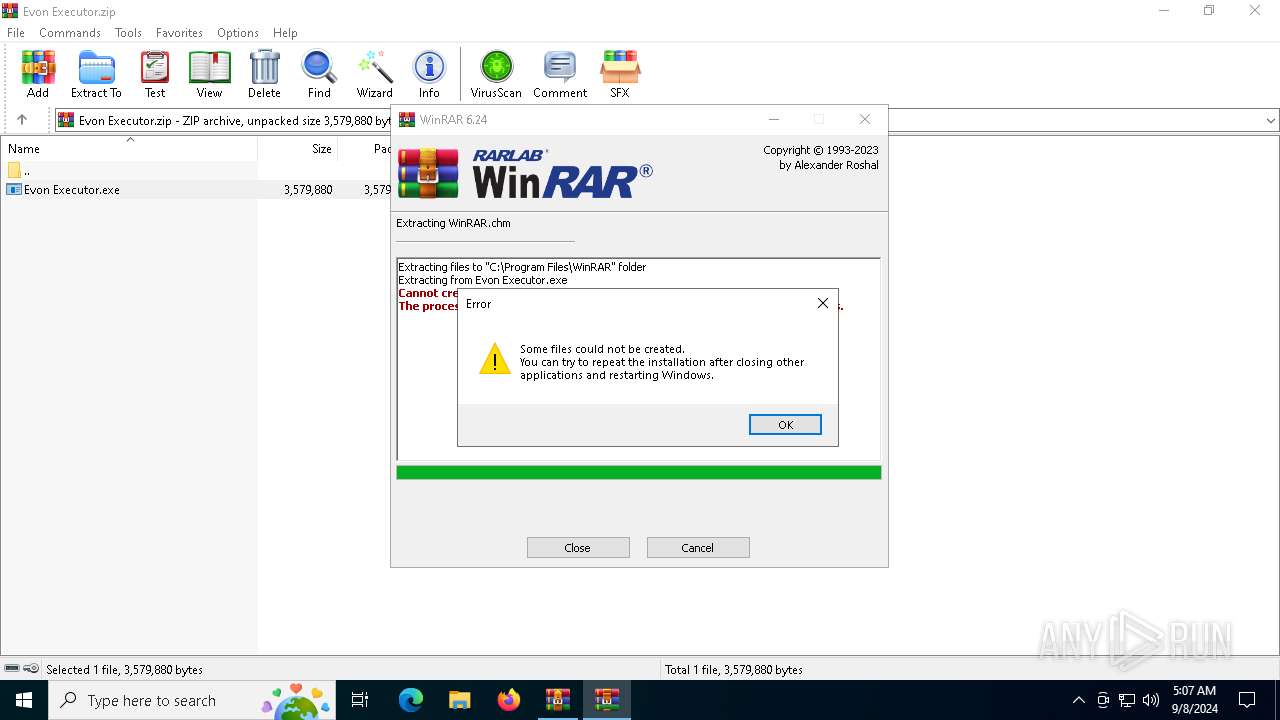
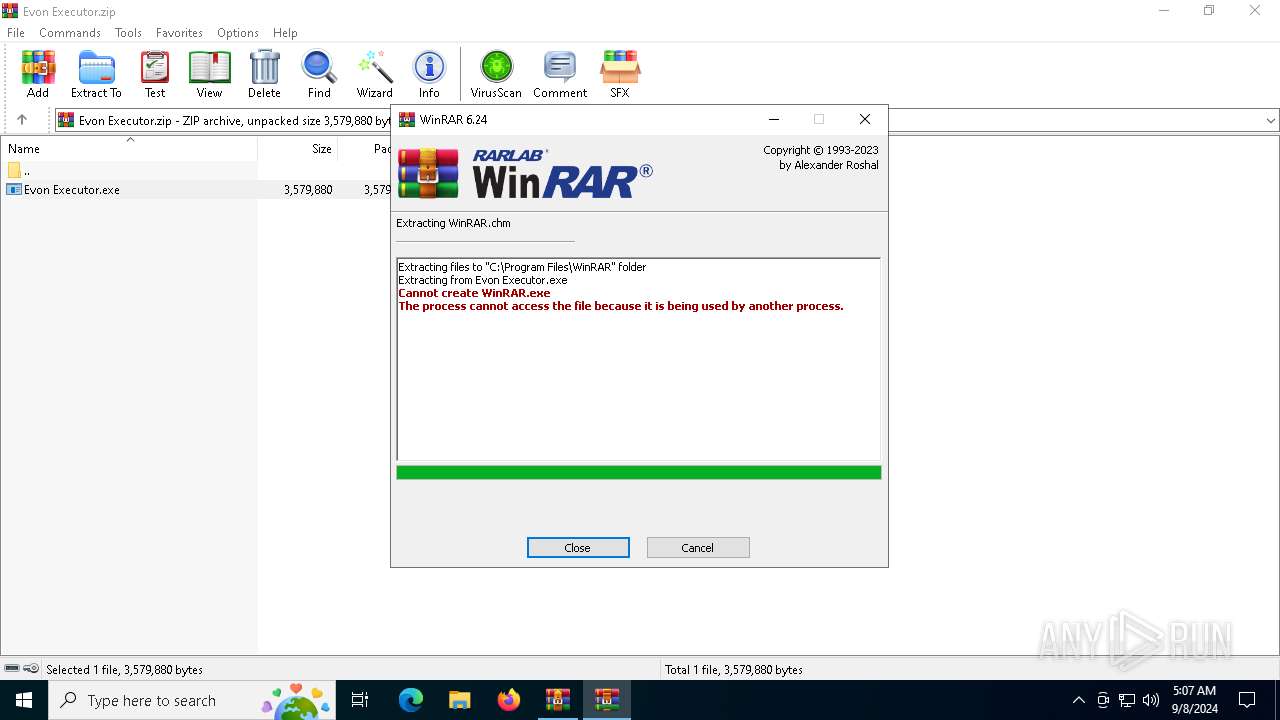
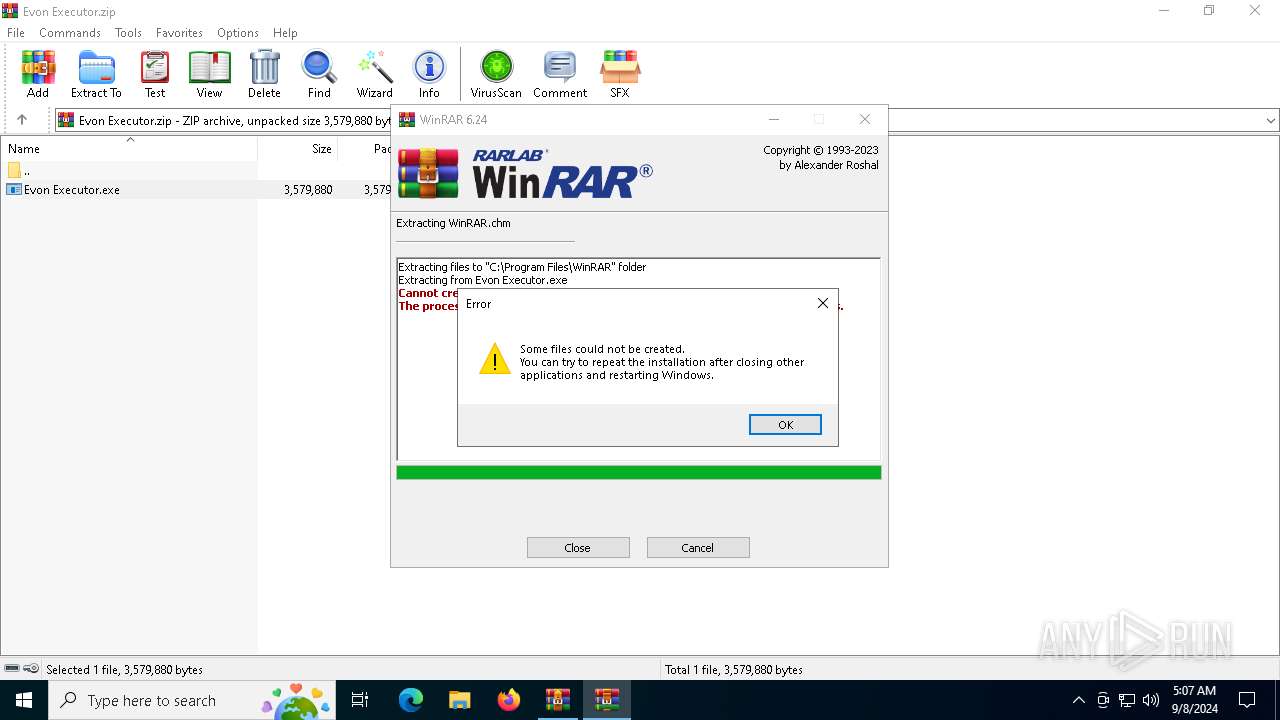
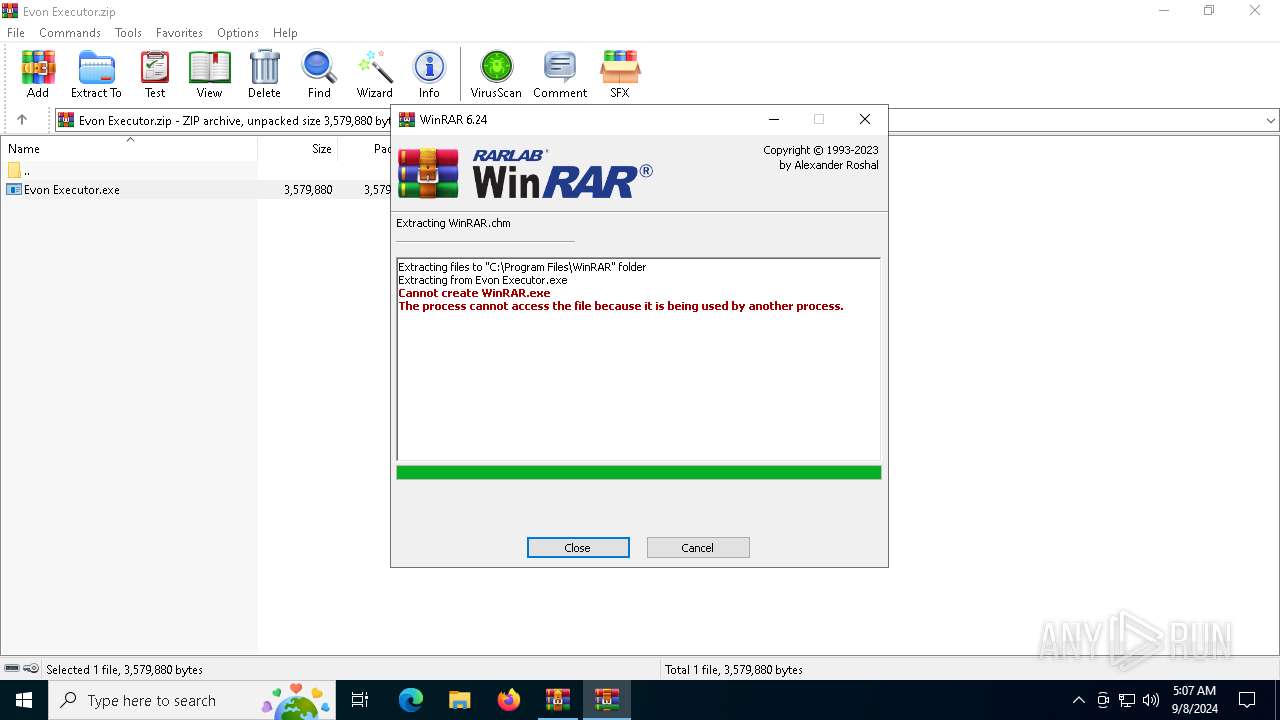
| File name: | Evon Executor.zip |
| Full analysis: | https://app.any.run/tasks/56a24848-00f1-470a-a98c-22c78f6bcd87 |
| Verdict: | Malicious activity |
| Analysis date: | September 08, 2024, 05:06:39 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | FAA0DC4686914D7BF11D07FE2E244396 |
| SHA1: | DD5686AB0AC8D46B02B86325D58106864EC2EF90 |
| SHA256: | 1B8103E2755CB6D4A66B3B16DE0A16E48E4132ADABD5ABDE4D58315FCCFFD282 |
| SSDEEP: | 98304:e/b6EtxpzjVa0cc+O1wf62QyV0MUa6Am9Uo8qihOrnStI3/EQMLCHqZKIngLTG7X:OyhDSIfk4 |
MALICIOUS
No malicious indicators.SUSPICIOUS
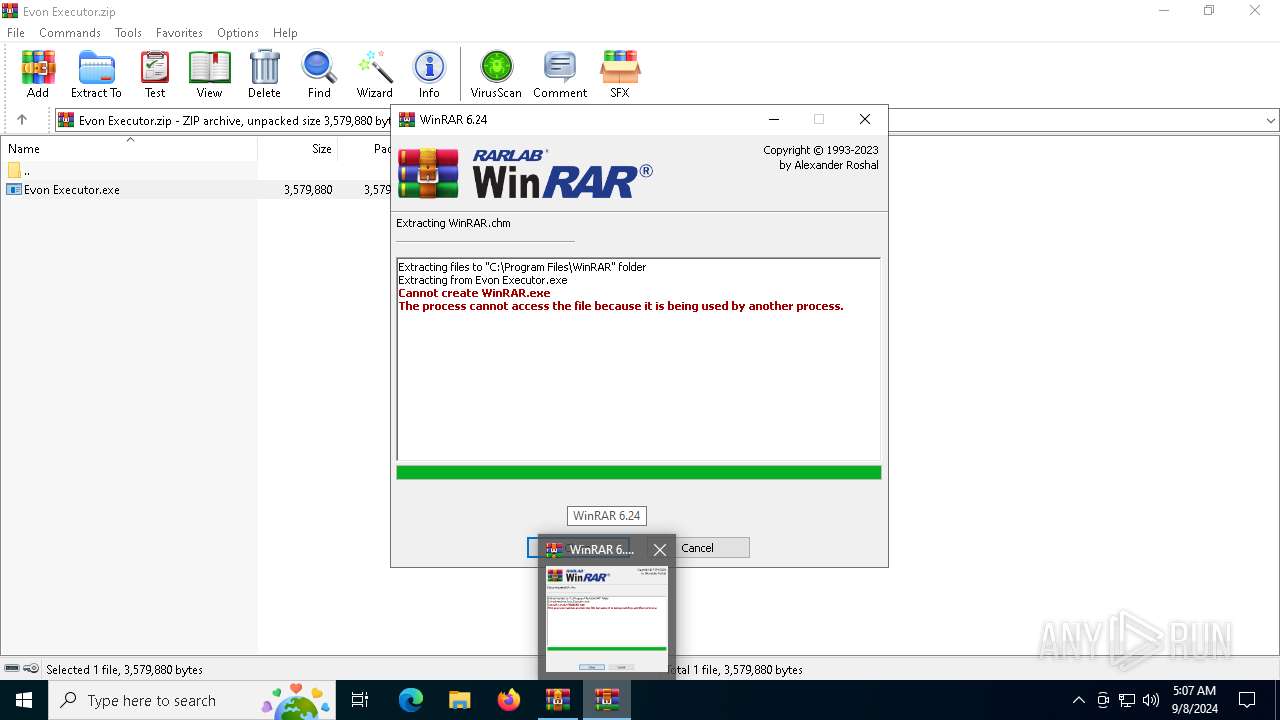
Reads security settings of Internet Explorer
- Evon Executor.exe (PID: 6244)
- WinRAR.exe (PID: 4440)
- Evon Executor.exe (PID: 3160)
Reads Internet Explorer settings
- Evon Executor.exe (PID: 6244)
- Evon Executor.exe (PID: 3160)
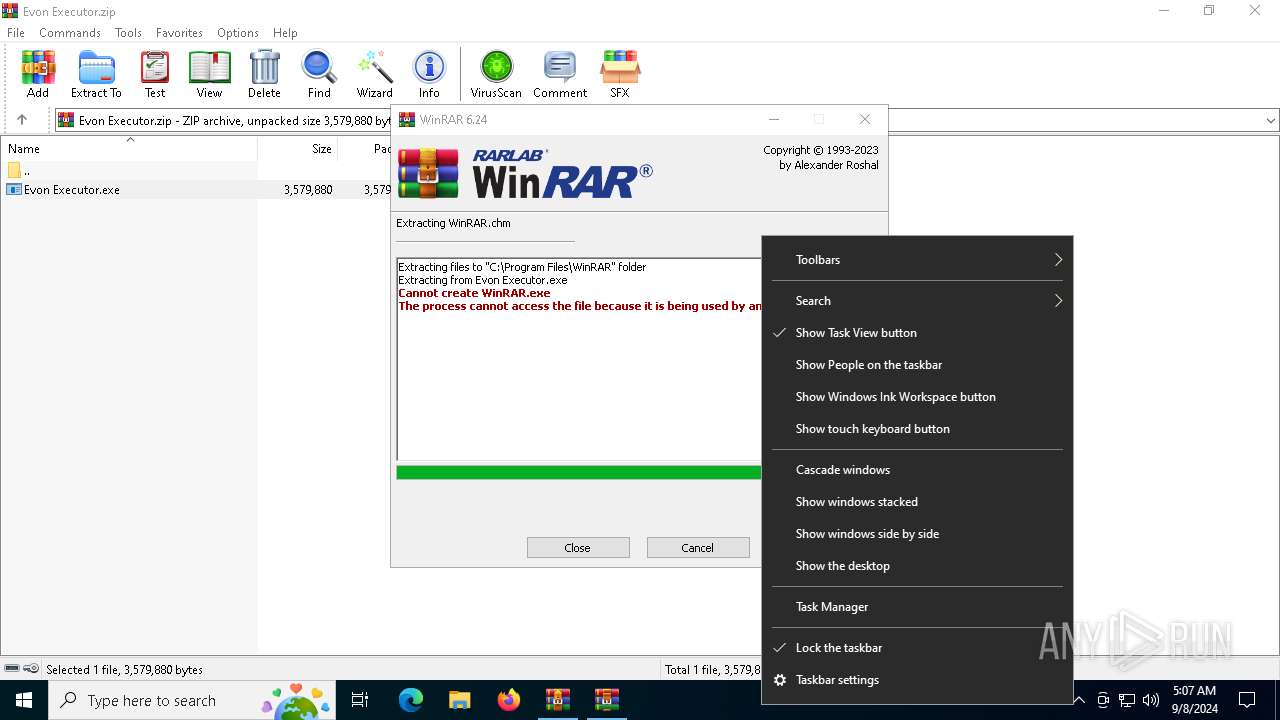
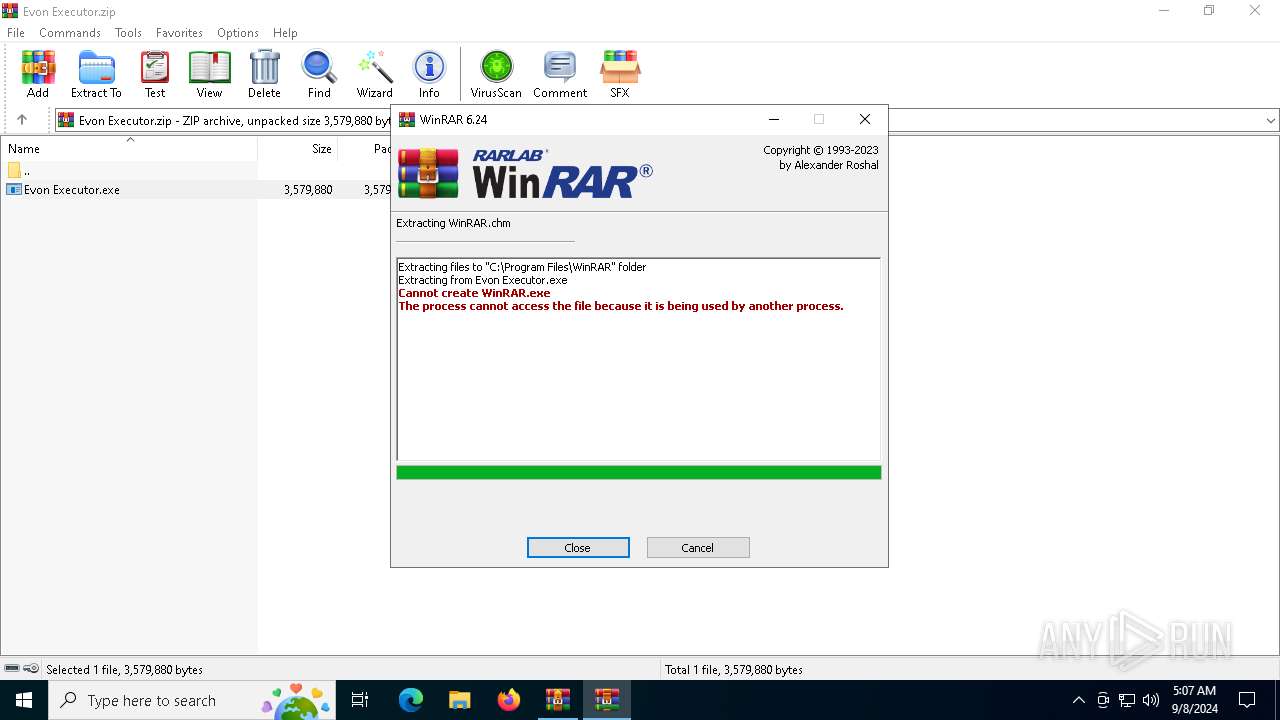
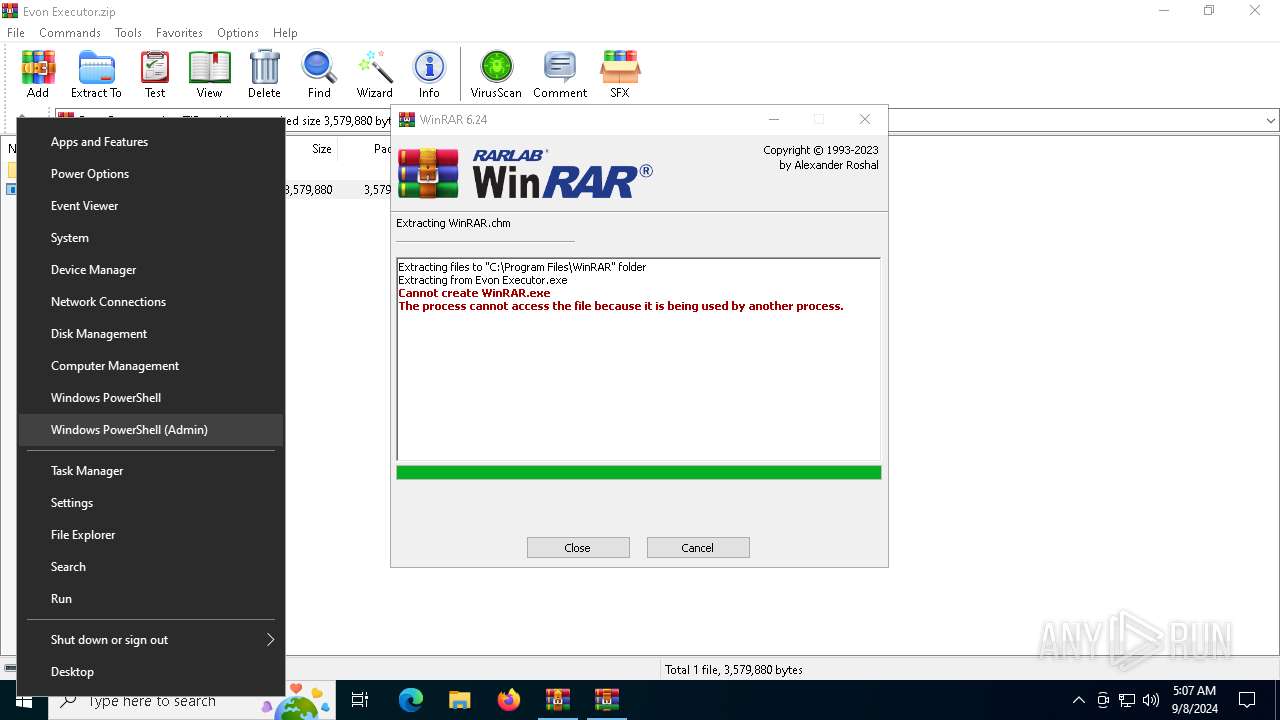
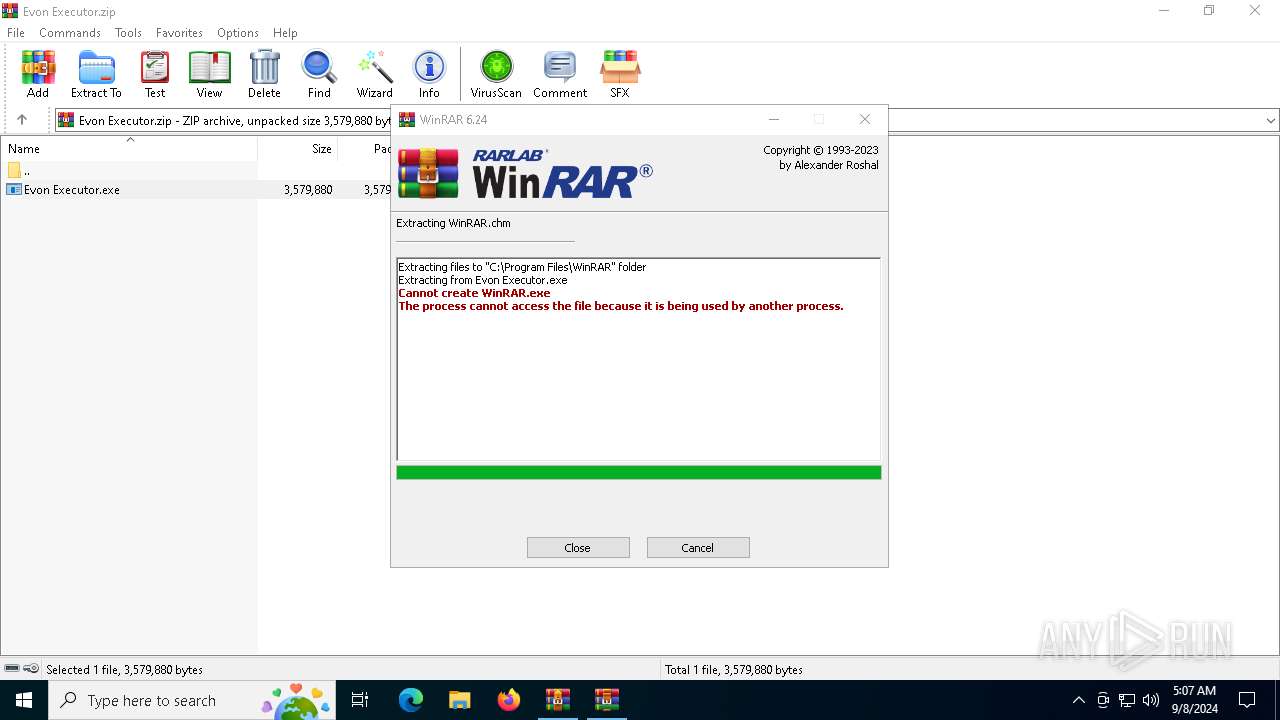
Drops 7-zip archiver for unpacking
- Evon Executor.exe (PID: 6244)
Executable content was dropped or overwritten
- Evon Executor.exe (PID: 6244)
- Evon Executor.exe (PID: 3160)
Reads Microsoft Outlook installation path
- Evon Executor.exe (PID: 3160)
- Evon Executor.exe (PID: 6244)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4440)
The process uses the downloaded file
- WinRAR.exe (PID: 4440)
Reads the computer name
- Evon Executor.exe (PID: 3160)
- Evon Executor.exe (PID: 6244)
Checks proxy server information
- Evon Executor.exe (PID: 3160)
- Evon Executor.exe (PID: 6244)
Checks supported languages
- Evon Executor.exe (PID: 3160)
- Evon Executor.exe (PID: 6244)
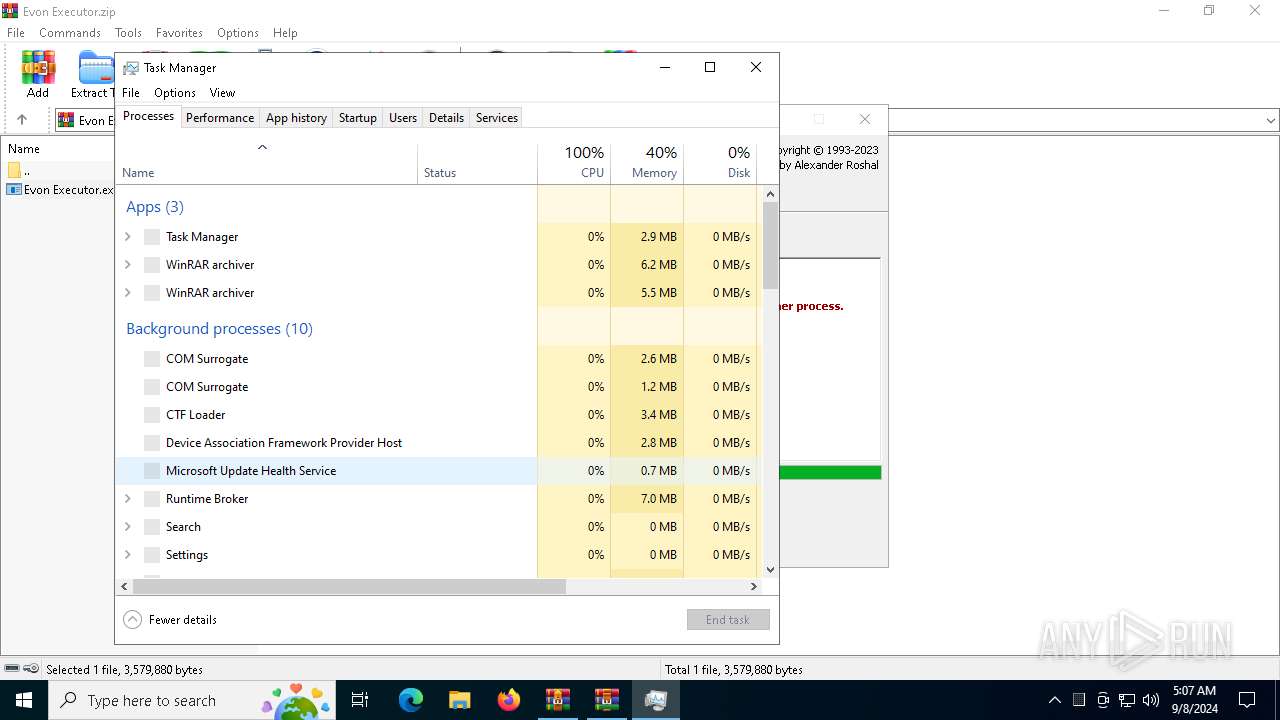
Manual execution by a user
- Taskmgr.exe (PID: 5128)
- Taskmgr.exe (PID: 2576)
Creates files in the program directory
- Evon Executor.exe (PID: 3160)
- Evon Executor.exe (PID: 6244)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 5128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:09:08 05:05:44 |
| ZipCRC: | 0x55fb9f36 |
| ZipCompressedSize: | 3579880 |
| ZipUncompressedSize: | 3579880 |
| ZipFileName: | Evon Executor.exe |
Total processes
132
Monitored processes
7
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2576 | "C:\WINDOWS\system32\taskmgr.exe" /0 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3160 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa4440.33832\Evon Executor.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa4440.33832\Evon Executor.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: HIGH Description: WinRAR archiver Version: 6.24.0 Modules
| |||||||||||||||
| 4440 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Evon Executor.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4824 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa4440.33832\Evon Executor.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa4440.33832\Evon Executor.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 3221226540 Version: 6.24.0 Modules
| |||||||||||||||
| 5128 | "C:\WINDOWS\system32\taskmgr.exe" /0 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6244 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa4440.32451\Evon Executor.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa4440.32451\Evon Executor.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: HIGH Description: WinRAR archiver Exit code: 9 Version: 6.24.0 Modules
| |||||||||||||||
| 6640 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa4440.32451\Evon Executor.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa4440.32451\Evon Executor.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 3221226540 Version: 6.24.0 Modules
| |||||||||||||||
Total events
4 471
Read events
4 453
Write events
15
Delete events
3
Modification events
| (PID) Process: | (4440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (4440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Evon Executor.zip | |||
| (PID) Process: | (4440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6244) Evon Executor.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6244) Evon Executor.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6244) Evon Executor.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6244) Evon Executor.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR SFX |
| Operation: | write | Name: | C%%Program Files%WinRAR |
Value: C:\Program Files\WinRAR | |||
Executable files
17
Suspicious files
3
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4440 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4440.32451\Evon Executor.exe | executable | |
MD5:15596B41DBA42CDCCE4F677FBBC86B6E | SHA256:377ABC9D367E61CB5C4761BF48DCFDF5BCD3822F303E0F972D7F4C8295A2EA79 | |||
| 6244 | Evon Executor.exe | C:\Program Files\WinRAR\Resources.pri | pri | |
MD5:43CB15C1F1CC705305AEBA33B0A9EE73 | SHA256:A7BB097441D9F06DD7A8D08874D70E7495626760C05284CA1AE3A208C11B52F0 | |||
| 6244 | Evon Executor.exe | C:\Program Files\WinRAR\WhatsNew.txt | text | |
MD5:C78A76E698514A835452DE89025B7778 | SHA256:BF30A7D667B61A90BC00908317D96599386C841759540BDB74CA249E28EC8624 | |||
| 6244 | Evon Executor.exe | C:\Program Files\WinRAR\ReadMe.txt | text | |
MD5:00D0A57A6D64EE3DE8F4D5529D6C6447 | SHA256:FCD13E1B97AF47B8B923BA97AE15E9731C66093609667C3171D5DD24A6F7F2E6 | |||
| 6244 | Evon Executor.exe | C:\Program Files\WinRAR\RarExt32.dll | executable | |
MD5:8510BEA1DC5A2245A72DFE5ECD20CDA6 | SHA256:53322BE2FDF24B09DE1070A2713855EA3D01BBC895C6D24A2991D1E2139CA585 | |||
| 6244 | Evon Executor.exe | C:\Program Files\WinRAR\Descript.ion | text | |
MD5:3FB658E292A09D2303B6D84FAF079E0C | SHA256:FA7BFC756E502CA814F927130574CBB472FC8B9C608F98B470409E7D8D1AD30D | |||
| 6244 | Evon Executor.exe | C:\Program Files\WinRAR\Rar.txt | text | |
MD5:B689A0CB8C288849FEBFFAFC2144576B | SHA256:59334A8FFFF612755A64A912389BC23FBC35933CF209F845BDE34F055011B8A6 | |||
| 6244 | Evon Executor.exe | C:\Program Files\WinRAR\RarExtInstaller.exe | executable | |
MD5:1E1CAC0725CF47E62EA96669EAC678FC | SHA256:48B44BD3342A68ECBBD40A485930A22E02FDF157B2939EE346C2B123F6D5E99C | |||
| 6244 | Evon Executor.exe | C:\Program Files\WinRAR\Uninstall.lst | text | |
MD5:D2098C2817A55B955B39D504B5A460D9 | SHA256:2A0A49154CFF5F00F85A14DD2AC65050638D11E3B6C2177CE45ABE8E7DD92353 | |||
| 6244 | Evon Executor.exe | C:\Program Files\WinRAR\RarFiles.lst | text | |
MD5:08EA0309D72A874C182F08CBF9DA2CC3 | SHA256:12787F8204EEDB0B8BDABF5D68D557334FDDB2D70B46E1422510713DDA5E6A01 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
23
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1440 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1496 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1496 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7056 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1440 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1440 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |