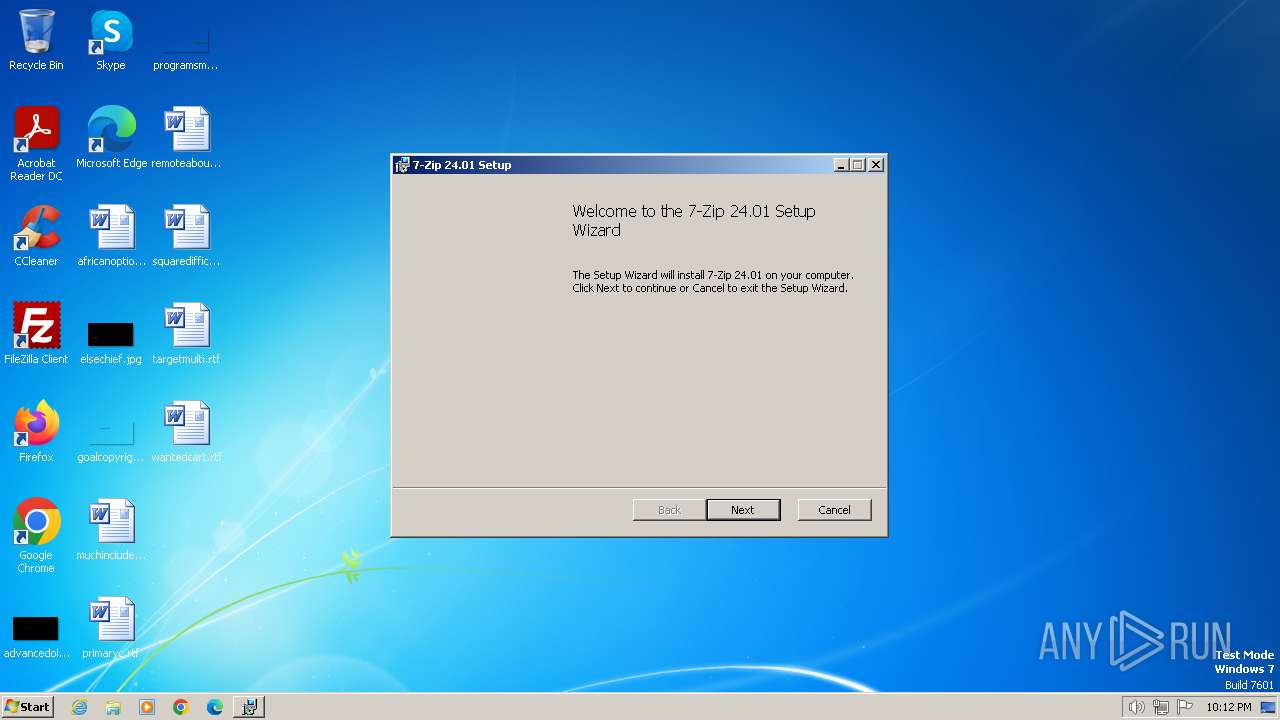
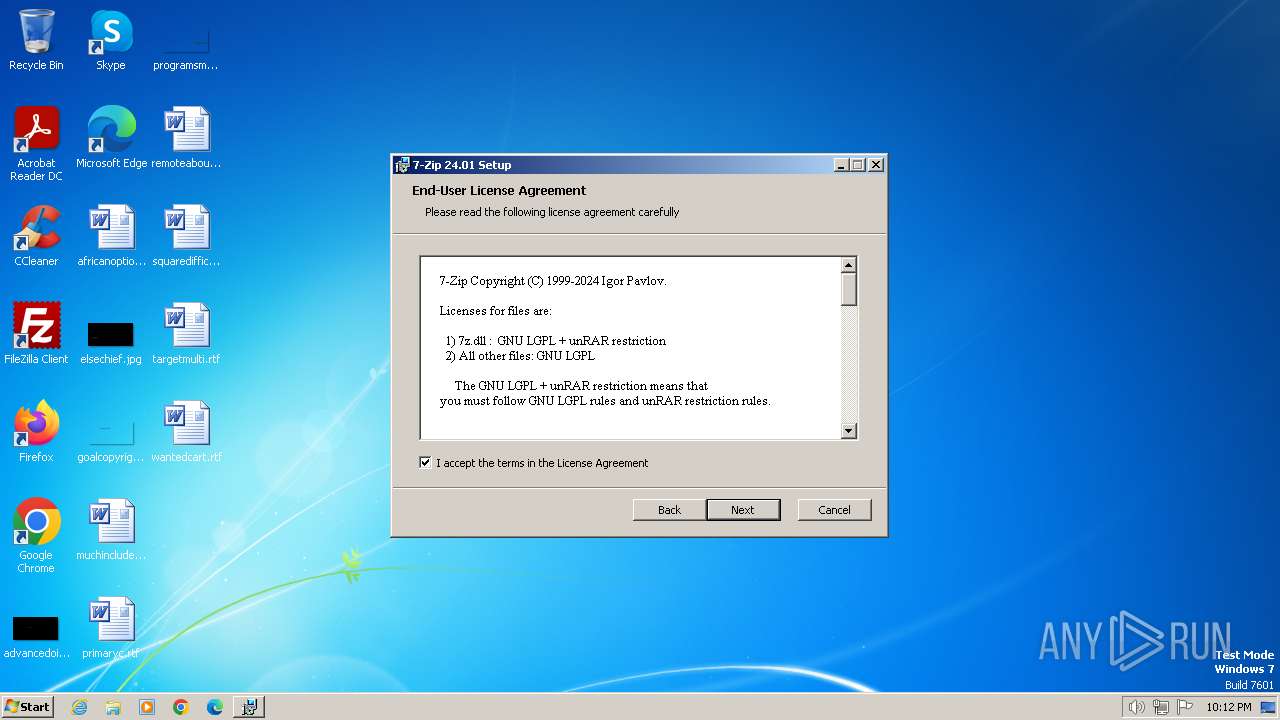
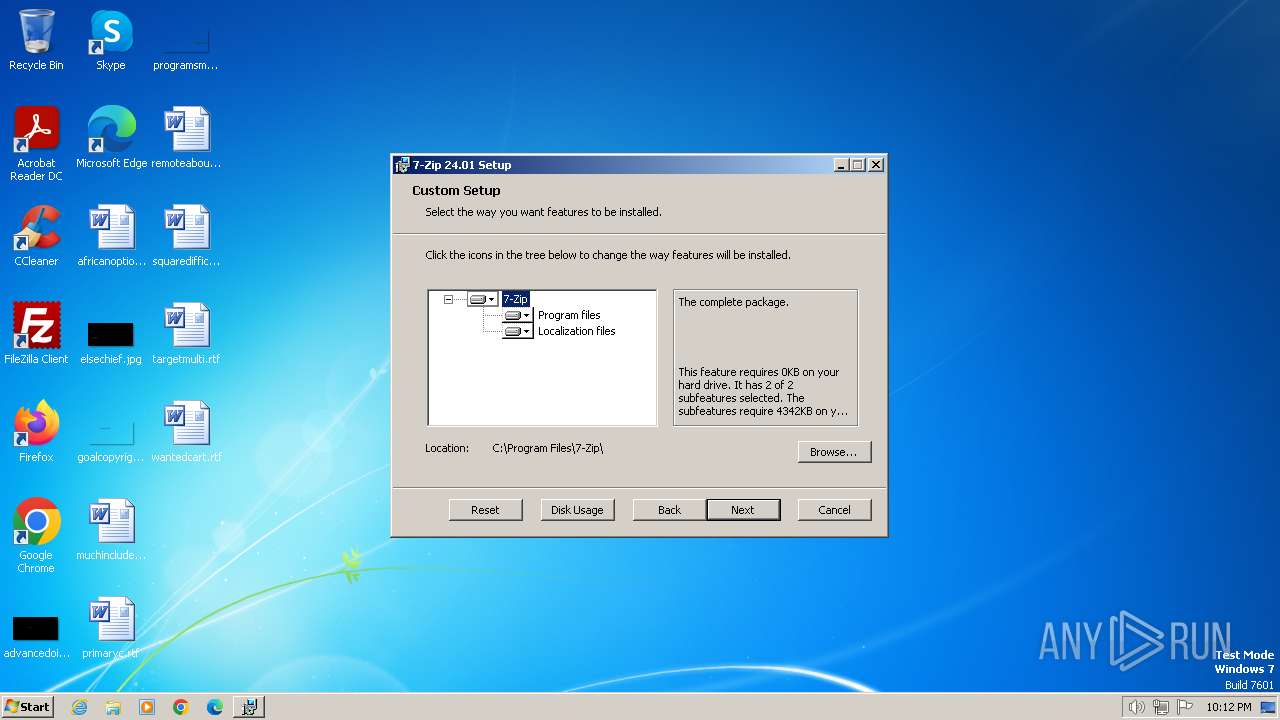
| File name: | 7z2401.msi |
| Full analysis: | https://app.any.run/tasks/c083a664-0328-48b0-a628-f39216f49509 |
| Verdict: | Malicious activity |
| Analysis date: | June 24, 2024, 21:12:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: 7-Zip Package, Author: Igor Pavlov, Keywords: Installer, Comments: 7-Zip Package, Template: Intel;1033, Revision Number: {23170F69-40C1-2701-2401-000002000000}, Number of Pages: 200, Number of Words: 2, Security: 2, Create Time/Date: Sun Dec 31 20:42:34 2023, Last Saved Time/Date: Sun Dec 31 20:42:34 2023, Name of Creating Application: Windows Installer XML v2.0.3719.0 (candle/light) |
| MD5: | A141303FE3FD74208C1C8A1121A7F67D |
| SHA1: | B55C286E80A9E128FBF615DA63169162C08AEF94 |
| SHA256: | 1C3C3560906974161F25F5F81DE4620787B55CA76002AC3C4FC846D57A06DF99 |
| SSDEEP: | 49152:iczFhLwrW5+7Z8e3+FjI+fK6mAgq6L/YptQAi9NPWutgdtdprJtKI3zF/dIrJYvh:iczFhyL7Z93+vfBWMI/ptuzpdU+dIFip |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 3520)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 3172)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 3520)
Drops 7-zip archiver for unpacking
- msiexec.exe (PID: 3520)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 3520)
INFO
Checks supported languages
- msiexec.exe (PID: 3520)
Reads the machine GUID from the registry
- msiexec.exe (PID: 3520)
An automatically generated document
- msiexec.exe (PID: 3392)
Executable content was dropped or overwritten
- msiexec.exe (PID: 3520)
Reads the computer name
- msiexec.exe (PID: 3520)
Create files in a temporary directory
- msiexec.exe (PID: 3520)
Creates a software uninstall entry
- msiexec.exe (PID: 3520)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (88.6) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (10) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | 7-Zip Package |
| Author: | Igor Pavlov |
| Keywords: | Installer |
| Comments: | 7-Zip Package |
| Template: | Intel;1033 |
| RevisionNumber: | {23170F69-40C1-2701-2401-000002000000} |
| Pages: | 200 |
| Words: | 2 |
| Security: | Read-only recommended |
| CreateDate: | 2024:01:31 20:42:34 |
| ModifyDate: | 2024:01:31 20:42:34 |
| Software: | Windows Installer XML v2.0.3719.0 (candle/light) |
Total processes
42
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3172 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3392 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\7z2401.msi | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3520 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 271
Read events
5 009
Write events
250
Delete events
12
Modification events
| (PID) Process: | (3520) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 400000000000000098E0B2387BC6DA01C00D0000C8080000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3520) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000F242B5387BC6DA01C00D0000C8080000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3520) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 75 | |||
| (PID) Process: | (3520) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 40000000000000007A887D397BC6DA01C00D0000C8080000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3520) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000D4EA7F397BC6DA01C00D0000800B0000E80300000100000000000000000000000C88629208561A4B8CE27D2E581B67540000000000000000 | |||
| (PID) Process: | (3172) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000E21187397BC6DA01640C00002C090000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3172) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000E21187397BC6DA01640C0000980C0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3172) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000E21187397BC6DA01640C0000940C0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3172) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000E21187397BC6DA01640C0000340C0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3172) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 400000000000000096D68B397BC6DA01640C0000940C0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
9
Suspicious files
12
Text files
97
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3520 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3520 | msiexec.exe | C:\Program Files\7-Zip\7zG.exe | executable | |
MD5:D27857576DC7DDAF396517C64C0C9A92 | SHA256:5EC621037E383D513CD6CEE687E0FFA95E6725B25B3C561084D674276ACB395E | |||
| 3520 | msiexec.exe | C:\Program Files\7-Zip\7z.sfx | executable | |
MD5:D820D695B7433E4BD8B9A202F8626DC2 | SHA256:E1AF05EFEE86A5E1ED219F6A94FF6C76B10F664FCCB003291016030D0BBD0B13 | |||
| 3520 | msiexec.exe | C:\Program Files\7-Zip\7z.dll | executable | |
MD5:FCFF1973DB63CD9B11EF75478F921C1E | SHA256:B5A3B1CE2F876F9D15A6312CCBC2A7C3612F30799AAB2CDA209A7D2AF02634FB | |||
| 3520 | msiexec.exe | C:\Program Files\7-Zip\History.txt | text | |
MD5:5C549BB1F209566C292CC782700C3E9F | SHA256:E7CB88319991D7CD7475A1609952C5A540010EBB492B18BE259D586E6BDE3633 | |||
| 3520 | msiexec.exe | C:\Program Files\7-Zip\7zFM.exe | executable | |
MD5:52AE15F525A8732BCB89BA874461B05E | SHA256:1E6162AD80DC358BD58013500C18CE568EC97734EEBB94ACD70CB74BBA5C0C91 | |||
| 3520 | msiexec.exe | C:\Windows\Installer\MSI37F0.tmp | binary | |
MD5:127A9D7A8426172E7F3BAEA7FC635F22 | SHA256:9B3CD514295B635465903312C27CB8744F77588480A893A078C258EC12CFCC72 | |||
| 3520 | msiexec.exe | C:\Program Files\7-Zip\descript.ion | text | |
MD5:EB7E322BDC62614E49DED60E0FB23845 | SHA256:1DA513F5A4E8018B9AE143884EB3EAF72454B606FD51F2401B7CFD9BE4DBBF4F | |||
| 3520 | msiexec.exe | C:\Program Files\7-Zip\7zCon.sfx | executable | |
MD5:1CB7028EC37DDEA1C42CF5DC0E7A8B6B | SHA256:B91F3E162F9873164FEF560469A9729884D8FB0DCE5561642B657A6880A85A5D | |||
| 3520 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:51B61B50E2A3C15C5FAF1C55850E4F3D | SHA256:ACFD6909C88629D32859F15755A5C920CAADF99AACA4BB2C71D450DEEB2CD310 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
10
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 88.221.110.91:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 2.16.164.51:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 2.19.126.137:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8f69642324cc87bd | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1372 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1372 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1372 | svchost.exe | 88.221.110.91:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 2.16.164.51:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
1372 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
1060 | svchost.exe | 2.19.126.137:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
dns.msftncsi.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |