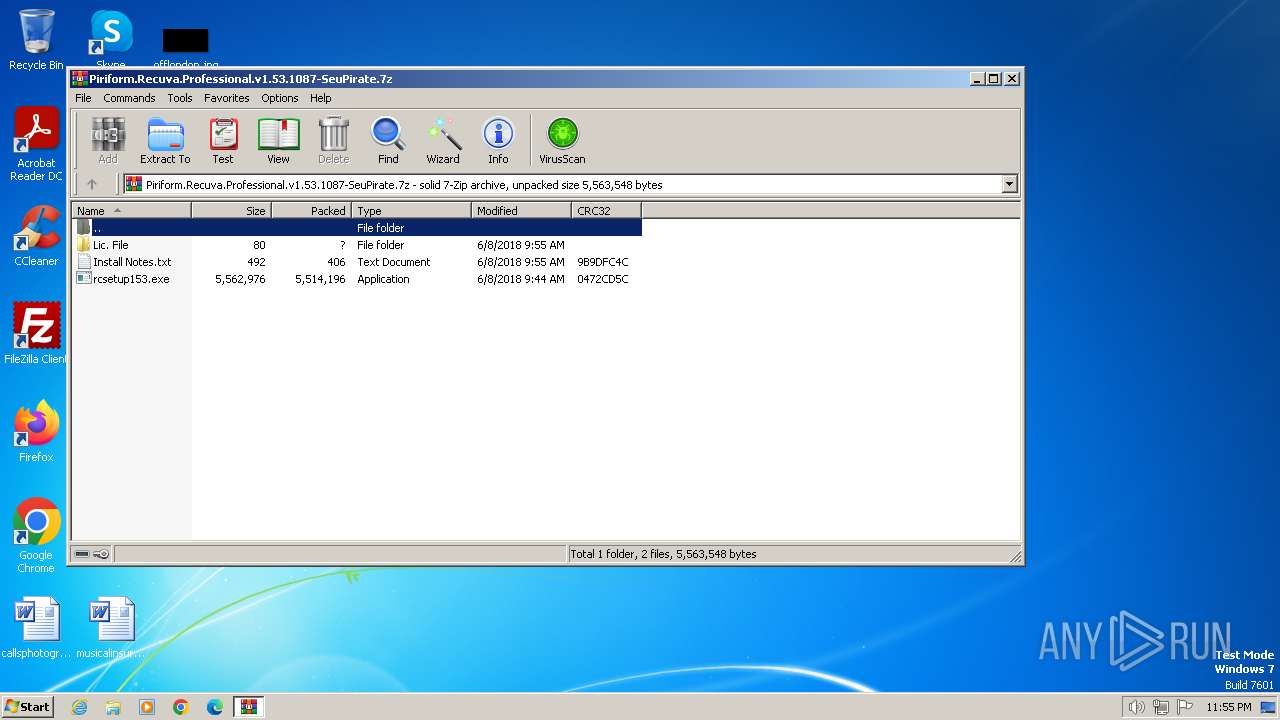
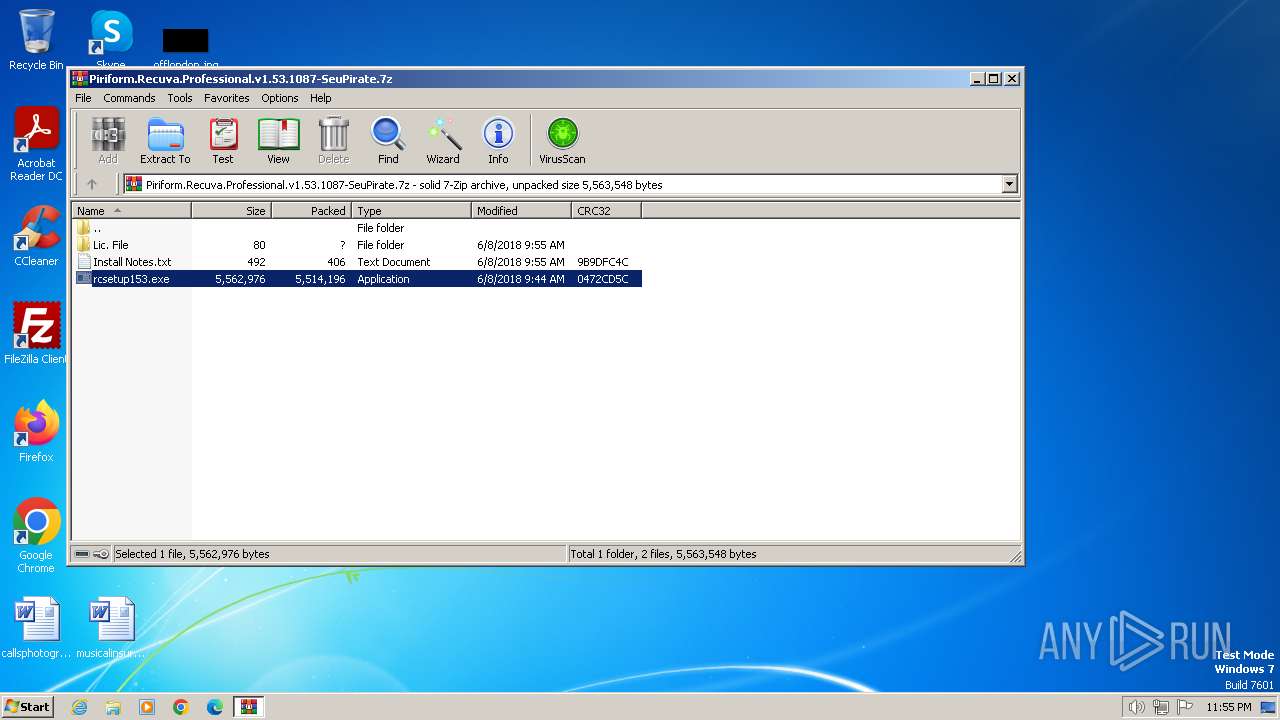
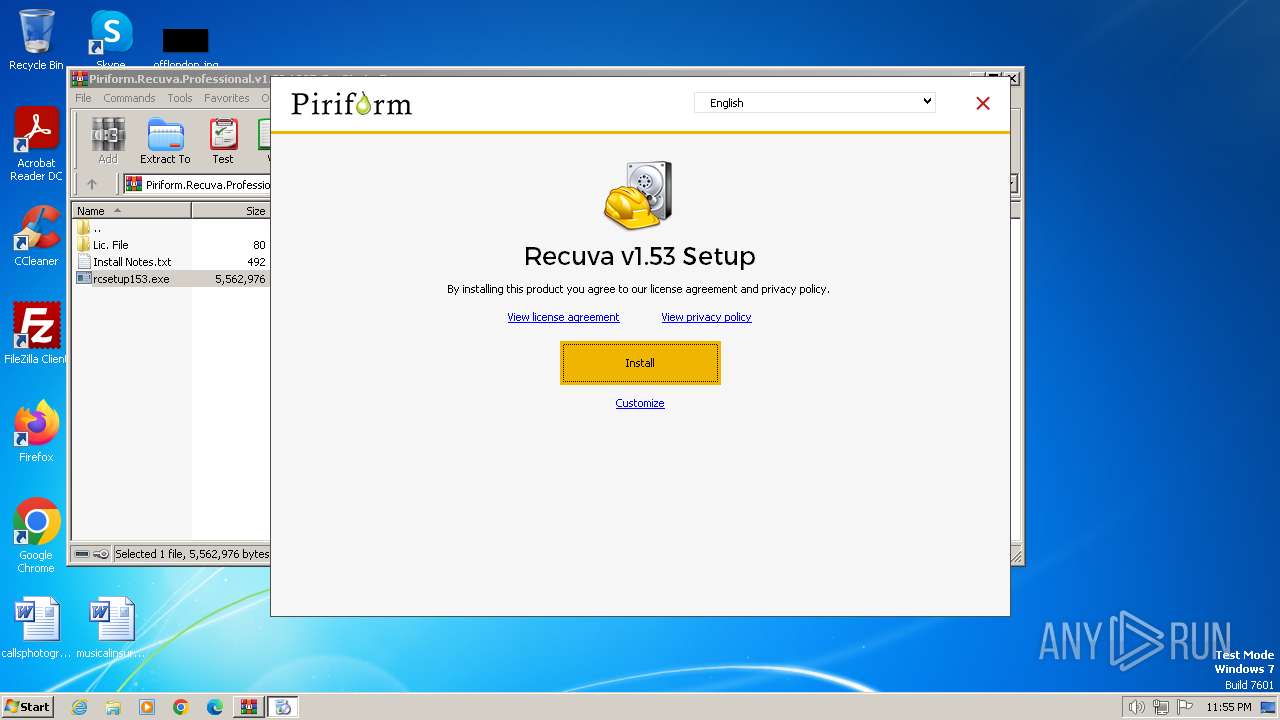
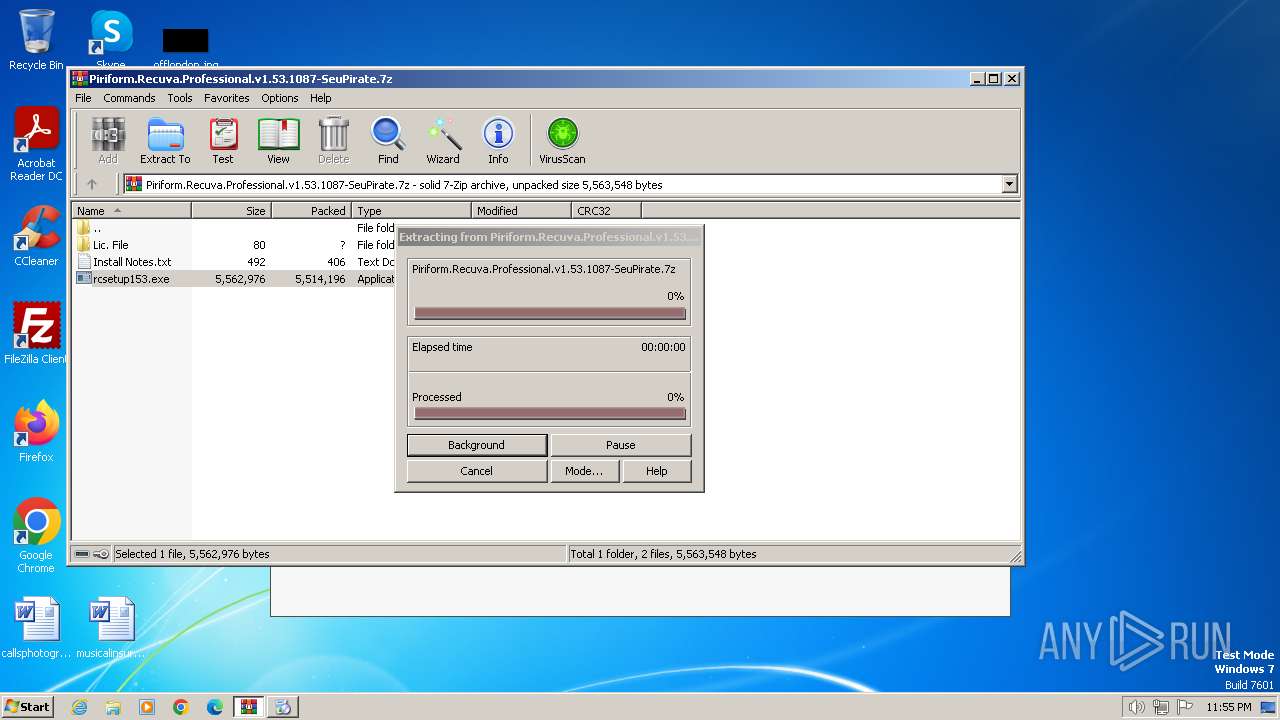
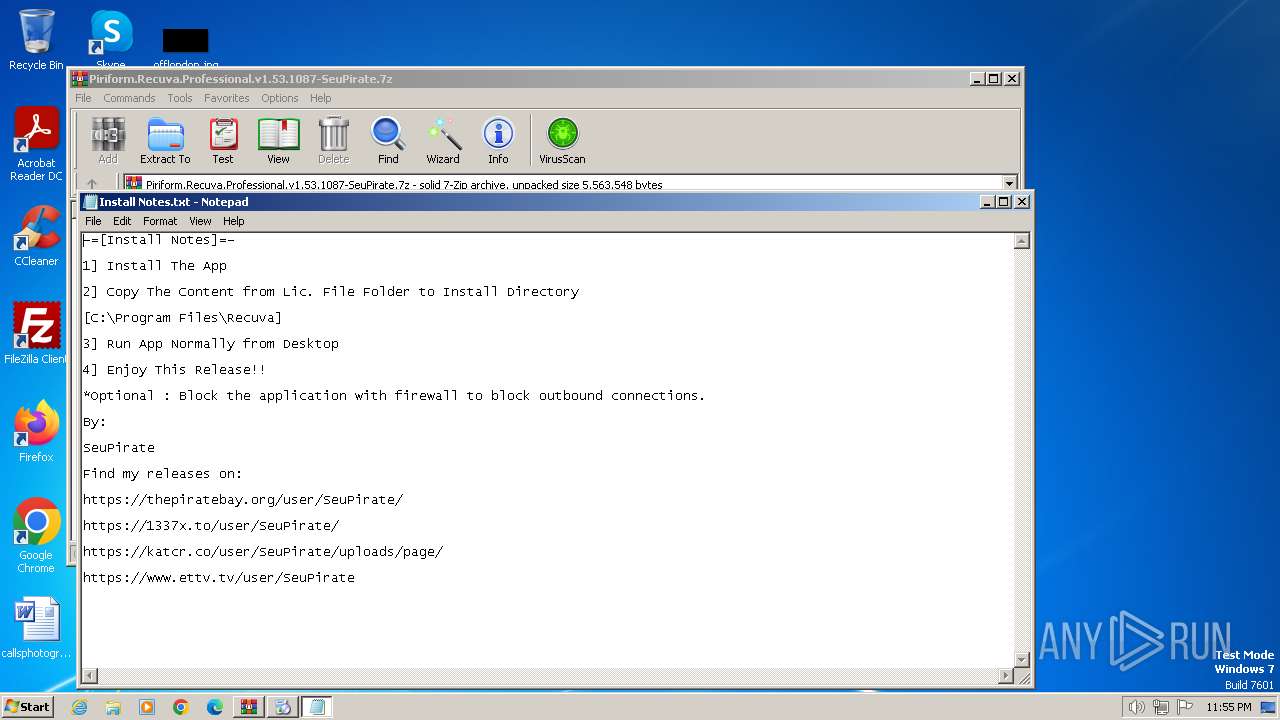
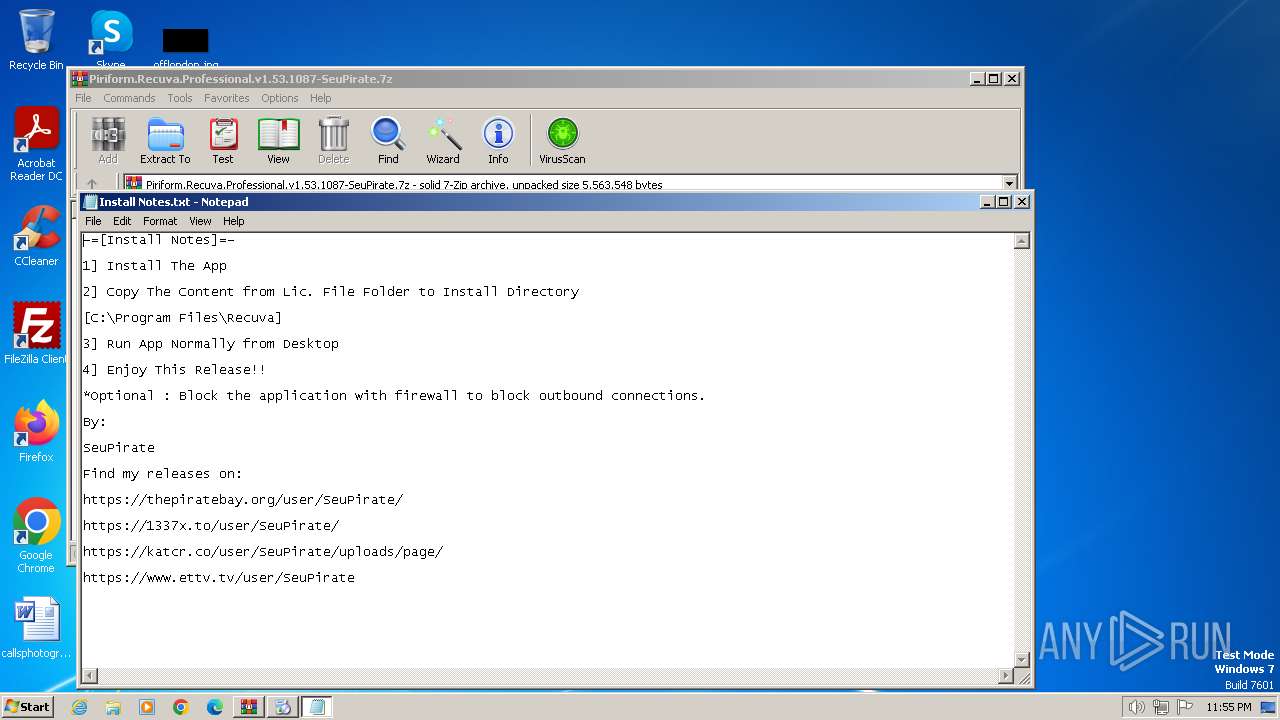
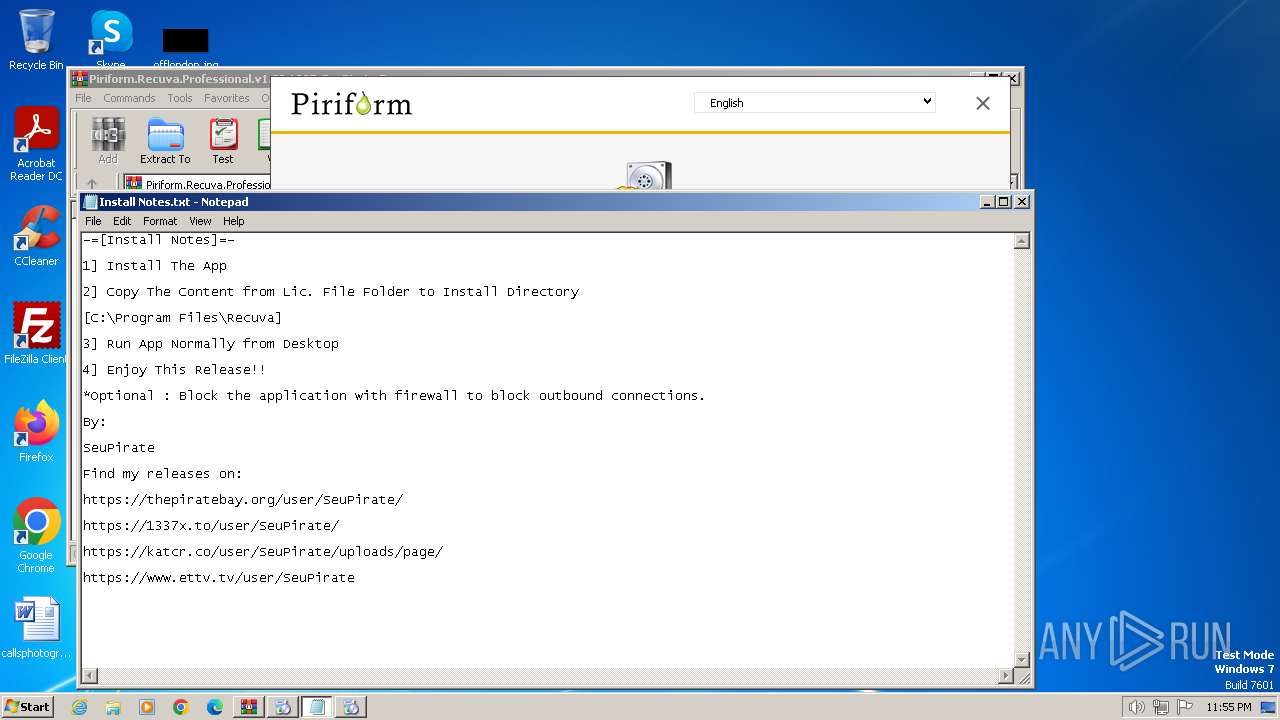
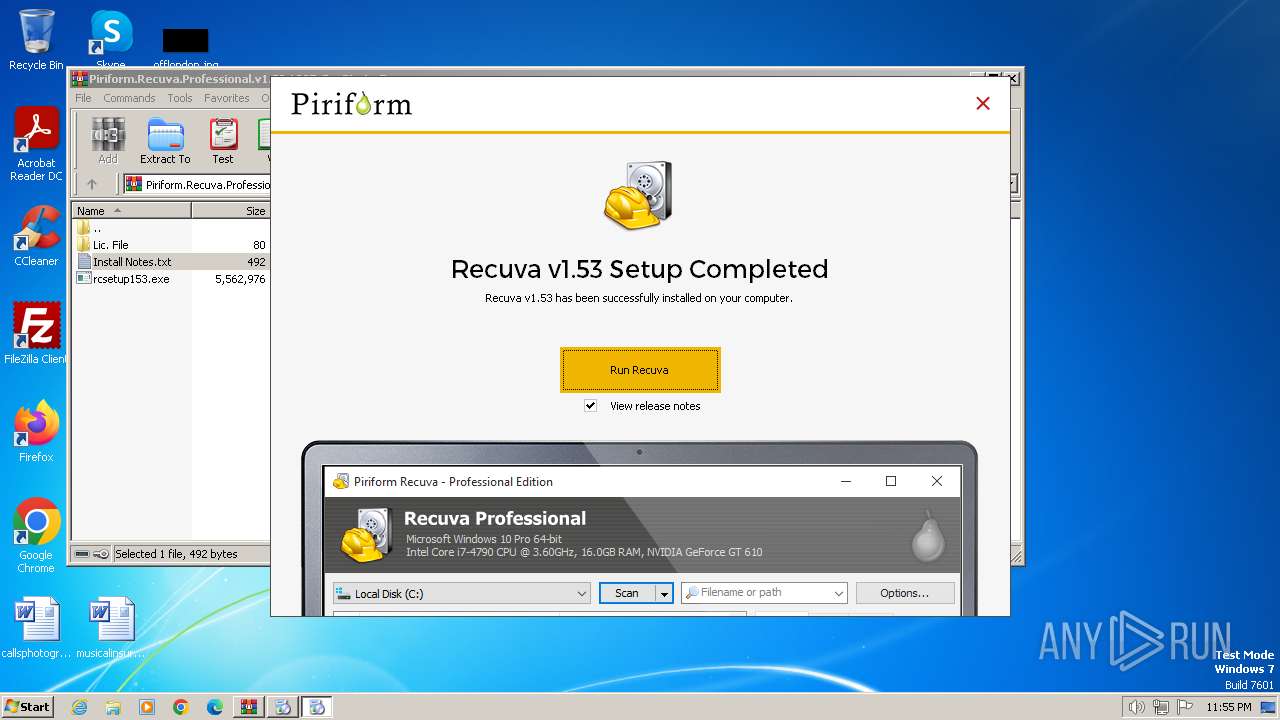
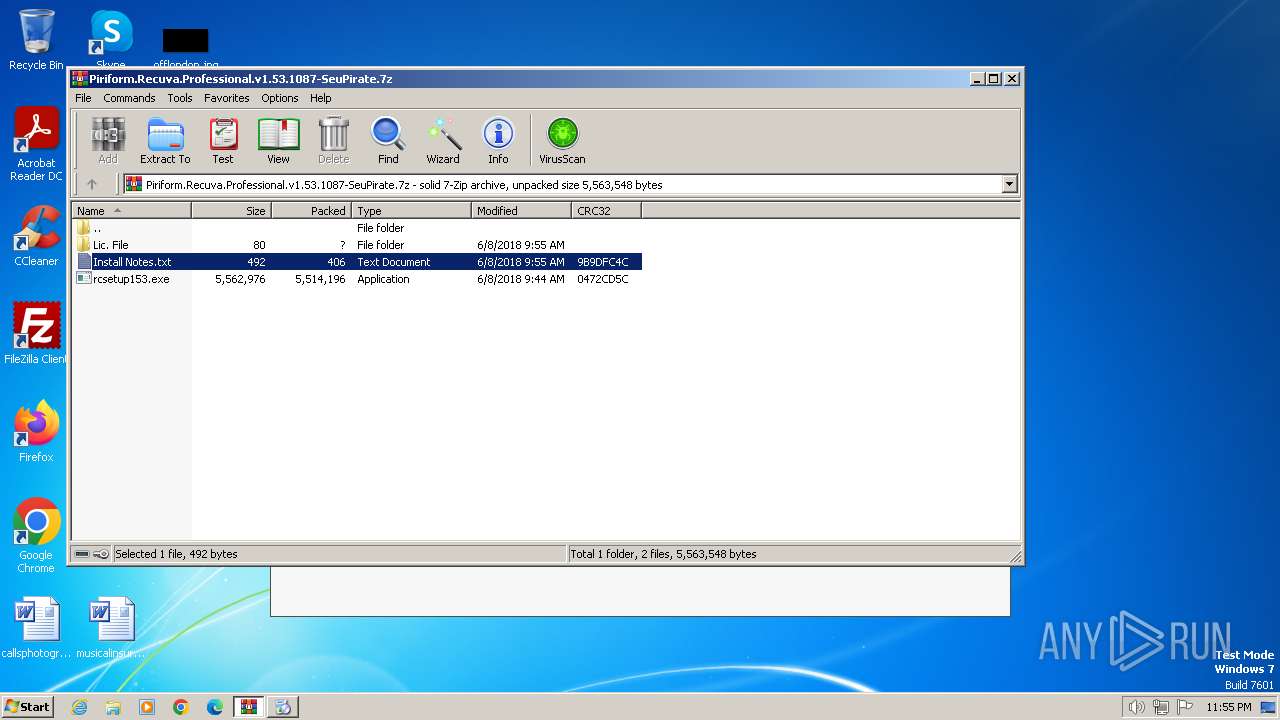
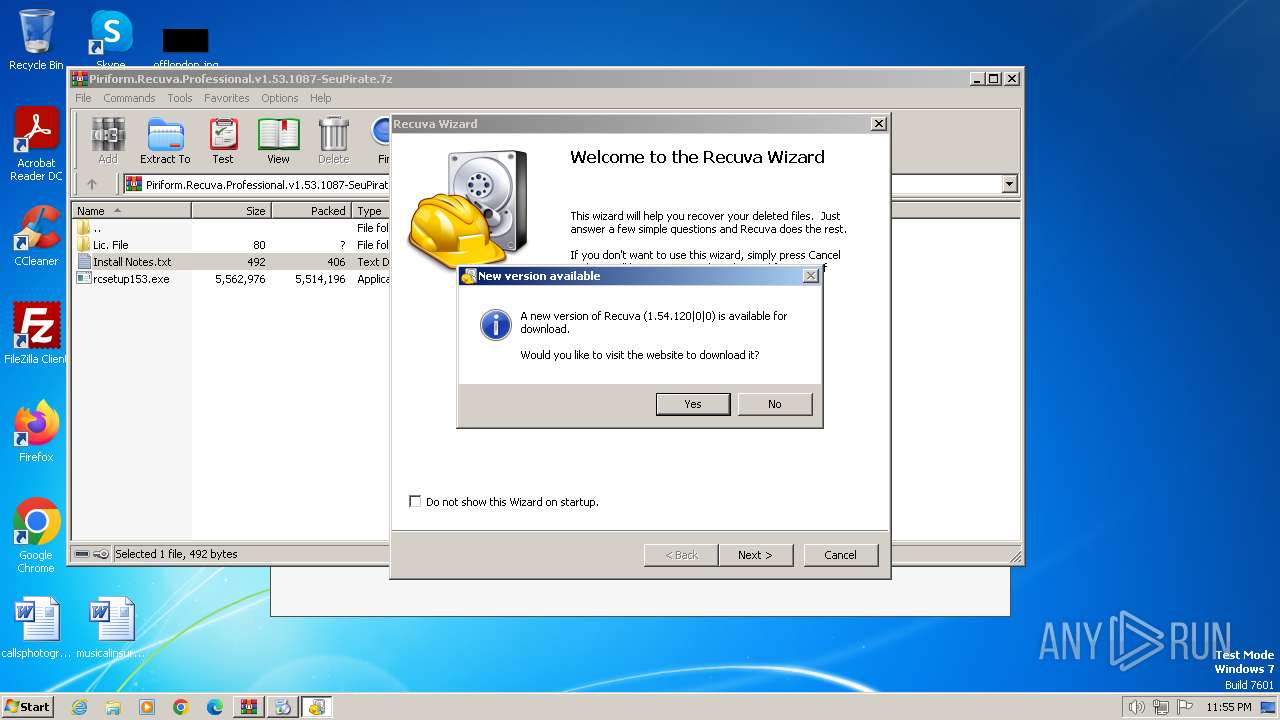
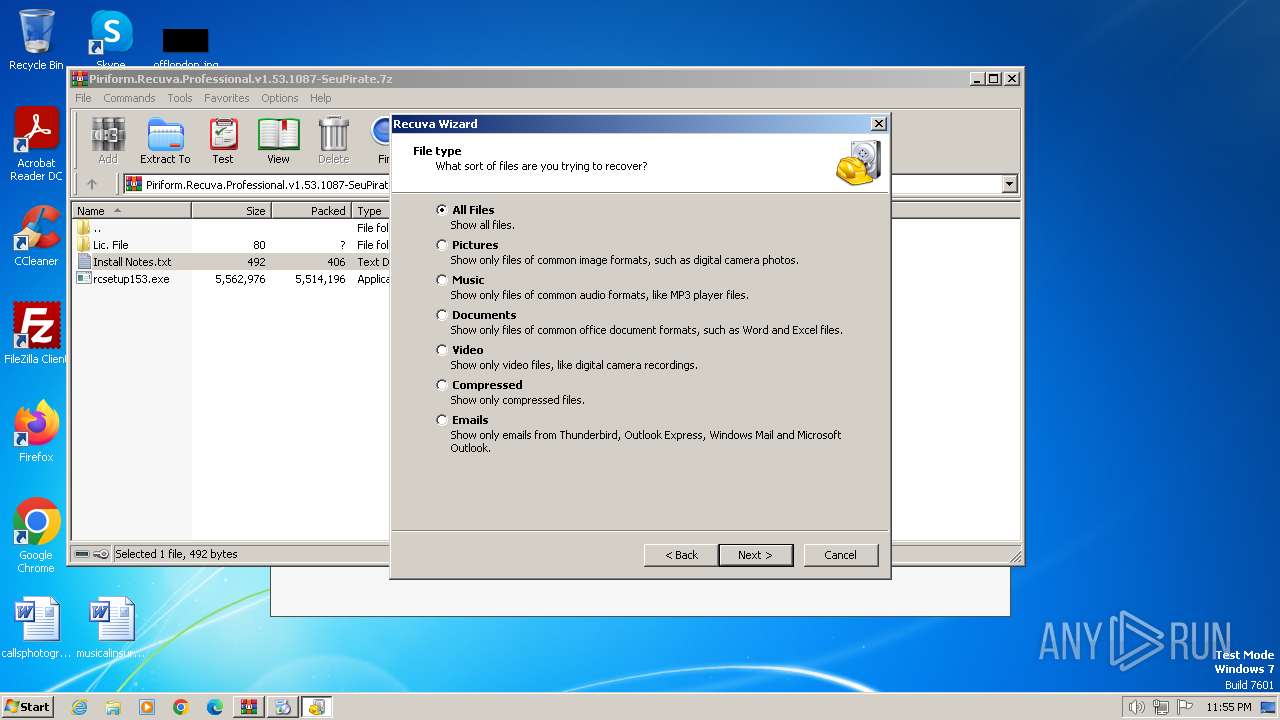
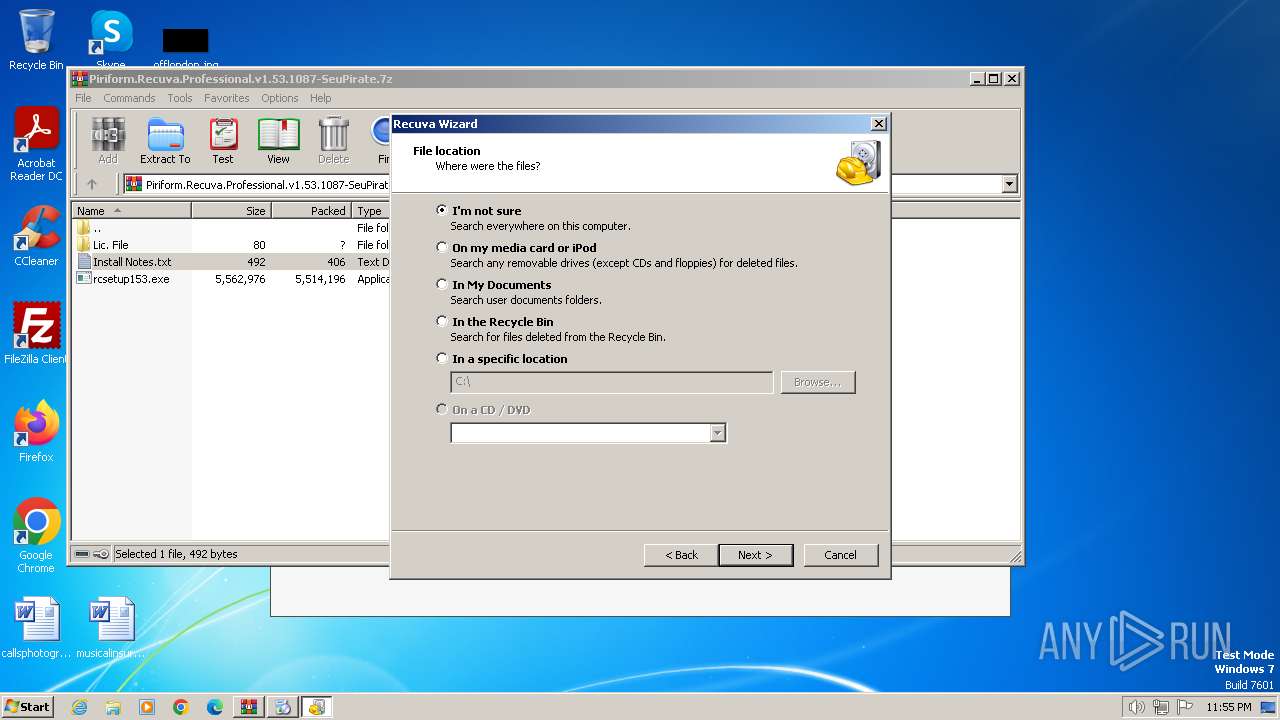
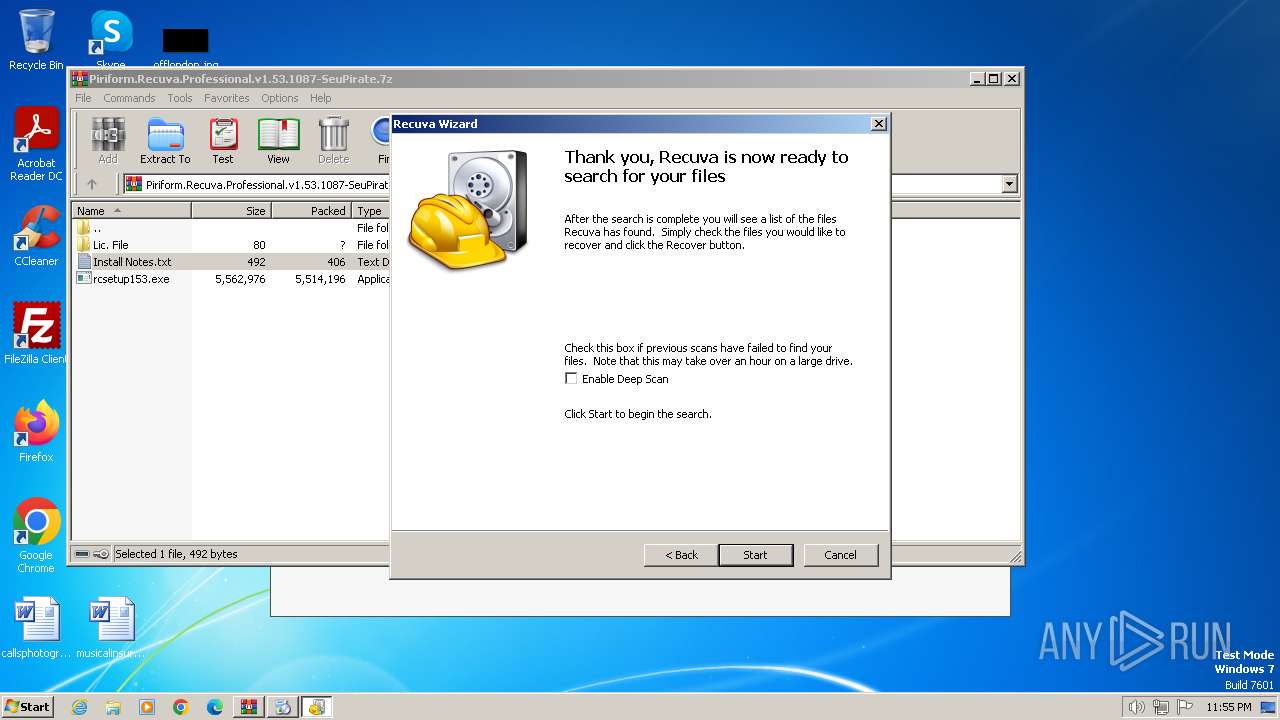
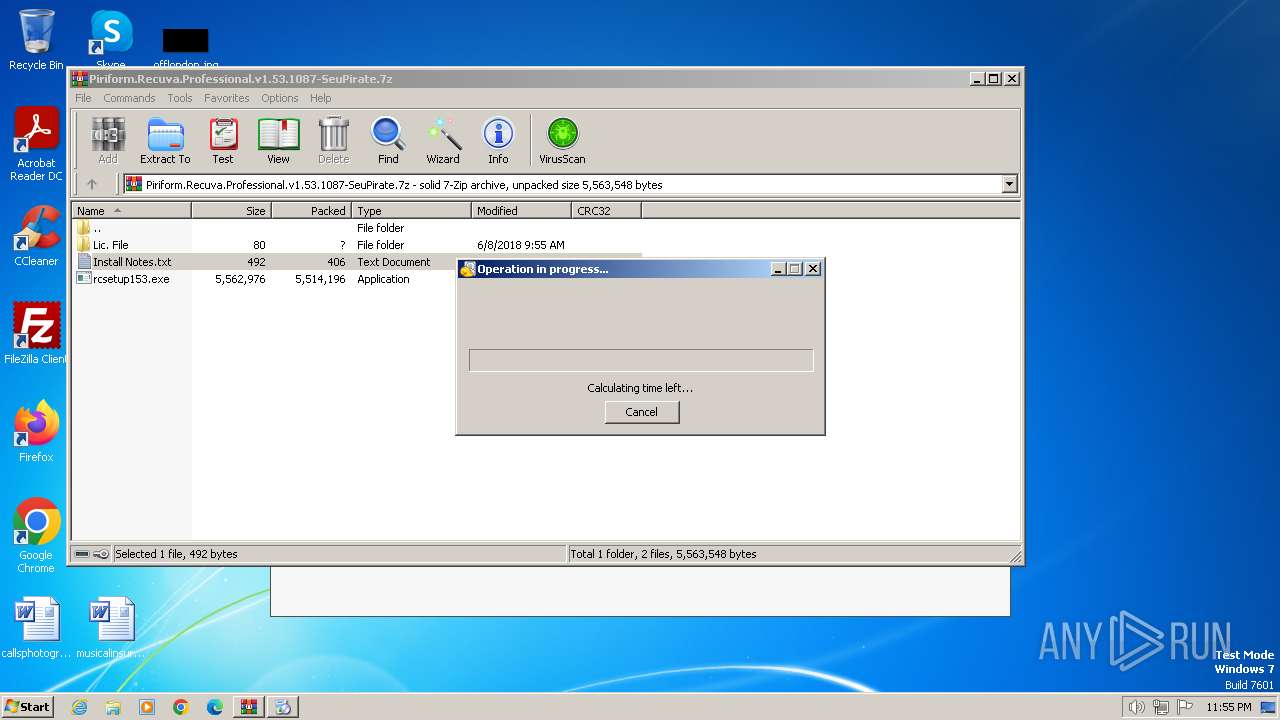
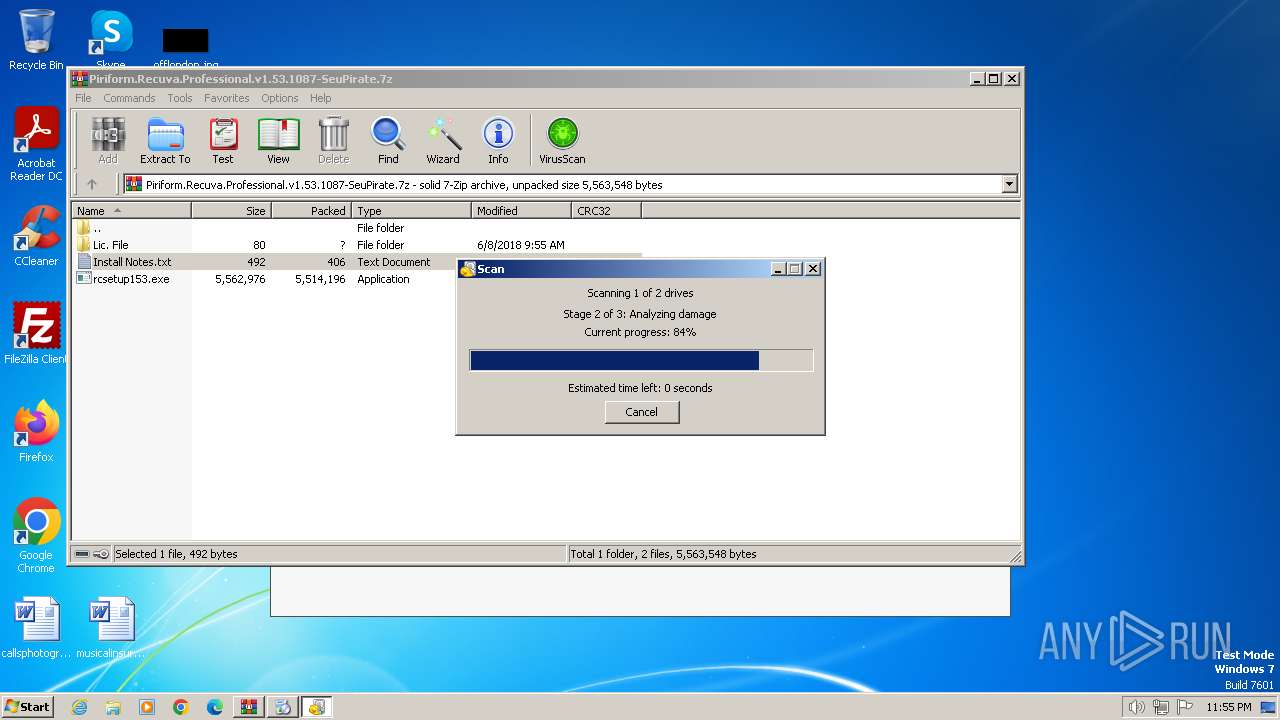
| File name: | Piriform.Recuva.Professional.v1.53.1087-SeuPirate.7z |
| Full analysis: | https://app.any.run/tasks/1f953b75-ba3f-4115-a0ce-d9ce063f5433 |
| Verdict: | Malicious activity |
| Analysis date: | July 02, 2024, 22:54:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 126A1AD85F4FC88799D07A565AEA9330 |
| SHA1: | C2F6B3A1574733E8695C4C648FECAD94A8107584 |
| SHA256: | 1C20B75C72F04F17069AB6474624FFBE9C71DE013EC4DB7D0737A36DA610BEC2 |
| SSDEEP: | 98304:4tvzcjKt0T9xpexAAv/XQo9DBq8NU0BGTVPVll+enfzUdSwrxzTpuH+lkEfRP8P9:/qBLPVBW |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3532)
- rcsetup153.exe (PID: 2348)
- rcsetup153.exe (PID: 932)
Steals credentials from Web Browsers
- rcsetup153.exe (PID: 932)
Registers / Runs the DLL via REGSVR32.EXE
- rcsetup153.exe (PID: 932)
Actions looks like stealing of personal data
- rcsetup153.exe (PID: 932)
SUSPICIOUS
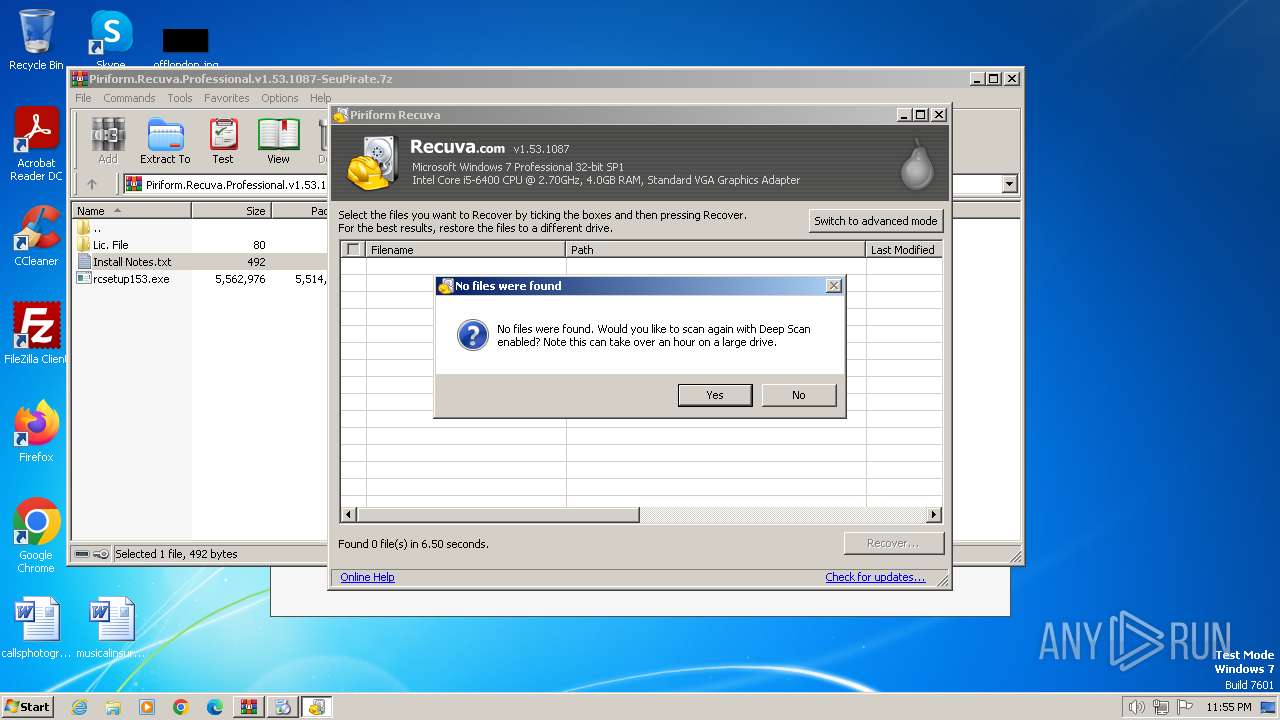
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 3532)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3532)
- rcsetup153.exe (PID: 932)
- recuva.exe (PID: 4044)
The process creates files with name similar to system file names
- rcsetup153.exe (PID: 2348)
- rcsetup153.exe (PID: 932)
Malware-specific behavior (creating "System.dll" in Temp)
- rcsetup153.exe (PID: 2348)
- rcsetup153.exe (PID: 932)
Executable content was dropped or overwritten
- rcsetup153.exe (PID: 2348)
- rcsetup153.exe (PID: 932)
Searches for installed software
- rcsetup153.exe (PID: 932)
- rcsetup153.exe (PID: 2348)
Starts application with an unusual extension
- rcsetup153.exe (PID: 932)
- rcsetup153.exe (PID: 2348)
Reads browser cookies
- rcsetup153.exe (PID: 932)
Reads Internet Explorer settings
- rcsetup153.exe (PID: 932)
- recuva.exe (PID: 4044)
- rcsetup153.exe (PID: 2348)
Reads the Internet Settings
- rcsetup153.exe (PID: 932)
- recuva.exe (PID: 4044)
Checks Windows Trust Settings
- rcsetup153.exe (PID: 932)
- recuva.exe (PID: 4044)
Reads settings of System Certificates
- rcsetup153.exe (PID: 932)
- recuva.exe (PID: 4044)
- rcsetup153.exe (PID: 2348)
Creates a software uninstall entry
- rcsetup153.exe (PID: 932)
Process requests binary or script from the Internet
- rcsetup153.exe (PID: 932)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 1072)
Executes as Windows Service
- VSSVC.exe (PID: 2328)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3532)
Reads the machine GUID from the registry
- rcsetup153.exe (PID: 2348)
- rcsetup153.exe (PID: 932)
- recuva.exe (PID: 4044)
Checks supported languages
- rcsetup153.exe (PID: 2348)
- ns356.tmp (PID: 3124)
- rcsetup153.exe (PID: 932)
- ns1AC6.tmp (PID: 3068)
- ns586C.tmp (PID: 3844)
- recuva.exe (PID: 3312)
- recuva.exe (PID: 4044)
Reads the computer name
- rcsetup153.exe (PID: 2348)
- rcsetup153.exe (PID: 932)
- recuva.exe (PID: 3312)
- recuva.exe (PID: 4044)
Create files in a temporary directory
- rcsetup153.exe (PID: 2348)
- rcsetup153.exe (PID: 932)
Reads Environment values
- rcsetup153.exe (PID: 2348)
- rcsetup153.exe (PID: 932)
Reads product name
- rcsetup153.exe (PID: 932)
- rcsetup153.exe (PID: 2348)
Reads the software policy settings
- rcsetup153.exe (PID: 932)
- recuva.exe (PID: 4044)
- rcsetup153.exe (PID: 2348)
Creates files or folders in the user directory
- rcsetup153.exe (PID: 932)
Creates files in the program directory
- rcsetup153.exe (PID: 932)
- recuva.exe (PID: 4044)
Checks proxy server information
- rcsetup153.exe (PID: 932)
- recuva.exe (PID: 4044)
Reads CPU info
- recuva.exe (PID: 4044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
65
Monitored processes
16
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 932 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3532.22156\rcsetup153.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3532.22156\rcsetup153.exe | WinRAR.exe | ||||||||||||
User: admin Company: Piriform Ltd Integrity Level: HIGH Description: Recuva Installer Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1072 | regsvr32.exe /I "C:\Program Files\Recuva\RecuvaShell.dll" /s | C:\Windows\System32\regsvr32.exe | — | rcsetup153.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 4 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1808 | ping -n 1 -w 5000 www.piriform.com | C:\Windows\System32\PING.EXE | — | ns586C.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2012 | ping -n 1 -w 1000 www.piriform.com | C:\Windows\System32\PING.EXE | — | ns1AC6.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2328 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2348 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3532.21531\rcsetup153.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3532.21531\rcsetup153.exe | WinRAR.exe | ||||||||||||
User: admin Company: Piriform Ltd Integrity Level: HIGH Description: Recuva Installer Version: 1.0.0.0 Modules
| |||||||||||||||
| 2732 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3532.21531\rcsetup153.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3532.21531\rcsetup153.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Piriform Ltd Integrity Level: MEDIUM Description: Recuva Installer Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2864 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3532.22156\rcsetup153.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3532.22156\rcsetup153.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Piriform Ltd Integrity Level: MEDIUM Description: Recuva Installer Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2900 | ping -n 1 -w 1000 www.piriform.com | C:\Windows\System32\PING.EXE | — | ns356.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3068 | "C:\Users\admin\AppData\Local\Temp\nsn171B.tmp\ns1AC6.tmp" ping -n 1 -w 1000 www.piriform.com | C:\Users\admin\AppData\Local\Temp\nsn171B.tmp\ns1AC6.tmp | — | rcsetup153.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
21 683
Read events
21 442
Write events
215
Delete events
26
Modification events
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Piriform.Recuva.Professional.v1.53.1087-SeuPirate.7z | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
161
Suspicious files
8
Text files
11
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2348 | rcsetup153.exe | C:\Users\admin\AppData\Local\Temp\nsjFED1.tmp\UserInfo.dll | executable | |
MD5:C1F778A6D65178D34BDE4206161A98E0 | SHA256:9CAF7A78F750713180CF64D18967A2B803B5580E636E59279DCAAF18BA0DAA87 | |||
| 3532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3532.21531\Lic. File\recuva.dat | binary | |
MD5:5B7084354FB28EC3CF45AF803356EF2D | SHA256:5E86174EC5718A07F5D902E26EF82690E1B42CA63A923F24FAF9988BA3CCFF05 | |||
| 2348 | rcsetup153.exe | C:\Users\admin\AppData\Local\Temp\nsjFED1.tmp\p\pfWWW.dll | executable | |
MD5:CB1D8D51ABC47FCF036A8AAC36C5F4AA | SHA256:903EBBD07A9D551E41BA8CF581069E5E1C70894D2E6473C009B8CED94E8C0D2F | |||
| 3532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3532.21531\Install Notes.txt | text | |
MD5:5BFD02FD05FB43F4E8D036E34913B818 | SHA256:B7CC4DD117CF834D09974257BE54776A4BF9FE9E713BC18C48514738A6BBBD97 | |||
| 2348 | rcsetup153.exe | C:\Users\admin\AppData\Local\Temp\nsjFED1.tmp\nsExec.dll | executable | |
MD5:5ED60250F74FA36A5A247A715BCD026E | SHA256:EA8026766ADC2D7CC26E2206CFDF5F0865B1426BFE3BC2AEC8F43D3FC9A072EF | |||
| 2348 | rcsetup153.exe | C:\Users\admin\AppData\Local\Temp\nsjFED1.tmp\g\gtapi_signed.dll | executable | |
MD5:61BC40D1FAD9E0FAA9A07219B90BA0E4 | SHA256:89E157A4F61D7D18180CB7F901C0095DA3B7A5CC5A9FD58D710099E5F0EE505A | |||
| 2348 | rcsetup153.exe | C:\Users\admin\AppData\Local\Temp\nsjFED1.tmp\ui\pfUI.dll | executable | |
MD5:4406A985E08F66B8921DCE39FD3E7A2D | SHA256:8FBCA8477B43EF3877D3CA6CD7C077FADC46C5C45ADB78725449A194D064AE11 | |||
| 2348 | rcsetup153.exe | C:\Users\admin\AppData\Local\Temp\nsjFED1.tmp\ns356.tmp | executable | |
MD5:5ED60250F74FA36A5A247A715BCD026E | SHA256:EA8026766ADC2D7CC26E2206CFDF5F0865B1426BFE3BC2AEC8F43D3FC9A072EF | |||
| 2348 | rcsetup153.exe | C:\Users\admin\AppData\Local\Temp\nsjFED1.tmp\ui\res\PF_logo.png | image | |
MD5:079CCA30760CCA3C01863B6B96E87848 | SHA256:8DD37D3721E25C32C5BF878B6DBA9E61D04B7CE8AEC45BDF703A41BC41802DFA | |||
| 2348 | rcsetup153.exe | C:\Users\admin\AppData\Local\Temp\nsjFED1.tmp\g\gcapi_dll.dll | executable | |
MD5:2973AF8515EFFD0A3BFC7A43B03B3FCC | SHA256:D0E4581210A22135CE5DEB47D9DF4D636A94B3813E0649AAB84822C9F08AF2A0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
18
DNS requests
10
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
932 | rcsetup153.exe | GET | 302 | 23.45.96.145:80 | http://service.piriform.com/installcheck.aspx?p=2&v=1.53.1087&vx=&l=1033&b=1&o=6.1W3&g=0&i=1&a=0&c=0&d=0&e=0&n=rcsetup153.exe&id=003 | unknown | — | — | unknown |
932 | rcsetup153.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | unknown |
4044 | recuva.exe | GET | 302 | 23.45.96.145:80 | http://www.piriform.com/auto?p=rc&v=1.53.1087&l=1033&a=0 | unknown | — | — | unknown |
4044 | recuva.exe | GET | 301 | 23.206.209.82:80 | http://www.ccleaner.com/auto?p=rc&v=1.53.1087&l=1033&a=0 | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?60bcd71e49d094b3 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2348 | rcsetup153.exe | 23.45.96.145:443 | www.piriform.com | AKAMAI-AS | DE | unknown |
932 | rcsetup153.exe | 23.45.96.145:443 | www.piriform.com | AKAMAI-AS | DE | unknown |
1372 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
1372 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
932 | rcsetup153.exe | 23.45.96.145:80 | www.piriform.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.piriform.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
service.piriform.com |
| whitelisted |
license.piriform.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.ccleaner.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4044 | recuva.exe | Misc activity | ET POLICY Recuva File Recovery Software - Observed User-Agent |
4044 | recuva.exe | Misc activity | ET POLICY Recuva File Recovery Software - Observed User-Agent |