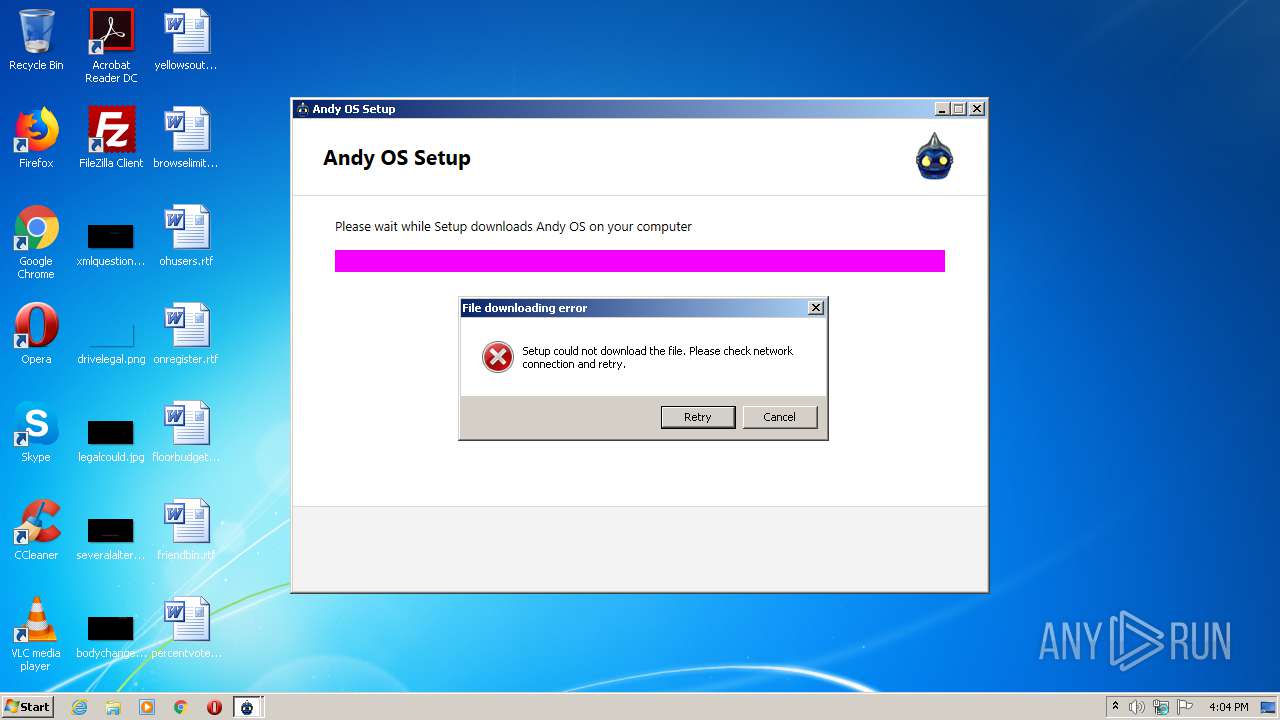
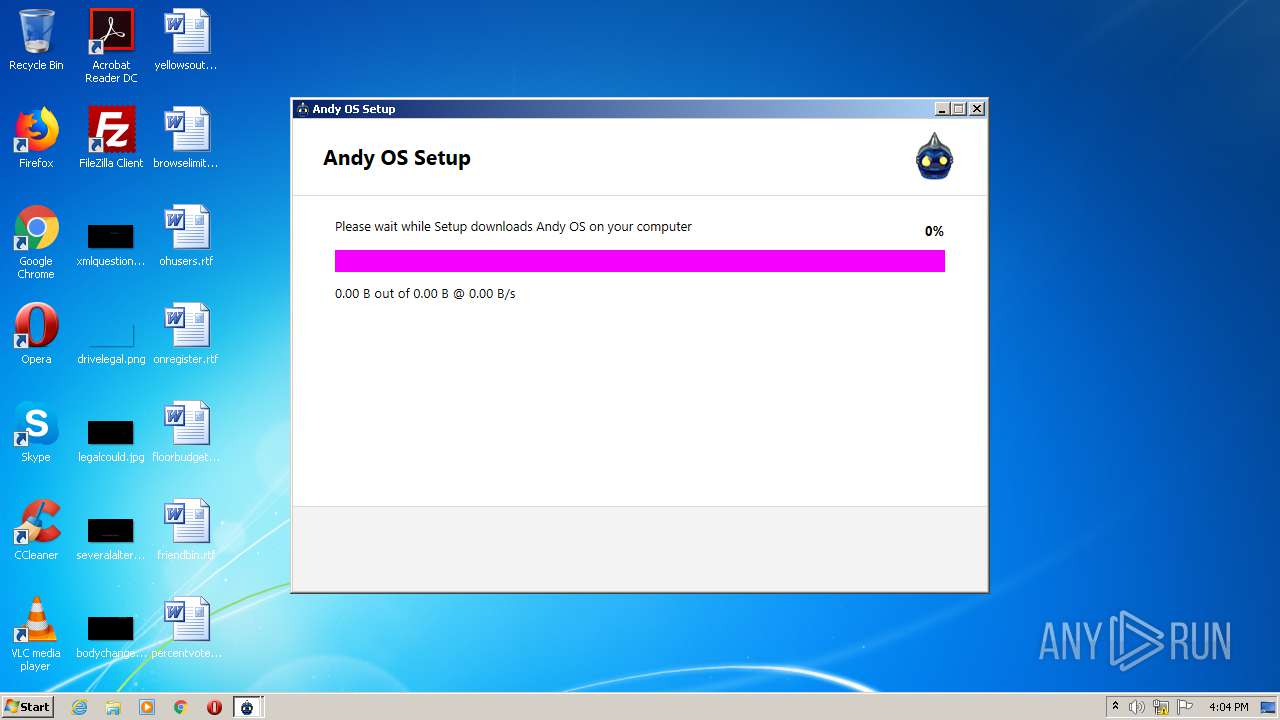
| File name: | Andy_47.260_1096_26_x64.exe |
| Full analysis: | https://app.any.run/tasks/57f435c6-87b2-4a37-8e22-518c18c1629b |
| Verdict: | Malicious activity |
| Analysis date: | May 21, 2021, 15:03:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | BF8EF7F57BA2FE1228EEEBF31AADE0B3 |
| SHA1: | 9082FDB033E4BFF0B94F6FFDA92ED07E41E11B31 |
| SHA256: | 1B1AB12B84C21384DA162AC9E17ACC6A40540779DB21C14BE3FCA6F9C3031CF9 |
| SSDEEP: | 49152:KG5UfgZ+QJLD1PqmbOw4rhWwFJhqnN3sXRCFKJcidM8ZUoXyPQ/NGxAd20bqbmJh:KG5QgZ+G/xqC6nJYm+n8ZUc9AbIh |
MALICIOUS
Application was dropped or rewritten from another process
- GenericSetup.exe (PID: 2880)
- installer.exe (PID: 1724)
Drops executable file immediately after starts
- Andy_47.260_1096_26_x64.exe (PID: 748)
Loads dropped or rewritten executable
- installer.exe (PID: 1724)
- GenericSetup.exe (PID: 2880)
Actions looks like stealing of personal data
- GenericSetup.exe (PID: 2880)
Changes settings of System certificates
- GenericSetup.exe (PID: 2880)
SUSPICIOUS
Drops a file with a compile date too recent
- Andy_47.260_1096_26_x64.exe (PID: 748)
Drops a file that was compiled in debug mode
- Andy_47.260_1096_26_x64.exe (PID: 748)
Drops a file with too old compile date
- Andy_47.260_1096_26_x64.exe (PID: 748)
Executable content was dropped or overwritten
- Andy_47.260_1096_26_x64.exe (PID: 748)
Adds / modifies Windows certificates
- GenericSetup.exe (PID: 2880)
Reads the Windows organization settings
- GenericSetup.exe (PID: 2880)
Reads Environment values
- GenericSetup.exe (PID: 2880)
Reads Windows owner or organization settings
- GenericSetup.exe (PID: 2880)
Searches for installed software
- GenericSetup.exe (PID: 2880)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
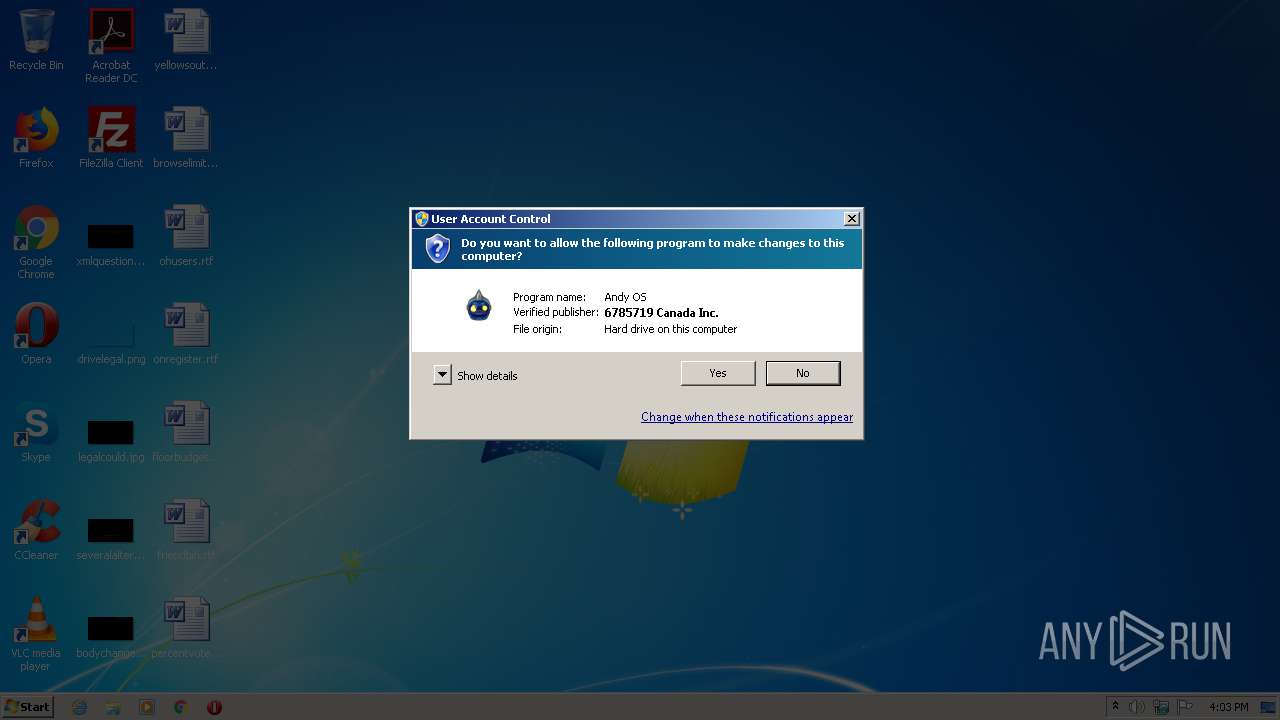
| ProductName: | Andy OS |
|---|---|
| OriginalFileName: | GenericSetup.exe |
| LegalCopyright: | Copyright © Adaware 2021 |
| InternalName: | 7zS.sfx |
| FileDescription: | Andy OS |
| CompanyName: | Andy OS Inc. |
| ProductVersion: | 1.0.0.0 |
| FileVersion: | 1.0.0.0 |
| CharacterSet: | Unicode |
| LanguageCode: | English (U.S.) |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Windows NT 32-bit |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 1.0.0.0 |
| FileVersionNumber: | 1.0.0.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 4 |
| ImageVersion: | - |
| OSVersion: | 4 |
| EntryPoint: | 0x148d4 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 404992 |
| CodeSize: | 104448 |
| LinkerVersion: | 6 |
| PEType: | PE32 |
| TimeStamp: | 2011:04:18 20:54:06+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Total processes
44
Monitored processes
4
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 748 | "C:\Users\admin\AppData\Local\Temp\Andy_47.260_1096_26_x64.exe" | C:\Users\admin\AppData\Local\Temp\Andy_47.260_1096_26_x64.exe | explorer.exe | ||||||||||||
User: admin Company: Andy OS Inc. Integrity Level: HIGH Description: Andy OS Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1724 | .\installer.exe | C:\Users\admin\AppData\Local\Temp\7zSCE2CDA95\installer.exe | Andy_47.260_1096_26_x64.exe | ||||||||||||
User: admin Company: adaware Integrity Level: HIGH Description: Andy OS Exit code: 0 Version: 6.2.0.4620 Modules
| |||||||||||||||
| 2668 | "C:\Users\admin\AppData\Local\Temp\Andy_47.260_1096_26_x64.exe" | C:\Users\admin\AppData\Local\Temp\Andy_47.260_1096_26_x64.exe | — | explorer.exe | |||||||||||
User: admin Company: Andy OS Inc. Integrity Level: MEDIUM Description: Andy OS Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2880 | "C:\Users\admin\AppData\Local\Temp\7zSCE2CDA95\GenericSetup.exe" C:\Users\admin\AppData\Local\Temp\7zSCE2CDA95\GenericSetup.exe hik=371d008b-9a62-400f-bb66-9c6937c1501b hmk=e00168c2-75b6-a117-16bf-50a05de7d133 hut=Admin hpp="QzpcVXNlcnNcYWRtaW5cQXBwRGF0YVxMb2NhbFxUZW1wXEFuZHlfNDcuMjYwXzEwOTZfMjZfeDY0LmV4ZQ==" hts=1621609419735 | C:\Users\admin\AppData\Local\Temp\7zSCE2CDA95\GenericSetup.exe | installer.exe | ||||||||||||
User: admin Company: Adaware Integrity Level: HIGH Description: Andy OS Exit code: 0 Version: 1.1.0.4620 Modules
| |||||||||||||||
Total events
3 357
Read events
3 337
Write events
20
Delete events
0
Modification events
| (PID) Process: | (2880) GenericSetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2880) GenericSetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (1724) installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1724) installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2880) GenericSetup.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2880) GenericSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\0563B8630D62D75ABBC8AB1E4BDFB5A899B24D43 |
| Operation: | write | Name: | Blob |
Value: 04000000010000001000000087CE0B7B2A0E4900E158719B37A893720F00000001000000140000006DCA5BD00DCF1C0F327059D374B29CA6E3C50AA60300000001000000140000000563B8630D62D75ABBC8AB1E4BDFB5A899B24D431D00000001000000100000004F5F106930398D09107B40C3C7CA8F1C0B000000010000001200000044006900670069004300650072007400000014000000010000001400000045EBA2AFF492CB82312D518BA7A7219DF36DC80F6200000001000000200000003E9099B5015E8F486C00BCEA9D111EE721FABA355A89BCF1DF69561E3DC6325C5300000001000000230000003021301F06096086480186FD6C020130123010060A2B0601040182373C0101030200C0090000000100000034000000303206082B0601050507030106082B0601050507030206082B0601050507030406082B0601050507030306082B06010505070308190000000100000010000000749966CECC95C1874194CA7203F9B6202000000001000000BB030000308203B73082029FA00302010202100CE7E0E517D846FE8FE560FC1BF03039300D06092A864886F70D01010505003065310B300906035504061302555331153013060355040A130C446967694365727420496E6331193017060355040B13107777772E64696769636572742E636F6D312430220603550403131B4469676943657274204173737572656420494420526F6F74204341301E170D3036313131303030303030305A170D3331313131303030303030305A3065310B300906035504061302555331153013060355040A130C446967694365727420496E6331193017060355040B13107777772E64696769636572742E636F6D312430220603550403131B4469676943657274204173737572656420494420526F6F7420434130820122300D06092A864886F70D01010105000382010F003082010A0282010100AD0E15CEE443805CB187F3B760F97112A5AEDC269488AAF4CEF520392858600CF880DAA9159532613CB5B128848A8ADC9F0A0C83177A8F90AC8AE779535C31842AF60F98323676CCDEDD3CA8A2EF6AFB21F25261DF9F20D71FE2B1D9FE1864D2125B5FF9581835BC47CDA136F96B7FD4B0383EC11BC38C33D9D82F18FE280FB3A783D6C36E44C061359616FE599C8B766DD7F1A24B0D2BFF0B72DA9E60D08E9035C678558720A1CFE56D0AC8497C3198336C22E987D0325AA2BA138211ED39179D993A72A1E6FAA4D9D5173175AE857D22AE3F014686F62879C8B1DAE45717C47E1C0EB0B492A656B3BDB297EDAAA7F0B7C5A83F9516D0FFA196EB085F18774F0203010001A3633061300E0603551D0F0101FF040403020186300F0603551D130101FF040530030101FF301D0603551D0E0416041445EBA2AFF492CB82312D518BA7A7219DF36DC80F301F0603551D2304183016801445EBA2AFF492CB82312D518BA7A7219DF36DC80F300D06092A864886F70D01010505000382010100A20EBCDFE2EDF0E372737A6494BFF77266D832E4427562AE87EBF2D5D9DE56B39FCCCE1428B90D97605C124C58E4D33D834945589735691AA847EA56C679AB12D8678184DF7F093C94E6B8262C20BD3DB32889F75FFF22E297841FE965EF87E0DFC16749B35DEBB2092AEB26ED78BE7D3F2BF3B726356D5F8901B6495B9F01059BAB3D25C1CCB67FC2F16F86C6FA6468EB812D94EB42B7FA8C1EDD62F1BE5067B76CBDF3F11F6B0C3607167F377CA95B6D7AF112466083D72704BE4BCE97BEC3672A6811DF80E70C3366BF130D146EF37F1F63101EFA8D1B256D6C8FA5B76101B1D2A326A110719DADE2C3F9C39951B72B0708CE2EE650B2A7FA0A452FA2F0F2 | |||
| (PID) Process: | (2880) GenericSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\8CF427FD790C3AD166068DE81E57EFBB932272D4 |
| Operation: | write | Name: | Blob |
Value: 0400000001000000100000004BE2C99196650CF40E5A9392A00AFEB20F0000000100000020000000FDE5F2D9CE2026E1E10064C0A468C9F355B90ACF85BAF5CE6F52D4016837FD940300000001000000140000008CF427FD790C3AD166068DE81E57EFBB932272D41D0000000100000010000000521B5F4582C1DCAAE381B05E37CA2D341400000001000000140000006A72267AD01EEF7DE73B6951D46C8D9F901266AB0B000000010000001800000045006E00740072007500730074002E006E0065007400000062000000010000002000000043DF5774B03E7FEF5FE40D931A7BEDF1BB2E6B42738C4E6D3841103D3AA7F33953000000010000002400000030223020060A6086480186FA6C0A010230123010060A2B0601040182373C0101030200C0090000000100000054000000305206082B0601050507030106082B0601050507030206082B0601050507030406082B0601050507030306082B06010505070308060A2B0601040182370A030406082B0601050507030606082B06010505070307190000000100000010000000FA46CE7CBB85CFB4310075313A09EE052000000001000000420400003082043E30820326A00302010202044A538C28300D06092A864886F70D01010B05003081BE310B300906035504061302555331163014060355040A130D456E74727573742C20496E632E31283026060355040B131F536565207777772E656E74727573742E6E65742F6C6567616C2D7465726D7331393037060355040B1330286329203230303920456E74727573742C20496E632E202D20666F7220617574686F72697A656420757365206F6E6C793132303006035504031329456E747275737420526F6F742043657274696669636174696F6E20417574686F72697479202D204732301E170D3039303730373137323535345A170D3330313230373137353535345A3081BE310B300906035504061302555331163014060355040A130D456E74727573742C20496E632E31283026060355040B131F536565207777772E656E74727573742E6E65742F6C6567616C2D7465726D7331393037060355040B1330286329203230303920456E74727573742C20496E632E202D20666F7220617574686F72697A656420757365206F6E6C793132303006035504031329456E747275737420526F6F742043657274696669636174696F6E20417574686F72697479202D20473230820122300D06092A864886F70D01010105000382010F003082010A0282010100BA84B672DB9E0C6BE299E93001A776EA32B895411AC9DA614E5872CFFEF68279BF7361060AA527D8B35FD3454E1C72D64E32F2728A0FF78319D06A808000451EB0C7E79ABF1257271CA3682F0A87BD6A6B0E5E65F31C77D5D4858D7021B4B332E78BA2D5863902B1B8D247CEE4C949C43BA7DEFB547D57BEF0E86EC279B23A0B55E250981632135C2F7856C1C294B3F25AE4279A9F24D7C6ECD09B2582E3CCC2C445C58C977A066B2A119FA90A6E483B6FDBD4111942F78F07BFF5535F9C3EF4172CE669AC4E324C6277EAB7E8E5BB34BC198BAE9C51E7B77EB553B13322E56DCF703C1AFAE29B67B683F48DA5AF624C4DE058AC64341203F8B68D946324A4710203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E041604146A72267AD01EEF7DE73B6951D46C8D9F901266AB300D06092A864886F70D01010B05000382010100799F1D96C6B6793F228D87D3870304606A6B9A2E59897311AC43D1F513FF8D392BC0F2BD4F708CA92FEA17C40B549ED41B9698333CA8AD62A20076AB59696E061D7EC4B9448D98AF12D461DB0A194647F3EBF763C1400540A5D2B7F4B59A36BFA98876880455042B9C877F1A373C7E2DA51AD8D4895ECABDAC3D6CD86DAFD5F3760FCD3B8838229D6C939AC43DBF821B653FA60F5DAAFCE5B215CAB5ADC6BC3DD084E8EA0672B04D393278BF3E119C0BA49D9A21F3F09B0B3078DBC1DC8743FEBC639ACAC5C21CC9C78DFF3B125808E6B63DEC7A2C4EFB8396CE0C3C69875473A473C293FF5110AC155401D8FC05B189A17F74839A49D7DC4E7B8A486F8B45F6 | |||
Executable files
22
Suspicious files
0
Text files
18
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 748 | Andy_47.260_1096_26_x64.exe | C:\Users\admin\AppData\Local\Temp\7zSCE2CDA95\Resources\OfferPage.html | html | |
MD5:— | SHA256:— | |||
| 748 | Andy_47.260_1096_26_x64.exe | C:\Users\admin\AppData\Local\Temp\7zSCE2CDA95\de\DevLib.resources.dll | executable | |
MD5:— | SHA256:— | |||
| 748 | Andy_47.260_1096_26_x64.exe | C:\Users\admin\AppData\Local\Temp\7zSCE2CDA95\Resources\style.css | text | |
MD5:— | SHA256:— | |||
| 748 | Andy_47.260_1096_26_x64.exe | C:\Users\admin\AppData\Local\Temp\7zSCE2CDA95\GenericSetup.exe.config | xml | |
MD5:377B63CF5F7E747B3B7727DDC4D4F288 | SHA256:54FC68E5B9AA2740F740D5BE1E7ED22F39379EAAD9FEE3358B298E39C69E85B1 | |||
| 748 | Andy_47.260_1096_26_x64.exe | C:\Users\admin\AppData\Local\Temp\7zSCE2CDA95\es\DevLib.resources.dll | executable | |
MD5:— | SHA256:— | |||
| 748 | Andy_47.260_1096_26_x64.exe | C:\Users\admin\AppData\Local\Temp\7zSCE2CDA95\Resources\images\loader.gif | image | |
MD5:2B26F73D382AB69F3914A7D9FDA97B0F | SHA256:A6A0B05B1D5C52303DD3E9E2F9CDA1E688A490FBE84EA0D6E22A051AB6EFD643 | |||
| 748 | Andy_47.260_1096_26_x64.exe | C:\Users\admin\AppData\Local\Temp\7zSCE2CDA95\BundleConfig.json | text | |
MD5:— | SHA256:— | |||
| 748 | Andy_47.260_1096_26_x64.exe | C:\Users\admin\AppData\Local\Temp\7zSCE2CDA95\Resources\tis\TranslateOfferTemplate.tis | text | |
MD5:551029A3E046C5ED6390CC85F632A689 | SHA256:7B8C76A85261C5F9E40E49F97E01A14320E9B224FF3D6AF8286632CA94CF96F8 | |||
| 748 | Andy_47.260_1096_26_x64.exe | C:\Users\admin\AppData\Local\Temp\7zSCE2CDA95\Resources\tis\Config.tis | text | |
MD5:FB1C09FC31CE983ED99D8913BB9F1474 | SHA256:293959C3F8EBB87BFFE885CE2331F0B40AB5666F9D237BE4791ED4903CE17BF4 | |||
| 748 | Andy_47.260_1096_26_x64.exe | C:\Users\admin\AppData\Local\Temp\7zSCE2CDA95\Resources\InstallingPage.html | html | |
MD5:402FF230A83D7B62E79FAB6C52CAF95A | SHA256:EB4F74678C8D678180B7E9F6BE5ABEED7D9250E86C6F5D5A719CD7849934746D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
47
DNS requests
5
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2880 | GenericSetup.exe | GET | 404 | 52.0.15.144:80 | http://dl.andyroid.net/andy_latest.exe | US | xml | 341 b | suspicious |
2880 | GenericSetup.exe | GET | — | 52.0.15.144:80 | http://dl.andyroid.net/andy_latest.exe | US | — | — | suspicious |
2880 | GenericSetup.exe | GET | 404 | 52.0.15.144:80 | http://dl.andyroid.net/andy_latest.exe | US | xml | 341 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2880 | GenericSetup.exe | 104.16.236.79:443 | sos.adaware.com | Cloudflare Inc | US | shared |
— | — | 104.18.87.101:443 | flow.lavasoft.com | Cloudflare Inc | US | shared |
2880 | GenericSetup.exe | 104.18.87.101:443 | flow.lavasoft.com | Cloudflare Inc | US | shared |
2880 | GenericSetup.exe | 52.0.15.144:80 | dl.andyroid.net | Amazon.com, Inc. | US | suspicious |
2880 | GenericSetup.exe | 52.239.214.132:443 | offerservicefallback.blob.core.windows.net | Microsoft Corporation | US | whitelisted |
1724 | installer.exe | 104.18.87.101:443 | flow.lavasoft.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
flow.lavasoft.com |
| whitelisted |
www.google.com |
| malicious |
sos.adaware.com |
| whitelisted |
offerservicefallback.blob.core.windows.net |
| suspicious |
dl.andyroid.net |
| suspicious |
Threats
3 ETPRO signatures available at the full report