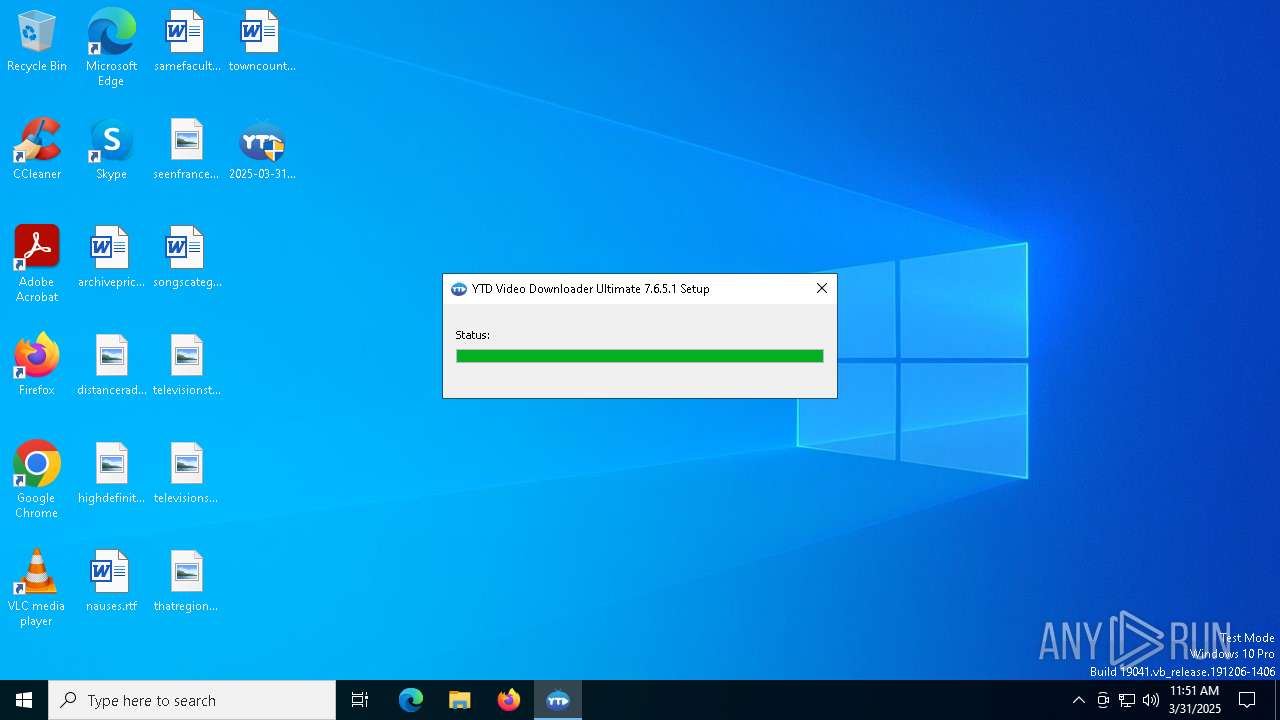
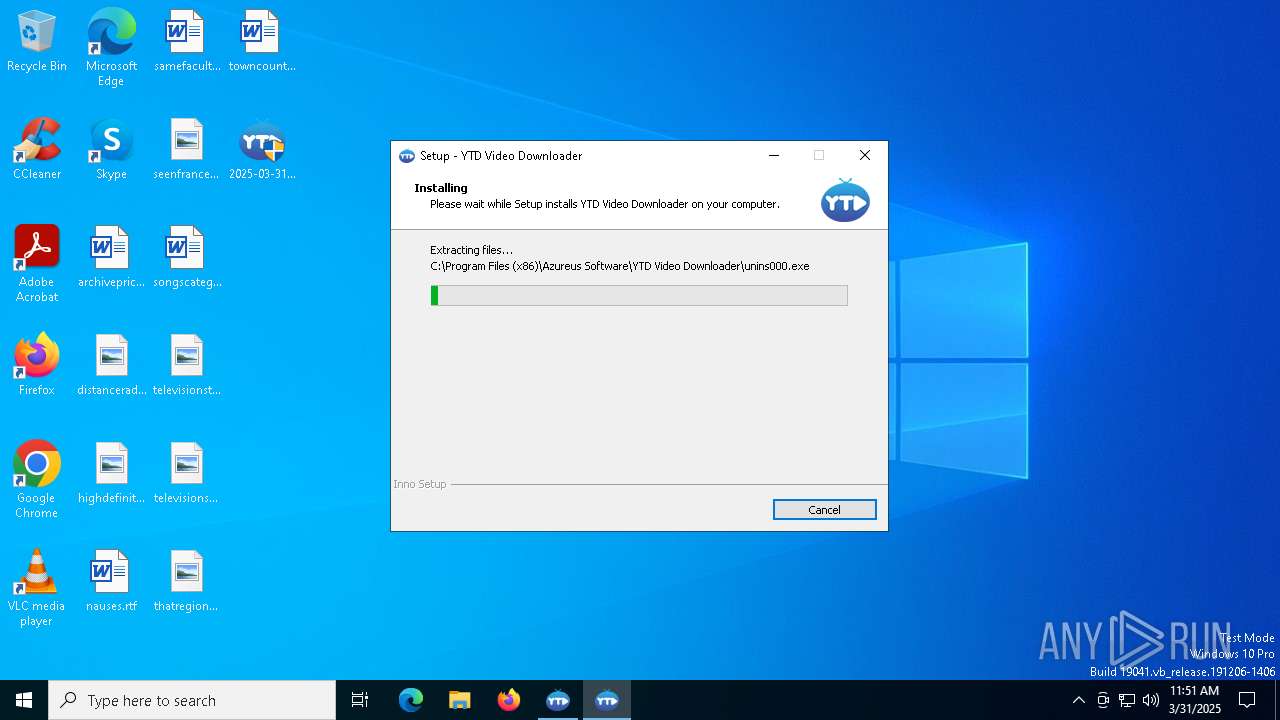
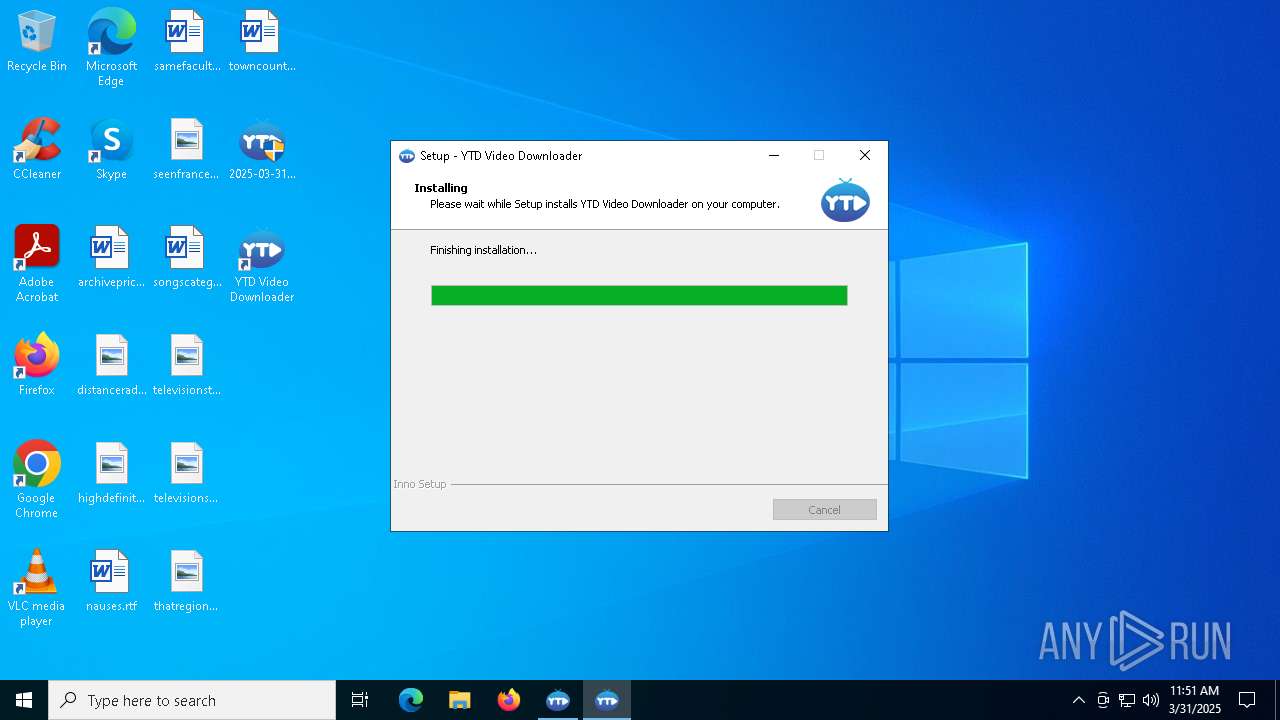
| File name: | 2025-03-31_79f8d3b72befc7188da3bfd4285803b9_black-basta_hijackloader_luca-stealer_remcos |
| Full analysis: | https://app.any.run/tasks/59836334-0270-4acb-bba7-f3f2b752cdbf |
| Verdict: | Malicious activity |
| Analysis date: | March 31, 2025, 11:50:56 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 7 sections |
| MD5: | 79F8D3B72BEFC7188DA3BFD4285803B9 |
| SHA1: | EA8069975251FB76F15AD1AE298284EC8AE700A4 |
| SHA256: | 1B00F0C95FD19DE6AFEFF6C62DD6DFC851CE69253B4B2401731B1DD726D8C991 |
| SSDEEP: | 393216:Hr8S+7LTqKR31FAMEvDDrJqMUquA8lskWu10Kj1:YN1R3nJE39fUquA8ikWuuk |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
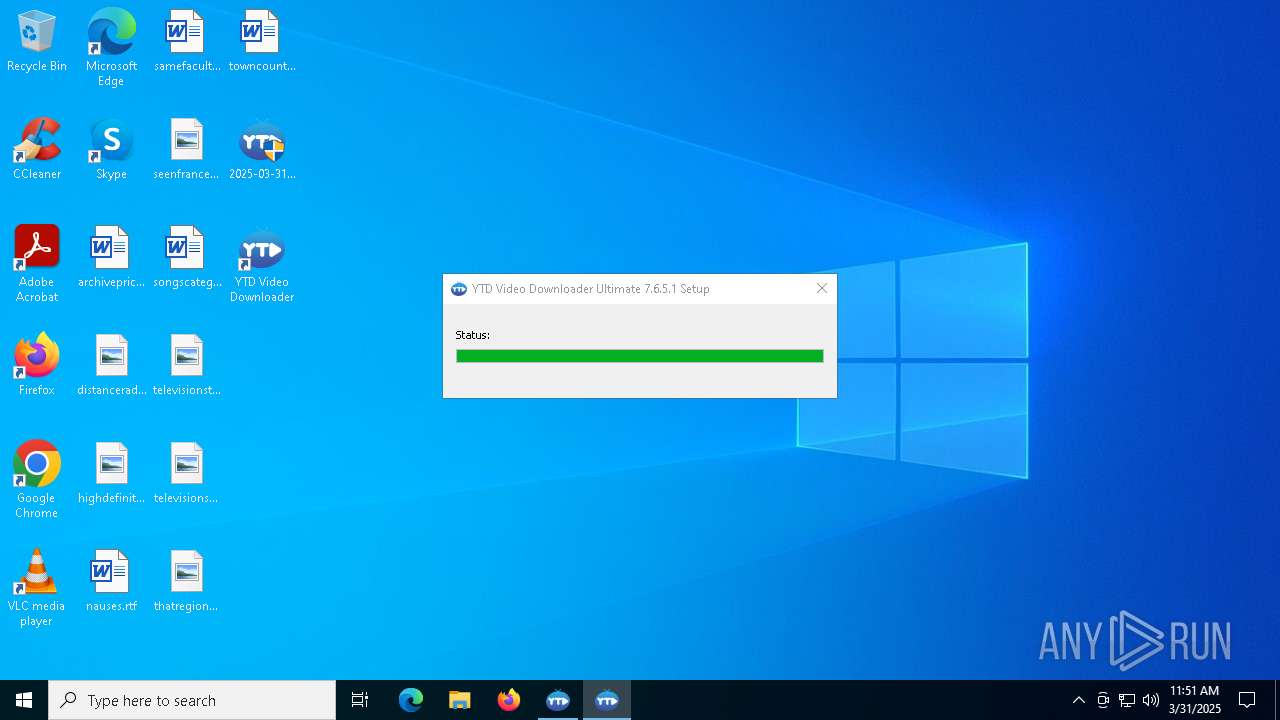
- 2025-03-31_79f8d3b72befc7188da3bfd4285803b9_black-basta_hijackloader_luca-stealer_remcos.exe (PID: 7672)
- YTDSetup.tmp (PID: 7980)
ADVANCEDINSTALLER mutex has been found
- 2025-03-31_79f8d3b72befc7188da3bfd4285803b9_black-basta_hijackloader_luca-stealer_remcos.exe (PID: 7672)
Reads the Windows owner or organization settings
- 2025-03-31_79f8d3b72befc7188da3bfd4285803b9_black-basta_hijackloader_luca-stealer_remcos.exe (PID: 7672)
- YTDSetup.tmp (PID: 7980)
- msiexec.exe (PID: 7740)
Executable content was dropped or overwritten
- 2025-03-31_79f8d3b72befc7188da3bfd4285803b9_black-basta_hijackloader_luca-stealer_remcos.exe (PID: 7672)
- YTDSetup.exe (PID: 7952)
- YTDSetup.tmp (PID: 7980)
Reads security settings of Internet Explorer
- 2025-03-31_79f8d3b72befc7188da3bfd4285803b9_black-basta_hijackloader_luca-stealer_remcos.exe (PID: 7672)
- YTDSetup.tmp (PID: 7980)
- ytd.exe (PID: 1184)
There is functionality for taking screenshot (YARA)
- 2025-03-31_79f8d3b72befc7188da3bfd4285803b9_black-basta_hijackloader_luca-stealer_remcos.exe (PID: 7672)
Detects AdvancedInstaller (YARA)
- 2025-03-31_79f8d3b72befc7188da3bfd4285803b9_black-basta_hijackloader_luca-stealer_remcos.exe (PID: 7672)
Reads Internet Explorer settings
- ytd.exe (PID: 1184)
Reads Microsoft Outlook installation path
- ytd.exe (PID: 1184)
INFO
Checks supported languages
- msiexec.exe (PID: 7740)
- msiexec.exe (PID: 7836)
- 2025-03-31_79f8d3b72befc7188da3bfd4285803b9_black-basta_hijackloader_luca-stealer_remcos.exe (PID: 7672)
- YTDSetup.exe (PID: 7952)
- YTDSetup.tmp (PID: 7980)
- ytd.exe (PID: 1184)
- msiexec.exe (PID: 7252)
- msiexec.exe (PID: 3884)
- identity_helper.exe (PID: 4212)
Reads the computer name
- msiexec.exe (PID: 7740)
- msiexec.exe (PID: 7836)
- 2025-03-31_79f8d3b72befc7188da3bfd4285803b9_black-basta_hijackloader_luca-stealer_remcos.exe (PID: 7672)
- ytd.exe (PID: 1184)
- YTDSetup.tmp (PID: 7980)
- msiexec.exe (PID: 7252)
- msiexec.exe (PID: 3884)
- identity_helper.exe (PID: 4212)
The sample compiled with english language support
- 2025-03-31_79f8d3b72befc7188da3bfd4285803b9_black-basta_hijackloader_luca-stealer_remcos.exe (PID: 7672)
- YTDSetup.tmp (PID: 7980)
- msiexec.exe (PID: 7740)
Reads Environment values
- msiexec.exe (PID: 7836)
- 2025-03-31_79f8d3b72befc7188da3bfd4285803b9_black-basta_hijackloader_luca-stealer_remcos.exe (PID: 7672)
- msiexec.exe (PID: 3884)
- identity_helper.exe (PID: 4212)
Create files in a temporary directory
- 2025-03-31_79f8d3b72befc7188da3bfd4285803b9_black-basta_hijackloader_luca-stealer_remcos.exe (PID: 7672)
- YTDSetup.exe (PID: 7952)
- YTDSetup.tmp (PID: 7980)
Process checks computer location settings
- 2025-03-31_79f8d3b72befc7188da3bfd4285803b9_black-basta_hijackloader_luca-stealer_remcos.exe (PID: 7672)
Creates files in the program directory
- YTDSetup.tmp (PID: 7980)
Creates a software uninstall entry
- YTDSetup.tmp (PID: 7980)
Application launched itself
- msedge.exe (PID: 7224)
- msedge.exe (PID: 7316)
Manual execution by a user
- msedge.exe (PID: 7316)
Checks proxy server information
- ytd.exe (PID: 1184)
- slui.exe (PID: 5740)
Reads the software policy settings
- ytd.exe (PID: 1184)
- YTDSetup.tmp (PID: 7980)
- slui.exe (PID: 5740)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7740)
Reads the machine GUID from the registry
- YTDSetup.tmp (PID: 7980)
- ytd.exe (PID: 1184)
Disables trace logs
- ytd.exe (PID: 1184)
Creates files or folders in the user directory
- ytd.exe (PID: 1184)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (18) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (2.9) |
| .exe | | | Generic Win/DOS Executable (1.3) |
| .exe | | | DOS Executable Generic (1.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:03:03 13:51:40+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.43 |
| CodeSize: | 2920960 |
| InitializedDataSize: | 1325568 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2351b0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | GetintoWAY |
| FileDescription: | YTD Video Downloader Ultimate 7.6.5.1 Installer |
| FileVersion: | 0.0.0.0 |
| InternalName: | YTD Video Downloader Ultimate 7.6.5.1 |
| LegalCopyright: | Copyright (C) 2025 GetintoWAY |
| OriginalFileName: | YTD Video Downloader Ultimate 7.6.5.1.exe |
| ProductName: | YTD Video Downloader Ultimate 7.6.5.1 |
| ProductVersion: | 0.0.0.0 |
Total processes
183
Monitored processes
54
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1184 | "C:\Program Files (x86)\Azureus Software\YTD Video Downloader\ytd.exe" | C:\Program Files (x86)\Azureus Software\YTD Video Downloader\ytd.exe | YTDSetup.tmp | ||||||||||||
User: admin Integrity Level: HIGH Description: YTD Version: 7.6.5.1 Modules
| |||||||||||||||
| 1272 | "C:\WINDOWS\system32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\YTD_Video_Downloader_Ultimate.msi AI_SETUPEXEPATH=C:\Users\admin\Desktop\2025-03-31_79f8d3b72befc7188da3bfd4285803b9_black-basta_hijackloader_luca-stealer_remcos.exe SETUPEXEDIR=C:\Users\admin\Desktop\ EXE_CMD_LINE="/exenoupdates /forcecleanup /wintime 1743420773 " AI_EUIMSI="" AI_MISSING_PREREQS="YTD Video Downloader Application" | C:\Windows\SysWOW64\msiexec.exe | — | 2025-03-31_79f8d3b72befc7188da3bfd4285803b9_black-basta_hijackloader_luca-stealer_remcos.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2088 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x310,0x314,0x318,0x308,0x320,0x7ffc89055fd8,0x7ffc89055fe4,0x7ffc89055ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2240 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=4108 --field-trial-handle=2420,i,8722816933747562524,9420820038150297805,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2656 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=1668 --field-trial-handle=2420,i,8722816933747562524,9420820038150297805,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2852 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=6912 --field-trial-handle=2420,i,8722816933747562524,9420820038150297805,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3024 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6356 --field-trial-handle=2420,i,8722816933747562524,9420820038150297805,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3884 | C:\Windows\syswow64\MsiExec.exe -Embedding CF022D259076909644A98F066B739854 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3956 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6984 --field-trial-handle=2420,i,8722816933747562524,9420820038150297805,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 4212 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6328 --field-trial-handle=2420,i,8722816933747562524,9420820038150297805,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
20 129
Read events
20 053
Write events
75
Delete events
1
Modification events
| (PID) Process: | (7224) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7224) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7224) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7980) YTDSetup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Azureus Software\YTD |
| Operation: | write | Name: | ISN |
Value: 5F8D46741B1A409C98A9644C3A4E731E | |||
| (PID) Process: | (7980) YTDSetup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Azureus Software\YTD |
| Operation: | write | Name: | Language |
Value: 1033 | |||
| (PID) Process: | (7980) YTDSetup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Azureus Software\YTD |
| Operation: | write | Name: | kitType |
Value: PAD | |||
| (PID) Process: | (7980) YTDSetup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{1a413f37-ed88-4fec-9666-5c48dc4b7bb7} |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files (x86)\Azureus Software\YTD Video Downloader\ytd.exe,0 | |||
| (PID) Process: | (7980) YTDSetup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{1a413f37-ed88-4fec-9666-5c48dc4b7bb7} |
| Operation: | write | Name: | DisplayName |
Value: YTD Video Downloader 7.6.5.1 | |||
| (PID) Process: | (7980) YTDSetup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{1a413f37-ed88-4fec-9666-5c48dc4b7bb7} |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files (x86)\Azureus Software\YTD Video Downloader\unins000.exe" | |||
| (PID) Process: | (7980) YTDSetup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{1a413f37-ed88-4fec-9666-5c48dc4b7bb7} |
| Operation: | write | Name: | Publisher |
Value: Azureus Software, Inc. | |||
Executable files
43
Suspicious files
324
Text files
93
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7672 | 2025-03-31_79f8d3b72befc7188da3bfd4285803b9_black-basta_hijackloader_luca-stealer_remcos.exe | C:\Users\admin\AppData\Local\Temp\YTD_Video_Downloader_Ultimate.msi | executable | |
MD5:7E5C00B2374EC69D134B6760CB3E184A | SHA256:34D9FC8FC7B6DD7F7EBF5CBAEEDD697AE48BC476FC9FDE88E0297D445C383D63 | |||
| 7672 | 2025-03-31_79f8d3b72befc7188da3bfd4285803b9_black-basta_hijackloader_luca-stealer_remcos.exe | C:\Users\admin\AppData\Local\Temp\MSIFE97.tmp | executable | |
MD5:2330EBBE491C6026AF5E8853F3692798 | SHA256:3ADA2257732FAE73114BB6A5E082CEF4BD72C3D6842924BE6F22728C7D7CACC4 | |||
| 7672 | 2025-03-31_79f8d3b72befc7188da3bfd4285803b9_black-basta_hijackloader_luca-stealer_remcos.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_7672\removico | image | |
MD5:1FFFE5C3CC990D0C012A428A59B2AE46 | SHA256:45791627AE8E67E6B616117CF21F04DA381722FAF08D07C0C25E0F28C9B8F82B | |||
| 7672 | 2025-03-31_79f8d3b72befc7188da3bfd4285803b9_black-basta_hijackloader_luca-stealer_remcos.exe | C:\Users\admin\AppData\Local\Temp\MSIFFC0.tmp | executable | |
MD5:2330EBBE491C6026AF5E8853F3692798 | SHA256:3ADA2257732FAE73114BB6A5E082CEF4BD72C3D6842924BE6F22728C7D7CACC4 | |||
| 7672 | 2025-03-31_79f8d3b72befc7188da3bfd4285803b9_black-basta_hijackloader_luca-stealer_remcos.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_7672\dialog.jpg | image | |
MD5:5F6253CFF5A8B031BFB3B161079D0D86 | SHA256:36D9BAB35D1E4B50045BF902F5D42B6F865488C75F6E60FC00A6CD6F69034AB0 | |||
| 7672 | 2025-03-31_79f8d3b72befc7188da3bfd4285803b9_black-basta_hijackloader_luca-stealer_remcos.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_7672\custicon | image | |
MD5:BE6D2F48AA6634FB2101C273C798D4D9 | SHA256:0E22BC2BF7184DFDB55223A11439304A453FB3574E3C9034A6497AF405C628EF | |||
| 7672 | 2025-03-31_79f8d3b72befc7188da3bfd4285803b9_black-basta_hijackloader_luca-stealer_remcos.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_7672\info | image | |
MD5:8595D2A2D58310B448729E28649443D6 | SHA256:27F13C4829994B214BB1A26EEF474DA67C521FD429536CB8421BA2F7C3E02B5F | |||
| 7672 | 2025-03-31_79f8d3b72befc7188da3bfd4285803b9_black-basta_hijackloader_luca-stealer_remcos.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_7672\insticon | image | |
MD5:EAC3781BA9FB0502D6F16253EB67B2B4 | SHA256:F864E8640C98B65C6C1B9B66A850661E8397ED6E66B06F4424396275488AF1BE | |||
| 7672 | 2025-03-31_79f8d3b72befc7188da3bfd4285803b9_black-basta_hijackloader_luca-stealer_remcos.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_7672\exclamic | image | |
MD5:3FBB7DDBC13EDF109E3ACAA7A4A69A4E | SHA256:F8429073C7A83377AD754824B0B81040D68F8C1350A82FF4DCCF8BC4BF31F177 | |||
| 7672 | 2025-03-31_79f8d3b72befc7188da3bfd4285803b9_black-basta_hijackloader_luca-stealer_remcos.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_7672\Up | image | |
MD5:FD64F54DB4CBF736A6FC0D7049F5991E | SHA256:C269353D19D50E2688DB102FEF8226CA492DB17133043D7EB5420EE8542D571C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
128
TCP/UDP connections
114
DNS requests
81
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 23.216.77.36:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.36:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 4.245.163.56:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 401 | 13.107.6.158:443 | https://business.bing.com/api/v1/user/token/microsoftgraph?&clienttype=edge-omnibox | unknown | — | — | unknown |
8080 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
8080 | SIHClient.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
— | — | OPTIONS | 504 | 23.48.23.26:443 | https://bzib.nelreports.net/api/report?cat=bingbusiness | unknown | — | — | unknown |
— | — | POST | 400 | 40.126.32.140:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 40.126.32.74:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
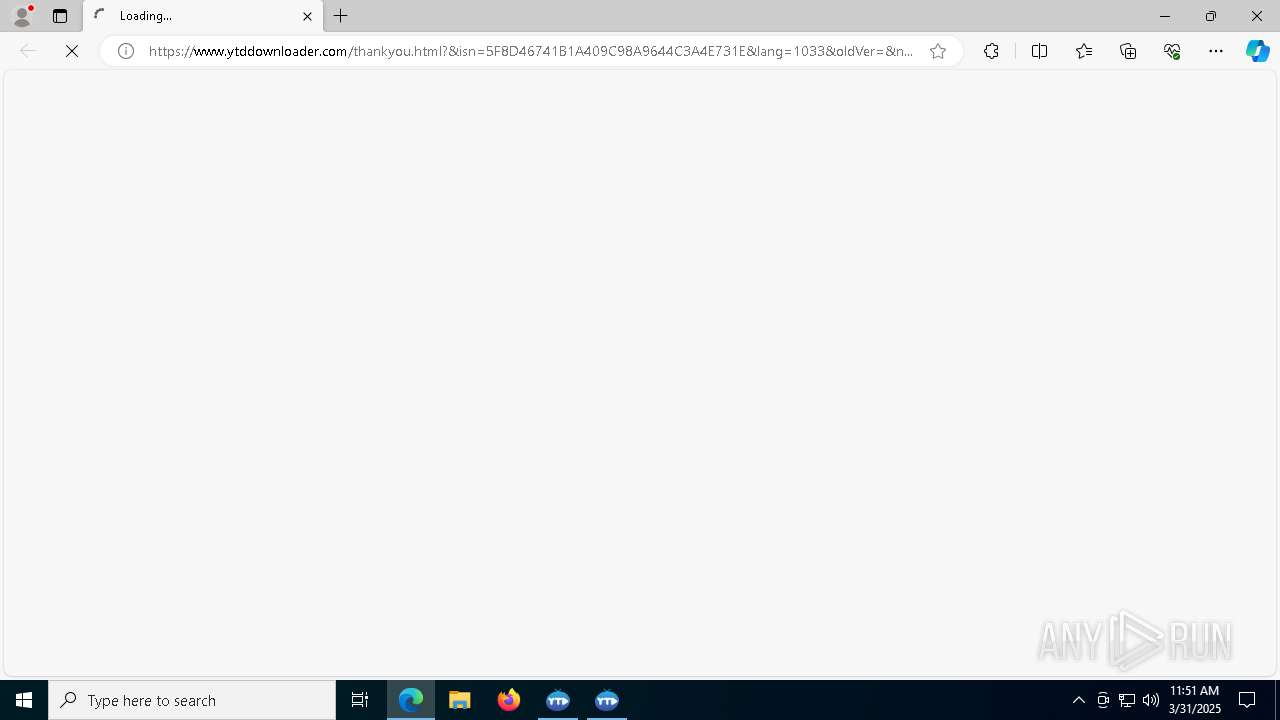
— | — | GET | 200 | 52.207.28.40:443 | https://www.ytddownloader.com/thankyou.html?&isn=5F8D46741B1A409C98A9644C3A4E731E&lang=1033&oldVer=&newVer=7.6.5.1&kt=PAD&pv=0 | unknown | html | 12.3 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.198.162.78:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
2104 | svchost.exe | 23.216.77.36:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.216.77.36:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 20.190.159.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 20.190.159.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 20.198.162.78:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.ytddownloader.com |
| unknown |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5280 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
5280 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
5280 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
5280 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
5280 | msedge.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
5280 | msedge.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
5280 | msedge.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |