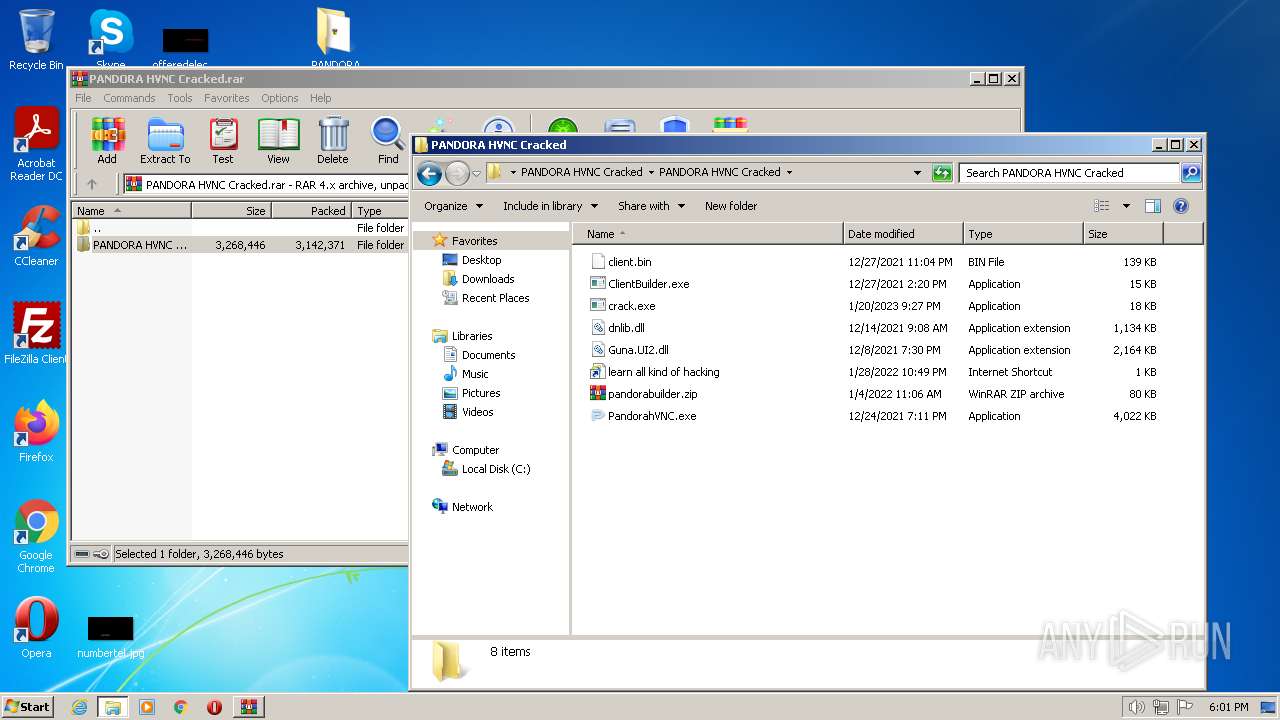
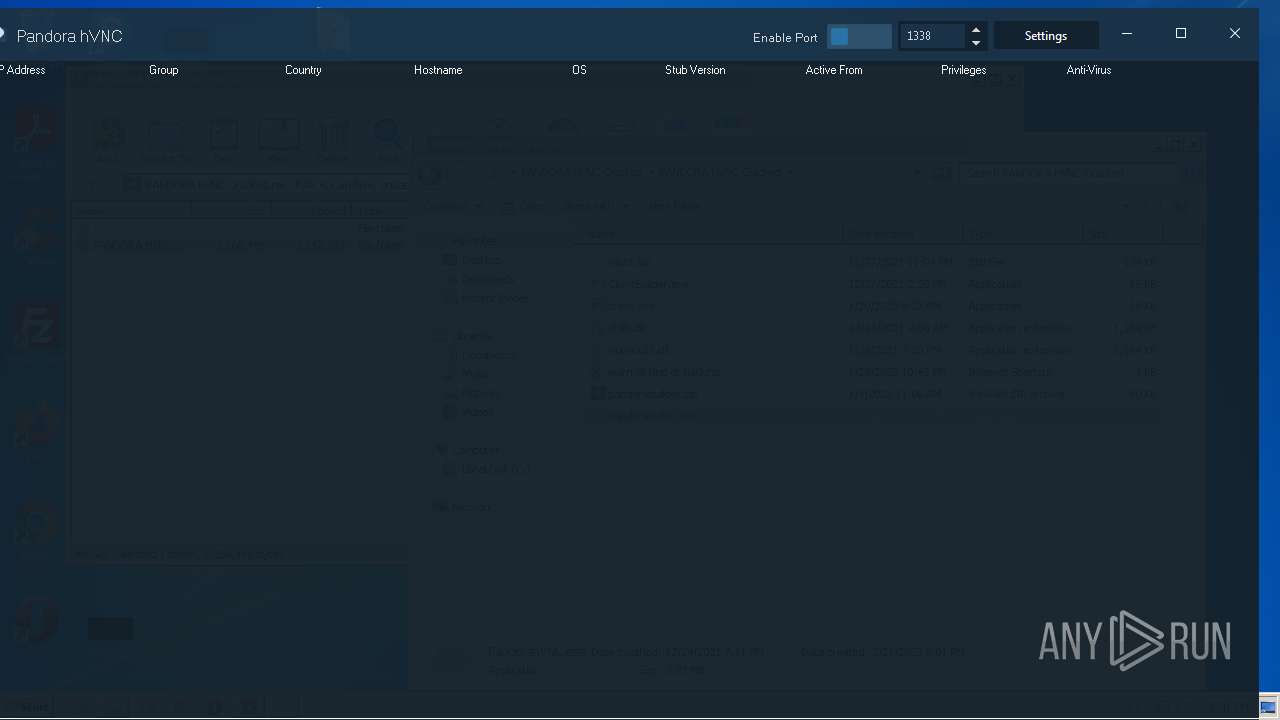
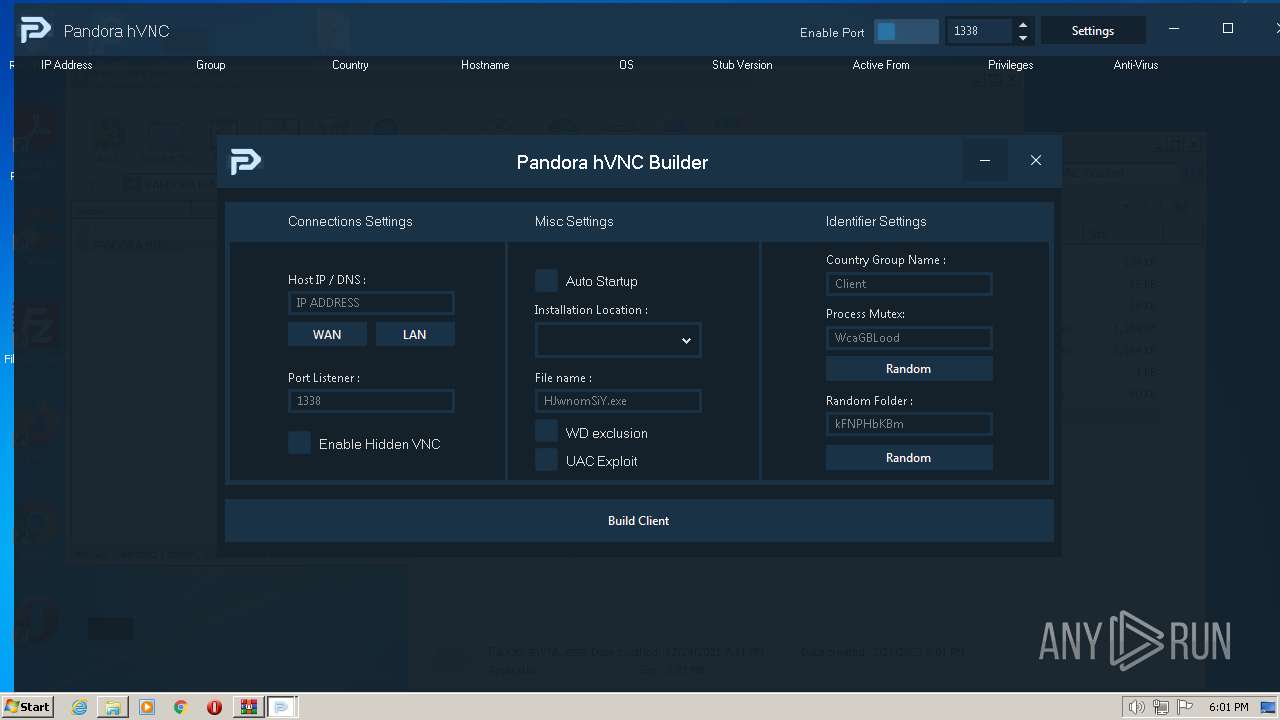
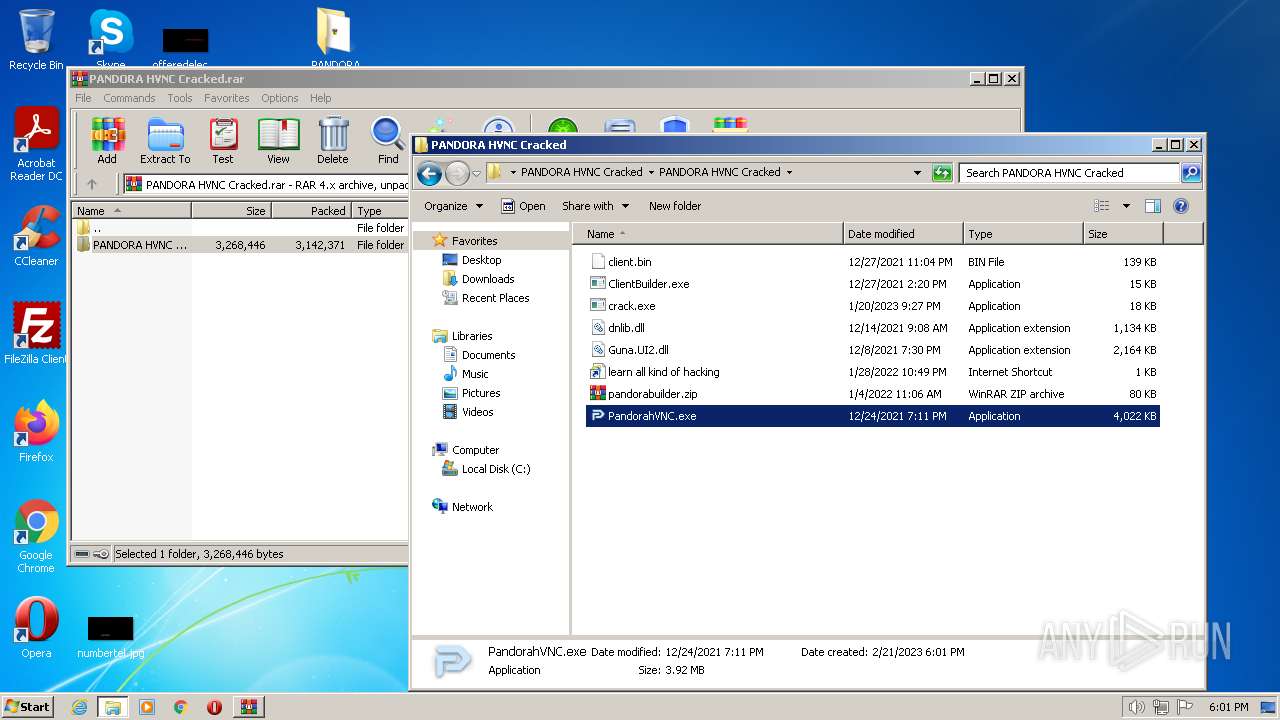
| File name: | PANDORA HVNC Cracked.rar |
| Full analysis: | https://app.any.run/tasks/015c0cca-993d-405f-849e-5896f9787c10 |
| Verdict: | Malicious activity |
| Analysis date: | February 21, 2023, 18:01:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32, flags: RecoveryRecordPresent |
| MD5: | 0E034C20B69CE88B1C426B68A4B74921 |
| SHA1: | 656B9C48B2B5C732FAF19D93147311DE24B6EB35 |
| SHA256: | 1B89A30FC28488683B9C1CB8AF0C2E574EFD8405B38F1DD26727C1EF04D2097A |
| SSDEEP: | 98304:IryNpLb32Kt1uLKv1T4ej0H+8Yc7GyZFVh:1pnGxK+g0Hr7Gyv |
MALICIOUS
Application was dropped or rewritten from another process
- PandorahVNC.exe (PID: 3720)
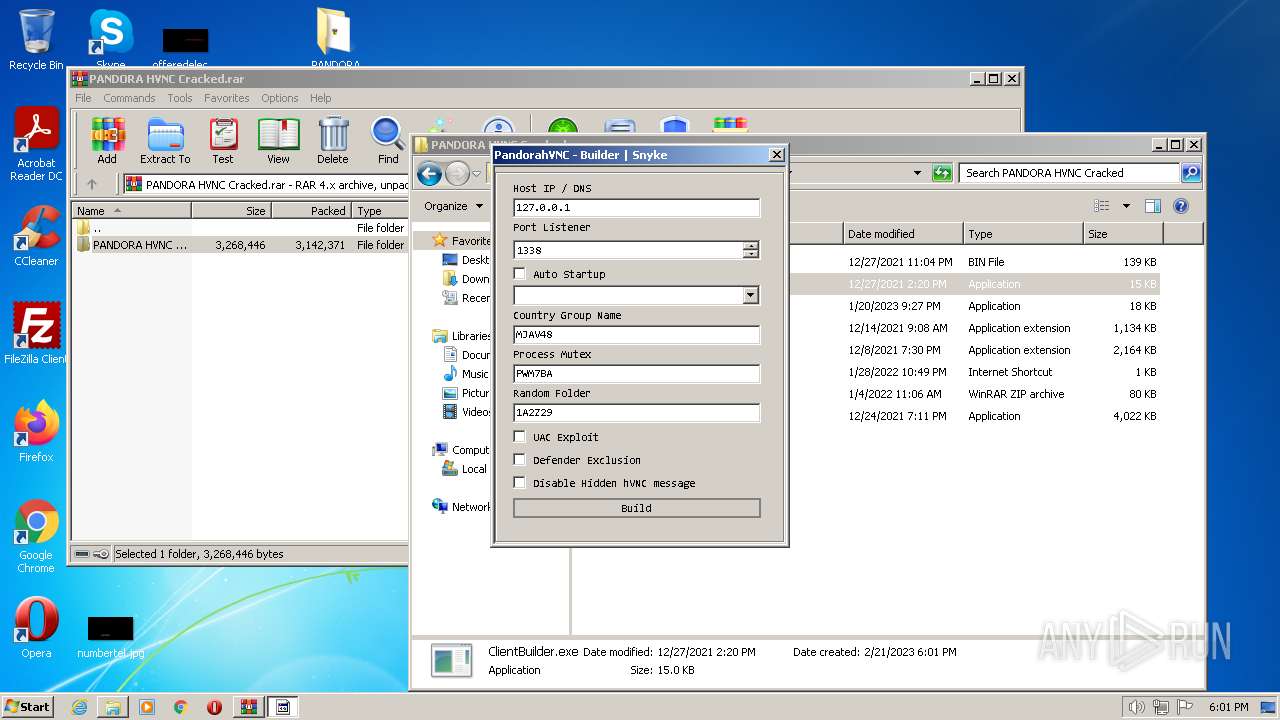
- ClientBuilder.exe (PID: 2836)
Drops the executable file immediately after the start
- PandorahVNC.exe (PID: 3720)
SUSPICIOUS
Executable content was dropped or overwritten
- PandorahVNC.exe (PID: 3720)
INFO
Manual execution by a user
- WinRAR.exe (PID: 3716)
- PandorahVNC.exe (PID: 3720)
- ClientBuilder.exe (PID: 2836)
Checks supported languages
- PandorahVNC.exe (PID: 3720)
- ClientBuilder.exe (PID: 2836)
Reads the computer name
- PandorahVNC.exe (PID: 3720)
- ClientBuilder.exe (PID: 2836)
Reads the machine GUID from the registry
- PandorahVNC.exe (PID: 3720)
- ClientBuilder.exe (PID: 2836)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3492)
- WinRAR.exe (PID: 3716)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3716)
- WinRAR.exe (PID: 3492)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3492)
- WinRAR.exe (PID: 3716)
- PandorahVNC.exe (PID: 3720)
Create files in a temporary directory
- PandorahVNC.exe (PID: 3720)
The process checks LSA protection
- PandorahVNC.exe (PID: 3720)
- ClientBuilder.exe (PID: 2836)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| ArchivedFileName: | PANDORA HVNC Cracked\PANDORA HVNC Cracked.exe |
|---|---|
| PackingMethod: | Normal |
| ModifyDate: | 2023:02:15 02:30:20 |
| OperatingSystem: | Win32 |
| UncompressedSize: | 3268446 |
| CompressedSize: | 3142442 |
Total processes
43
Monitored processes
5
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2088 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe3_ Global\UsGthrCtrlFltPipeMssGthrPipe3 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
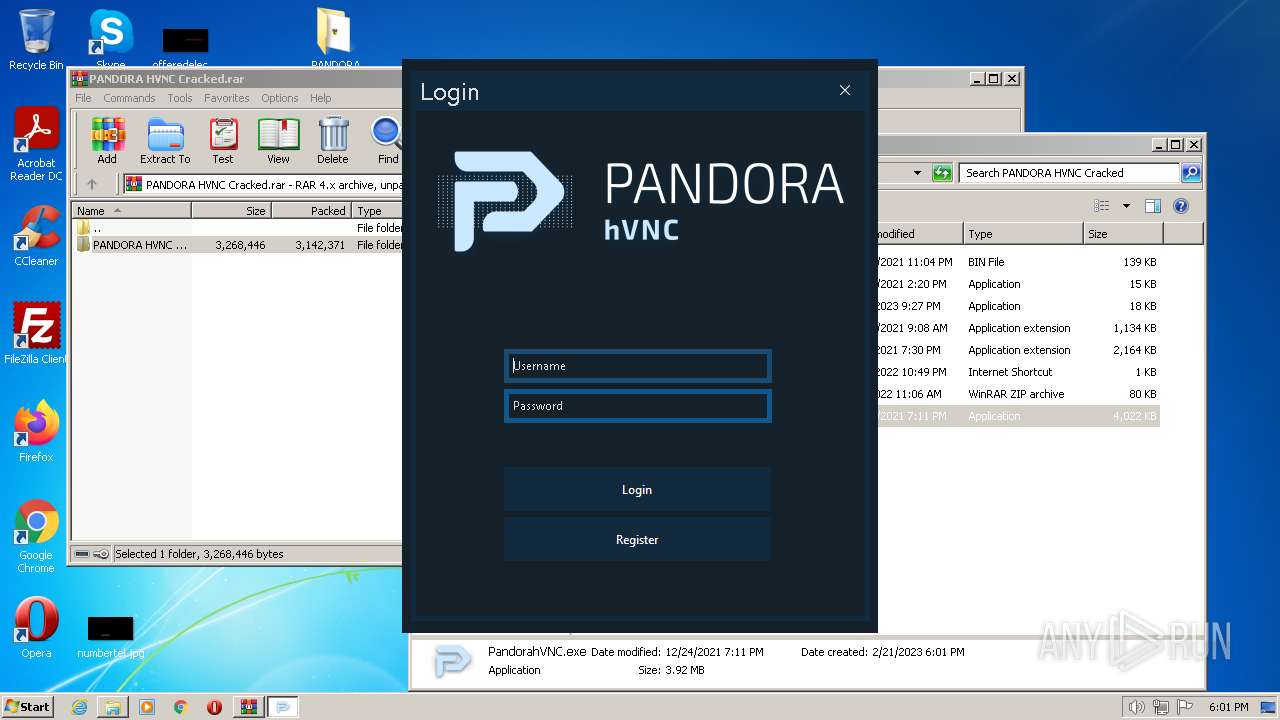
| 2836 | "C:\Users\admin\Desktop\PANDORA HVNC Cracked\PANDORA HVNC Cracked\ClientBuilder.exe" | C:\Users\admin\Desktop\PANDORA HVNC Cracked\PANDORA HVNC Cracked\ClientBuilder.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: ClientBuilder Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3492 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\PANDORA HVNC Cracked.rar" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3716 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\PANDORA HVNC Cracked\PANDORA HVNC Cracked.exe" "C:\Users\admin\Desktop\PANDORA HVNC Cracked\PANDORA HVNC Cracked\" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3720 | "C:\Users\admin\Desktop\PANDORA HVNC Cracked\PANDORA HVNC Cracked\PandorahVNC.exe" | C:\Users\admin\Desktop\PANDORA HVNC Cracked\PANDORA HVNC Cracked\PandorahVNC.exe | Explorer.EXE | ||||||||||||
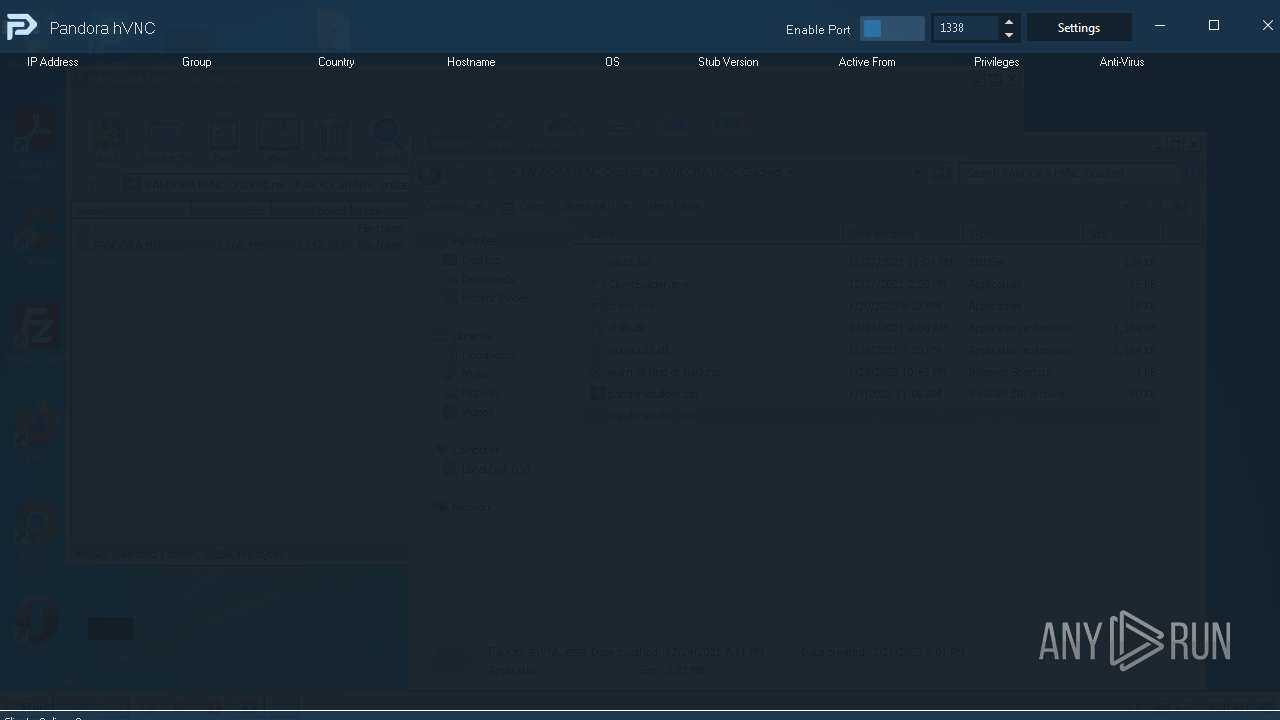
User: admin Integrity Level: MEDIUM Description: Pandora hVNC Exit code: 0 Version: 1.0.1 Modules
| |||||||||||||||
Total events
4 228
Read events
4 182
Write events
46
Delete events
0
Modification events
| (PID) Process: | (3492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3492) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\PANDORA HVNC Cracked.rar | |||
| (PID) Process: | (3492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
16
Suspicious files
2
Text files
0
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3716 | WinRAR.exe | C:\Users\admin\Desktop\PANDORA HVNC Cracked\PANDORA HVNC Cracked\Guna.UI2.dll | executable | |
MD5:D65FD6DBBD3C9AC74139AEAEDC4A5816 | SHA256:84199A22C8669A39800272C3DA0D969EC4E8D77D67B9D324CA049953A5042C71 | |||
| 3716 | WinRAR.exe | C:\Users\admin\Desktop\PANDORA HVNC Cracked\PANDORA HVNC Cracked\client.bin | executable | |
MD5:60B39085C266F364C6B1269AB8FE79F5 | SHA256:AD45703EBDFD43596469416BC9E24374D77A6F361057A31B6CC659789522DA75 | |||
| 3716 | WinRAR.exe | C:\Users\admin\Desktop\PANDORA HVNC Cracked\PANDORA HVNC Cracked\learn all kind of hacking.url | url | |
MD5:7ADE4A739CBD8F44D0EF52A2F1BC6E7B | SHA256:CC7649ED53C65E4851ACE414529564FE16801BB2BED4CB15588BFD6B4AC13616 | |||
| 3716 | WinRAR.exe | C:\Users\admin\Desktop\PANDORA HVNC Cracked\PANDORA HVNC Cracked\pandorabuilder.zip | compressed | |
MD5:D086F5DE761BCABE7CEEC28B6F2BEABA | SHA256:303F76F0CFE8D7C356C738ABFF2861AD9F021007CAEBF7918FC35985132AB80B | |||
| 3716 | WinRAR.exe | C:\Users\admin\Desktop\PANDORA HVNC Cracked\PANDORA HVNC Cracked\dnlib.dll | executable | |
MD5:E517EAEABD955F1E0F83ED04A0E6DD86 | SHA256:D04369E2FAFABB36FDC31FC63B9A4BFD2BBA577A203EE8180F9B084D9B344676 | |||
| 3716 | WinRAR.exe | C:\Users\admin\Desktop\PANDORA HVNC Cracked\PANDORA HVNC Cracked\ClientBuilder.exe | executable | |
MD5:77D61A2FC9E55E0CDB6F52CB91005A86 | SHA256:FB82B4746CD8878EC6CC3A934F11E8192B381A6B3A18AAE57323DD950D9F91E5 | |||
| 3716 | WinRAR.exe | C:\Users\admin\Desktop\PANDORA HVNC Cracked\PANDORA HVNC Cracked\PandorahVNC.exe | executable | |
MD5:39EF11E7673738D7DAB6B7396044D003 | SHA256:ECED18F42CC7A54E40444F42B4EE3A200022837B66235E5239CEBE0AB96A2740 | |||
| 3720 | PandorahVNC.exe | C:\Users\admin\AppData\Local\Temp\1a5fdae6-8f46-4b8b-a738-d6572f690d43\AgileDotNetRT.dll | executable | |
MD5:14FF402962AD21B78AE0B4C43CD1F194 | SHA256:FB9646CB956945BDC503E69645F6B5316D3826B780D3C36738D6B944E884D15B | |||
| 3716 | WinRAR.exe | C:\Users\admin\Desktop\PANDORA HVNC Cracked\PANDORA HVNC Cracked\crack.exe | executable | |
MD5:163BDC6F6240D733ABF9083AC7E4ECED | SHA256:CB184F8C1AEB967C72B3FF6093BA3E275E3BDEC4B40DE4D570E92BCEAACED1E9 | |||
| 3492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3492.45402\PANDORA HVNC Cracked\PANDORA HVNC Cracked.exe | executable | |
MD5:C6A702F28372143712668B5ED78A0977 | SHA256:9BFD2E4DA54AD6962A88F2322A203A403A5F42AFA463C04CFDE24DFB922A042A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report