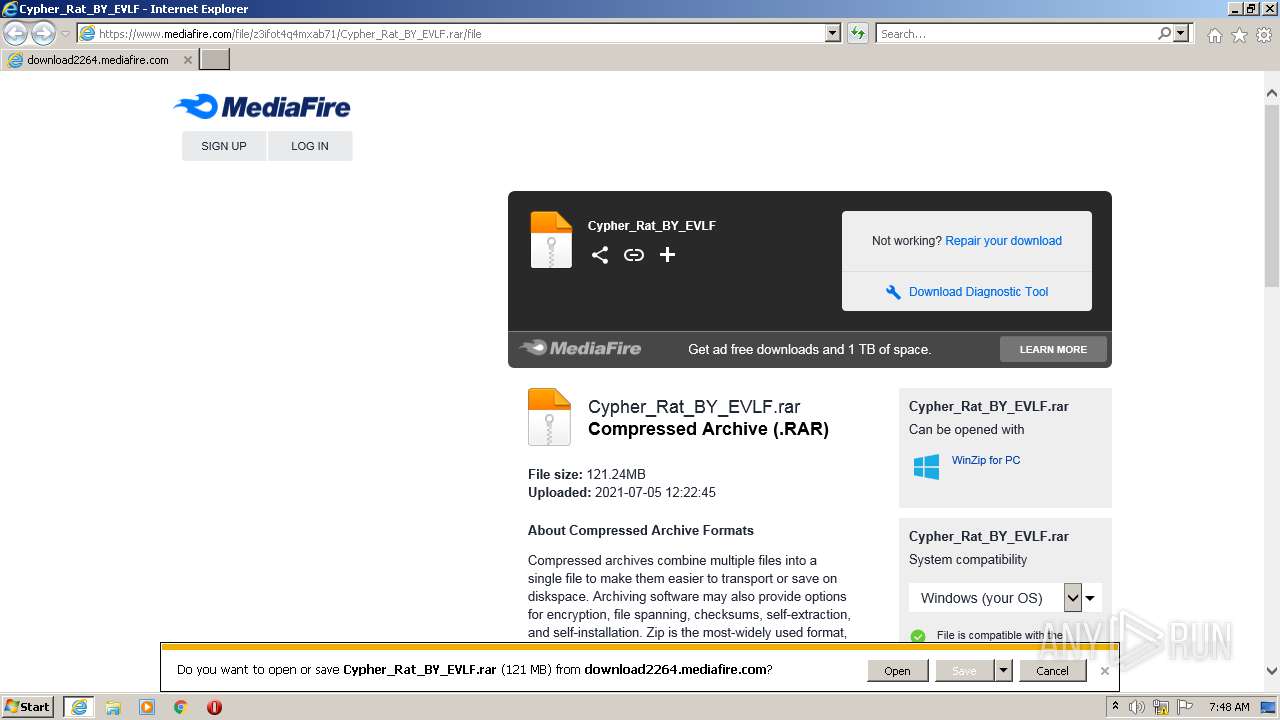
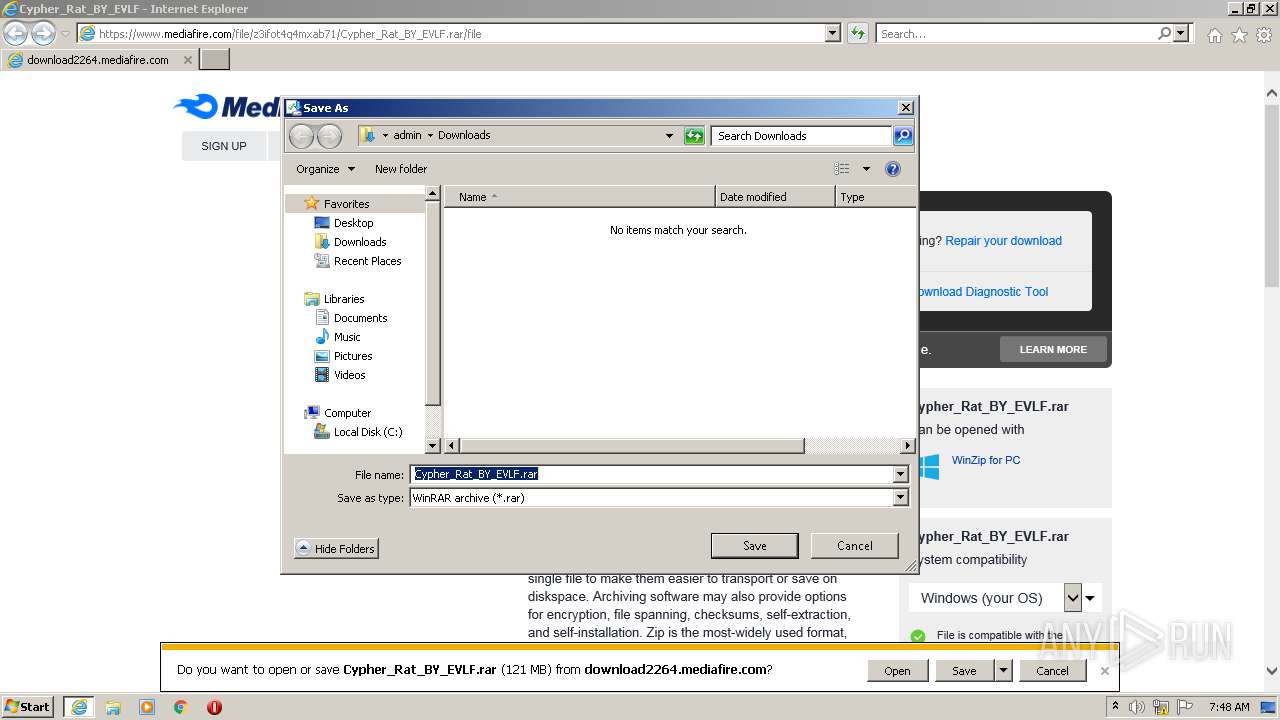
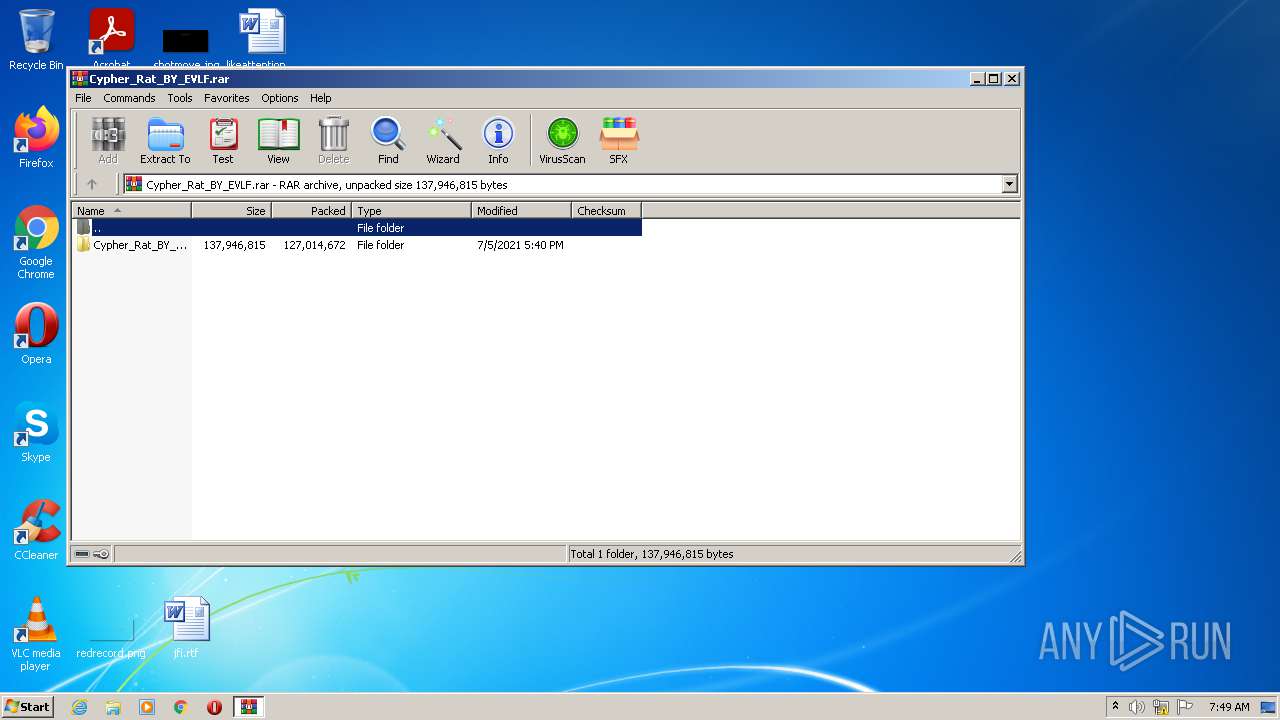
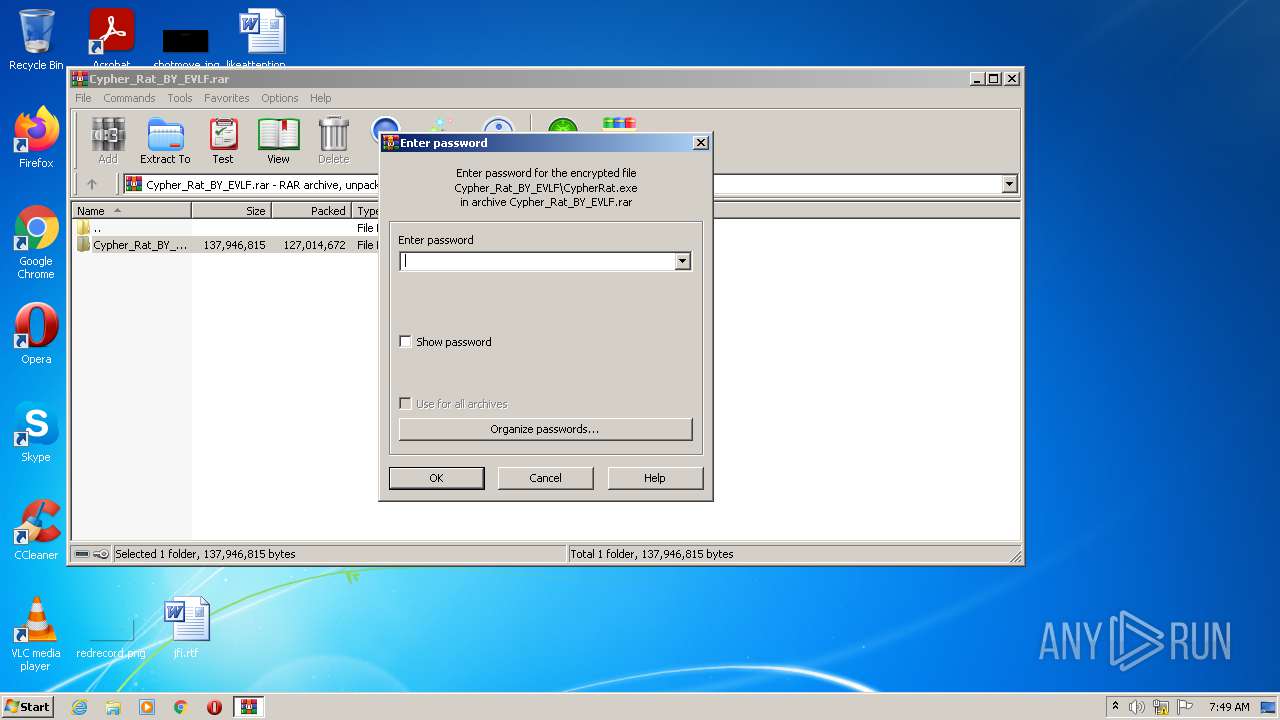
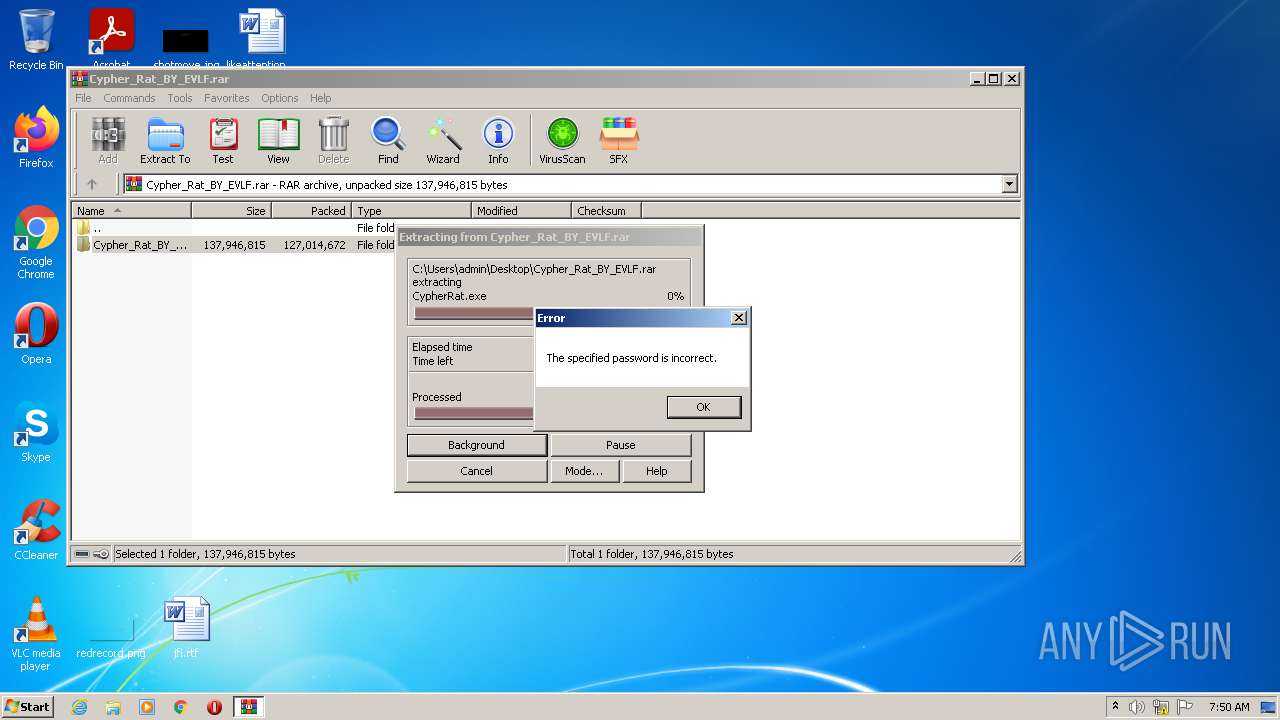
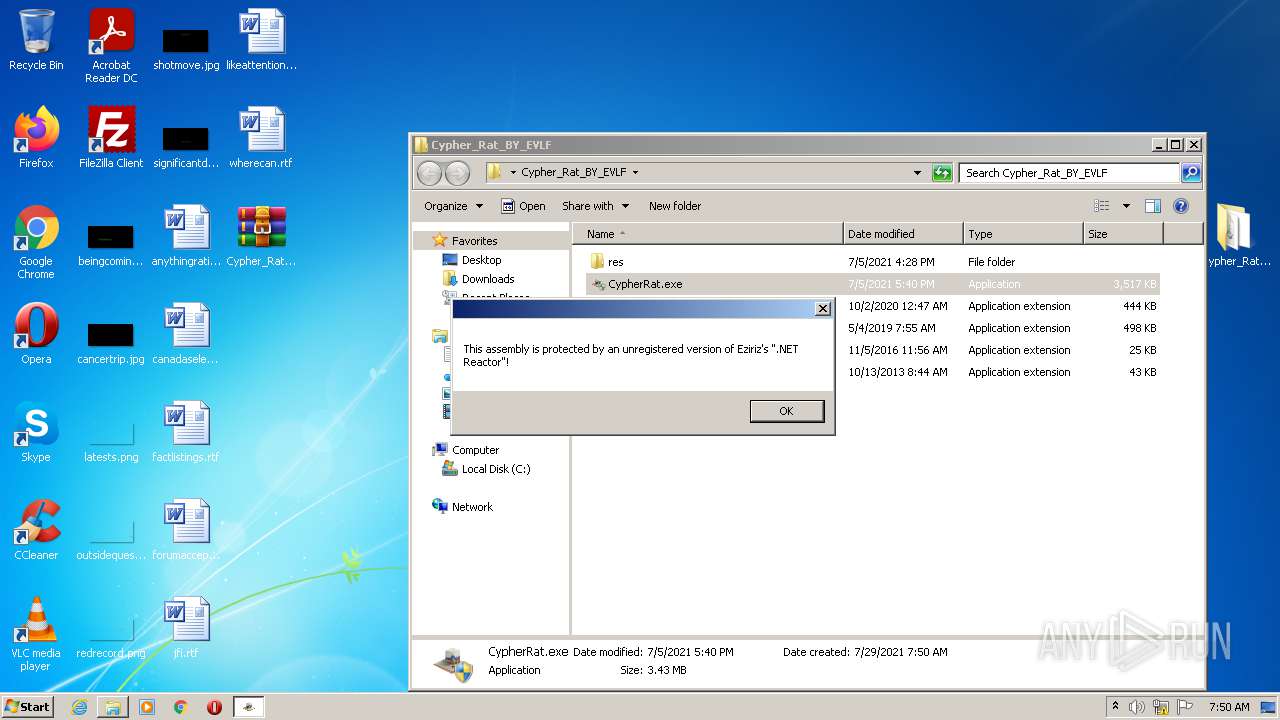
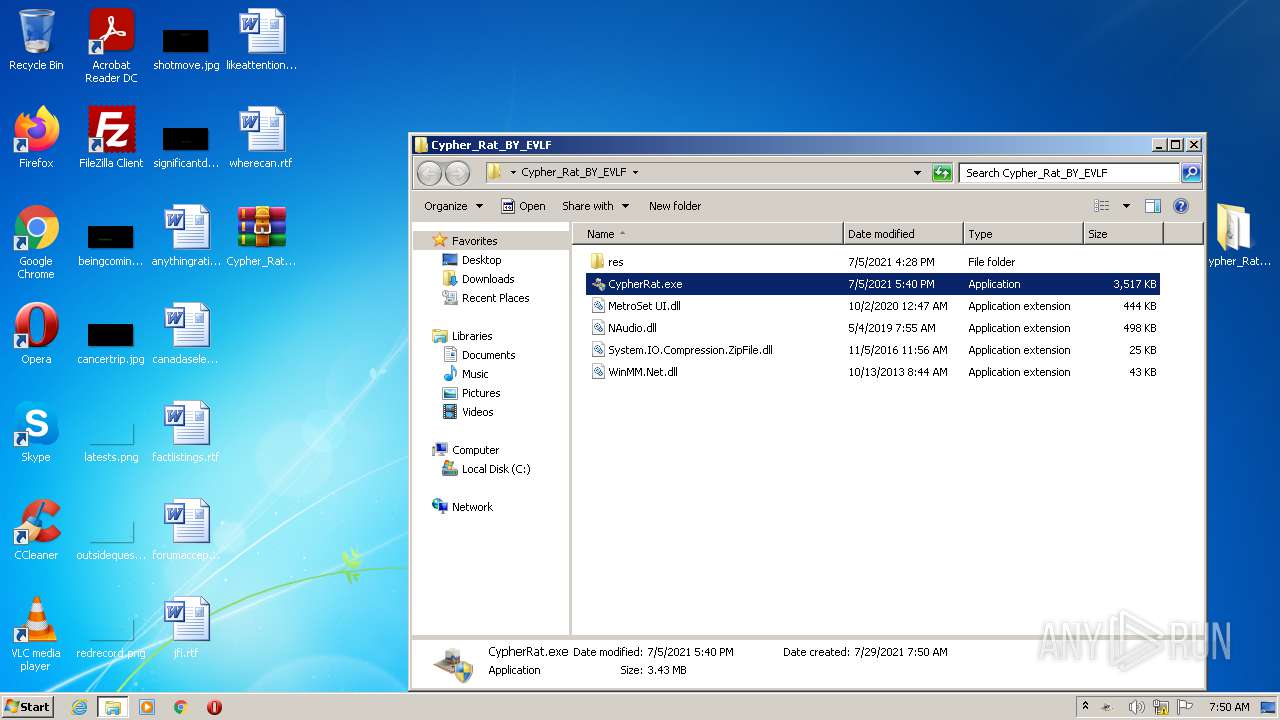
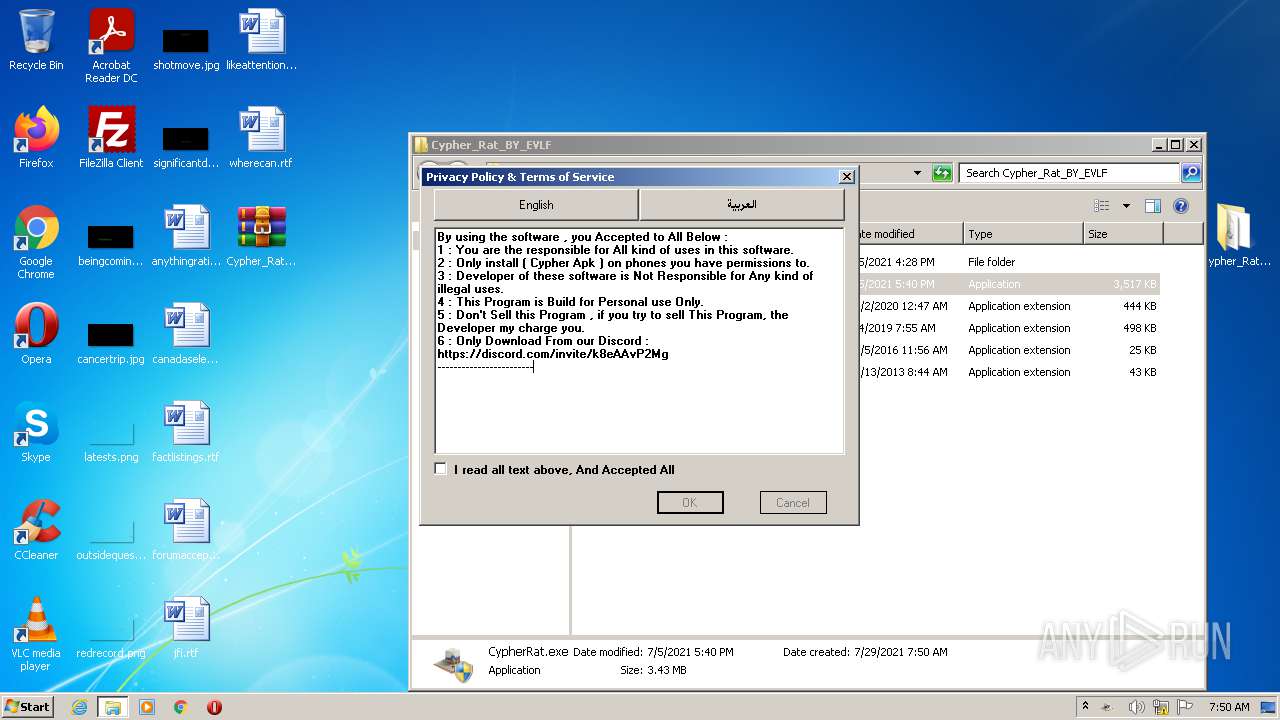
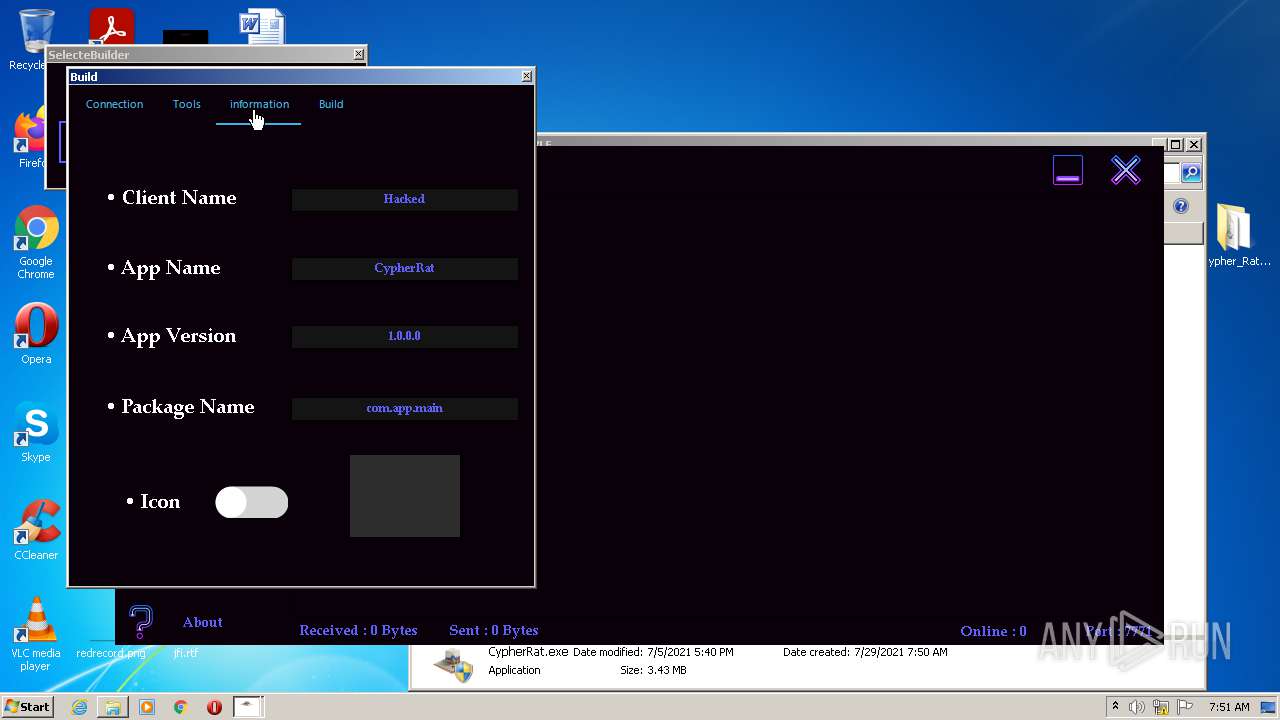
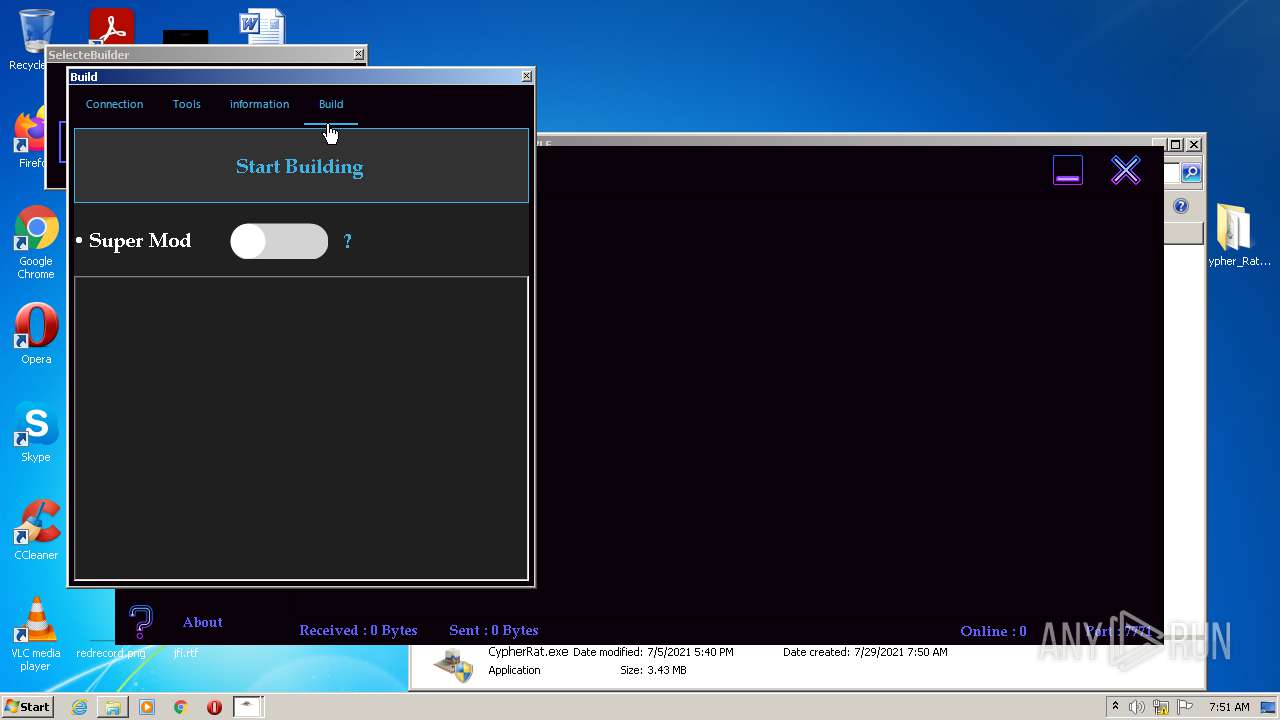
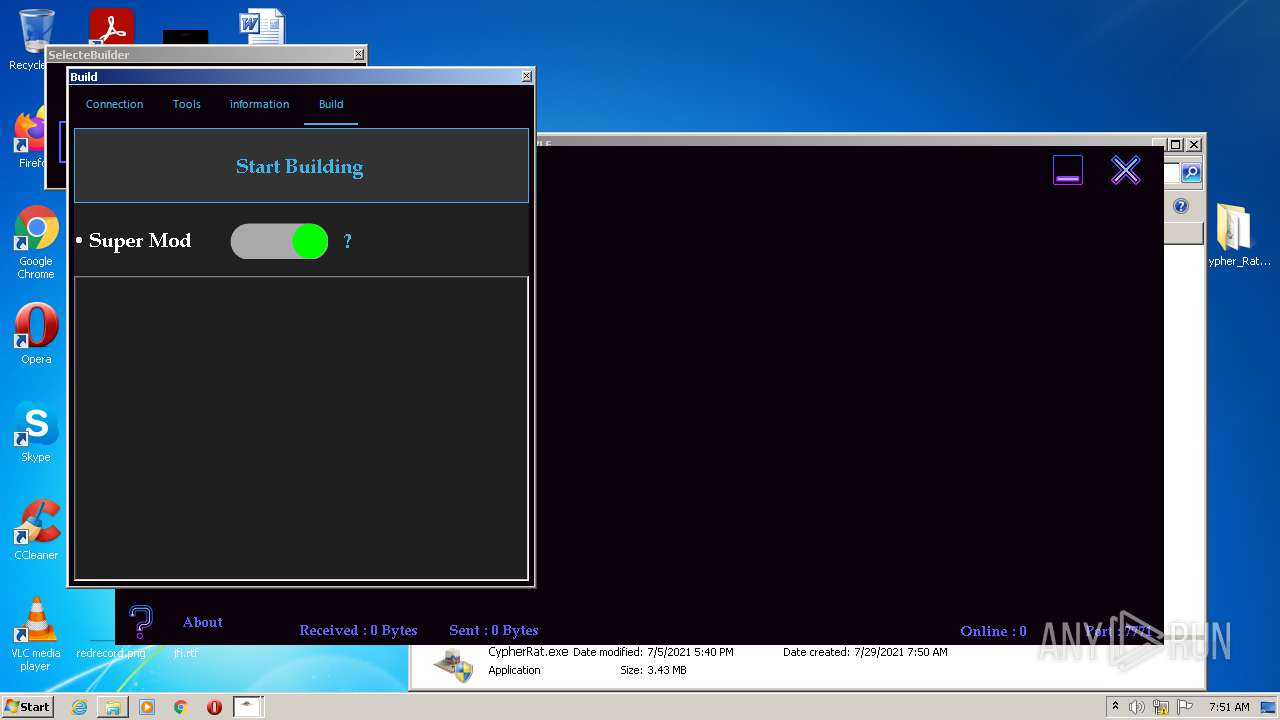
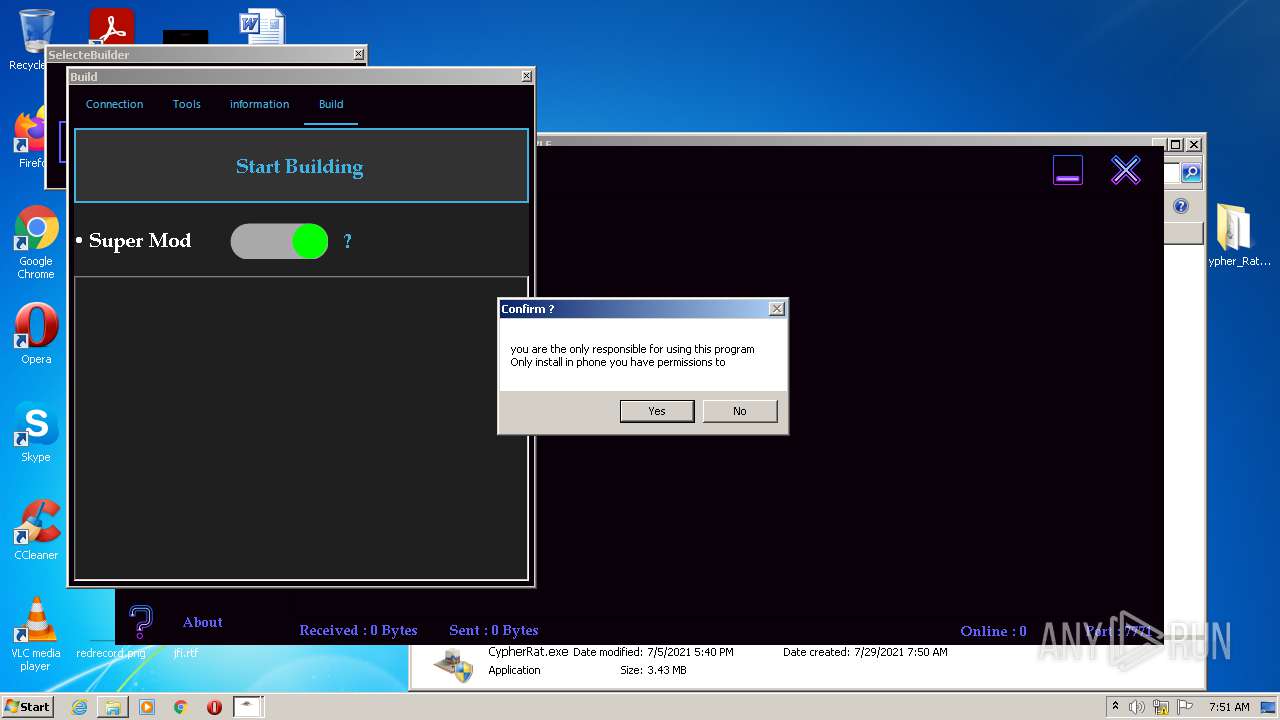
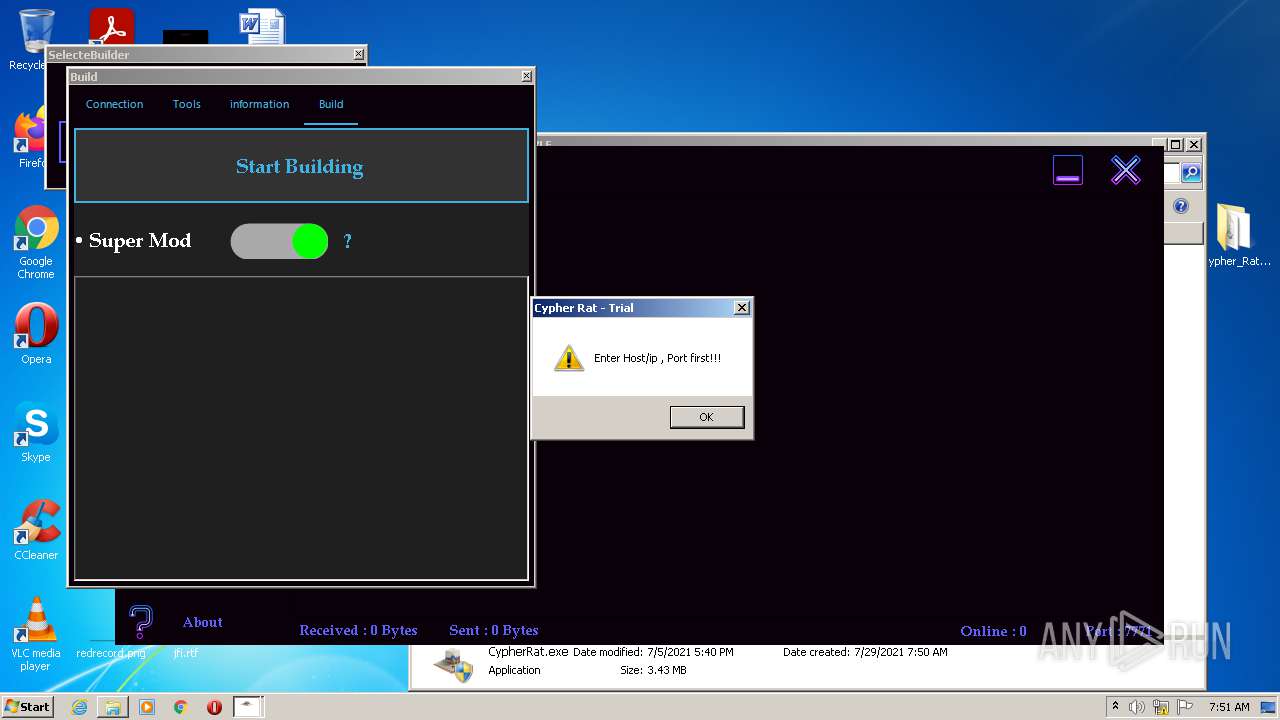
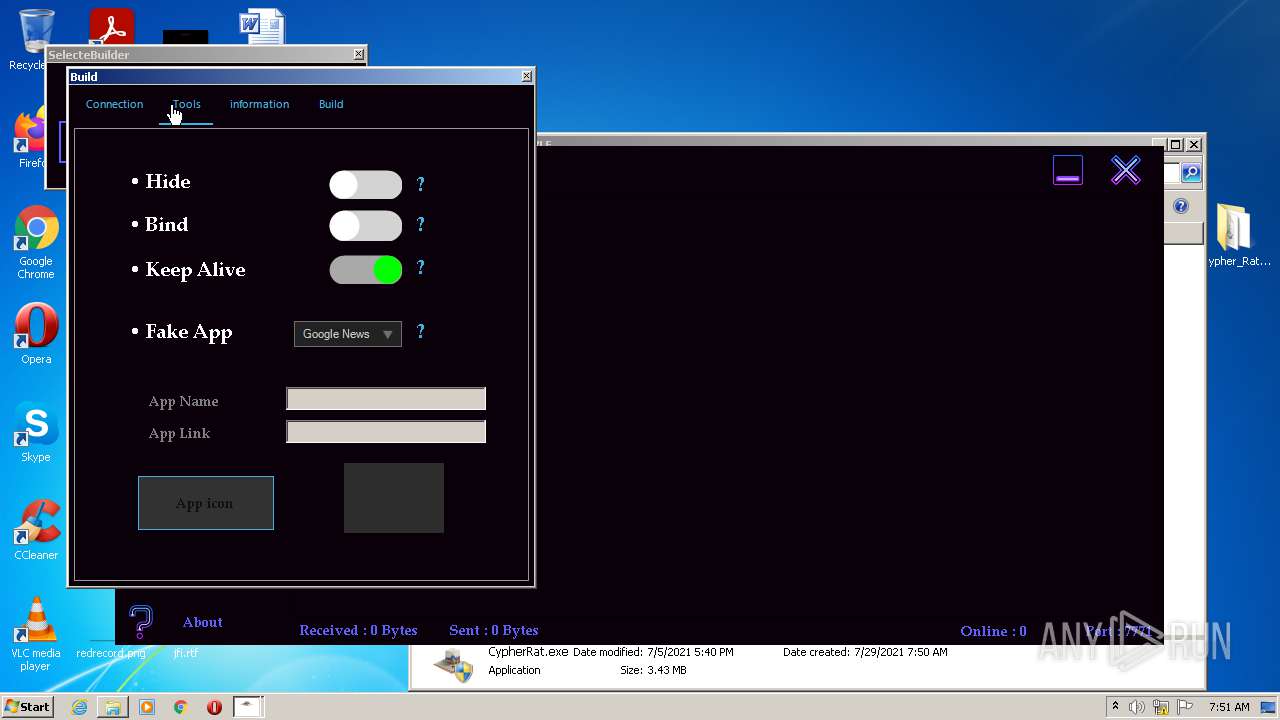
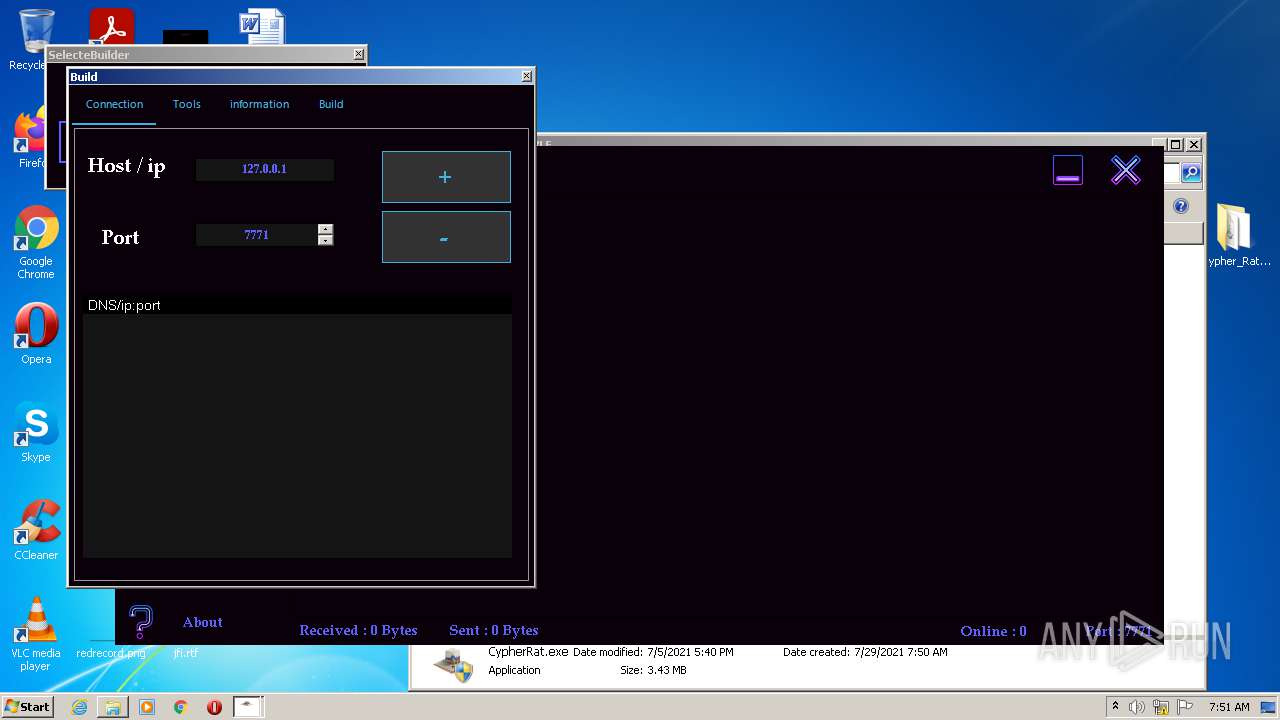
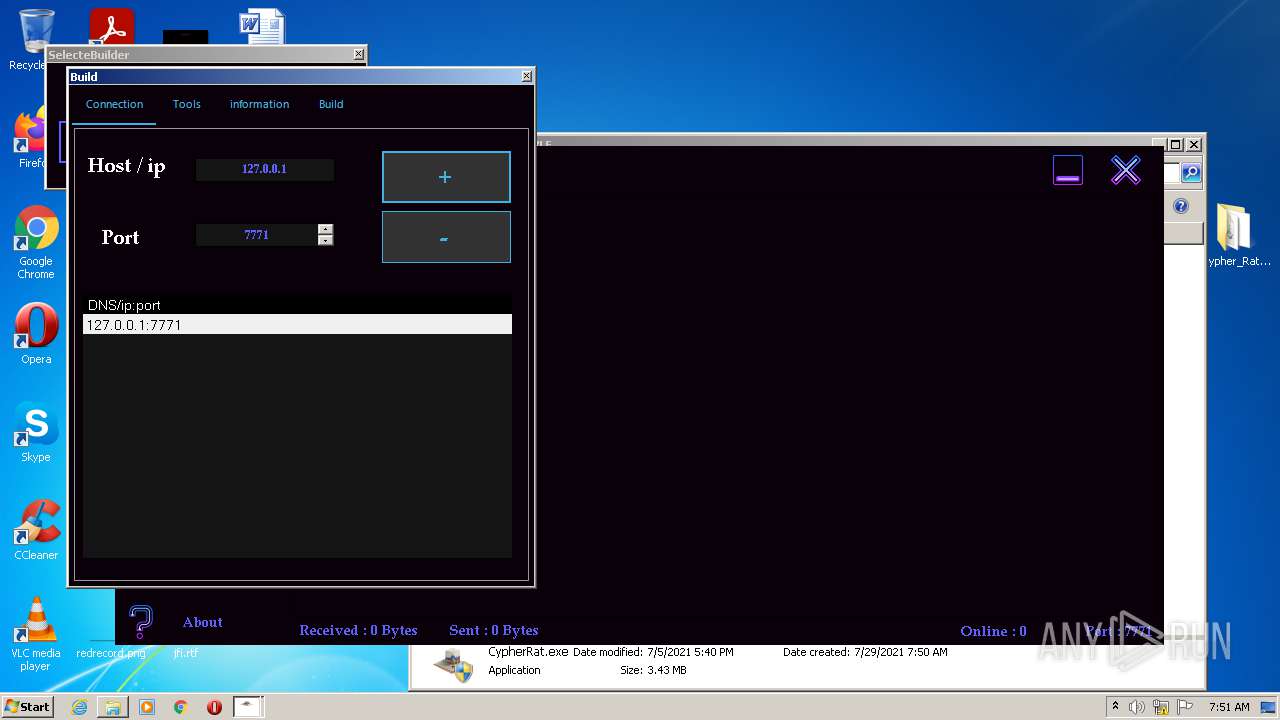
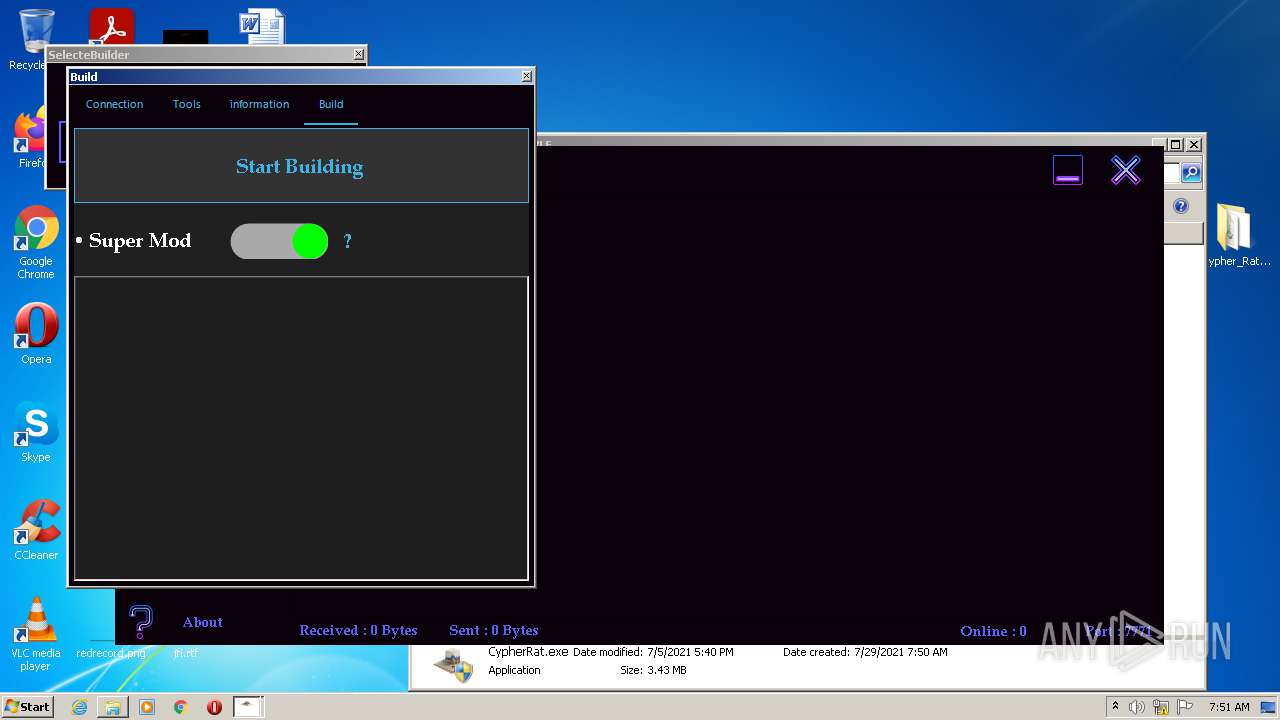
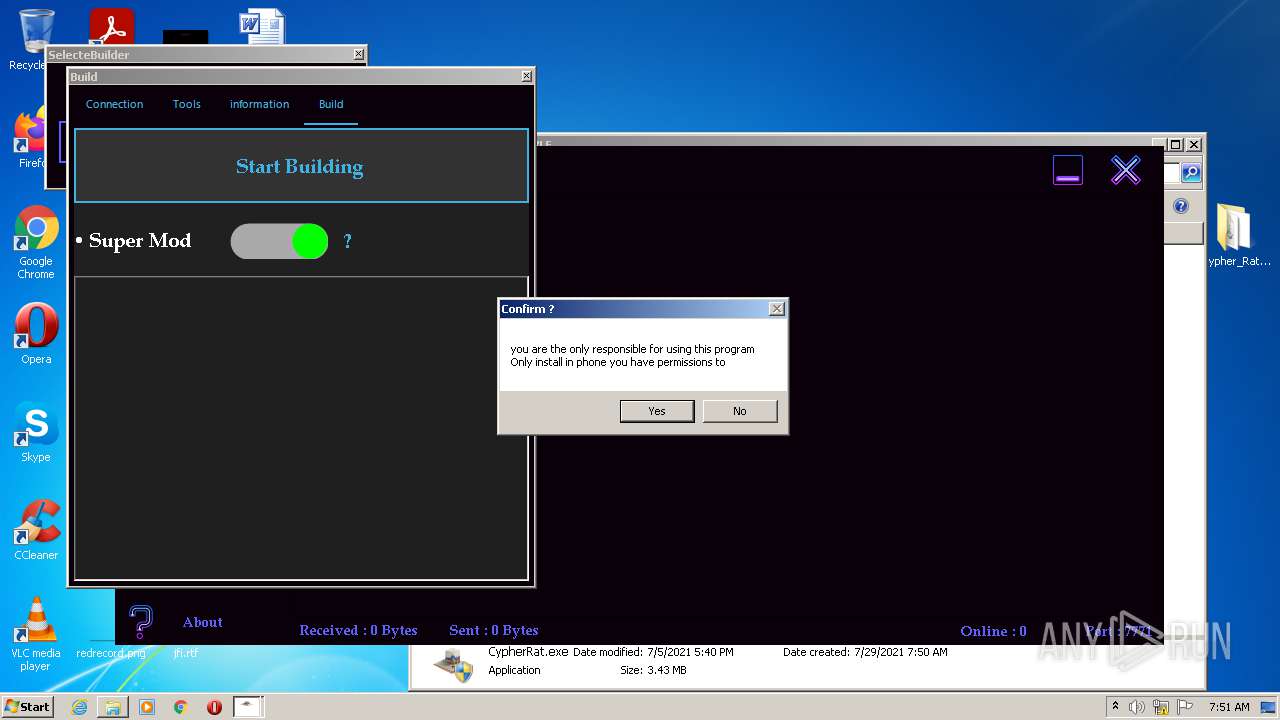
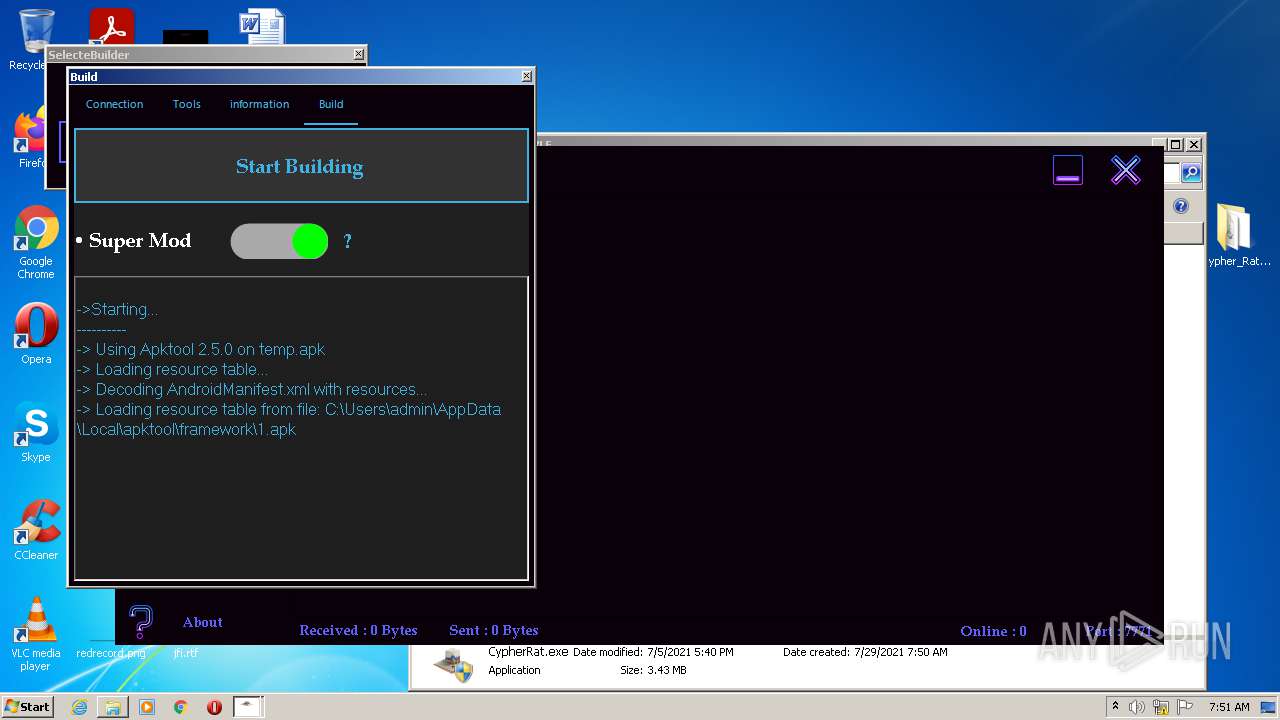
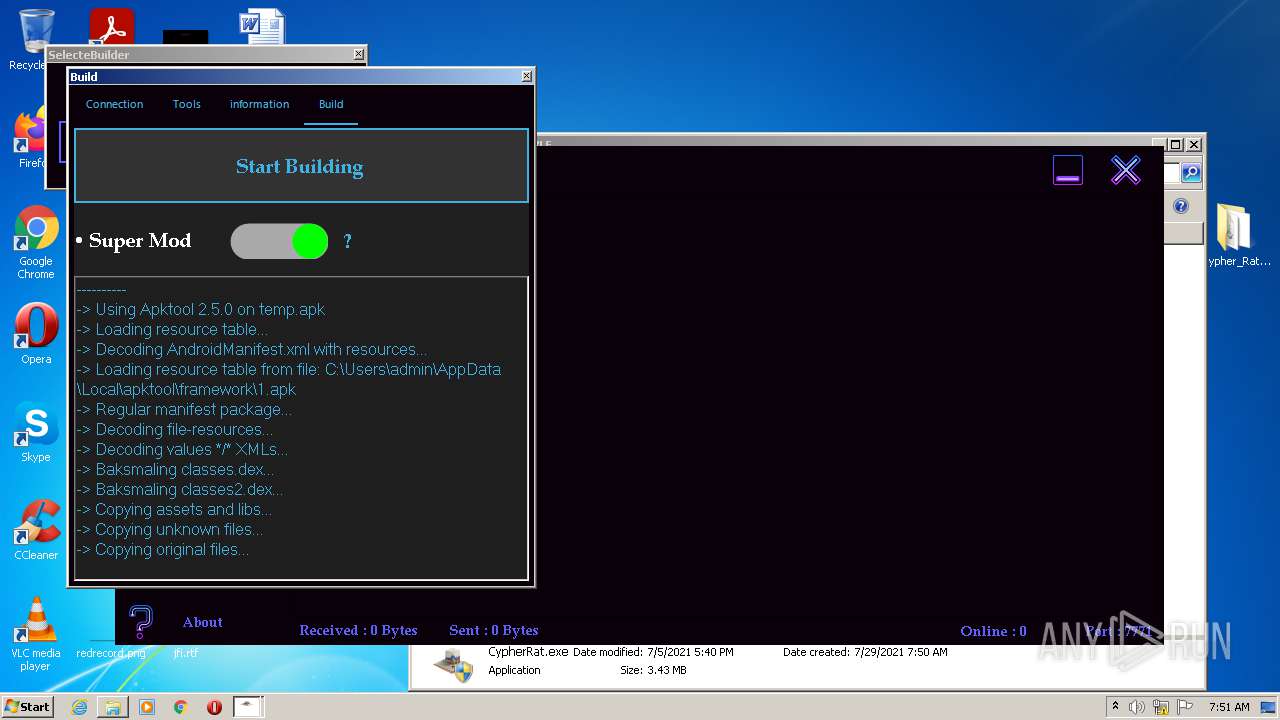
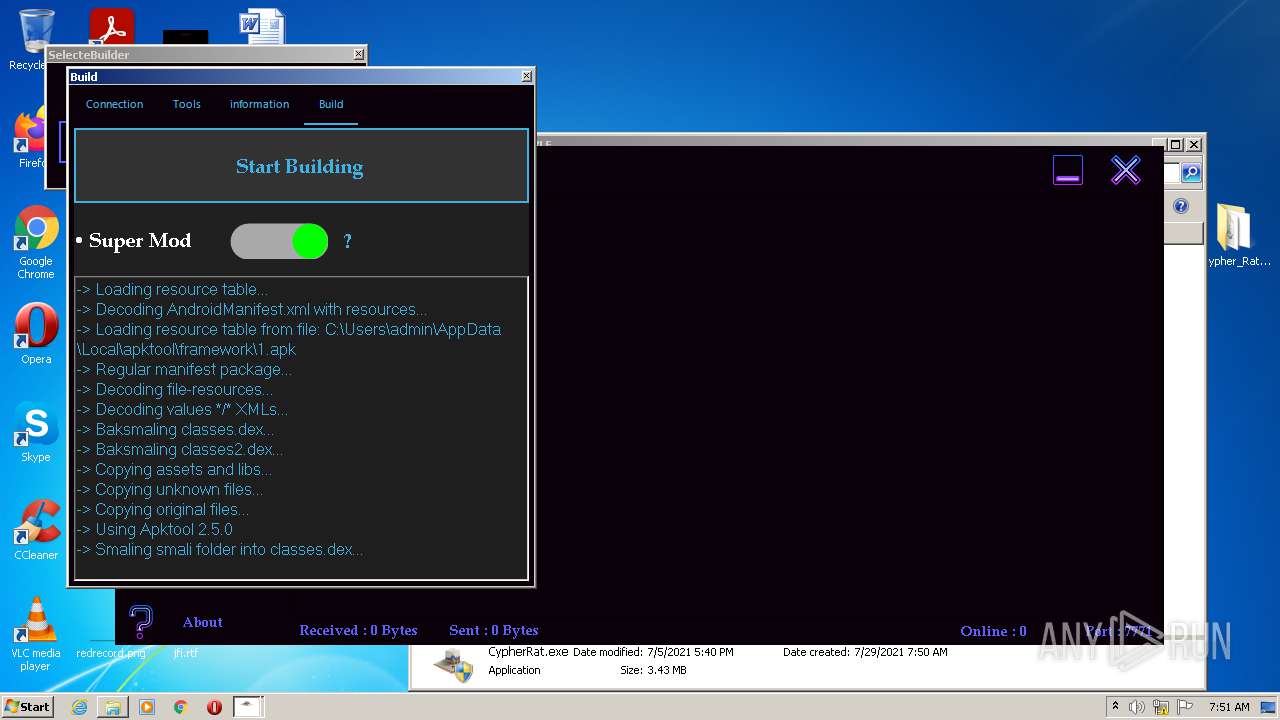
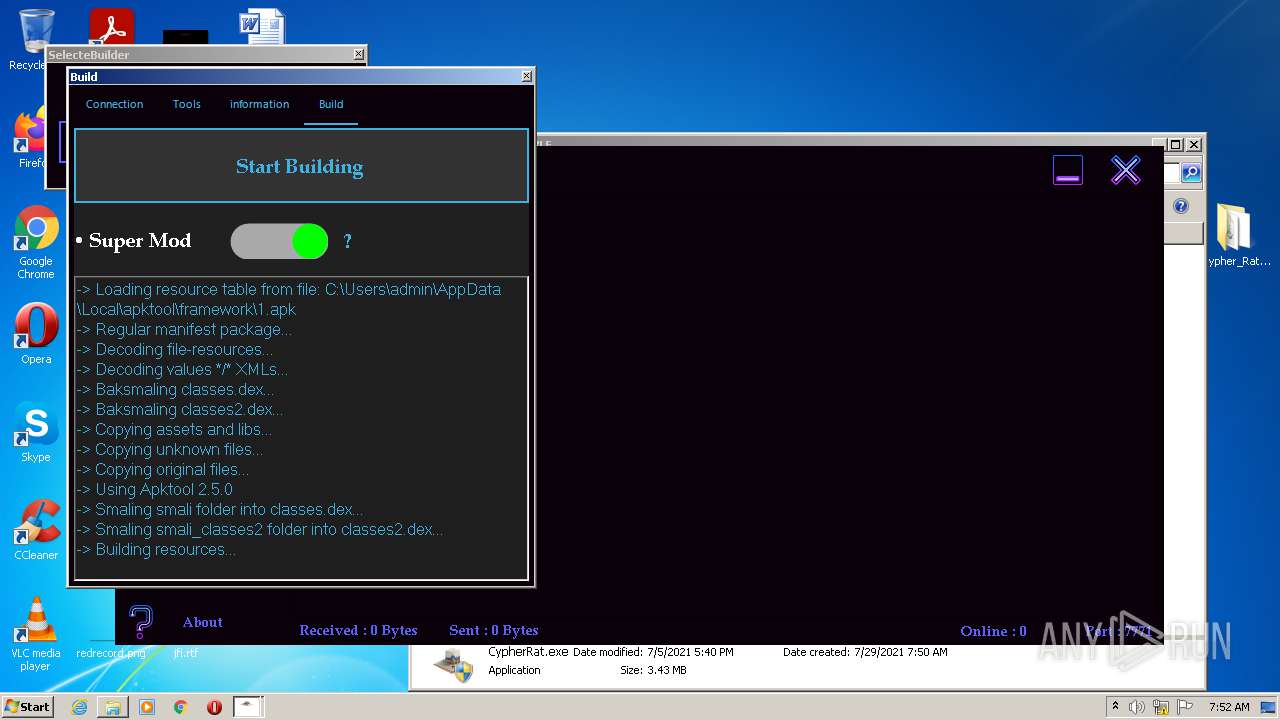
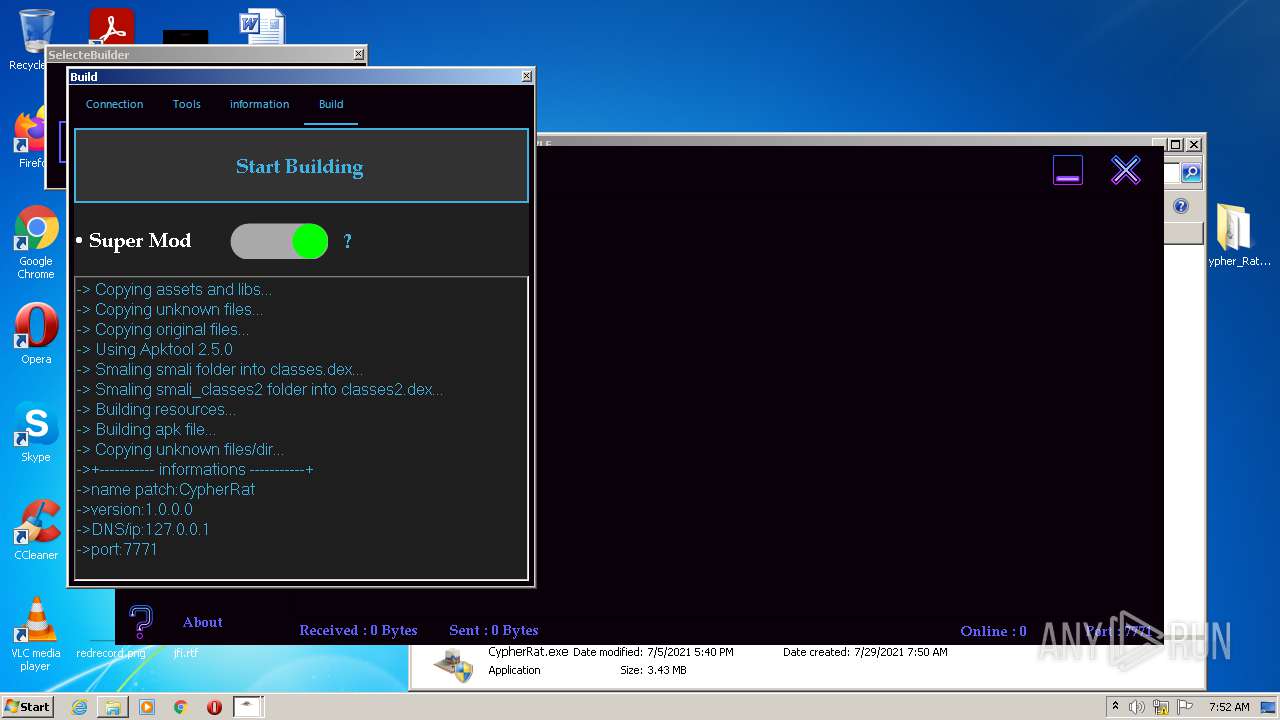
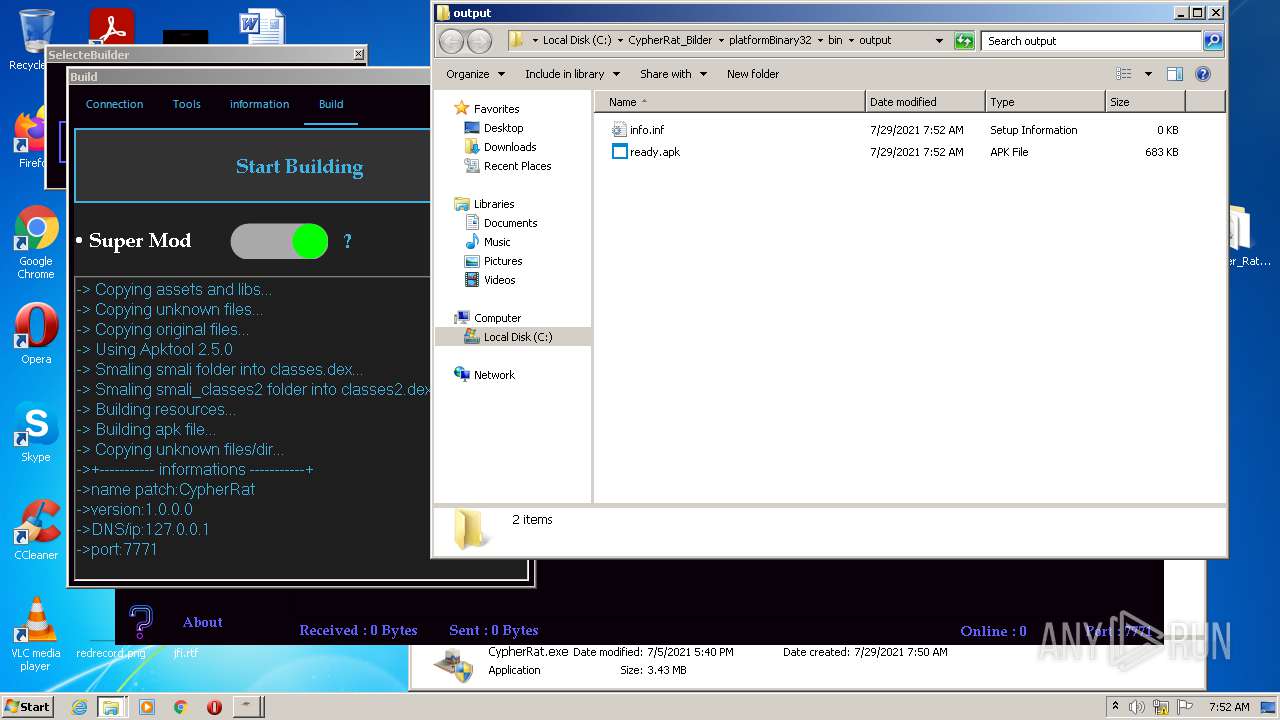
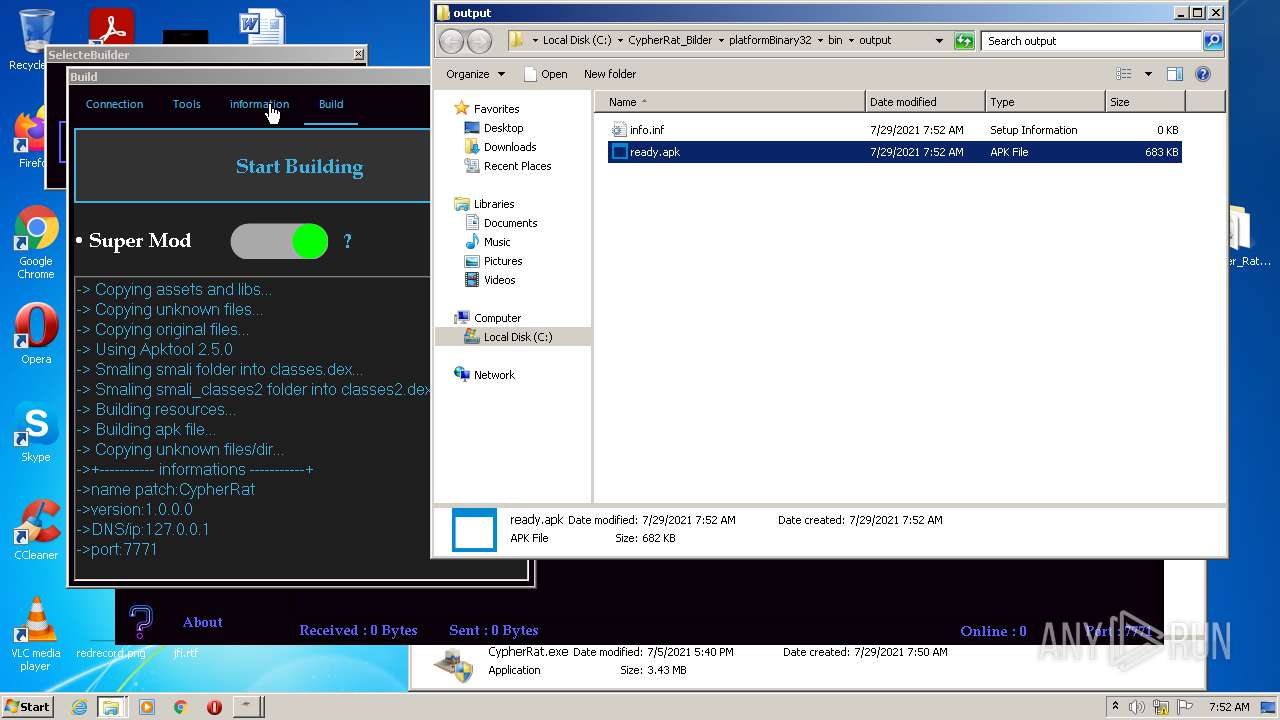
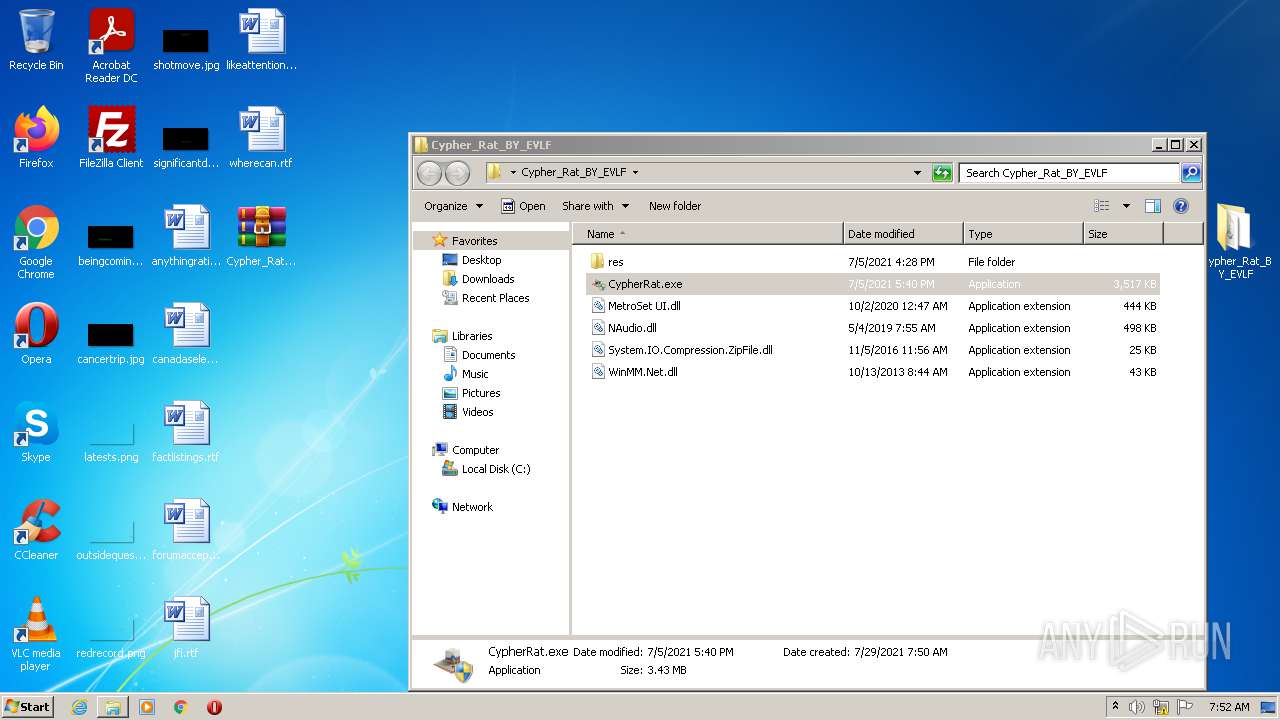
| URL: | https://www.mediafire.com/file/z3ifot4q4mxab71/Cypher_Rat_BY_EVLF.rar/file |
| Full analysis: | https://app.any.run/tasks/4fba23f9-0714-4611-b616-9cb8111f042d |
| Verdict: | Malicious activity |
| Analysis date: | July 29, 2021, 06:47:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | E93DCB94184686DA9C24F9488F0EF74F |
| SHA1: | A25D2A43E7220B8E1E20D5C1F3D707DECE12B2EF |
| SHA256: | 1AF126D5FFB62AEF49EAF716B9ED77BE8CC6A7E0E5FD3140EA299EB297D5E3CA |
| SSDEEP: | 3:N8DSLw3eGUozDKIBdk3ER6KZlcA:2OLw3eG/WIBlR6KZlcA |
MALICIOUS
Application was dropped or rewritten from another process
- CypherRat.exe (PID: 896)
- CypherRat.exe (PID: 3056)
- java.exe (PID: 2708)
- java.exe (PID: 668)
- java.exe (PID: 2248)
- brut_util_Jar_1398384834270666914379605051068884331.tmp (PID: 3644)
- java.exe (PID: 2060)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3428)
- CypherRat.exe (PID: 896)
- cmd.exe (PID: 464)
- java.exe (PID: 2248)
- java.exe (PID: 2708)
- java.exe (PID: 668)
- java.exe (PID: 2060)
Runs app for hidden code execution
- CypherRat.exe (PID: 896)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3064)
Checks supported languages
- WinRAR.exe (PID: 2980)
- CypherRat.exe (PID: 896)
- cmd.exe (PID: 464)
- java.exe (PID: 2708)
- java.exe (PID: 668)
- java.exe (PID: 2248)
- brut_util_Jar_1398384834270666914379605051068884331.tmp (PID: 3644)
- java.exe (PID: 2060)
Reads the computer name
- WinRAR.exe (PID: 2980)
- CypherRat.exe (PID: 896)
- java.exe (PID: 2248)
- java.exe (PID: 668)
- java.exe (PID: 2060)
Drops a file with too old compile date
- WinRAR.exe (PID: 2980)
- java.exe (PID: 668)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 2980)
- CypherRat.exe (PID: 896)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2980)
- CypherRat.exe (PID: 896)
- java.exe (PID: 668)
Creates files in the user directory
- CypherRat.exe (PID: 896)
Starts CMD.EXE for commands execution
- CypherRat.exe (PID: 896)
Drops a file with a compile date too recent
- CypherRat.exe (PID: 896)
Starts application with an unusual extension
- java.exe (PID: 668)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2464)
Reads the computer name
- iexplore.exe (PID: 2464)
- iexplore.exe (PID: 3064)
Checks supported languages
- iexplore.exe (PID: 2464)
- iexplore.exe (PID: 3064)
Checks Windows Trust Settings
- iexplore.exe (PID: 2464)
- iexplore.exe (PID: 3064)
Creates files in the user directory
- iexplore.exe (PID: 2464)
- iexplore.exe (PID: 3064)
Reads the date of Windows installation
- iexplore.exe (PID: 2464)
Reads settings of System Certificates
- iexplore.exe (PID: 3064)
- iexplore.exe (PID: 2464)
Reads internet explorer settings
- iexplore.exe (PID: 3064)
Changes settings of System certificates
- iexplore.exe (PID: 2464)
Manual execution by user
- WinRAR.exe (PID: 2980)
- CypherRat.exe (PID: 3056)
- CypherRat.exe (PID: 896)
Application launched itself
- iexplore.exe (PID: 2464)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2464)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2464)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
57
Monitored processes
12
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 464 | "cmd.exe" | C:\Windows\system32\cmd.exe | — | CypherRat.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 4294967295 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 668 | java -jar -Duser.language=en "C:\CypherRat_Bilder\platformBinary32\bin\\apktool.jar" b -f -r temp | C:\CypherRat_Bilder\platformBinary32\bin\java.exe | cmd.exe | ||||||||||||
User: admin Company: Azul Systems Inc. Integrity Level: HIGH Description: Zulu Platform x32 Architecture Exit code: 0 Version: 8.38.0.13 Modules
| |||||||||||||||
| 896 | "C:\Users\admin\Desktop\Cypher_Rat_BY_EVLF\CypherRat.exe" | C:\Users\admin\Desktop\Cypher_Rat_BY_EVLF\CypherRat.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Description: Spy MAX - RAT Exit code: 0 Version: 2.0.0.0 Modules
| |||||||||||||||
| 2060 | java -jar C:\CypherRat_Bilder\platformBinary32\bin\SignApk.jar C:\CypherRat_Bilder\platformBinary32\bin\certificate.pem C:\CypherRat_Bilder\platformBinary32\bin\key.pk8 C:\CypherRat_Bilder\platformBinary32\bin\temp\dist\temp.apk C:\CypherRat_Bilder\platformBinary32\bin\output\ready.apk | C:\CypherRat_Bilder\platformBinary32\bin\java.exe | — | cmd.exe | |||||||||||
User: admin Company: Azul Systems Inc. Integrity Level: HIGH Description: Zulu Platform x32 Architecture Exit code: 0 Version: 8.38.0.13 Modules
| |||||||||||||||
| 2248 | java -jar -Duser.language=en "C:\CypherRat_Bilder\platformBinary32\bin\\apktool.jar" d temp.apk | C:\CypherRat_Bilder\platformBinary32\bin\java.exe | — | cmd.exe | |||||||||||
User: admin Company: Azul Systems Inc. Integrity Level: HIGH Description: Zulu Platform x32 Architecture Exit code: 0 Version: 8.38.0.13 Modules
| |||||||||||||||
| 2464 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.mediafire.com/file/z3ifot4q4mxab71/Cypher_Rat_BY_EVLF.rar/file" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2708 | java -version | C:\CypherRat_Bilder\platformBinary32\bin\java.exe | — | cmd.exe | |||||||||||
User: admin Company: Azul Systems Inc. Integrity Level: HIGH Description: Zulu Platform x32 Architecture Exit code: 0 Version: 8.38.0.13 Modules
| |||||||||||||||
| 2980 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Cypher_Rat_BY_EVLF.rar" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3056 | "C:\Users\admin\Desktop\Cypher_Rat_BY_EVLF\CypherRat.exe" | C:\Users\admin\Desktop\Cypher_Rat_BY_EVLF\CypherRat.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: Spy MAX - RAT Exit code: 3221226540 Version: 2.0.0.0 Modules
| |||||||||||||||
| 3064 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2464 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
24 128
Read events
23 886
Write events
237
Delete events
5
Modification events
| (PID) Process: | (2464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30901317 | |||
| (PID) Process: | (2464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30901317 | |||
| (PID) Process: | (2464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
169
Suspicious files
46
Text files
1 460
Unknown types
81
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3064 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3064 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:— | SHA256:— | |||
| 3064 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\84NLQ2N2.txt | text | |
MD5:— | SHA256:— | |||
| 3064 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:— | SHA256:— | |||
| 3064 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\icons_sprite[1].svg | image | |
MD5:— | SHA256:— | |||
| 3064 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\file[1].htm | html | |
MD5:— | SHA256:— | |||
| 3064 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\apps_list_sprite-v5[1].png | image | |
MD5:— | SHA256:— | |||
| 3064 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_D975BBA8033175C8D112023D8A7A8AD6 | der | |
MD5:— | SHA256:— | |||
| 3064 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | der | |
MD5:— | SHA256:— | |||
| 3064 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\5WS6D1Q9.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
71
DNS requests
28
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3064 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
3064 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEEq9Zf45tp3TCgAAAADrWg0%3D | US | der | 471 b | whitelisted |
3064 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
3064 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEHFTDTdAe7AICgAAAADrSro%3D | US | der | 471 b | whitelisted |
3064 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECECUTgfQsc%2BcBwNBMQNWQl0M%3D | US | der | 471 b | whitelisted |
2464 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3064 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
3064 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
2464 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
2464 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3064 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
— | — | 20.73.194.208:443 | — | — | US | whitelisted |
2464 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3064 | iexplore.exe | 104.16.203.237:443 | www.mediafire.com | Cloudflare Inc | US | unknown |
3064 | iexplore.exe | 151.139.128.14:80 | ocsp.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
2464 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3064 | iexplore.exe | 216.58.212.174:443 | translate.google.com | Google Inc. | US | whitelisted |
3064 | iexplore.exe | 142.250.185.72:443 | www.googletagmanager.com | Google Inc. | US | suspicious |
3064 | iexplore.exe | 104.16.95.65:443 | static.cloudflareinsights.com | Cloudflare Inc | US | shared |
3064 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.mediafire.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
translate.google.com |
| whitelisted |
static.cloudflareinsights.com |
| whitelisted |
Threats
Process | Message |
|---|---|
CypherRat.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |