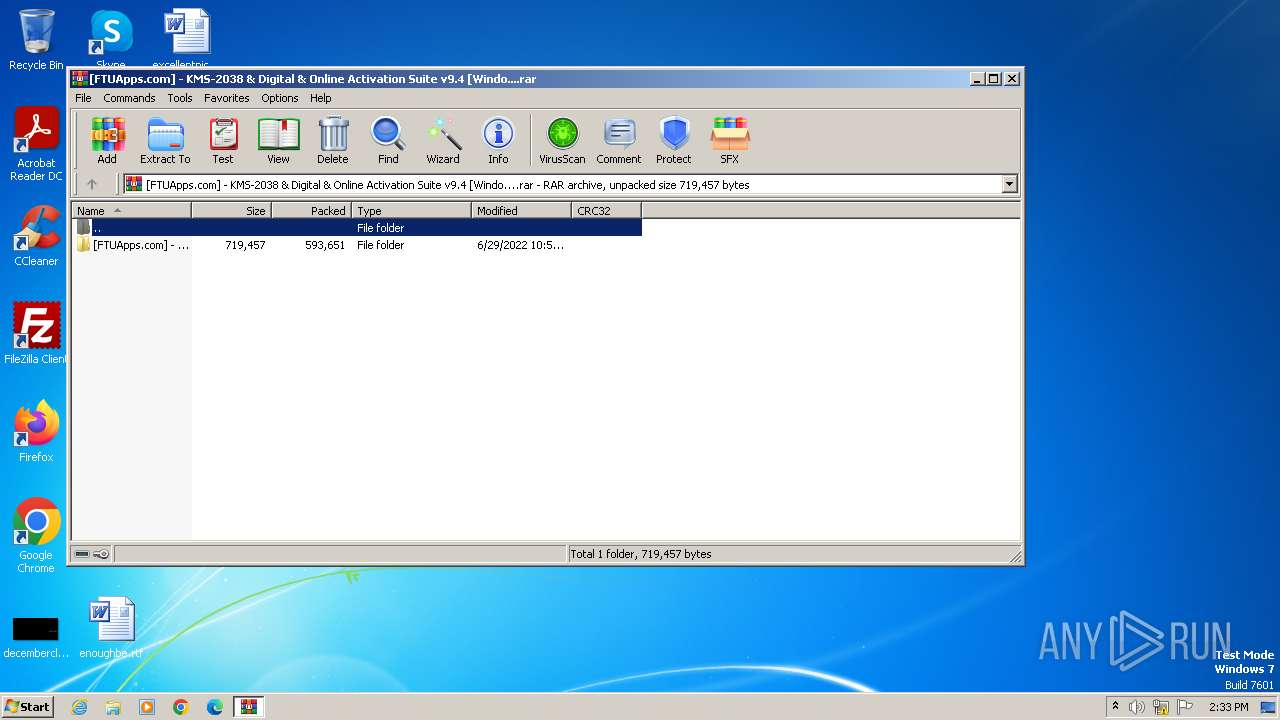
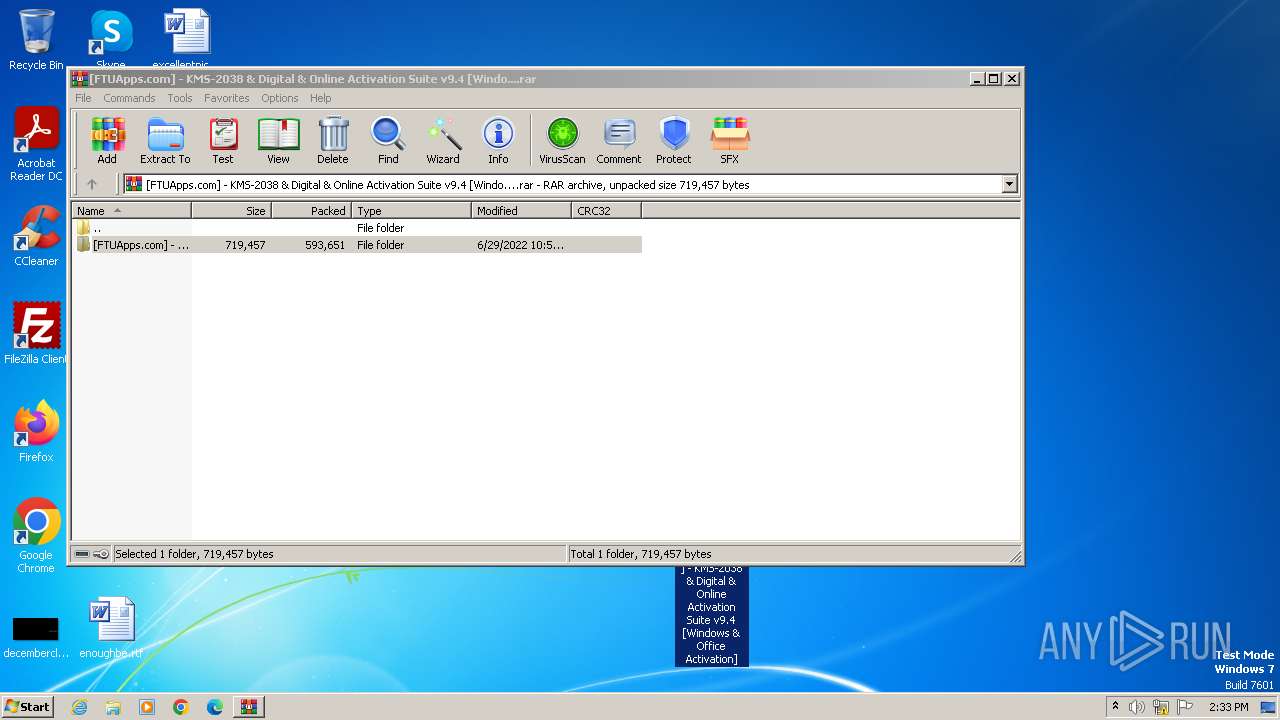
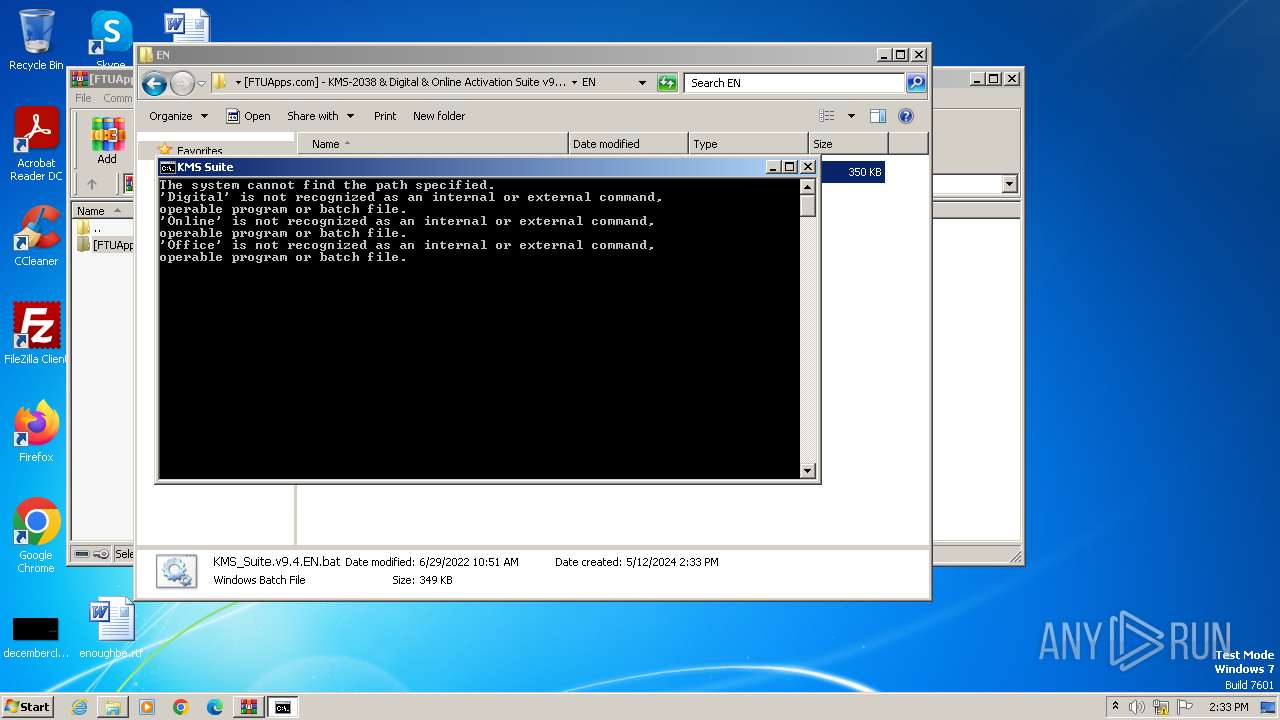
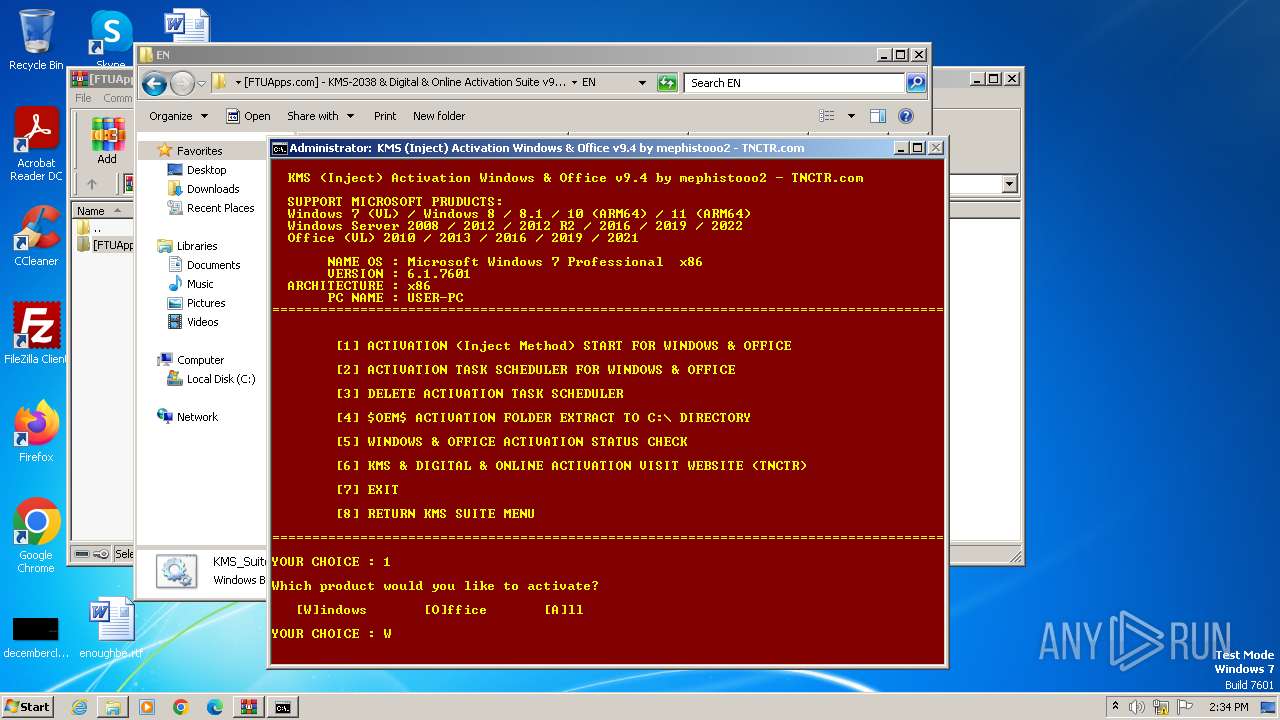
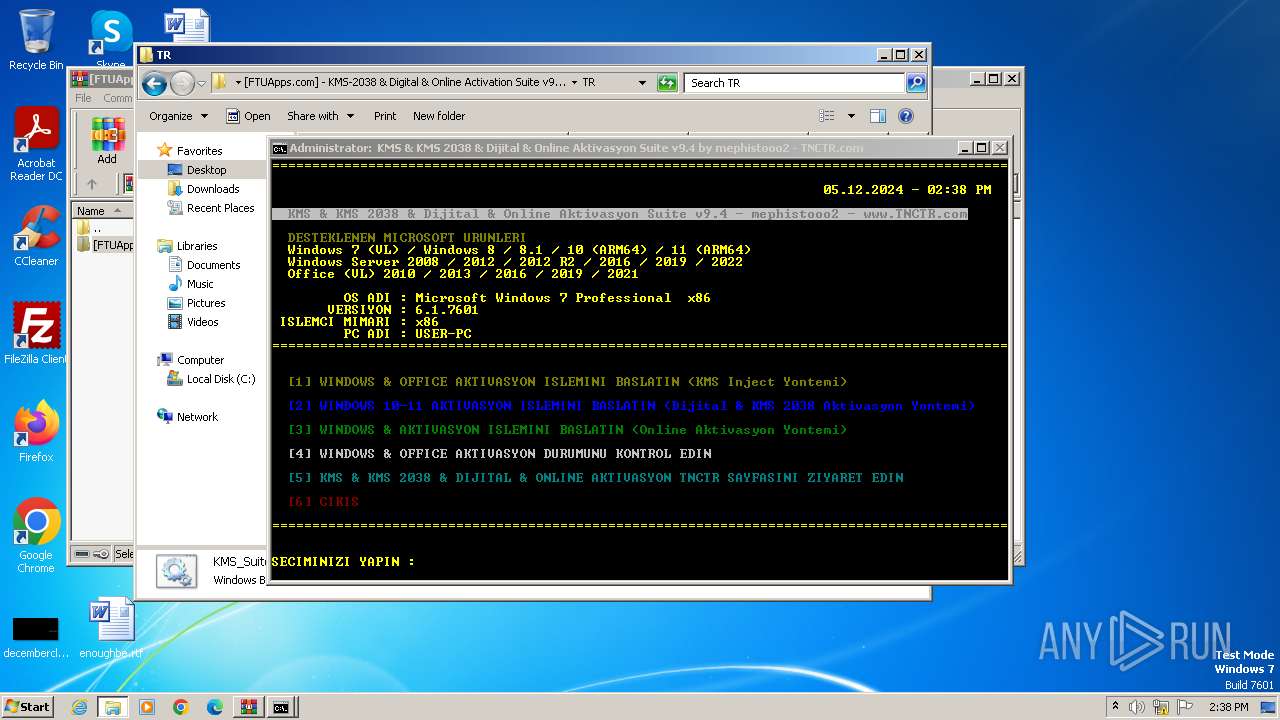
| File name: | [FTUApps.com] - KMS-2038 & Digital & Online Activation Suite v9.4 [Windo....rar |
| Full analysis: | https://app.any.run/tasks/f0da22d5-260b-44cc-bcc3-dab873ebb730 |
| Verdict: | Malicious activity |
| Analysis date: | May 12, 2024, 13:33:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | F17D40E54D1D327690F61BD6E5BE6292 |
| SHA1: | E151FD1D57A6F477C4E67B833CCA9A8E5B8CEDA7 |
| SHA256: | 1AF39C598DAA1F09ADB1046AEF0D5B214DF4A89F94780E11606002C91024A040 |
| SSDEEP: | 24576:oI7UQxwcda2YBbKtGZmnKeueqKX4qbbhmrbYrXlhNrc59EPI/Q:oI7UQxwQa2YBbKtGZmnKeueqKX4qbbhF |
MALICIOUS
Starts Visual C# compiler
- powershell.exe (PID: 1604)
- powershell.exe (PID: 1368)
Drops the executable file immediately after the start
- csc.exe (PID: 1800)
- csc.exe (PID: 1044)
Creates a writable file in the system directory
- cmd.exe (PID: 2460)
Starts NET.EXE for service management
- net.exe (PID: 2336)
- cmd.exe (PID: 2460)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 660)
- cmd.exe (PID: 2244)
- cmd.exe (PID: 2460)
- cmd.exe (PID: 2700)
- cmd.exe (PID: 2816)
- cmd.exe (PID: 2972)
- cmd.exe (PID: 2980)
- cmd.exe (PID: 3788)
- cmd.exe (PID: 3900)
- cmd.exe (PID: 1820)
- cmd.exe (PID: 676)
- cmd.exe (PID: 972)
- cmd.exe (PID: 2452)
- cmd.exe (PID: 2972)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 660)
- cmd.exe (PID: 1820)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 660)
- cmd.exe (PID: 2244)
- cmd.exe (PID: 2460)
- cmd.exe (PID: 2700)
- cmd.exe (PID: 2816)
- cmd.exe (PID: 2972)
- cmd.exe (PID: 2980)
- cmd.exe (PID: 3788)
- cmd.exe (PID: 3900)
- cmd.exe (PID: 1820)
- cmd.exe (PID: 972)
- cmd.exe (PID: 2452)
- cmd.exe (PID: 2972)
- cmd.exe (PID: 676)
Uses .NET C# to load dll
- powershell.exe (PID: 1604)
- powershell.exe (PID: 1368)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 660)
- cmd.exe (PID: 1820)
Executable content was dropped or overwritten
- csc.exe (PID: 1800)
- expand.exe (PID: 1932)
- xcopy.exe (PID: 1548)
- expand.exe (PID: 1344)
- xcopy.exe (PID: 2548)
- csc.exe (PID: 1044)
Process drops legitimate windows executable
- expand.exe (PID: 1932)
- xcopy.exe (PID: 1548)
- expand.exe (PID: 1344)
- xcopy.exe (PID: 2548)
Executing commands from a ".bat" file
- powershell.exe (PID: 2232)
- cmd.exe (PID: 660)
- cmd.exe (PID: 1820)
- powershell.exe (PID: 2076)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 660)
- cmd.exe (PID: 2460)
- powershell.exe (PID: 2232)
- cmd.exe (PID: 1820)
- powershell.exe (PID: 2076)
- cmd.exe (PID: 972)
Application launched itself
- cmd.exe (PID: 660)
- cmd.exe (PID: 2460)
- cmd.exe (PID: 1820)
- cmd.exe (PID: 972)
Powershell scripting: start process
- cmd.exe (PID: 2244)
- cmd.exe (PID: 676)
Reads the Internet Settings
- powershell.exe (PID: 2232)
- wscript.exe (PID: 2360)
- cmd.exe (PID: 2460)
- WMIC.exe (PID: 3412)
- WMIC.exe (PID: 324)
- WMIC.exe (PID: 1576)
- WMIC.exe (PID: 936)
- WMIC.exe (PID: 1012)
- WMIC.exe (PID: 2412)
- WMIC.exe (PID: 2748)
- WMIC.exe (PID: 2400)
- WMIC.exe (PID: 916)
- powershell.exe (PID: 2076)
- cmd.exe (PID: 972)
- wscript.exe (PID: 2364)
The executable file from the user directory is run by the CMD process
- center.exe (PID: 2548)
- center.exe (PID: 2516)
The process executes VB scripts
- cmd.exe (PID: 2460)
- cmd.exe (PID: 972)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2360)
- wscript.exe (PID: 2364)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 2360)
- wscript.exe (PID: 2364)
Blank space has been found in the path
- cmd.exe (PID: 2460)
- cmd.exe (PID: 972)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2460)
- cmd.exe (PID: 972)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 2460)
Starts SC.EXE for service management
- cmd.exe (PID: 2460)
Hides command output
- cmd.exe (PID: 1704)
- cmd.exe (PID: 1552)
- cmd.exe (PID: 2104)
- cmd.exe (PID: 928)
- cmd.exe (PID: 2240)
- cmd.exe (PID: 2556)
- cmd.exe (PID: 2020)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 2460)
- cmd.exe (PID: 2076)
- cmd.exe (PID: 2780)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2460)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 1868)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 2460)
INFO
Manual execution by a user
- cmd.exe (PID: 660)
- cmd.exe (PID: 1820)
Checks supported languages
- csc.exe (PID: 1800)
- cvtres.exe (PID: 1836)
- mode.com (PID: 692)
- mode.com (PID: 2240)
- mode.com (PID: 2340)
- mode.com (PID: 676)
- center.exe (PID: 2548)
- DisableX.exe (PID: 2708)
- mode.com (PID: 2892)
- mode.com (PID: 2944)
- mode.com (PID: 3144)
- mode.com (PID: 1932)
- mode.com (PID: 2468)
- mode.com (PID: 2080)
- cvtres.exe (PID: 1012)
- csc.exe (PID: 1044)
- mode.com (PID: 4032)
- mode.com (PID: 2552)
- mode.com (PID: 2816)
- mode.com (PID: 1408)
- mode.com (PID: 2512)
- center.exe (PID: 2516)
- DisableX.exe (PID: 2620)
- mode.com (PID: 3260)
Create files in a temporary directory
- csc.exe (PID: 1800)
- cvtres.exe (PID: 1836)
- expand.exe (PID: 1932)
- xcopy.exe (PID: 1548)
- csc.exe (PID: 1044)
- xcopy.exe (PID: 2548)
- cvtres.exe (PID: 1012)
- expand.exe (PID: 1344)
Reads the machine GUID from the registry
- csc.exe (PID: 1800)
- cvtres.exe (PID: 1836)
- cvtres.exe (PID: 1012)
- csc.exe (PID: 1044)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1604)
- powershell.exe (PID: 1368)
Drops the executable file immediately after the start
- expand.exe (PID: 1932)
- xcopy.exe (PID: 1548)
- expand.exe (PID: 1344)
- xcopy.exe (PID: 2548)
Checks operating system version
- cmd.exe (PID: 2460)
Reads Microsoft Office registry keys
- reg.exe (PID: 1548)
- reg.exe (PID: 3284)
- reg.exe (PID: 3268)
- reg.exe (PID: 2832)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
268
Monitored processes
218
Malicious processes
6
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe" /f /v KMS_RenewalInterval /t REG_DWORD /d 43200 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 304 | reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe" /f /v VerifierFlags /t REG_DWORD /d 0x80000000 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 324 | wmic path SoftwareLicensingProduct where (Description like '%KMSCLIENT%' ) get Name /value | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 368 | C:\Windows\system32\cmd.exe /c time /t | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 588 | reg delete "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\osppsvc.exe" /f /v Debugger | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 600 | findstr "1" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 660 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\[FTUApps.com] - KMS-2038 & Digital & Online Activation Suite v9.4 [Windows & Office Activation]\EN\KMS_Suite.v9.4.EN.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 255 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 660 | reg delete "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\55c92734-d682-4d71-983e-d6ec3f16059f" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 664 | reg delete "HKU\S-1-5-20\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\55c92734-d682-4d71-983e-d6ec3f16059f" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 676 | mode con cols=92 lines=35 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
46 892
Read events
46 794
Write events
80
Delete events
18
Modification events
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\[FTUApps.com] - KMS-2038 & Digital & Online Activation Suite v9.4 [Windo....rar | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
56
Suspicious files
32
Text files
87
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
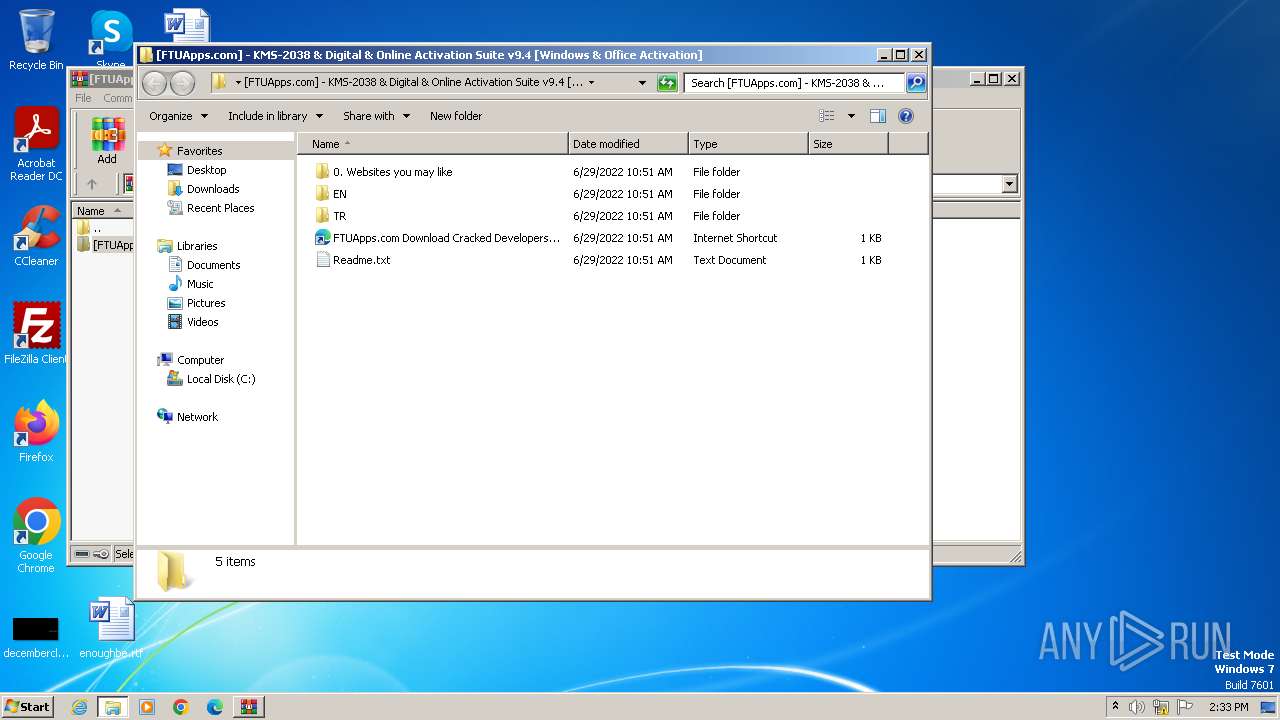
| 3988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3988.12857\[FTUApps.com] - KMS-2038 & Digital & Online Activation Suite v9.4 [Windows & Office Activation]\FTUApps.com Download Cracked Developers Applications For Free.url | url | |
MD5:708A581C8010D315C99C5ED36512CA2C | SHA256:0F5746A7B0CD0A4904117B92F1330FBBA1981BFFF6AA8913C6EC19C0FF7F65B6 | |||
| 3988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3988.12857\[FTUApps.com] - KMS-2038 & Digital & Online Activation Suite v9.4 [Windows & Office Activation]\EN\KMS_Suite.v9.4.EN.bat | text | |
MD5:D89B73628837F9B1DED1CCE801D1C342 | SHA256:238797E00B9C9BC81CB5209BB7A149EFCED89C60D6B84E530884657DDA4FF513 | |||
| 1604 | powershell.exe | C:\Users\admin\AppData\Local\Temp\12r5rbvc.0.cs | text | |
MD5:2619C2087E535BD9EF20A732A58BFA84 | SHA256:85835D9BE283D806347DB25628B7E5108A11F46F9EF540656DF28F09F66CA0FB | |||
| 1800 | csc.exe | C:\Users\admin\AppData\Local\Temp\12r5rbvc.dll | executable | |
MD5:BD465396D98A4FF9261212C4C57BF2D4 | SHA256:3C36059FDC2FC82B787C94F5ED5C8F0613D0C41B74F96C53DADFD8C29ECA0C69 | |||
| 3988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3988.12857\[FTUApps.com] - KMS-2038 & Digital & Online Activation Suite v9.4 [Windows & Office Activation]\Readme.txt | text | |
MD5:1DAB7853DBBED7BFFE4584CA1DFC4DB8 | SHA256:F4137E9003953CA3C715C386110C81B744FBB82A78C38DB6E867404EB5E71151 | |||
| 1604 | powershell.exe | C:\Users\admin\AppData\Local\Temp\12r5rbvc.cmdline | text | |
MD5:8BB93C3ADB584A3074C850F5489D3ABD | SHA256:985EF0495EC58539A0CB4B212D6BDEBC4A5C2C40C8EC3A734DAC2E5D722008F4 | |||
| 1932 | expand.exe | C:\Users\admin\AppData\Local\Temp\KMS_Suite\KMS_Suite.bat | text | |
MD5:207D21899E0C0CC765A9C17DD22D86B6 | SHA256:708ECFBD75F3D5CBC3A55044DFAB774B1E9D68B20AD0826A18050A0D89630119 | |||
| 3988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3988.12857\[FTUApps.com] - KMS-2038 & Digital & Online Activation Suite v9.4 [Windows & Office Activation]\TR\KMS_Suite.v9.4.TR.bat | text | |
MD5:BD1C2A91640014B0DC15356CA3A3790B | SHA256:C4D71A21C4D6A9F6149B70A6F3A2531ECCEE397DD6001C7967779E5D3A0E16E2 | |||
| 1800 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC45CCE56058704160A563F9FF8E9EB71.TMP | binary | |
MD5:3FF82196E5C12E4752DC64FD9BA32272 | SHA256:BD365CA32DCEA6E3159AF6FF607D18348094ECA5FFD83592F185BCBF73511353 | |||
| 1836 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES8222.tmp | binary | |
MD5:64209D9B59B74D7A33B544F714C4E5A5 | SHA256:03959523DF057644BE4546FE3F21D45B4589EBB1B4BE8BB831676735AA4A7F1D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |