| File name: | gatherNetworkInfo.vbs |
| Full analysis: | https://app.any.run/tasks/8ef592ff-eaf8-408d-80bc-b2e0480892b1 |
| Verdict: | Malicious activity |
| Analysis date: | May 22, 2024, 01:04:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | DA4D4261A43DE7E851A9378ED0668EB9 |
| SHA1: | E4227677479EFB82B6E7044BCC1B28CB9CB5A4F5 |
| SHA256: | 1C9337004CBD0E1E5C09BEE609EE1991BE3AA791C31F1C873E6D8F70C3C876D0 |
| SSDEEP: | 1536:sImNGeeGUJIgZf/A+qfwkgKo9kNxyJ3OOjPl68fef0qLbIE5ToGaUKTYL7TBHQ/E:sImNGXGUJtx/A+qfol6yqEs8q |
MALICIOUS
Creates a new folder (SCRIPT)
- wscript.exe (PID: 3956)
Opens a text file (SCRIPT)
- wscript.exe (PID: 3956)
Checks whether a specified folder exists (SCRIPT)
- wscript.exe (PID: 3956)
Accesses environment variables (SCRIPT)
- wscript.exe (PID: 3956)
Accesses the network adapter (Win32_NetworkAdapter) via WMI (SCRIPT)
- wscript.exe (PID: 3956)
Gets %windir% folder path (SCRIPT)
- wscript.exe (PID: 3956)
Accesses name of a computer manufacturer via WMI (SCRIPT)
- wscript.exe (PID: 3956)
SUSPICIOUS
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 3956)
Reads data from a binary Stream object (SCRIPT)
- wscript.exe (PID: 3956)
Get information on the list of running processes
- cmd.exe (PID: 948)
- wscript.exe (PID: 3956)
Uses WEVTUTIL.EXE to export log
- cmd.exe (PID: 2784)
- cmd.exe (PID: 2824)
- cmd.exe (PID: 2896)
- cmd.exe (PID: 4024)
- cmd.exe (PID: 4092)
- cmd.exe (PID: 2204)
- cmd.exe (PID: 3540)
Reads the Internet Settings
- wscript.exe (PID: 3956)
- dxdiag.exe (PID: 1424)
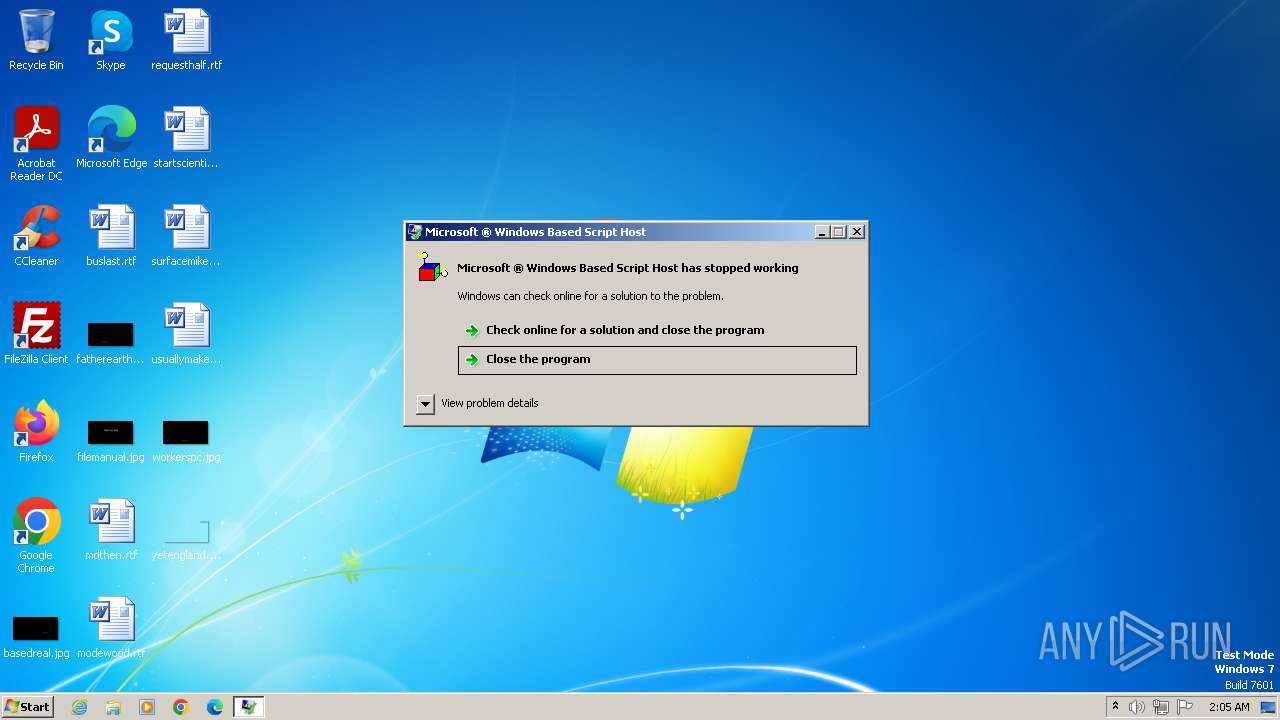
Runs shell command (SCRIPT)
- wscript.exe (PID: 3956)
Uses WEVTUTIL.EXE to archive the exported log
- cmd.exe (PID: 2792)
- cmd.exe (PID: 2960)
- cmd.exe (PID: 3040)
- cmd.exe (PID: 2316)
- cmd.exe (PID: 3828)
- cmd.exe (PID: 1580)
- cmd.exe (PID: 3860)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 3208)
- cmd.exe (PID: 2728)
- cmd.exe (PID: 3248)
- cmd.exe (PID: 3492)
- cmd.exe (PID: 1964)
- cmd.exe (PID: 2956)
Suspicious use of NETSH.EXE
- cmd.exe (PID: 3760)
- cmd.exe (PID: 3508)
- cmd.exe (PID: 2776)
- cmd.exe (PID: 2432)
- cmd.exe (PID: 2168)
- cmd.exe (PID: 2840)
- cmd.exe (PID: 3092)
- cmd.exe (PID: 3516)
- cmd.exe (PID: 3916)
- cmd.exe (PID: 4064)
- cmd.exe (PID: 2516)
- cmd.exe (PID: 2736)
- cmd.exe (PID: 4028)
- cmd.exe (PID: 2520)
- cmd.exe (PID: 2356)
- cmd.exe (PID: 3040)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 3956)
Process uses IPCONFIG to discover network configuration
- cmd.exe (PID: 2036)
- cmd.exe (PID: 2136)
Uses ROUTE.EXE to obtain the routing table information
- cmd.exe (PID: 1856)
Reads settings of System Certificates
- certutil.exe (PID: 1936)
- dxdiag.exe (PID: 1424)
Starts SC.EXE for service management
- cmd.exe (PID: 2412)
- cmd.exe (PID: 2436)
- cmd.exe (PID: 1028)
- cmd.exe (PID: 2704)
- cmd.exe (PID: 2536)
- cmd.exe (PID: 2928)
Accesses Windows installation date via WMI (SCRIPT)
- wscript.exe (PID: 3956)
Accesses computer name via WMI (SCRIPT)
- wscript.exe (PID: 3956)
