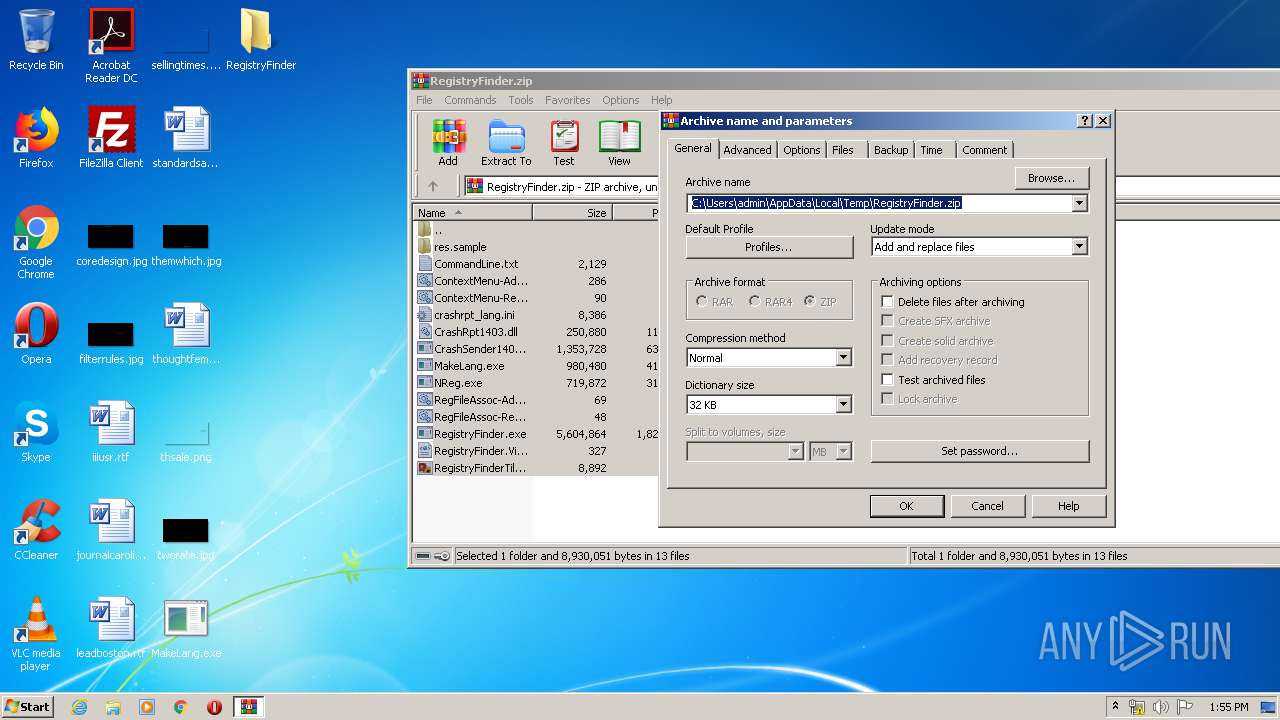
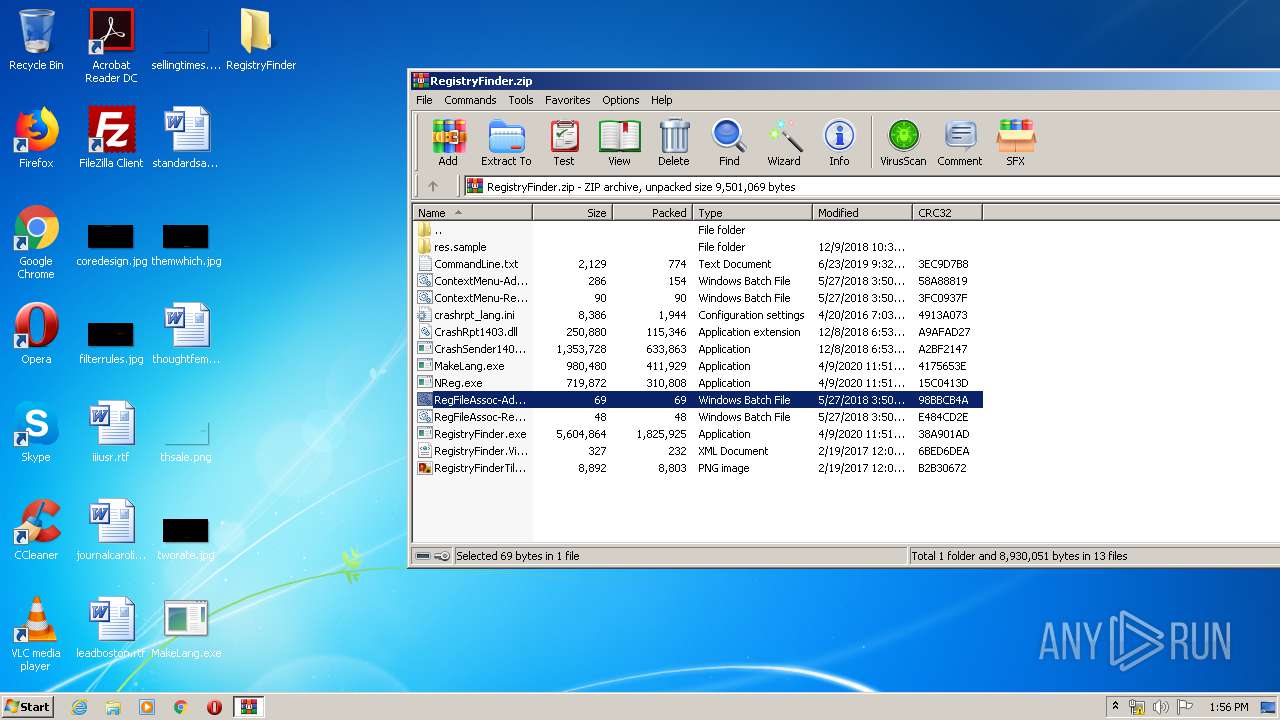
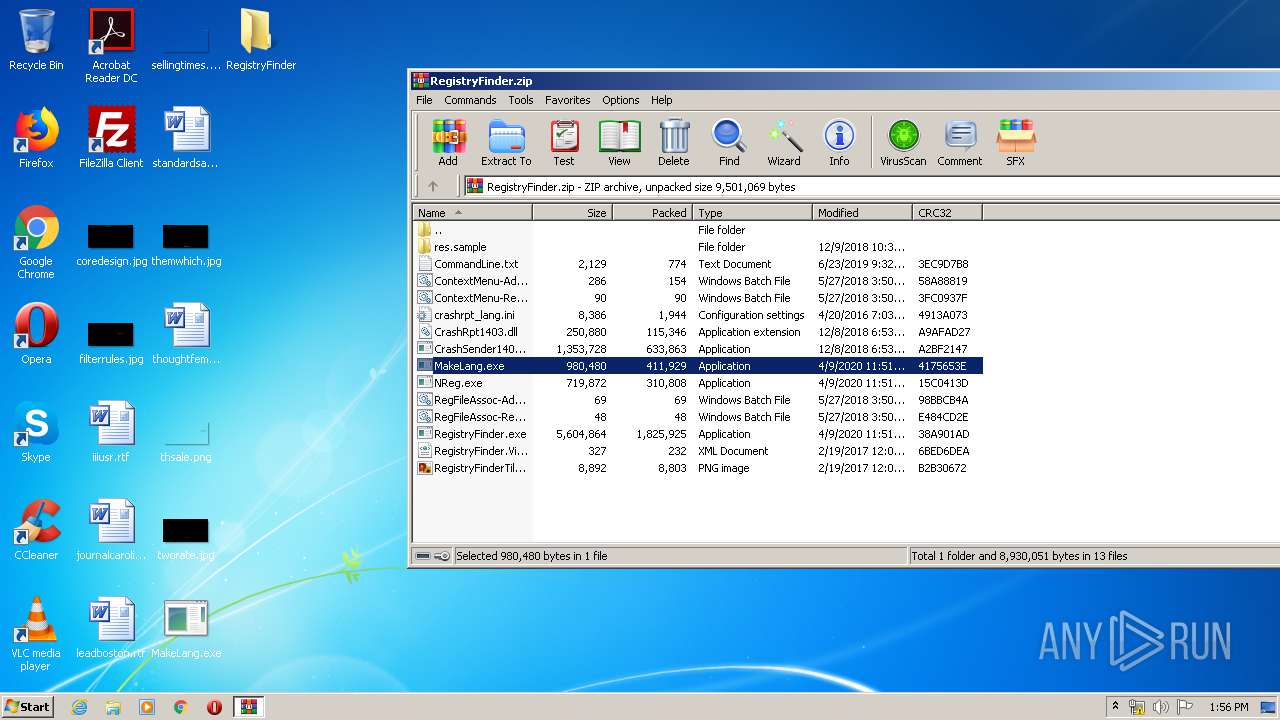
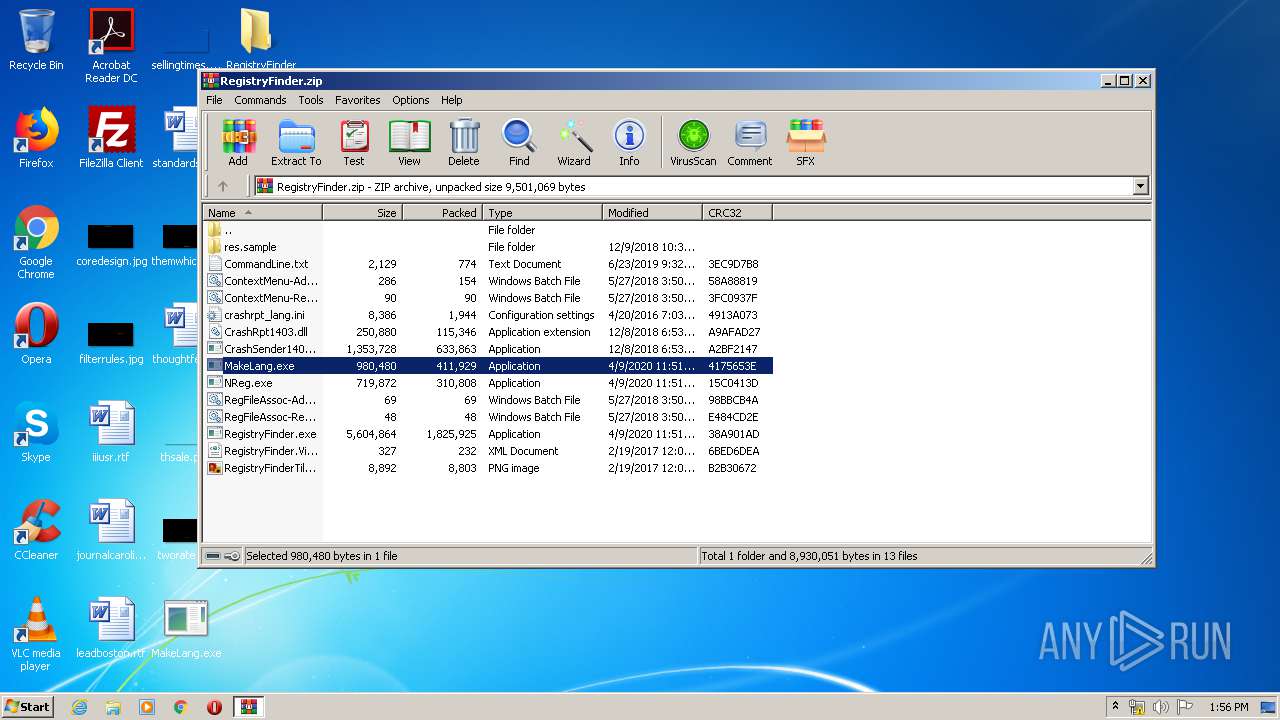
| File name: | RegistryFinder.zip |
| Full analysis: | https://app.any.run/tasks/148593d8-9a7a-421a-8731-d69e6a0e745b |
| Verdict: | Malicious activity |
| Analysis date: | April 21, 2020, 12:54:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 9A9CBC2219420CF3B4D560163033C6FE |
| SHA1: | 0AEC1829B940563C16C6D1F0144E56C70661C378 |
| SHA256: | 1B893297CA2A733FD11A555897422B5885A9BD8EF37959CD562608F1FB172B46 |
| SSDEEP: | 98304:w+ogaqGuObCuyQyhedvpEuVxWTeyKA3bq18wHwcG:w+r3Gu8CFhovquVQTe23bqvwcG |
MALICIOUS
Application was dropped or rewritten from another process
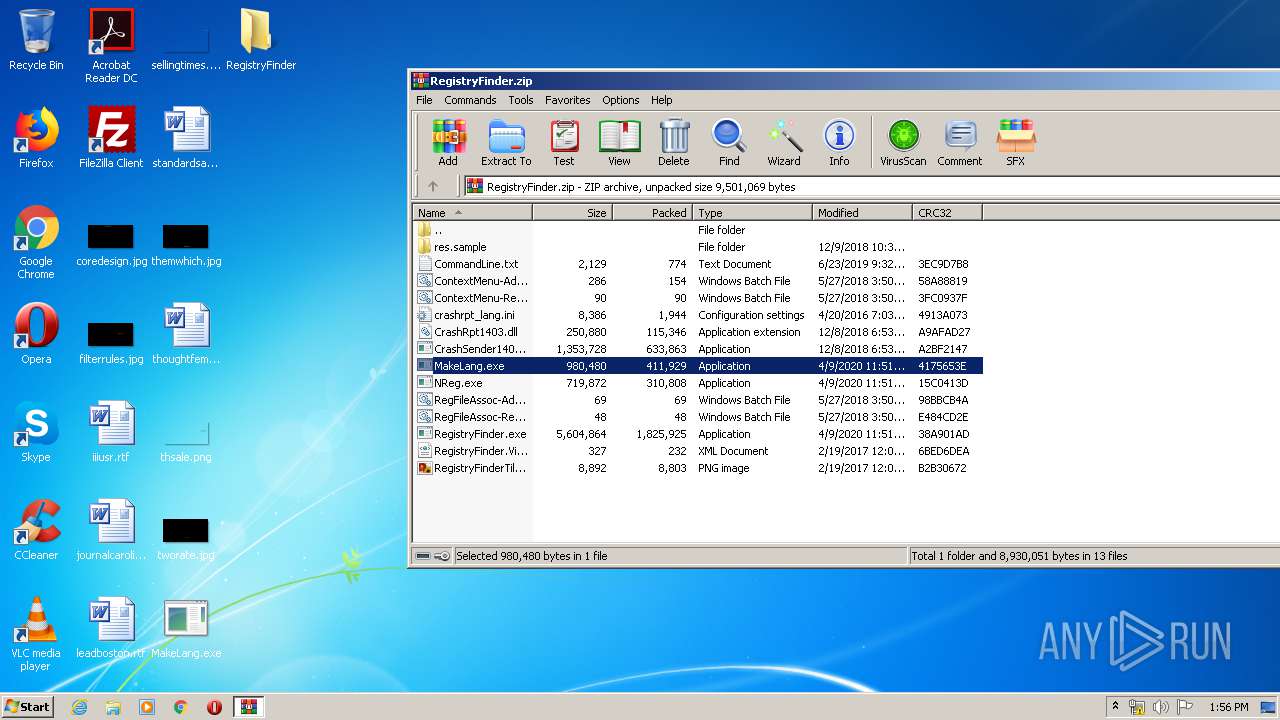
- MakeLang.exe (PID: 3212)
- MakeLang.exe (PID: 1016)
- MakeLang.exe (PID: 2440)
Actions looks like stealing of personal data
- WinRAR.exe (PID: 332)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 332)
INFO
Manual execution by user
- MakeLang.exe (PID: 1016)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:06:23 11:32:17 |
| ZipCRC: | 0x3ec9d7b8 |
| ZipCompressedSize: | 774 |
| ZipUncompressedSize: | 2129 |
| ZipFileName: | CommandLine.txt |
Total processes
45
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 332 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\RegistryFinder.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1016 | "C:\Users\admin\Desktop\MakeLang.exe" | C:\Users\admin\Desktop\MakeLang.exe | — | explorer.exe | |||||||||||
User: admin Company: Sergey Filippov Integrity Level: MEDIUM Description: Localization helper utility. Creates language ini and dll files. Exit code: 0 Version: 2.44.0.0 Modules
| |||||||||||||||
| 2440 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa332.9378\MakeLang.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa332.9378\MakeLang.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Sergey Filippov Integrity Level: MEDIUM Description: Localization helper utility. Creates language ini and dll files. Exit code: 0 Version: 2.44.0.0 Modules
| |||||||||||||||
| 3212 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa332.2220\MakeLang.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa332.2220\MakeLang.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Sergey Filippov Integrity Level: MEDIUM Description: Localization helper utility. Creates language ini and dll files. Exit code: 0 Version: 2.44.0.0 Modules
| |||||||||||||||
Total events
714
Read events
622
Write events
91
Delete events
1
Modification events
| (PID) Process: | (332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (332) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\RegistryFinder.zip | |||
| (PID) Process: | (332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (332) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\acppage.dll,-6002 |
Value: Windows Batch File | |||
| (PID) Process: | (332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
11
Suspicious files
0
Text files
52
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa332.2220\CrashSender1403.exe | executable | |
MD5:— | SHA256:— | |||
| 332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa332.2220\NReg.exe | executable | |
MD5:— | SHA256:— | |||
| 332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa332.2220\MakeLang.exe | executable | |
MD5:— | SHA256:— | |||
| 332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa332.2220\ContextMenu-Add.bat | text | |
MD5:CDBFE75CF2ABE91E574A986FF562AE31 | SHA256:48100ECEEA29C6608B975A55CDEA38B1C849E4DDB5B1A7A17264D45285569487 | |||
| 332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa332.2220\CrashRpt1403.dll | executable | |
MD5:— | SHA256:— | |||
| 332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa332.2220\crashrpt_lang.ini | text | |
MD5:0B46F5E01A1EDCF2AD3C85134CBB8659 | SHA256:9C2C1319BA3014EF54196C9BEC89BC8AD39A92F35DAAC3089ADEE051B73387AB | |||
| 332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa332.2220\ContextMenu-Remove.bat | text | |
MD5:BF4EB57A26E7D736EC79F01D1E07338B | SHA256:A512E2969623A67EAD9D2625824280F01534899E308D5C032AF751508901D232 | |||
| 332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa332.2220\res.sample\!readme.txt | text | |
MD5:67777E1BBA5D3352CF113271981D69BF | SHA256:914F4885DCCD0A3FDE5BC9C104D218D802CDE1DEACAB12E95759C1D218704026 | |||
| 332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa332.2220\RegFileAssoc-Add.bat | text | |
MD5:E40403342A71DCCA2F6373EAA7CDF33D | SHA256:E7B57CEBFFD4C487D7320659D9616BF15EC097160E180C3F8606A6DF6F05F953 | |||
| 332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa332.2220\RegistryFinder.VisualElementsManifest.xml | xml | |
MD5:991F8A494137E9652DBD2EC77EA821B2 | SHA256:8785A59706AC758BE8F060C08A77D5C570E51FE87FBEC6E2F4C826A5DAAFCCD4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report