5:D20EA1F7448A12E835E3F40DF0FF9AFA | SHA256:E55544BF48735CD7DF2E891E0B7B809FC96EF2703E0772DD6C232498DAD8B110 | |||
| 6272 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\MAS\Separate-Files-Version\Check-Activation-Status-vbs.cmd | text | |
MD5:0ABF0120716BAFCF4D9301D5A70EF1CF | SHA256:9A225A9253B8D2DB1DA6001422A40D175FD5E52057F2F2032947037608D23612 | |||
| 6272 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\LICENSE | text | |
MD5:5B4473596678D62D9D83096273422C8C | SHA256:E57F1C320B8CF8798A7D2FF83A6F9E06A33A03585F6E065FEA97F1D86DB84052 | |||
| 6272 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\MAS\Separate-Files-Version\Activators\KMS38_Activation.cmd | text | |
MD5:421BE375C0E33294CF4E0F75D97AA928 | SHA256:D85D2DAF27AFCF21DBAA1AF528F034009E30BACA8050A1A4D26C8DA7927C95A6 | |||
| 6272 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\MAS\Separate-Files-Version\Troubleshoot.cmd | text | |
MD5:CA4F211BED0FD63236E2CECE5BCA2E0D | SHA256:5DFA0352906231CE8769EEEF1056711C5F5E88770AB21FA44EF1B65D5178422F | |||
| 6272 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\MAS\Separate-Files-Version\Extract_OEM_Folder.cmd | text | |
MD5:B1EC6D1E48D653D74D896910A2763402 | SHA256:CB1EA084614DE7B67177A127505F0864E2CA5BD807B2A578D28CD30957F3FF21 | |||
| 6272 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\MAS\Separate-Files-Version\Check-Activation-Status-wmi.cmd | text | |
MD5:FC7DFD4ABBD167E7303301FA7F593CC2 | SHA256:DE2A3F3016732D6C46CEFA13BA70889EDEDA8FAE3A244DD1C507F1B80D4579F3 | |||
| 6272 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\MAS\All-In-One-Version\MAS_AIO-CRC32_8C3AA7E0.cmd | text | |
MD5:92CC8F1F67A875563D1299E7DD7B5723 | SHA256:D666A4C7810B9D3FE9749F2D4E15C5A65D4AC0D7F0B14A144D6631CE61CC5DF3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
29
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6604 | SIHClient.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6744 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4816 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6744 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
updatecheck.massgrave.dev |
| unknown |
Threats
Process | Message |
|---|---|
Dism.exe | PID=5096 TID=5544 Instantiating the Provider Store. - CDISMImageSession::get_ProviderStore |
Dism.exe | PID=5096 TID=5544 Initializing a provider store for the LOCAL session type. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=5096 TID=5544 Attempting to initialize the logger from the Image Session. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=5096 TID=5544 Provider has not previously been encountered. Attempting to initialize the provider. - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=5096 TID=5544 Loading Provider from location C:\Windows\System32\Dism\LogProvider.dll - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=5096 TID=5544 Connecting to the provider located at C:\Windows\System32\Dism\LogProvider.dll. - CDISMProviderStore::Internal_LoadProvider |
DismHost.exe | PID=6296 TID=6816 Disconnecting the provider store - CDISMImageSession::Final_OnDisconnect |
DismHost.exe | PID=6296 TID=6816 Encountered a loaded provider DISMLogger. - CDISMProviderStore::Internal_DisconnectProvider |
DismHost.exe | PID=6296 TID=6816 Disconnecting Provider: DISMLogger - CDISMProviderStore::Internal_DisconnectProvider |
Dism.exe | PID=5096 TID=5544 Disconnecting the provider store - CDISMImageSession::Final_OnDisconnect |