| File name: | 애플고딕.js |
| Full analysis: | https://app.any.run/tasks/2fd9ac98-4f1a-47a5-b28b-b8cf2f30ef5b |
| Verdict: | Malicious activity |
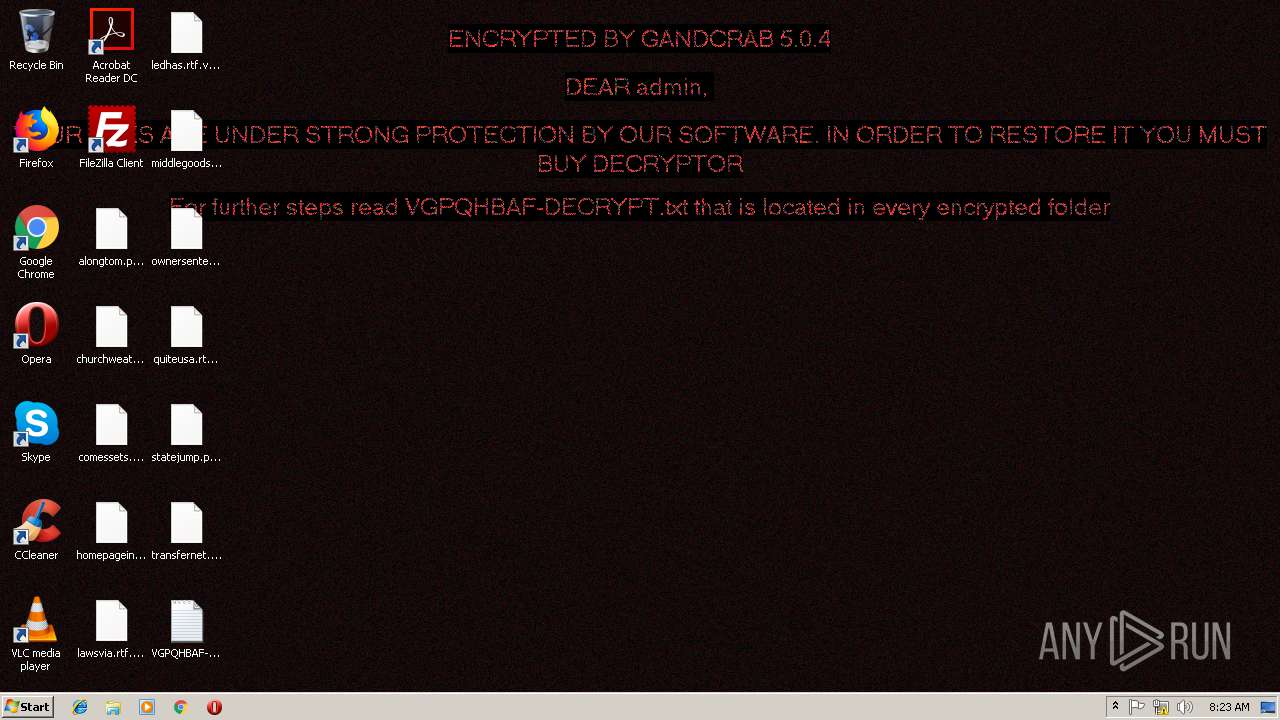
| Threats: | GandCrab is probably one of the most famous Ransomware. A Ransomware is a malware that asks the victim to pay money in order to restore access to encrypted files. If the user does not cooperate the files are forever lost. |
| Analysis date: | December 14, 2018, 08:22:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 7240C414E14963D219D0F363AEFCE28A |
| SHA1: | EE63A6281B970CE36B0054D36656F0949F0445EE |
| SHA256: | 1B5A2162D5C07BCB49965764E3A8450D134D86960B9FB7D5D68547F8C279B204 |
| SSDEEP: | 24576:t0Ew/XgLpnH7hIYEoluDWV/m2ja6R/WrPUyaytRMInw76ARzO89EePW5Qp40Pgaj:R |
MALICIOUS
GandCrab keys found
- powershell.exe (PID: 2384)
Actions looks like stealing of personal data
- powershell.exe (PID: 2384)
Writes file to Word startup folder
- powershell.exe (PID: 2384)
Renames files like Ransomware
- powershell.exe (PID: 2384)
Deletes shadow copies
- powershell.exe (PID: 2384)
SUSPICIOUS
Creates files in the user directory
- WScript.exe (PID: 2996)
- powershell.exe (PID: 2384)
Executes PowerShell scripts
- WScript.exe (PID: 2996)
Reads the cookies of Mozilla Firefox
- powershell.exe (PID: 2384)
Creates files like Ransomware instruction
- powershell.exe (PID: 2384)
INFO
Dropped object may contain TOR URL's
- powershell.exe (PID: 2384)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
36
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2384 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass -Command "IEX (([System.IO.File]::ReadAllText('C:\Users\admin\AppData\Roaming\nxfzgakogffcxdj.log')).Replace('?',''));" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WScript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2964 | "C:\Windows\system32\wbem\wmic.exe" shadowcopy delete | C:\Windows\system32\wbem\wmic.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 2147749908 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2996 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\애플고딕.js" | C:\Windows\System32\WScript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
369
Read events
289
Write events
80
Delete events
0
Modification events
| (PID) Process: | (2996) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2996) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2384) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2384) powershell.exe | Key: | HKEY_CURRENT_USER\Software\ex_data\data |
| Operation: | write | Name: | ext |
Value: 2E00760067007000710068006200610066000000 | |||
| (PID) Process: | (2384) powershell.exe | Key: | HKEY_CURRENT_USER\Software\keys_data\data |
| Operation: | write | Name: | public |
Value: 0602000000A400005253413100080000010001003FABA53FB0EF8FE991439CD47D5A4C11D380A94774ECF237AC89B457F51D6EB5AAE666B4A536AC2319580A145F650547605D63C774DCF54B8A1C6E0F97722E4CFB92EA374274593B683870AA2E5E148FB001E048EA6D71A87DB051DFBB5E3D8B7AE7F1CEC4F29FAF6C95FE0FE7AC6AB04141B2DDF58EA60AF0C15BF10C7015D3B9FC98ADD2EC960FDFAB3C9E915E5E5AAFB79514D9BE69A73BC9B252947FDEC412BDBF8D4A1F5F3C558435065CB7D4FC0BC2AEF6641F01A8180C1D85B1755380E711254F7BF2393549C956849005DFE10164811E519B409E074EEC76C0A174250A5F24F18A4C85BE2F4298037F5958AF11E48F770AD6E5596AD66D704F5FEACC | |||
| (PID) Process: | (2384) powershell.exe | Key: | HKEY_CURRENT_USER\Software\keys_data\data |
| Operation: | write | Name: | private |
Value: 94040000BE9A536768FA617E720C4EDCD541ABEAF85F8D7FC46129DC7D575F49CE0B1E3706749C7FD255DF945E996C1A3ACC19DFCCA89E90A31646B94861708BF24CD6E34AE090FB5E3F40726D80B5358AA1C4A88692C5B774B0A3D993B9F309487216B063F4728116DC02A7B98F9C98F0663AE07CBAE299C24D74D728CA5A2C8CBD343676A36B998B826DC66EDD7FDF1C5916AAD6572A1AA44F3F7B2745CF0E7DC4BD8D3824508D5FFD269E1B565DA13E13B7BDB6181C0210CA8DB941C864624D310C9165E230ABCBF91861588E4891D38C763B71F9669DD41FA2BCFE3B1D9886CD0E147A94EA58F79F8164B62A3BA97CCC44625B2A6B513A5F8BB3E5AE6F1CF8C9BA827293DD97FDA928960D0374C90F0D10844EA24961496E84CE41B6213C412B8CD1D0D7C29689937D1632199DF736240220AB5FA7CB8FBED9E5F7CF9432697AE27E7583DEE85751C1099BF94C1FD31D0AEB83F9EA8E13F89FD885D7B6C78D03CBBF9747900871A152C672E71E5554F761627DDF782A4B1278CF2163DF53622E4D3D1A8335C800D9DCFBA9BBA4ED0085A56871B5C18AF430963B4A6943757AEE02C131185D4BA650A560C437482A8C19806AF2CA6647C0A673B5F22FD0699A3D0AD8F5FC74C20130A99B6BA61D51171CB071A2F4DE694D62BB816FF6124A27AA1061DF0E0730C0FB2F6A1A7E90F2AEBF404EFF149FE414406DEBE5ED0FC24C12528C7F7726B17AA3228683FC02F54D27AB36312C9C340BD4D47B8DD26D35F60FBB75F13A94F3FCA9D26724E57404F1334CB1BF19E2238C92DC77977173FB9DD1143DD33BF97CCB7C01DD60A86B9B475371FB257AEA11CACF17B59C5BBA300848E6AE48FB768E10173FB41444437E783C0AE843BECB8F369E67658583C8BCE8AE72739F251CB2DBB88FF568D81DA24E679BAC5F3C1867204FF3D03BEE7EEB1BB6407343E12B8A5A4063C4ED66B1A545FED1CA66212990F9E2A85E4AB2F8B770F5C39DC237005A5D61C26532D577471EAE2E4EF575EEB2DEC085C6447075D6370E4D5E16307C0BD5D084F252CF47E8E814A2C7BF25C1E3187D9F31164D4BD2B9CBDFCFF8AEA67F1FC784E1B7F155F393F1F437CB24661E675E2E8B900095AD51F0BCC8F40DBAA93F1CEDA178D03B7D4A669706C90CC1E622576D68E25CF23078DD37951C6FDDA47888EDE87EA1798749F503F001DF4539C8F878B6A7FEA96342A4D688E55622F28D61C2350965C3FD1300C43FD48ACD128FCEDED37D0350AA0A1BFF351FC6E1089FEB48670EEAEDEA5E0DFD0CFAD28206FDBCE84F6CB2EF26E023C2708EBE1E39757BDF51E9D35680D9314D154AE605DA9EC53F42769434F0683F03DFA053328334EFEFE1C9807A4585773A0CB6D5235DEB8DB241626E0A6587881D47F592259D17479CF1F23FA4E803D4FA704F68C60E24323D369DCF3A5C1D9DEBED9399AC3A4A0449D4D1ED344596313B0625B7409444FCE6DA83AA76BF42E4321E9F82CA41D6A47A9193EFBFC1FC1084818182837FD4A37131F310F4C56DA35DD129E0689C5B903AFDDDE190F9AEF6336F746D7167908A7446F3A9290D018ED11E1FD2B2E49EA61A37D32EB90BC290BD641E2149EE387FE04AFC05A50C6CBC2582618BCCF4882D2EC37E81DC0DEF7F68620B760DEB0E67D9071301F262D130042AE35095F7D54AAD954F2C10F722DF0A4CD3E09F5A7859ED19D1CB924E8A04421C8132C2AB653618A206F56EDAC489C69FD5CE9102AC63ABF1023A11799AE0E0D14821F243DAC42E4307D8BC80E59CB9DB732D94E4F53A42B1502DC70269669D4BD123E0FAE8C7E9F25C6919782945AD1565B195C4D4429E7507FF64DBE5A6A9CB2E1ED56DDDEB1CEFB12E740AA3423528D3E3B041E40C6820603DA5FCB324DD96932C1DFA86967D555195D2C94D8873520110D14E516AAF75CC1611C0AF516E4C26FCF1C7AAC539D9E548A258757BBAC18EA0F979BED0AAB572EA4A43646174051DE59F1F032364544FFF04F704007D17362928BA4CFE936FDA8FEDFC404AE6ABEAF8D427C3C73D372BED3F37F5996CA2056908A7E04B38E5D3BC6196B2322C5FB6ECC8076F0C205880F73A05E9CB732B1D770D4162C03423D3CB1A31AAD1843CBA92FE1DEE019DB47E8096BE6E5AC6BFB053510AC035620ED353C41C912B94146FE93593EC8084E84E72F8F110D87DA9C85E3D0020C9614DEB7DAB805F92D0A142E838079913CD67007081580C37C96EDF3C98F3FD6C6A5A7BDADD2CF33D7570A535403C856107504B50E10F894D38A24F3D384A7C1E0A3FC555C4A7A3B703DED3B33B921716EF9C9AD7FB5F1AC2C3BEE031A010340BF766819FEC7C609724C47F359B5696FDF2570952199125A151E6FD41C3F7 | |||
| (PID) Process: | (2384) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2384) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2384) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2384) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
0
Suspicious files
159
Text files
127
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2384 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\PHONCQYGN9E4AC944FB3.temp | — | |
MD5:— | SHA256:— | |||
| 2384 | powershell.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | — | |
MD5:— | SHA256:— | |||
| 2384 | powershell.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\JSCache\GlobData | — | |
MD5:— | SHA256:— | |||
| 2384 | powershell.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\JSCache\GlobSettings | — | |
MD5:— | SHA256:— | |||
| 2384 | powershell.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\addressbook.acrodata | — | |
MD5:— | SHA256:— | |||
| 2384 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF19b0d7.TMP | binary | |
MD5:— | SHA256:— | |||
| 2384 | powershell.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\CRLCache\0FDED5CEB68C302B1CDB2BDDD9D0000E76539CB0.crl | — | |
MD5:— | SHA256:— | |||
| 2384 | powershell.exe | C:\Users\admin\VGPQHBAF-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 2384 | powershell.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\CRLCache\CE338828149963DCEA4CD26BB86F0363B4CA0BA5.crl | — | |
MD5:— | SHA256:— | |||
| 2384 | powershell.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\VGPQHBAF-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2384 | powershell.exe | GET | — | 78.46.77.98:80 | http://www.2mmotorsport.biz/ | DE | — | — | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2384 | powershell.exe | 78.46.77.98:80 | www.2mmotorsport.biz | Hetzner Online GmbH | DE | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.2mmotorsport.biz |
| unknown |