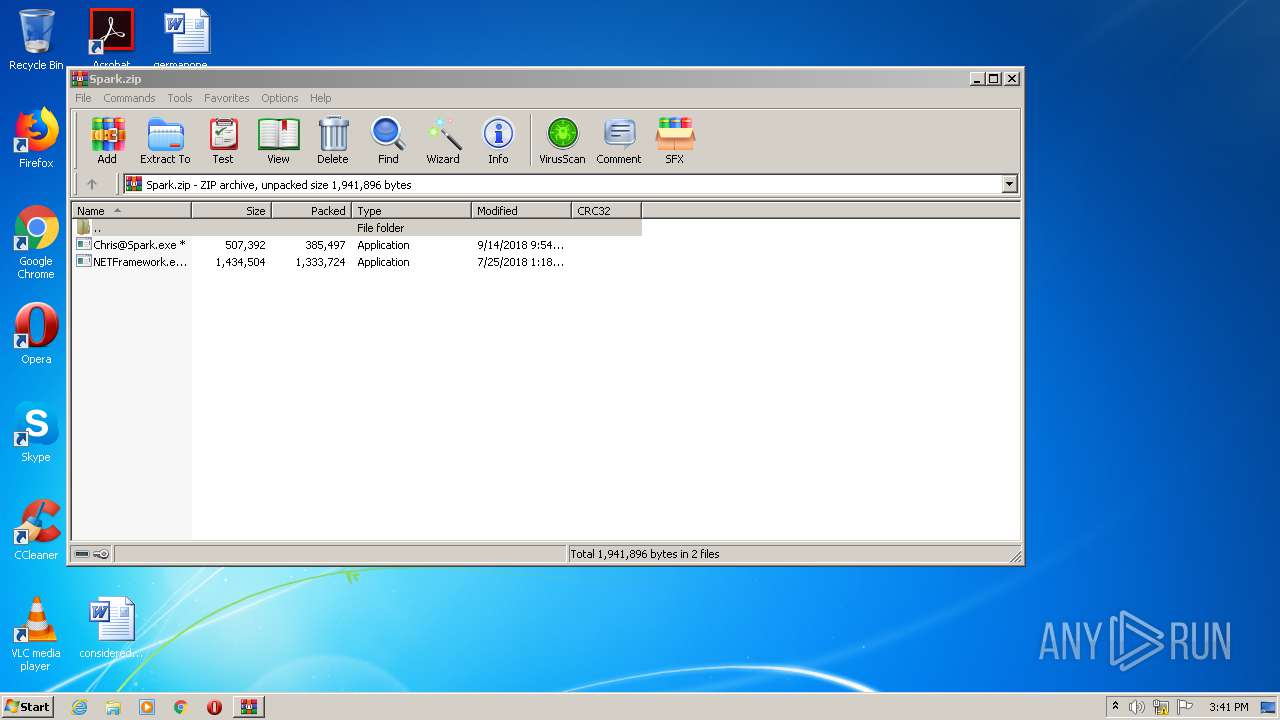
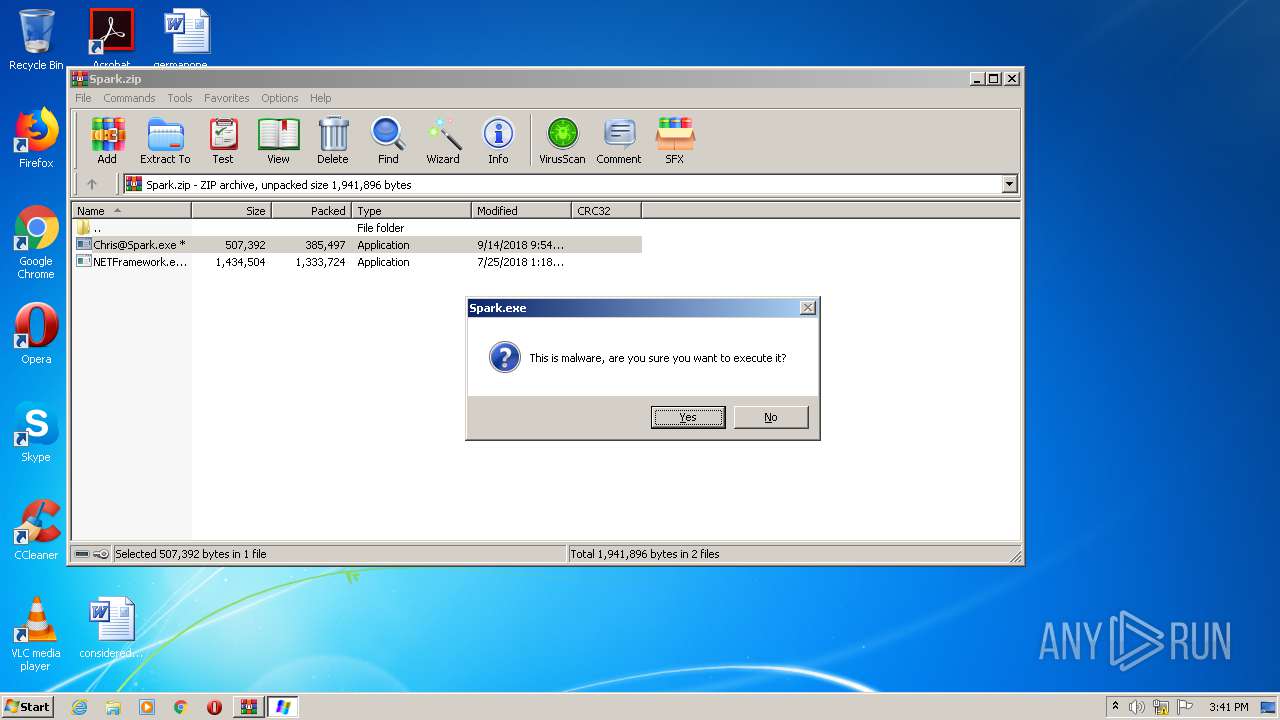
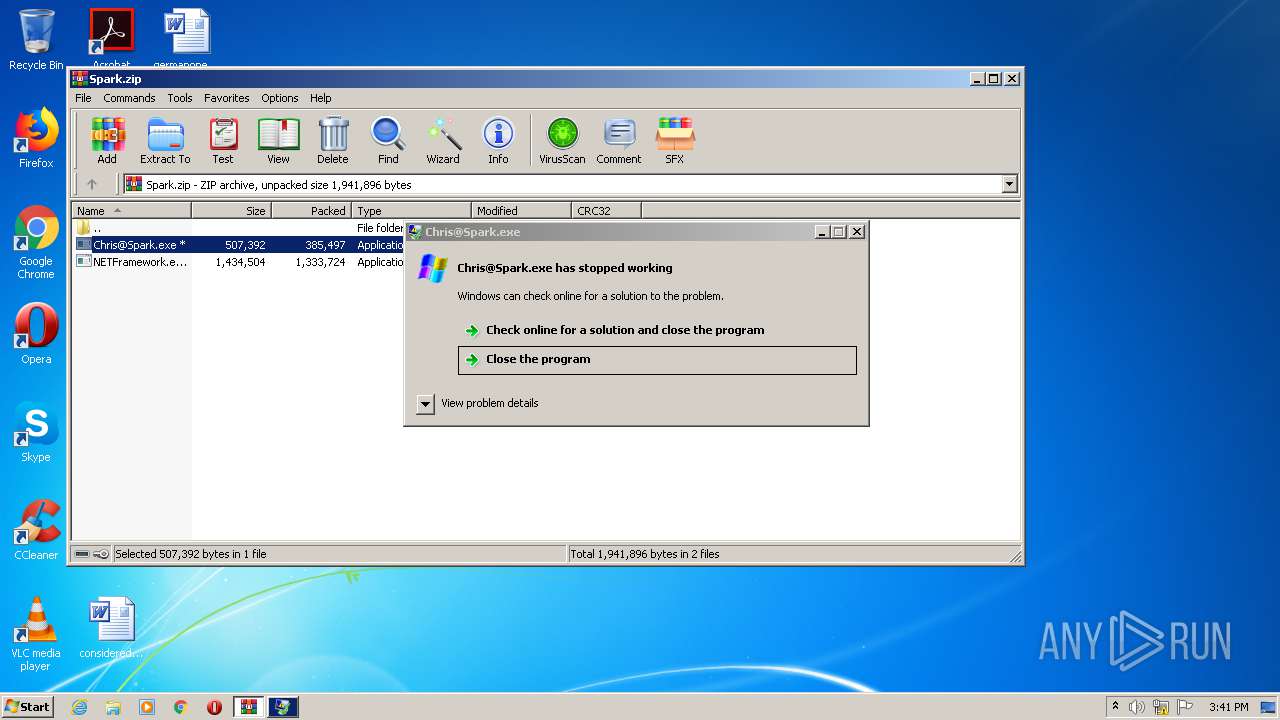
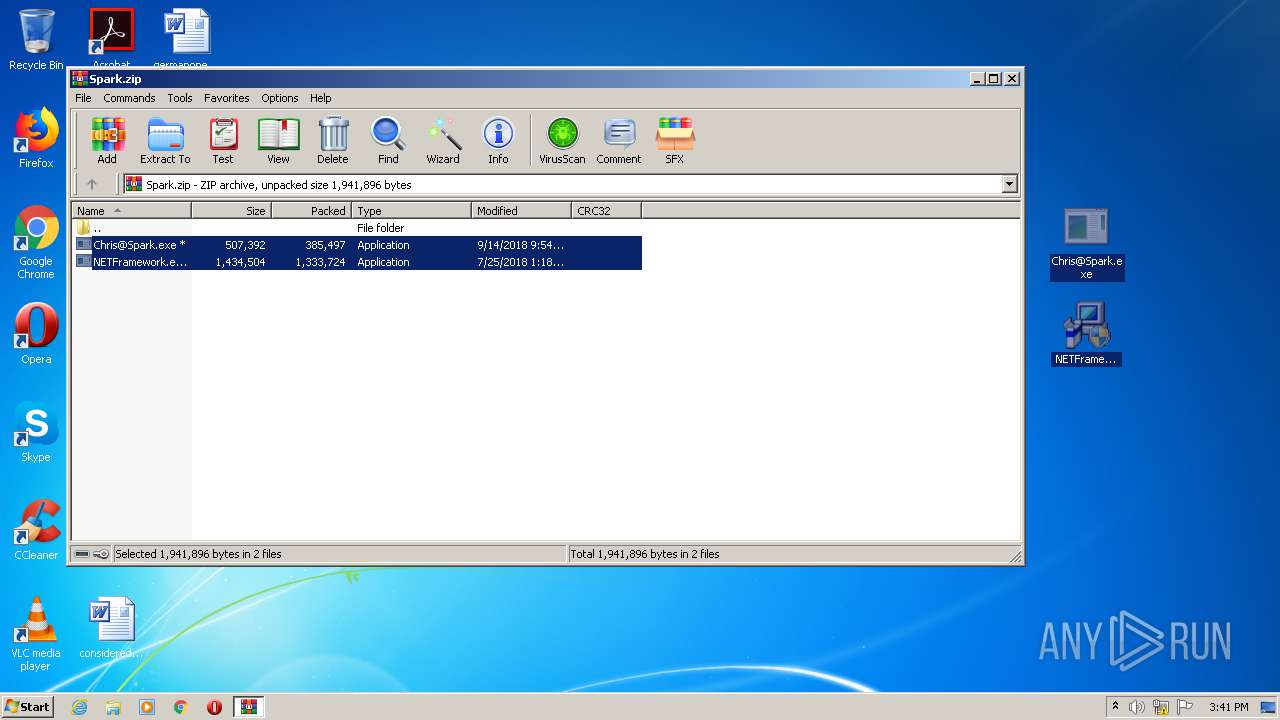
| File name: | Spark.zip |
| Full analysis: | https://app.any.run/tasks/61b13877-e919-4704-984e-821cb5a27315 |
| Verdict: | Malicious activity |
| Analysis date: | November 29, 2020, 15:40:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract |
| MD5: | 860168A14356BE3E65650B8A3CF6C3A0 |
| SHA1: | EA99E29E119D88CAF9D38FB6AAC04A97E9C5AC63 |
| SHA256: | 1AE2A53C8ADC94B1566EA6B3AA63CE7FE2A2B2FCBE4CEC3112F9EBE76E2E9BF9 |
| SSDEEP: | 49152:p0iszfe7OgN0Fw6KDfcqm6YvBK1+bgHXFZn:4CN0FHMcTvu+E3FZn |
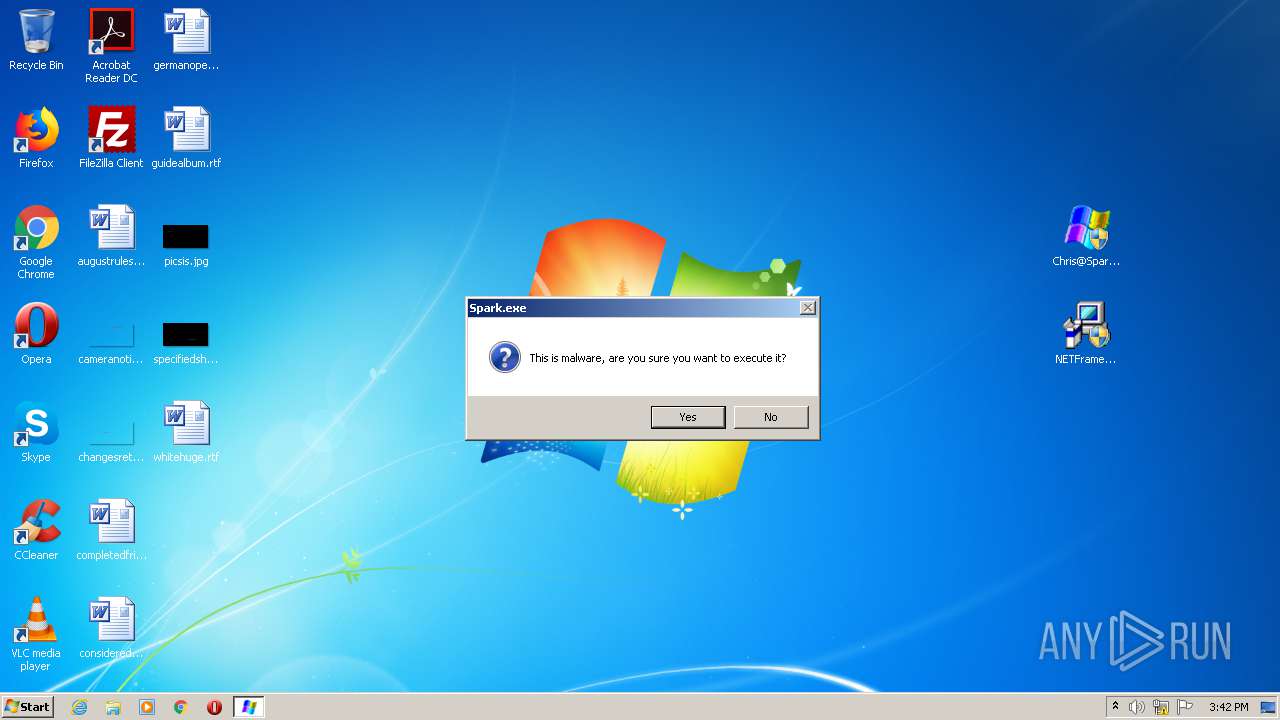
MALICIOUS
Application was dropped or rewritten from another process
- Chris@Spark.exe (PID: 3204)
- NETFramework.exe (PID: 2400)
- NETFramework.exe (PID: 4032)
- Chris@Spark.exe (PID: 2832)
- Setup.exe (PID: 1732)
- SetupUtility.exe (PID: 2492)
- SetupUtility.exe (PID: 1332)
- SetupUtility.exe (PID: 3728)
- SetupUtility.exe (PID: 2808)
- Chris@Spark.exe (PID: 3848)
- Chris@Spark.exe (PID: 2200)
Actions looks like stealing of personal data
- Chris@Spark.exe (PID: 3204)
- NETFramework.exe (PID: 4032)
- Chris@Spark.exe (PID: 2200)
Drops executable file immediately after starts
- NETFramework.exe (PID: 4032)
Loads dropped or rewritten executable
- Setup.exe (PID: 1732)
Changes settings of System certificates
- Setup.exe (PID: 1732)
SUSPICIOUS
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 2364)
- Chris@Spark.exe (PID: 3204)
- NETFramework.exe (PID: 4032)
- Chris@Spark.exe (PID: 2200)
Executable content was dropped or overwritten
- Chris@Spark.exe (PID: 3204)
- WinRAR.exe (PID: 2364)
- NETFramework.exe (PID: 4032)
- Chris@Spark.exe (PID: 2200)
Creates files in the Windows directory
- Chris@Spark.exe (PID: 3204)
INFO
Manual execution by user
- NETFramework.exe (PID: 4032)
- NETFramework.exe (PID: 2400)
- Chris@Spark.exe (PID: 3848)
- Chris@Spark.exe (PID: 2200)
Reads settings of System Certificates
- Setup.exe (PID: 1732)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
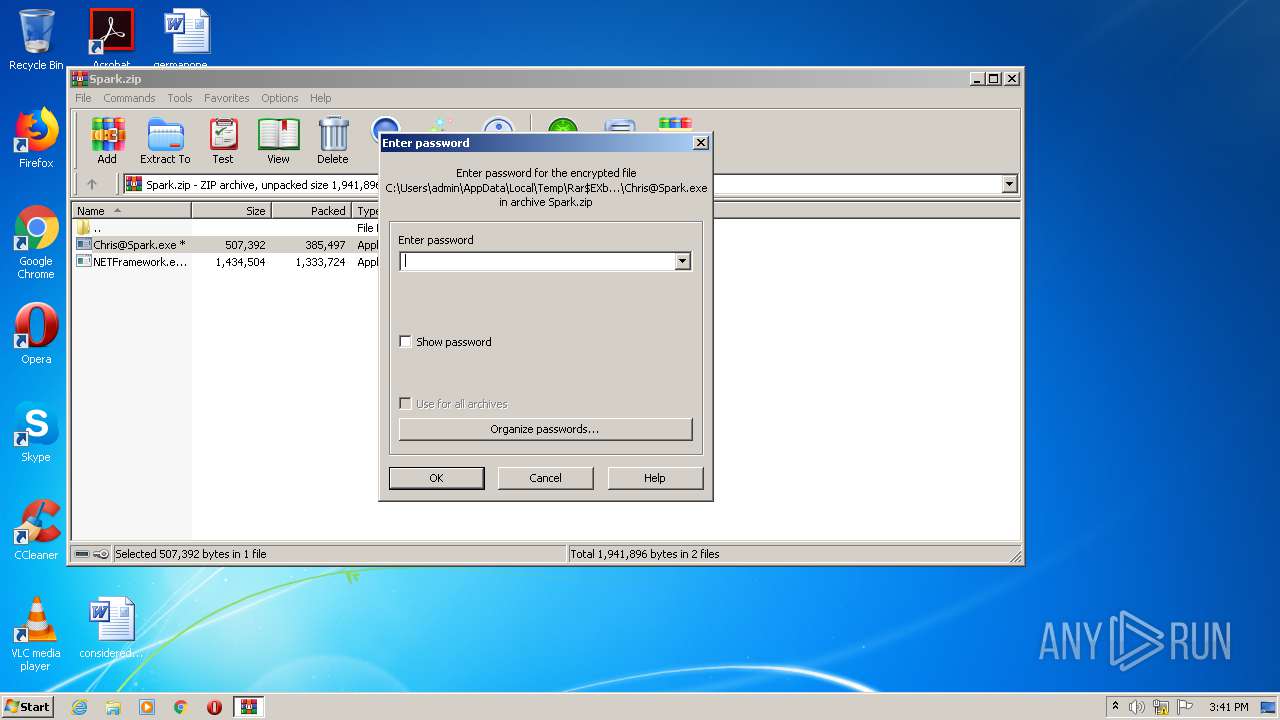
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2018:09:14 23:54:10 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 385497 |
| ZipUncompressedSize: | 507392 |
| ZipFileName: | Chris@Spark.exe |
Total processes
61
Monitored processes
12
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1332 | SetupUtility.exe /msureboot 461310 | C:\cb5a6f3baae017cbbc4e12e4\SetupUtility.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 4.5 Setup Exit code: 0 Version: 14.7.2558.0 built by: NET471REL1 Modules
| |||||||||||||||
| 1732 | C:\cb5a6f3baae017cbbc4e12e4\\Setup.exe /x86 /x64 /web | C:\cb5a6f3baae017cbbc4e12e4\Setup.exe | NETFramework.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Setup Installer Exit code: 0 Version: 14.7.2558.0 built by: NET471REL1 Modules
| |||||||||||||||
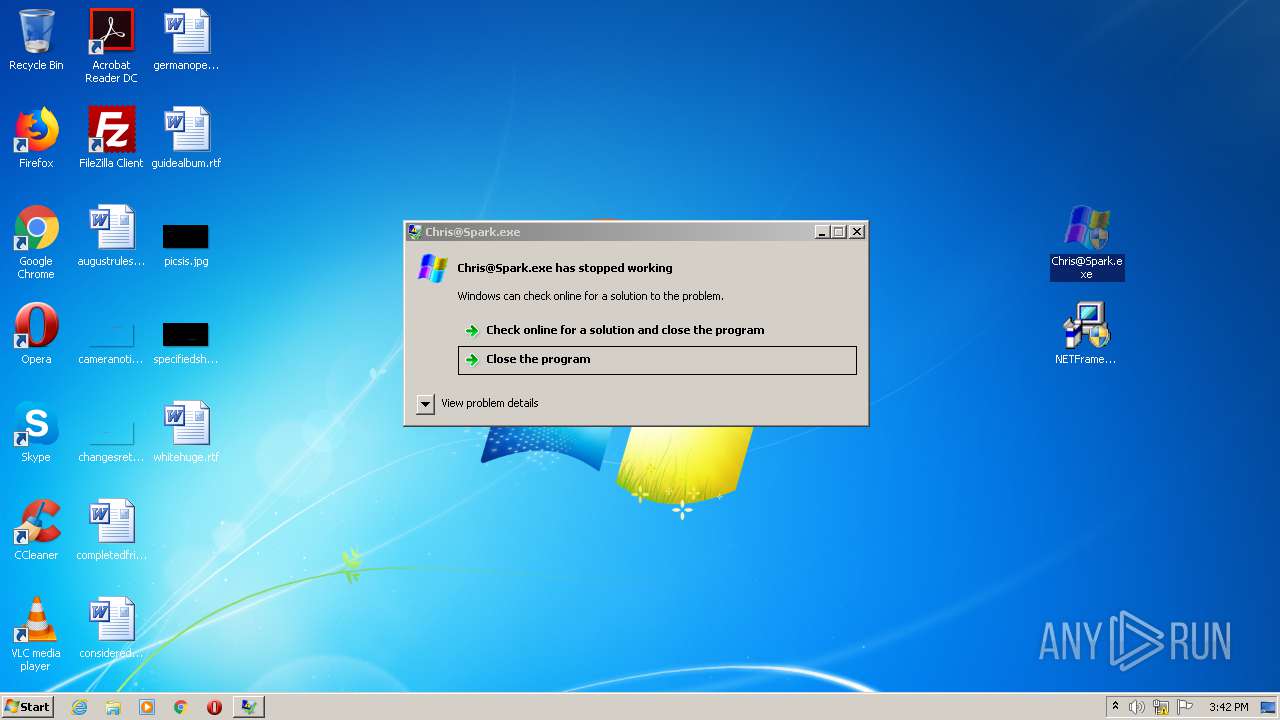
| 2200 | "C:\Users\admin\Desktop\Chris@Spark.exe" | C:\Users\admin\Desktop\Chris@Spark.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 3762504530 Version: 0.0.0.0 Modules
| |||||||||||||||
| 2364 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Spark.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
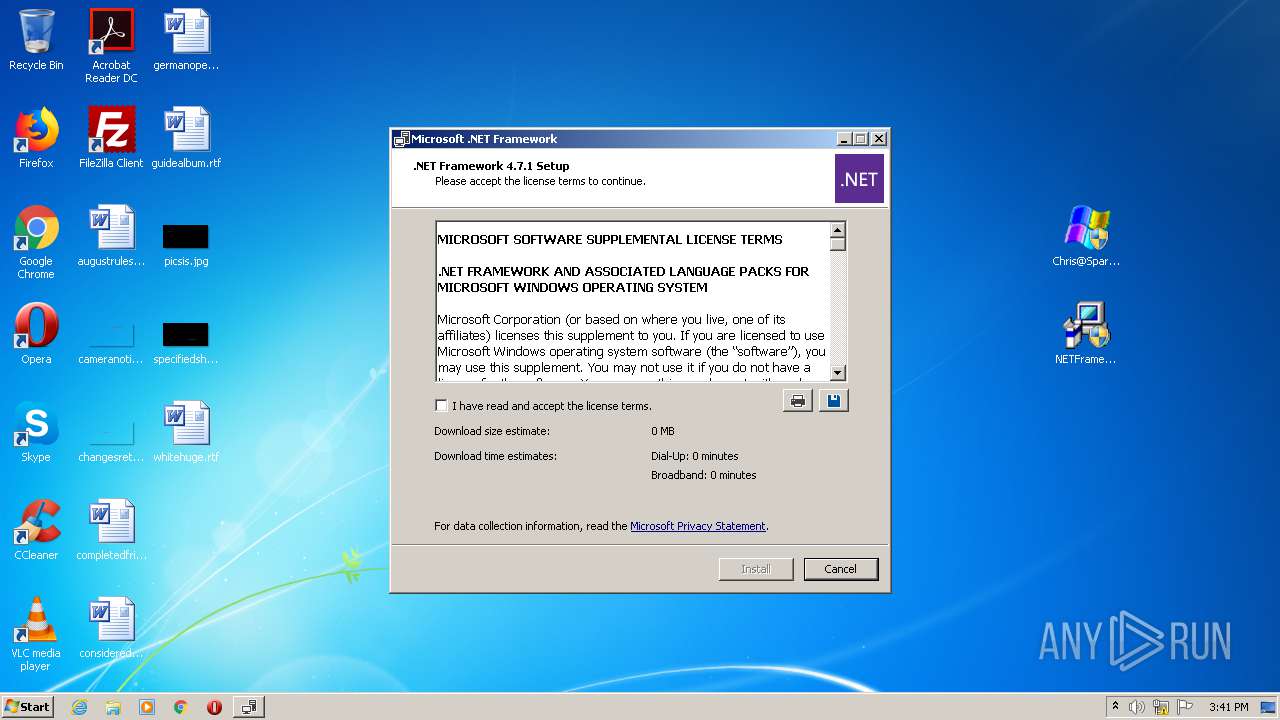
| 2400 | "C:\Users\admin\Desktop\NETFramework.exe" | C:\Users\admin\Desktop\NETFramework.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Framework 4.7.1 Setup Exit code: 3221226540 Version: 4.7.02558.00 Modules
| |||||||||||||||
| 2492 | SetupUtility.exe /aupause | C:\cb5a6f3baae017cbbc4e12e4\SetupUtility.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 4.5 Setup Exit code: 0 Version: 14.7.2558.0 built by: NET471REL1 Modules
| |||||||||||||||
| 2808 | SetupUtility.exe /auresume | C:\cb5a6f3baae017cbbc4e12e4\SetupUtility.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 4.5 Setup Exit code: 0 Version: 14.7.2558.0 built by: NET471REL1 Modules
| |||||||||||||||
| 2832 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2364.31169\Chris@Spark.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2364.31169\Chris@Spark.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 3204 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2364.31169\Chris@Spark.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2364.31169\Chris@Spark.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 3762504530 Version: 0.0.0.0 Modules
| |||||||||||||||
| 3728 | SetupUtility.exe /screboot | C:\cb5a6f3baae017cbbc4e12e4\SetupUtility.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 4.5 Setup Exit code: 0 Version: 14.7.2558.0 built by: NET471REL1 Modules
| |||||||||||||||
Total events
604
Read events
561
Write events
39
Delete events
4
Modification events
| (PID) Process: | (2364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2364) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Spark.zip | |||
| (PID) Process: | (2364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
37
Suspicious files
6
Text files
82
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2364.33183\Chris@Spark.exe | — | |
MD5:— | SHA256:— | |||
| 2364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2364.33183\NETFramework.exe | — | |
MD5:— | SHA256:— | |||
| 2364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2364.31169\Chris@Spark.exe | executable | |
MD5:181EE63003E5C3EC8C378030286ED7A2 | SHA256:55BFCB784904477EF62EF7E4994DEE42F03D69BFEC3591989513CCCBBA3FC8FE | |||
| 3204 | Chris@Spark.exe | C:\Windows\File Cache\DLL.dll | executable | |
MD5:A61C26B360471C8258C7571037C4BCA0 | SHA256:E77316A1FD682E1AF8AF3CCD03C170F886B9EC8EDF7013E1BE6A6207CB5A6F16 | |||
| 4032 | NETFramework.exe | C:\cb5a6f3baae017cbbc4e12e4\watermark.bmp | image | |
MD5:B0075CEE80173D764C0237E840BA5879 | SHA256:AB18374B3AAB10E5979E080D0410579F9771DB888BA1B80A5D81BA8896E2D33A | |||
| 4032 | NETFramework.exe | C:\cb5a6f3baae017cbbc4e12e4\header.bmp | image | |
MD5:41C22EFA84CA74F0CE7076EB9A482E38 | SHA256:255025A0D79EF2DAC04BD610363F966EF58328400BF31E1F8915E676478CD750 | |||
| 2364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2364.31169\NETFramework.exe | executable | |
MD5:4FB795478A8F346C337A1F84BACCC85B | SHA256:65A7CB8FD1C7C529C40345B4746818F8947BE736AA105007DFCC57B05897ED62 | |||
| 4032 | NETFramework.exe | C:\cb5a6f3baae017cbbc4e12e4\SplashScreen.bmp | image | |
MD5:BC32088BFAA1C76BA4B56639A2DEC592 | SHA256:B05141DBC71669A7872A8E735E5E43A7F9713D4363B7A97543E1E05DCD7470A7 | |||
| 4032 | NETFramework.exe | C:\cb5a6f3baae017cbbc4e12e4\DisplayIcon.ico | image | |
MD5:F9657D290048E169FFABBBB9C7412BE0 | SHA256:B74AD253B9B8F9FCADE725336509143828EE739CC2B24782BE3ECFF26F229160 | |||
| 4032 | NETFramework.exe | C:\cb5a6f3baae017cbbc4e12e4\Graphics\Rotate6.ico | image | |
MD5:5AC2B8E1A766C204F996D9CE33FB3DB4 | SHA256:EE387D9642DF93E4240361077AF6051C1B7E643C3CF110F43DA42E0EFE29A375 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1732 | Setup.exe | GET | 200 | 2.16.186.120:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | der | 781 b | whitelisted |
1732 | Setup.exe | GET | 200 | 2.16.186.120:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | der | 550 b | whitelisted |
1732 | Setup.exe | GET | 200 | 2.16.186.120:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | der | 564 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1732 | Setup.exe | 2.16.186.120:80 | crl.microsoft.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Setup.exe | The operation completed successfully.
|
Setup.exe | The operation completed successfully.
|