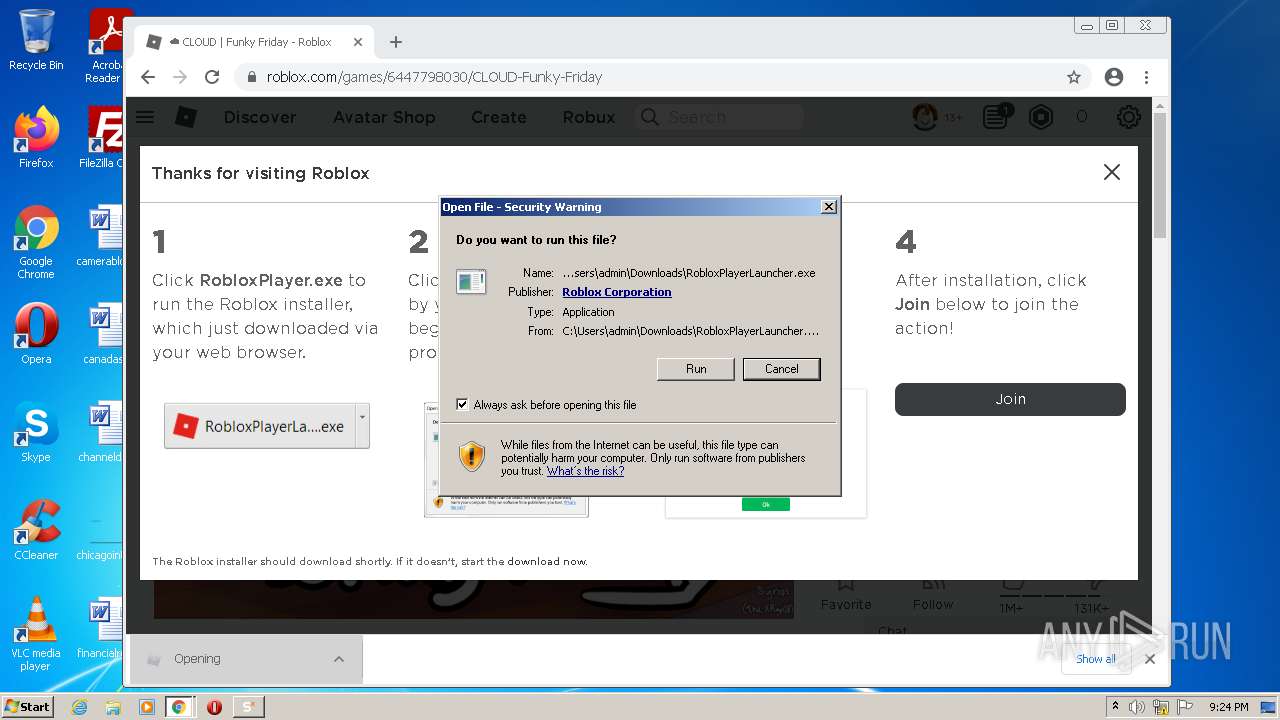
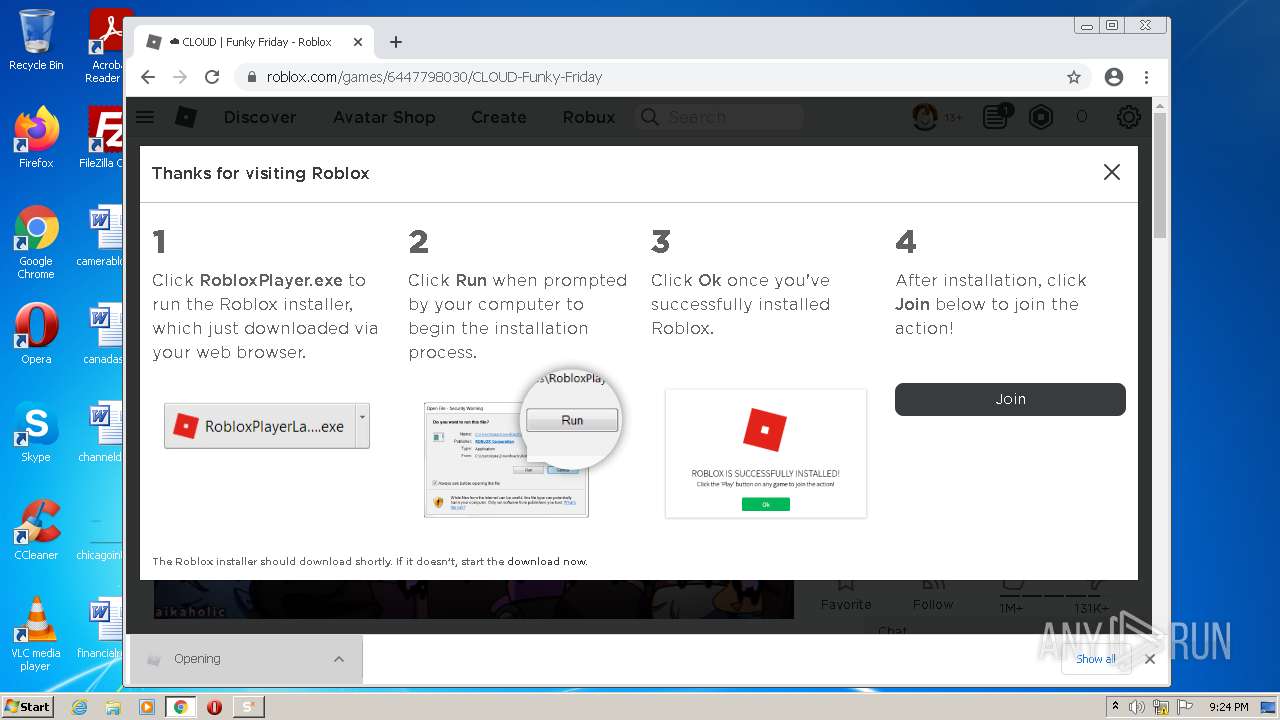
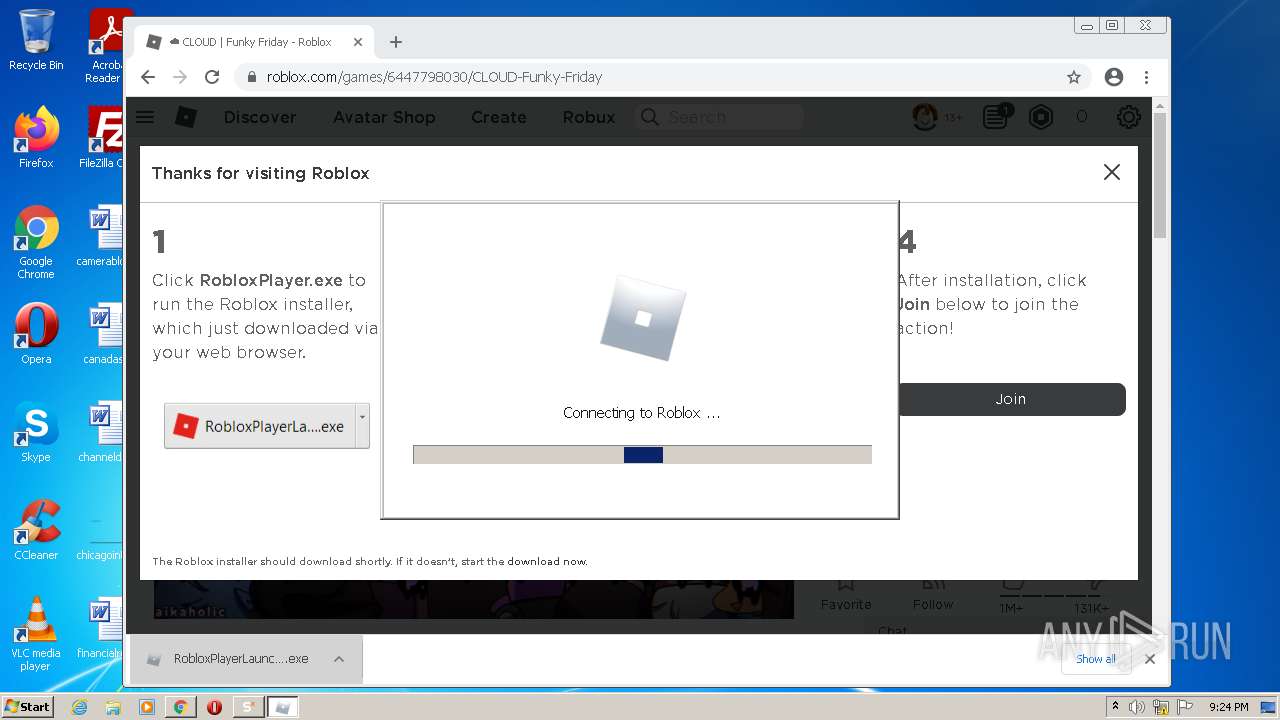
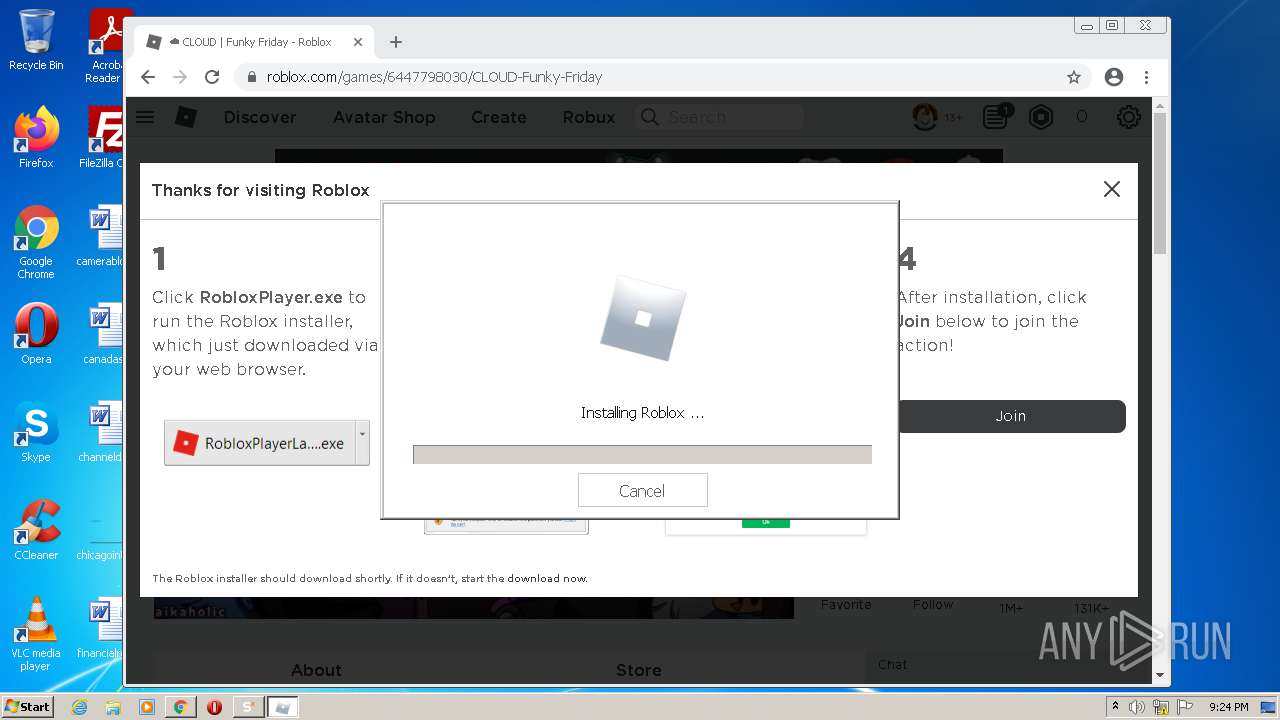
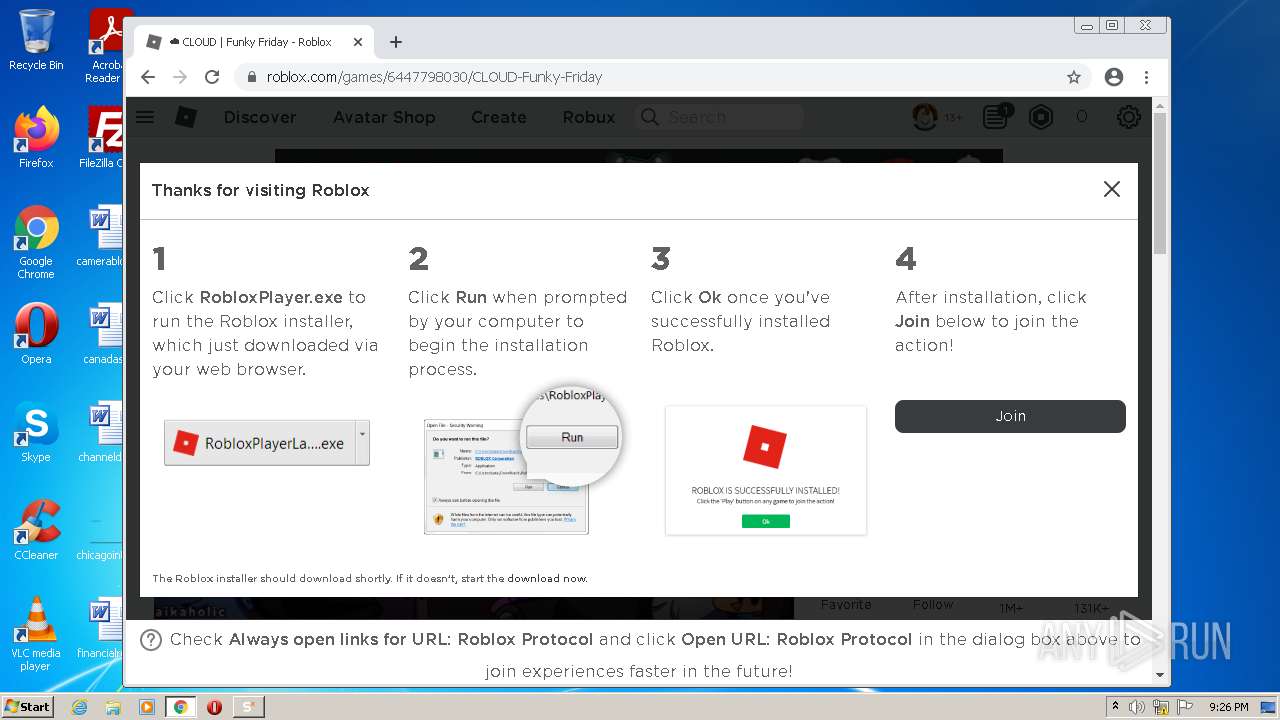
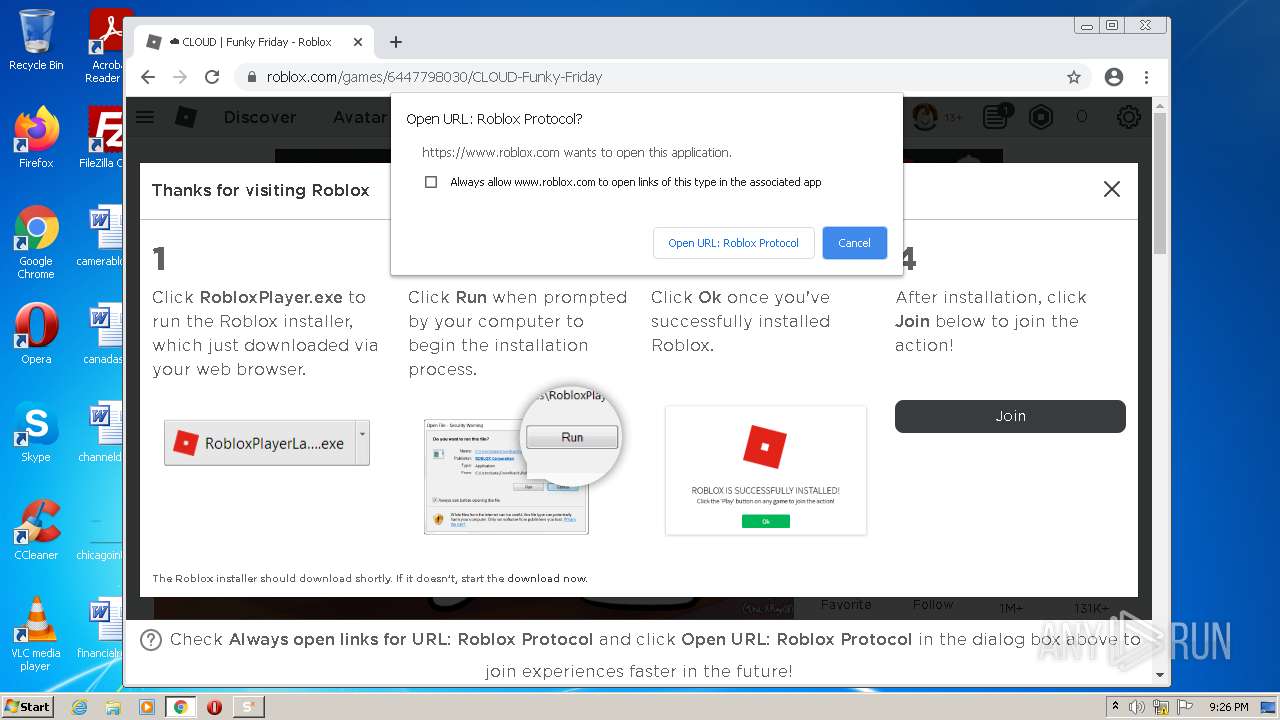
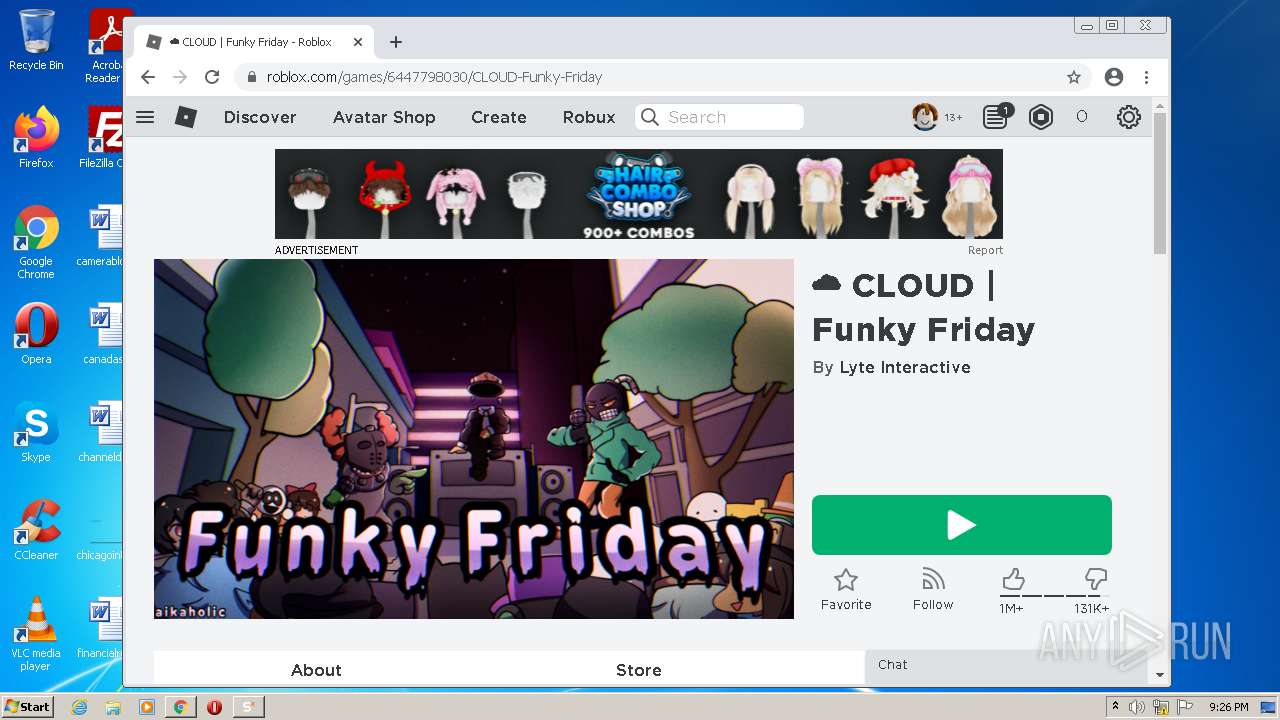
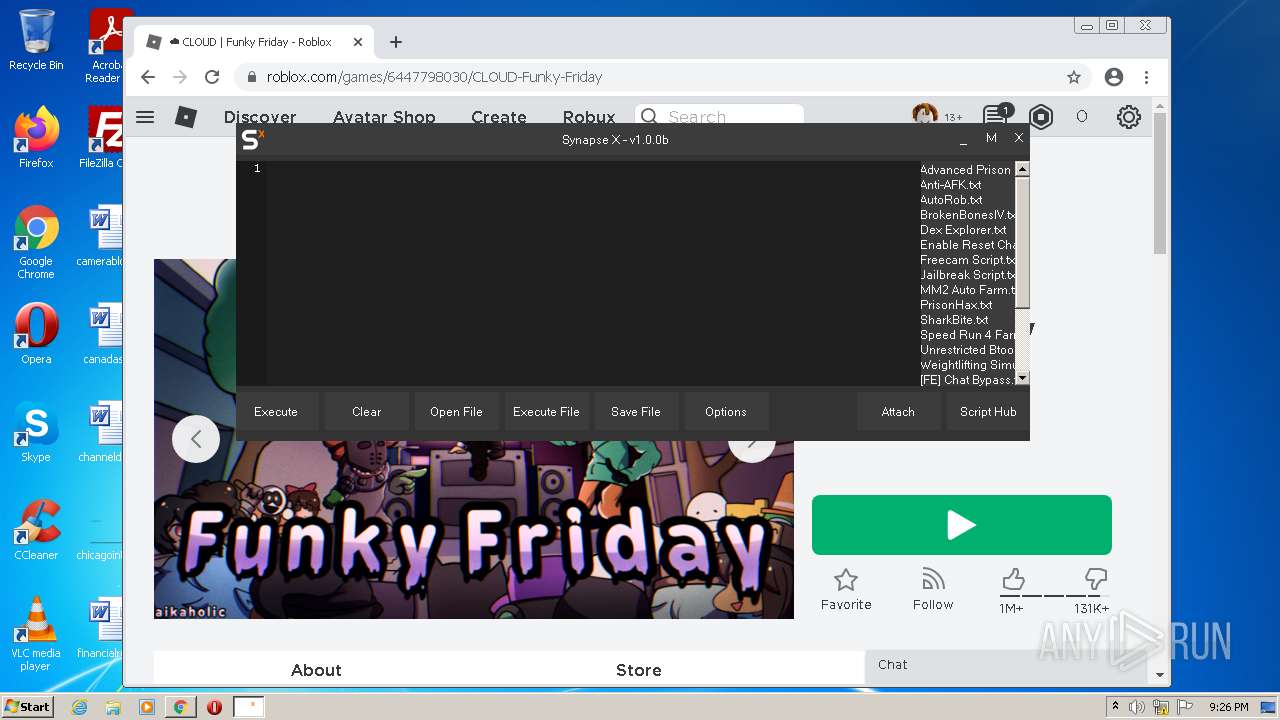
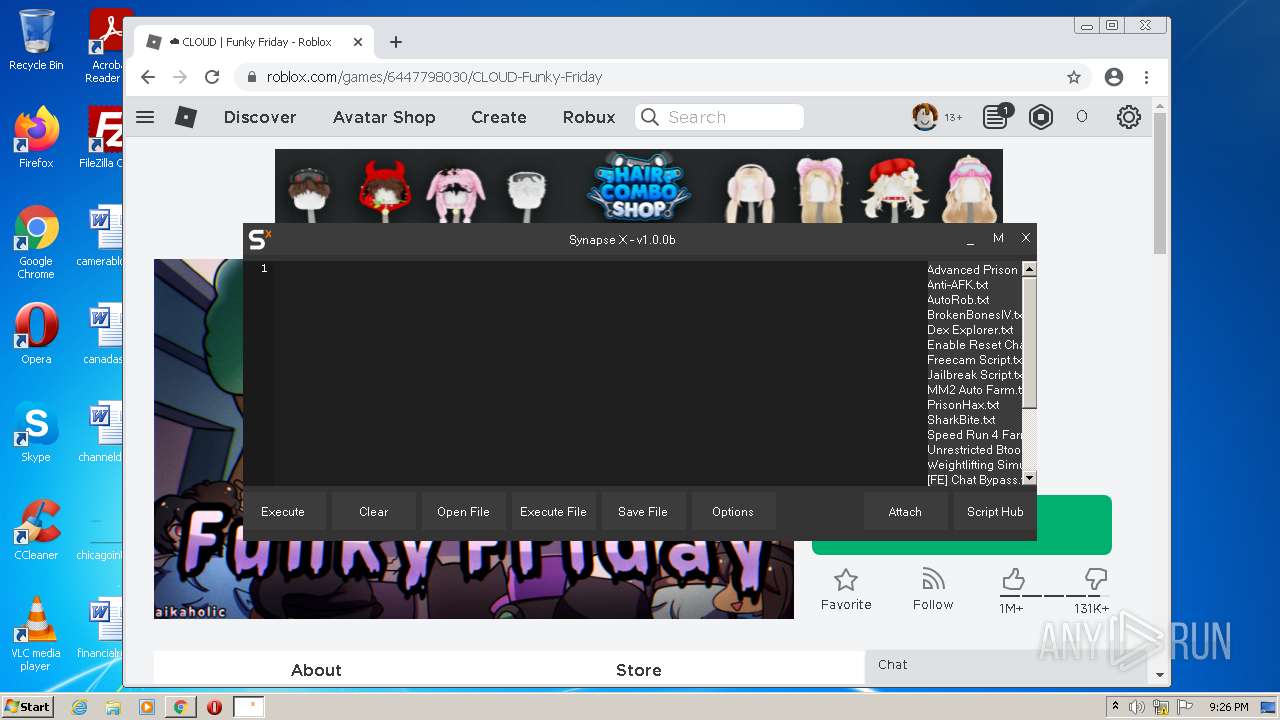
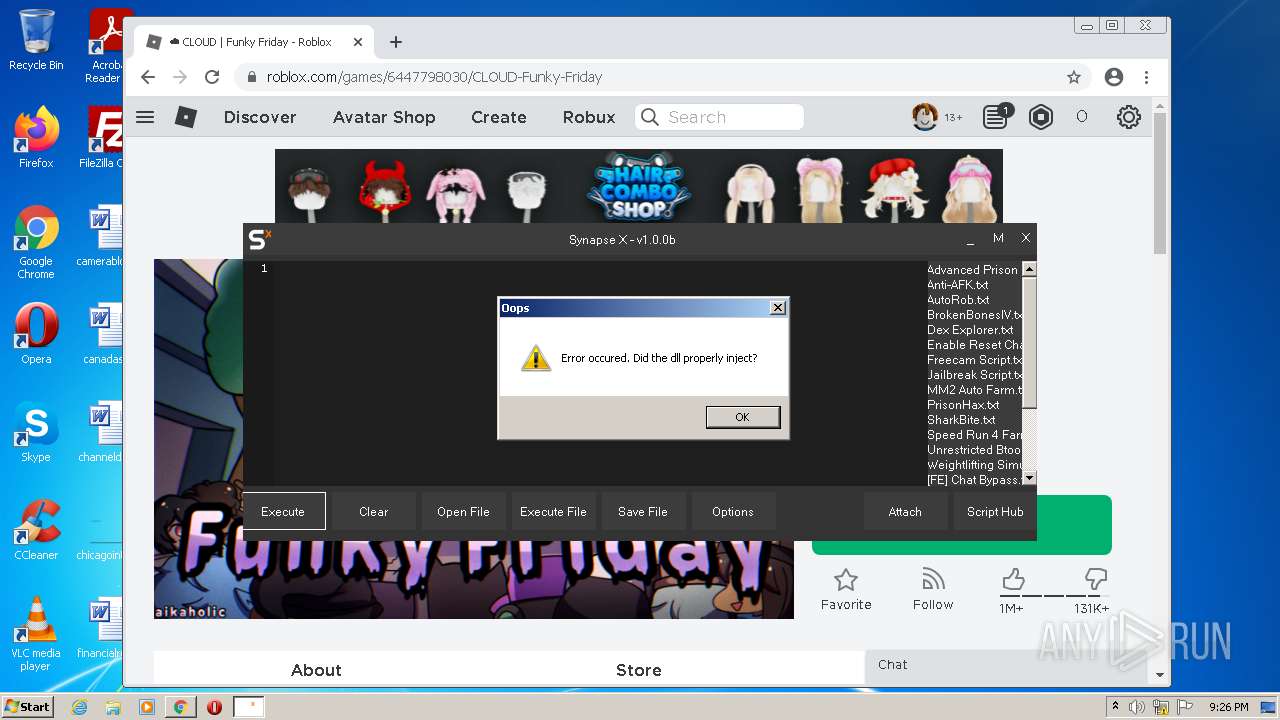
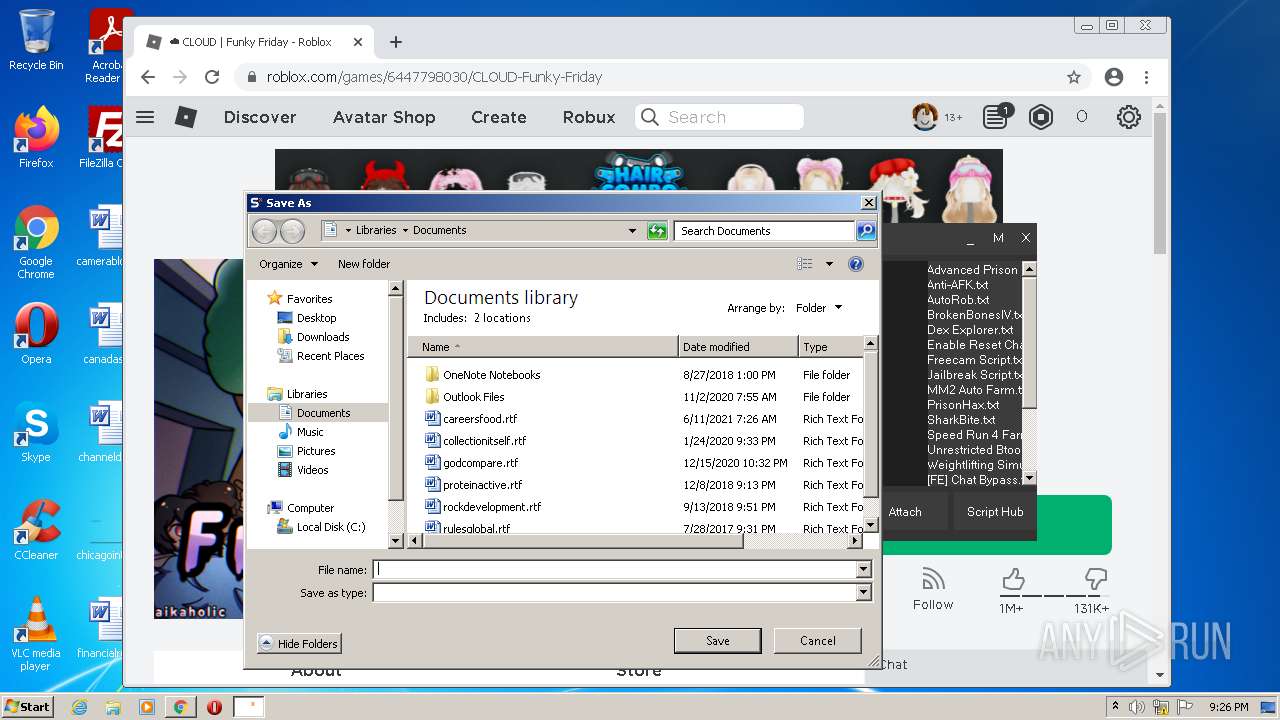
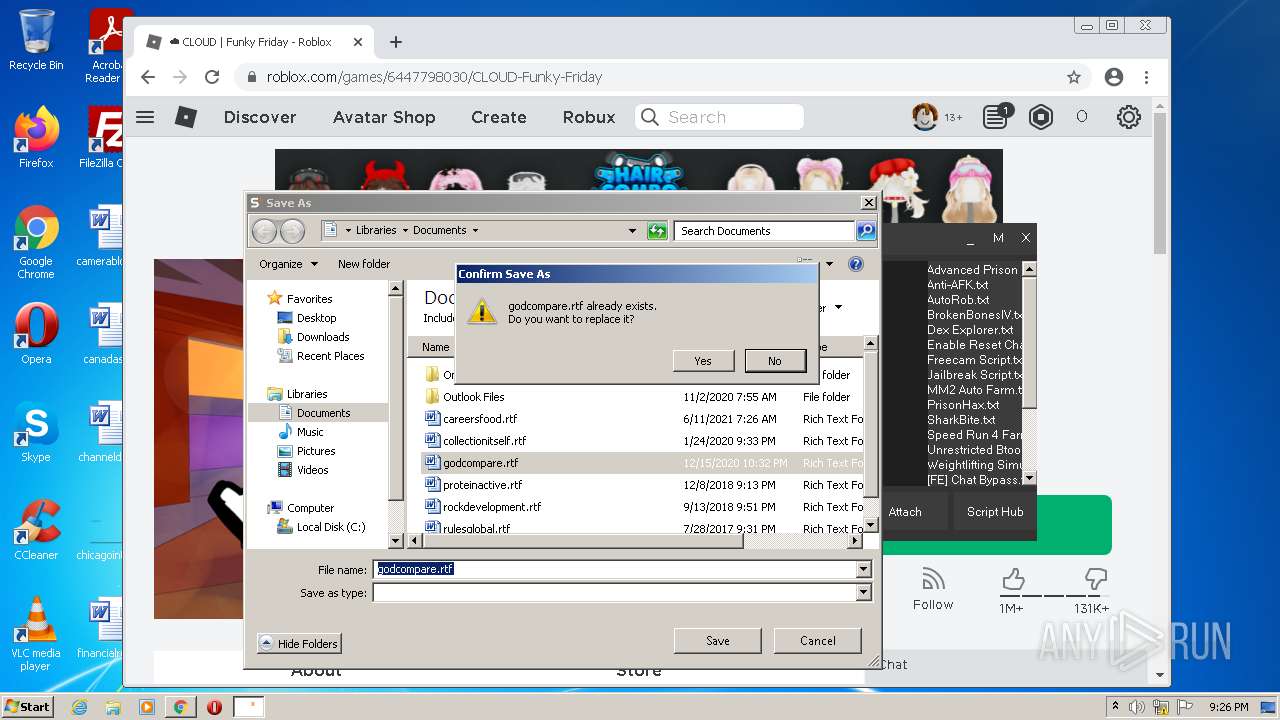
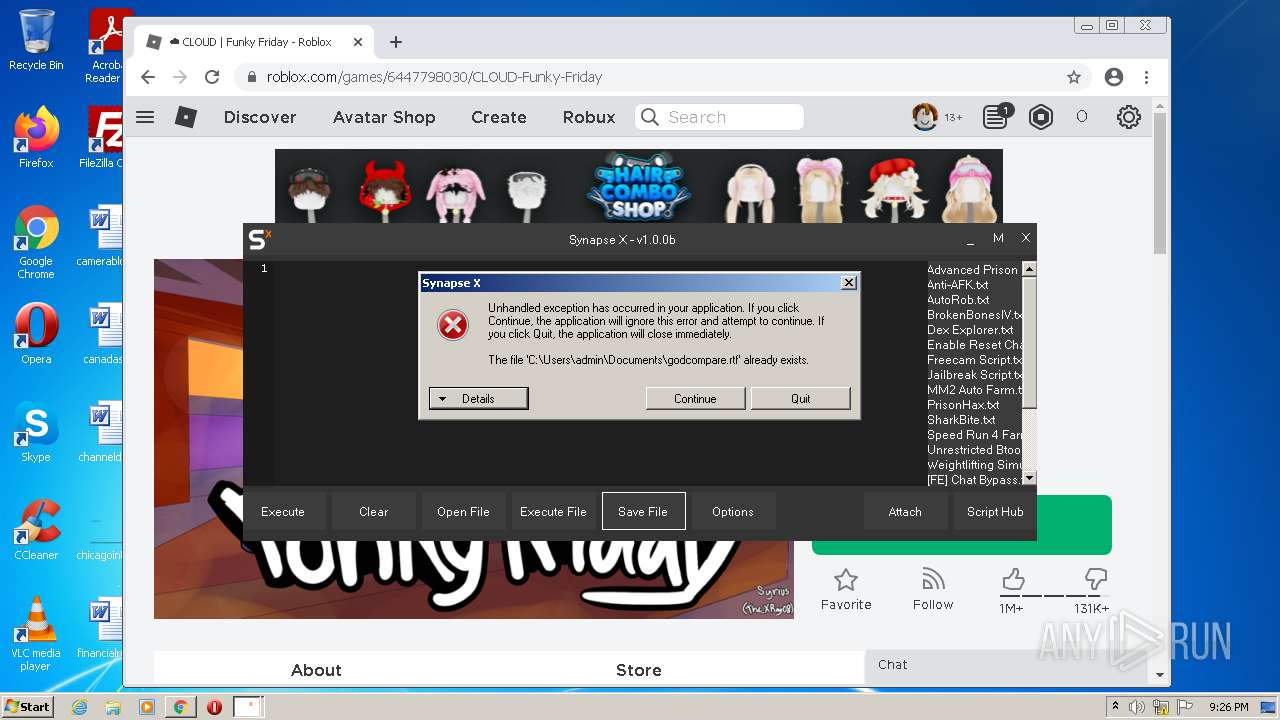
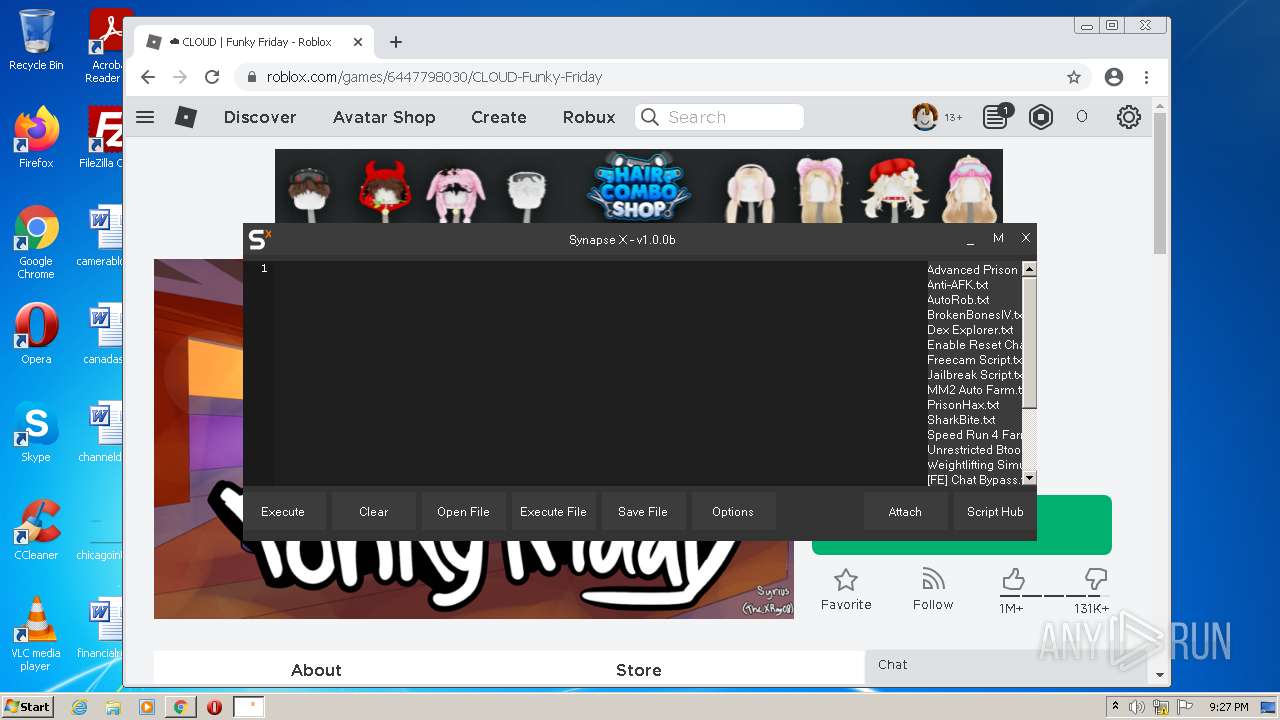
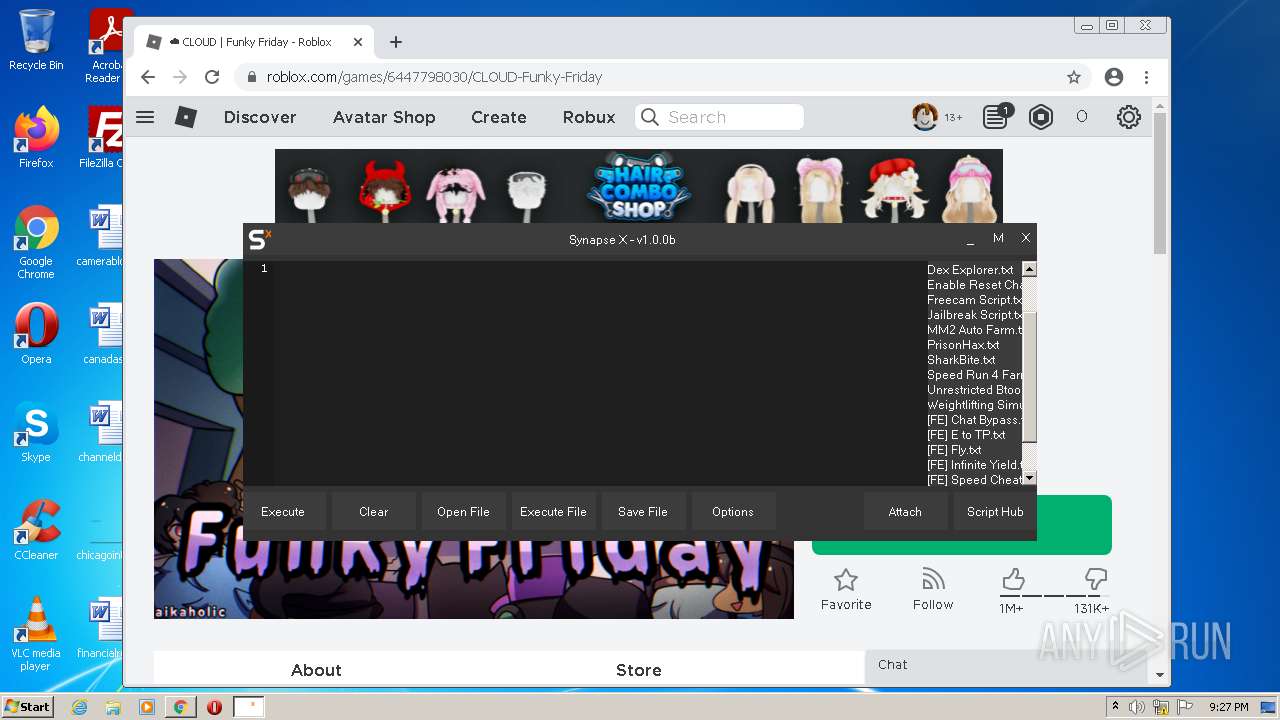
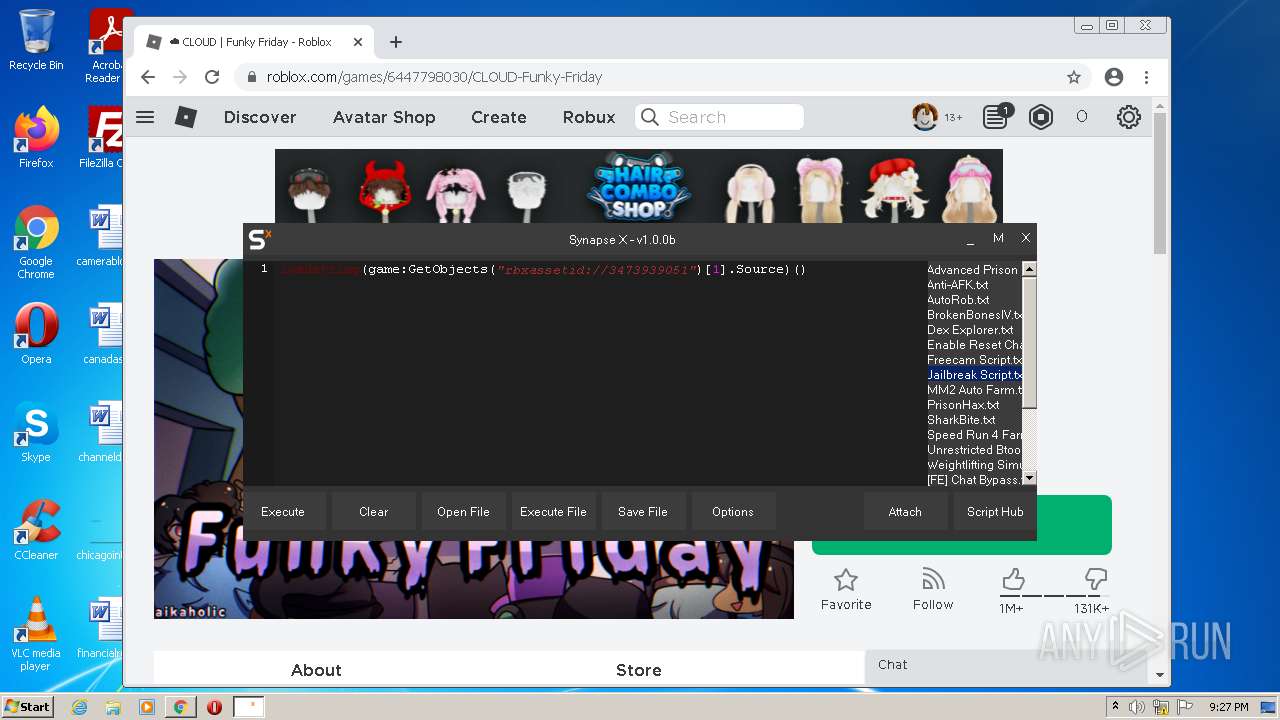
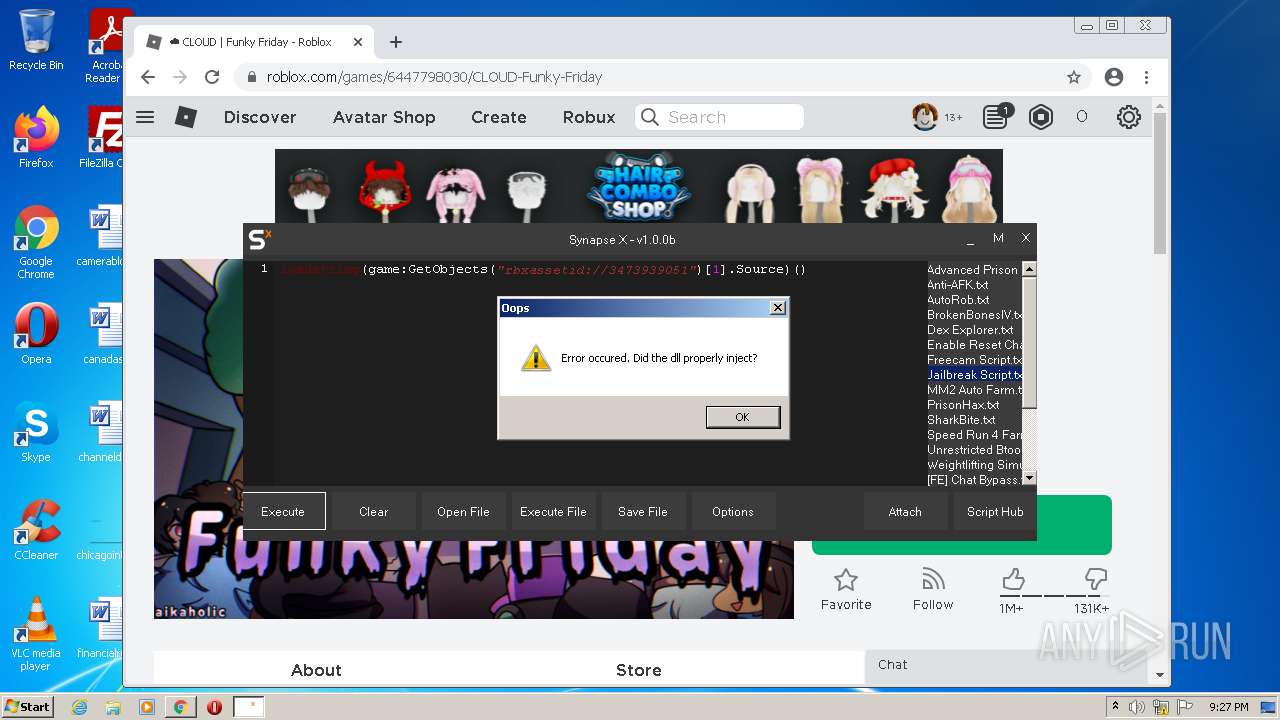
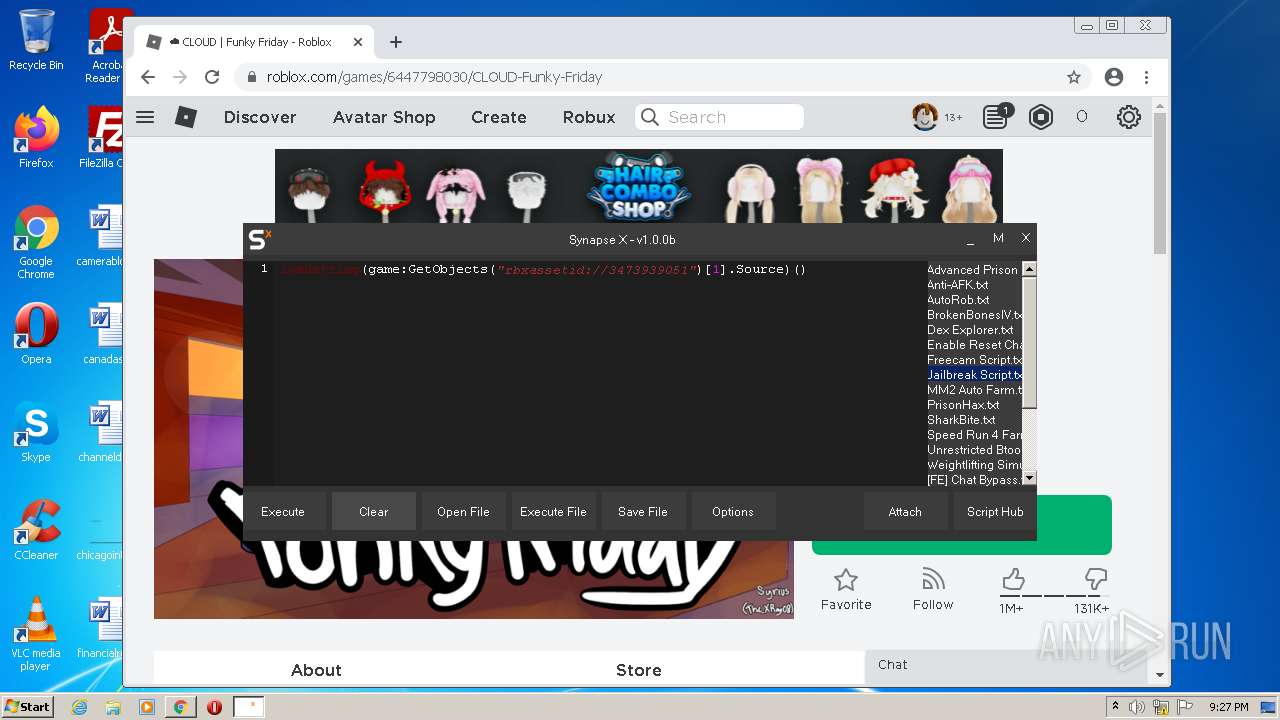
| File name: | Synapse X.zip |
| Full analysis: | https://app.any.run/tasks/9fb89ed5-6284-4933-8b4e-46cbe27f75e7 |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 21:22:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 2A4F3913C992A31E7D0CC45BE18DF119 |
| SHA1: | 5DA22BA82349EFE200A564232C2133C2F5528F51 |
| SHA256: | 1B72E303855D6CD69DC71B24783F0D43F0C58B2B6C83973EE672174B601BB51D |
| SSDEEP: | 196608:15noJeE1+j/4bT3tdQhiKHm9EukBj7yQg5ejJNjjm+OjRRwiq:XoT10YPKHm9SBjBg5eTQjRRS |
MALICIOUS
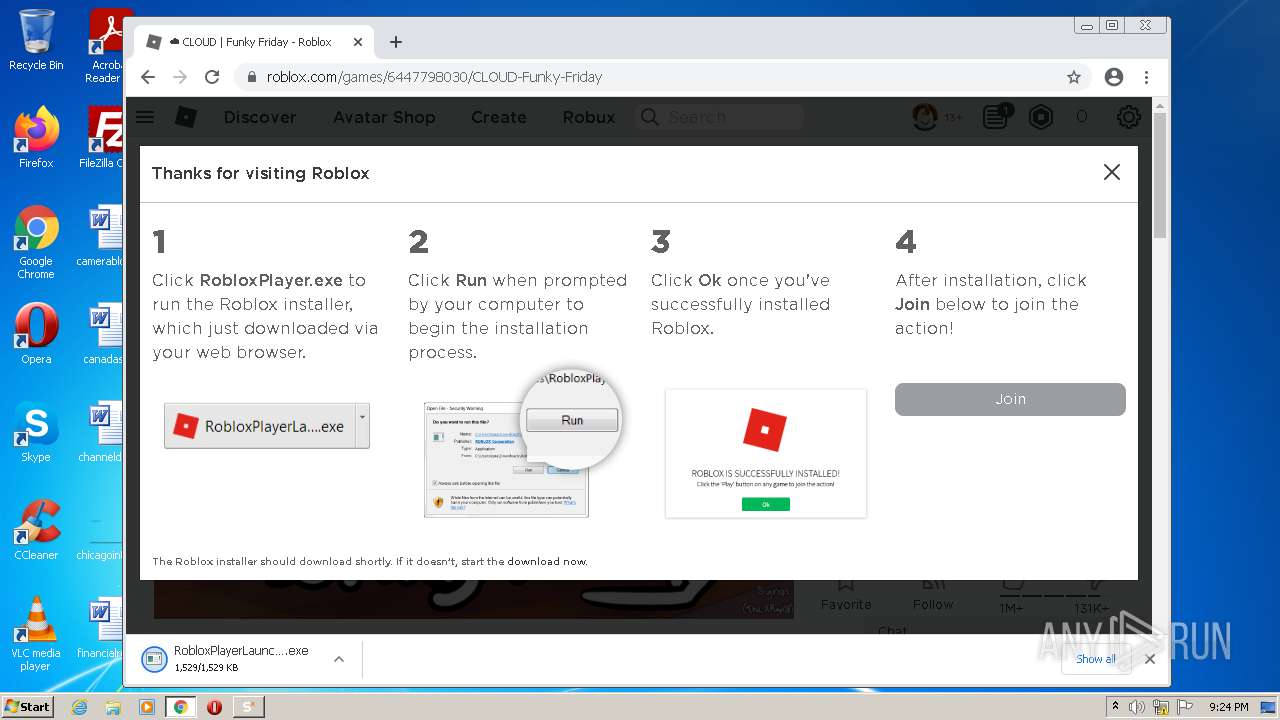
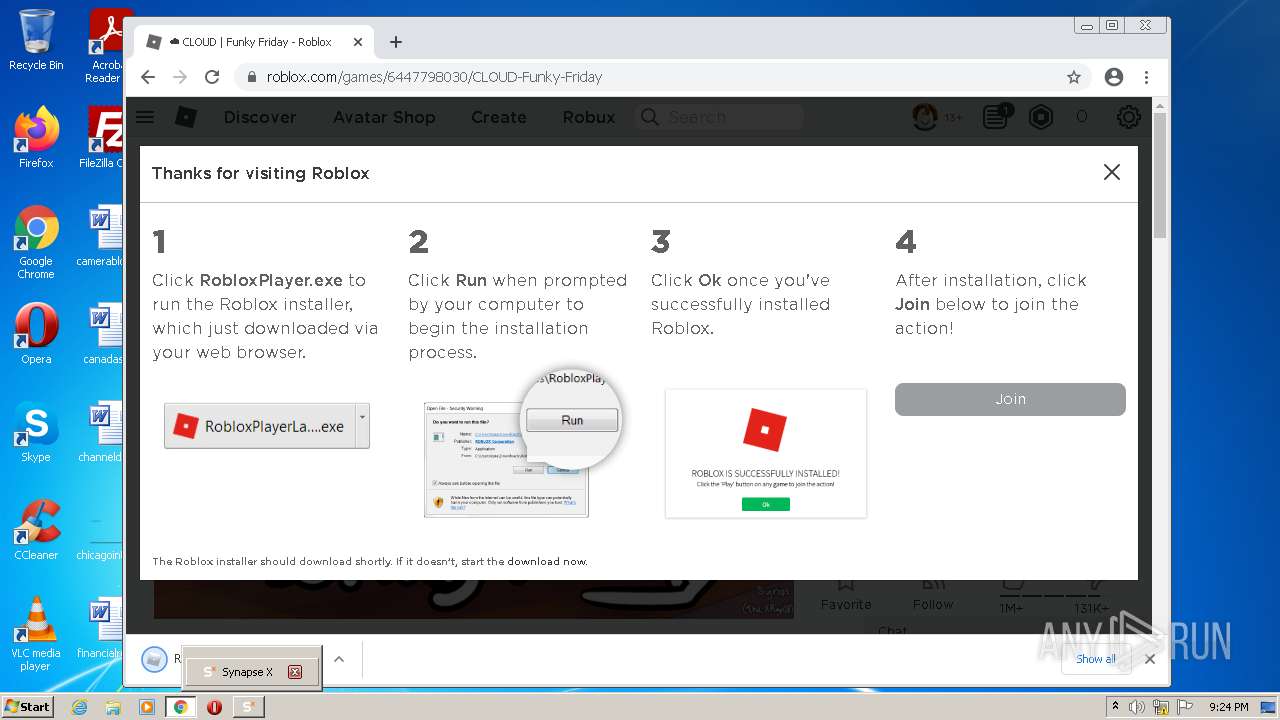
Application was dropped or rewritten from another process
- Synapse X.exe (PID: 3148)
- RobloxPlayerLauncher.exe (PID: 2760)
- RobloxPlayerLauncher.exe (PID: 4012)
- RobloxPlayerLauncher.exe (PID: 1656)
- RobloxPlayerLauncher.exe (PID: 424)
Loads dropped or rewritten executable
- Synapse X.exe (PID: 3148)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 3460)
- Synapse X.exe (PID: 3148)
- RobloxPlayerLauncher.exe (PID: 2760)
- RobloxPlayerLauncher.exe (PID: 4012)
- RobloxPlayerLauncher.exe (PID: 424)
- RobloxPlayerLauncher.exe (PID: 1656)
- RobloxPlayerBeta.exe (PID: 2716)
Reads the computer name
- WinRAR.exe (PID: 3460)
- Synapse X.exe (PID: 3148)
- RobloxPlayerLauncher.exe (PID: 4012)
- RobloxPlayerLauncher.exe (PID: 424)
- RobloxPlayerBeta.exe (PID: 2716)
- RobloxPlayerLauncher.exe (PID: 1656)
- RobloxPlayerLauncher.exe (PID: 2760)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3460)
- chrome.exe (PID: 2492)
- RobloxPlayerLauncher.exe (PID: 2760)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3460)
- chrome.exe (PID: 2492)
- RobloxPlayerLauncher.exe (PID: 2760)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3460)
- chrome.exe (PID: 2492)
- RobloxPlayerLauncher.exe (PID: 2760)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2492)
Reads Microsoft Outlook installation path
- chrome.exe (PID: 2148)
Creates files in the user directory
- RobloxPlayerLauncher.exe (PID: 2760)
Cleans NTFS data-stream (Zone Identifier)
- RobloxPlayerLauncher.exe (PID: 2760)
Application launched itself
- RobloxPlayerLauncher.exe (PID: 2760)
- RobloxPlayerLauncher.exe (PID: 424)
Drops a file with too old compile date
- RobloxPlayerLauncher.exe (PID: 2760)
Changes default file association
- RobloxPlayerLauncher.exe (PID: 2760)
Creates a software uninstall entry
- RobloxPlayerLauncher.exe (PID: 2760)
Changes IE settings (feature browser emulation)
- RobloxPlayerBeta.exe (PID: 2716)
INFO
Checks supported languages
- WINWORD.EXE (PID: 2996)
- chrome.exe (PID: 2492)
- chrome.exe (PID: 2784)
- chrome.exe (PID: 3972)
- chrome.exe (PID: 2980)
- chrome.exe (PID: 576)
- chrome.exe (PID: 3072)
- chrome.exe (PID: 3996)
- chrome.exe (PID: 2908)
- chrome.exe (PID: 436)
- chrome.exe (PID: 1012)
- chrome.exe (PID: 3280)
- chrome.exe (PID: 3732)
- chrome.exe (PID: 2484)
- chrome.exe (PID: 3184)
- chrome.exe (PID: 2160)
- chrome.exe (PID: 3616)
- chrome.exe (PID: 1232)
- chrome.exe (PID: 2324)
- chrome.exe (PID: 2236)
- chrome.exe (PID: 344)
- chrome.exe (PID: 3640)
- chrome.exe (PID: 3280)
- chrome.exe (PID: 2792)
- chrome.exe (PID: 2892)
- chrome.exe (PID: 1088)
- chrome.exe (PID: 2300)
- chrome.exe (PID: 468)
- chrome.exe (PID: 3196)
- chrome.exe (PID: 128)
- chrome.exe (PID: 2212)
- chrome.exe (PID: 2884)
- chrome.exe (PID: 1780)
- chrome.exe (PID: 2052)
- chrome.exe (PID: 128)
- chrome.exe (PID: 3564)
- chrome.exe (PID: 3684)
- chrome.exe (PID: 2148)
- chrome.exe (PID: 1540)
- chrome.exe (PID: 4012)
- chrome.exe (PID: 2716)
- chrome.exe (PID: 2452)
- chrome.exe (PID: 1036)
- chrome.exe (PID: 392)
- chrome.exe (PID: 2596)
- chrome.exe (PID: 3908)
- chrome.exe (PID: 1256)
- chrome.exe (PID: 2360)
- chrome.exe (PID: 2932)
- chrome.exe (PID: 3632)
- chrome.exe (PID: 2420)
- chrome.exe (PID: 4044)
Manual execution by user
- WINWORD.EXE (PID: 2996)
- chrome.exe (PID: 2492)
Reads the computer name
- WINWORD.EXE (PID: 2996)
- chrome.exe (PID: 2492)
- chrome.exe (PID: 3072)
- chrome.exe (PID: 2980)
- chrome.exe (PID: 2908)
- chrome.exe (PID: 468)
- chrome.exe (PID: 128)
- chrome.exe (PID: 2884)
- chrome.exe (PID: 2212)
- chrome.exe (PID: 128)
- chrome.exe (PID: 1540)
- chrome.exe (PID: 2148)
- chrome.exe (PID: 3632)
Creates files in the user directory
- WINWORD.EXE (PID: 2996)
Reads the hosts file
- chrome.exe (PID: 2492)
- chrome.exe (PID: 3072)
Application launched itself
- chrome.exe (PID: 2492)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2996)
Reads settings of System Certificates
- chrome.exe (PID: 3072)
- chrome.exe (PID: 2492)
- RobloxPlayerLauncher.exe (PID: 4012)
- RobloxPlayerLauncher.exe (PID: 2760)
- RobloxPlayerLauncher.exe (PID: 424)
- RobloxPlayerLauncher.exe (PID: 1656)
- RobloxPlayerBeta.exe (PID: 2716)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 2492)
Reads the date of Windows installation
- chrome.exe (PID: 2884)
Checks Windows Trust Settings
- chrome.exe (PID: 2492)
- RobloxPlayerLauncher.exe (PID: 4012)
- RobloxPlayerLauncher.exe (PID: 424)
- RobloxPlayerLauncher.exe (PID: 1656)
- RobloxPlayerBeta.exe (PID: 2716)
- RobloxPlayerLauncher.exe (PID: 2760)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | Synapse X/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2022:01:23 22:19:07 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 10 |
Total processes
108
Monitored processes
59
Malicious processes
3
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1052,16751803291629401274,10121511774458577501,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3552 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1052,16751803291629401274,10121511774458577501,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3916 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 344 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1052,16751803291629401274,10121511774458577501,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3684 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 392 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1052,16751803291629401274,10121511774458577501,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1236 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 424 | "C:\Users\admin\AppData\Local\Roblox\Versions\version-1a42d2dceb424b0b\RobloxPlayerLauncher.exe" roblox-player:1+launchmode:play+gameinfo:3B1DF912E1E6DD10F9EECC9A311E2E7C90F1FA99BE750872A1D6D80B8104924EF95219CAB280DC8A9C57887A5AD55735F4EFEBC189BA785145C88135680BF44C54D6B3B97BAE72F7859FF16B86AEA689CA4EAC339AF590FF4FDC2B1312A06466C84CE02C5309169D37A0F4A1B3DEB034EA8737E5BEF17CFA4230845B26261C1DAF51A7FA9678E24DBD2140D356749AECDC504A8EDB0FFA9C29CA609EECADD969901B57D3D9339F8D3408BD55A418A55F39903E57+launchtime:1643059450118+placelauncherurl:https%3A%2F%2Fassetgame.roblox.com%2Fgame%2FPlaceLauncher.ashx%3Frequest%3DRequestGame%26browserTrackerId%3D125283338949%26placeId%3D6447798030%26isPlayTogetherGame%3Dfalse+browsertrackerid:125283338949+robloxLocale:en_us+gameLocale:en_us+channel: | C:\Users\admin\AppData\Local\Roblox\Versions\version-1a42d2dceb424b0b\RobloxPlayerLauncher.exe | chrome.exe | ||||||||||||
User: admin Company: Roblox Corporation Integrity Level: MEDIUM Description: Roblox Exit code: 0 Version: 1, 6, 0, 5090219 Modules
| |||||||||||||||
| 436 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1052,16751803291629401274,10121511774458577501,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2904 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 468 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1052,16751803291629401274,10121511774458577501,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2368 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 576 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1052,16751803291629401274,10121511774458577501,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3092 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1012 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1052,16751803291629401274,10121511774458577501,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2232 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1036 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1052,16751803291629401274,10121511774458577501,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3852 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
45 615
Read events
44 758
Write events
690
Delete events
167
Modification events
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Synapse X.zip | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
11
Suspicious files
389
Text files
306
Unknown types
26
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.1035\Synapse X\exploit-main.dll | executable | |
MD5:— | SHA256:— | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.1035\Synapse X\Scripts\Freecam Script.txt | text | |
MD5:— | SHA256:— | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.1035\Synapse X\Scripts\BrokenBonesIV.txt | text | |
MD5:328A2D6EE854477896ECDF75E0F1FC6E | SHA256:53F93CE6CBE9EBB909AFABF70A419823AE49B1EB55DFAE77C6C65BECF0466462 | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.1035\Synapse X\Scripts\PrisonHaxx.lua | text | |
MD5:6DF7A7B99E65085B2576FC284B310F29 | SHA256:D1F9B96C3FA1E6CBAC133CFB11094FD4BD2CDAC9FCF02E3D33786F22A1337A17 | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.1035\Synapse X\Scripts\Anti-AFK.txt | text | |
MD5:E79F153A0CF5BADDEDD0309AD8177EF2 | SHA256:BF75DF2DD2558A5804E7E2FEAA168064B2DA3EFA652F0355E949117EB198F187 | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.1035\Synapse X\Scripts\Dex Explorer.txt | text | |
MD5:5C3866FD535E0D8753999ABAD37CC58A | SHA256:9CF75612842A8527D3E7C112690B5A0758FB996D536E0D2218CB6C63846A1FC0 | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.1035\Synapse X\Scripts\Weightlifting Simulator 2 GUI.txt | text | |
MD5:32CB10AE81C71021CFBF55B9C448A49B | SHA256:86CDA24B60F0C217138E757F2860D630FA1F11B4B1A8A82EC2C8397565A67BB3 | |||
| 2996 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRD781.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.1035\Synapse X\Scripts\[FE] Chat Bypass.txt | text | |
MD5:5DF5AA257054B58592D33FF5F3A2E28E | SHA256:C36B9D4F6DA0084F066DCADC38C72EB2578E1D8157B90E45958152DEAC992141 | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.1035\Synapse X\Scripts\MM2.lua | text | |
MD5:933DFC531AEAC6B3F8C80CD013B9F585 | SHA256:243263E0349B1690CD242666116AE6BD79E3E1271C95D8D200AE0ABFAF77E6FA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
35
TCP/UDP connections
159
DNS requests
119
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
860 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | — | — | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 5.63 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 43.4 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 88.5 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 9.69 Kb | whitelisted |
2760 | RobloxPlayerLauncher.exe | GET | 200 | 192.124.249.22:80 | http://ocsp.godaddy.com//MEowSDBGMEQwQjAJBgUrDgMCGgUABBS2CA1fbGt26xPkOKX4ZguoUjM0TgQUQMK9J47MNIMwojPX%2B2yz8LQsgM4CCQC7VHqEx4vVjg%3D%3D | US | der | 1.74 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 9.70 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 9.69 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 20.9 Kb | whitelisted |
2760 | RobloxPlayerLauncher.exe | GET | 200 | 192.124.249.22:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | US | der | 1.69 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3072 | chrome.exe | 142.250.186.110:443 | encrypted-tbn0.gstatic.com | Google Inc. | US | whitelisted |
3072 | chrome.exe | 142.250.186.106:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3072 | chrome.exe | 142.250.184.227:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3072 | chrome.exe | 142.250.181.228:443 | www.google.com | Google Inc. | US | whitelisted |
3072 | chrome.exe | 92.123.194.146:443 | js.rbxcdn.com | Akamai International B.V. | — | suspicious |
3072 | chrome.exe | 142.250.181.227:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
3072 | chrome.exe | 104.18.24.64:443 | roblox-api.arkoselabs.com | Cloudflare Inc | US | suspicious |
3072 | chrome.exe | 142.250.186.174:443 | apis.google.com | Google Inc. | US | whitelisted |
3072 | chrome.exe | 92.123.224.152:443 | css.rbxcdn.com | Akamai International B.V. | — | unknown |
3072 | chrome.exe | 142.250.185.138:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
clients2.google.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
Threats
Process | Message |
|---|---|
RobloxPlayerBeta.exe | 2022-01-24T21:26:39.029Z,0.029816,0b50,6 [FLog::Output] RobloxGitHash: 6808cda89fc399b0dd5f649acece51d2cd151e77 |
RobloxPlayerBeta.exe | |
RobloxPlayerBeta.exe | 2022-01-24T21:26:39.030Z,0.030816,0b50,6 [FLog::Output] The channel is production |
RobloxPlayerBeta.exe | |
RobloxPlayerBeta.exe | 2022-01-24T21:26:39.103Z,0.103298,0b50,6 [FLog::Error] Test log: Map check complete and successful! |
RobloxPlayerBeta.exe | |
RobloxPlayerBeta.exe | 2022-01-24T21:26:39.103Z,0.103298,0b50,6 [FLog::Error] Dynamic initializer test result: SUCCESS |
RobloxPlayerBeta.exe | |
RobloxPlayerBeta.exe | 2022-01-24T21:26:39.103Z,0.103796,0b50,6 [FLog::Output] TaskSchedulerMk2::applyAsyncTaskThreadCount( 3 ) <req: 0 active: 0> |
RobloxPlayerBeta.exe | |