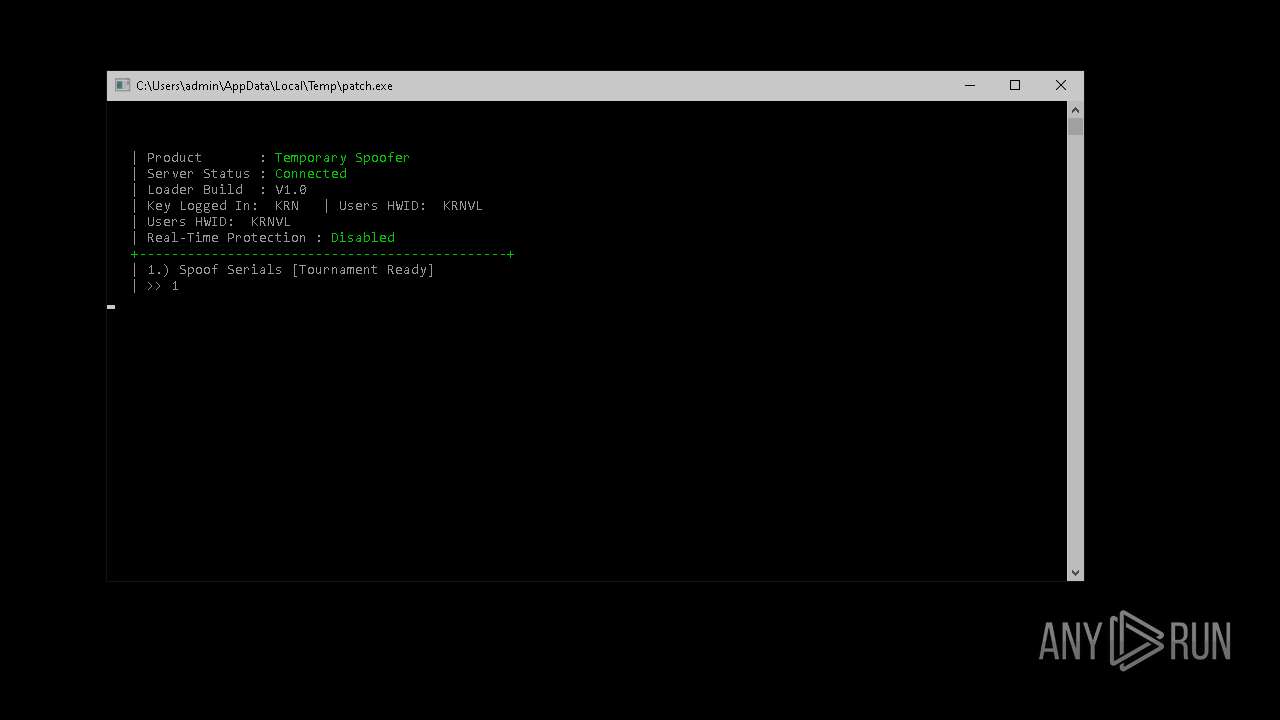
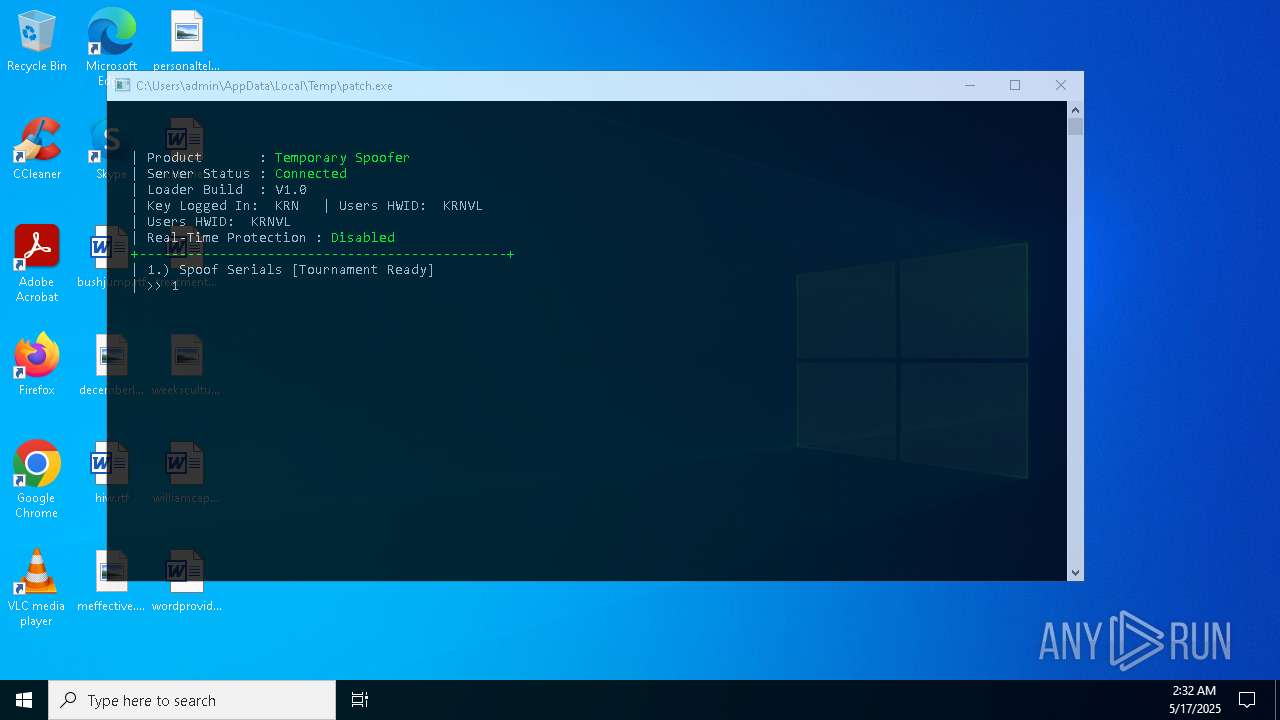
| File name: | patch.exe |
| Full analysis: | https://app.any.run/tasks/e0635a02-121f-488a-80f0-5cd4736d489c |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2025, 02:32:29 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 6 sections |
| MD5: | 7A5DD15FE60BFC39283C1711D0325935 |
| SHA1: | 86B9CF34A56E74F7A8DA8E420D5C753BD45A9B37 |
| SHA256: | 1C26F39A584C255156ABE4B4913F353367473446413B4E33BBC9DAB4ACE39B22 |
| SSDEEP: | 49152:tnJEsQPvftbboucJLmSO/mblzi8AjmZdpIG:tnJEsgftIuyLmCk |
MALICIOUS
Starts NET.EXE for service management
- cmd.exe (PID: 7920)
- net.exe (PID: 2568)
- cmd.exe (PID: 1300)
- net.exe (PID: 7948)
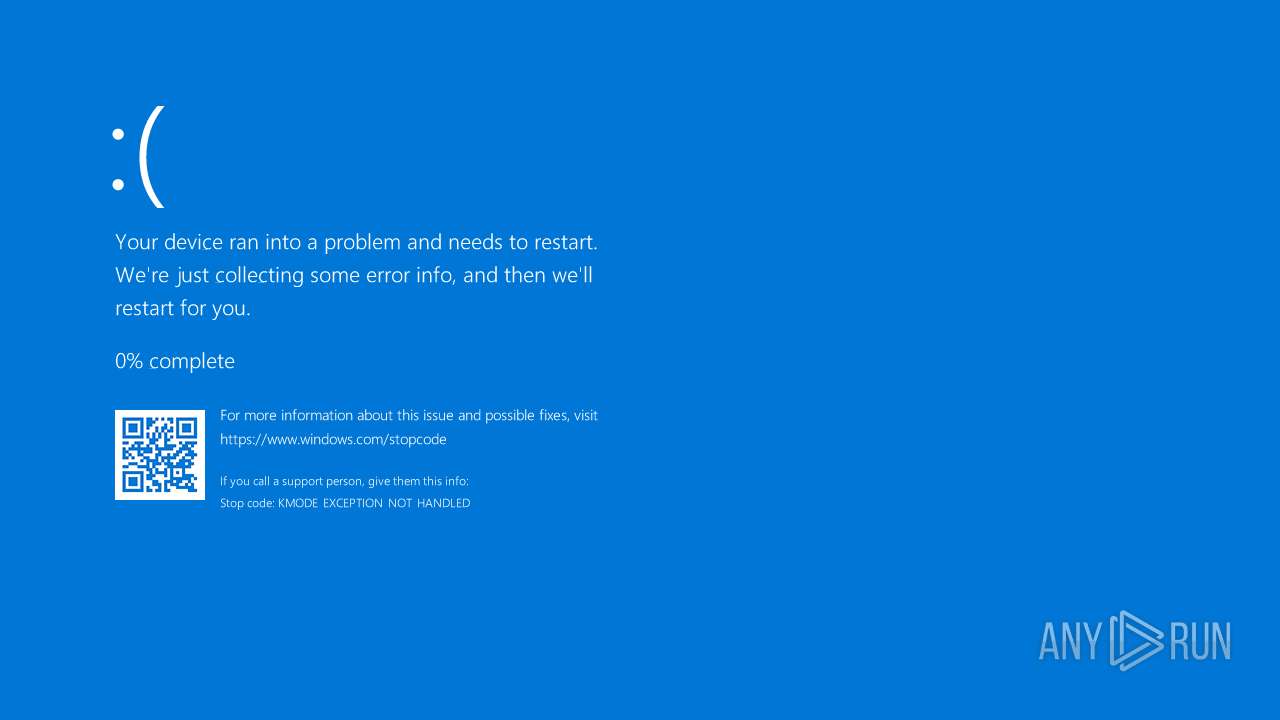
Vulnerable driver has been detected
- vmN8CTSWBk24.exe (PID: 4228)
SUSPICIOUS
Starts SC.EXE for service management
- cmd.exe (PID: 7760)
Hides command output
- cmd.exe (PID: 7920)
- cmd.exe (PID: 1300)
- vmN8CTSWBk24.exe (PID: 4228)
Reads security settings of Internet Explorer
- StartMenuExperienceHost.exe (PID: 4696)
- vmN8CTSWBk24.exe (PID: 4228)
Drops a system driver (possible attempt to evade defenses)
- patch.exe (PID: 7300)
Creates or modifies Windows services
- vmN8CTSWBk24.exe (PID: 4228)
Executable content was dropped or overwritten
- patch.exe (PID: 7300)
- vmN8CTSWBk24.exe (PID: 4228)
Starts CMD.EXE for commands execution
- patch.exe (PID: 7300)
Windows service management via SC.EXE
- sc.exe (PID: 7776)
Reads the date of Windows installation
- StartMenuExperienceHost.exe (PID: 4696)
INFO
Create files in a temporary directory
- patch.exe (PID: 7300)
- vmN8CTSWBk24.exe (PID: 4228)
Checks supported languages
- patch.exe (PID: 7300)
- TextInputHost.exe (PID: 4488)
- SearchApp.exe (PID: 5124)
- StartMenuExperienceHost.exe (PID: 4696)
- vmN8CTSWBk24.exe (PID: 4228)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 5124)
- vmN8CTSWBk24.exe (PID: 4228)
Reads the computer name
- TextInputHost.exe (PID: 4488)
- StartMenuExperienceHost.exe (PID: 4696)
- SearchApp.exe (PID: 5124)
- vmN8CTSWBk24.exe (PID: 4228)
Checks proxy server information
- SearchApp.exe (PID: 5124)
- vmN8CTSWBk24.exe (PID: 4228)
Process checks computer location settings
- StartMenuExperienceHost.exe (PID: 4696)
- SearchApp.exe (PID: 5124)
Reads Environment values
- SearchApp.exe (PID: 5124)
Reads the software policy settings
- SearchApp.exe (PID: 5124)
- vmN8CTSWBk24.exe (PID: 4228)
Creates files or folders in the user directory
- vmN8CTSWBk24.exe (PID: 4228)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:03:30 20:58:56+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 740352 |
| InitializedDataSize: | 456192 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb2500 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
158
Monitored processes
21
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | C:\WINDOWS\system32\net1 start winmgmt /y | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1300 | C:\WINDOWS\system32\cmd.exe /c net start winmgmt /y > nul 2>&1 | C:\Windows\System32\cmd.exe | — | patch.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2140 | "C:\Users\admin\AppData\Local\Temp\patch.exe" | C:\Users\admin\AppData\Local\Temp\patch.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2568 | net start winmgmt /y | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4228 | "C:\Users\admin\AppData\Local\Temp\kHnsbDhO\vmN8CTSWBk24.exe" "C:\Users\admin\AppData\Local\Temp\kHnsbDhO\Qx98vFX4YPLp.sys" > nul 2>&1 | C:\Users\admin\AppData\Local\Temp\kHnsbDhO\vmN8CTSWBk24.exe | patch.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 4488 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 4624 | C:\WINDOWS\System32\mobsync.exe -Embedding | C:\Windows\System32\mobsync.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Sync Center Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4696 | "C:\WINDOWS\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe" -ServerName:App.AppXywbrabmsek0gm3tkwpr5kwzbs55tkqay.mca | C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5124 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 563
Read events
13 477
Write events
85
Delete events
1
Modification events
| (PID) Process: | (4696) StartMenuExperienceHost.exe | Key: | \REGISTRY\A\{2ea09473-cc5d-b935-99ba-fb05aaae0176}\LocalState\DataCorruptionRecovery |
| Operation: | write | Name: | InitializationAttemptCount |
Value: 01000000F9936501D4C6DB01 | |||
| (PID) Process: | (4696) StartMenuExperienceHost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\TileDataModel\Migration\StartNonLayoutProperties |
| Operation: | write | Name: | Completed |
Value: 1 | |||
| (PID) Process: | (4696) StartMenuExperienceHost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\TileDataModel\Migration\StartNonLayoutProperties_AppUsageData |
| Operation: | write | Name: | Completed |
Value: 1 | |||
| (PID) Process: | (4696) StartMenuExperienceHost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\TileDataModel\Migration\StartNonLayoutProperties_TargetedContentTiles |
| Operation: | write | Name: | Completed |
Value: 1 | |||
| (PID) Process: | (1056) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdHigh |
Value: 31180500 | |||
| (PID) Process: | (1056) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: 24995322 | |||
| (PID) Process: | (4696) StartMenuExperienceHost.exe | Key: | \REGISTRY\A\{2ea09473-cc5d-b935-99ba-fb05aaae0176}\LocalState\DataCorruptionRecovery |
| Operation: | write | Name: | InitializationAttemptCount |
Value: 00000000D49C9701D4C6DB01 | |||
| (PID) Process: | (5124) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | SafeSearchMode |
Value: 1 | |||
| (PID) Process: | (5124) SearchApp.exe | Key: | \REGISTRY\A\{94eb010a-3fe3-f7b8-5c32-7511509843cb}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_USEREMAIL |
Value: 000037593702D4C6DB01 | |||
| (PID) Process: | (5124) SearchApp.exe | Key: | \REGISTRY\A\{94eb010a-3fe3-f7b8-5c32-7511509843cb}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_ACCOUNTTYPETEXT |
Value: 000037593702D4C6DB01 | |||
Executable files
3
Suspicious files
48
Text files
93
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5124 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\Internet Explorer\DOMStore\ZWUI0EBX\www.bing[1].xml | text | |
MD5:B4DF24E28A75D8CE1ABC7B52FCA881BD | SHA256:8ADABFABD394F0A8240DB9C4FE2D23D3DE932E2603CDE0236CB667BA9BEACDED | |||
| 7300 | patch.exe | C:\Users\admin\AppData\Local\Temp\kHnsbDhO\Qx98vFX4YPLp.sys | executable | |
MD5:2B038BB918BAA968DE2703DF061E3E27 | SHA256:B56620EFBAE4EE48183BD5A3AD2797A32FEAE2E183917E4FAF3D0C06245A1DDD | |||
| 5124 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:D93F7EA35EC5F78D98C5A4EB82BC083A | SHA256:8522AC0CD0A772D82D3BD86119C45B8D6CF3274DE95BD03C66EE0C3005E0A7CC | |||
| 5124 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\NajusmjIqB4kdLn9FmVxeS4xi2o[1].css | text | |
MD5:73D1CEBD8E3B6C7246F422D624EDF803 | SHA256:0674786CF9978A1F9065F57D98E986070C7CBB5177F154F40E8A924C0E0C13F2 | |||
| 5124 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\tUCiVcVWZ-go7BLlq95YW6bKHZE[1].css | text | |
MD5:445D78544E0CFC11EFC1E172DA3ECBBC | SHA256:76EFEBABB82AE8342985C99A498137C04B3E46BC59D78191F0DA44C660B980F5 | |||
| 5124 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\TokenBroker\Cache\fbaf94e759052658216786bfbabcdced1b67a5c2.tbres | binary | |
MD5:5A136C724D63916BBC933C70A4458C4C | SHA256:36C4FD47FB71856229D9F55976EB556CC08B02B12DCA61B11B209C88D9407AA2 | |||
| 7300 | patch.exe | C:\Users\admin\AppData\Local\Temp\license.txt | text | |
MD5:5A1E3A5AEDE16D438C38862CAC1A78DB | SHA256:35A99A53FF1B46F86A14A375742DFD7FEFFF96A8A2E9C4BCF0FE3546C36C9520 | |||
| 5124 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:A256CD162E80BB743677FB464DAD2625 | SHA256:472B36EEC24D8CBA3F80FFCAEC5728F4833A37D73132E01497E2999229CD48CE | |||
| 4228 | vmN8CTSWBk24.exe | C:\Users\admin\AppData\Local\Temp\zEHKyPnxHDloSbUKbW | executable | |
MD5:2D8E4F38B36C334D0A32A7324832501D | SHA256:01AA278B07B58DC46C84BD0B1B5C8E9EE4E62EA0BF7A695862444AF32E87F1FD | |||
| 1056 | TiWorker.exe | C:\Windows\Logs\CBS\CBS.log | text | |
MD5:C302F540DD1AAADAA8FA9191CC9DB46E | SHA256:3098744C0AD611D0F1C4CF406FAD7EB025621BB1594D1A95732E3A7A3D4D6690 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
30
DNS requests
17
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5124 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4228 | vmN8CTSWBk24.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2772 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2772 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7012 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5124 | SearchApp.exe | 2.19.96.107:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
msdl.microsoft.com |
| whitelisted |
vsblobprodscussu5shard49.blob.core.windows.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Blob Storage (.blob .core .windows .net) |