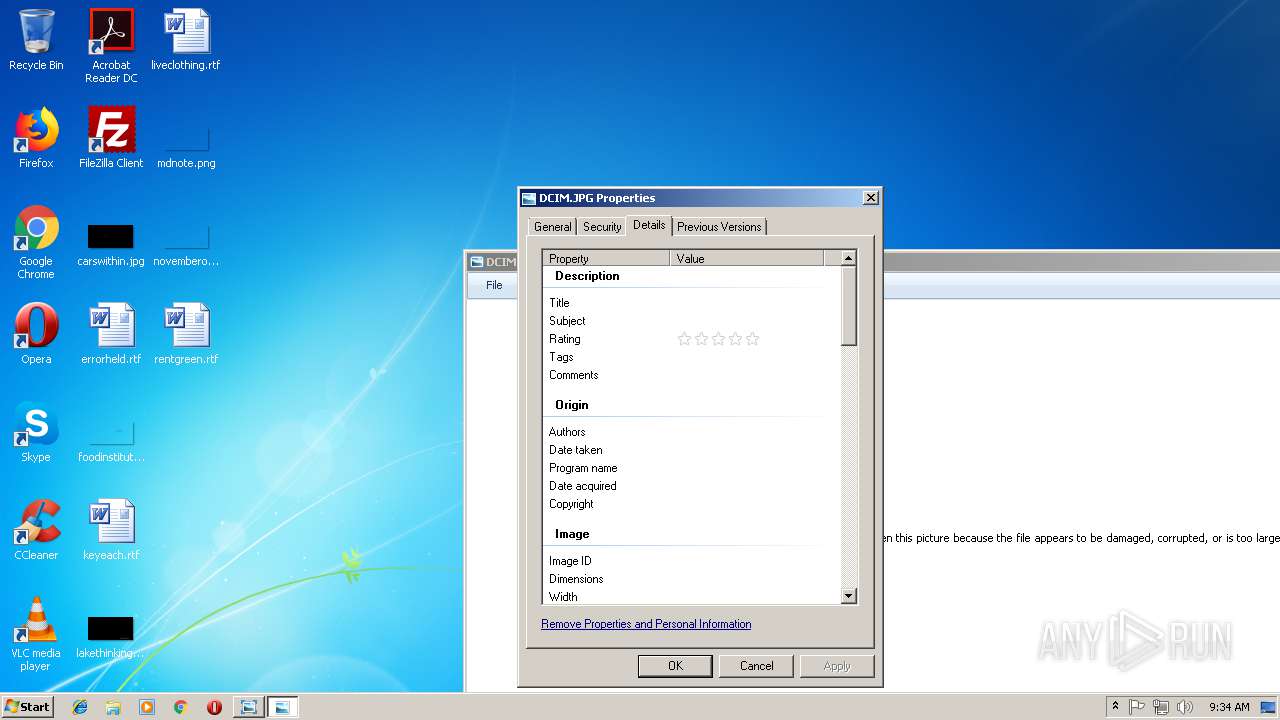
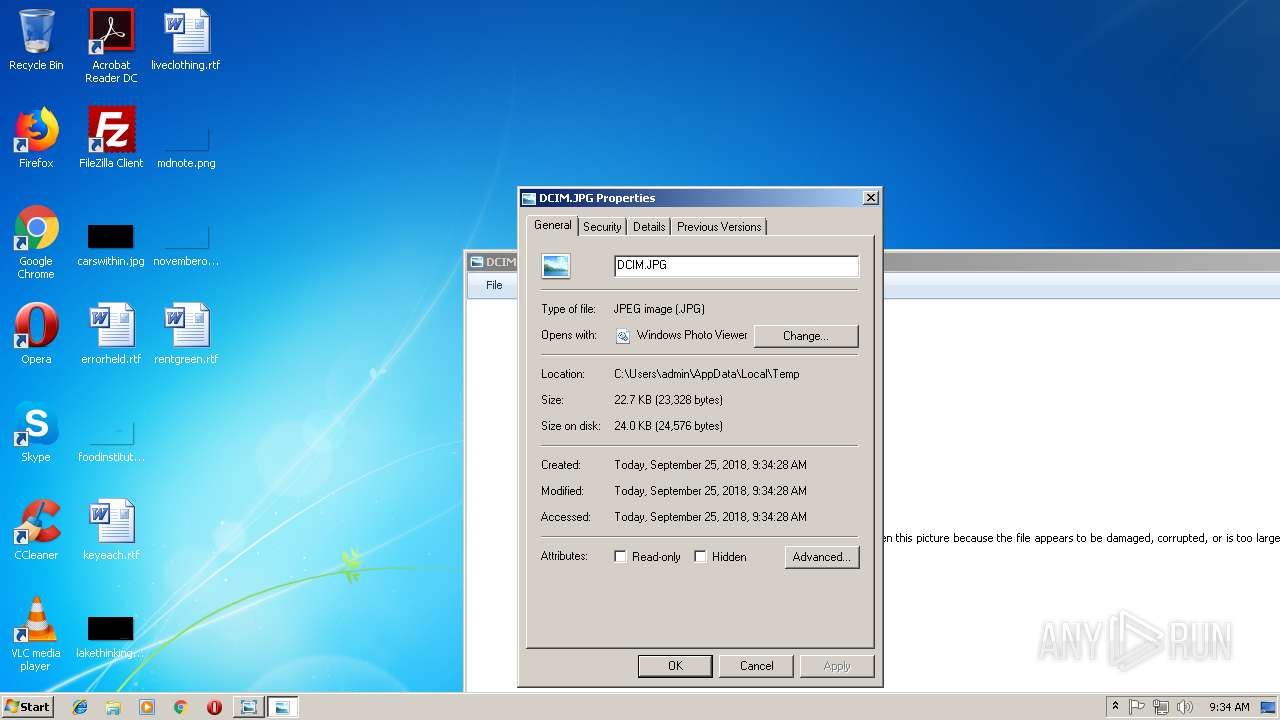
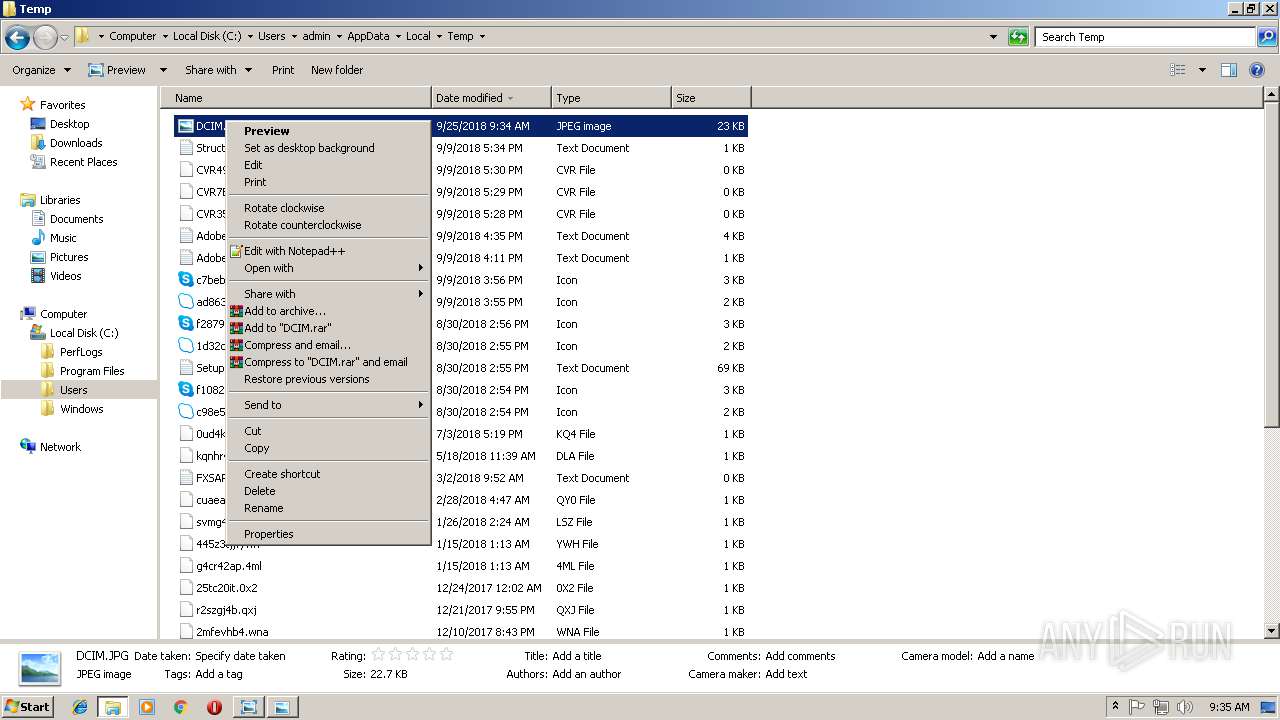
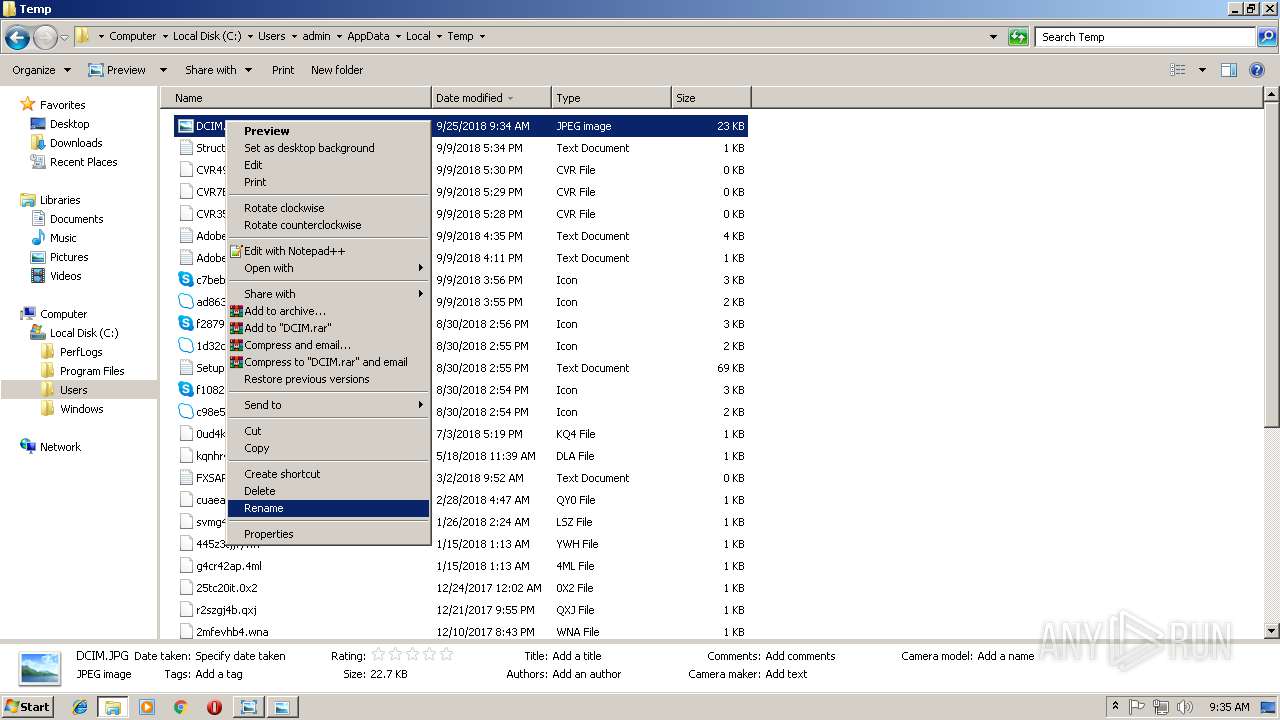
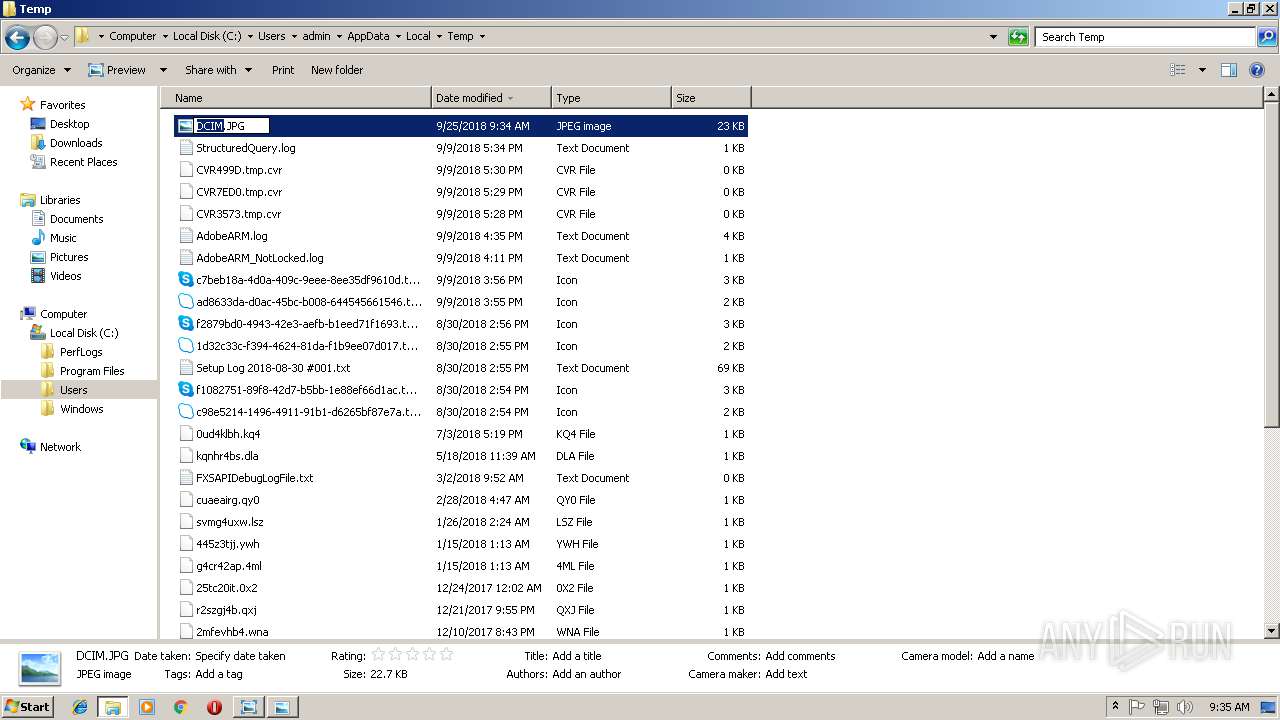
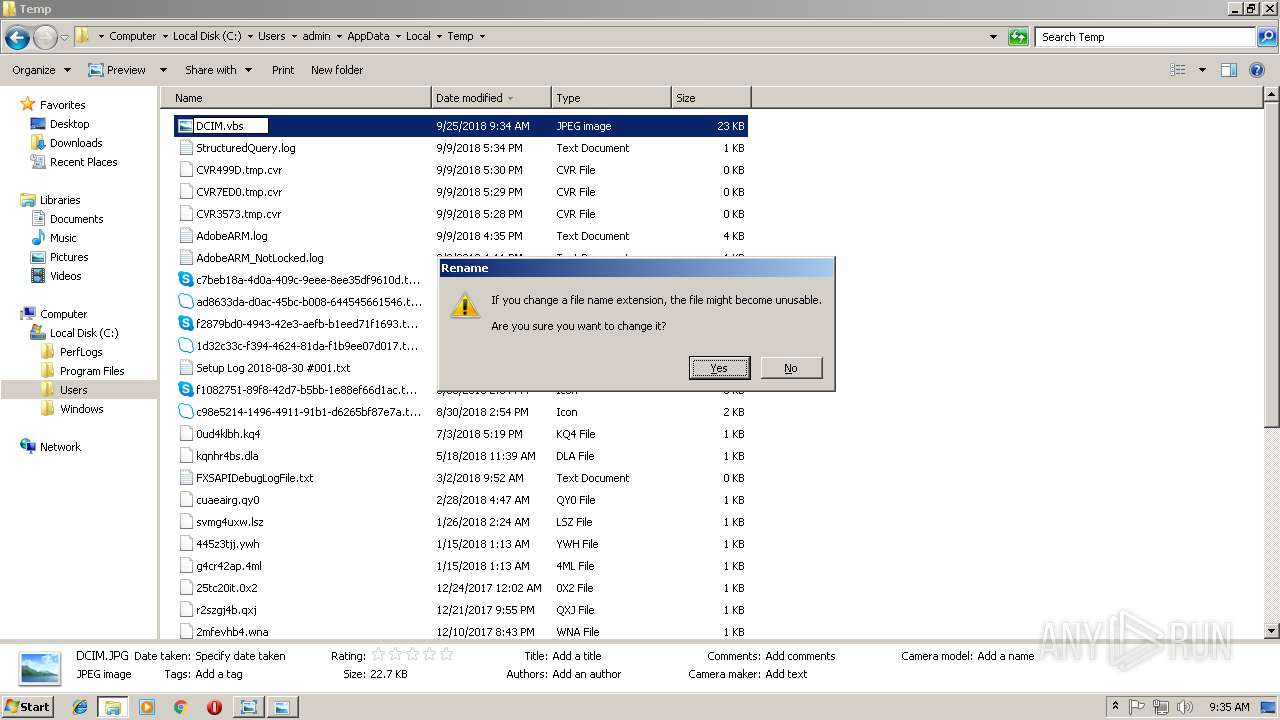
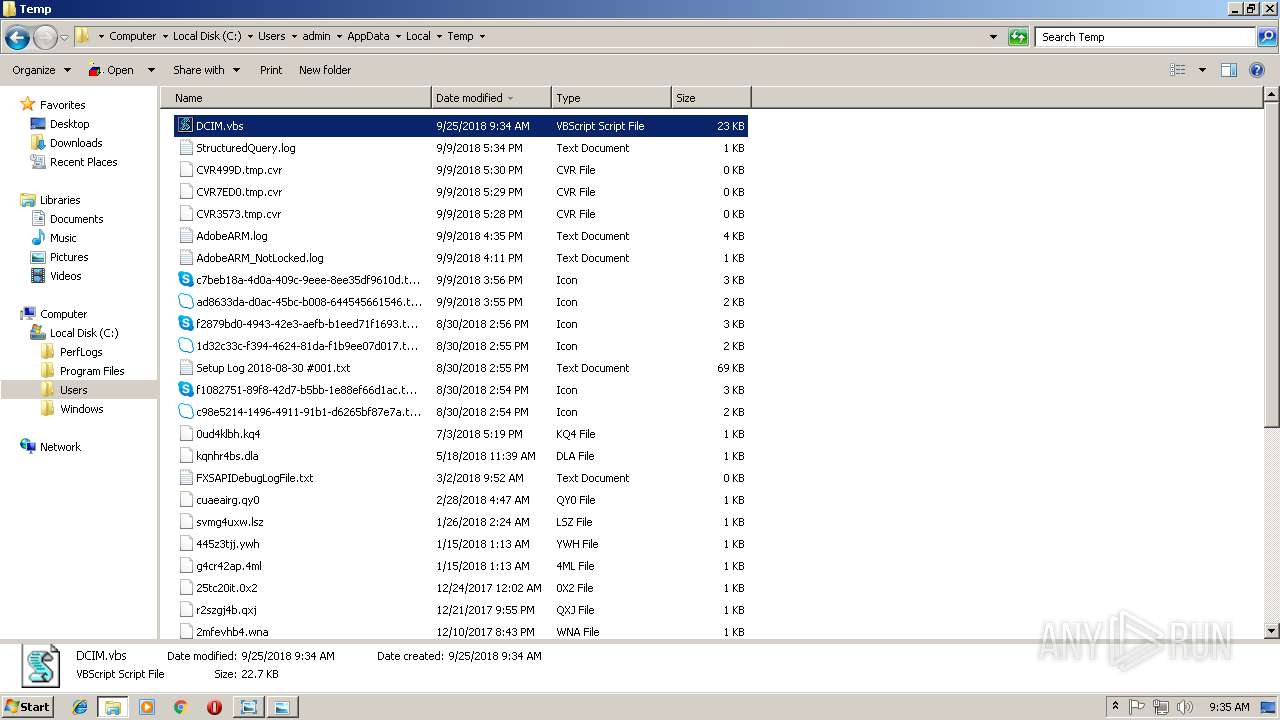
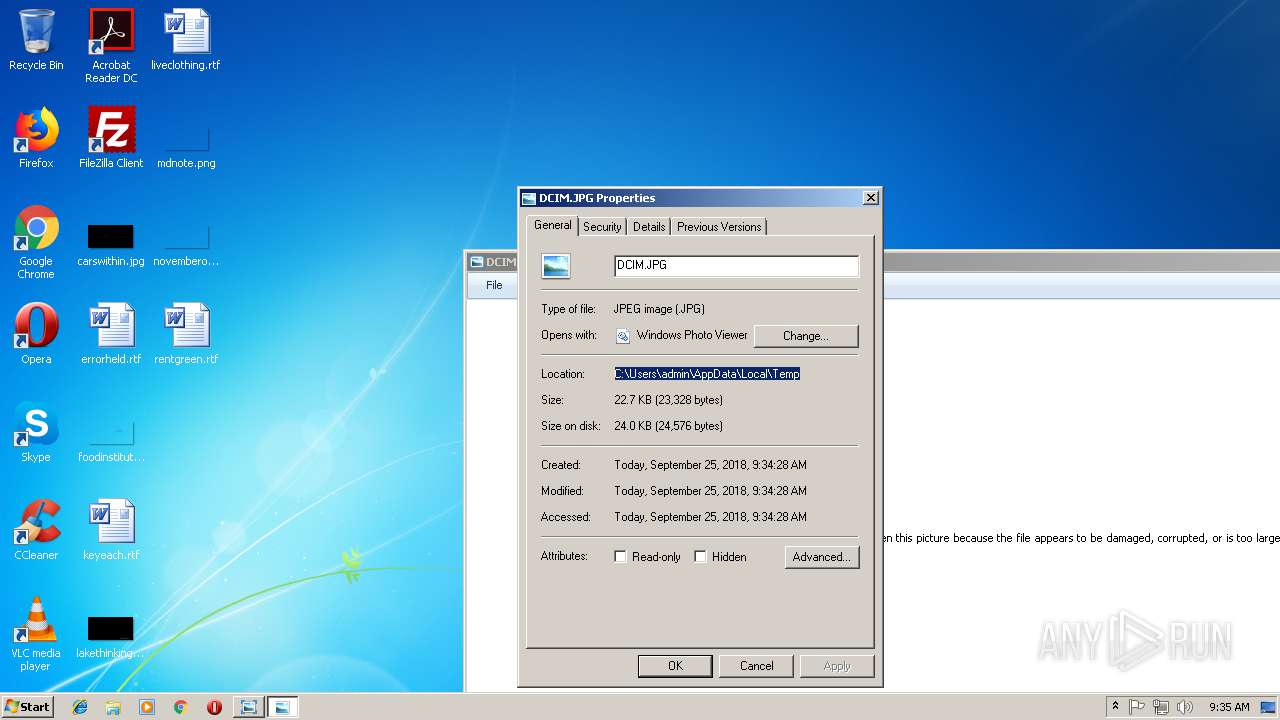
| File name: | DCIM.JPG |
| Full analysis: | https://app.any.run/tasks/10a4b019-d0b8-4611-9833-62fc3f0fa1ef |
| Verdict: | Malicious activity |
| Analysis date: | September 25, 2018, 08:34:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 3A62608CEFCBD3A10AFEA8CDF570749B |
| SHA1: | 77B98B40C24DCCF6762EC704FC33B48FD5CC84A4 |
| SHA256: | 1C44B60B4866B1BC82FB9928D713B010DF42122D156A5CC6C70B2A2B35F38A34 |
| SSDEEP: | 384:/Lkj3tQYhzGhPh8hGpC1OGiBt7M0mCrRzRZREcRmRGRURtRa9mrwdbKoTnxRosBU:/Lkj3tQYhzGhPh8hGpC1OGiBt7M0mCrm |
MALICIOUS
Changes the autorun value in the registry
- WScript.exe (PID: 3980)
Writes to a start menu file
- WScript.exe (PID: 3980)
Application was dropped or rewritten from another process
- WScript.exe (PID: 3980)
SUSPICIOUS
Connects to unusual port
- WScript.exe (PID: 3980)
Executable content was dropped or overwritten
- WScript.exe (PID: 3980)
Creates files in the user directory
- WScript.exe (PID: 3980)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 964 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1972 | "C:\Windows\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\AppData\Local\Temp\DCIM.JPG | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3980 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\DCIM.vbs" | C:\Windows\System32\WScript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
187
Read events
155
Write events
32
Delete events
0
Modification events
| (PID) Process: | (1972) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: rundll32.exe | |||
| (PID) Process: | (1972) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {A38B883C-1682-497E-97B0-0A3A9E801682} {886D8EEB-8CF2-4446-8D02-CDBA1DBDCF99} 0xFFFF |
Value: 01000000000000003A4137A0AA54D401 | |||
| (PID) Process: | (1972) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Windows Photo Viewer\PhotoViewer.dll |
Value: Windows Photo Viewer | |||
| (PID) Process: | (3980) WScript.exe | Key: | HKEY_CURRENT_USER |
| Operation: | write | Name: | Visionneuse de Photos Windows |
Value: False - 9/25/2018 | |||
| (PID) Process: | (3980) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Visionneuse de Photos Windows |
Value: "C:\Users\admin\PerfLogs\csrss.pif" /e:Vbscript.Encode "C:\Users\admin\PerfLogs\DCIM.JPG" /MINIMIZED | |||
| (PID) Process: | (3980) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Visionneuse de Photos Windows |
Value: "C:\Users\admin\PerfLogs\csrss.pif" /e:Vbscript.Encode "C:\Users\admin\PerfLogs\DCIM.JPG" /MINIMIZED | |||
| (PID) Process: | (3980) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced |
| Operation: | write | Name: | ShowSuperHidden |
Value: 0 | |||
| (PID) Process: | (3980) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3980) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3980) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
Executable files
1
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3980 | WScript.exe | C:\Users\admin\PerfLogs\DCIM.JPG | text | |
MD5:3A62608CEFCBD3A10AFEA8CDF570749B | SHA256:1C44B60B4866B1BC82FB9928D713B010DF42122D156A5CC6C70B2A2B35F38A34 | |||
| 3980 | WScript.exe | C:\Users\admin\PerfLogs\csrss.pif | executable | |
MD5:D1AB72DB2BEDD2F255D35DA3DA0D4B16 | SHA256:047F3C5A7AB0EA05F35B2CA8037BF62DD4228786D07707064DBD0D46569305D0 | |||
| 3980 | WScript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\DCIM.JPG | text | |
MD5:3A62608CEFCBD3A10AFEA8CDF570749B | SHA256:1C44B60B4866B1BC82FB9928D713B010DF42122D156A5CC6C70B2A2B35F38A34 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
7
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3980 | WScript.exe | 41.105.48.176:1995 | kaka00.myq-see.com | Telecom Algeria | DZ | unknown |
3980 | WScript.exe | 41.105.13.160:1995 | memo47.linkpc.net | Telecom Algeria | DZ | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
do47.redirectme.net |
| unknown |
kaka00.myq-see.com |
| unknown |
dns.msftncsi.com |
| shared |
memo47.linkpc.net |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1056 | svchost.exe | Potential Corporate Privacy Violation | ET INFO Observed DNS Query to .myq-see .com DDNS Domain |
1 ETPRO signatures available at the full report