Accesses WMI object caption (SCRIPT)
- wscript.exe (PID: 3956)
Group Policy Discovery via Microsoft GPResult Utility
- cmd.exe (PID: 3992)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- wscript.exe (PID: 3956)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 3956)
Executes WMI query (SCRIPT)
- wscript.exe (PID: 3956)
Uses powercfg.exe to modify the power settings
- cmd.exe (PID: 2424)
INFO
Create files in a temporary directory
- reg.exe (PID: 4044)
- reg.exe (PID: 2024)
- dxdiag.exe (PID: 1424)
- dispdiag.exe (PID: 1820)
- reg.exe (PID: 1120)
Reads security settings of Internet Explorer
- dxdiag.exe (PID: 1424)
Reads the software policy settings
- dxdiag.exe (PID: 1424)
Reads the computer name
- wmpnscfg.exe (PID: 1852)
Manual execution by a user
- wmpnscfg.exe (PID: 1852)
Checks supported languages
- wmpnscfg.exe (PID: 1852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
261
Monitored processes
143
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 112 | "C:\Windows\System32\cmd.exe" /c reg export "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Provider Filters" Reg\AllCredFilter.reg.txt /y | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 316 | "C:\Windows\System32\cmd.exe" /c echo ROUTE PRINT: >> config\envinfo.txt | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 560 | "C:\Windows\System32\cmd.exe" /c systeminfo >> config\osinfo.txt | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 580 | certutil -v -store -silent -user My | C:\Windows\System32\certutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CertUtil.exe Exit code: 0 Version: 6.1.7601.18151 (win7sp1_gdr.130512-1533) Modules
| |||||||||||||||
| 768 | "C:\Windows\System32\cmd.exe" /c dxdiag /t dxdiag.txt | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 824 | "C:\Windows\System32\cmd.exe" /c certutil -v -enterprise -store -silent NTAuth >> config\envinfo.txt | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 2147942402 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 904 | powercfg.exe /batteryreport /output config\battery-report.html | C:\Windows\System32\powercfg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Power Settings Command-Line Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 928 | netsh advfirewall monitor show currentprofile | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 948 | "C:\Windows\System32\cmd.exe" /c tasklist /svc > processes.txt | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 948 | sc query eaphost | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
30 981
Read events
29 717
Write events
1 248
Delete events
16
Modification events
| (PID) Process: | (3956) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3956) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3956) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3956) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1848) systeminfo.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1848) systeminfo.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\mlang.dll,-4386 |
Value: English (United States) | |||
| (PID) Process: | (2952) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2952) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-100 |
Value: DHCP Quarantine Enforcement Client | |||
| (PID) Process: | (2952) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-101 |
Value: Provides DHCP based enforcement for NAP | |||
| (PID) Process: | (2952) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-103 |
Value: 1.0 | |||
Executable files
0
Suspicious files
5
Text files
17
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4044 | reg.exe | C:\Users\admin\AppData\Local\Temp\Reg\Notif.reg.txt | text | |
MD5:0572A78575AA7DA541EE94C4081C9053 | SHA256:E8409F1706A481F7CE1DC8F6ED2C0E0C4F75A010D27C39C5D240BB42706BE3BD | |||
| 4044 | reg.exe | C:\Users\admin\AppData\Local\Temp\REG3952.tmp | text | |
MD5:0572A78575AA7DA541EE94C4081C9053 | SHA256:E8409F1706A481F7CE1DC8F6ED2C0E0C4F75A010D27C39C5D240BB42706BE3BD | |||
| 2744 | cmd.exe | C:\Users\admin\AppData\Local\Temp\config\WindowsFirewallEffectiveRules.txt | text | |
MD5:4E01CF6C5FBB5CFED6A3684F69054365 | SHA256:A31A85891221410DBAF4D3D1BF5F842405140BF583945088D585BC5E8A9FBED3 | |||
| 2476 | cmd.exe | C:\Users\admin\AppData\Local\Temp\config\WindowsFirewallConfig.txt | text | |
MD5:AD8950C6786F15B97C301AA2901E8CA0 | SHA256:6EAC416B5702E44C8E91729AA5B0B24D4FD79EBC723D3572E67807198B5935D5 | |||
| 2024 | reg.exe | C:\Users\admin\AppData\Local\Temp\REG39CF.tmp | text | |
MD5:9A5A295EFDC30925C631166A5D041BD3 | SHA256:88275B3C833910726328D29FB29F50FF6E5D357E8D3F316362C6D709D5FA5EF5 | |||
| 3956 | wscript.exe | C:\Users\admin\AppData\Local\Temp\config\osinfo.txt | text | |
MD5:C0205219CB5287D35C031F5239196BF2 | SHA256:0DE7759F2E8E1A55D71729420D823EEFCA68DB450967F29AE63FF029BD610649 | |||
| 2024 | reg.exe | C:\Users\admin\AppData\Local\Temp\Reg\AllCredFilter.reg.txt | text | |
MD5:9A5A295EFDC30925C631166A5D041BD3 | SHA256:88275B3C833910726328D29FB29F50FF6E5D357E8D3F316362C6D709D5FA5EF5 | |||
| 948 | cmd.exe | C:\Users\admin\AppData\Local\Temp\processes.txt | text | |
MD5:BA4D52BC4659FD91E629D724B3D2C169 | SHA256:150B24E1E0091913AD0DD43DEEB0E8EAD60B4E24F95D66B09ADC070CB2D76AE2 | |||
| 3956 | wscript.exe | C:\Users\admin\AppData\Local\Temp\config\adapterinfo.txt | text | |
MD5:9D802859FD9B5EA73A3E091B1C0BD756 | SHA256:FE76734F917305044829017FC0DCCCEC32E33A1E74A038067ABD8297F338F715 | |||
| 3956 | wscript.exe | C:\Users\admin\AppData\Local\Temp\config\wlaninfo.txt | text | |
MD5:3803004BBE62440259C78E26CAA816BD | SHA256:D0D3E0AACA17C51D781ED4CA6D3D8023EF1B7D374368CB81AD3B9575EA9A8D88 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
5
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1424 | dxdiag.exe | GET | 200 | 23.50.131.200:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?7ada1ce17af523a3 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1424 | dxdiag.exe | 23.50.131.200:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |