| File name: | [FTUApps.com] - KMS-2038 & Digital & Online Activation Suite v9.4 [Windo....rar |
| Full analysis: | https://app.any.run/tasks/b9e6ff0f-4bbe-4e01-96f2-d88e65b4ad7c |
| Verdict: | Malicious activity |
| Analysis date: | May 12, 2024, 13:31:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | F17D40E54D1D327690F61BD6E5BE6292 |
| SHA1: | E151FD1D57A6F477C4E67B833CCA9A8E5B8CEDA7 |
| SHA256: | 1AF39C598DAA1F09ADB1046AEF0D5B214DF4A89F94780E11606002C91024A040 |
| SSDEEP: | 24576:oI7UQxwcda2YBbKtGZmnKeueqKX4qbbhmrbYrXlhNrc59EPI/Q:oI7UQxwQa2YBbKtGZmnKeueqKX4qbbhF |
MALICIOUS
Starts Visual C# compiler
- powershell.exe (PID: 1604)
Drops the executable file immediately after the start
- csc.exe (PID: 1944)
Creates a writable file in the system directory
- cmd.exe (PID: 2624)
Starts NET.EXE for service management
- cmd.exe (PID: 2624)
- net.exe (PID: 2524)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 316)
- cmd.exe (PID: 1640)
- cmd.exe (PID: 2624)
- cmd.exe (PID: 2388)
- cmd.exe (PID: 2688)
- cmd.exe (PID: 2988)
- cmd.exe (PID: 3072)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 316)
- cmd.exe (PID: 1640)
- cmd.exe (PID: 2624)
- cmd.exe (PID: 2388)
- cmd.exe (PID: 2688)
- cmd.exe (PID: 2988)
- cmd.exe (PID: 3072)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 316)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 316)
Uses .NET C# to load dll
- powershell.exe (PID: 1604)
Executable content was dropped or overwritten
- csc.exe (PID: 1944)
- expand.exe (PID: 1844)
- xcopy.exe (PID: 580)
Process drops legitimate windows executable
- xcopy.exe (PID: 580)
- expand.exe (PID: 1844)
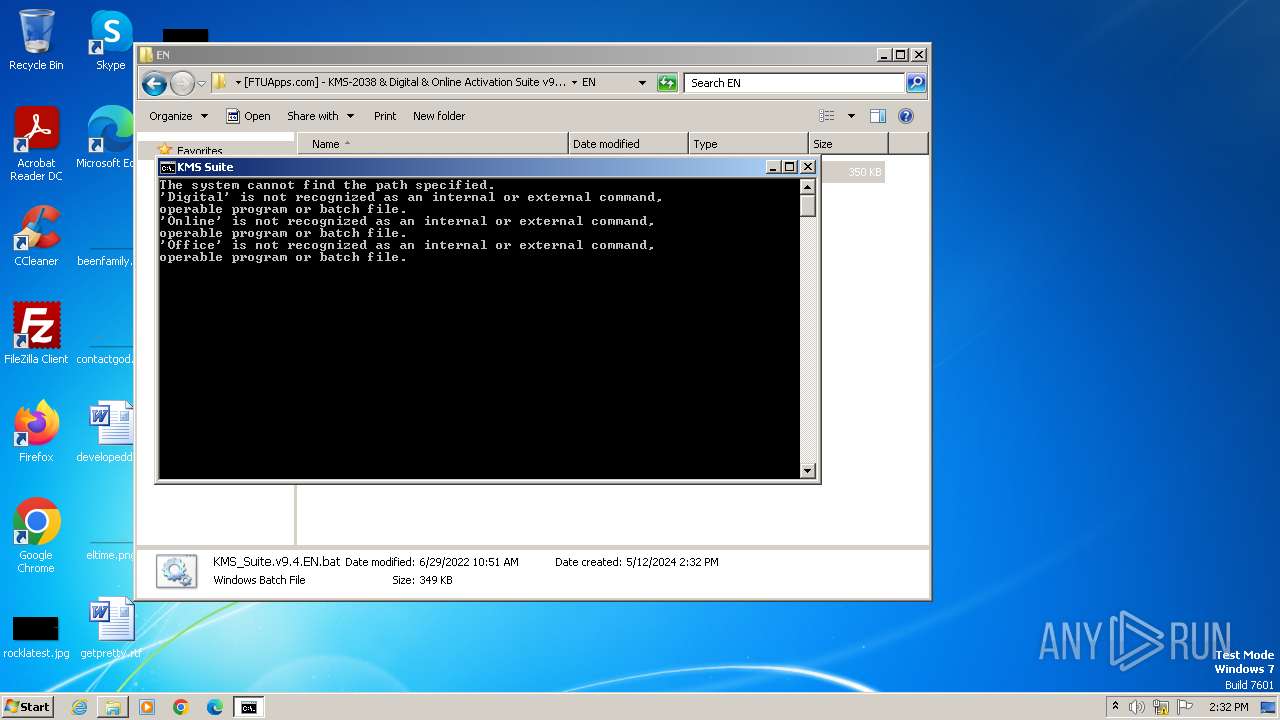
Executing commands from a ".bat" file
- cmd.exe (PID: 316)
- powershell.exe (PID: 2348)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 316)
- powershell.exe (PID: 2348)
- cmd.exe (PID: 2624)
Powershell scripting: start process
- cmd.exe (PID: 1640)
Application launched itself
- cmd.exe (PID: 316)
- cmd.exe (PID: 2624)
Reads the Internet Settings
- powershell.exe (PID: 2348)
- cmd.exe (PID: 2624)
- wscript.exe (PID: 956)
- WMIC.exe (PID: 3408)
- WMIC.exe (PID: 2480)
- WMIC.exe (PID: 2476)
- WMIC.exe (PID: 2188)
- WMIC.exe (PID: 2560)
- WMIC.exe (PID: 2416)
- WMIC.exe (PID: 2768)
- WMIC.exe (PID: 1576)
- WMIC.exe (PID: 2664)
The executable file from the user directory is run by the CMD process
- center.exe (PID: 1568)
The process executes VB scripts
- cmd.exe (PID: 2624)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 956)
Runs shell command (SCRIPT)
- wscript.exe (PID: 956)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2624)
Blank space has been found in the path
- cmd.exe (PID: 2624)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 2624)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2624)
Starts SC.EXE for service management
- cmd.exe (PID: 2624)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 2624)
Hides command output
- cmd.exe (PID: 2064)
- cmd.exe (PID: 2284)
- cmd.exe (PID: 1824)
- cmd.exe (PID: 1676)
- cmd.exe (PID: 1548)
- cmd.exe (PID: 112)
- cmd.exe (PID: 1876)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 2624)
- cmd.exe (PID: 2300)
- cmd.exe (PID: 948)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 2448)
INFO
Manual execution by a user
- cmd.exe (PID: 316)
Checks supported languages
- mode.com (PID: 692)
- csc.exe (PID: 1944)
- cvtres.exe (PID: 1796)
- mode.com (PID: 2244)
- mode.com (PID: 324)
- mode.com (PID: 2472)
- center.exe (PID: 1568)
- mode.com (PID: 2076)
- DisableX.exe (PID: 2504)
- mode.com (PID: 2784)
- mode.com (PID: 3092)
- mode.com (PID: 2840)
- mode.com (PID: 1944)
Create files in a temporary directory
- cvtres.exe (PID: 1796)
- csc.exe (PID: 1944)
- expand.exe (PID: 1844)
- xcopy.exe (PID: 580)
Reads the machine GUID from the registry
- csc.exe (PID: 1944)
- cvtres.exe (PID: 1796)
Drops the executable file immediately after the start
- expand.exe (PID: 1844)
- xcopy.exe (PID: 580)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1604)
Checks operating system version
- cmd.exe (PID: 2624)
Reads Microsoft Office registry keys
- reg.exe (PID: 2092)
- reg.exe (PID: 2884)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
195
Monitored processes
154
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 112 | C:\Windows\system32\cmd.exe /c "reg query HKLM\SOFTWARE\Wow6432Node\Microsoft\Office\15.0\Common\InstallRoot /v Path" 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 308 | reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe" /f /v KMS_Emulation /t REG_DWORD /d 1 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 316 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\[FTUApps.com] - KMS-2038 & Digital & Online Activation Suite v9.4 [Windows & Office Activation]\EN\KMS_Suite.v9.4.EN.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 255 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 324 | mode con cols=78 lines=6 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
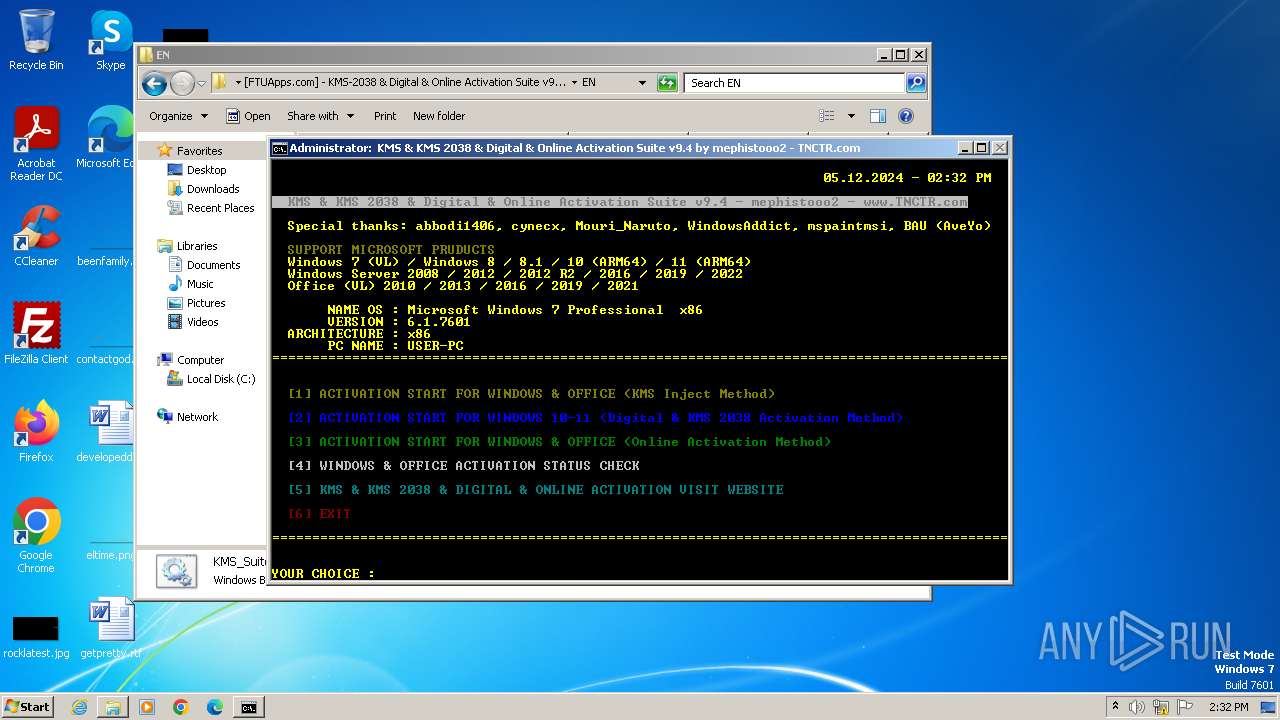
| 368 | choice /C:12345678 /N /M "YOUR CHOICE : " | C:\Windows\System32\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Offers the user a choice Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 560 | findstr "1" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 580 | xcopy /s /h KMS_Suite 20536 | C:\Windows\System32\xcopy.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extended Copy Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 580 | reg query HKLM\SOFTWARE\Wow6432Node\Microsoft\Office\14.0\Common\InstallRoot /v Path | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 616 | reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\osppsvc.exe" /f /v GlobalFlag /t REG_DWORD /d 0x00000100 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 664 | powershell -noprofile "$W=(get-host).ui.rawui; $B=$W.buffersize; $B.height=90; $W.buffersize=$B" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
27 098
Read events
27 028
Write events
65
Delete events
5
Modification events
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\[FTUApps.com] - KMS-2038 & Digital & Online Activation Suite v9.4 [Windo....rar | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
28
Suspicious files
18
Text files
48
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3968.2829\[FTUApps.com] - KMS-2038 & Digital & Online Activation Suite v9.4 [Windows & Office Activation]\0. Websites you may like\1. Get Free Premium Accounts Daily On Our Discord Server!.txt | text | |
MD5:7E2BC71B046D54FDE236216919E007D2 | SHA256:5151A0DA914EAE36575D3A7764F29E6948C8D6A3181A599AAEB555F78DC47D82 | |||
| 1604 | powershell.exe | C:\Users\admin\AppData\Local\Temp\pmckcics.qnc.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1604 | powershell.exe | C:\Users\admin\AppData\Local\Temp\rntm2wbu.0.cs | text | |
MD5:2619C2087E535BD9EF20A732A58BFA84 | SHA256:85835D9BE283D806347DB25628B7E5108A11F46F9EF540656DF28F09F66CA0FB | |||
| 1944 | csc.exe | C:\Users\admin\AppData\Local\Temp\rntm2wbu.dll | executable | |
MD5:663E8FF37219B6F4355B379838A88961 | SHA256:BA53E9BD2B32C56B9E5126280938D2E52C037521F5D888A38B39CC71DF7DE514 | |||
| 1604 | powershell.exe | C:\Users\admin\AppData\Local\Temp\rntm2wbu.cmdline | text | |
MD5:11E49C9D1BB78B3D4A2A51E8BB3FF658 | SHA256:04F628FCCC52F013523F78E0BBD4F61220F605EF9A8DE439BE783FFF221C45AE | |||
| 1796 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES7B2D.tmp | binary | |
MD5:6B279A320507EFC6140C005414B44719 | SHA256:2A1D495710EA15C809A75C7601032F532621D4048786F84C07D514B490AA5CCB | |||
| 1844 | expand.exe | C:\Users\admin\AppData\Local\Temp\KMS_Suite\bin\DisableX.vbs | text | |
MD5:C2206C9C9B0C97F7C5DB4F473E96E9A3 | SHA256:F1CEC878CD1DB36CA4CCB68296CD47CE039054E2ECE4CD22D9933B90C8625C1F | |||
| 1844 | expand.exe | C:\Users\admin\AppData\Local\Temp\KMS_Suite\KMS_Suite.bat | text | |
MD5:207D21899E0C0CC765A9C17DD22D86B6 | SHA256:708ECFBD75F3D5CBC3A55044DFAB774B1E9D68B20AD0826A18050A0D89630119 | |||
| 1844 | expand.exe | C:\Users\admin\AppData\Local\Temp\KMS_Suite\bin\Inject\KMSInject.bat | — | |
MD5:— | SHA256:— | |||
| 1844 | expand.exe | C:\Users\admin\AppData\Local\Temp\KMS_Suite\bin\Inject\$OEM$\$\Setup\Scripts\run.bat | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |