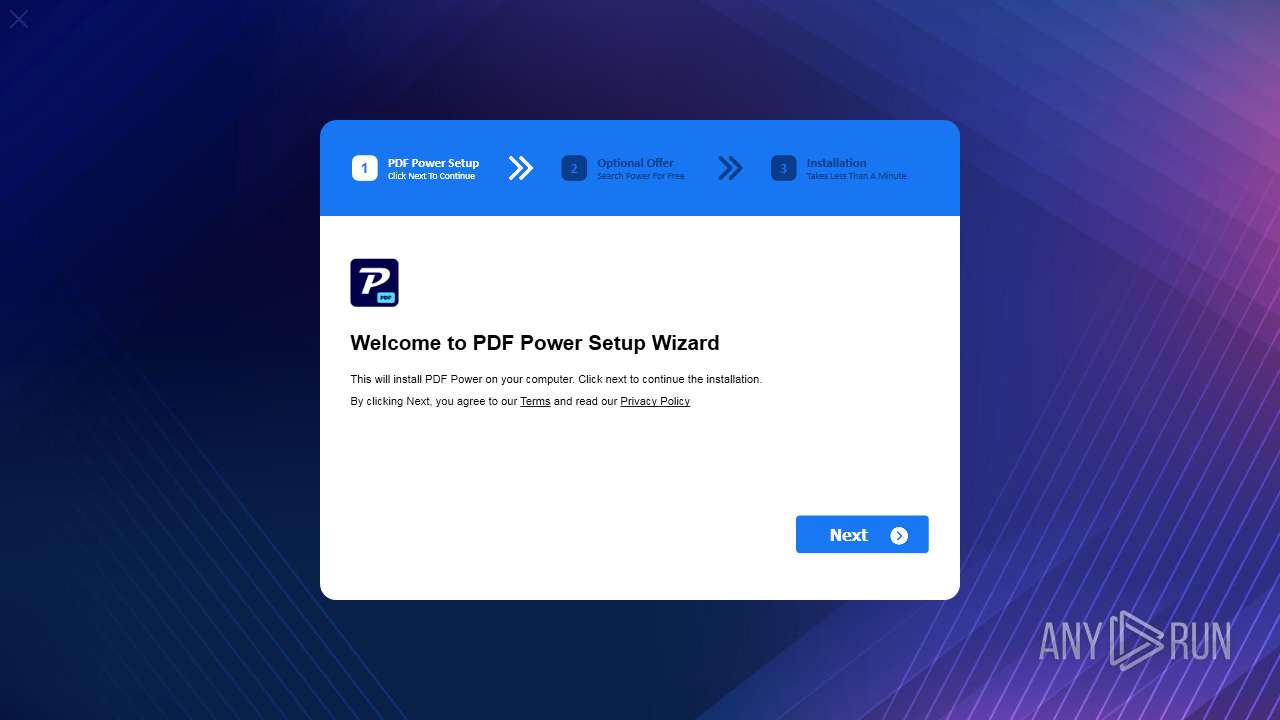
| File name: | PDFpower.exe |
| Full analysis: | https://app.any.run/tasks/786358bc-603b-400f-8998-2505ea82e250 |
| Verdict: | Malicious activity |
| Analysis date: | November 15, 2023, 14:42:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | FB396E6E8B08308F8D12F2776EDA4C85 |
| SHA1: | 69D56902CA69FB3486221301B76C67DCBD2D6BF6 |
| SHA256: | 1BD00252035EADAE62C03A8396B5B6E3C355082359714D8F02ABD9770CB2EF7E |
| SSDEEP: | 24576:sW9Ytb3SRxqO8m657w6ZBLmkitKqBCjC0PDgM5A6F:sWWtbCJVV1BCjBB |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads settings of System Certificates
- PDFpower.exe (PID: 3308)
Reads the Internet Settings
- PDFpower.exe (PID: 3308)
INFO
Reads the computer name
- PDFpower.exe (PID: 3308)
- wmpnscfg.exe (PID: 3864)
Checks supported languages
- PDFpower.exe (PID: 3308)
- wmpnscfg.exe (PID: 3864)
Reads the machine GUID from the registry
- PDFpower.exe (PID: 3308)
- wmpnscfg.exe (PID: 3864)
Reads Environment values
- PDFpower.exe (PID: 3308)
Create files in a temporary directory
- PDFpower.exe (PID: 3308)
Manual execution by a user
- wmpnscfg.exe (PID: 3864)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (49.4) |
|---|---|---|
| .scr | | | Windows screen saver (23.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (11.7) |
| .exe | | | Win32 Executable (generic) (8) |
| .exe | | | Generic Win/DOS Executable (3.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2041:05:08 16:54:26+02:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 1055232 |
| InitializedDataSize: | 19456 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x10391e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.0.0.0 |
| ProductVersionNumber: | 3.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | PdfPower |
| FileVersion: | 3.0.0.0 |
| InternalName: | PdfPowerB2C.exe |
| LegalCopyright: | Copyright © 2022 |
| LegalTrademarks: | - |
| OriginalFileName: | PdfPowerB2C.exe |
| ProductName: | PdfPower |
| ProductVersion: | 3.0.0.0 |
| AssemblyVersion: | 3.0.0.0 |
Total processes
40
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3124 | "C:\Windows\SYSTEM32\WISPTIS.EXE" /ManualLaunch; | C:\Windows\System32\wisptis.exe | — | PDFpower.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Pen and Touch Input Component Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3308 | "C:\Users\admin\AppData\Local\Temp\PDFpower.exe" | C:\Users\admin\AppData\Local\Temp\PDFpower.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: PdfPower Exit code: 0 Version: 3.0.0.0 Modules
| |||||||||||||||
| 3528 | "C:\Windows\SYSTEM32\WISPTIS.EXE" /ManualLaunch; | C:\Windows\System32\wisptis.exe | PDFpower.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Pen and Touch Input Component Exit code: 24 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3864 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 014
Read events
4 989
Write events
22
Delete events
3
Modification events
| (PID) Process: | (3308) PDFpower.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: Explorer.EXE | |||
| (PID) Process: | (3308) PDFpower.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3308) PDFpower.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3308) PDFpower.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3308) PDFpower.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3528) wisptis.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: PDFpower.exe | |||
| (PID) Process: | (3308) PDFpower.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3864) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{7543228E-AD57-433D-8C0C-ACF60DFC9CAE}\{6A0BB000-918F-4AEF-A491-6020B1DFB752} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3864) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{7543228E-AD57-433D-8C0C-ACF60DFC9CAE} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3864) wmpnscfg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{73B3FDD6-644E-4846-AF5A-9C23B8416E40} |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
0
Suspicious files
4
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3308 | PDFpower.exe | C:\Users\admin\AppData\Local\Temp\PdfPowerB2C\installing.gif | image | |
MD5:375DA4DEA8747071B487386DA14B1264 | SHA256:B891A5DFE676B829D5A1B68063765EFE3B7CA842D69315EB25DD97F47A02080A | |||
| 3308 | PDFpower.exe | C:\Users\admin\AppData\Local\Temp\Tar7F38.tmp | binary | |
MD5:9441737383D21192400ECA82FDA910EC | SHA256:BC3A6E84E41FAEB57E7C21AA3B60C2A64777107009727C5B7C0ED8FE658909E5 | |||
| 3308 | PDFpower.exe | C:\Users\admin\AppData\Local\Temp\Cab7F37.tmp | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 3308 | PDFpower.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 3308 | PDFpower.exe | C:\Users\admin\AppData\Local\Temp\PdfPowerB2C\favicon.ico | image | |
MD5:68814A062FD60A524FFC92E3132B924C | SHA256:49CFC761F6EF30F7FF6276AF7A7093026D8985090200362858E1E77336ED2448 | |||
| 3308 | PDFpower.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:15305A8364E194EEDEDA39305CDA1522 | SHA256:52BC51CAFC81035503116FE94A5B0F9722BC355F7C35C6567B6C1C7E65CA05B9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
13
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3308 | PDFpower.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?bb160f6ba035d51f | unknown | compressed | 61.6 Kb | unknown |
3308 | PDFpower.exe | GET | 301 | 5.161.217.107:80 | http://www.bl.searchpoweronline.com/interpolate?emid=178BFBFF000506E34d5130303030203120202020202020202020202012A9866C77DE&appId=1636018850881182&string_interpolation=GET_SIGNATURE | unknown | text | 17 b | unknown |
3308 | PDFpower.exe | GET | 301 | 5.161.217.107:80 | http://www.bl.searchpoweronline.com/interpolate?emid=178BFBFF000506E34d5130303030203120202020202020202020202012A9866C77DE&appId=1636018850881182&string_interpolation=GET_BRAND_NAME | unknown | text | 17 b | unknown |
3308 | PDFpower.exe | GET | 301 | 5.161.217.107:80 | http://www.bl.searchpoweronline.com/v4/install/first_time?BwQYBwYBGj4CEFIPEVBfFwpfQ0wKRw5eWVVTFwtDTFBaFUJaQwdfTF5eR1dYEFdIFREbKwYKSVBdR1leRVlTQV9WTFBaTF1IEQwCEFJfQ1kpMi0oMlFbRFpeQiRYQAtbRVJbR19dRFJbRl9dRVNbRl9cRFNbRl9cRFNbRl9cRFNbRl9cRFBZNVZWQlcoQ1gqMUcCGhwaFQ0HKxkLBhICGwFTRUcCEAoAAAgfDVJIBwgMSUkKGxYFGAAPED4JBgAZBwQZSQoKEwQ0FwccGwwOUgAdKxcOBhwHGw9WQkFfWlZdRF5IBlxaQ1peQVlbQV9d | unknown | text | 17 b | unknown |
3308 | PDFpower.exe | GET | 301 | 5.161.217.107:80 | http://www.bl.searchpoweronline.com/interpolate?emid=178BFBFF000506E34d5130303030203120202020202020202020202012A9866C77DE&appId=1636018850881182&string_interpolation=GET_OSOU | unknown | text | 17 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3308 | PDFpower.exe | 142.250.186.78:443 | www.google-analytics.com | GOOGLE | US | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3308 | PDFpower.exe | 5.161.217.107:443 | bl.searchpoweronline.com | Hetzner Online GmbH | US | unknown |
3308 | PDFpower.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3308 | PDFpower.exe | 5.161.217.107:80 | bl.searchpoweronline.com | Hetzner Online GmbH | US | unknown |
868 | svchost.exe | 95.101.148.135:80 | — | Akamai International B.V. | NL | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
868 | svchost.exe | 88.221.124.138:80 | armmf.adobe.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google-analytics.com |
| whitelisted |
bl.searchpoweronline.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
www.bl.searchpoweronline.com |
| unknown |
armmf.adobe.com |
| whitelisted |
dns.msftncsi.com |
| shared |
Threats
Process | Message |
|---|---|
PDFpower.exe | MainWindow Started
|
PDFpower.exe | FirstScreen Started
|
PDFpower.exe | GA TRACK START - IMP_FTA_PPW
|
PDFpower.exe | Is succeed to execute machine code? True; CPUId = 178BFBFF000506E3
|
PDFpower.exe | GetMacAddress :: uuid = 4818d70c-83c5-11ee-a826-12a9866c77de
|
PDFpower.exe | Mac Adress after adjusting = 12A9866C77DE
|
PDFpower.exe | Mac Adress before adjusting = 12A9866C77DE
|
PDFpower.exe | FAILED to retrieve HddId(obviously admin rights) by HDSerialNumber.GetSerialNumber(0), ex = Access is denied
|
PDFpower.exe | Testing HddId by GetHDD_OLD, value = 4d51303030302031202020202020202020202020
|
PDFpower.exe | Is succeed to get hdd attributes? True; HddId = 4d51303030302031202020202020202020202020
|