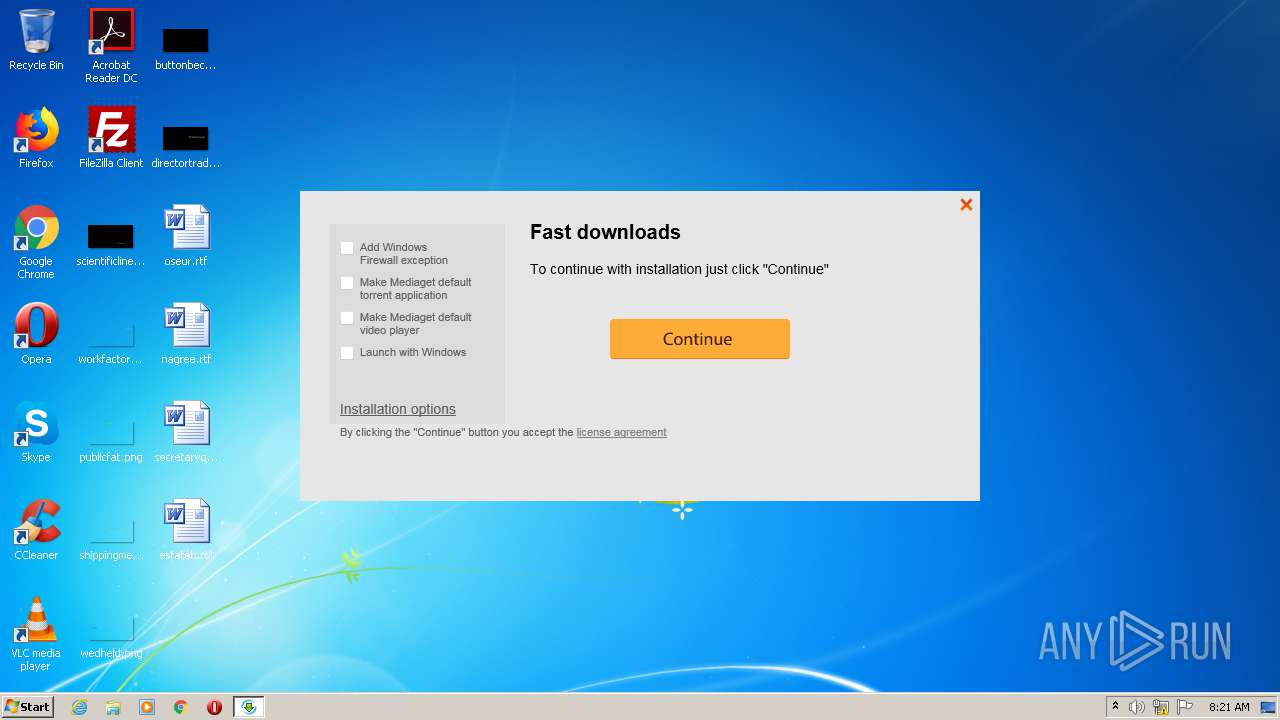
| File name: | we-were-here-together_id2457064ids1s.exe |
| Full analysis: | https://app.any.run/tasks/b028044f-2eaf-4d27-ac97-0aff66731f12 |
| Verdict: | Malicious activity |
| Analysis date: | December 29, 2020, 08:20:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | E00E778F042A624A8B7EADD8B77D0763 |
| SHA1: | 35C4C2B87B35CF84FFCD14A1FB758971346E0322 |
| SHA256: | 1AFA0BDF1DDA537129E435AC361F6333E5C0F4640DB278ED2598C274BABE5791 |
| SSDEEP: | 49152:hSBrpYL3+HzziPX0imuldpMnlRe+eWyocsVuponN5RT7YE4:CpYSz2PdInl0+eMcxou |
MALICIOUS
Actions looks like stealing of personal data
- we-were-here-together_id2457064ids1s.exe (PID: 3440)
Loads dropped or rewritten executable
- mediaget.exe (PID: 2560)
- SearchProtocolHost.exe (PID: 3184)
- mediaget_crashpad_handler.exe (PID: 768)
- QtWebEngineProcess.exe (PID: 3556)
- QtWebEngineProcess.exe (PID: 2888)
- QtWebEngineProcess.exe (PID: 3712)
- QtWebEngineProcess.exe (PID: 3844)
- QtWebEngineProcess.exe (PID: 3068)
Application was dropped or rewritten from another process
- mediaget_crashpad_handler.exe (PID: 768)
- QtWebEngineProcess.exe (PID: 3556)
- QtWebEngineProcess.exe (PID: 3712)
- QtWebEngineProcess.exe (PID: 2888)
- QtWebEngineProcess.exe (PID: 3844)
- QtWebEngineProcess.exe (PID: 3068)
- mediaget.exe (PID: 2560)
Changes settings of System certificates
- QtWebEngineProcess.exe (PID: 3556)
SUSPICIOUS
Reads internet explorer settings
- we-were-here-together_id2457064ids1s.exe (PID: 3440)
Drops a file that was compiled in debug mode
- we-were-here-together_id2457064ids1s.exe (PID: 3440)
Drops a file with too old compile date
- we-were-here-together_id2457064ids1s.exe (PID: 3440)
- mediaget.exe (PID: 2560)
Drops a file with a compile date too recent
- we-were-here-together_id2457064ids1s.exe (PID: 3440)
Executable content was dropped or overwritten
- we-were-here-together_id2457064ids1s.exe (PID: 3440)
- mediaget.exe (PID: 2560)
Creates a software uninstall entry
- we-were-here-together_id2457064ids1s.exe (PID: 3440)
Creates files in the user directory
- we-were-here-together_id2457064ids1s.exe (PID: 3440)
Reads Environment values
- mediaget.exe (PID: 2560)
Changes default file association
- mediaget.exe (PID: 2560)
Starts Internet Explorer
- mediaget.exe (PID: 2560)
Adds / modifies Windows certificates
- QtWebEngineProcess.exe (PID: 3556)
INFO
Dropped object may contain Bitcoin addresses
- we-were-here-together_id2457064ids1s.exe (PID: 3440)
- iexplore.exe (PID: 3768)
Reads the hosts file
- mediaget.exe (PID: 2560)
- QtWebEngineProcess.exe (PID: 3556)
Reads settings of System Certificates
- QtWebEngineProcess.exe (PID: 3556)
- iexplore.exe (PID: 3768)
Application launched itself
- iexplore.exe (PID: 2504)
Creates files in the user directory
- iexplore.exe (PID: 3768)
Reads internet explorer settings
- iexplore.exe (PID: 3768)
Changes internet zones settings
- iexplore.exe (PID: 2504)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3768)
Changes settings of System certificates
- iexplore.exe (PID: 3768)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:11:23 16:49:56+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 1477632 |
| InitializedDataSize: | 1254912 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x15f782 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 1 |
| InternalName: | - |
| LegalCopyright: | - |
| OriginalFileName: | - |
| ProductName: | - |
| ProductVersion: | 1 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 23-Nov-2020 15:49:56 |
| Detected languages: |
|
| Comments: | - |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 1.0 |
| InternalName: | - |
| LegalCopyright: | - |
| OriginalFilename: | - |
| ProductName: | - |
| ProductVersion: | 1.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000118 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 23-Nov-2020 15:49:56 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00168A54 | 0x00168C00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.62267 |
.rdata | 0x0016A000 | 0x0006E7C0 | 0x0006E800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.09177 |
.data | 0x001D9000 | 0x0000F4C0 | 0x00009600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.05308 |
.rsrc | 0x001E9000 | 0x000A4B38 | 0x000A4C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.72685 |
.reloc | 0x0028E000 | 0x00015B46 | 0x00015C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.08903 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.22706 | 820 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 5.18073 | 4264 | Latin 1 / Western European | English - United States | RT_ICON |
3 | 5.05232 | 2440 | Latin 1 / Western European | English - United States | RT_ICON |
4 | 4.75162 | 1128 | Latin 1 / Western European | English - United States | RT_ICON |
128 | 2.62308 | 62 | Latin 1 / Western European | English - United States | RT_GROUP_ICON |
129 | 1.67172 | 170 | Latin 1 / Western European | English - United States | UNKNOWN |
HTML | 7.9995 | 388065 | Latin 1 / Western European | Russian - Russia | ARCHIVE_7Z |
PRELOADER | 7.98607 | 15254 | Latin 1 / Western European | Russian - Russia | ARCHIVE_7Z |
CABUNDLE | 6.0253 | 227153 | Latin 1 / Western European | Russian - Russia | CRT |
YACLIDS | 3.22226 | 22061 | Latin 1 / Western European | Russian - Russia | TXT |
Imports
ADVAPI32.dll |
COMCTL32.dll |
CRYPT32.dll |
GDI32.dll |
KERNEL32.dll |
MSVCR90.dll |
OLEAUT32.dll |
OPENGL32.dll |
PSAPI.DLL |
SHELL32.dll |
Total processes
51
Monitored processes
12
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 768 | C:/Users/admin/MediaGet2/mediaget_crashpad_handler.exe --no-rate-limit --no-upload-gzip "--attachment=__sentry-breadcrumb1=C:/Users/admin/AppData/Local/Media Get LLC/MediaGet2/crashdumps\sentry-runs\1609230123-346194799\__sentry-breadcrumb1" "--attachment=__sentry-breadcrumb2=C:/Users/admin/AppData/Local/Media Get LLC/MediaGet2/crashdumps\sentry-runs\1609230123-346194799\__sentry-breadcrumb2" "--attachment=__sentry-event=C:/Users/admin/AppData/Local/Media Get LLC/MediaGet2/crashdumps\sentry-runs\1609230123-346194799\__sentry-event" "--database=C:/Users/admin/AppData/Local/Media Get LLC/MediaGet2/crashdumps" "--metrics-dir=C:/Users/admin/AppData/Local/Media Get LLC/MediaGet2/crashdumps" --url=https://sentry.mediaget.com:443/api/3/minidump/?sentry_key=cd52914f7f6f44b6be0d8a871825b54d --initial-client-data=0x39c,0x3a0,0x3a4,0x398,0x3a8,0x6a4daa9c,0x6a4daaac,0x6a4daabc | C:\Users\admin\MediaGet2\mediaget_crashpad_handler.exe | — | mediaget.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2504 | "C:\Program Files\Internet Explorer\iexplore.exe" http://sub2.bubblesmedia.ru/client/mg_install?version=3.01.3941&install_id=2534022&ref_id=al_allgamerus.ru&mg_new=1 | C:\Program Files\Internet Explorer\iexplore.exe | mediaget.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2560 | "C:\Users\admin\MediaGet2\mediaget.exe" --installer | C:\Users\admin\MediaGet2\mediaget.exe | we-were-here-together_id2457064ids1s.exe | ||||||||||||
User: admin Company: MediaGet Integrity Level: HIGH Description: MediaGet torrent client Exit code: 0 Modules
| |||||||||||||||
| 2684 | "C:\Users\admin\AppData\Local\Temp\we-were-here-together_id2457064ids1s.exe" | C:\Users\admin\AppData\Local\Temp\we-were-here-together_id2457064ids1s.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.0 Modules
| |||||||||||||||
| 2888 | "C:\Users\admin\MediaGet2\QtWebEngineProcess.exe" --type=renderer --disable-speech-api --enable-threaded-compositing --enable-features=AllowContentInitiatedDataUrlNavigations,TracingServiceInProcess --disable-features=BackgroundFetch,ConsolidatedMovementXY,DnsOverHttpsUpgrade,FormControlsRefresh,MojoVideoCapture,PictureInPicture,SmsReceiver,UseSkiaRenderer,WebPayments,WebUSB --disable-gpu-compositing --lang=en-US --webengine-schemes=qrc:sLV --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --mojo-platform-channel-handle=2712 /prefetch:1 | C:\Users\admin\MediaGet2\QtWebEngineProcess.exe | — | mediaget.exe | |||||||||||
User: admin Company: The Qt Company Ltd. Integrity Level: LOW Description: C++ Application Development Framework Exit code: 0 Version: 5.15.2.0 Modules
| |||||||||||||||
| 3068 | "C:\Users\admin\MediaGet2\QtWebEngineProcess.exe" --type=renderer --disable-speech-api --enable-threaded-compositing --enable-features=AllowContentInitiatedDataUrlNavigations,TracingServiceInProcess --disable-features=BackgroundFetch,ConsolidatedMovementXY,DnsOverHttpsUpgrade,FormControlsRefresh,MojoVideoCapture,PictureInPicture,SmsReceiver,UseSkiaRenderer,WebPayments,WebUSB --disable-gpu-compositing --lang=en-US --webengine-schemes=qrc:sLV --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3248 /prefetch:1 | C:\Users\admin\MediaGet2\QtWebEngineProcess.exe | — | mediaget.exe | |||||||||||
User: admin Company: The Qt Company Ltd. Integrity Level: LOW Description: C++ Application Development Framework Exit code: 0 Version: 5.15.2.0 Modules
| |||||||||||||||
| 3184 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3440 | "C:\Users\admin\AppData\Local\Temp\we-were-here-together_id2457064ids1s.exe" | C:\Users\admin\AppData\Local\Temp\we-were-here-together_id2457064ids1s.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0 Modules
| |||||||||||||||
| 3556 | "C:\Users\admin\MediaGet2\QtWebEngineProcess.exe" --type=utility --enable-features=AllowContentInitiatedDataUrlNavigations,TracingServiceInProcess --disable-features=BackgroundFetch,ConsolidatedMovementXY,DnsOverHttpsUpgrade,FormControlsRefresh,MojoVideoCapture,PictureInPicture,SmsReceiver,UseSkiaRenderer,WebPayments,WebUSB --lang=en-US --service-sandbox-type=network --application-name=MediaGet2 --webengine-schemes=qrc:sLV --mojo-platform-channel-handle=1648 /prefetch:8 | C:\Users\admin\MediaGet2\QtWebEngineProcess.exe | mediaget.exe | ||||||||||||
User: admin Company: The Qt Company Ltd. Integrity Level: HIGH Description: C++ Application Development Framework Exit code: 0 Version: 5.15.2.0 Modules
| |||||||||||||||
| 3712 | "C:\Users\admin\MediaGet2\QtWebEngineProcess.exe" --type=renderer --disable-speech-api --enable-threaded-compositing --enable-features=AllowContentInitiatedDataUrlNavigations,TracingServiceInProcess --disable-features=BackgroundFetch,ConsolidatedMovementXY,DnsOverHttpsUpgrade,FormControlsRefresh,MojoVideoCapture,PictureInPicture,SmsReceiver,UseSkiaRenderer,WebPayments,WebUSB --disable-gpu-compositing --lang=en-US --webengine-schemes=qrc:sLV --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=3 --mojo-platform-channel-handle=2404 /prefetch:1 | C:\Users\admin\MediaGet2\QtWebEngineProcess.exe | — | mediaget.exe | |||||||||||
User: admin Company: The Qt Company Ltd. Integrity Level: LOW Description: C++ Application Development Framework Exit code: 0 Version: 5.15.2.0 Modules
| |||||||||||||||
Total events
1 971
Read events
1 415
Write events
466
Delete events
90
Modification events
| (PID) Process: | (3440) we-were-here-together_id2457064ids1s.exe | Key: | HKEY_CURRENT_USER\Software\Media Get LLC\MediaGet2-systemScope\mediaget_info |
| Operation: | write | Name: | hasDownloadedUpdate |
Value: false | |||
| (PID) Process: | (3440) we-were-here-together_id2457064ids1s.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3440) we-were-here-together_id2457064ids1s.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3440) we-were-here-together_id2457064ids1s.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3440) we-were-here-together_id2457064ids1s.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3440) we-were-here-together_id2457064ids1s.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3440) we-were-here-together_id2457064ids1s.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3440) we-were-here-together_id2457064ids1s.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Width |
Value: 318 | |||
| (PID) Process: | (3440) we-were-here-together_id2457064ids1s.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Height |
Value: 288 | |||
| (PID) Process: | (3440) we-were-here-together_id2457064ids1s.exe | Key: | HKEY_CURRENT_USER\Software\MediaGet |
| Operation: | write | Name: | (default) |
Value: C:\Users\admin\MediaGet2\mediaget.exe | |||
Executable files
149
Suspicious files
73
Text files
235
Unknown types
52
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3440 | we-were-here-together_id2457064ids1s.exe | C:\Users\admin\Desktop\write_file_test | — | |
MD5:— | SHA256:— | |||
| 3440 | we-were-here-together_id2457064ids1s.exe | C:\Users\admin\AppData\Local\Temp\mediaget-installer-tmp\archive.7z | compressed | |
MD5:— | SHA256:— | |||
| 3440 | we-were-here-together_id2457064ids1s.exe | C:\Users\admin\AppData\Local\Temp\mediaget-installer-tmp\img\rucola1.jpg | image | |
MD5:— | SHA256:— | |||
| 3440 | we-were-here-together_id2457064ids1s.exe | C:\Users\admin\AppData\Local\Temp\mediaget-installer-tmp\img\rucola2.jpg | image | |
MD5:— | SHA256:— | |||
| 3440 | we-were-here-together_id2457064ids1s.exe | C:\Users\admin\AppData\Local\Temp\mediaget-installer-tmp\preloader.html | html | |
MD5:3E2A88C55776A6118C91B8B11D5211A3 | SHA256:57B689D69089B3DE9BE51928FE6C9A08664F986BC68EBABBB886BF3C26B1EC03 | |||
| 3440 | we-were-here-together_id2457064ids1s.exe | C:\Users\admin\AppData\Local\Temp\mediaget-installer-tmp\yaclids | text | |
MD5:7ADCD3EBB928564F6AD957C07DB9C4FE | SHA256:C4A774D06B97A966A015278C0F763A483971015C096684BE46008955F8EB3C46 | |||
| 3440 | we-were-here-together_id2457064ids1s.exe | C:\Users\admin\AppData\Local\Temp\mediaget-installer-tmp\img\opera\opera-mockup.jpg | image | |
MD5:5FC2F45724B2CD7A6DAEC6F84FAE01CD | SHA256:898C1B5F3ED1F8236D86E46EE617F9FF9FEAF6192EDEDEEEA3FFD9D99F7AB14A | |||
| 3440 | we-were-here-together_id2457064ids1s.exe | C:\Users\admin\AppData\Local\Temp\mediaget-installer-tmp\img\yandex\yasovetnik-screenshot.jpg | image | |
MD5:D9A31A1AB0D82640C717B743C52E4ACC | SHA256:F88EF77BA384C701CEA4FC329847DE073396098498F757D276286ACC8B493743 | |||
| 3440 | we-were-here-together_id2457064ids1s.exe | C:\Users\admin\AppData\Local\Temp\mediaget-installer-tmp\img\cancel-cancel-grey-en.png | image | |
MD5:B763B80BA47497BD8DFBC3758A31CBA7 | SHA256:4FB6BF93445C6E987D988F9E3ACA6A8380A56F8AFDBAB4940EE69FD20E82B457 | |||
| 3440 | we-were-here-together_id2457064ids1s.exe | C:\Users\admin\AppData\Local\Temp\mediaget-installer-tmp\img\accept.png | image | |
MD5:6974CD17749849D5AAE93AF0A2D5C460 | SHA256:3A505EF15D53235CC633A6137B8232C48825677391CCC911B90ED8FA911BCF19 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
401
DNS requests
29
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3556 | QtWebEngineProcess.exe | GET | 200 | 2.16.186.11:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
3556 | QtWebEngineProcess.exe | GET | 200 | 23.111.31.142:80 | http://sub2.admitlead.ru/r/display/44/bl_up/?a=1&mg_version=3.01.3941&rnd=78338 | NL | text | 325 b | malicious |
3556 | QtWebEngineProcess.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
3556 | QtWebEngineProcess.exe | GET | 200 | 23.111.31.135:80 | http://www2.bubblesmedia.ru/file/mg_qt_banner.php?version=3.01.3941&client_id=&sub_id=bl_up&os=6.1.7601 | NL | html | 699 b | malicious |
3556 | QtWebEngineProcess.exe | GET | 200 | 2.16.186.27:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgQPlXybN0eeb2bVz2Ko5G5p%2Bw%3D%3D | unknown | der | 527 b | whitelisted |
3556 | QtWebEngineProcess.exe | GET | 200 | 23.111.31.142:80 | http://sub2.admitlead.ru/r/get_code_qt/44/?sub_id=bl_up&version=3.01.3941 | NL | html | 5.27 Kb | malicious |
3556 | QtWebEngineProcess.exe | GET | 200 | 172.217.23.131:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEB6CSjN0CZFqBQAAAAB%2BjGs%3D | US | der | 471 b | whitelisted |
3556 | QtWebEngineProcess.exe | GET | 200 | 193.0.201.71:80 | http://admitlead.ru/file/images/557/FwKogn7mvS3fC0HqEaB4.png | RU | image | 158 Kb | malicious |
3556 | QtWebEngineProcess.exe | GET | 200 | 2.16.186.163:80 | http://subca.ocsp-certum.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTYOkzrrCGQj08njZXbUQQpkoUmuQQUCHbNywf%2FJPbFze27kLzihDdGdfcCEQDkBUeDDgxkUpdvejVJwN1I | unknown | der | 1.63 Kb | whitelisted |
3556 | QtWebEngineProcess.exe | GET | 200 | 172.217.23.131:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDCM7HfIeUYqwUAAAAAfoxq | US | der | 472 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2560 | mediaget.exe | 87.98.162.88:6881 | dht.transmissionbt.com | OVH SAS | FR | suspicious |
— | — | 67.215.246.10:6881 | router.bittorrent.com | QuadraNet, Inc | US | suspicious |
— | — | 212.129.33.59:6881 | dht.transmissionbt.com | Online S.a.s. | FR | suspicious |
— | — | 185.45.195.162:28041 | — | NForce Entertainment B.V. | NL | unknown |
3440 | we-were-here-together_id2457064ids1s.exe | 23.111.31.137:443 | mediaget.com | Servers.com, Inc. | NL | unknown |
2560 | mediaget.exe | 92.241.171.245:6881 | update.mgtracker.org | OAO Webalta | RU | suspicious |
— | — | 23.111.31.137:443 | mediaget.com | Servers.com, Inc. | NL | unknown |
— | — | 5.79.68.76:49389 | — | LeaseWeb Netherlands B.V. | NL | unknown |
— | — | 144.76.75.214:51413 | — | Hetzner Online GmbH | DE | unknown |
— | — | 5.79.105.97:51413 | — | LeaseWeb Netherlands B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mediaget.com |
| suspicious |
router.bittorrent.com |
| shared |
dht.transmissionbt.com |
| suspicious |
dht.libtorrent.org |
| suspicious |
update.mgtracker.org |
| suspicious |
tracker.opentrackr.org |
| suspicious |
www.google-analytics.com |
| whitelisted |
turbo.to |
| suspicious |
www2.bubblesmedia.ru |
| malicious |
sub2.admitlead.ru |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2560 | mediaget.exe | Potential Corporate Privacy Violation | ET P2P BitTorrent DHT ping request |
— | — | Potential Corporate Privacy Violation | ET P2P Vuze BT UDP Connection (5) |
1060 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |
1060 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
2560 | mediaget.exe | Potential Corporate Privacy Violation | ET P2P BitTorrent peer sync |
— | — | Potential Corporate Privacy Violation | ET P2P BitTorrent DHT announce_peers request |
Process | Message |
|---|---|
mediaget.exe | > __thiscall Application::Application(int &,char *[])
|
mediaget.exe | os version: "6.1.7601" __ os name: "Windows 7 Version 6.1 (Build 7601: SP 1)"
|
mediaget.exe | > int __thiscall Application::exec(void)
|
mediaget.exe | > __thiscall MediagetServerSettings::MediagetServerSettings(void)
|
mediaget.exe | INSTALL ID: "" _ OLD ID: ""
|
mediaget.exe | reseller - "" installId ""
|
mediaget.exe | > void __thiscall MediagetServerSettings::flushSettings(void)
|
QtWebEngineProcess.exe | Qt WebEngine resources not found at C:/Users/admin/MediaGet2/resources. Trying parent directory...
|
mediaget.exe | main libvlc debug: VLC media player - 3.0.11.1 Vetinari
|
mediaget.exe | main libvlc debug: Copyright © 1996-2020 the VideoLAN team
|