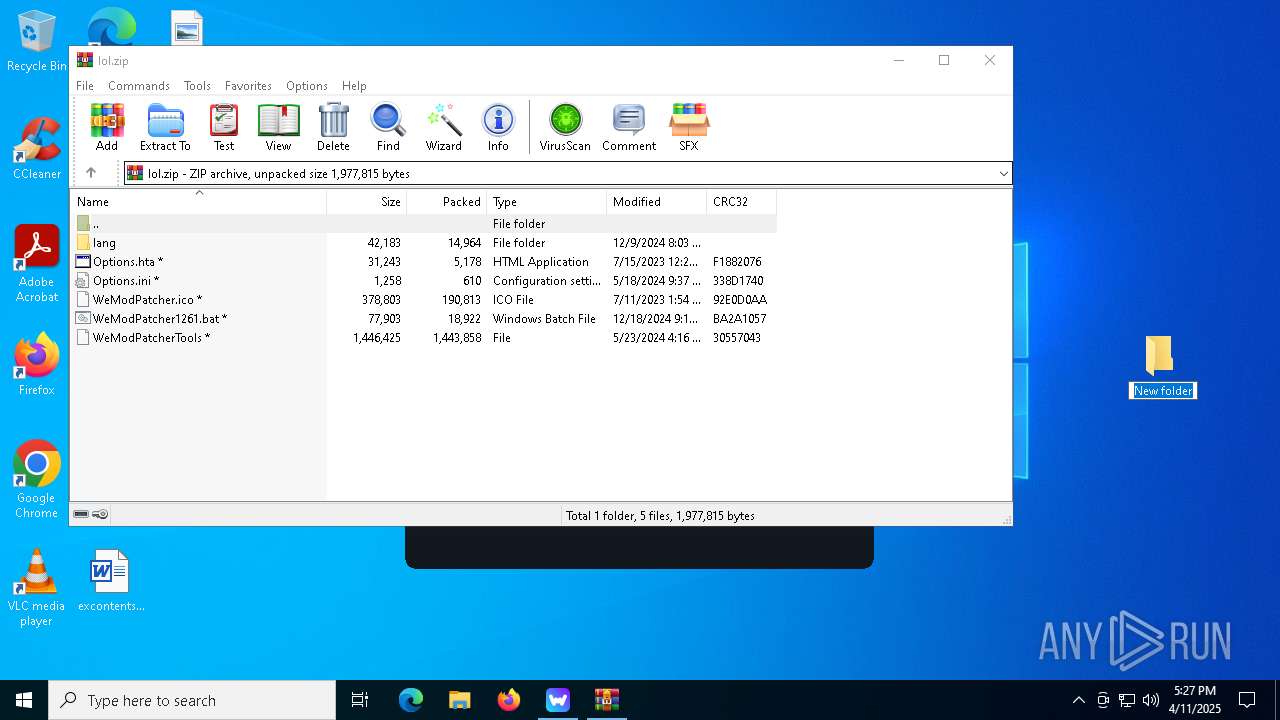
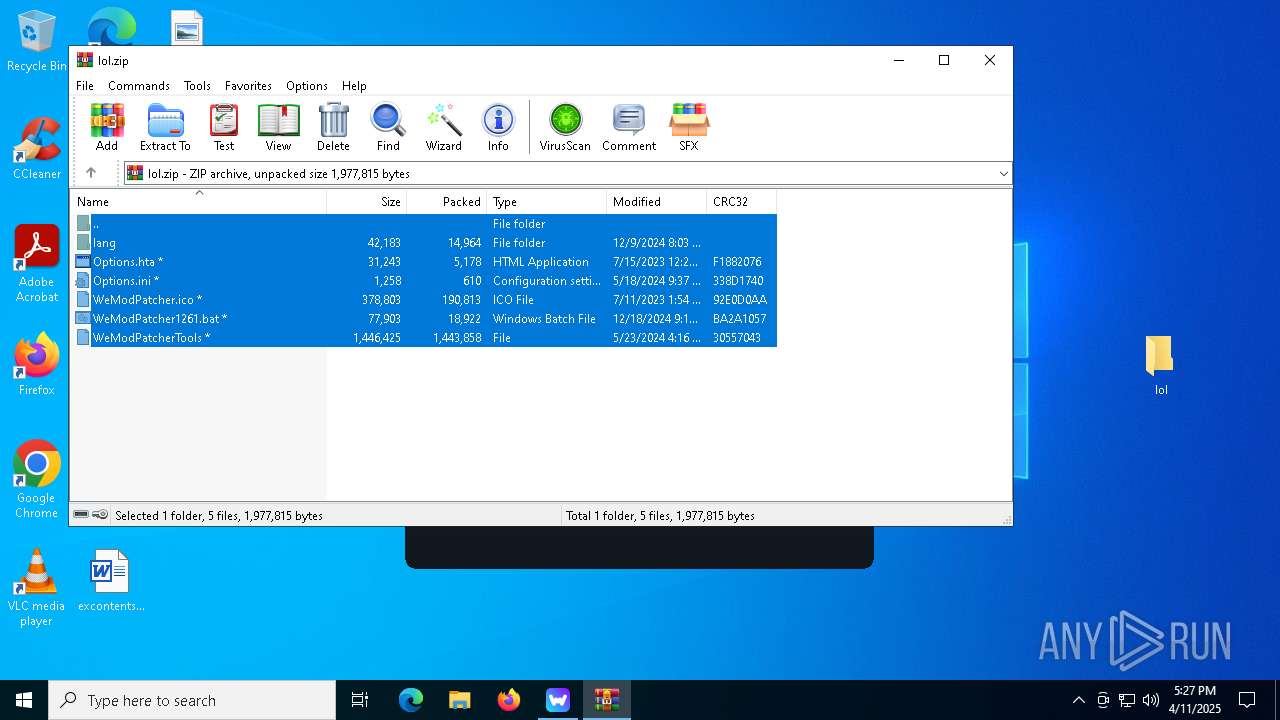
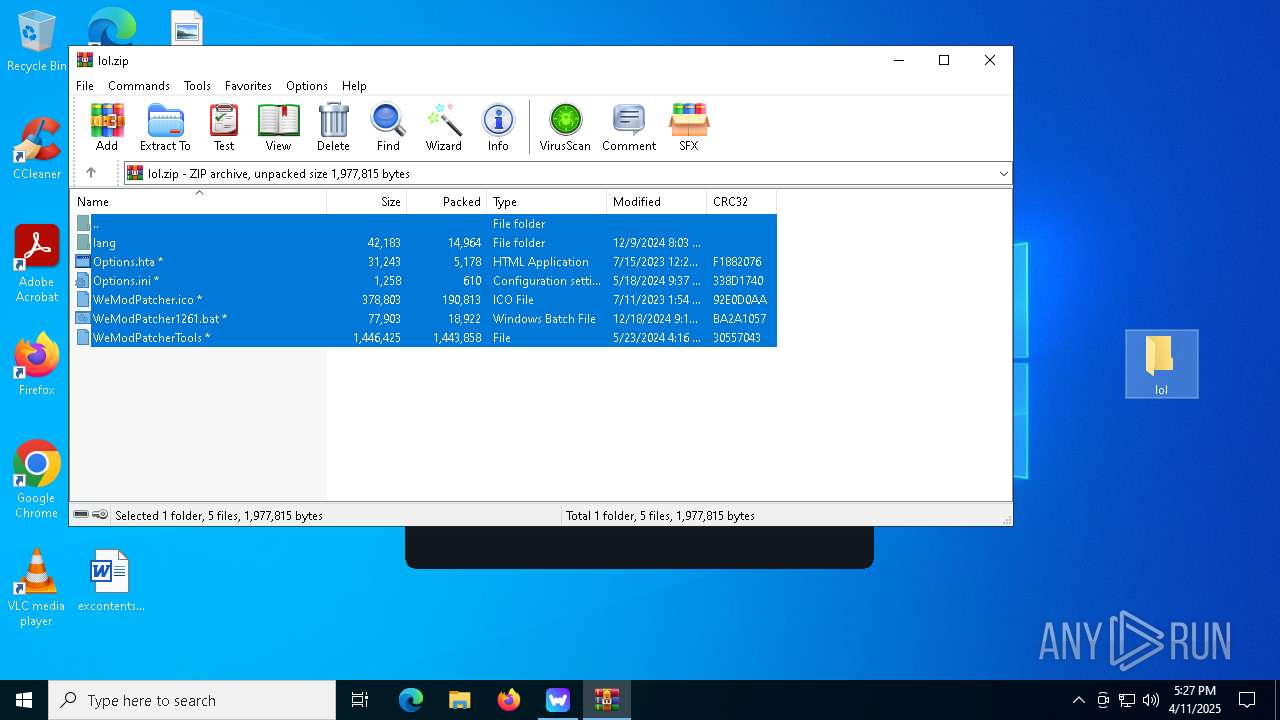
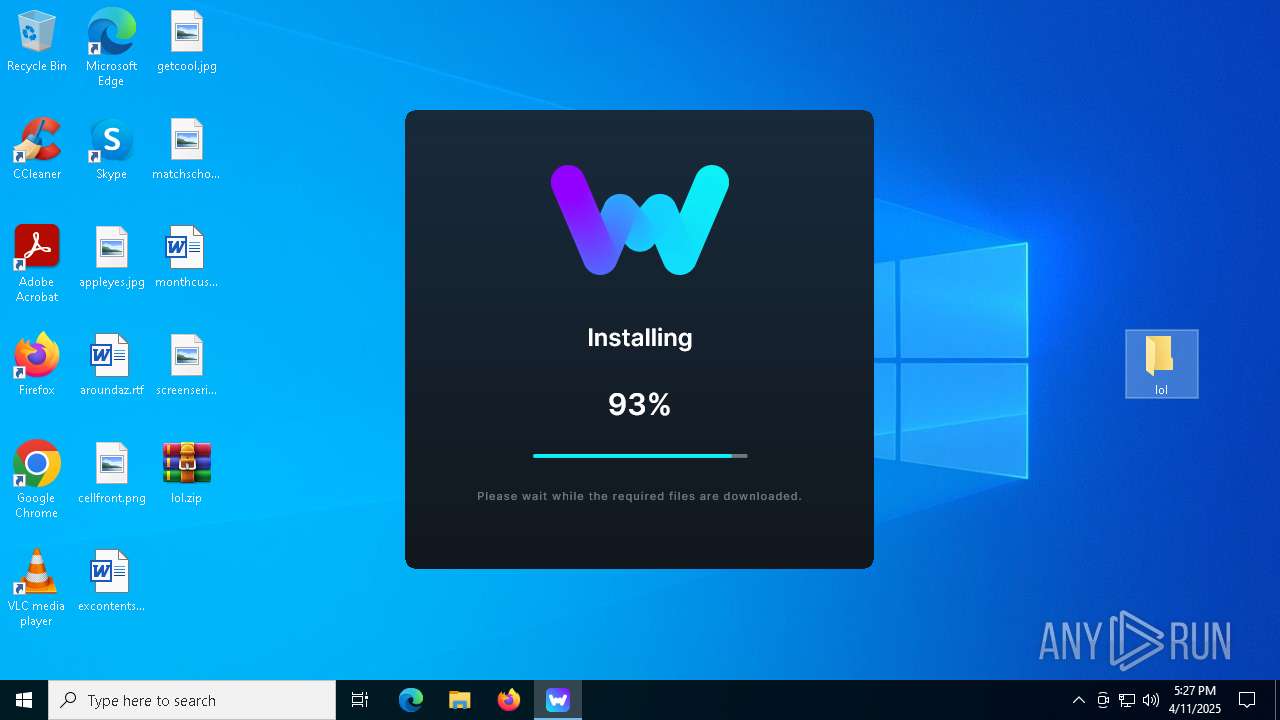
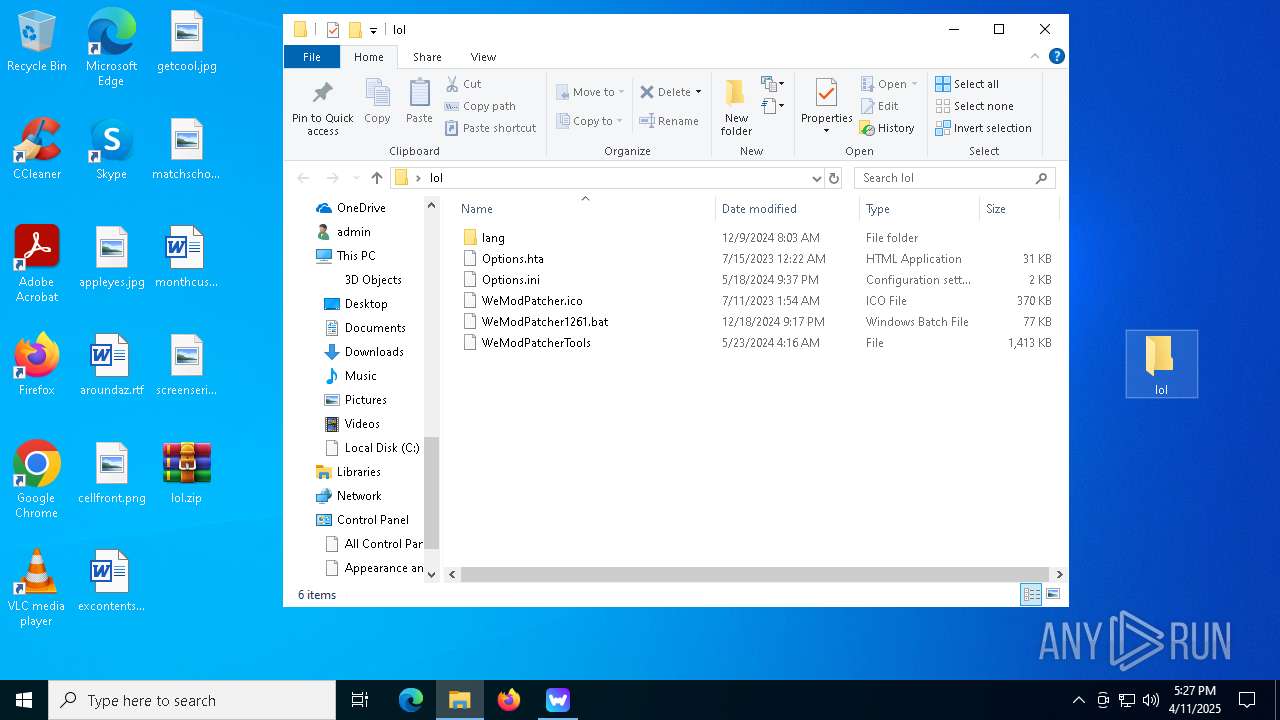
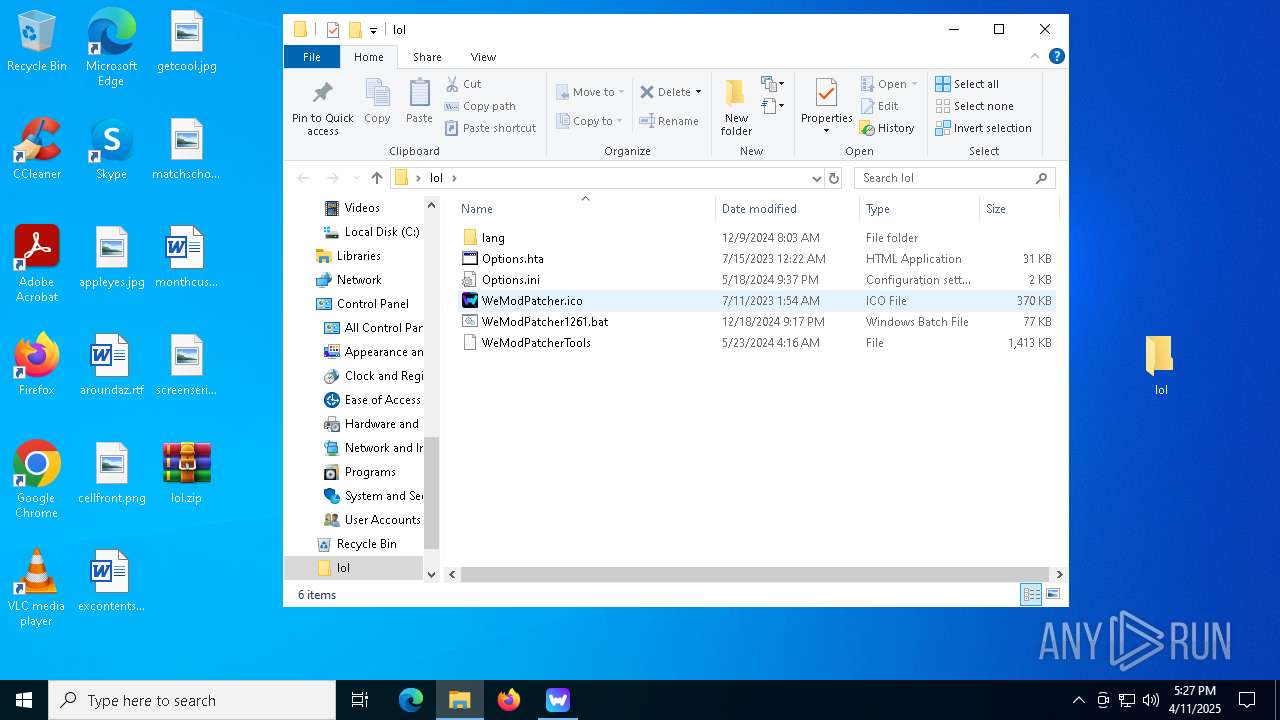
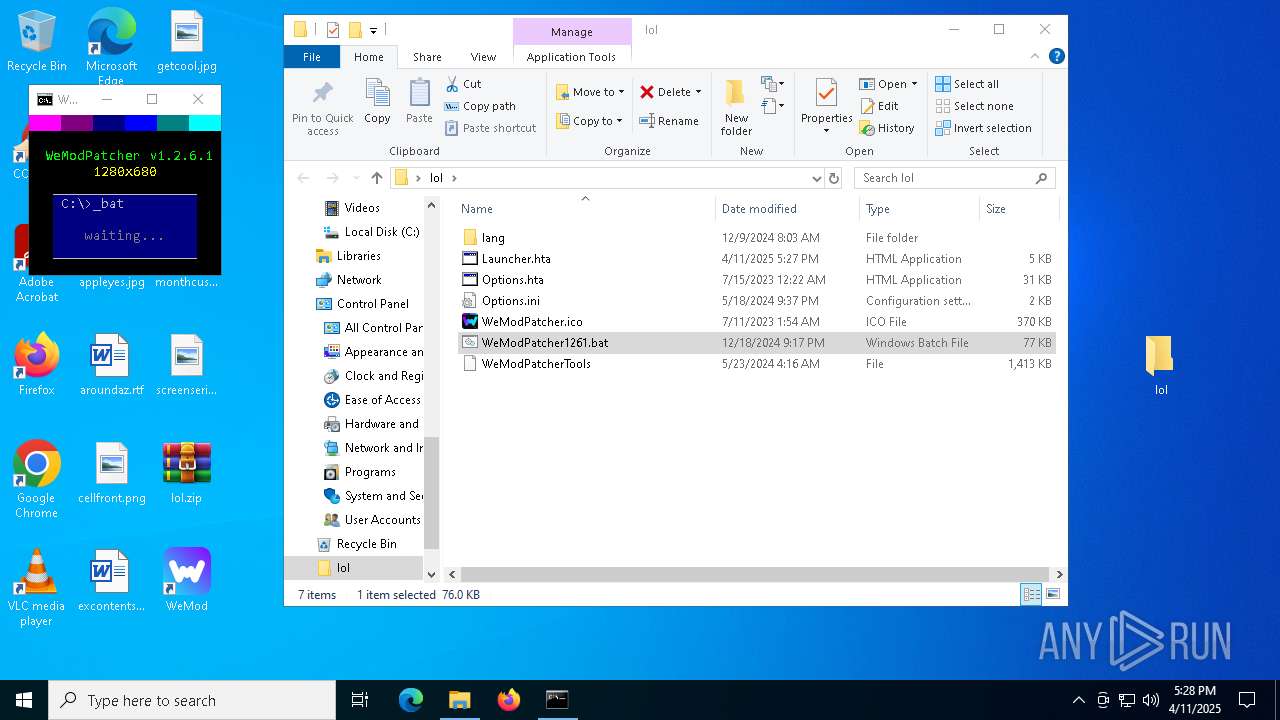
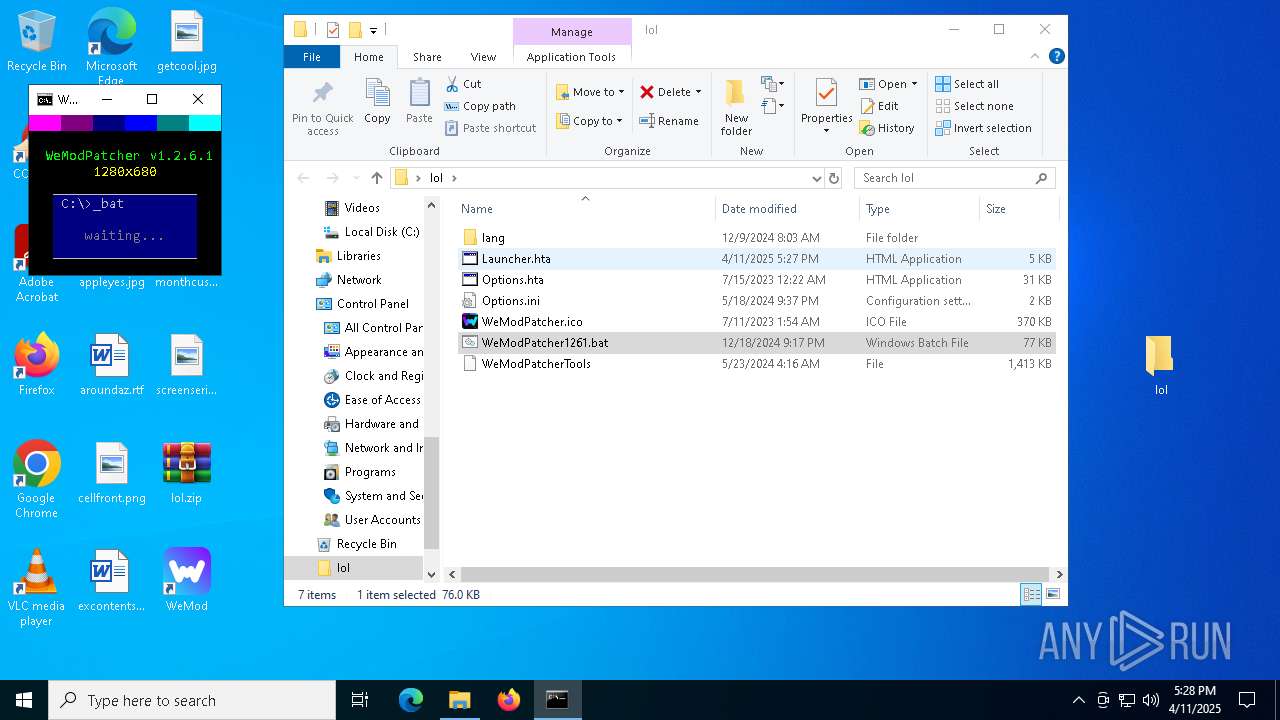
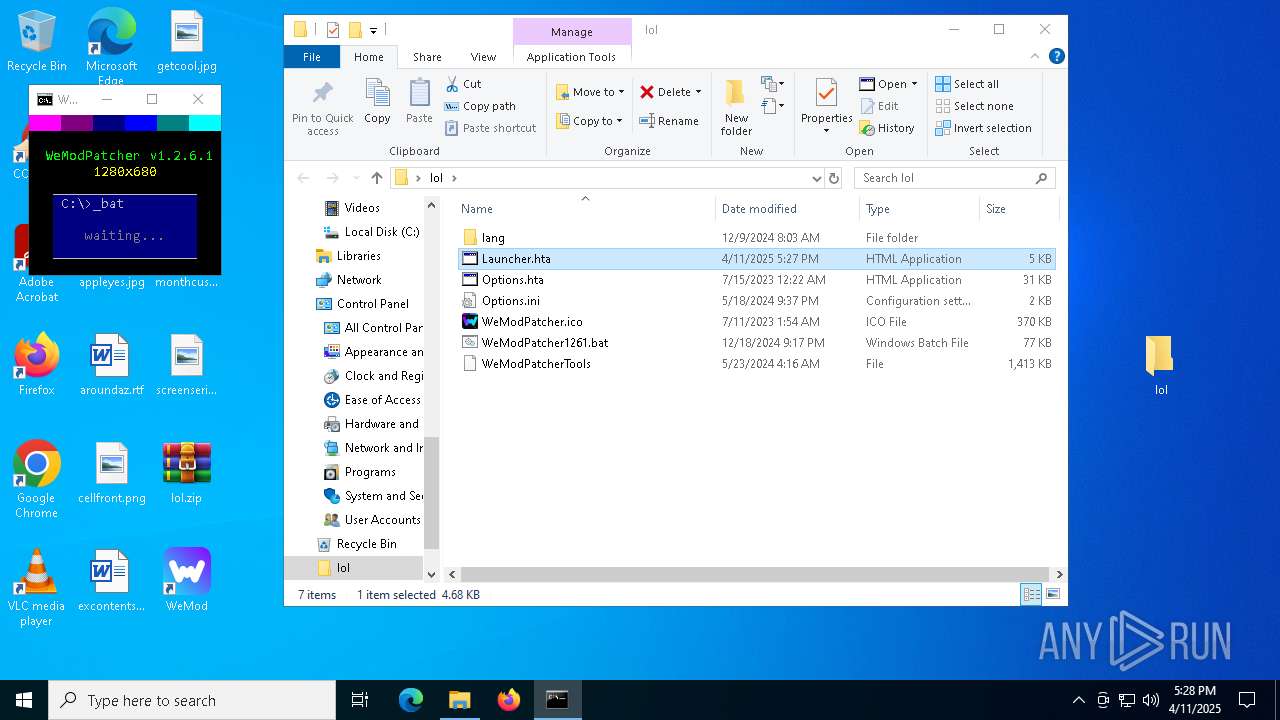
| File name: | WeMod-Setup.exe |
| Full analysis: | https://app.any.run/tasks/b5a07db9-1ace-4d90-9719-63e72b1a0346 |
| Verdict: | Malicious activity |
| Analysis date: | April 11, 2025, 17:26:36 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | C4DF4804B83E9E89A40CD9CC0EF0B2E7 |
| SHA1: | 95B22D2E6D68283AC773488C8ED44FEA595F1AB5 |
| SHA256: | 1C1058F1361F2A1E5E346BC150ACCE1D1EF8F4E3E622EB374E5ED97126437A53 |
| SSDEEP: | 1536:Q668Dtf9nk7RBog5KG6JkOiVPL+09ME5LBtJD64uQgCYO6+YFyHA7OqCkNRBog5m:w8DvE57miVj+J6pHdHg7OA57N/u |
MALICIOUS
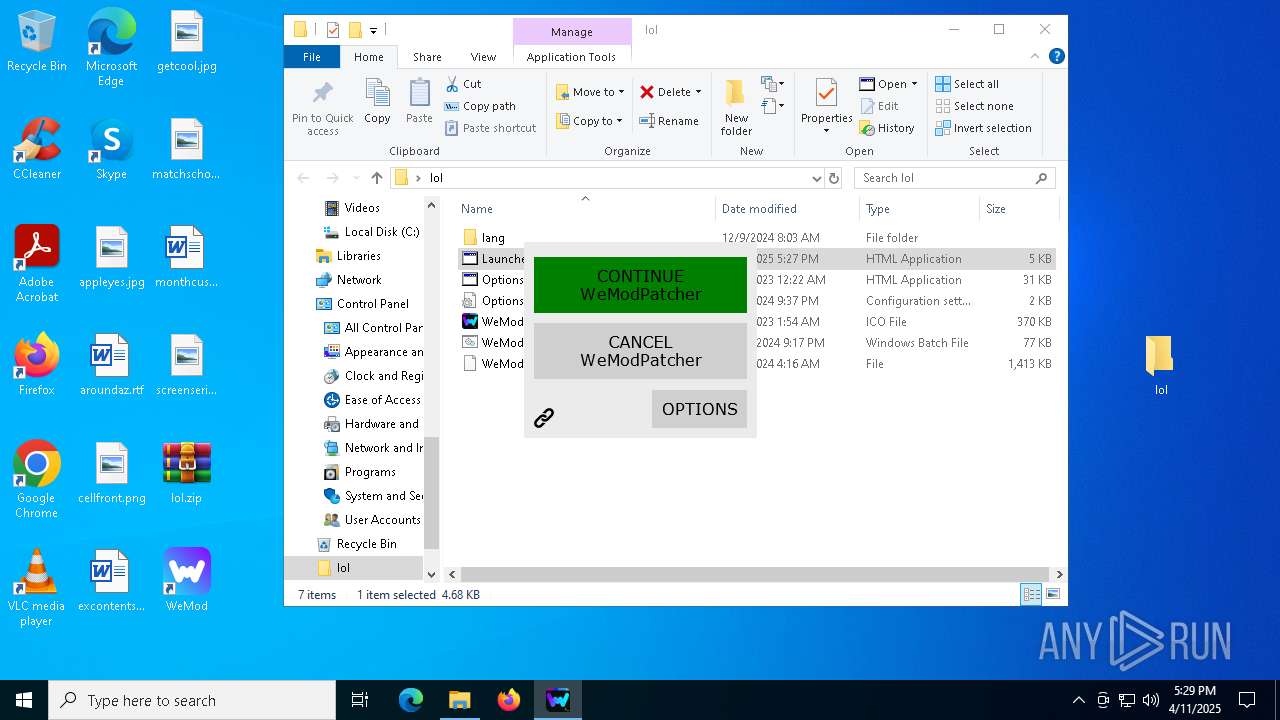
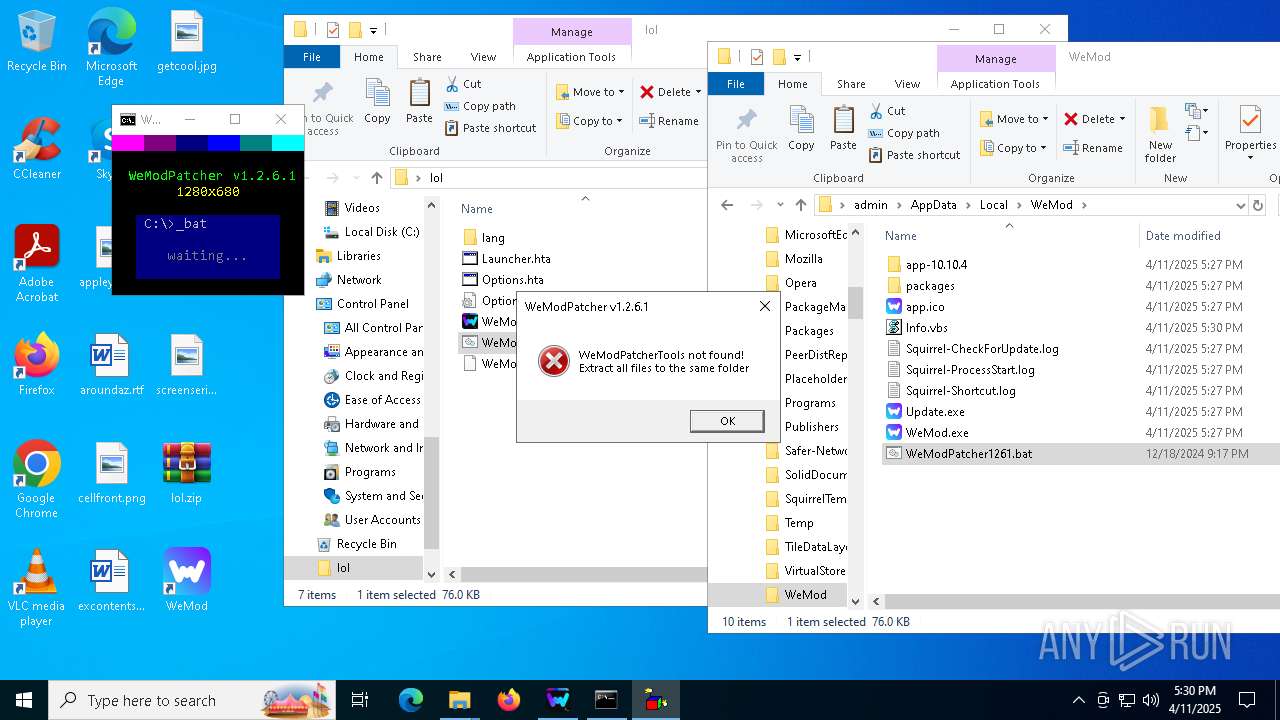
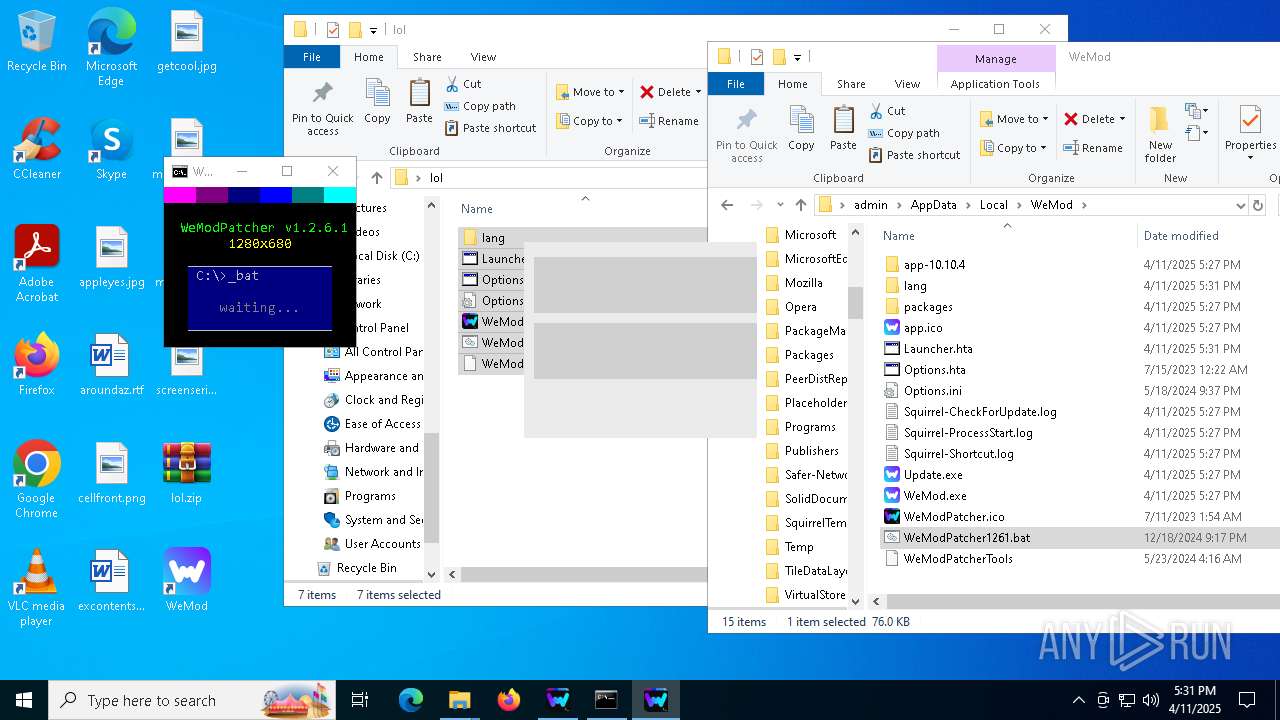
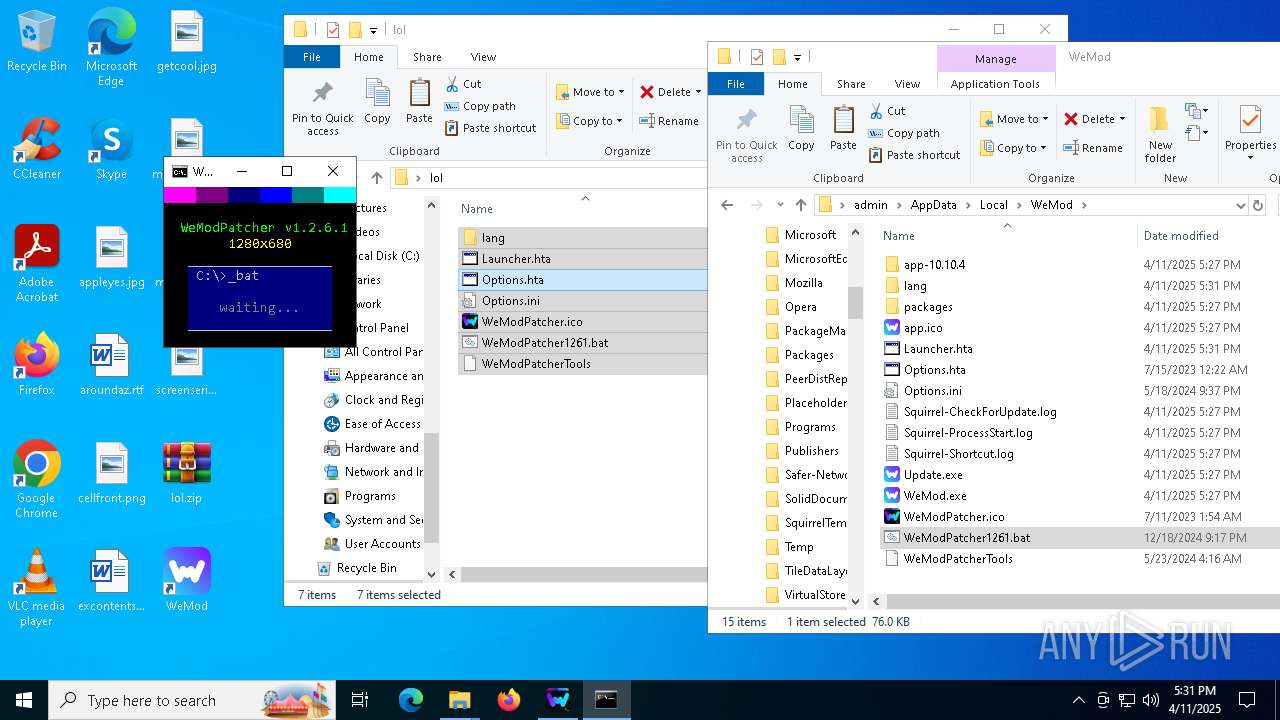
Opens a text file (SCRIPT)
- mshta.exe (PID: 5408)
- mshta.exe (PID: 5232)
Checks whether a specified folder exists (SCRIPT)
- mshta.exe (PID: 5408)
- mshta.exe (PID: 5232)
SUSPICIOUS
Reads security settings of Internet Explorer
- WeMod-Setup.exe (PID: 6036)
- Update.exe (PID: 3676)
- Update.exe (PID: 5156)
- WeModAuxiliaryService.exe (PID: 2960)
Reads Microsoft Outlook installation path
- WeMod-Setup.exe (PID: 6036)
Reads Internet Explorer settings
- WeMod-Setup.exe (PID: 6036)
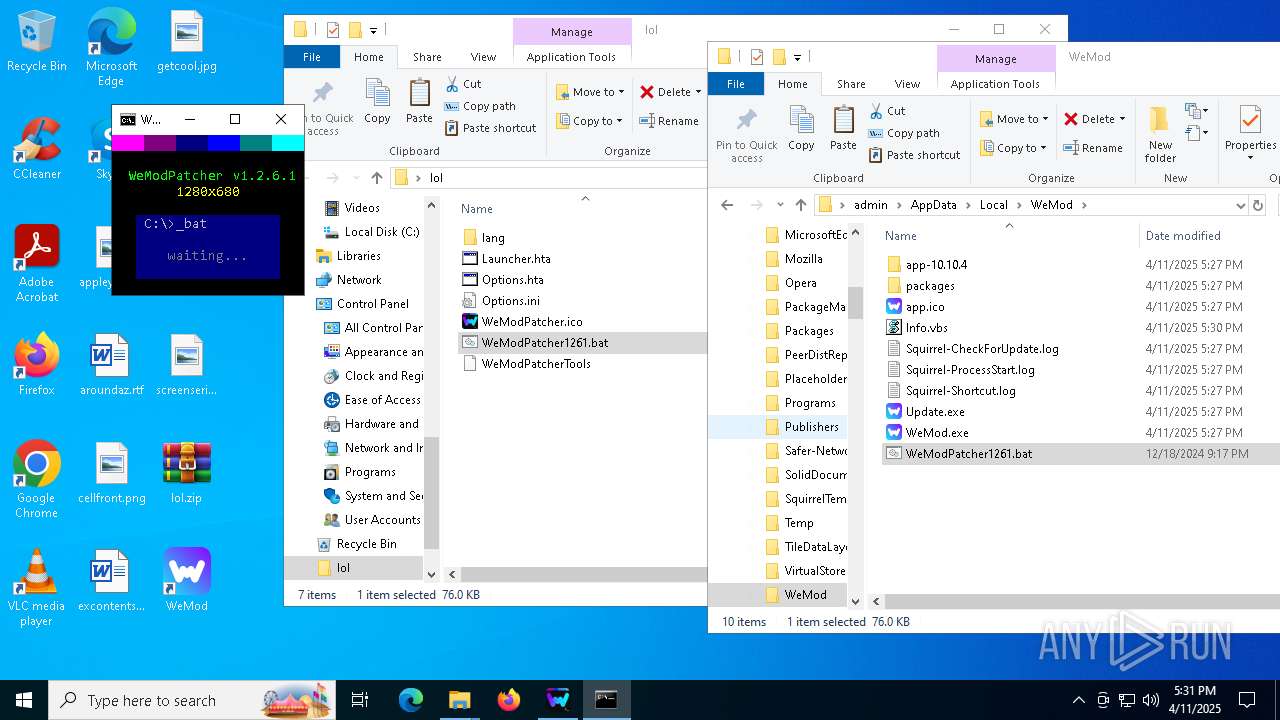
Executable content was dropped or overwritten
- WeMod-Setup-638799892126045532.exe (PID: 5720)
- Update.exe (PID: 3676)
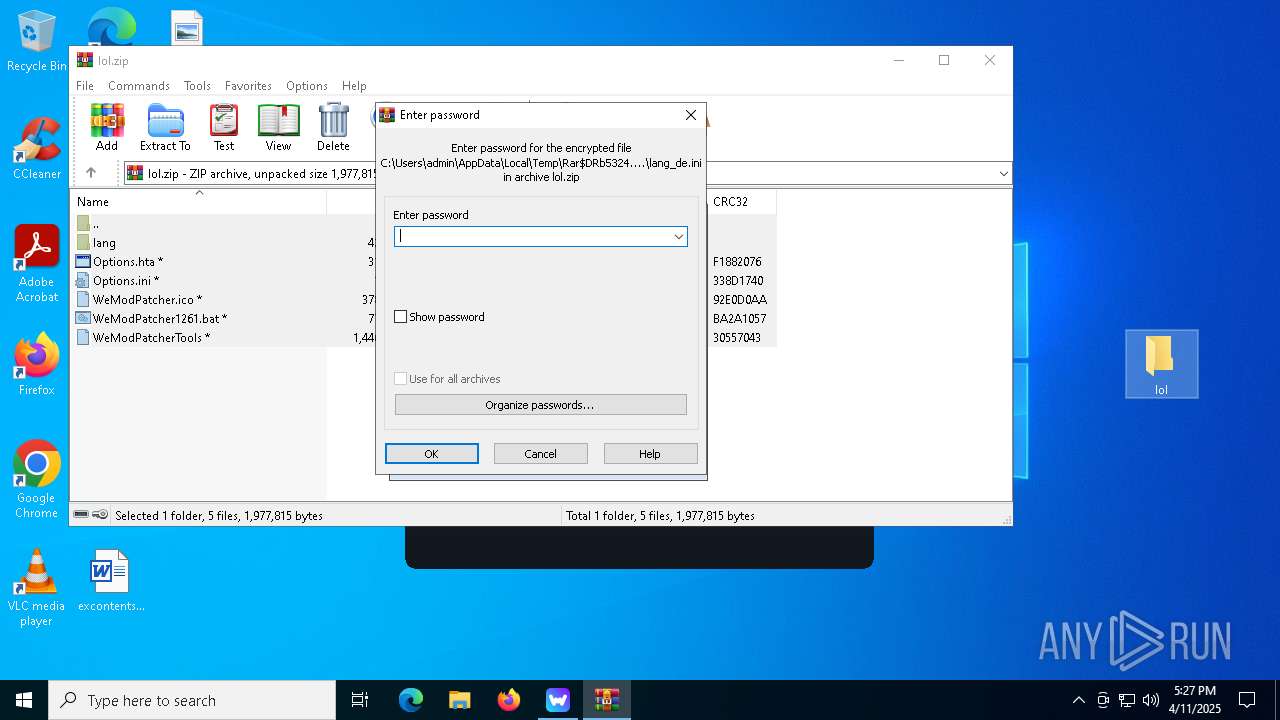
Drops 7-zip archiver for unpacking
- WinRAR.exe (PID: 5324)
Process drops legitimate windows executable
- Update.exe (PID: 3676)
Application launched itself
- cmd.exe (PID: 3332)
- WeMod.exe (PID: 5624)
- mshta.exe (PID: 6944)
- cmd.exe (PID: 6940)
- cmd.exe (PID: 2852)
Execution of CURL command
- cmd.exe (PID: 3332)
- cmd.exe (PID: 6940)
- cmd.exe (PID: 2852)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6656)
- cmd.exe (PID: 6208)
- cmd.exe (PID: 3332)
- cmd.exe (PID: 2136)
- cmd.exe (PID: 5232)
- cmd.exe (PID: 6132)
- cmd.exe (PID: 2772)
- cmd.exe (PID: 780)
- cmd.exe (PID: 976)
- cmd.exe (PID: 5188)
- cmd.exe (PID: 1388)
- cmd.exe (PID: 132)
- cmd.exe (PID: 976)
- cmd.exe (PID: 4980)
- cmd.exe (PID: 5188)
- cmd.exe (PID: 3028)
- cmd.exe (PID: 960)
- cmd.exe (PID: 1328)
- cmd.exe (PID: 896)
- cmd.exe (PID: 2596)
- cmd.exe (PID: 6740)
- cmd.exe (PID: 5588)
- cmd.exe (PID: 1180)
- cmd.exe (PID: 3020)
- cmd.exe (PID: 1676)
- cmd.exe (PID: 1388)
- cmd.exe (PID: 6940)
- cmd.exe (PID: 3008)
- cmd.exe (PID: 5232)
- cmd.exe (PID: 4528)
- cmd.exe (PID: 1764)
- cmd.exe (PID: 6592)
- cmd.exe (PID: 1812)
- cmd.exe (PID: 1764)
- cmd.exe (PID: 2852)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 3332)
- cmd.exe (PID: 4276)
- cmd.exe (PID: 6828)
- cmd.exe (PID: 800)
- cmd.exe (PID: 5552)
- cmd.exe (PID: 2780)
- cmd.exe (PID: 5348)
- cmd.exe (PID: 6736)
- cmd.exe (PID: 4452)
Found IP address in command line
- powershell.exe (PID: 6584)
- powershell.exe (PID: 2772)
- powershell.exe (PID: 1004)
- powershell.exe (PID: 2332)
- powershell.exe (PID: 3796)
- powershell.exe (PID: 6744)
- powershell.exe (PID: 6476)
Reads the date of Windows installation
- Update.exe (PID: 3676)
- WeMod-Setup.exe (PID: 6036)
- Update.exe (PID: 5156)
Get information on the list of running processes
- cmd.exe (PID: 3332)
- cmd.exe (PID: 6652)
- cmd.exe (PID: 6208)
- cmd.exe (PID: 4696)
- cmd.exe (PID: 6940)
- cmd.exe (PID: 3008)
- cmd.exe (PID: 6040)
- cmd.exe (PID: 4024)
- cmd.exe (PID: 2852)
- cmd.exe (PID: 3364)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 3416)
Starts NET.EXE to display or manage information about active sessions
- cmd.exe (PID: 3332)
- net.exe (PID: 960)
- net.exe (PID: 4628)
- cmd.exe (PID: 6940)
- cmd.exe (PID: 2852)
- net.exe (PID: 6572)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3332)
- cmd.exe (PID: 6940)
- cmd.exe (PID: 2852)
Starts application with an unusual extension
- cmd.exe (PID: 2564)
- cmd.exe (PID: 3332)
- cmd.exe (PID: 2088)
- cmd.exe (PID: 6940)
- cmd.exe (PID: 7104)
- cmd.exe (PID: 2852)
Creates a software uninstall entry
- Update.exe (PID: 3676)
Searches for installed software
- Update.exe (PID: 3676)
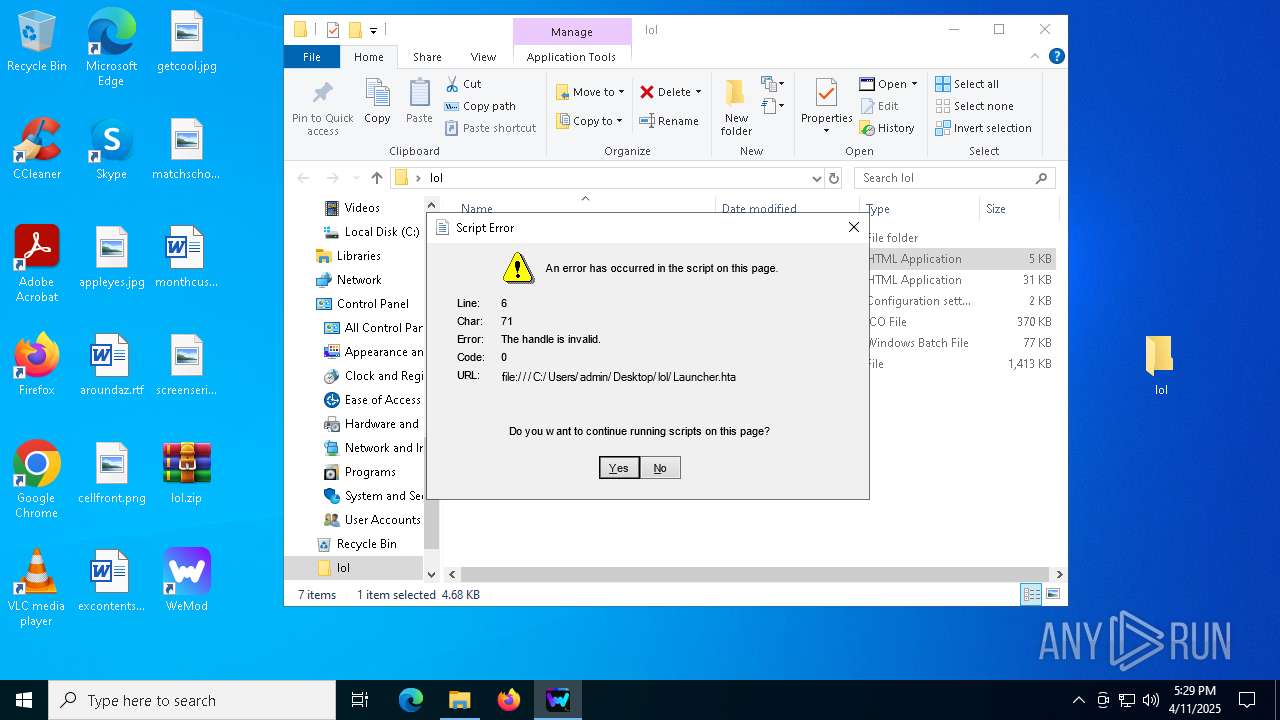
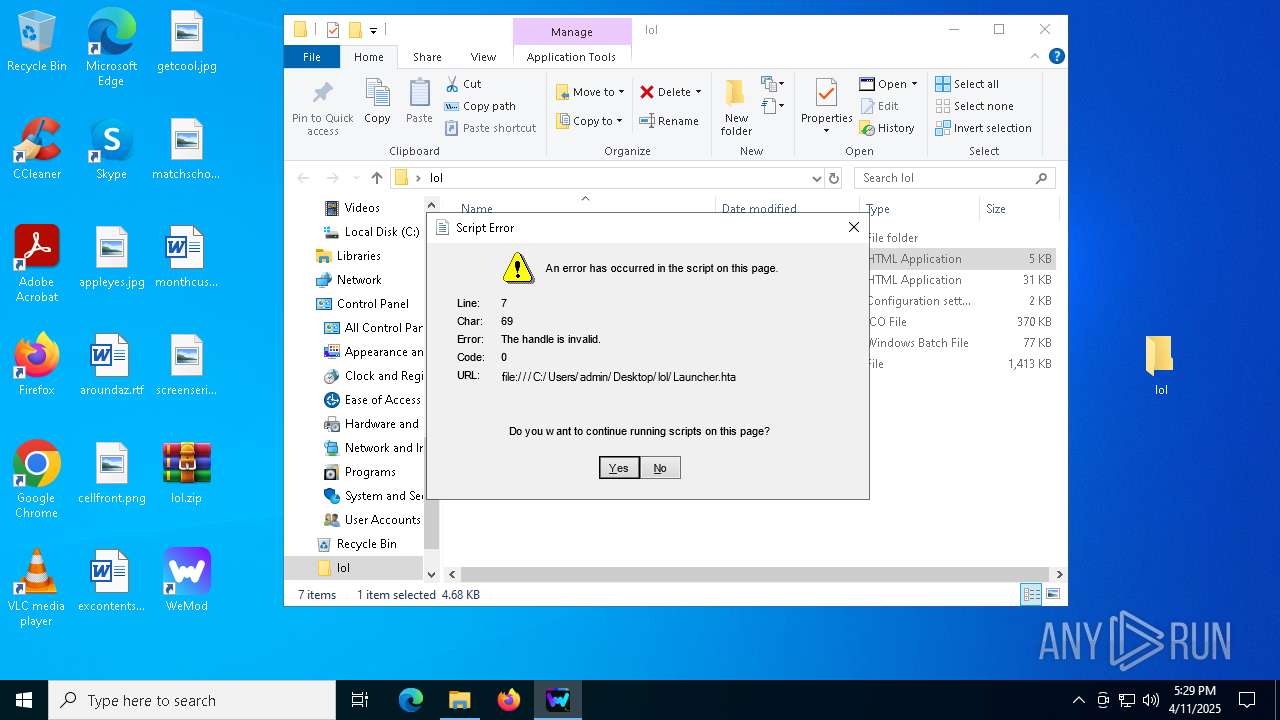
Executes application which crashes
- mshta.exe (PID: 6208)
- mshta.exe (PID: 4884)
- mshta.exe (PID: 3796)
- mshta.exe (PID: 1164)
- mshta.exe (PID: 4884)
- mshta.exe (PID: 4068)
- mshta.exe (PID: 672)
- mshta.exe (PID: 2664)
- mshta.exe (PID: 5544)
- mshta.exe (PID: 132)
- mshta.exe (PID: 4068)
- mshta.exe (PID: 2432)
- mshta.exe (PID: 6644)
- mshta.exe (PID: 5408)
- mshta.exe (PID: 5164)
- mshta.exe (PID: 6660)
- mshta.exe (PID: 5680)
- mshta.exe (PID: 5232)
- mshta.exe (PID: 6980)
- mshta.exe (PID: 5032)
- mshta.exe (PID: 3164)
- mshta.exe (PID: 3800)
Creates FileSystem object to access computer's file system (SCRIPT)
- mshta.exe (PID: 4884)
- mshta.exe (PID: 6208)
- mshta.exe (PID: 3796)
- mshta.exe (PID: 1164)
- mshta.exe (PID: 4884)
- mshta.exe (PID: 4068)
- mshta.exe (PID: 672)
- mshta.exe (PID: 2664)
- mshta.exe (PID: 5544)
- mshta.exe (PID: 132)
- mshta.exe (PID: 4068)
- mshta.exe (PID: 6944)
- mshta.exe (PID: 6644)
- mshta.exe (PID: 2432)
- mshta.exe (PID: 5408)
- mshta.exe (PID: 5164)
- mshta.exe (PID: 5680)
- mshta.exe (PID: 5232)
- mshta.exe (PID: 6660)
- mshta.exe (PID: 6980)
- mshta.exe (PID: 5352)
- mshta.exe (PID: 2092)
- mshta.exe (PID: 3164)
- mshta.exe (PID: 3800)
- mshta.exe (PID: 5032)
The process creates files with name similar to system file names
- WerFault.exe (PID: 1388)
- WerFault.exe (PID: 4880)
- WerFault.exe (PID: 4304)
- WerFault.exe (PID: 5384)
- WerFault.exe (PID: 6980)
- WerFault.exe (PID: 4180)
- WerFault.exe (PID: 1164)
- WerFault.exe (PID: 6640)
- WerFault.exe (PID: 4880)
- WerFault.exe (PID: 2288)
- WerFault.exe (PID: 7036)
- WerFault.exe (PID: 2852)
- WerFault.exe (PID: 3828)
- WerFault.exe (PID: 6652)
- WerFault.exe (PID: 3828)
- WerFault.exe (PID: 632)
- WerFault.exe (PID: 6700)
- WerFault.exe (PID: 5480)
- WerFault.exe (PID: 6136)
- WerFault.exe (PID: 6572)
Checks whether a specific file exists (SCRIPT)
- mshta.exe (PID: 6944)
- mshta.exe (PID: 5408)
- mshta.exe (PID: 5232)
- mshta.exe (PID: 5352)
Reads data from a binary Stream object (SCRIPT)
- mshta.exe (PID: 5408)
- mshta.exe (PID: 5232)
Runs shell command (SCRIPT)
- mshta.exe (PID: 6944)
Writes binary data to a Stream object (SCRIPT)
- mshta.exe (PID: 5352)
- mshta.exe (PID: 2092)
The process executes VB scripts
- cmd.exe (PID: 6940)
INFO
Checks supported languages
- WeMod-Setup.exe (PID: 6036)
- Update.exe (PID: 3676)
- WeMod-Setup-638799892126045532.exe (PID: 5720)
- curl.exe (PID: 5084)
- squirrel.exe (PID: 4172)
- mode.com (PID: 4268)
- chcp.com (PID: 2904)
- chcp.com (PID: 4996)
- Update.exe (PID: 856)
- WeMod.exe (PID: 5260)
- WeMod.exe (PID: 5624)
- WeMod.exe (PID: 6660)
- Update.exe (PID: 5156)
- WeMod.exe (PID: 7144)
- WeMod.exe (PID: 6676)
- Update.exe (PID: 6048)
- WeModAuxiliaryService.exe (PID: 2960)
- chcp.com (PID: 5796)
- chcp.com (PID: 7036)
- chcp.com (PID: 1616)
- chcp.com (PID: 2092)
- chcp.com (PID: 6132)
- chcp.com (PID: 4880)
- chcp.com (PID: 3976)
- chcp.com (PID: 2092)
- chcp.com (PID: 6132)
- chcp.com (PID: 2420)
- chcp.com (PID: 2420)
- chcp.com (PID: 5204)
- chcp.com (PID: 3300)
- chcp.com (PID: 6192)
- chcp.com (PID: 7052)
- chcp.com (PID: 2064)
- chcp.com (PID: 5324)
- chcp.com (PID: 5304)
- curl.exe (PID: 1072)
- mode.com (PID: 1616)
- chcp.com (PID: 2780)
- chcp.com (PID: 4452)
- chcp.com (PID: 5260)
- chcp.com (PID: 680)
- curl.exe (PID: 2504)
- chcp.com (PID: 300)
- mode.com (PID: 5360)
- chcp.com (PID: 6168)
- chcp.com (PID: 1512)
- chcp.com (PID: 7124)
Checks proxy server information
- WeMod-Setup.exe (PID: 6036)
- Update.exe (PID: 3676)
- WeMod.exe (PID: 5624)
- Update.exe (PID: 6048)
- WeModAuxiliaryService.exe (PID: 2960)
- mshta.exe (PID: 6208)
- mshta.exe (PID: 4884)
- mshta.exe (PID: 3796)
- mshta.exe (PID: 1164)
- mshta.exe (PID: 4884)
- mshta.exe (PID: 4068)
- mshta.exe (PID: 672)
- mshta.exe (PID: 2664)
- mshta.exe (PID: 5544)
- mshta.exe (PID: 132)
- mshta.exe (PID: 4068)
- mshta.exe (PID: 2432)
- mshta.exe (PID: 6944)
- mshta.exe (PID: 6644)
- mshta.exe (PID: 5164)
- slui.exe (PID: 4268)
- mshta.exe (PID: 6660)
- mshta.exe (PID: 5680)
- mshta.exe (PID: 6980)
- mshta.exe (PID: 5352)
- mshta.exe (PID: 2092)
- mshta.exe (PID: 3164)
- mshta.exe (PID: 5032)
Reads the computer name
- WeMod-Setup.exe (PID: 6036)
- Update.exe (PID: 3676)
- curl.exe (PID: 5084)
- squirrel.exe (PID: 4172)
- Update.exe (PID: 856)
- WeMod.exe (PID: 5624)
- Update.exe (PID: 5156)
- WeMod.exe (PID: 7144)
- Update.exe (PID: 6048)
- WeMod.exe (PID: 6660)
- WeModAuxiliaryService.exe (PID: 2960)
- curl.exe (PID: 1072)
- curl.exe (PID: 2504)
Disables trace logs
- WeMod-Setup.exe (PID: 6036)
- Update.exe (PID: 3676)
- Update.exe (PID: 6048)
Reads the machine GUID from the registry
- WeMod-Setup.exe (PID: 6036)
- Update.exe (PID: 3676)
- squirrel.exe (PID: 4172)
- Update.exe (PID: 856)
- Update.exe (PID: 5156)
- WeMod.exe (PID: 5624)
- Update.exe (PID: 6048)
- WeModAuxiliaryService.exe (PID: 2960)
Creates files or folders in the user directory
- WeMod-Setup.exe (PID: 6036)
- WeMod-Setup-638799892126045532.exe (PID: 5720)
- Update.exe (PID: 3676)
- squirrel.exe (PID: 4172)
- Update.exe (PID: 856)
- WeMod.exe (PID: 5624)
- Update.exe (PID: 5156)
- WeMod.exe (PID: 7144)
- Update.exe (PID: 6048)
- WeModAuxiliaryService.exe (PID: 2960)
- WerFault.exe (PID: 4880)
- WerFault.exe (PID: 1388)
- WerFault.exe (PID: 4304)
- WerFault.exe (PID: 5384)
- WerFault.exe (PID: 6980)
- WerFault.exe (PID: 4180)
- WerFault.exe (PID: 4880)
- WerFault.exe (PID: 1164)
- WerFault.exe (PID: 6640)
- WerFault.exe (PID: 7036)
- WerFault.exe (PID: 2288)
- WerFault.exe (PID: 2852)
- WerFault.exe (PID: 3828)
- WerFault.exe (PID: 6652)
- WerFault.exe (PID: 904)
- WerFault.exe (PID: 3828)
- WerFault.exe (PID: 6700)
- WerFault.exe (PID: 4528)
- WerFault.exe (PID: 632)
- WerFault.exe (PID: 6136)
Reads Environment values
- WeMod-Setup.exe (PID: 6036)
- WeMod.exe (PID: 5260)
- Update.exe (PID: 3676)
- WeMod.exe (PID: 5624)
- Update.exe (PID: 6048)
Reads the software policy settings
- WeMod-Setup.exe (PID: 6036)
- Update.exe (PID: 3676)
- Update.exe (PID: 6048)
- WeModAuxiliaryService.exe (PID: 2960)
- slui.exe (PID: 1532)
- slui.exe (PID: 4268)
Create files in a temporary directory
- WeMod-Setup.exe (PID: 6036)
- Update.exe (PID: 3676)
- WeMod.exe (PID: 5624)
- Update.exe (PID: 6048)
The sample compiled with english language support
- WinRAR.exe (PID: 5324)
- Update.exe (PID: 3676)
Manual execution by a user
- WinRAR.exe (PID: 5324)
- cmd.exe (PID: 3332)
- mshta.exe (PID: 6944)
- mshta.exe (PID: 5232)
- mshta.exe (PID: 5352)
- cmd.exe (PID: 6940)
- cmd.exe (PID: 2852)
Execution of CURL command
- cmd.exe (PID: 6240)
- cmd.exe (PID: 6980)
- cmd.exe (PID: 5772)
Process checks computer location settings
- Update.exe (PID: 3676)
- WeMod-Setup.exe (PID: 6036)
- Update.exe (PID: 5156)
- WeMod.exe (PID: 5624)
- WeMod.exe (PID: 6676)
Reads product name
- WeMod.exe (PID: 5260)
- WeMod.exe (PID: 5624)
Changes the display of characters in the console
- cmd.exe (PID: 2564)
- cmd.exe (PID: 3332)
- cmd.exe (PID: 2088)
- cmd.exe (PID: 6940)
- cmd.exe (PID: 7104)
- cmd.exe (PID: 2852)
Starts MODE.COM to configure console settings
- mode.com (PID: 4268)
- mode.com (PID: 1616)
- mode.com (PID: 5360)
Reads CPU info
- WeMod.exe (PID: 5624)
Gets data length (POWERSHELL)
- powershell.exe (PID: 5528)
- powershell.exe (PID: 1244)
- powershell.exe (PID: 6940)
Node.js compiler has been detected
- WeMod.exe (PID: 6676)
Reads Internet Explorer settings
- mshta.exe (PID: 4884)
- mshta.exe (PID: 6208)
- mshta.exe (PID: 3796)
- mshta.exe (PID: 1164)
- mshta.exe (PID: 672)
- mshta.exe (PID: 4884)
- mshta.exe (PID: 4068)
- mshta.exe (PID: 2664)
- mshta.exe (PID: 5544)
- mshta.exe (PID: 132)
- mshta.exe (PID: 4068)
- mshta.exe (PID: 2432)
- mshta.exe (PID: 6944)
- mshta.exe (PID: 6644)
- mshta.exe (PID: 5164)
- mshta.exe (PID: 6660)
- mshta.exe (PID: 5408)
- mshta.exe (PID: 5680)
- mshta.exe (PID: 5232)
- mshta.exe (PID: 6980)
- mshta.exe (PID: 5352)
- mshta.exe (PID: 3164)
- mshta.exe (PID: 5032)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2076:12:06 19:29:50+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 105984 |
| InitializedDataSize: | 28160 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1bcfe |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 8.0.0.0 |
| ProductVersionNumber: | 8.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | WeMod Setup |
| CompanyName: | WeMod LLC |
| FileDescription: | WeMod Setup |
| FileVersion: | 8.0.0.0 |
| InternalName: | WeMod-Setup.exe |
| LegalCopyright: | Copyright © WeMod LLC 2022 |
| LegalTrademarks: | - |
| OriginalFileName: | WeMod-Setup.exe |
| ProductName: | WeMod |
| ProductVersion: | 8.0.0.0 |
| AssemblyVersion: | 8.0.0.0 |
Total processes
415
Monitored processes
253
Malicious processes
12
Suspicious processes
25
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | C:\WINDOWS\system32\cmd.exe /c powershell -Command "(Get-FileHash Options.ini -Algorithm MD5).Hash" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
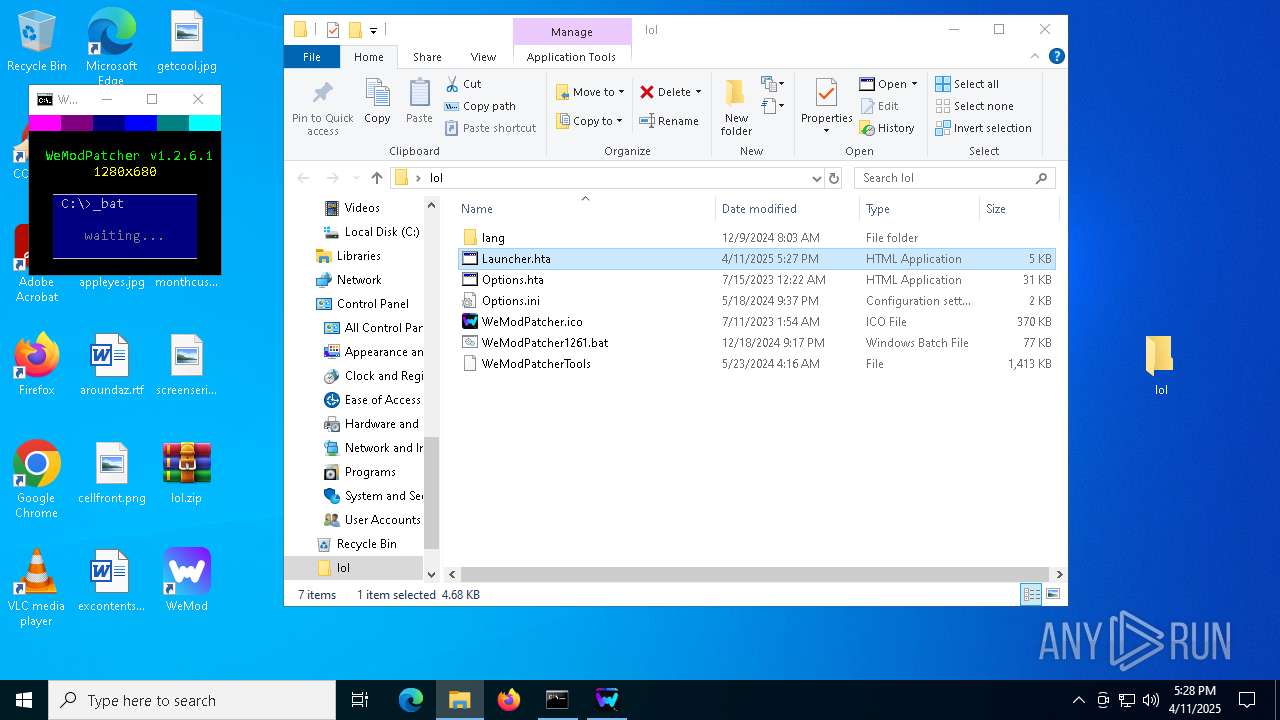
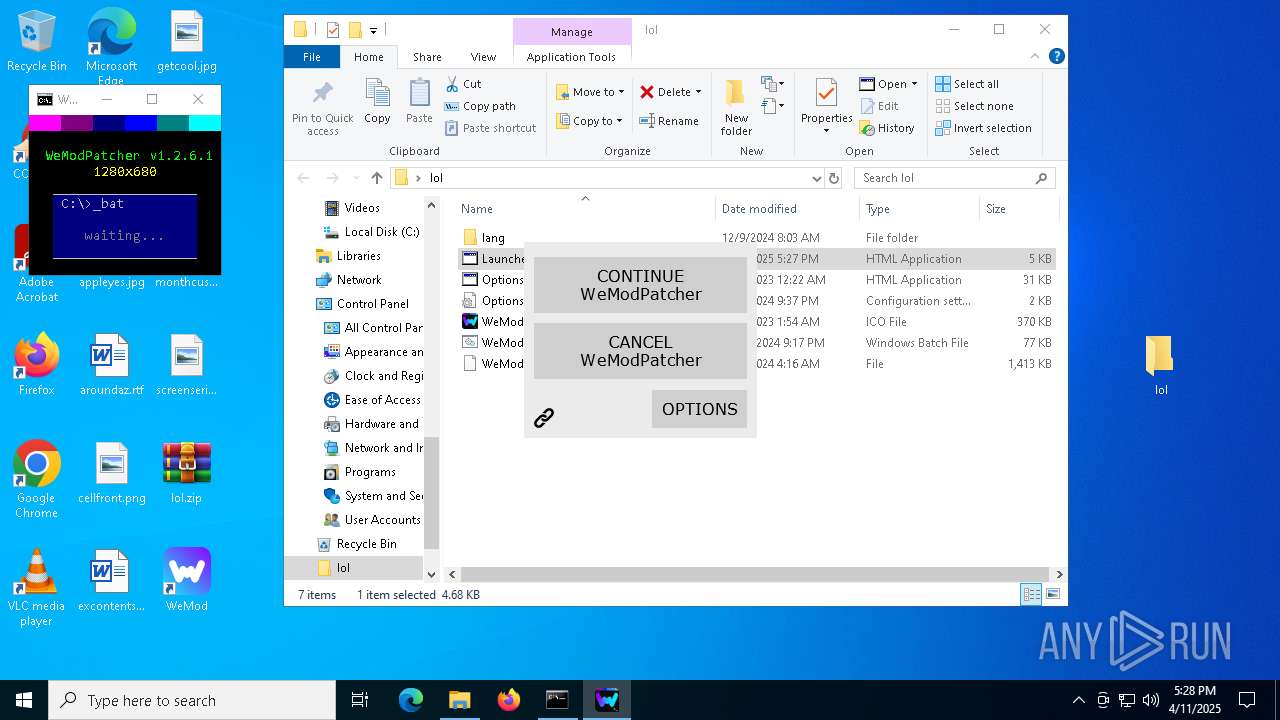
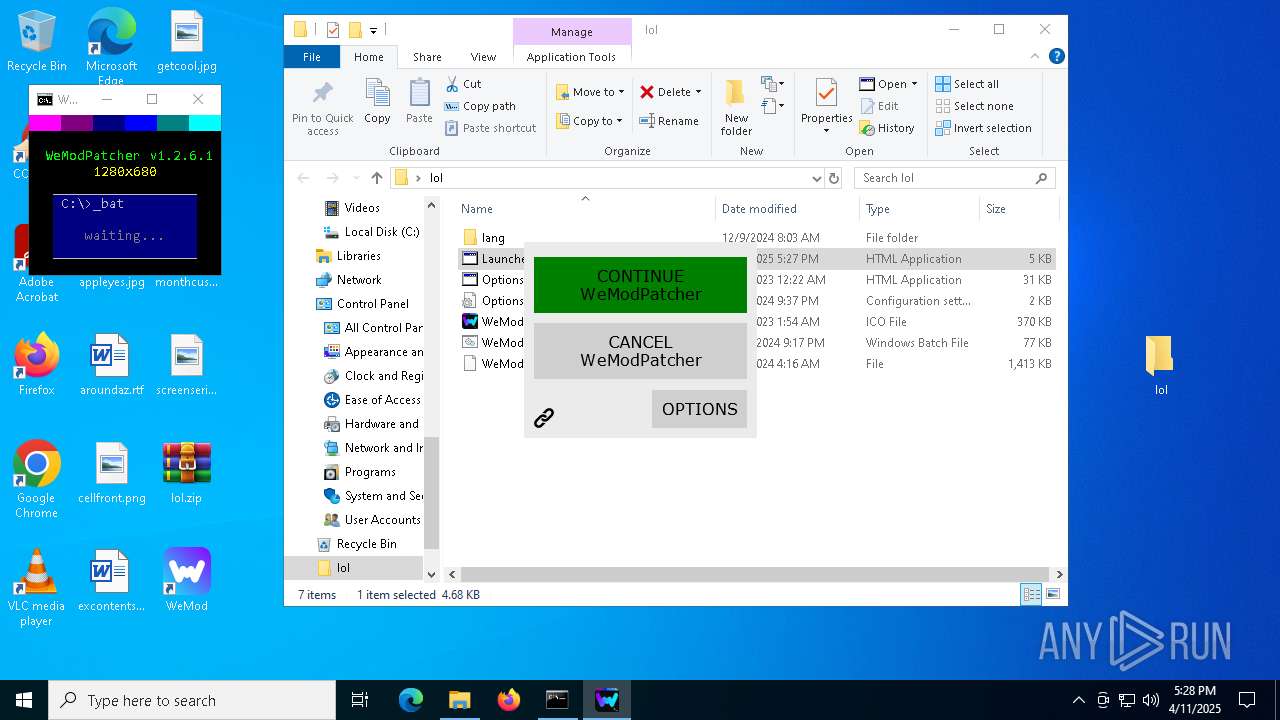
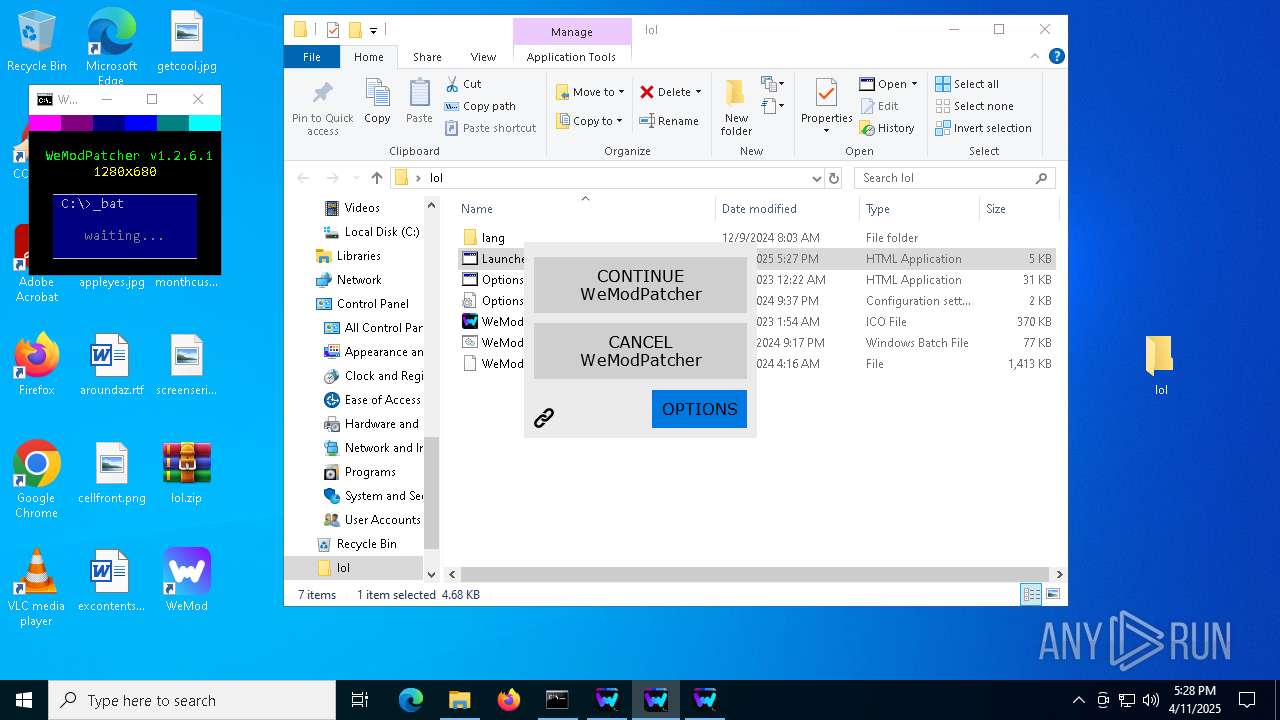
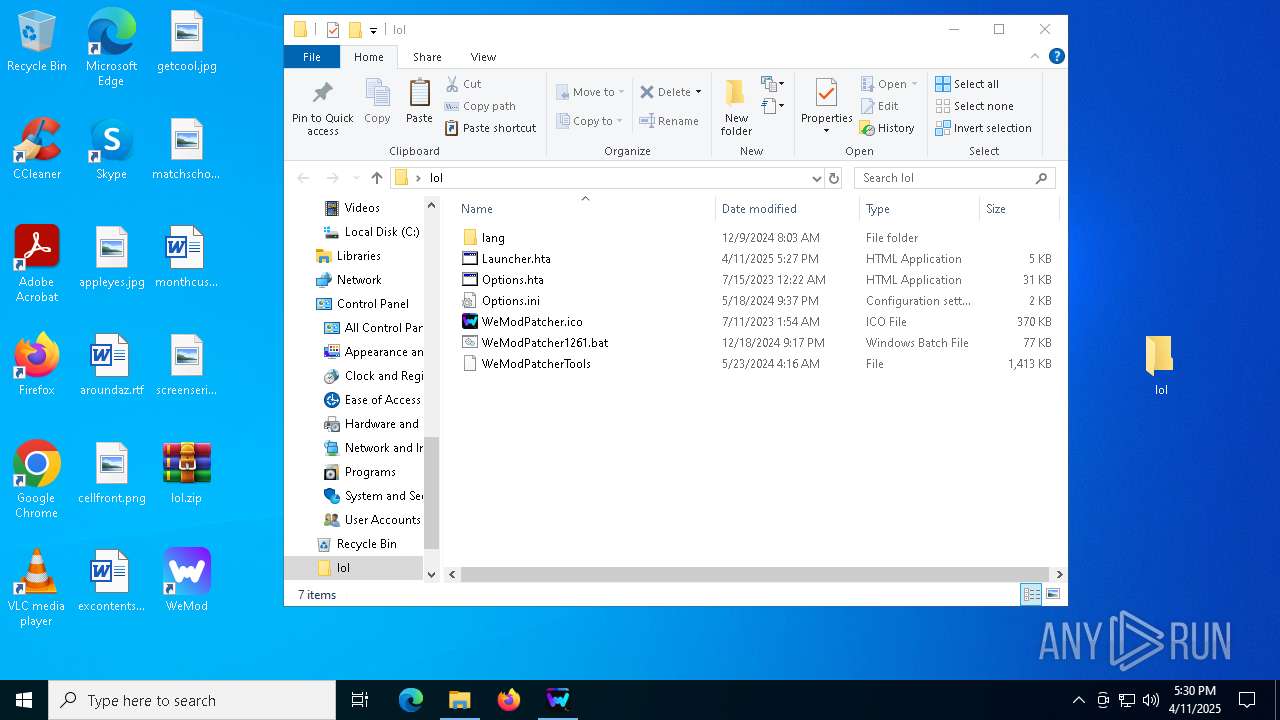
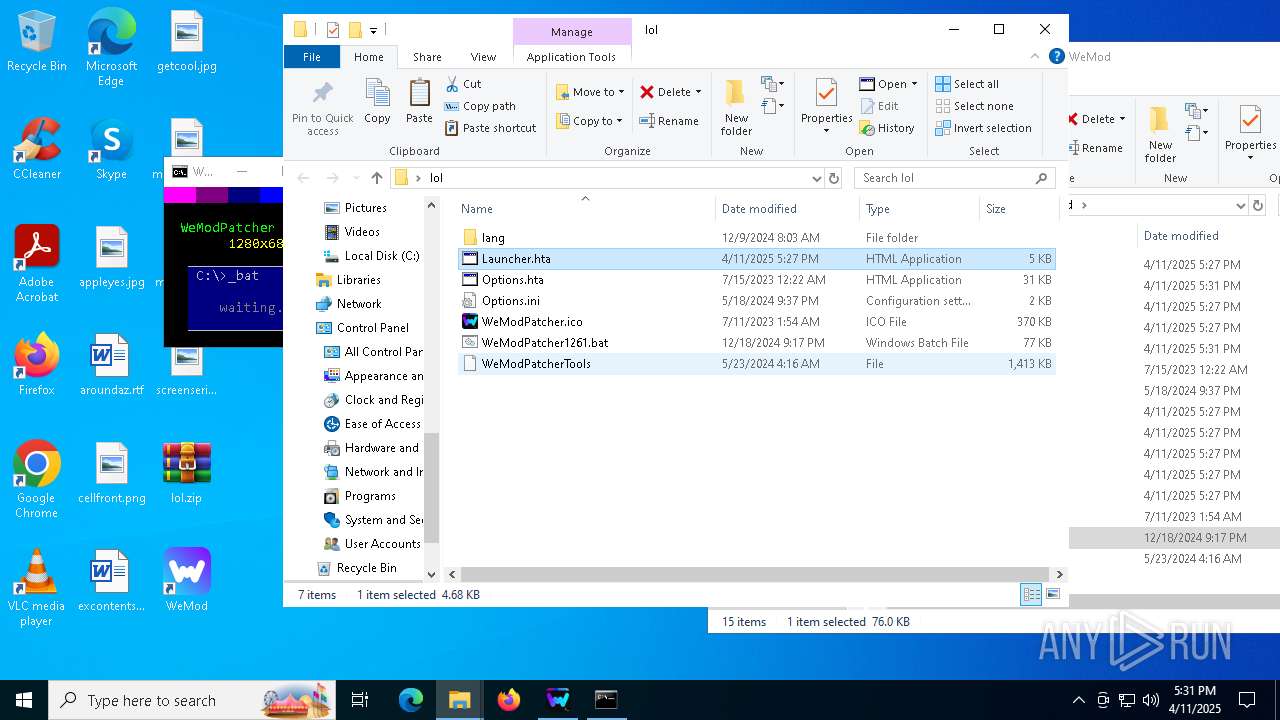
| 132 | mshta.exe "C:\Users\admin\Desktop\lol\Launcher.hta" | C:\Windows\System32\mshta.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 3221225477 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 132 | C:\WINDOWS\system32\cmd.exe /c mshta.exe "C:\Users\admin\Desktop\lol\Launcher.hta" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225477 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 208 | C:\WINDOWS\system32\net1 session | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 300 | chcp 850 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | powershell -Command "(Get-Culture).Name" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | C:\WINDOWS\system32\WerFault.exe -u -p 6980 -s 1860 | C:\Windows\System32\WerFault.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | C:\WINDOWS\system32\cmd.exe /c mshta.exe "C:\Users\admin\Desktop\lol\Launcher.hta" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
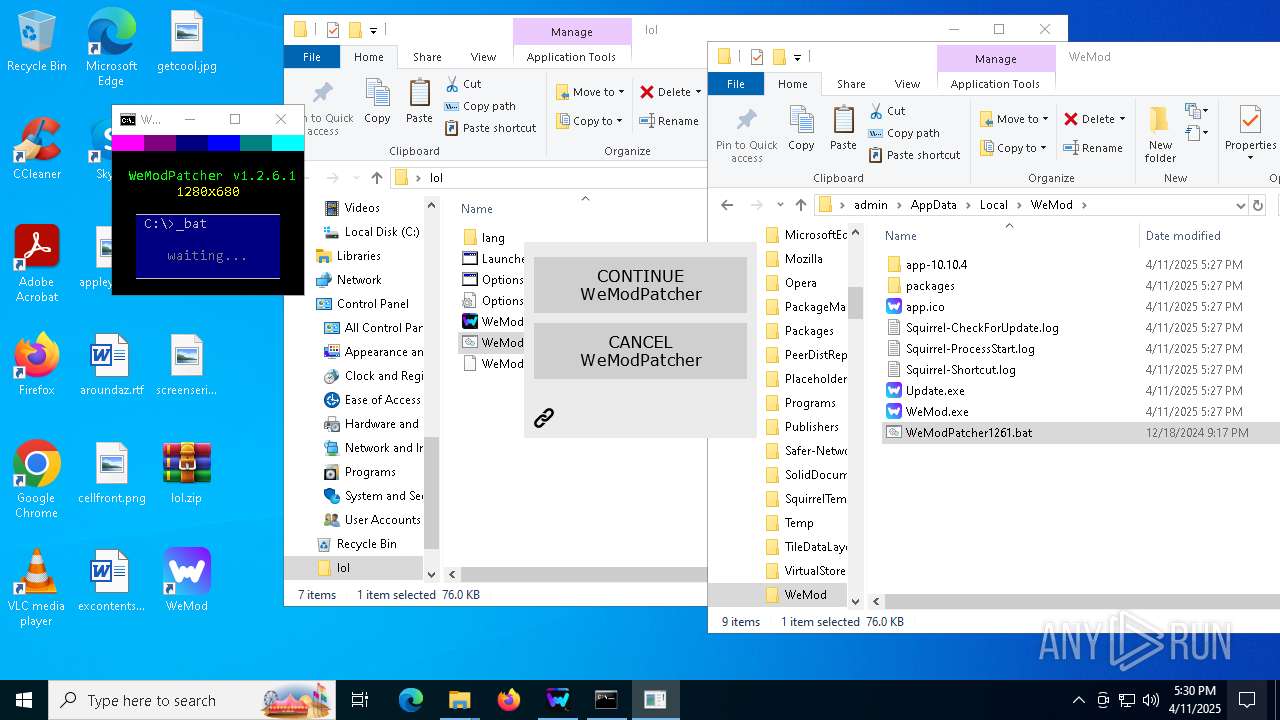
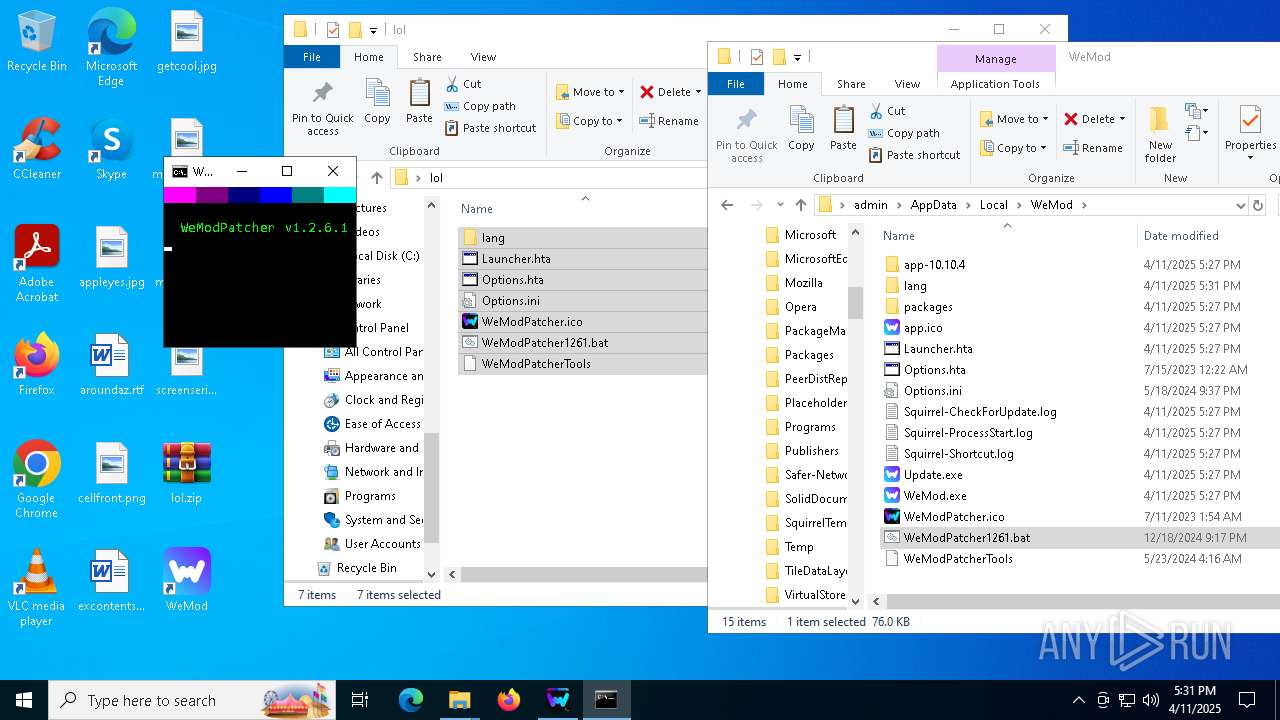
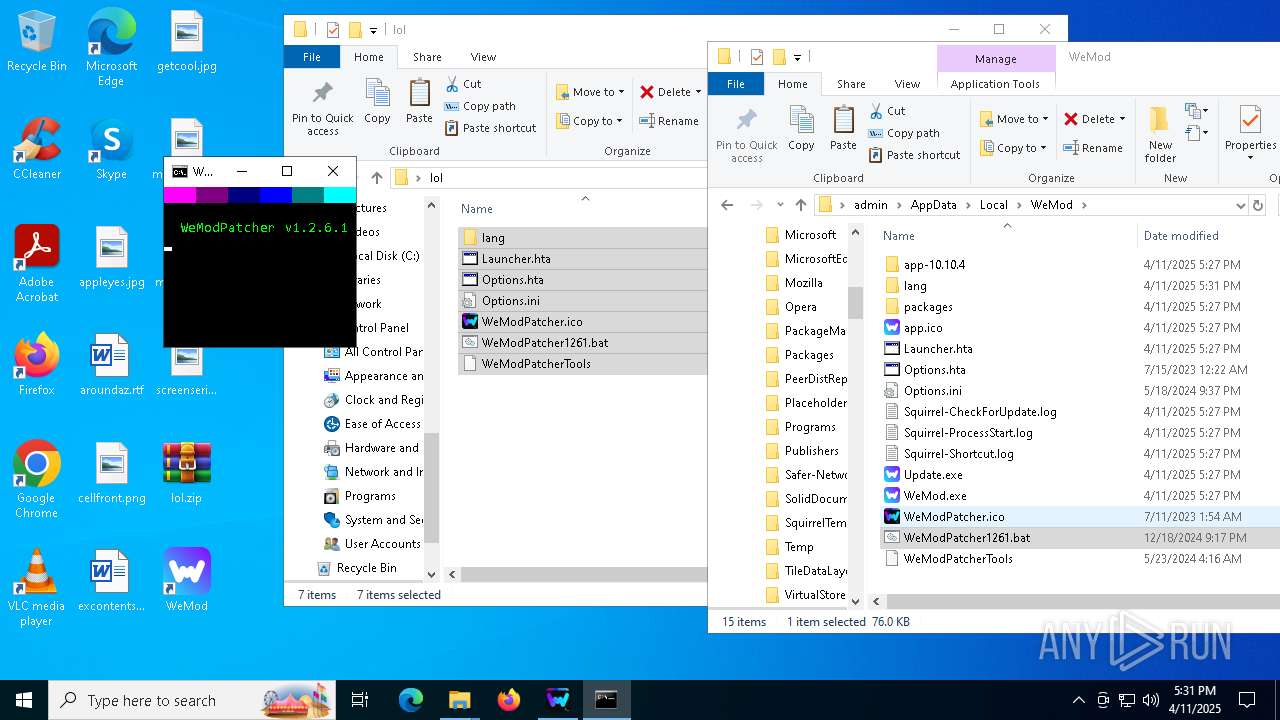
| 668 | powershell -Command "[console]::title='WeModPatcher'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | C:\WINDOWS\system32\cmd.exe /c mshta.exe "C:\Users\admin\Desktop\lol\Launcher.hta" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225477 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
301 799
Read events
301 702
Write events
77
Delete events
20
Modification events
| (PID) Process: | (6036) WeMod-Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6036) WeMod-Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6036) WeMod-Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6036) WeMod-Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\DOMStorage\wemod.com |
| Operation: | write | Name: | NumberOfSubdomains |
Value: 1 | |||
| (PID) Process: | (6036) WeMod-Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\DOMStorage\wemod.com |
| Operation: | write | Name: | Total |
Value: 33 | |||
| (PID) Process: | (6036) WeMod-Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WeMod-Setup_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6036) WeMod-Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WeMod-Setup_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6036) WeMod-Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WeMod-Setup_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6036) WeMod-Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WeMod-Setup_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (6036) WeMod-Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WeMod-Setup_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
26
Suspicious files
229
Text files
189
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6036 | WeMod-Setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:1FBB37F79B317A9A248E7C4CE4F5BAC5 | SHA256:9BF639C595FE335B6F694EE35990BEFD2123F5E07FD1973FF619E3FC88F5F49F | |||
| 6036 | WeMod-Setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C60C0C29522E01E6A22BD2717F20782E_58980020DC8E6BEE10BE87E29E100B20 | binary | |
MD5:9406FCF8D705DB9183E58688D031821E | SHA256:1697E227A1C861FA1BD5356878378EFE2069CC428610786618C9A9FB531178C6 | |||
| 6036 | WeMod-Setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:C5E9EB05785CB4F36F656C99B4122F93 | SHA256:16E2B3105494EF4F55AA5BDD5A34FA9AFB2E18B1127134564E1D477BBA48F58F | |||
| 6036 | WeMod-Setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:1A22A15FC9D2D916D97D420546ECF07B | SHA256:825B32BFD920463144829EC888664C1BA5CEABE3069FA33F3C2A72296DA20561 | |||
| 6036 | WeMod-Setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C60C0C29522E01E6A22BD2717F20782E_58980020DC8E6BEE10BE87E29E100B20 | binary | |
MD5:5D0270A286BA2C2F43A8E469CC6DFB38 | SHA256:250F674B8BDCADD7A0C1E4ECF25386C45E43F957B7C5E7BDBF6A2D939A0919B9 | |||
| 6036 | WeMod-Setup.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\Inter-Thin-0f080c40c6[1].woff | binary | |
MD5:0F080C40C639962E1CAD093AA58192DC | SHA256:E9DA5A64A6A8EB87A2C6D475327F072B5CA25731DF07119F576C10C50AA9554D | |||
| 6036 | WeMod-Setup.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\setup[1].htm | html | |
MD5:C9635EBD61F9F756C94D6DC339E65809 | SHA256:7A2D3E446889D74308252BE79DFE7AAB948FF0BBCCB95E20705971C314DE9668 | |||
| 6036 | WeMod-Setup.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\DOMStore\3QBJAGRD\api.wemod[1].xml | text | |
MD5:C1DDEA3EF6BBEF3E7060A1A9AD89E4C5 | SHA256:B71E4D17274636B97179BA2D97C742735B6510EB54F22893D3A2DAFF2CEB28DB | |||
| 6036 | WeMod-Setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\5080DC7A65DB6A5960ECD874088F3328_6CBA2C06D5985DD95AE59AF8FC7C6220 | binary | |
MD5:4DA92C1DEF937622B39B7FFB3701E782 | SHA256:5244CCBD6DC3CD81848C5806289B9A838D8D3EEC023B75B94D11C8846D327083 | |||
| 6036 | WeMod-Setup.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\Inter-Regular-14d1275c67[1].woff | binary | |
MD5:14D1275C67676CC5D911232D0C890D97 | SHA256:3710E2CE073EC0EB39274DECC63768B52091A27E35F5C28D6ABB7A5FCEF0B7FC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
71
DNS requests
59
Threats
29
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6036 | WeMod-Setup.exe | GET | 200 | 142.250.186.131:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6036 | WeMod-Setup.exe | GET | 200 | 142.250.184.195:80 | http://o.pki.goog/we2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTuMJxAT2trYla0jia%2F5EUSmLrk3QQUdb7Ed66J9kQ3fc%2BxaB8dGuvcNFkCEQCR4hOGkzE8vQlEve7TO1ud | unknown | — | — | whitelisted |
6036 | WeMod-Setup.exe | GET | 200 | 142.250.186.131:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
6036 | WeMod-Setup.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBR64T7ooMQqLLQoy%2BemBUYZQOKh6QQUkK9qOpRaC9iQ6hJWc99DtDoo2ucCEQCO1hzLqfF%2Fr9CBwEs60auM | unknown | — | — | whitelisted |
6036 | WeMod-Setup.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBReAhtobFzTvhaRmVeJ38QUchY9AwQUu69%2BAj36pvE8hI6t7jiY7NkyMtQCECsuburZdTZsFIpu26N8jAc%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5048 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5048 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6036 | WeMod-Setup.exe | 104.22.43.75:443 | api.wemod.com | CLOUDFLARENET | — | whitelisted |
6036 | WeMod-Setup.exe | 142.250.186.131:80 | c.pki.goog | GOOGLE | US | whitelisted |
6036 | WeMod-Setup.exe | 216.58.206.78:443 | www.google-analytics.com | GOOGLE | US | whitelisted |
6036 | WeMod-Setup.exe | 52.34.225.134:443 | api2.amplitude.com | AMAZON-02 | US | whitelisted |
6036 | WeMod-Setup.exe | 142.250.184.195:80 | o.pki.goog | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
api.wemod.com |
| whitelisted |
c.pki.goog |
| whitelisted |
www.google-analytics.com |
| whitelisted |
api2.amplitude.com |
| whitelisted |
o.pki.goog |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
7144 | WeMod.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
7144 | WeMod.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
7144 | WeMod.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
7144 | WeMod.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
7144 | WeMod.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
7144 | WeMod.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
7144 | WeMod.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
7144 | WeMod.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
7144 | WeMod.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |