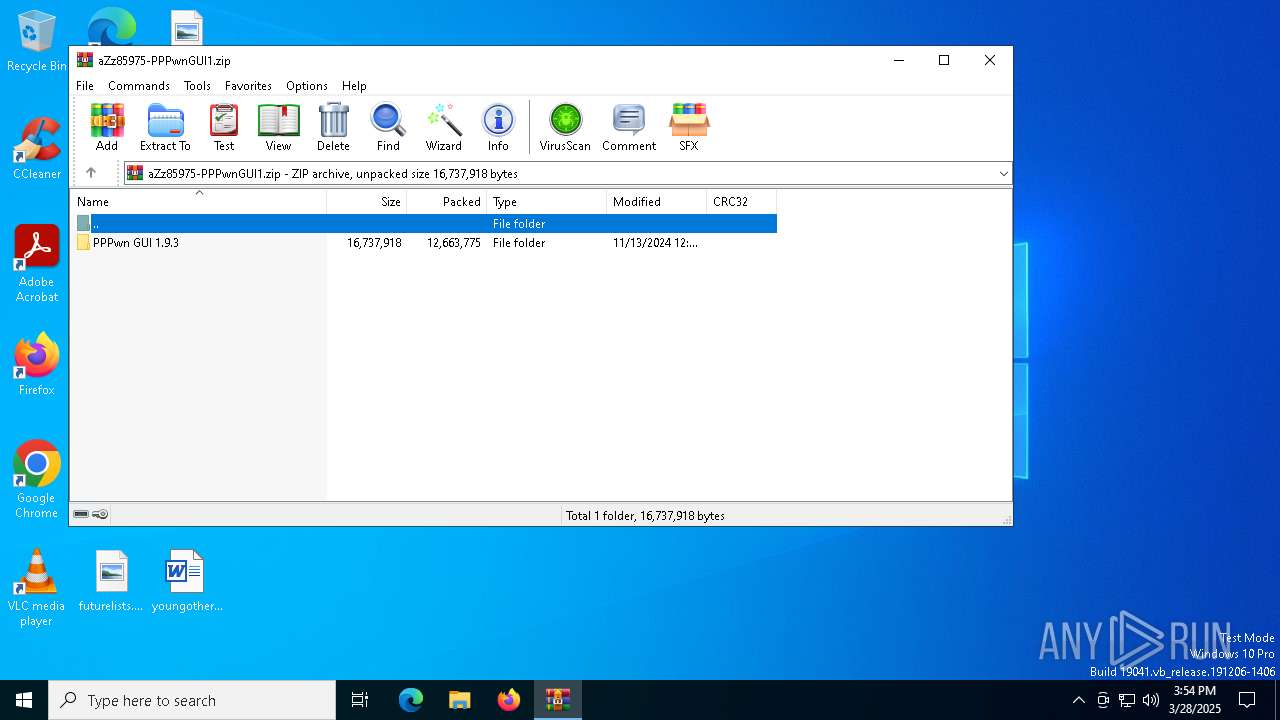
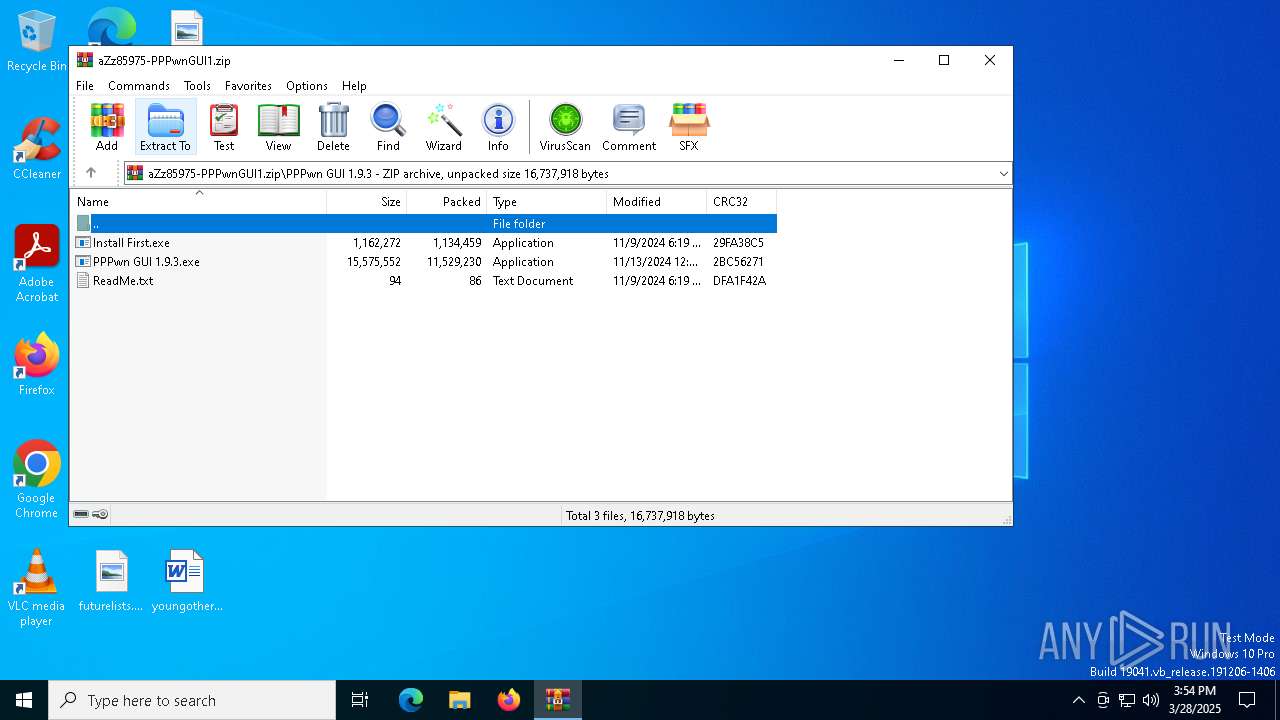
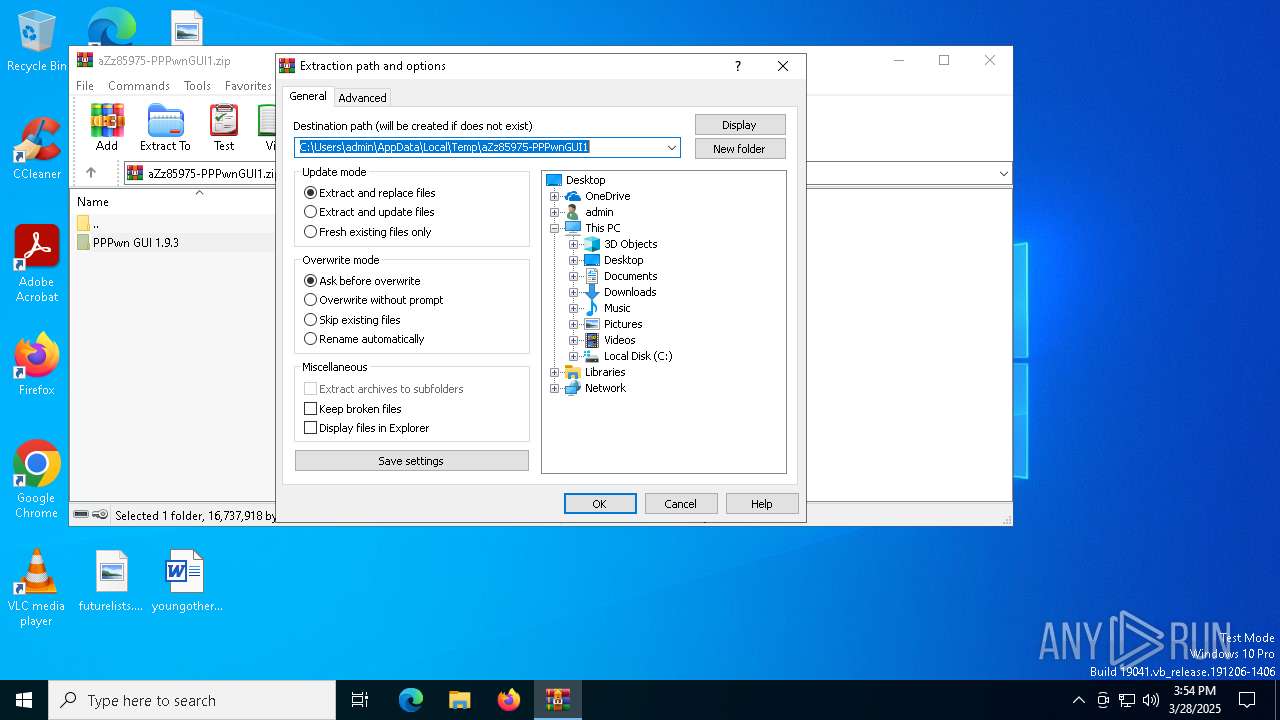
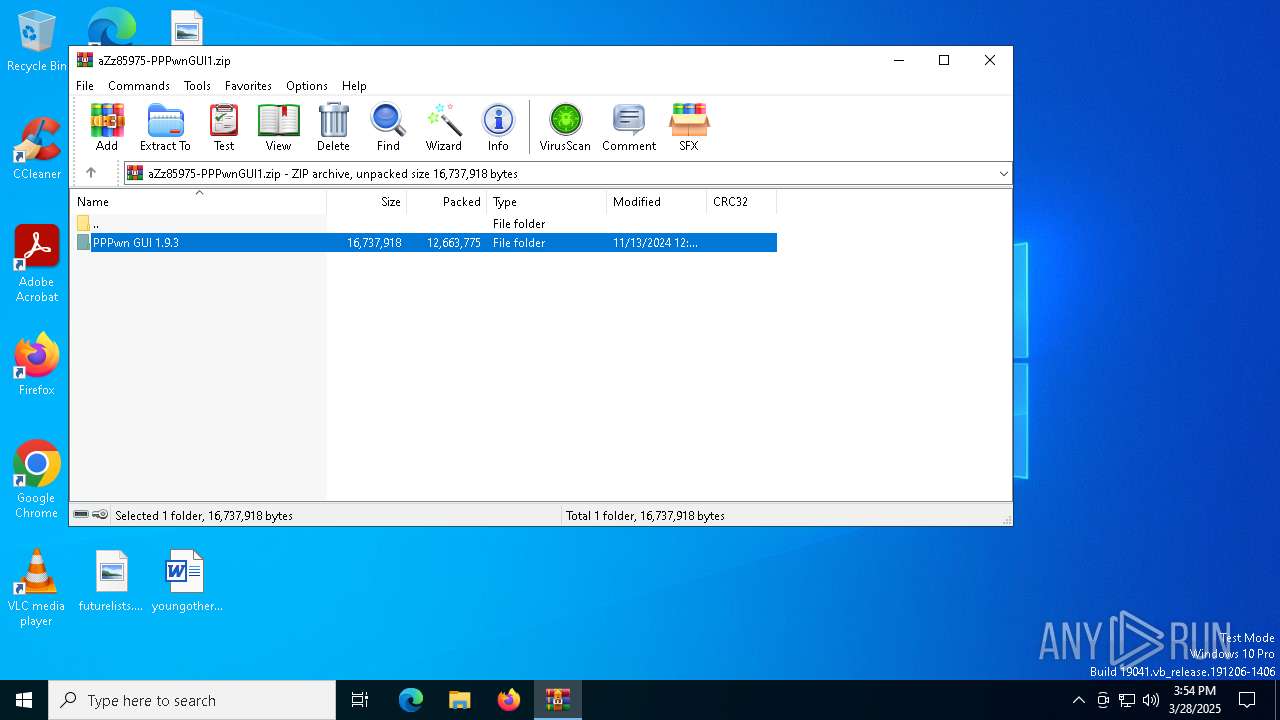
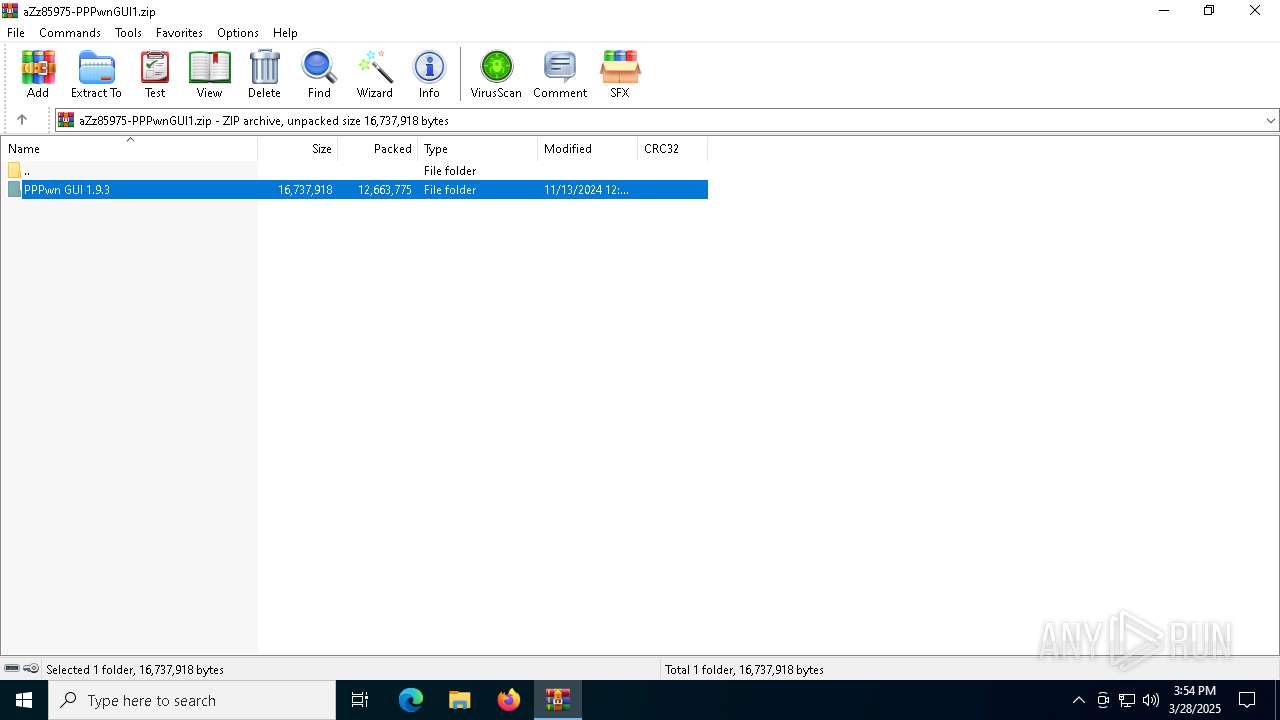
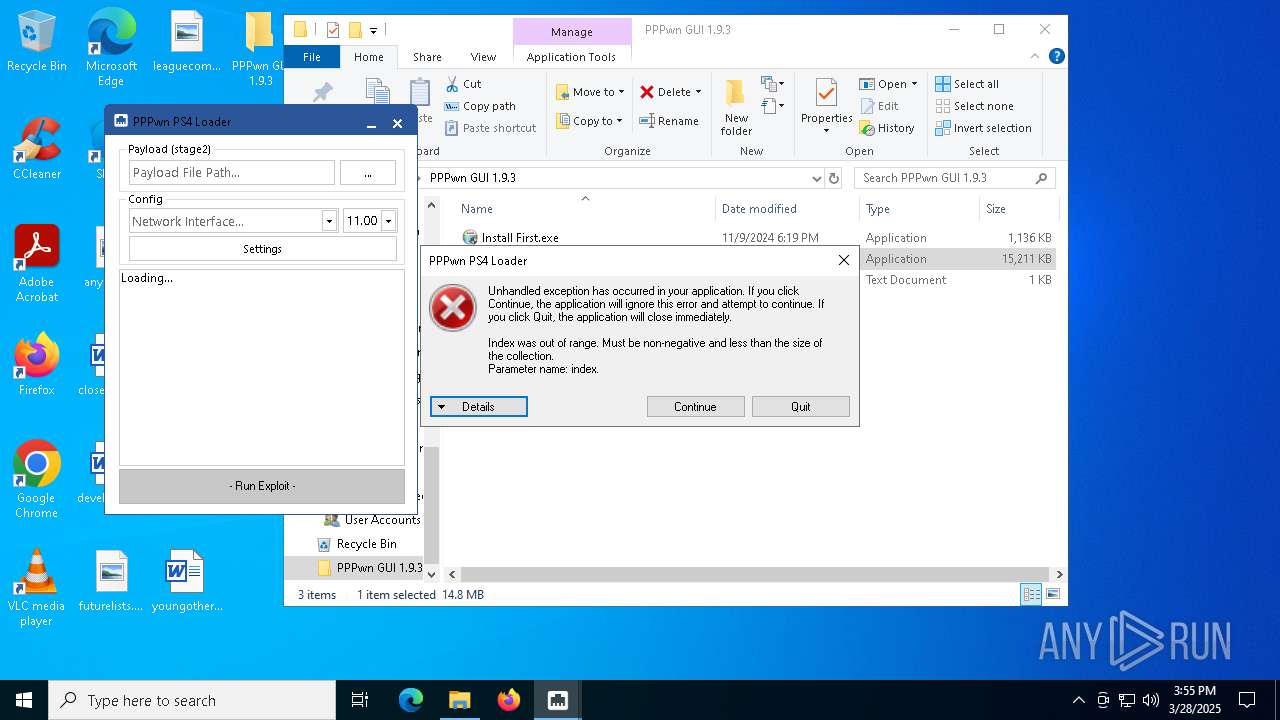
| download: | /aZz85975-PPPwnGUI1.zip |
| Full analysis: | https://app.any.run/tasks/7789b0e4-1bf1-4a70-b72d-50deaf0a7fd2 |
| Verdict: | Malicious activity |
| Analysis date: | March 28, 2025, 15:54:07 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 40361B86AB88202C0A4B8FC9CCA02B8E |
| SHA1: | F46487D8A1C1504F1CB125546BD8C8476367D474 |
| SHA256: | 1B120DB91276268A5629905DF45FA12E8DADA0F0BEC801676C950B177FF59AB3 |
| SSDEEP: | 98304:hFYAsoIFSe068mMtc1N7slkjcRZ6q0zmh6G7TRHryNWvv7iiSZJ+gH3yJmyX+hoe:S0x+QFImeVBbn1CjqLjN8UBZV |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 5164)
- powershell.exe (PID: 7632)
- powershell.exe (PID: 7856)
- powershell.exe (PID: 5436)
- powershell.exe (PID: 6476)
- powershell.exe (PID: 5576)
SUSPICIOUS
Executable content was dropped or overwritten
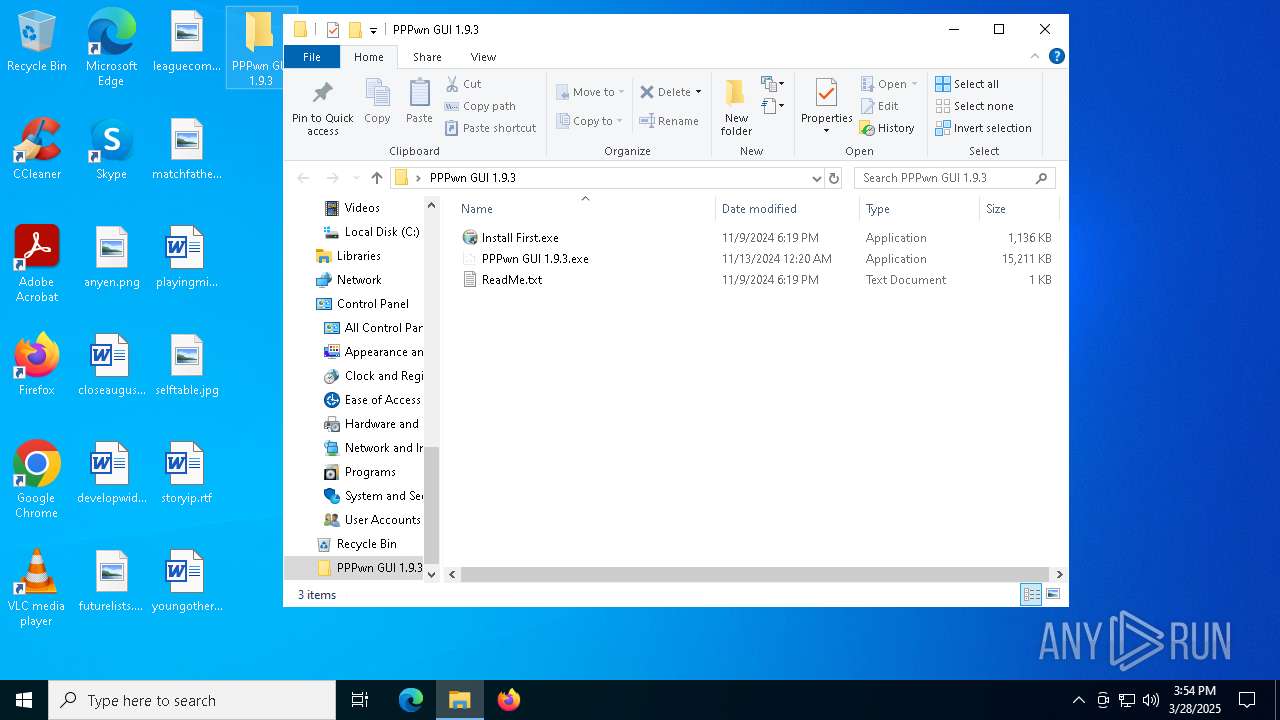
- Install First.exe (PID: 8132)
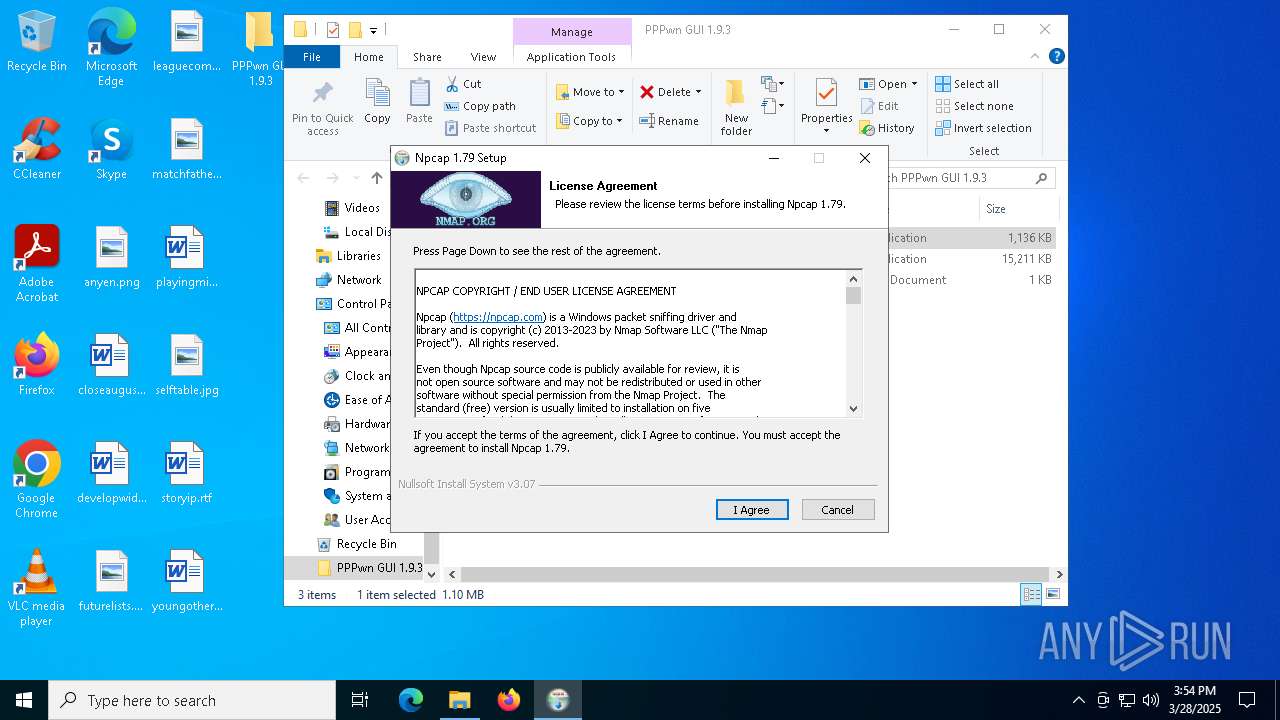
- NPFInstall.exe (PID: 1272)
- drvinst.exe (PID: 1616)
- PPPwn GUI 1.9.3.exe (PID: 7600)
Malware-specific behavior (creating "System.dll" in Temp)
- Install First.exe (PID: 8132)
The process creates files with name similar to system file names
- Install First.exe (PID: 8132)
Drops a system driver (possible attempt to evade defenses)
- Install First.exe (PID: 8132)
- drvinst.exe (PID: 1616)
- NPFInstall.exe (PID: 1272)
Starts POWERSHELL.EXE for commands execution
- Install First.exe (PID: 8132)
The process hide an interactive prompt from the user
- Install First.exe (PID: 8132)
Returns all items found within a container (POWERSHELL)
- powershell.exe (PID: 5164)
- powershell.exe (PID: 7632)
- powershell.exe (PID: 7856)
- powershell.exe (PID: 5436)
The process bypasses the loading of PowerShell profile settings
- Install First.exe (PID: 8132)
Removes files via Powershell
- powershell.exe (PID: 7632)
- powershell.exe (PID: 5436)
Adds/modifies Windows certificates
- certutil.exe (PID: 6824)
Creates files in the driver directory
- drvinst.exe (PID: 1616)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7884)
- cmd.exe (PID: 4944)
- cmd.exe (PID: 744)
- cmd.exe (PID: 7236)
- cmd.exe (PID: 2504)
- cmd.exe (PID: 1628)
Starts CMD.EXE for commands execution
- PPPwn GUI 1.9.3.exe (PID: 7600)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 720)
- Install First.exe (PID: 8132)
Manual execution by a user
- Install First.exe (PID: 8084)
- Install First.exe (PID: 8132)
- PPPwn GUI 1.9.3.exe (PID: 7600)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 720)
Creates files in the program directory
- NPFInstall.exe (PID: 6108)
- Install First.exe (PID: 8132)
Create files in a temporary directory
- Install First.exe (PID: 8132)
- NPFInstall.exe (PID: 1272)
- PPPwn GUI 1.9.3.exe (PID: 7600)
Returns hidden items found within a container (POWERSHELL)
- conhost.exe (PID: 4040)
- conhost.exe (PID: 7656)
- conhost.exe (PID: 7524)
- conhost.exe (PID: 7620)
- conhost.exe (PID: 7880)
- conhost.exe (PID: 5256)
- conhost.exe (PID: 2908)
- conhost.exe (PID: 7376)
- conhost.exe (PID: 1040)
- conhost.exe (PID: 8120)
- conhost.exe (PID: 4688)
- conhost.exe (PID: 6972)
- conhost.exe (PID: 7244)
- conhost.exe (PID: 1804)
- powershell.exe (PID: 5576)
- conhost.exe (PID: 7436)
- conhost.exe (PID: 6272)
- conhost.exe (PID: 7340)
- conhost.exe (PID: 7912)
- conhost.exe (PID: 1812)
- conhost.exe (PID: 5384)
- conhost.exe (PID: 2552)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5576)
Creates files or folders in the user directory
- PPPwn GUI 1.9.3.exe (PID: 7600)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:11:13 00:21:04 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | PPPwn GUI 1.9.3/ |
Total processes
202
Monitored processes
60
Malicious processes
1
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 720 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\aZz85975-PPPwnGUI1.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 744 | "cmd.exe" /C taskkill /IM pppwn_p.exe /f | C:\Windows\SysWOW64\cmd.exe | — | PPPwn GUI 1.9.3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 128 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | "C:\Program Files\Npcap\NPFInstall.exe" -n -i | C:\Program Files\Npcap\NPFInstall.exe | Install First.exe | ||||||||||||
User: admin Company: Insecure.Com LLC. Integrity Level: HIGH Description: A LWF & WFP driver installation tool Exit code: 0 Version: 1.79 Modules
| |||||||||||||||
| 1616 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{8a05dcfa-6e9e-9f4c-9aab-dc7bacf79ed7}\NPCAP.inf" "9" "405306be3" "0000000000000170" "WinSta0\Default" "00000000000001EC" "208" "C:\Program Files\Npcap" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1628 | "cmd.exe" /C taskkill /IM pppwn_p.exe /f | C:\Windows\SysWOW64\cmd.exe | — | PPPwn GUI 1.9.3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 128 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1804 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1812 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2504 | "cmd.exe" /C taskkill /IM pppwn_64.exe /f | C:\Windows\SysWOW64\cmd.exe | — | PPPwn GUI 1.9.3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 128 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2552 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
50 063
Read events
49 967
Write events
74
Delete events
22
Modification events
| (PID) Process: | (720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\aZz85975-PPPwnGUI1.zip | |||
| (PID) Process: | (720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
41
Suspicious files
58
Text files
23
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 720 | WinRAR.exe | C:\Users\admin\Desktop\PPPwn GUI 1.9.3\ReadMe.txt | text | |
MD5:995B06EF9DD951FB5F4E7F506CC11AA6 | SHA256:4B35FCA9534C39734412C3081ACC5771AD163C4BAE71ACB374A8A8B56E451775 | |||
| 8132 | Install First.exe | C:\Program Files\Npcap\DiagReport.ps1 | text | |
MD5:0B4DF7D19ADE75BEE930D54BE31AC09C | SHA256:27EB36CB165C6EDD2F55B72A6856E4BF32AE2FA6CADFFCD267F5DF96EEA0B011 | |||
| 8132 | Install First.exe | C:\Program Files\Npcap\DiagReport.bat | text | |
MD5:B82606A6AFB3777D62E35E8D9850FAED | SHA256:0843361F05255E3970ED955171C20003238756C57137FEF9AC19D29FBD49F9F6 | |||
| 8132 | Install First.exe | C:\Program Files\Npcap\FixInstall.bat | text | |
MD5:3DCB581D39D9349A906368B77A4CEDFA | SHA256:C6158E40BDFD88E892EE6C4DA3A16A037EDF2CC77DC008CBD8FBEB44C643DDDA | |||
| 8132 | Install First.exe | C:\Windows\SysWOW64\NpcapHelper.exe | executable | |
MD5:BCDB5E5E3AC9FA9BCB03674187FCB8F2 | SHA256:07F7F39D83B0DF929D1DEA1E4B91A0AAFE6970F39D771B29FC3CA3F3CD9883EA | |||
| 8132 | Install First.exe | C:\Program Files\Npcap\Uninstall.exe | executable | |
MD5:182AFDB82027F2D3CF246FF586DDFF9D | SHA256:685800E60444558FF66AFF832CA72311281935B9972DEF7485D97A236C04E0BA | |||
| 8132 | Install First.exe | C:\Windows\SysWOW64\Packet.dll | executable | |
MD5:9ACA1C6433A681FE05AB3922337F9A88 | SHA256:D22EC969ADAD9006F7B00D5B2FDC9CA36F02DEDE505F703F506A2D29DEA6207E | |||
| 8132 | Install First.exe | C:\Users\admin\AppData\Local\Temp\nsjFF15.tmp\InstallOptions.dll | executable | |
MD5:170C17AC80215D0A377B42557252AE10 | SHA256:61EA114D9D0CD1E884535095AA3527A6C28DF55A4ECEE733C8C398F50B84CC3D | |||
| 720 | WinRAR.exe | C:\Users\admin\Desktop\PPPwn GUI 1.9.3\Install First.exe | executable | |
MD5:A4D7E47DF742F62080BF845D606045B4 | SHA256:A95577EBBC67FC45B319E2EF3A55F4E9B211FE82ED4CB9D8BE6B1A9E2425CE53 | |||
| 8132 | Install First.exe | C:\Users\admin\AppData\Local\Temp\nsjFF15.tmp\System.dll | executable | |
MD5:F020A8D9EDE1FB2AF3651AD6E0AC9CB1 | SHA256:7EFE73A8D32ED1B01727AD4579E9EEC49C9309F2CB7BF03C8AFA80D70242D1C0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
22
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7228 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1628 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1628 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
3216 | svchost.exe | 172.172.255.217:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
5256 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7228 | backgroundTaskHost.exe | 20.74.19.45:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7228 | backgroundTaskHost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |