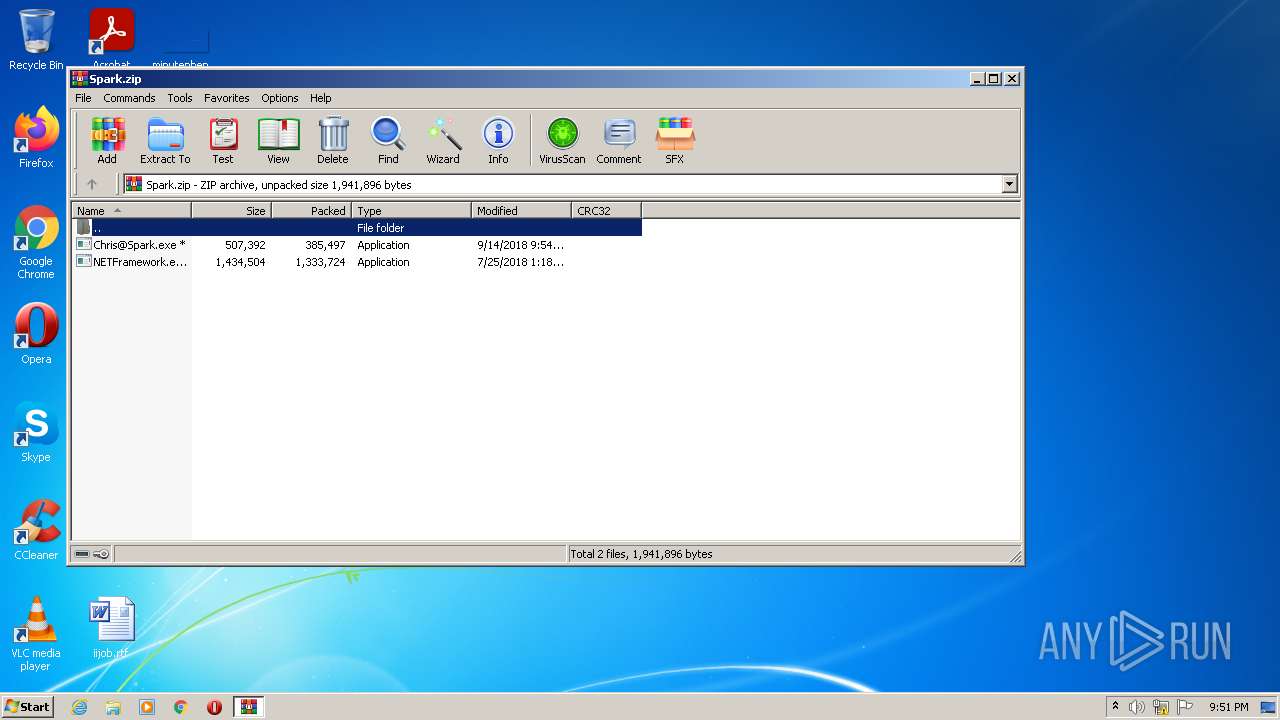
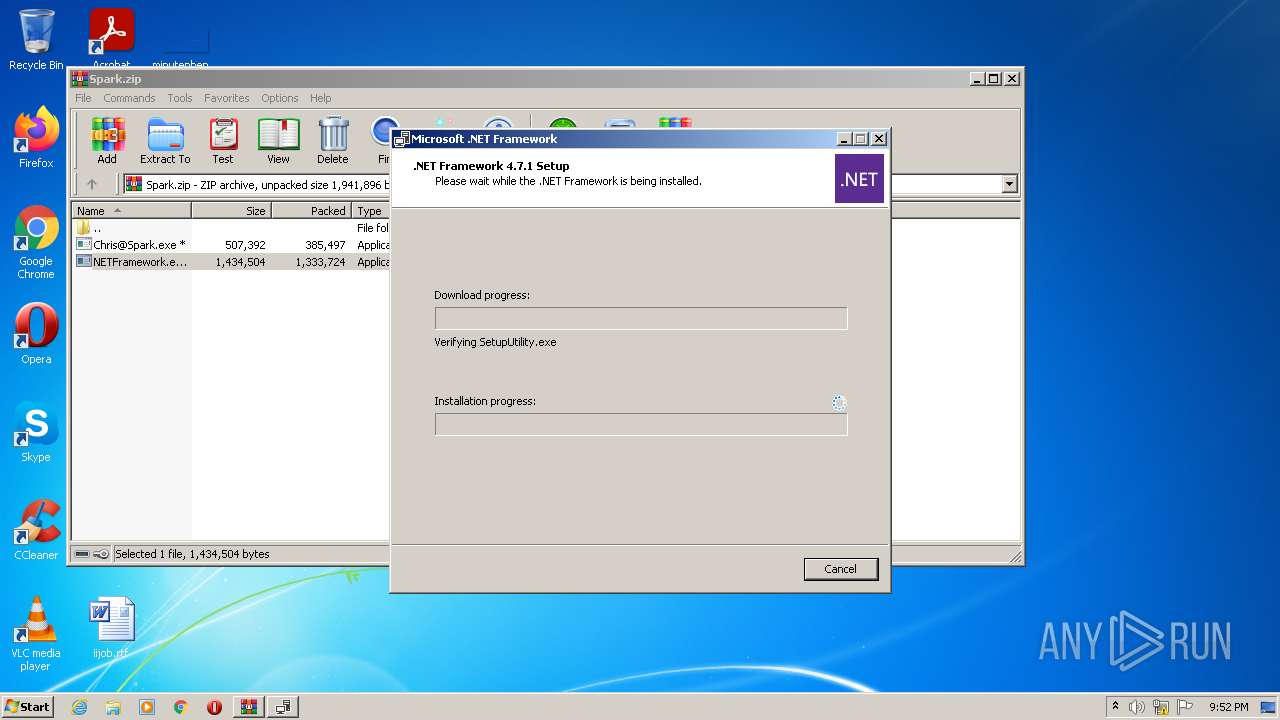
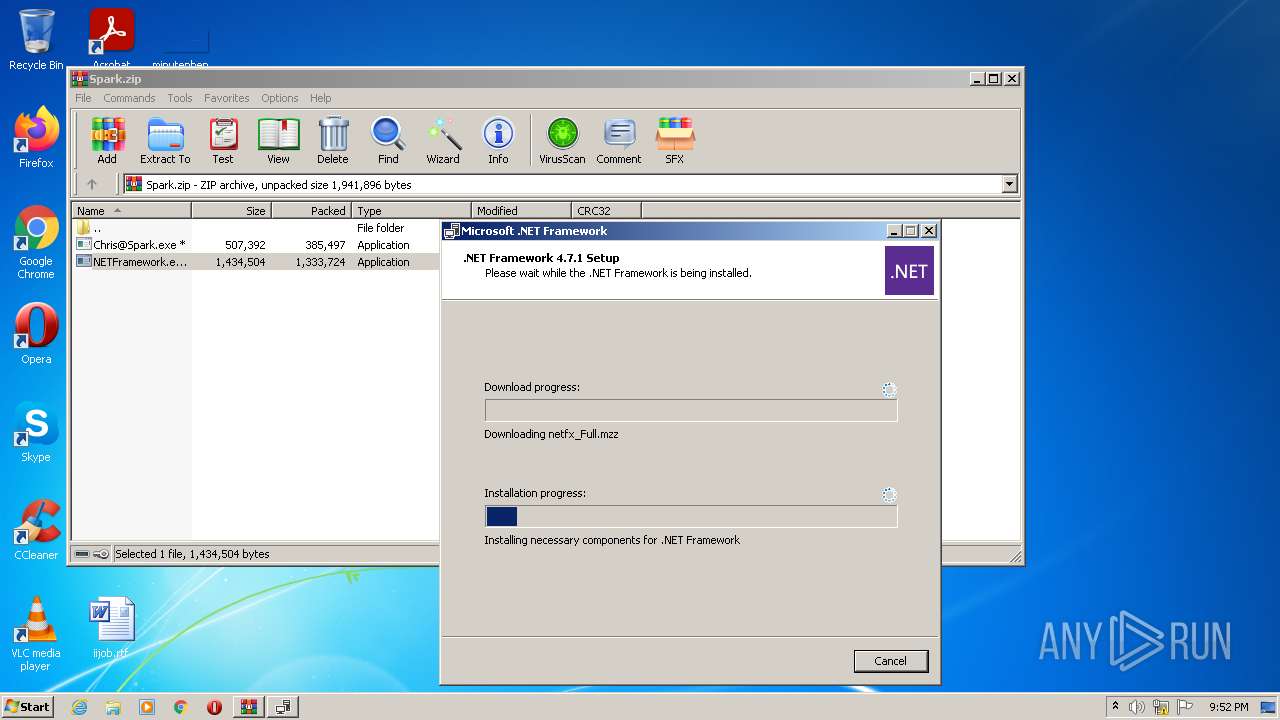
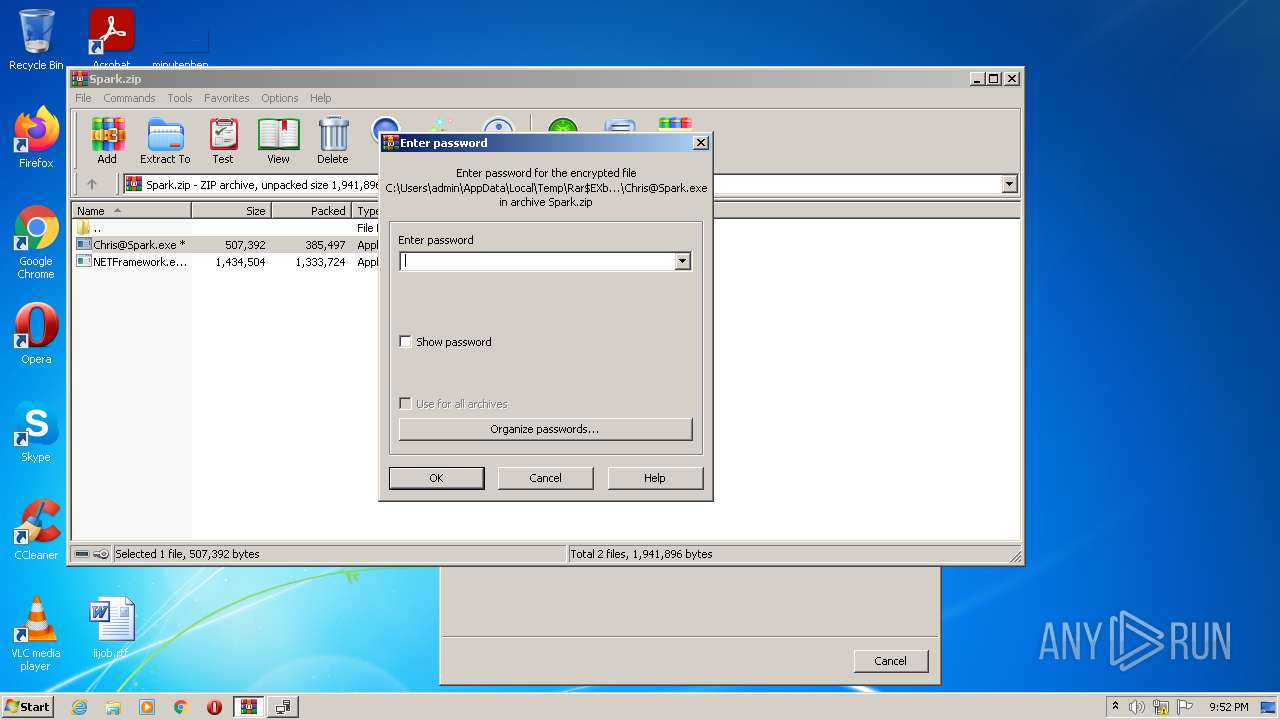
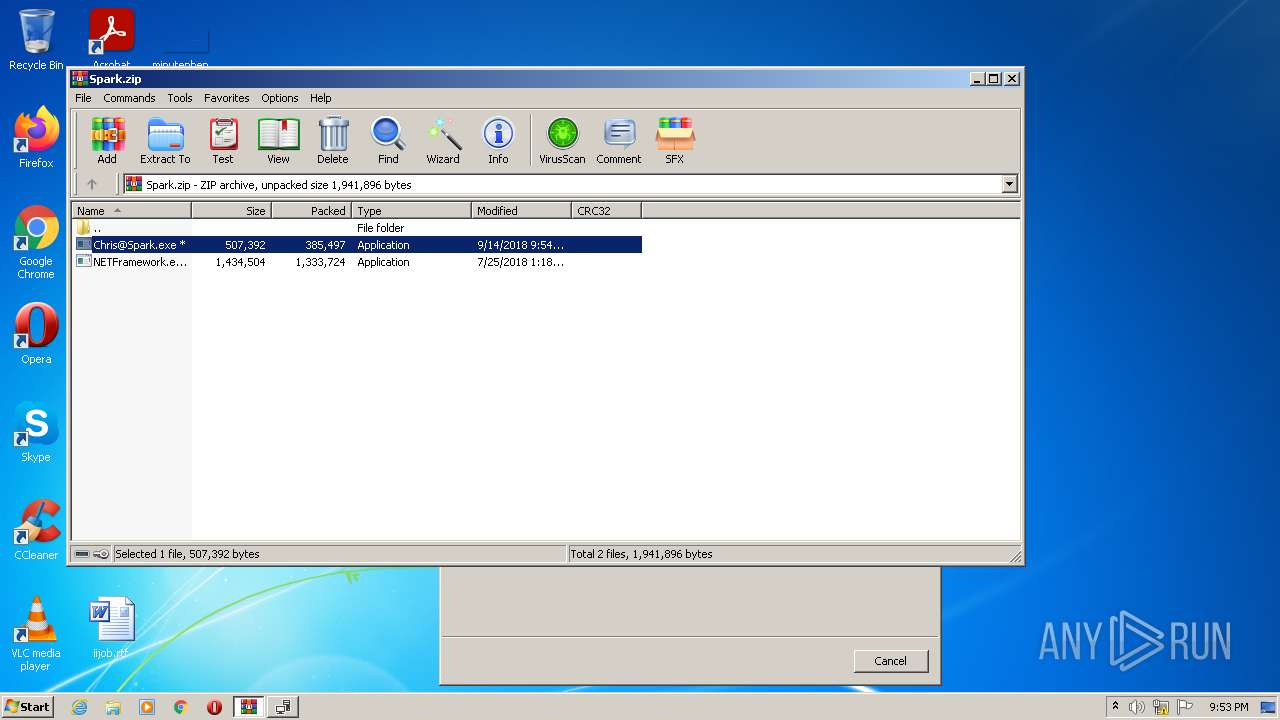
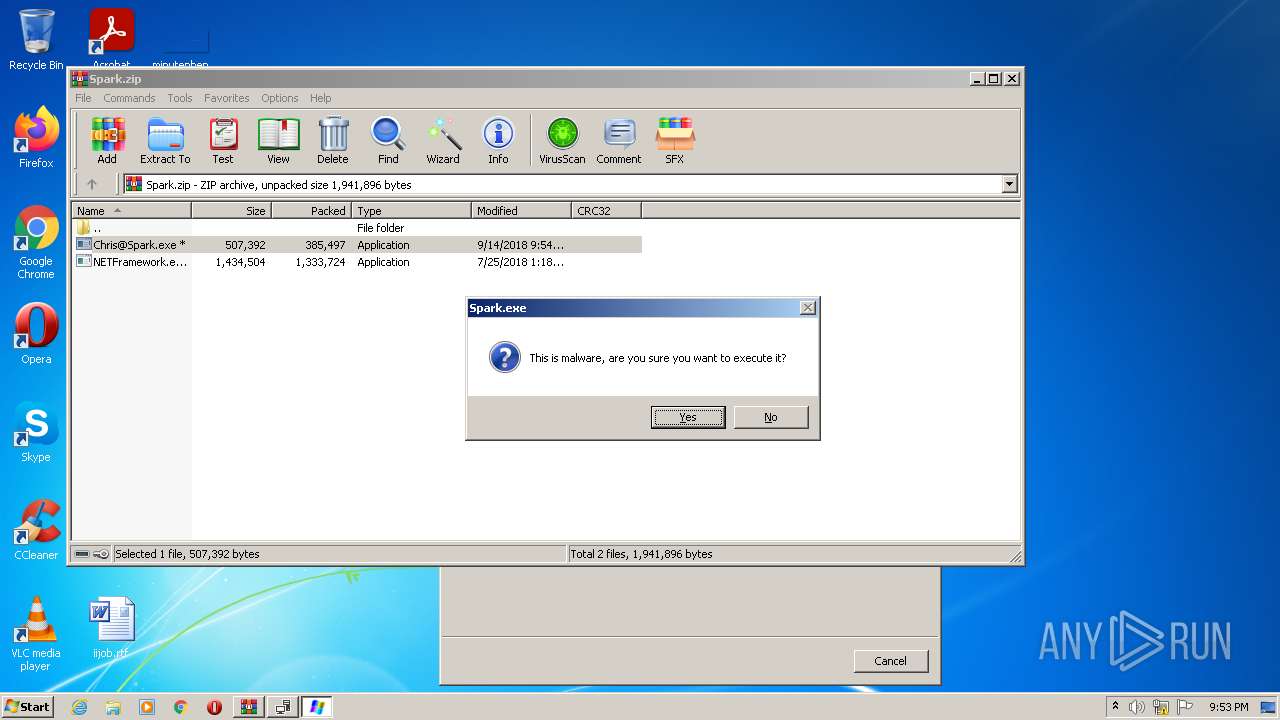
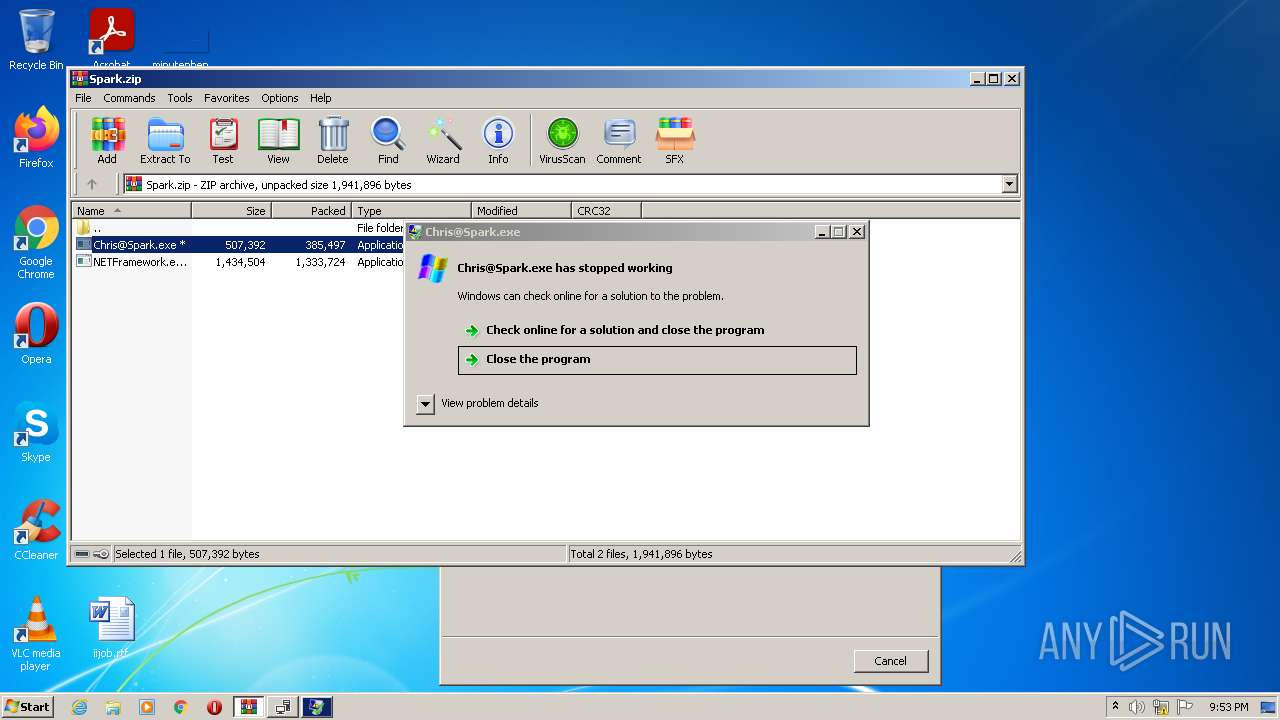
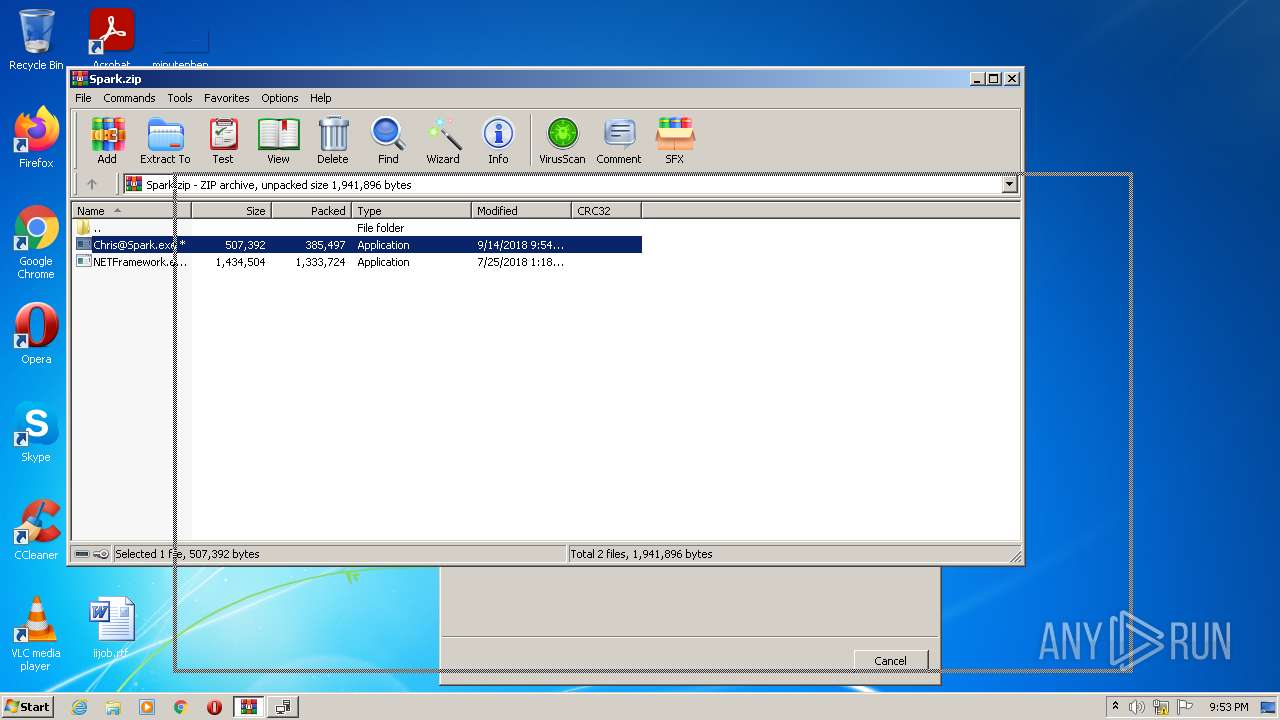
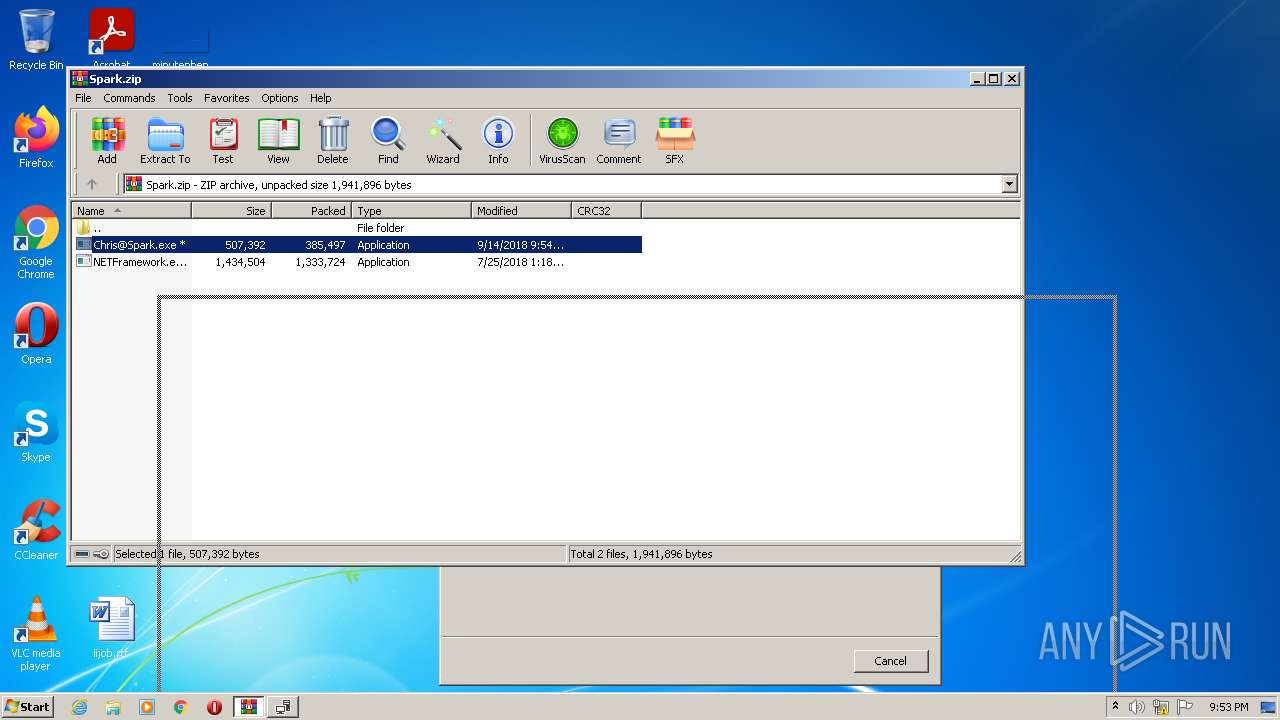
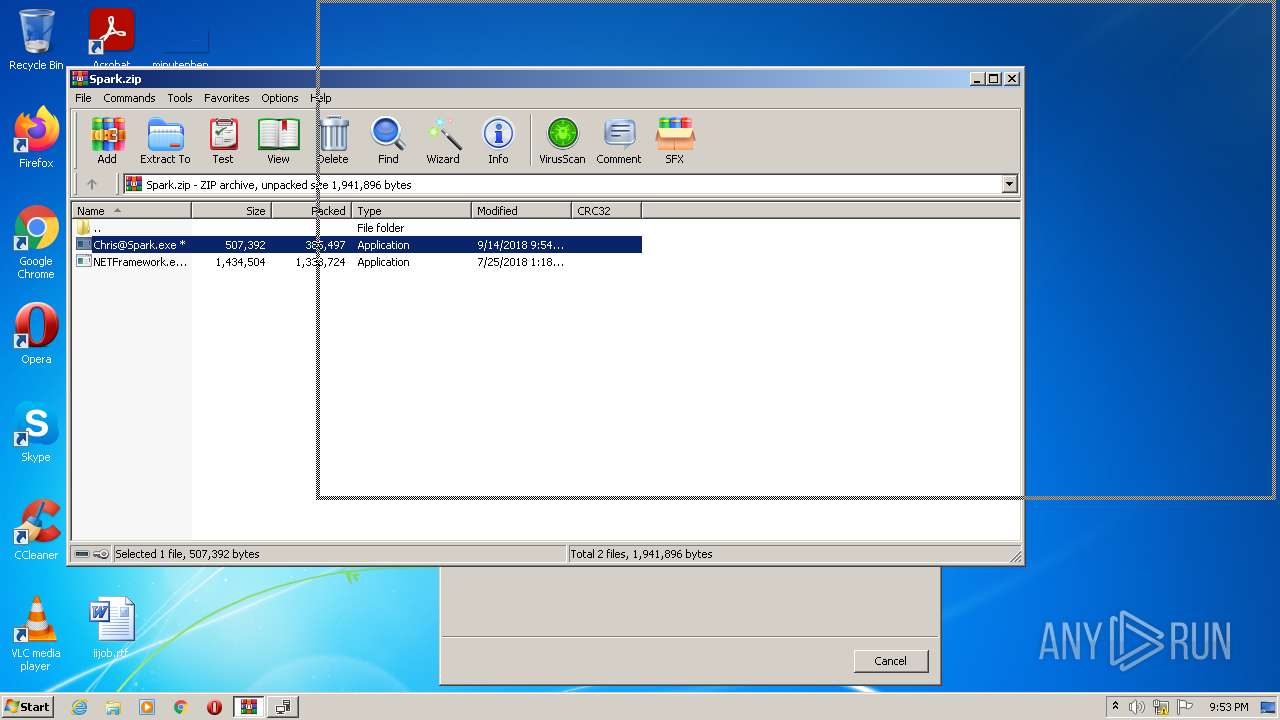
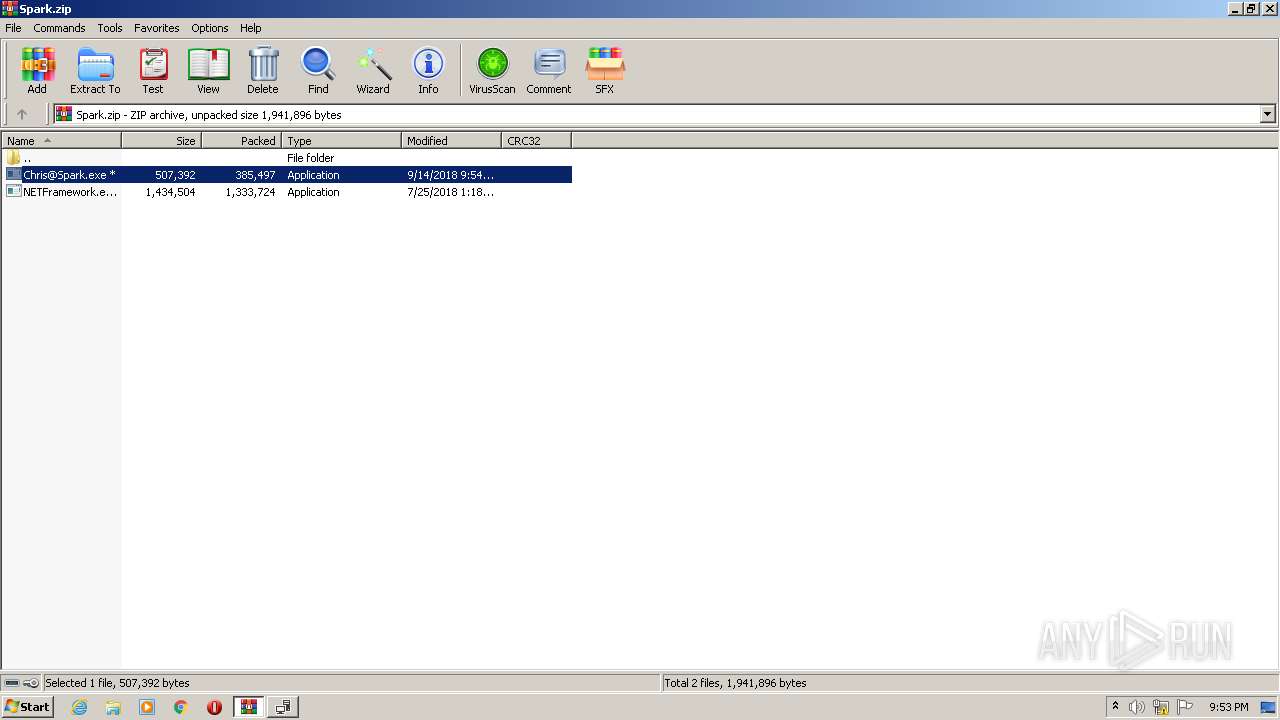
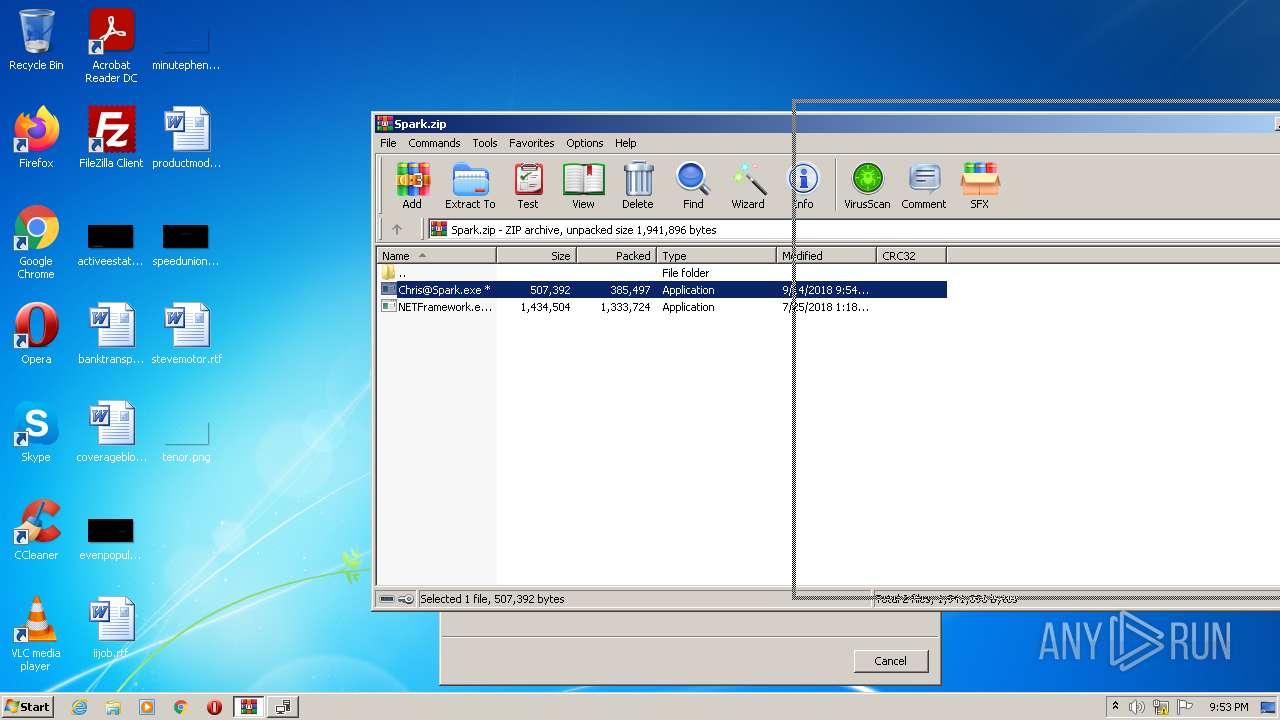
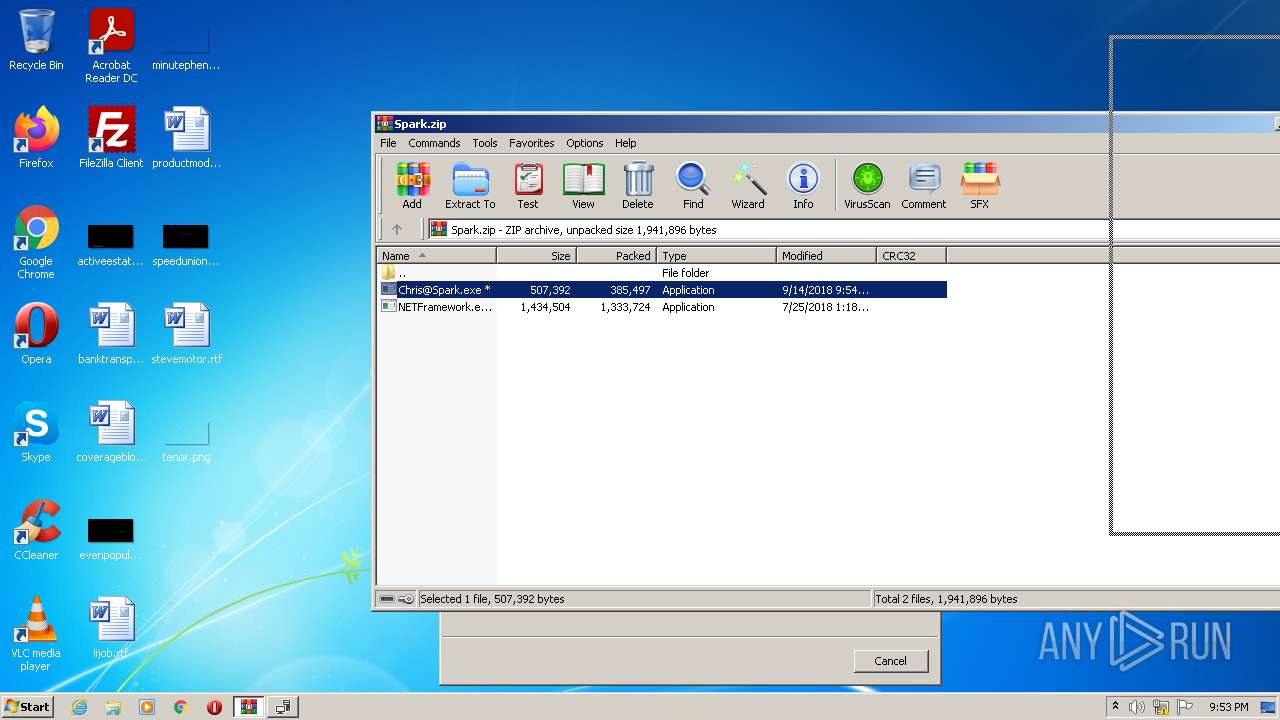
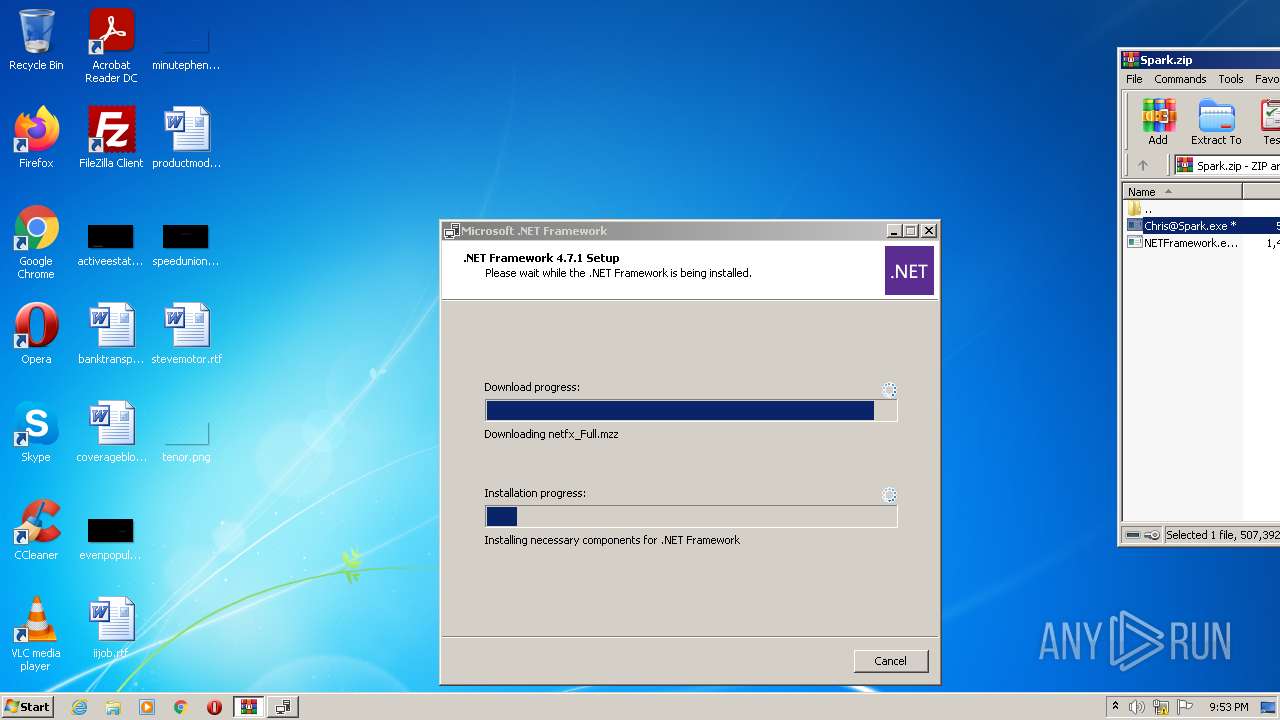
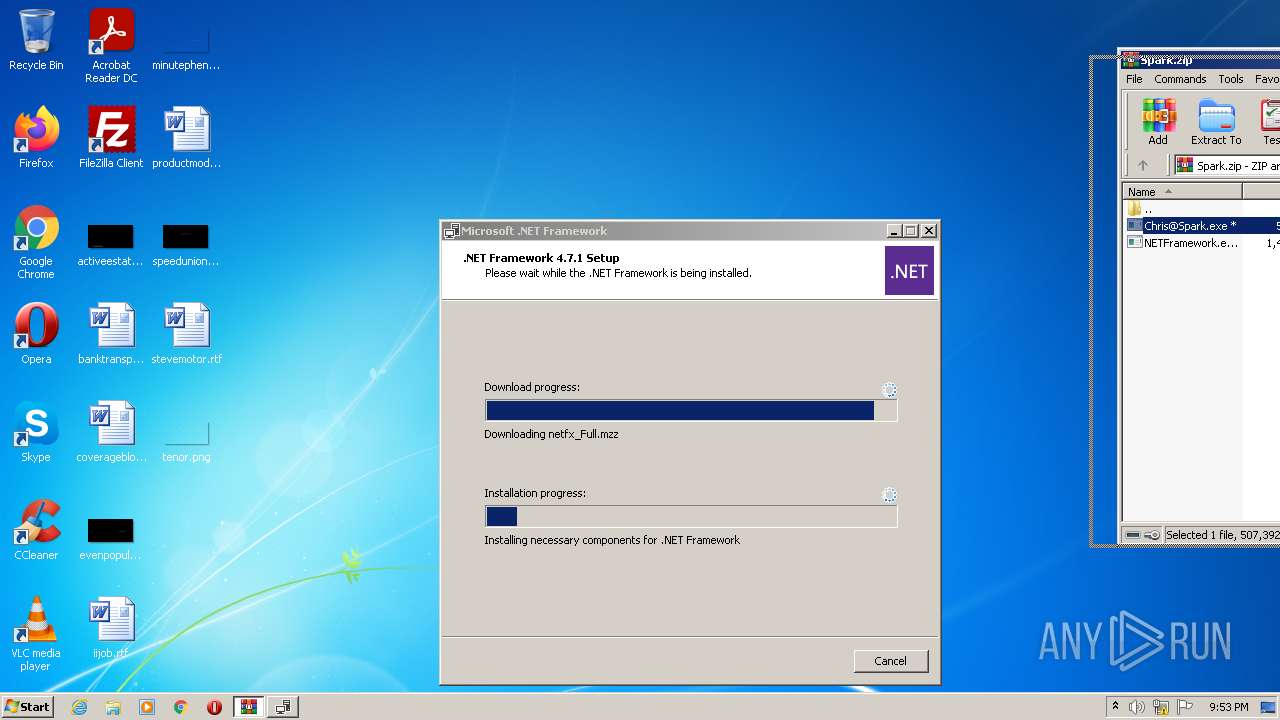
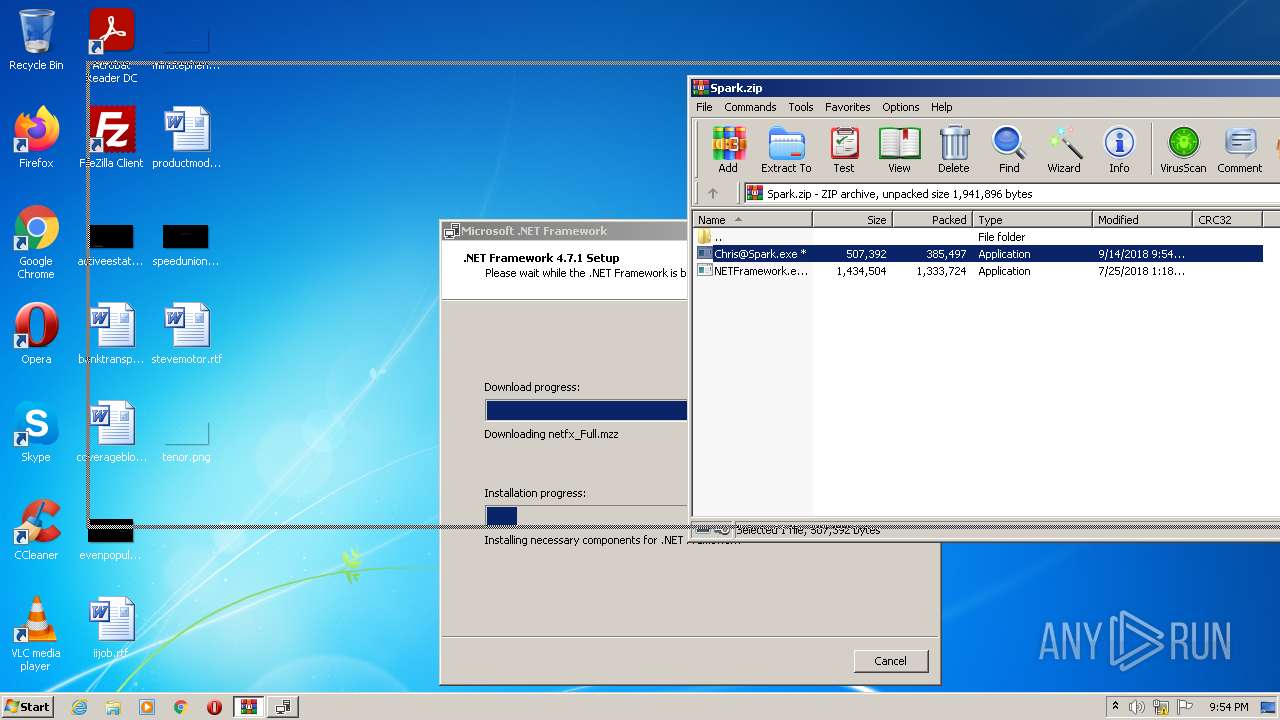
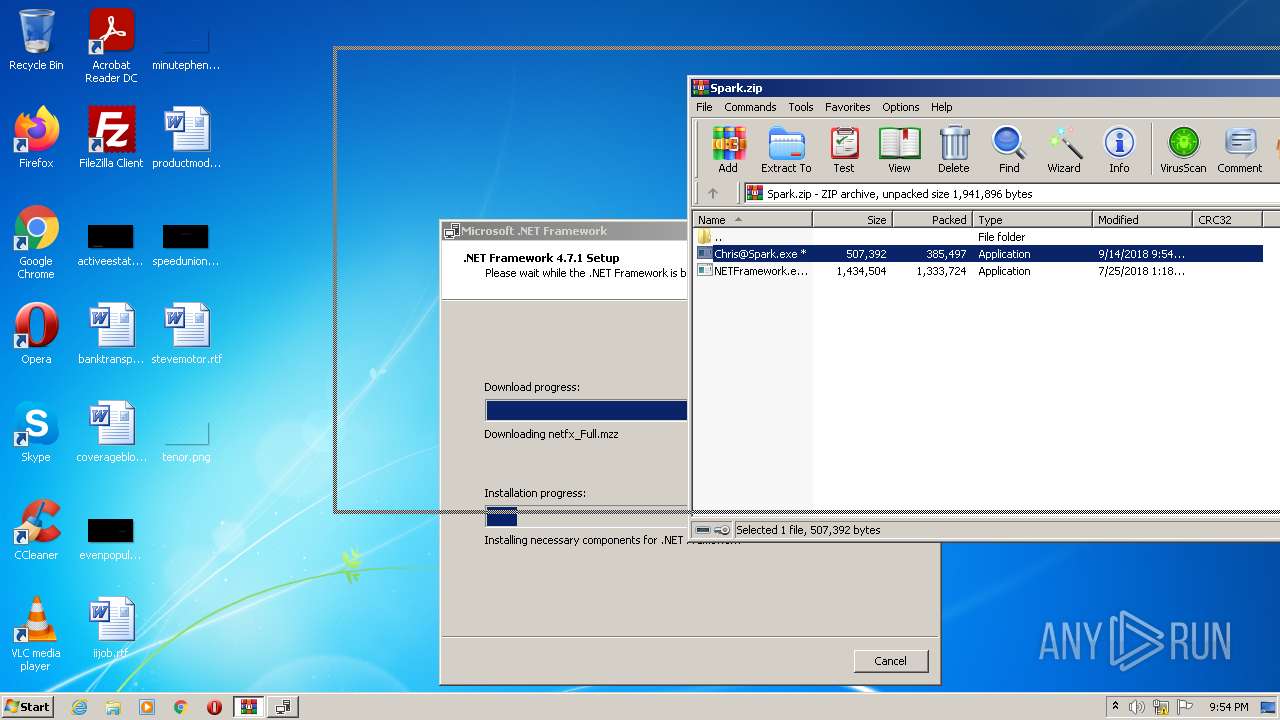
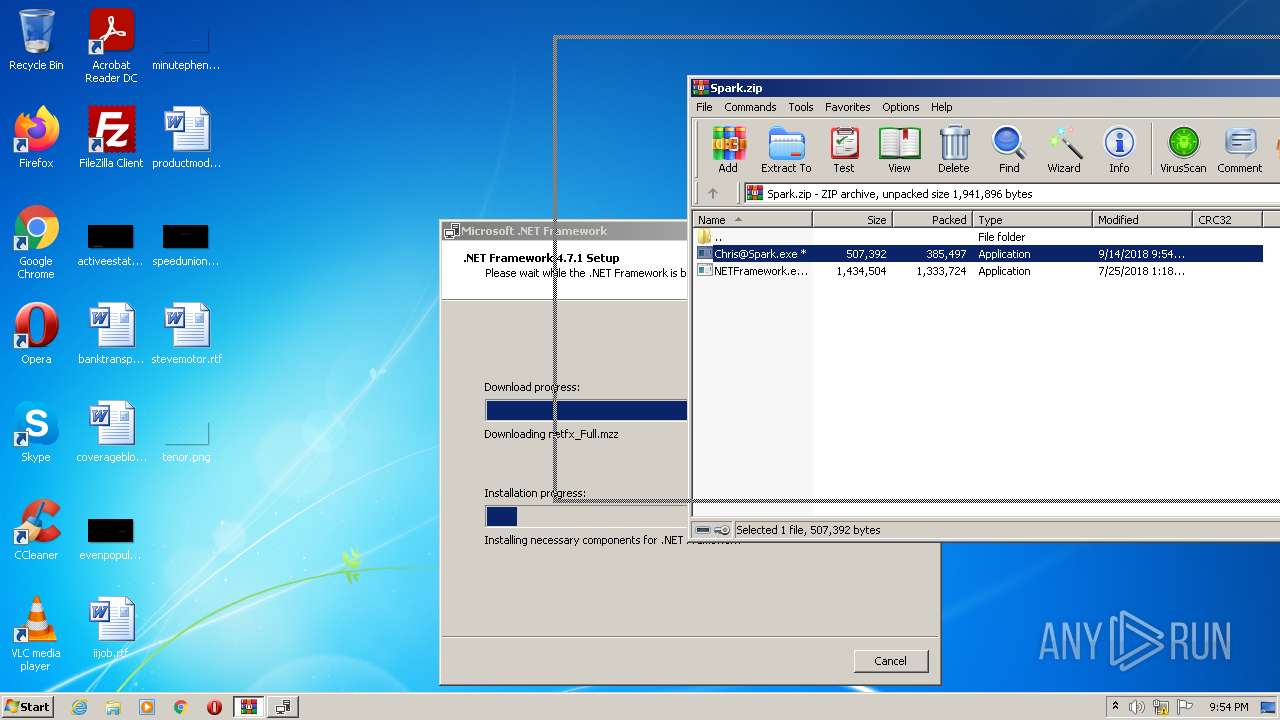
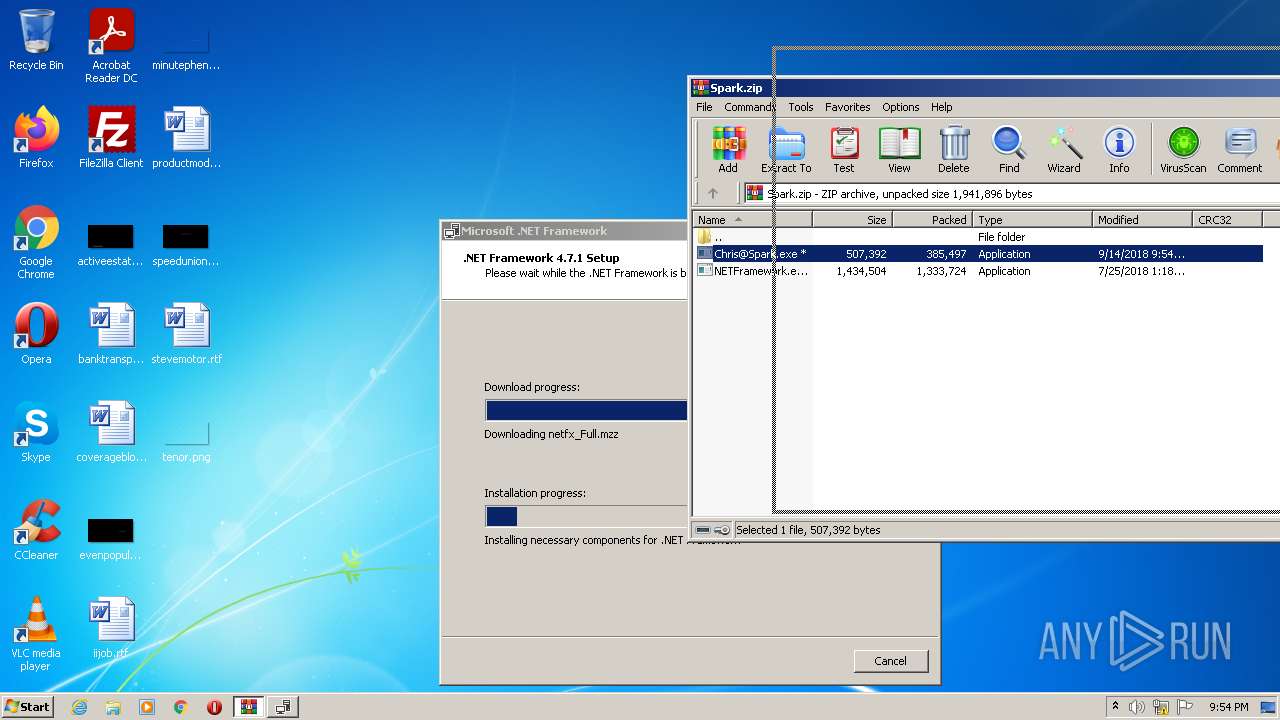
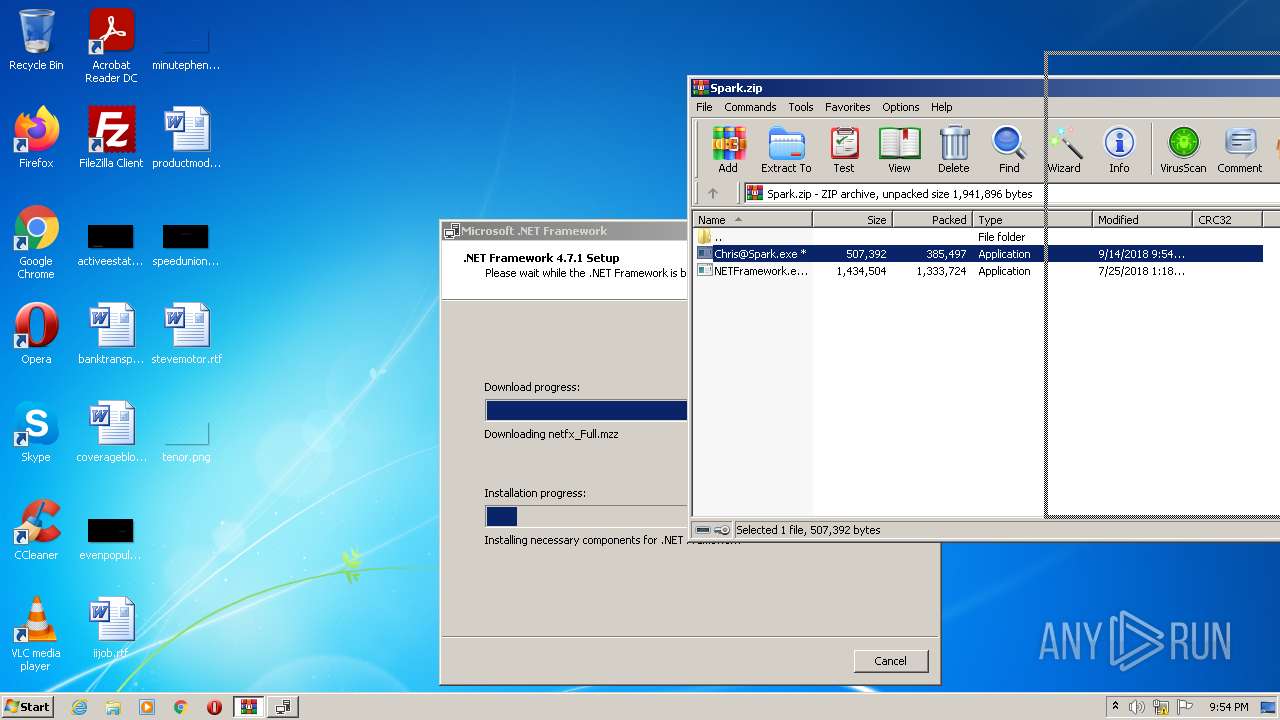
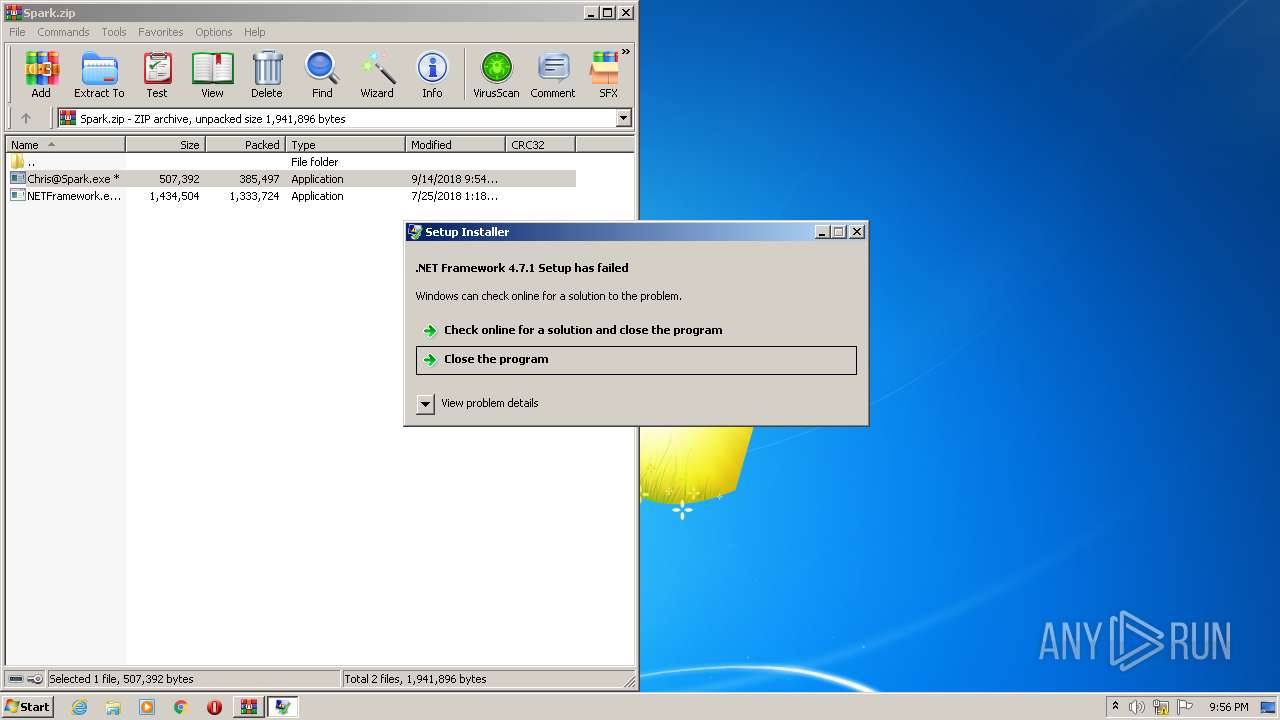
| File name: | Spark.zip |
| Full analysis: | https://app.any.run/tasks/06224c90-c0ea-4d27-81d9-9728f144b49b |
| Verdict: | Malicious activity |
| Analysis date: | February 07, 2022, 21:51:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract |
| MD5: | 860168A14356BE3E65650B8A3CF6C3A0 |
| SHA1: | EA99E29E119D88CAF9D38FB6AAC04A97E9C5AC63 |
| SHA256: | 1AE2A53C8ADC94B1566EA6B3AA63CE7FE2A2B2FCBE4CEC3112F9EBE76E2E9BF9 |
| SSDEEP: | 49152:p0iszfe7OgN0Fw6KDfcqm6YvBK1+bgHXFZn:4CN0FHMcTvu+E3FZn |
MALICIOUS
Application was dropped or rewritten from another process
- NETFramework.exe (PID: 1688)
- NETFramework.exe (PID: 3184)
- SetupUtility.exe (PID: 2728)
- Setup.exe (PID: 2744)
- Chris@Spark.exe (PID: 2084)
- Chris@Spark.exe (PID: 3004)
- SetupUtility.exe (PID: 3476)
Actions looks like stealing of personal data
- NETFramework.exe (PID: 1688)
- Chris@Spark.exe (PID: 3004)
Drops executable file immediately after starts
- NETFramework.exe (PID: 1688)
Application was injected by another process
- svchost.exe (PID: 924)
Changes settings of System certificates
- Setup.exe (PID: 2744)
Runs injected code in another process
- Setup.exe (PID: 2744)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3820)
- NETFramework.exe (PID: 1688)
- Chris@Spark.exe (PID: 3004)
Checks supported languages
- WinRAR.exe (PID: 3820)
- NETFramework.exe (PID: 1688)
- Setup.exe (PID: 2744)
- SetupUtility.exe (PID: 2728)
- SetupUtility.exe (PID: 3476)
- Chris@Spark.exe (PID: 3004)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3820)
- NETFramework.exe (PID: 1688)
- Chris@Spark.exe (PID: 3004)
Reads the computer name
- NETFramework.exe (PID: 1688)
- WinRAR.exe (PID: 3820)
- Setup.exe (PID: 2744)
- SetupUtility.exe (PID: 3476)
- SetupUtility.exe (PID: 2728)
- Chris@Spark.exe (PID: 3004)
Reads Environment values
- Setup.exe (PID: 2744)
Reads CPU info
- Setup.exe (PID: 2744)
Creates files in the Windows directory
- Chris@Spark.exe (PID: 3004)
Creates files in the program directory
- Setup.exe (PID: 2744)
INFO
Reads settings of System Certificates
- Setup.exe (PID: 2744)
Checks Windows Trust Settings
- Setup.exe (PID: 2744)
Checks supported languages
- svchost.exe (PID: 924)
Dropped object may contain Bitcoin addresses
- SetupUtility.exe (PID: 2728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | Chris@Spark.exe |
|---|---|
| ZipUncompressedSize: | 507392 |
| ZipCompressedSize: | 385497 |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2018:09:14 23:54:10 |
| ZipCompression: | Unknown (99) |
| ZipBitFlag: | 0x0001 |
| ZipRequiredVersion: | 51 |
Total processes
51
Monitored processes
9
Malicious processes
4
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 924 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\system32\svchost.exe | services.exe | |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
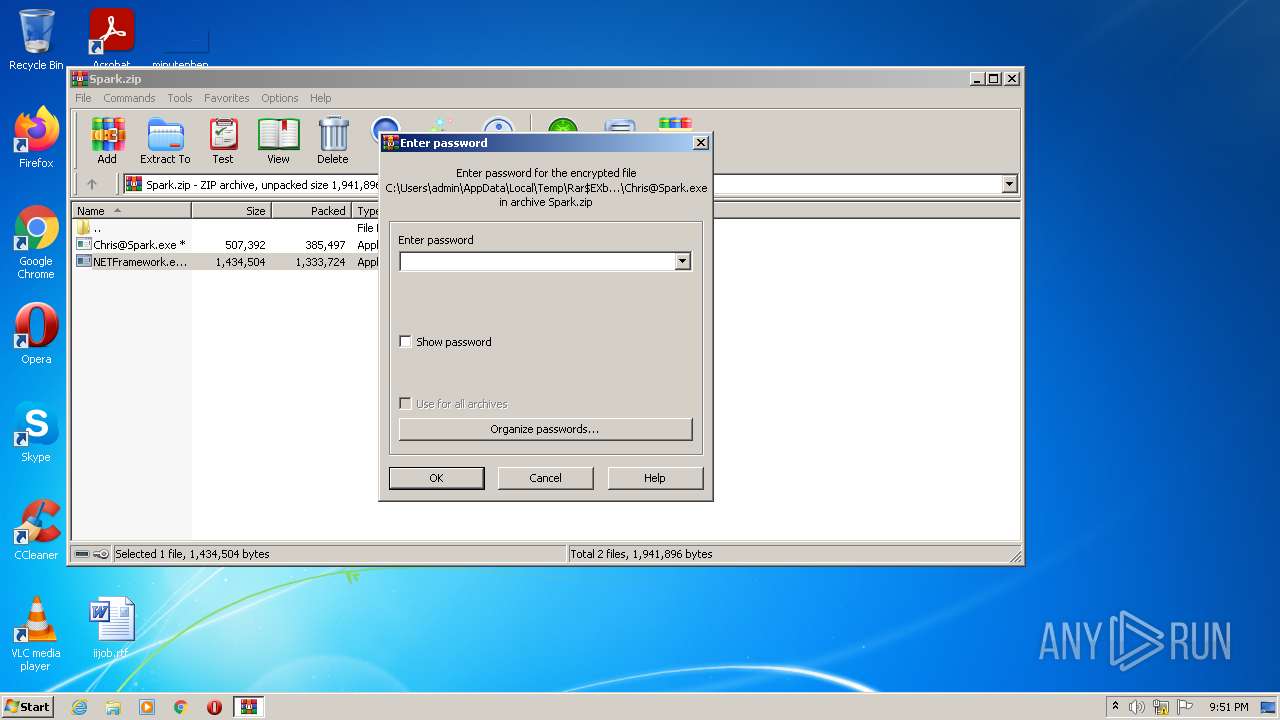
| 1688 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3820.37372\NETFramework.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3820.37372\NETFramework.exe | WinRAR.exe | |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 4.7.1 Setup Exit code: 2148204801 Version: 4.7.02558.00 | ||||
| 2084 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3820.42410\Chris@Spark.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3820.42410\Chris@Spark.exe | — | WinRAR.exe |
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 | ||||
| 2728 | SetupUtility.exe /aupause | C:\99878908134376de4078\SetupUtility.exe | — | Setup.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 4.5 Setup Exit code: 0 Version: 14.7.2558.0 built by: NET471REL1 | ||||
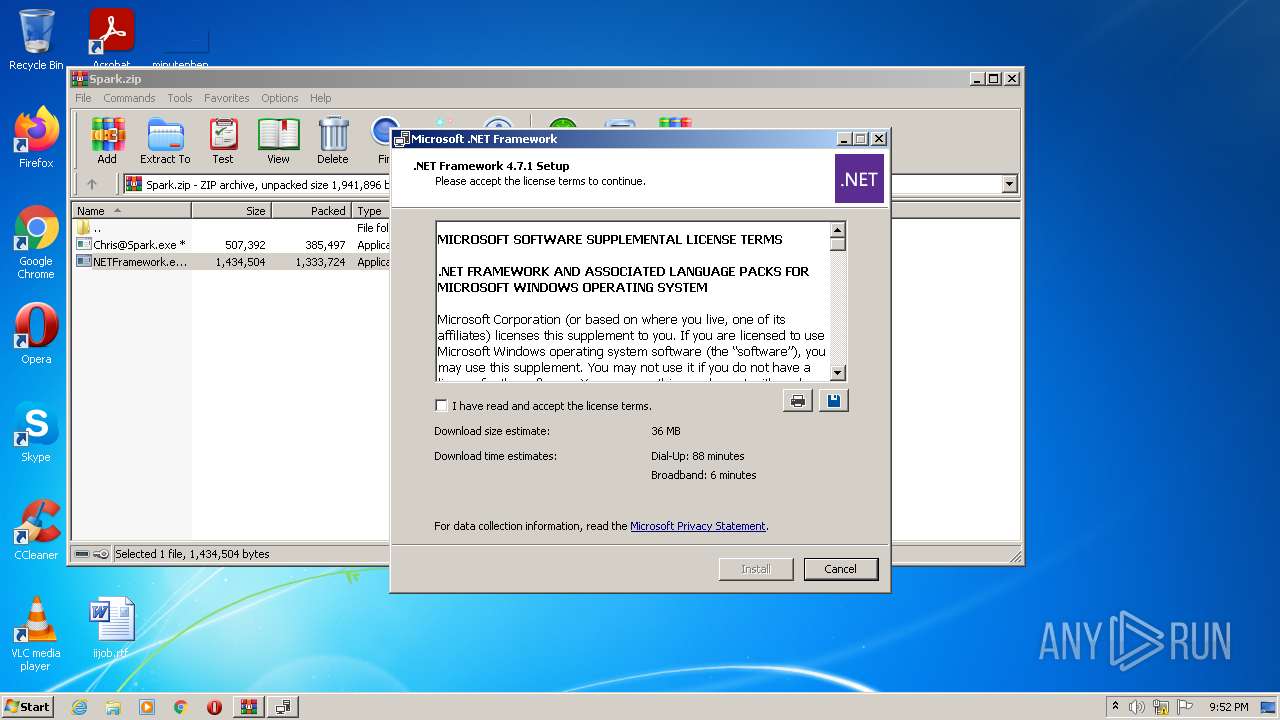
| 2744 | C:\99878908134376de4078\\Setup.exe /x86 /x64 /web | C:\99878908134376de4078\Setup.exe | NETFramework.exe | |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Setup Installer Exit code: 2148204801 Version: 14.7.2558.0 built by: NET471REL1 | ||||
| 3004 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3820.42410\Chris@Spark.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3820.42410\Chris@Spark.exe | WinRAR.exe | |
User: admin Integrity Level: HIGH Description: Exit code: 3762504530 Version: 0.0.0.0 | ||||
| 3184 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3820.37372\NETFramework.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3820.37372\NETFramework.exe | — | WinRAR.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Framework 4.7.1 Setup Exit code: 3221226540 Version: 4.7.02558.00 | ||||
| 3476 | SetupUtility.exe /screboot | C:\99878908134376de4078\SetupUtility.exe | — | Setup.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 4.5 Setup Exit code: 0 Version: 14.7.2558.0 built by: NET471REL1 | ||||
| 3820 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Spark.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | |
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
36
Suspicious files
9
Text files
81
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3820 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3820.37372\Chris@Spark.exe | executable | |
MD5:181EE63003E5C3EC8C378030286ED7A2 | SHA256:55BFCB784904477EF62EF7E4994DEE42F03D69BFEC3591989513CCCBBA3FC8FE | |||
| 3820 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3820.37372\NETFramework.exe | executable | |
MD5:4FB795478A8F346C337A1F84BACCC85B | SHA256:65A7CB8FD1C7C529C40345B4746818F8947BE736AA105007DFCC57B05897ED62 | |||
| 1688 | NETFramework.exe | C:\99878908134376de4078\Graphics\Rotate4.ico | image | |
MD5:267B198FEF022D3B1D44CCA7FE589373 | SHA256:303989B692A57FE34B47BB2F926B91AC605F288AE6C9479B33EAF15A14EB33AC | |||
| 1688 | NETFramework.exe | C:\99878908134376de4078\Graphics\Rotate1.ico | image | |
MD5:9B70C7FA81DCA6D3B992037D0C251D92 | SHA256:18226B9D56D2B1C070A2C606428892773CB00B5B4B95397E79D01DE26685CCD4 | |||
| 1688 | NETFramework.exe | C:\99878908134376de4078\DisplayIcon.ico | image | |
MD5:F9657D290048E169FFABBBB9C7412BE0 | SHA256:B74AD253B9B8F9FCADE725336509143828EE739CC2B24782BE3ECFF26F229160 | |||
| 1688 | NETFramework.exe | C:\99878908134376de4078\header.bmp | image | |
MD5:41C22EFA84CA74F0CE7076EB9A482E38 | SHA256:255025A0D79EF2DAC04BD610363F966EF58328400BF31E1F8915E676478CD750 | |||
| 1688 | NETFramework.exe | C:\99878908134376de4078\Graphics\Rotate10.ico | image | |
MD5:0CCA04A3468575FDCEFEE9957E32F904 | SHA256:B94E68C711B3B06D9A63C80AD013C7C7BBDB5F8E82CBC866B246FF22D99B03FE | |||
| 1688 | NETFramework.exe | C:\99878908134376de4078\Graphics\Rotate5.ico | image | |
MD5:25F0D572761CB610BDAD6DD980C46CC7 | SHA256:CE2AFC0AA52B3D459D6D8D7C551F7B8FBF323E2260326908C37A13F21FEE423E | |||
| 1688 | NETFramework.exe | C:\99878908134376de4078\Graphics\Rotate6.ico | image | |
MD5:5AC2B8E1A766C204F996D9CE33FB3DB4 | SHA256:EE387D9642DF93E4240361077AF6051C1B7E643C3CF110F43DA42E0EFE29A375 | |||
| 1688 | NETFramework.exe | C:\99878908134376de4078\Graphics\Save.ico | image | |
MD5:C66BBE8F84496EF85F7AF6BED5212CEC | SHA256:1372C7F132595DDAD210C617E44FEDFF7A990A9E8974CC534CA80D897DD15ABD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
32
TCP/UDP connections
80
DNS requests
6
Threats
36
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
924 | svchost.exe | HEAD | 302 | 23.2.175.10:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=netfx&sbp=Net471Rel1&plcid=0x409&clcid=0x409&ar=02558.00&sar=x86&o1=netfx_Full.mzz | US | — | — | whitelisted |
924 | svchost.exe | HEAD | 302 | 23.2.175.10:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=netfx&sbp=Net471Rel1&plcid=0x409&clcid=0x409&ar=02558.00&sar=x86&o1=netfx_Full.mzz | US | — | — | whitelisted |
924 | svchost.exe | HEAD | 302 | 23.2.175.10:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=netfx&sbp=Net471Rel1&plcid=0x409&clcid=0x409&ar=02558.00&sar=x86&o1=netfx_Full.mzz | US | — | — | whitelisted |
924 | svchost.exe | HEAD | 302 | 23.2.175.10:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=netfx&sbp=Net471Rel1&plcid=0x409&clcid=0x409&ar=02558.00&sar=x86&o1=netfx_Full.mzz | US | — | — | whitelisted |
924 | svchost.exe | HEAD | 302 | 23.2.175.10:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=netfx&sbp=Net471Rel1&plcid=0x409&clcid=0x409&ar=02558.00&sar=x86&o1=netfx_Full.mzz | US | — | — | whitelisted |
2744 | Setup.exe | GET | 302 | 23.2.175.10:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=netfx&sbp=Net471Rel1&plcid=0x409&clcid=0x409&ar=02558.00&sar=x86&o1=netfx_Full.mzz | US | — | — | whitelisted |
2744 | Setup.exe | GET | 302 | 23.2.175.10:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=netfx&sbp=Net471Rel1&plcid=0x409&clcid=0x409&ar=02558.00&sar=x86&o1=netfx_Full.mzz | US | — | — | whitelisted |
924 | svchost.exe | HEAD | 302 | 23.2.175.10:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=netfx&sbp=Net471Rel1&plcid=0x409&clcid=0x409&ar=02558.00&sar=x86&o1=netfx_Full.mzz | US | — | — | whitelisted |
924 | svchost.exe | HEAD | 302 | 23.2.175.10:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=netfx&sbp=Net471Rel1&plcid=0x409&clcid=0x409&ar=02558.00&sar=x86&o1=netfx_Full.mzz | US | — | — | whitelisted |
924 | svchost.exe | HEAD | 302 | 23.2.175.10:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=netfx&sbp=Net471Rel1&plcid=0x409&clcid=0x409&ar=02558.00&sar=x86&o1=netfx_Full.mzz | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2744 | Setup.exe | 104.110.191.140:80 | ctldl.windowsupdate.com | Akamai Technologies, Inc. | US | unknown |
2744 | Setup.exe | 104.109.143.7:80 | crl.microsoft.com | Akamai Technologies, Inc. | US | unknown |
924 | svchost.exe | 23.2.175.10:80 | go.microsoft.com | Akamai International B.V. | US | malicious |
924 | svchost.exe | 68.232.34.200:443 | download.visualstudio.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2744 | Setup.exe | 23.2.175.10:80 | go.microsoft.com | Akamai International B.V. | US | malicious |
— | — | 68.232.34.200:443 | download.visualstudio.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2744 | Setup.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2744 | Setup.exe | 68.232.34.200:443 | download.visualstudio.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2744 | Setup.exe | 104.85.1.163:80 | www.microsoft.com | Time Warner Cable Internet LLC | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
download.visualstudio.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
924 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
924 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
924 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
924 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
924 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
924 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
924 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
924 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2744 | Setup.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
924 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
Process | Message |
|---|---|
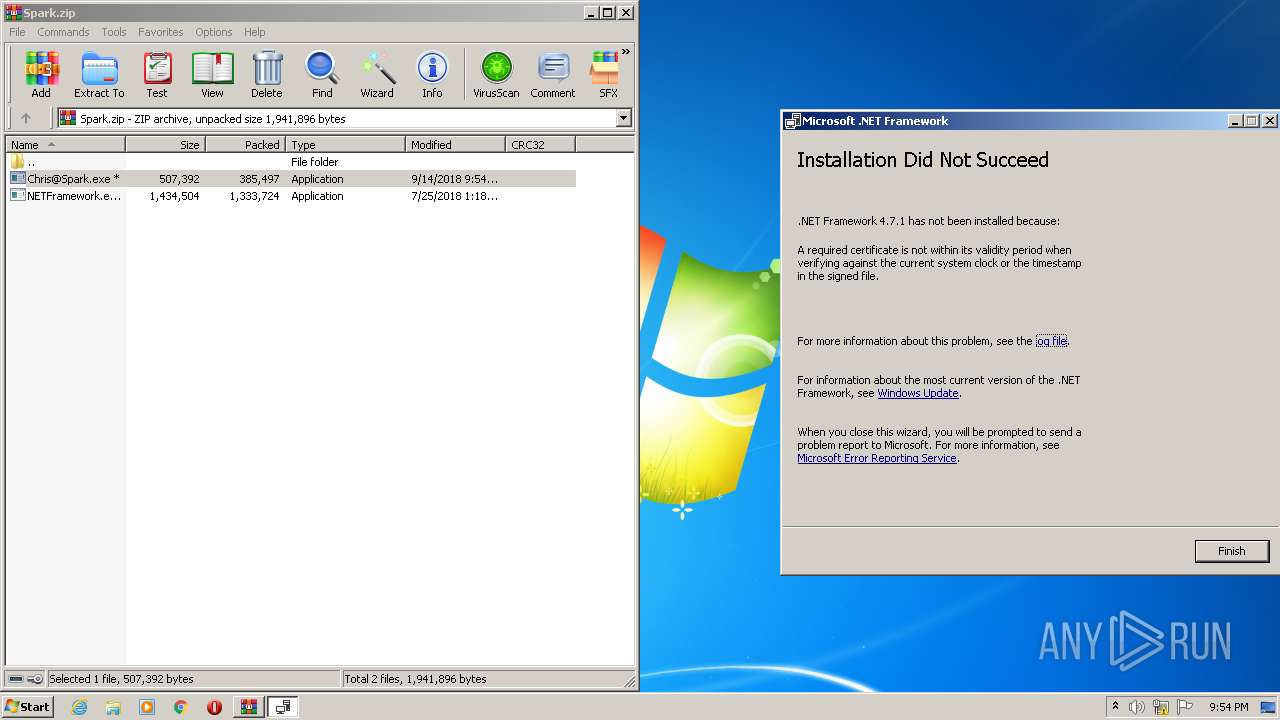
Setup.exe | A required certificate is not within its validity period when verifying against the current system clock or the timestamp in the signed file.
|
Setup.exe | A required certificate is not within its validity period when verifying against the current system clock or the timestamp in the signed file.
|