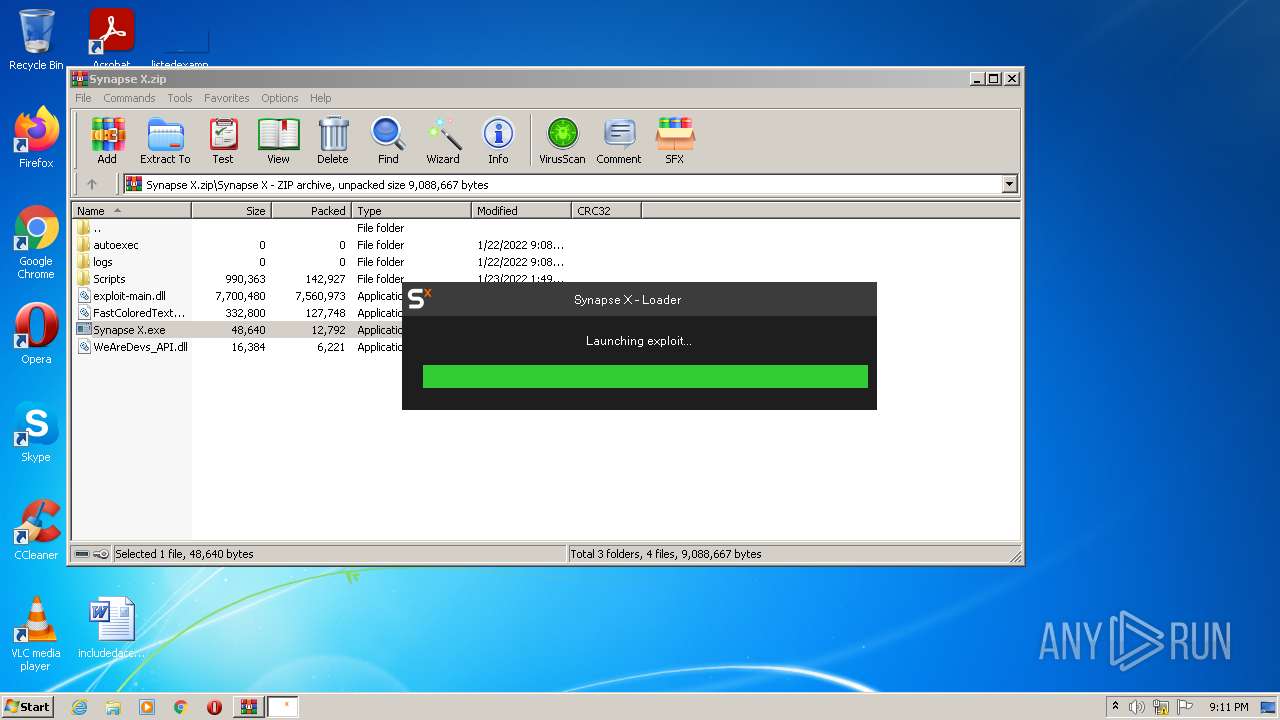
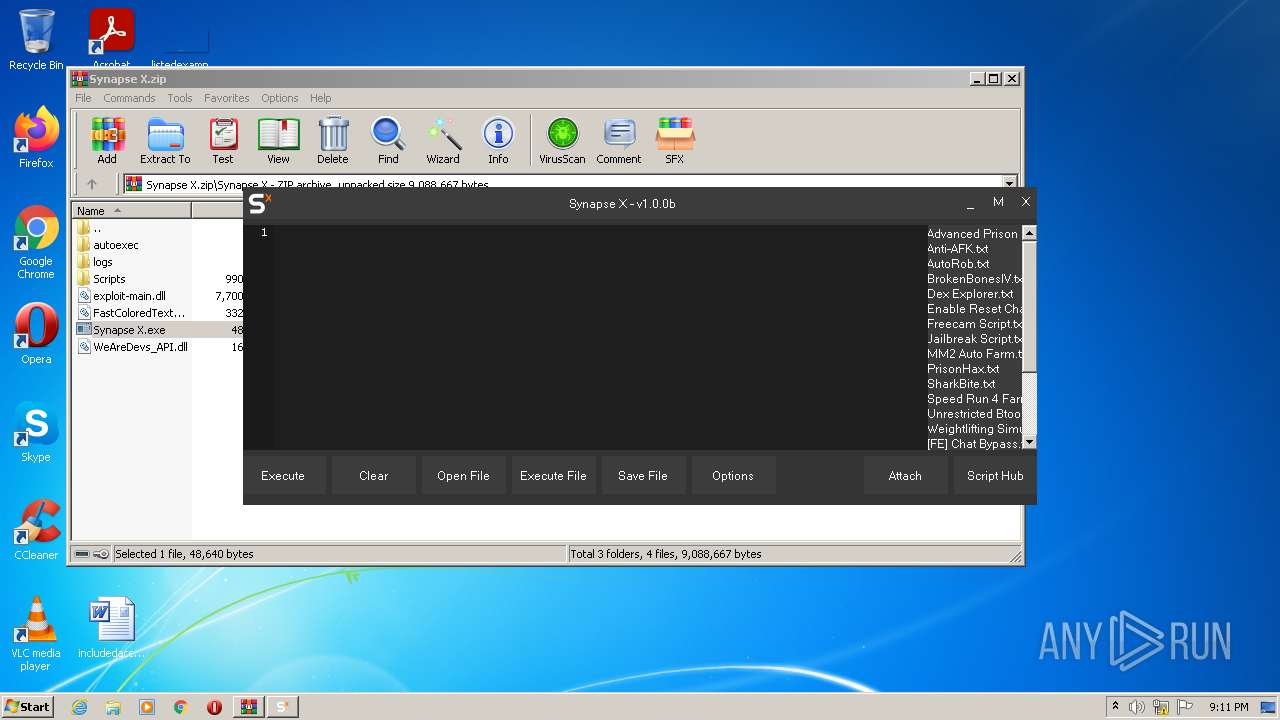
| File name: | Synapse X.zip |
| Full analysis: | https://app.any.run/tasks/4349b885-c4d5-4a15-bb5d-44e010969060 |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 21:10:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 2A4F3913C992A31E7D0CC45BE18DF119 |
| SHA1: | 5DA22BA82349EFE200A564232C2133C2F5528F51 |
| SHA256: | 1B72E303855D6CD69DC71B24783F0D43F0C58B2B6C83973EE672174B601BB51D |
| SSDEEP: | 196608:15noJeE1+j/4bT3tdQhiKHm9EukBj7yQg5ejJNjjm+OjRRwiq:XoT10YPKHm9SBjBg5eTQjRRS |
MALICIOUS
Application was dropped or rewritten from another process
- Synapse X.exe (PID: 3588)
Loads dropped or rewritten executable
- Synapse X.exe (PID: 3588)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 3856)
- Synapse X.exe (PID: 3588)
Checks supported languages
- WinRAR.exe (PID: 3856)
- Synapse X.exe (PID: 3588)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3856)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3856)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3856)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2380)
INFO
Manual execution by user
- chrome.exe (PID: 2380)
Checks supported languages
- chrome.exe (PID: 2380)
- chrome.exe (PID: 516)
- chrome.exe (PID: 2788)
- chrome.exe (PID: 3976)
- chrome.exe (PID: 2324)
- chrome.exe (PID: 3144)
- chrome.exe (PID: 3448)
- chrome.exe (PID: 3596)
- chrome.exe (PID: 3424)
- chrome.exe (PID: 2848)
- chrome.exe (PID: 3124)
- chrome.exe (PID: 4056)
- chrome.exe (PID: 2212)
- chrome.exe (PID: 1304)
- chrome.exe (PID: 1660)
- chrome.exe (PID: 3064)
- chrome.exe (PID: 1296)
- chrome.exe (PID: 2404)
- chrome.exe (PID: 1284)
- chrome.exe (PID: 2072)
- chrome.exe (PID: 2916)
- chrome.exe (PID: 3804)
- chrome.exe (PID: 3528)
- chrome.exe (PID: 2072)
- chrome.exe (PID: 3632)
- chrome.exe (PID: 2564)
- chrome.exe (PID: 1632)
- chrome.exe (PID: 3212)
- chrome.exe (PID: 3336)
- chrome.exe (PID: 2560)
Reads the computer name
- chrome.exe (PID: 2380)
- chrome.exe (PID: 3976)
- chrome.exe (PID: 2788)
- chrome.exe (PID: 3596)
- chrome.exe (PID: 2072)
Reads the hosts file
- chrome.exe (PID: 2380)
- chrome.exe (PID: 2788)
Application launched itself
- chrome.exe (PID: 2380)
Reads settings of System Certificates
- chrome.exe (PID: 2788)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | Synapse X/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2022:01:23 22:19:07 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 10 |
Total processes
66
Monitored processes
32
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=86.0.4240.198 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6e8ed988,0x6e8ed998,0x6e8ed9a4 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1284 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1064,3124633276037507271,11431958480988616683,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3720 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1296 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1064,3124633276037507271,11431958480988616683,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3696 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1304 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1064,3124633276037507271,11431958480988616683,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3160 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1632 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1064,3124633276037507271,11431958480988616683,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=27 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3028 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1660 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1064,3124633276037507271,11431958480988616683,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3044 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2072 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1064,3124633276037507271,11431958480988616683,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3912 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2072 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1064,3124633276037507271,11431958480988616683,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4272 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2212 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1064,3124633276037507271,11431958480988616683,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3012 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2324 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1064,3124633276037507271,11431958480988616683,131072 --enable-features=PasswordImport --lang=en-US --instant-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1932 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
12 956
Read events
12 875
Write events
81
Delete events
0
Modification events
| (PID) Process: | (3856) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3856) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3856) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3856) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3856) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3856) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Synapse X.zip | |||
| (PID) Process: | (3856) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3856) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3856) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3856) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
4
Suspicious files
196
Text files
95
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3856 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3856.32111\Synapse X\exploit-main.dll | executable | |
MD5:— | SHA256:— | |||
| 3856 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3856.32111\Synapse X\Scripts\Freecam Script.txt | text | |
MD5:— | SHA256:— | |||
| 3856 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3856.32111\Synapse X\Scripts\MM2 Auto Farm.txt | text | |
MD5:0C670D854E4A0E413D1C74346393BF0C | SHA256:9C92799CDF85BB9F5C34593D6CB5F6CB37846B337219DD7FBB7CBBD46AF57A7A | |||
| 3856 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3856.32111\Synapse X\Scripts\Dex Explorer.txt | text | |
MD5:5C3866FD535E0D8753999ABAD37CC58A | SHA256:9CF75612842A8527D3E7C112690B5A0758FB996D536E0D2218CB6C63846A1FC0 | |||
| 3856 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3856.32111\Synapse X\FastColoredTextBox.dll | executable | |
MD5:ADAC0CEE5CC4DE7D4046AE1243E41BF0 | SHA256:68D0E444C0B27552D2CB86501DCB7DB3FD64B82D966E9708DB0408EC1BA38C79 | |||
| 3856 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3856.32111\Synapse X\Scripts\Enable Reset Character.txt | text | |
MD5:72AE47DEEEC8069BE19F0A0E2C1A269D | SHA256:E701732CB1F0E5774C9468E09BD8C1D635801AA1AB832CF85F3D4C2D34627420 | |||
| 3856 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3856.32111\Synapse X\Scripts\Jailbreak Script.txt | text | |
MD5:809E8C36F51129E4D7EAC7CFD97702A2 | SHA256:9293C176F8E8FA0449B5EEAB00079F82CC3CA168CC44063941E40D9C4D25460B | |||
| 3856 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3856.32111\Synapse X\Scripts\Anti-AFK.txt | text | |
MD5:E79F153A0CF5BADDEDD0309AD8177EF2 | SHA256:BF75DF2DD2558A5804E7E2FEAA168064B2DA3EFA652F0355E949117EB198F187 | |||
| 3856 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3856.32111\Synapse X\Scripts\AutoRob.txt | text | |
MD5:B5B70D071D096BC2F28C04175B0C59B6 | SHA256:7B251A346721DA706A23CF50A9E69AA3FE45523075D6A1D46D138A64EF9ACC9E | |||
| 2380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-61EF15F0-94C.pma | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
49
DNS requests
33
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2788 | chrome.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | crx | 242 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2788 | chrome.exe | 142.250.185.227:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2788 | chrome.exe | 142.250.185.163:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
2788 | chrome.exe | 172.217.18.110:443 | apis.google.com | Google Inc. | US | whitelisted |
2788 | chrome.exe | 142.250.186.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2788 | chrome.exe | 142.250.186.161:443 | lh5.googleusercontent.com | Google Inc. | US | whitelisted |
2788 | chrome.exe | 92.123.194.172:443 | js.rbxcdn.com | Akamai International B.V. | — | suspicious |
2788 | chrome.exe | 142.250.186.163:443 | update.googleapis.com | Google Inc. | US | whitelisted |
2788 | chrome.exe | 142.250.186.46:443 | clients2.google.com | Google Inc. | US | whitelisted |
2788 | chrome.exe | 142.250.186.42:443 | content-autofill.googleapis.com | Google Inc. | US | whitelisted |
2788 | chrome.exe | 142.250.186.78:443 | consent.youtube.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| malicious |
clients2.google.com |
| whitelisted |
accounts.google.com |
| shared |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
lh5.googleusercontent.com |
| whitelisted |