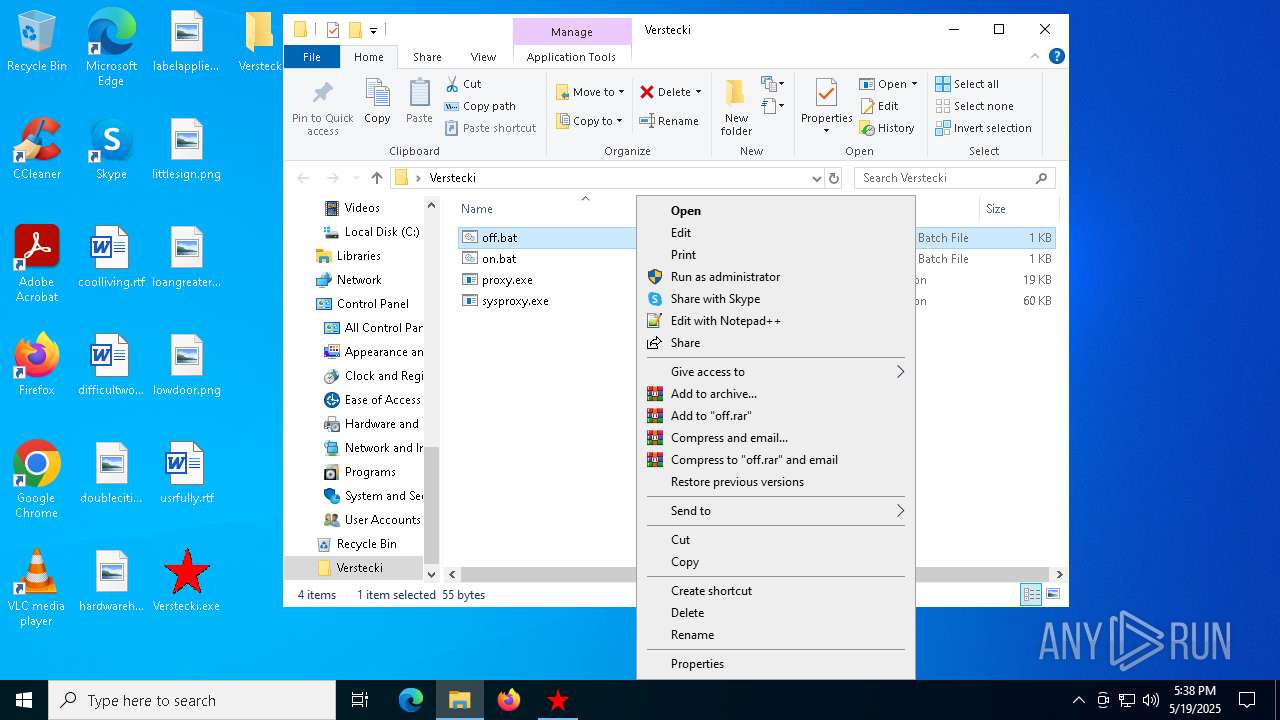
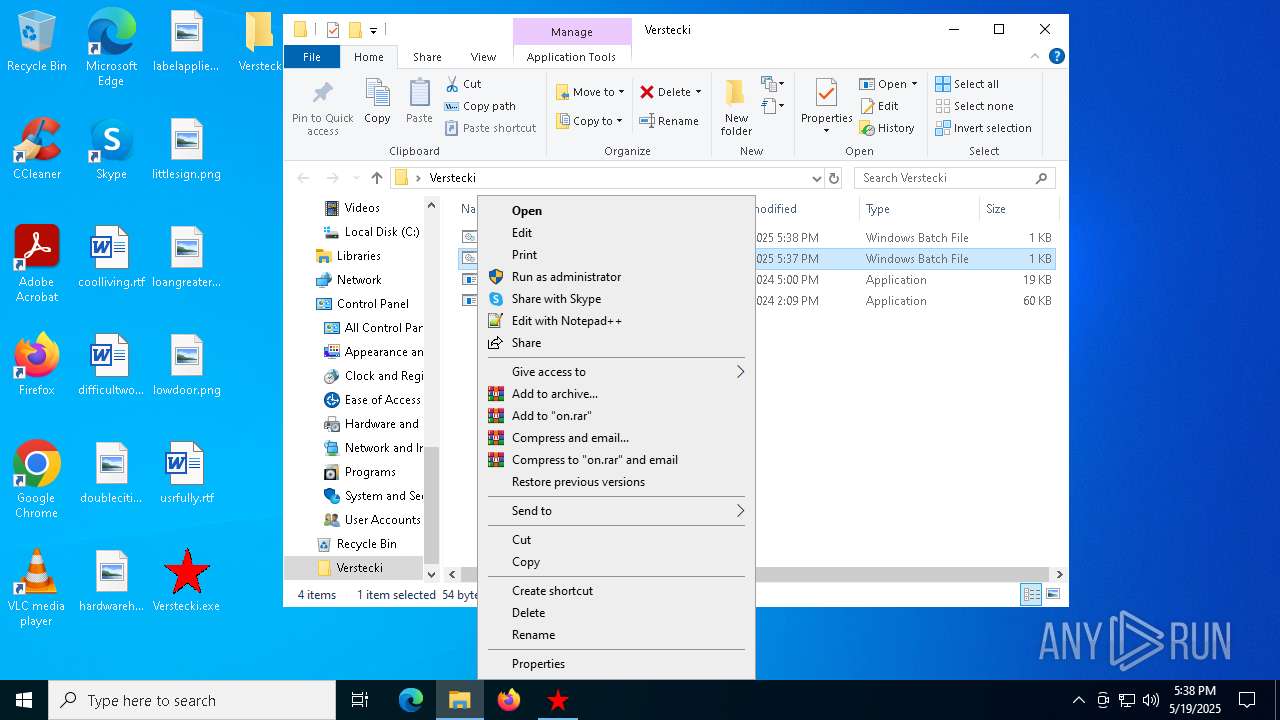
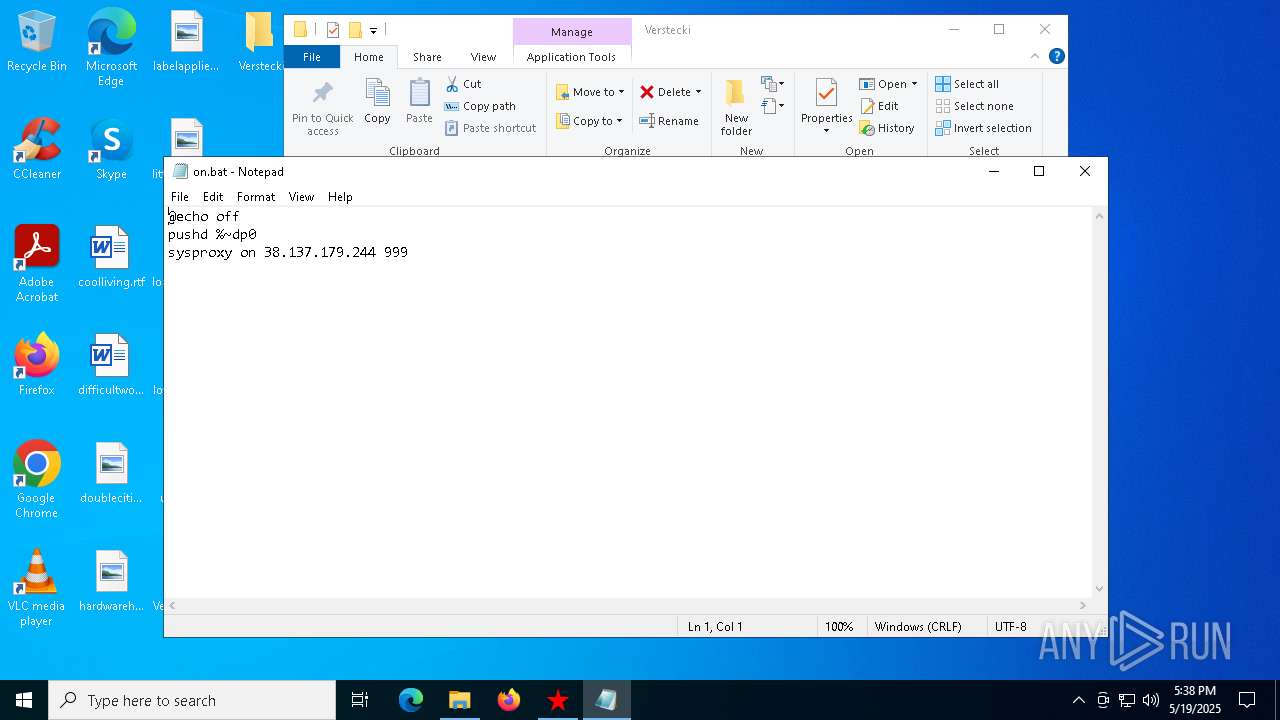
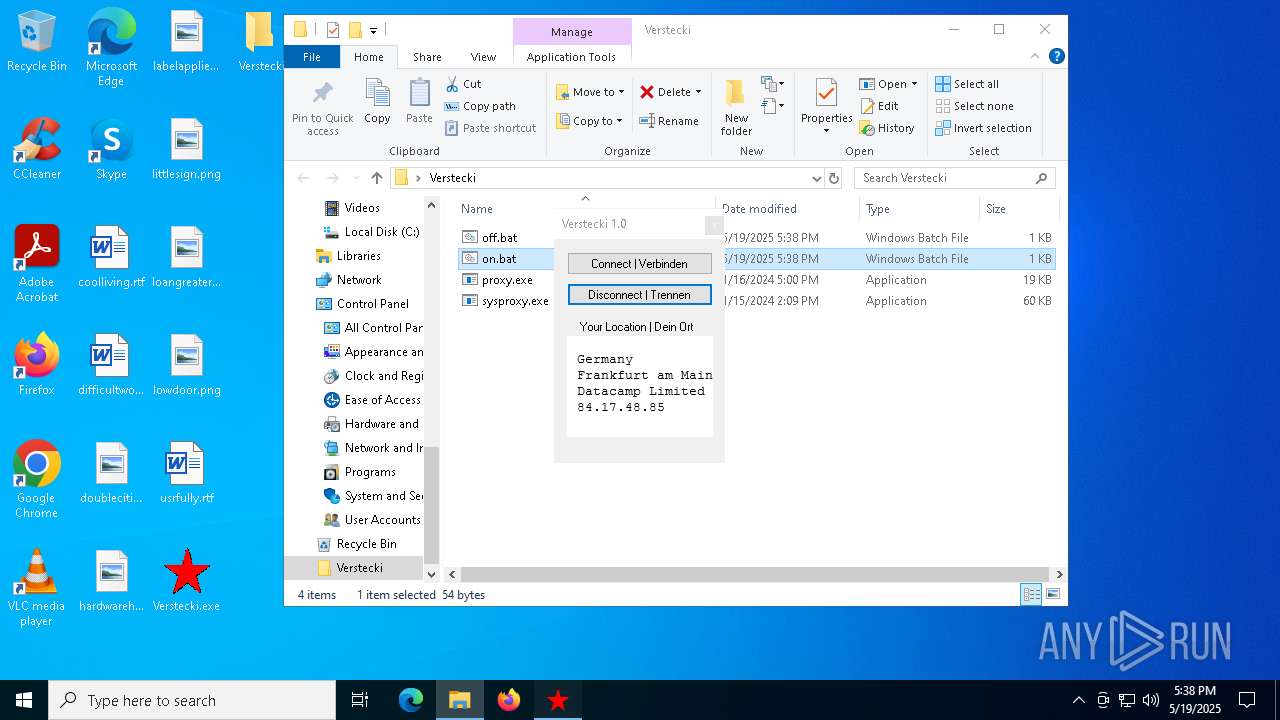
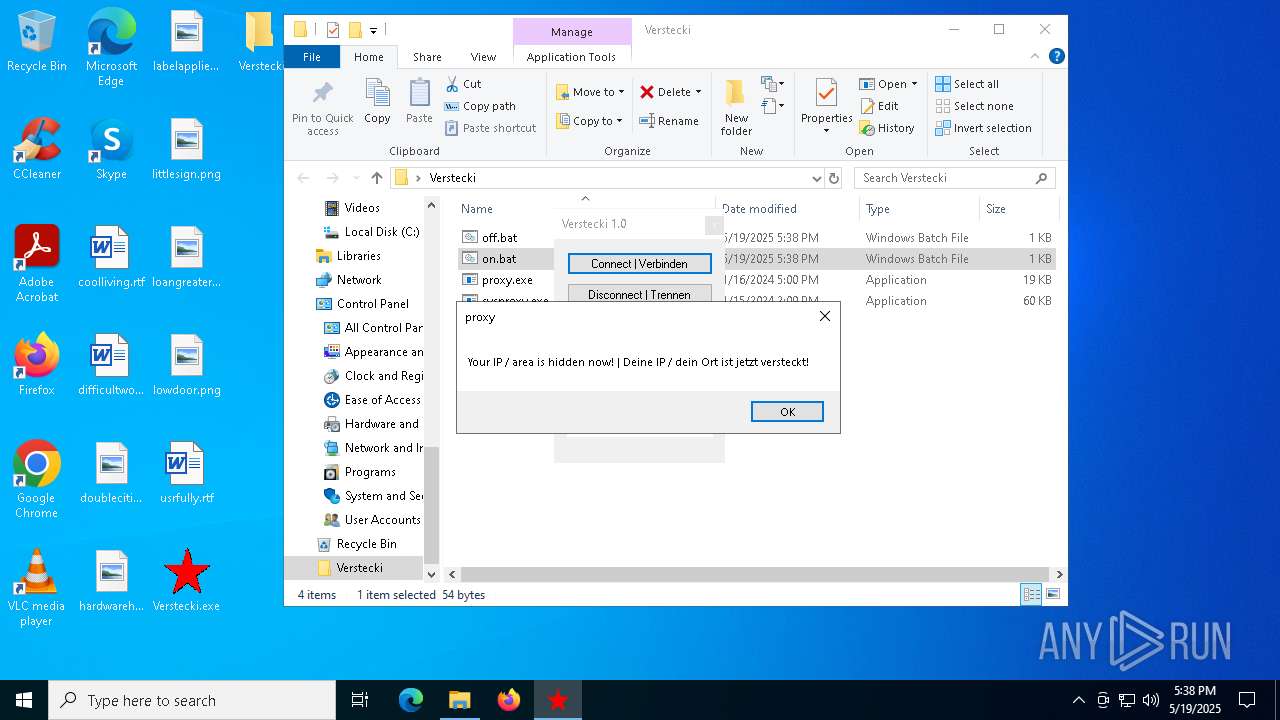
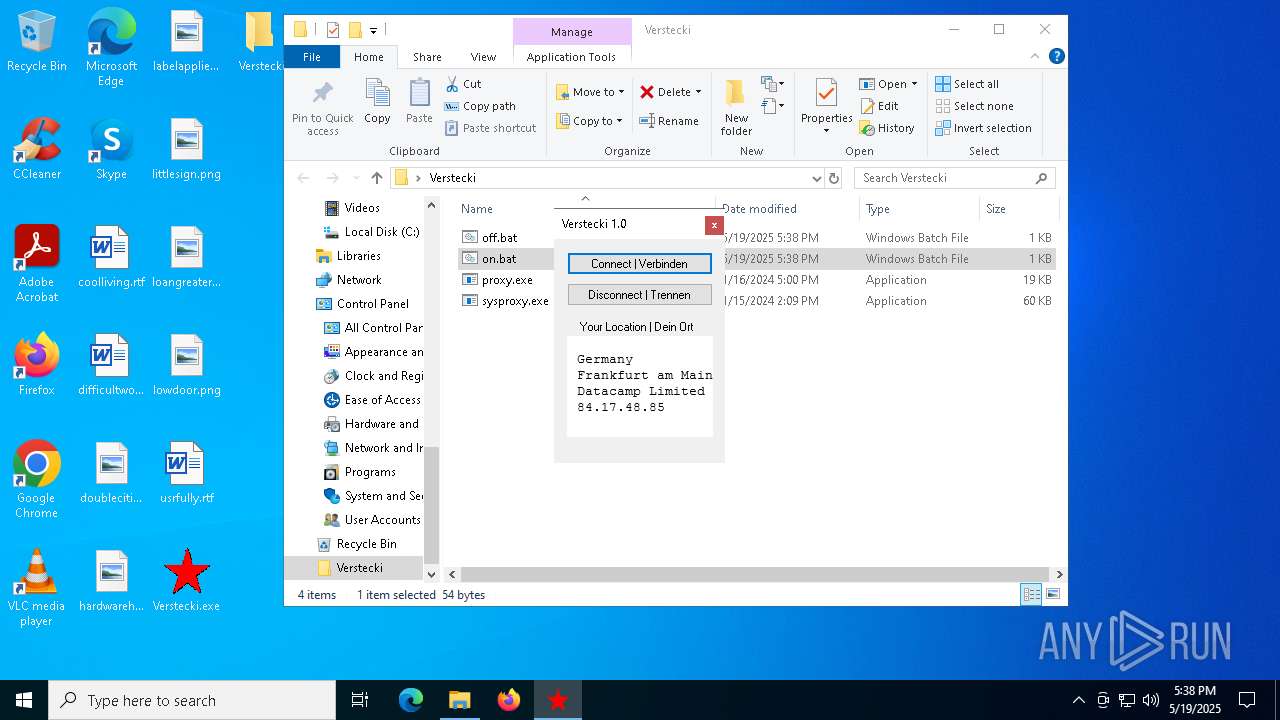
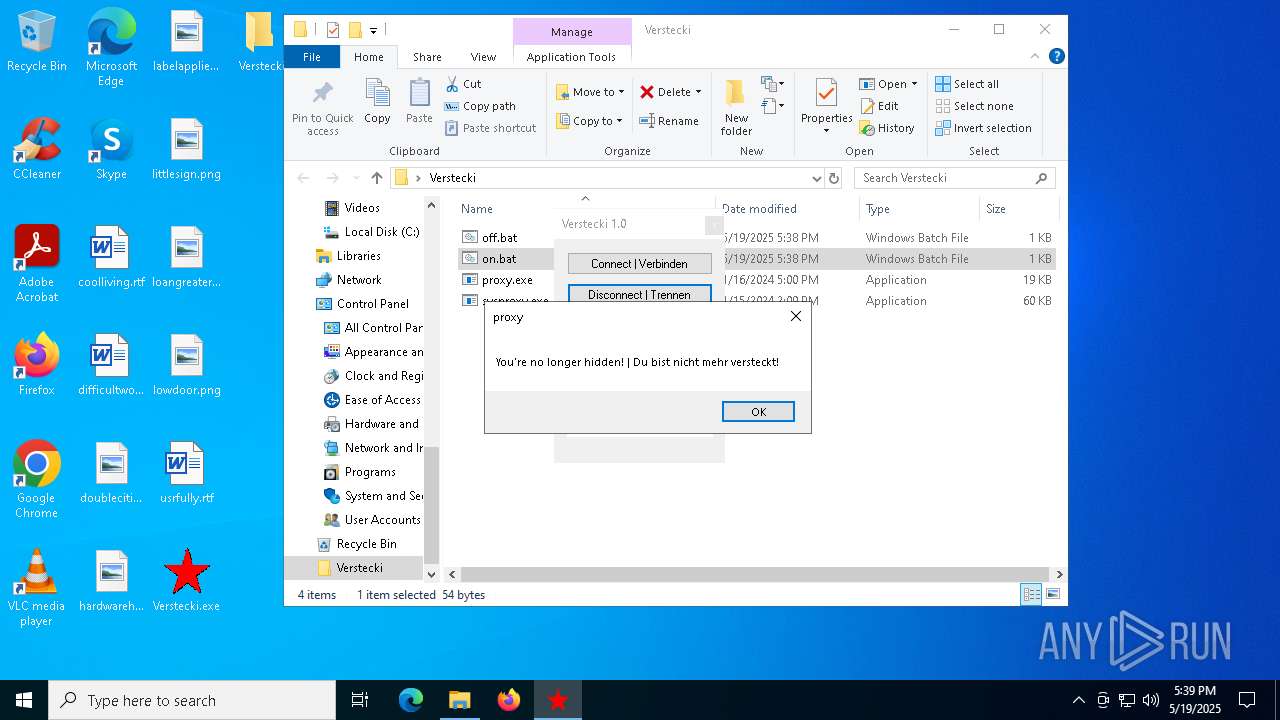
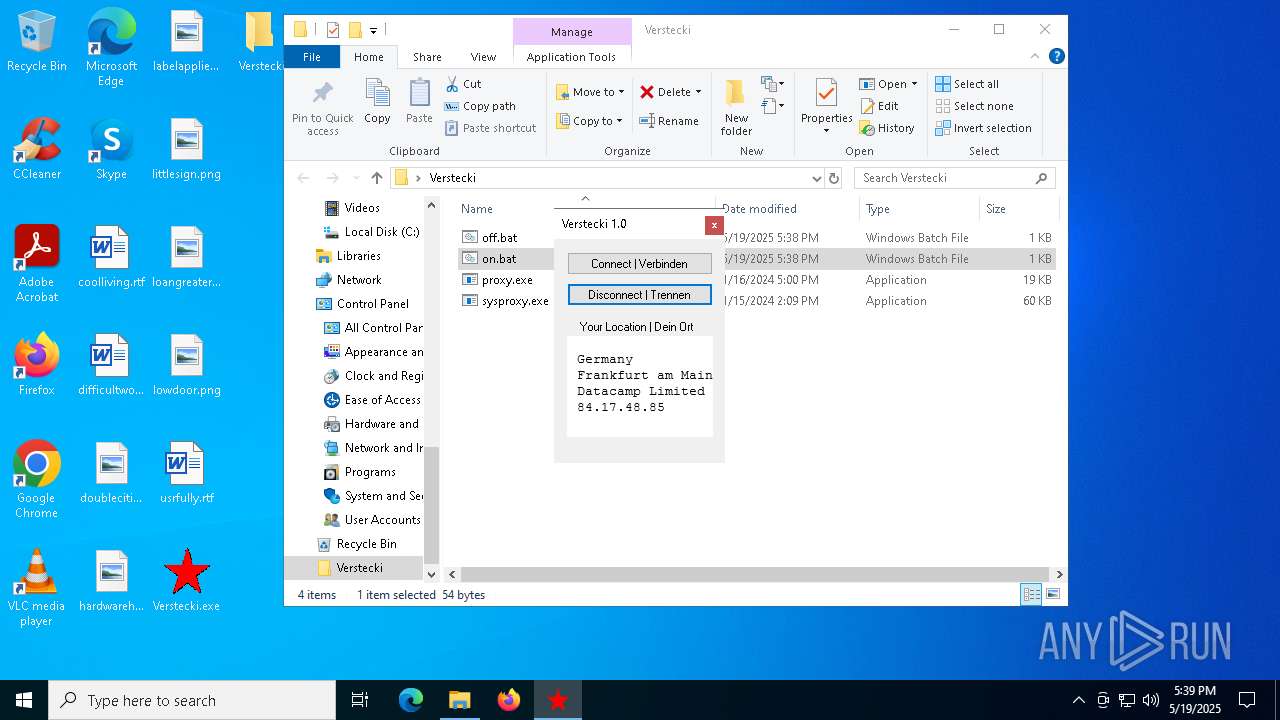
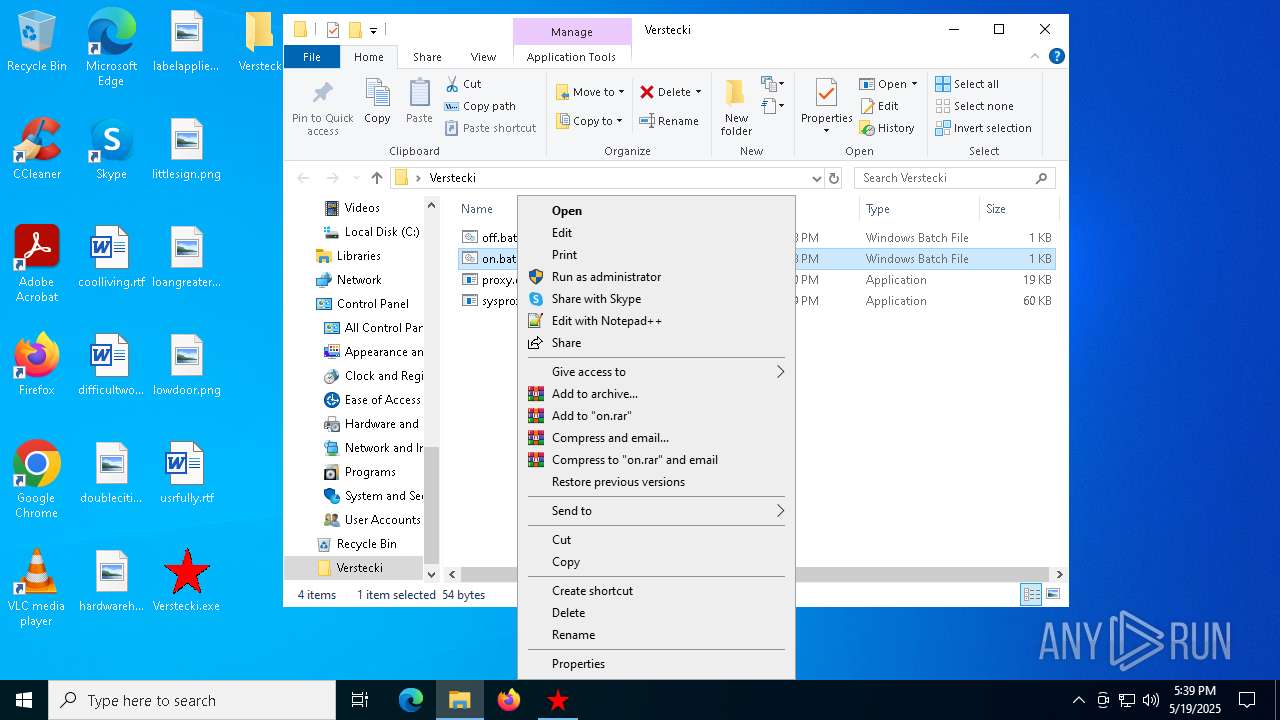
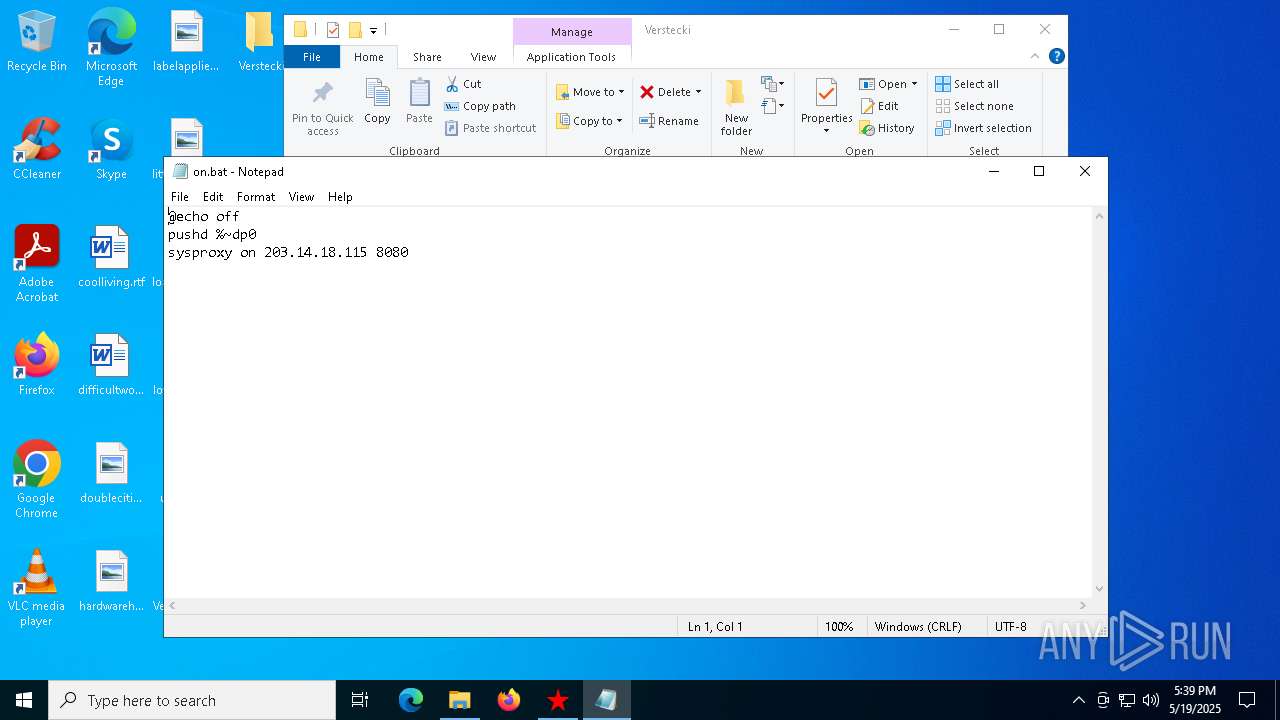
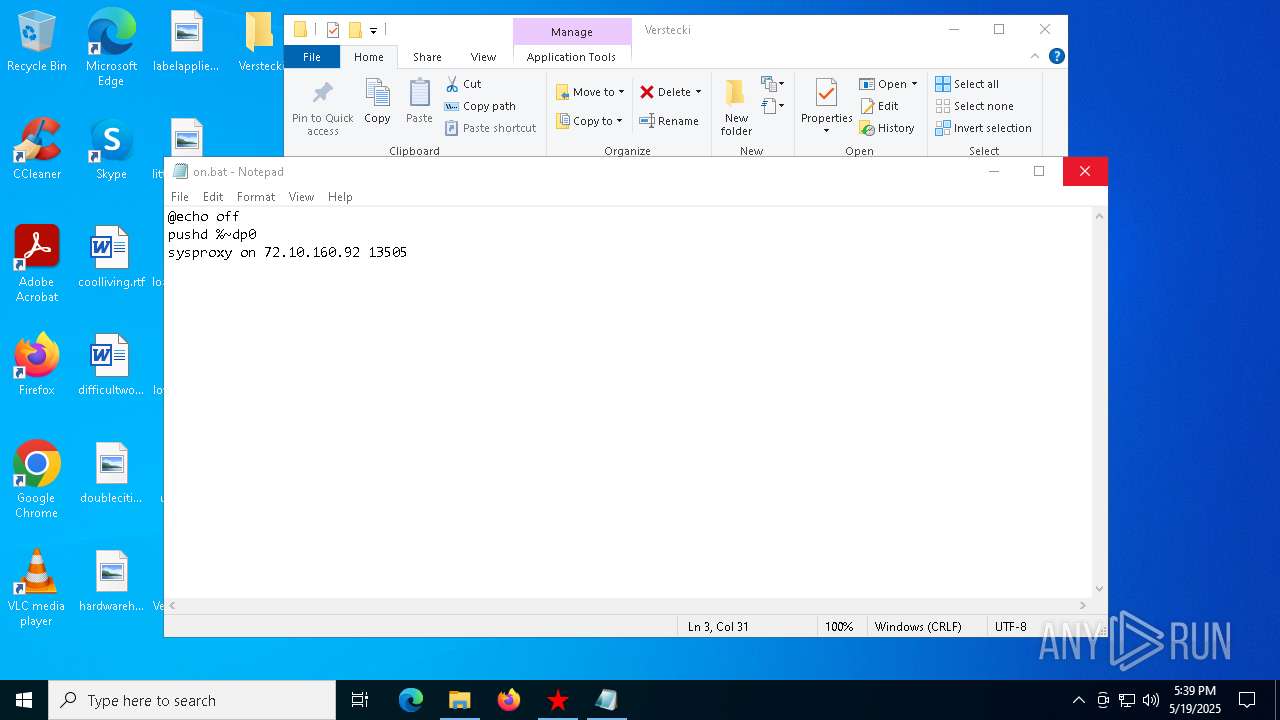
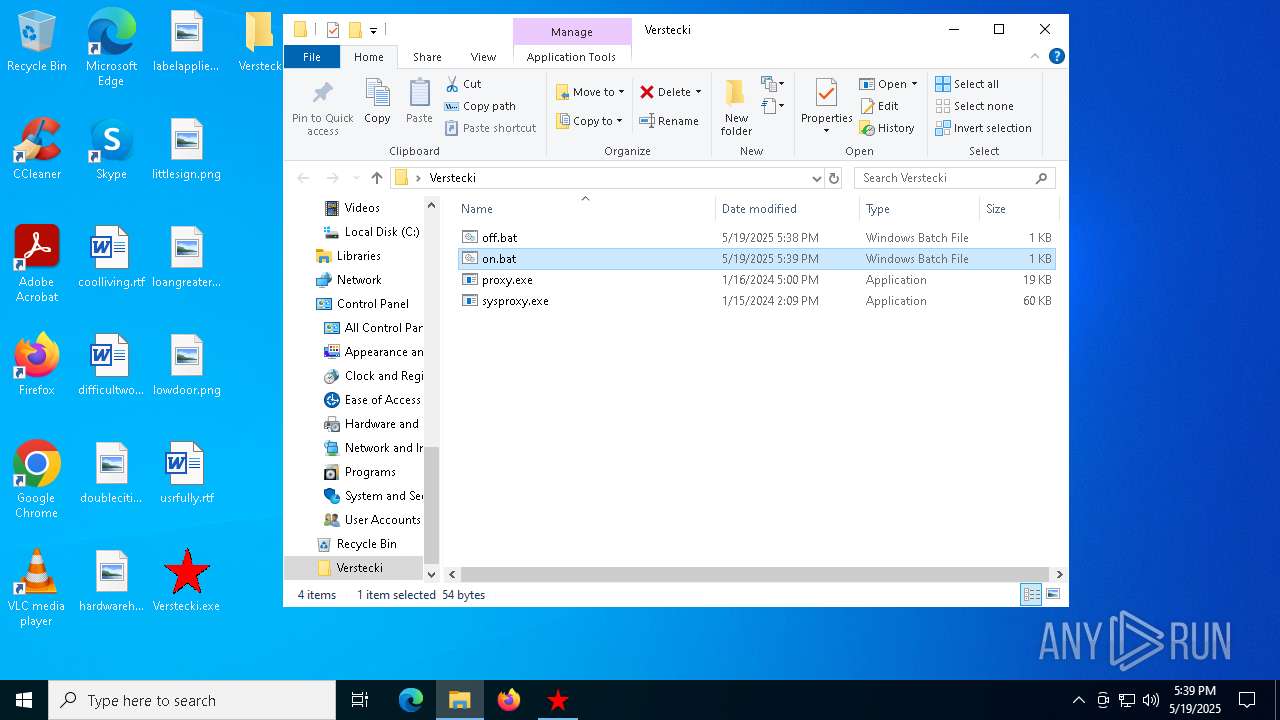
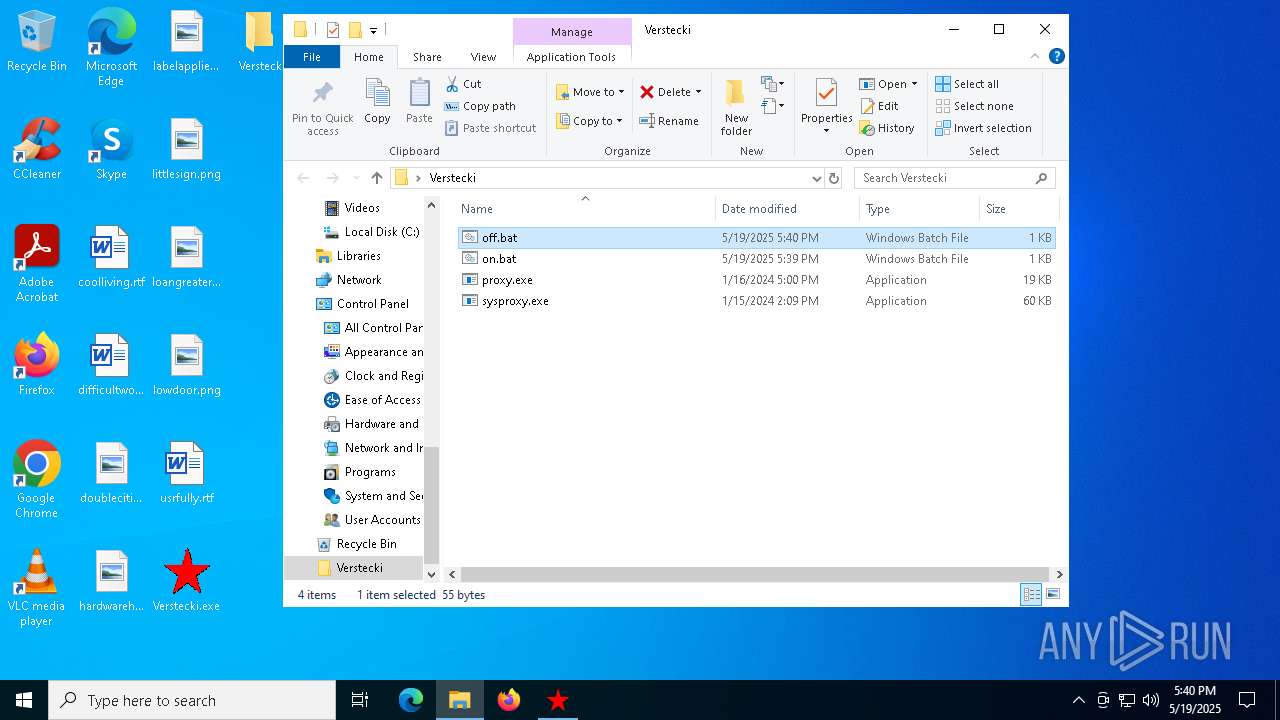
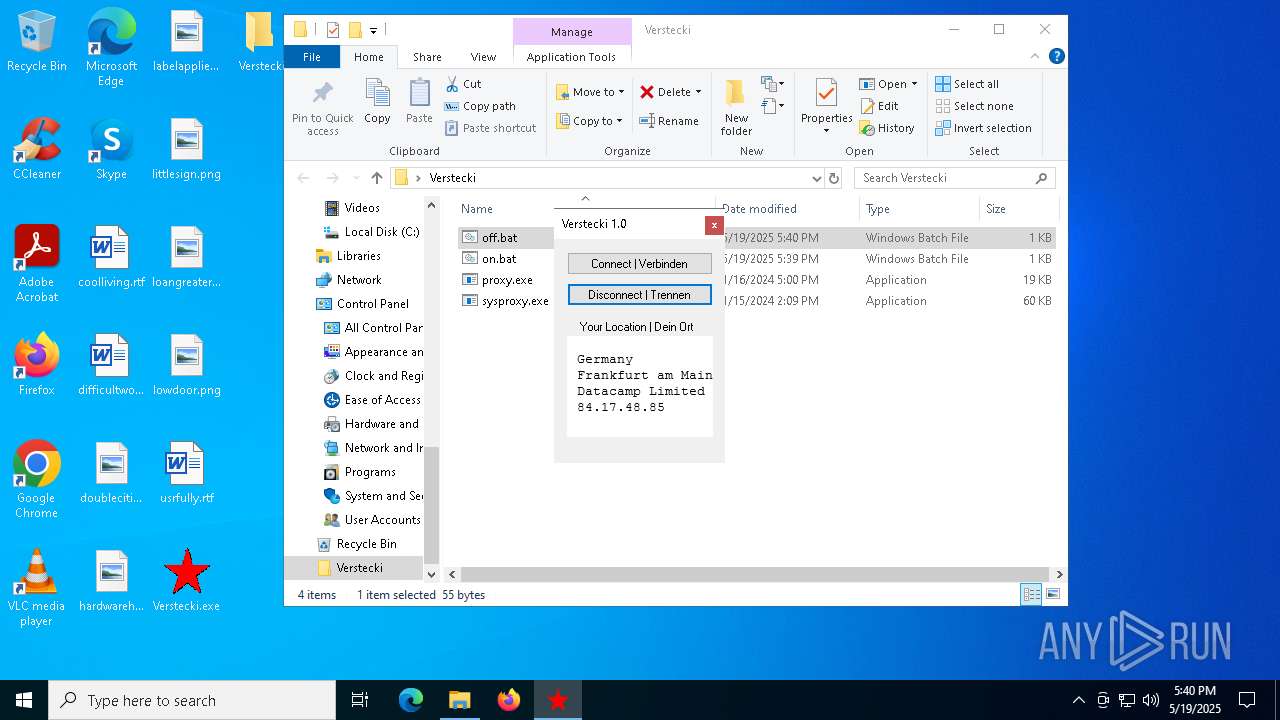
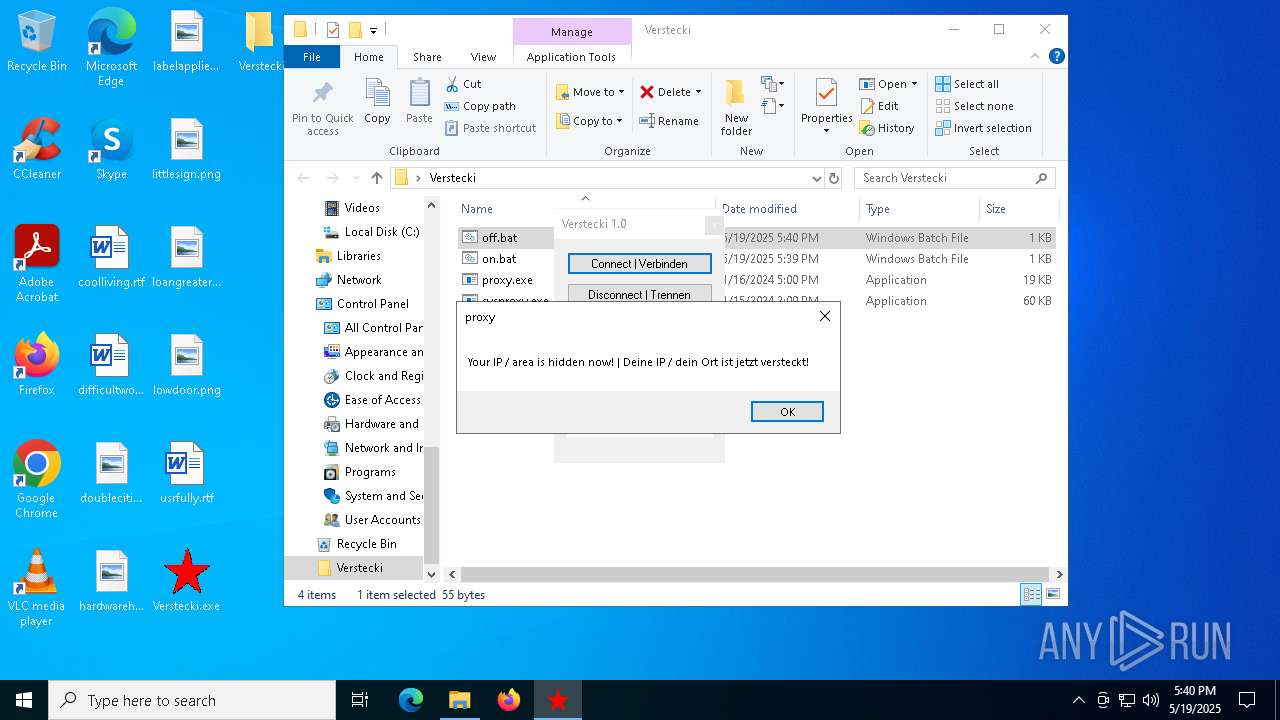
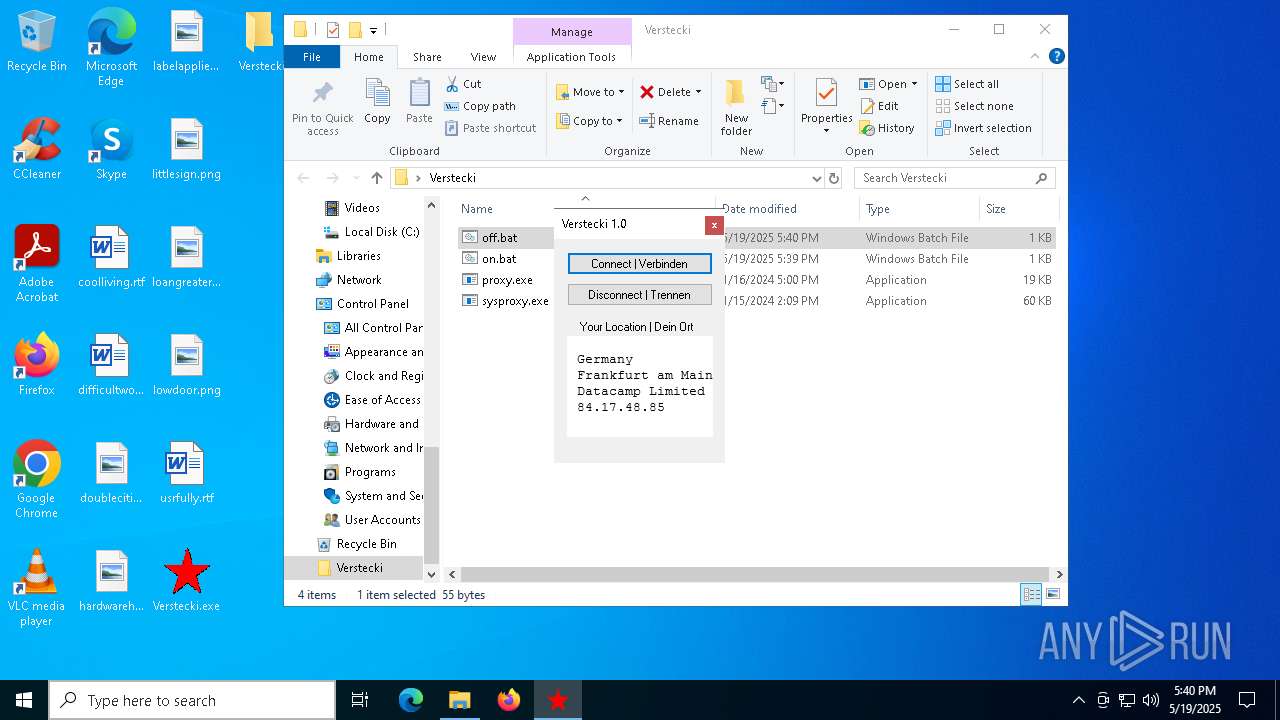
| File name: | Verstecki.exe |
| Full analysis: | https://app.any.run/tasks/3f024777-e717-49d7-ad36-e02f73fbd21c |
| Verdict: | Malicious activity |
| Analysis date: | May 19, 2025, 17:36:08 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 8C516CA608030E3E1D61375730B2AA99 |
| SHA1: | EE0DC02BCDD62F324AC14EB6F966BE17E0E5A203 |
| SHA256: | 1ACBE118B66EE76B74276EBA29BD044CE4F080F8D359E59D231E8DC3AACFFB2D |
| SSDEEP: | 12288:EjV8Uox9oUFydRxsQPyhv7qtoc3J851Jq//mq//06Kz6Ei:rAY5qtPJ85PnLPzDi |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- Verstecki.exe (PID: 6668)
Reads security settings of Internet Explorer
- Verstecki.exe (PID: 6668)
- proxy.exe (PID: 4424)
- proxy.exe (PID: 2552)
- sysproxy.exe (PID: 812)
- sysproxy.exe (PID: 5116)
- sysproxy.exe (PID: 5172)
- sysproxy.exe (PID: 5132)
- sysproxy.exe (PID: 5084)
Reads Microsoft Outlook installation path
- proxy.exe (PID: 4424)
- proxy.exe (PID: 2552)
Reads Internet Explorer settings
- proxy.exe (PID: 4424)
- proxy.exe (PID: 2552)
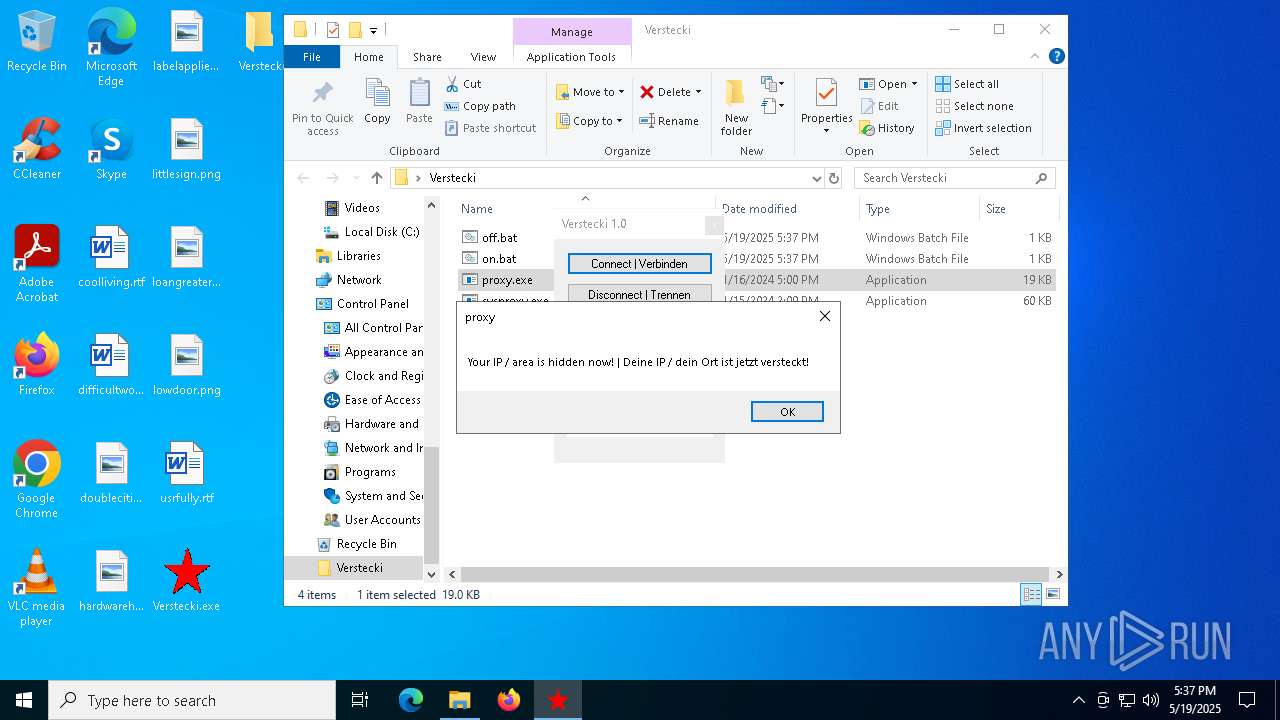
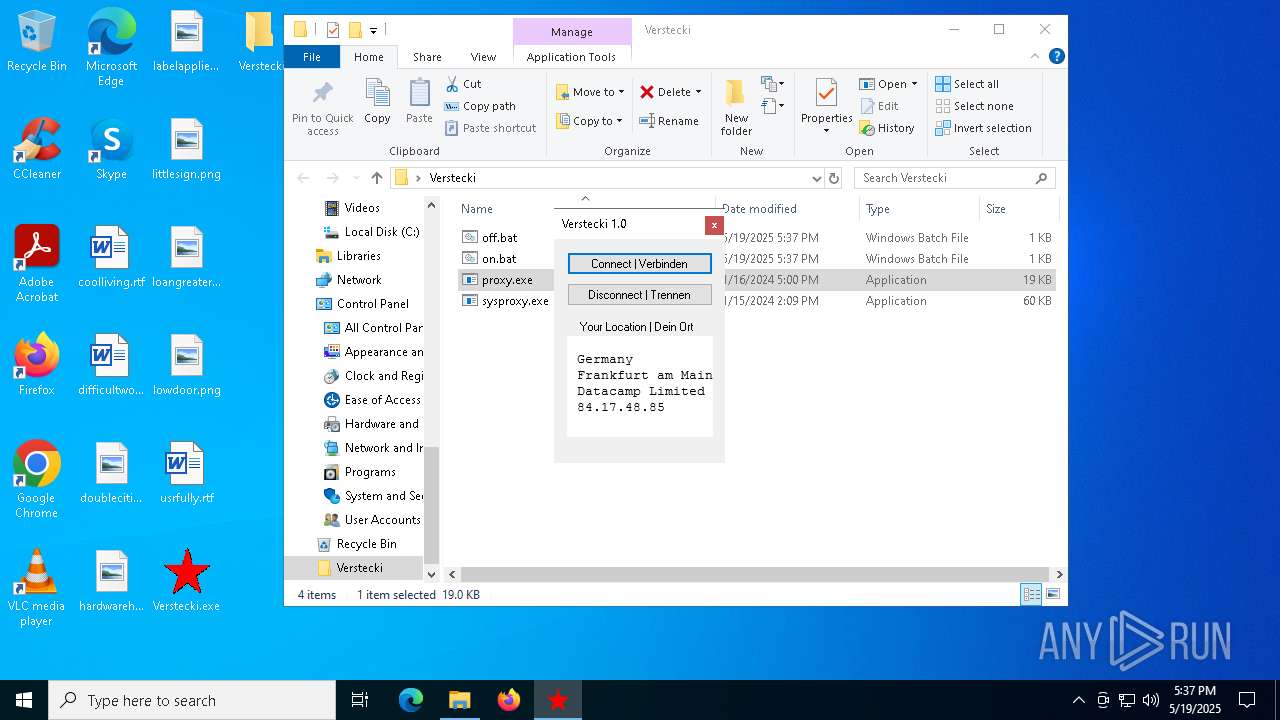
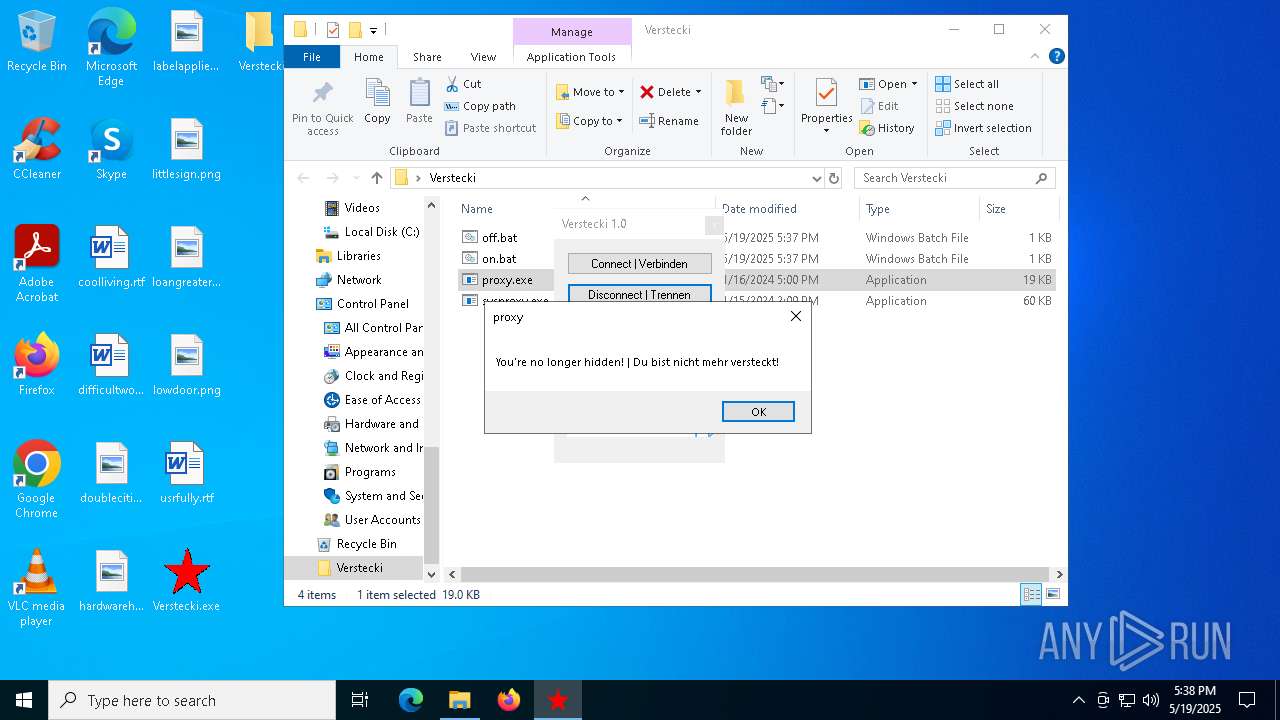
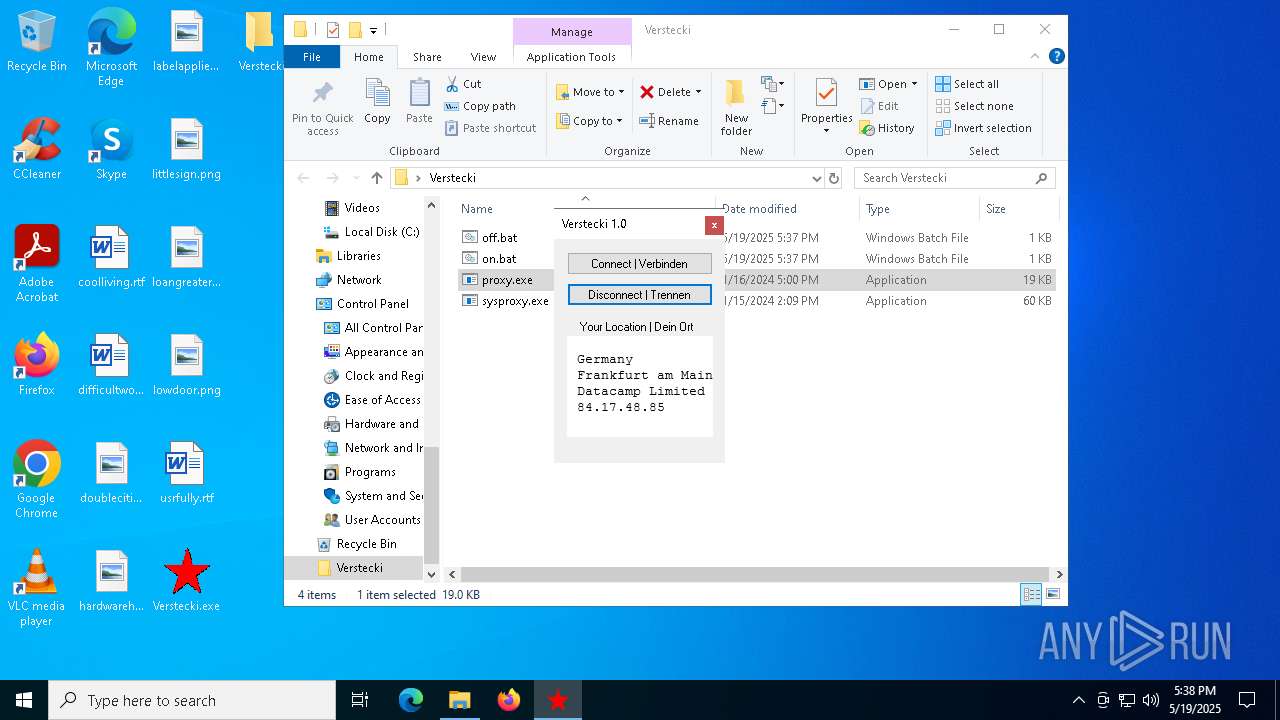
Checks for external IP
- proxy.exe (PID: 4424)
- svchost.exe (PID: 2196)
- proxy.exe (PID: 2552)
Connects to unusual port
- proxy.exe (PID: 2552)
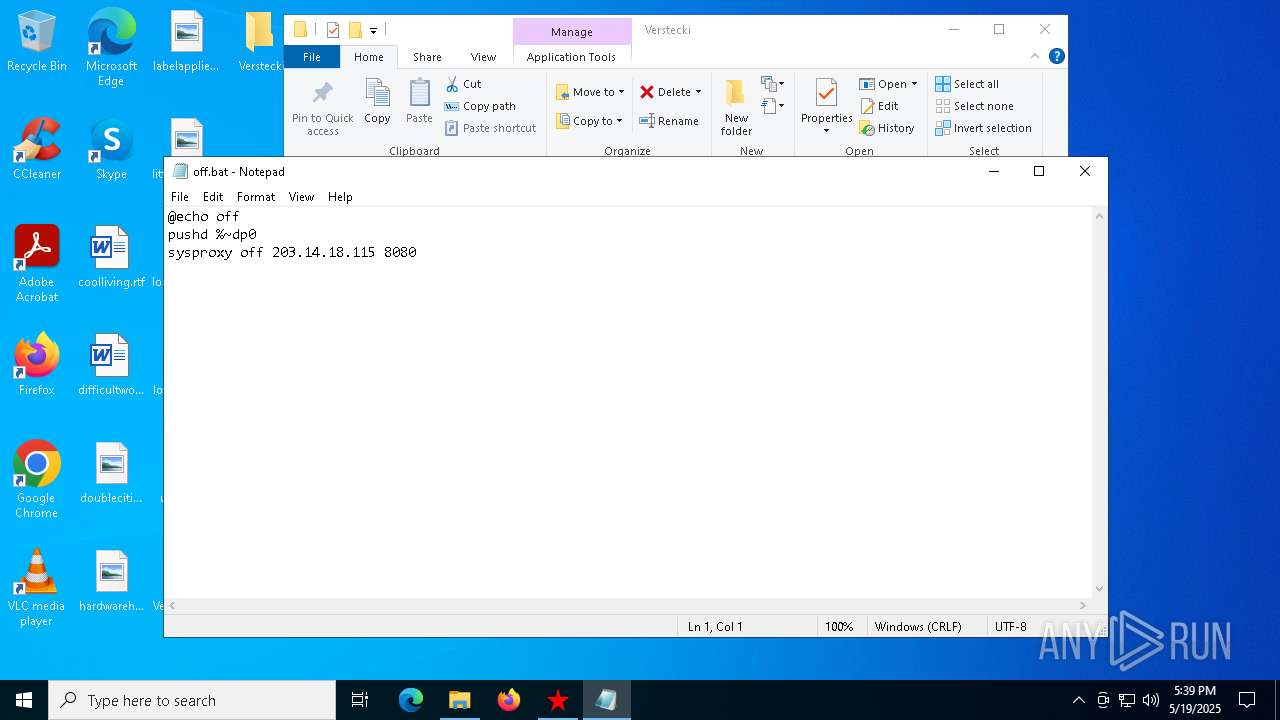
Starts CMD.EXE for commands execution
- proxy.exe (PID: 2552)
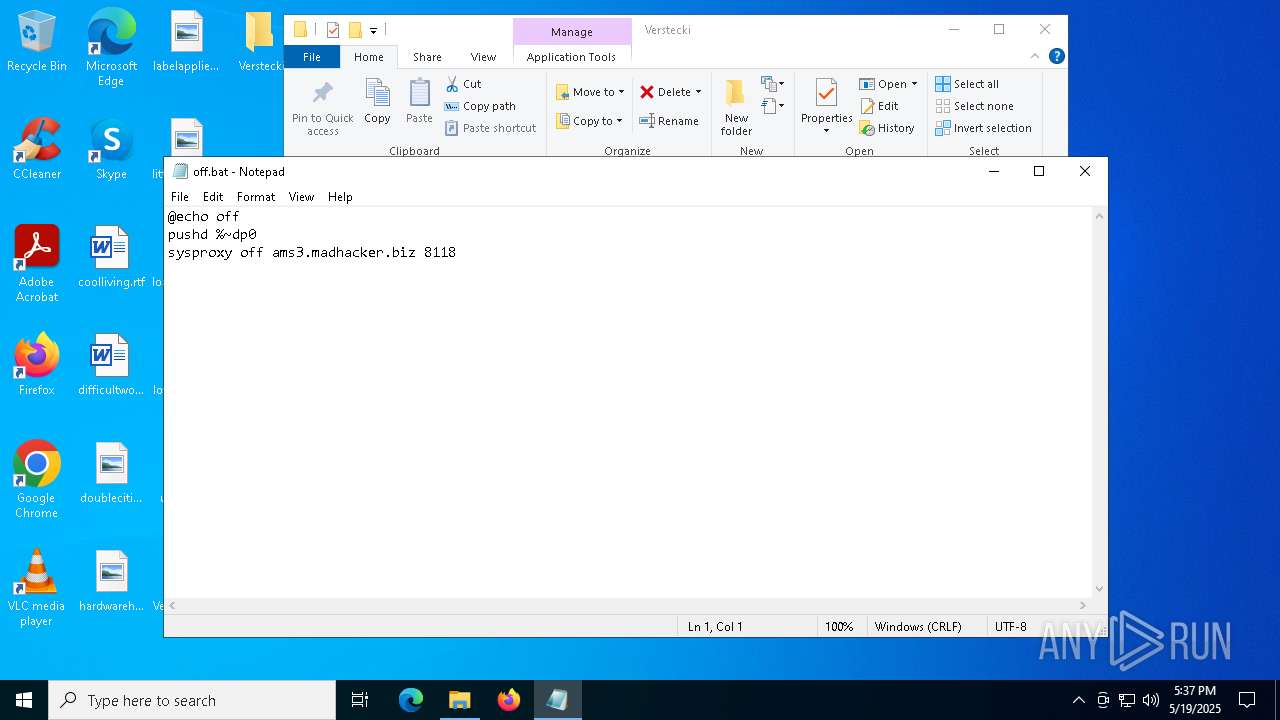
Executing commands from a ".bat" file
- proxy.exe (PID: 2552)
INFO
Reads the computer name
- Verstecki.exe (PID: 6668)
- proxy.exe (PID: 4424)
- proxy.exe (PID: 2552)
- sysproxy.exe (PID: 812)
- sysproxy.exe (PID: 5116)
- sysproxy.exe (PID: 5132)
- sysproxy.exe (PID: 5172)
- sysproxy.exe (PID: 5084)
Process checks computer location settings
- Verstecki.exe (PID: 6668)
- proxy.exe (PID: 2552)
Create files in a temporary directory
- Verstecki.exe (PID: 6668)
Checks supported languages
- proxy.exe (PID: 4424)
- Verstecki.exe (PID: 6668)
- proxy.exe (PID: 2552)
- sysproxy.exe (PID: 5116)
- sysproxy.exe (PID: 812)
- sysproxy.exe (PID: 5132)
- sysproxy.exe (PID: 5172)
- sysproxy.exe (PID: 5084)
Reads the machine GUID from the registry
- proxy.exe (PID: 4424)
- proxy.exe (PID: 2552)
Checks proxy server information
- proxy.exe (PID: 4424)
- proxy.exe (PID: 2552)
- sysproxy.exe (PID: 812)
- sysproxy.exe (PID: 5116)
- slui.exe (PID: 2420)
- sysproxy.exe (PID: 5132)
- sysproxy.exe (PID: 5172)
- sysproxy.exe (PID: 5084)
Creates files or folders in the user directory
- proxy.exe (PID: 4424)
- proxy.exe (PID: 2552)
Manual execution by a user
- notepad.exe (PID: 5384)
- proxy.exe (PID: 2552)
- WinRAR.exe (PID: 6540)
- notepad.exe (PID: 7152)
- notepad.exe (PID: 2320)
- notepad.exe (PID: 6072)
- notepad.exe (PID: 3796)
- notepad.exe (PID: 2064)
Reads security settings of Internet Explorer
- notepad.exe (PID: 5384)
- notepad.exe (PID: 7152)
- notepad.exe (PID: 6072)
- notepad.exe (PID: 3796)
- notepad.exe (PID: 2320)
- notepad.exe (PID: 2064)
Reads the software policy settings
- slui.exe (PID: 5972)
- slui.exe (PID: 2420)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6540)
Disables trace logs
- sysproxy.exe (PID: 812)
- sysproxy.exe (PID: 5116)
- sysproxy.exe (PID: 5132)
- sysproxy.exe (PID: 5172)
- sysproxy.exe (PID: 5084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:06:11 09:16:47+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 201728 |
| InitializedDataSize: | 79872 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1eef0 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
159
Monitored processes
30
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
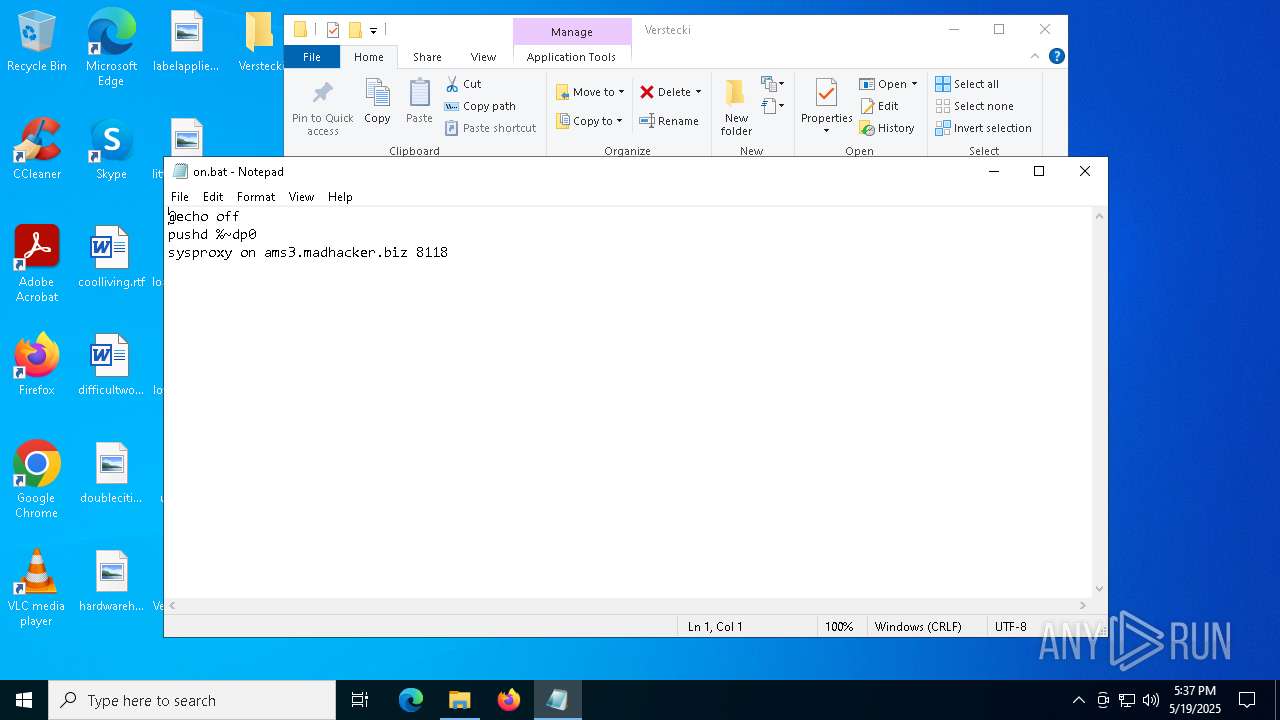
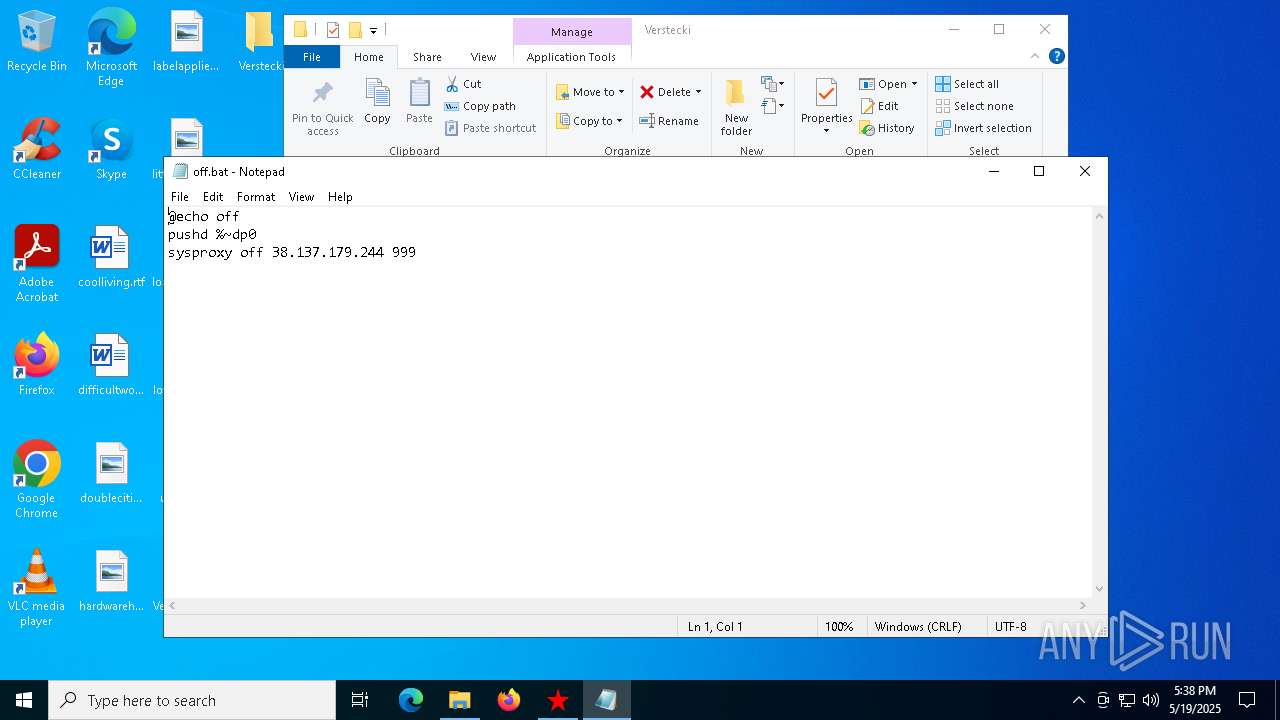
| 812 | sysproxy on 38.137.179.244 999 | C:\Users\admin\Desktop\Verstecki\sysproxy.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 900 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2064 | "C:\WINDOWS\System32\NOTEPAD.EXE" C:\Users\admin\Desktop\Verstecki\on.bat | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\Verstecki\off.bat" " | C:\Windows\SysWOW64\cmd.exe | — | proxy.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2320 | "C:\WINDOWS\System32\NOTEPAD.EXE" C:\Users\admin\Desktop\Verstecki\off.bat | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2420 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
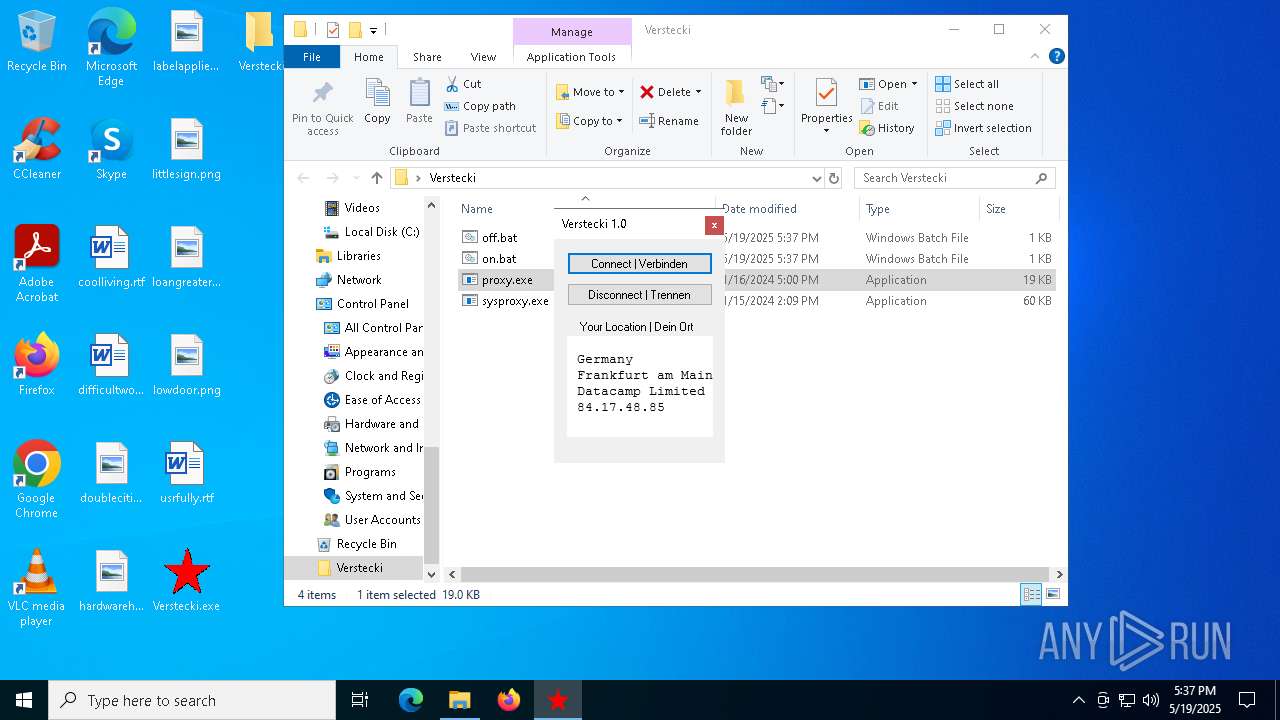
| 2552 | "C:\Users\admin\Desktop\Verstecki\proxy.exe" | C:\Users\admin\Desktop\Verstecki\proxy.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: proxy Version: 1.0.0.0 Modules
| |||||||||||||||
| 3180 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\Verstecki\off.bat" " | C:\Windows\SysWOW64\cmd.exe | — | proxy.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3796 | "C:\WINDOWS\System32\NOTEPAD.EXE" C:\Users\admin\Desktop\Verstecki\off.bat | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 154
Read events
7 124
Write events
28
Delete events
2
Modification events
| (PID) Process: | (4424) proxy.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4424) proxy.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4424) proxy.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4424) proxy.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main\WindowsSearch |
| Operation: | write | Name: | Version |
Value: WS not running | |||
| (PID) Process: | (4424) proxy.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | DisableFirstRunCustomize |
Value: 1 | |||
| (PID) Process: | (4424) proxy.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFavoritesInitialSelection |
Value: | |||
| (PID) Process: | (4424) proxy.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFeedsInitialSelection |
Value: | |||
| (PID) Process: | (6540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
4
Suspicious files
0
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
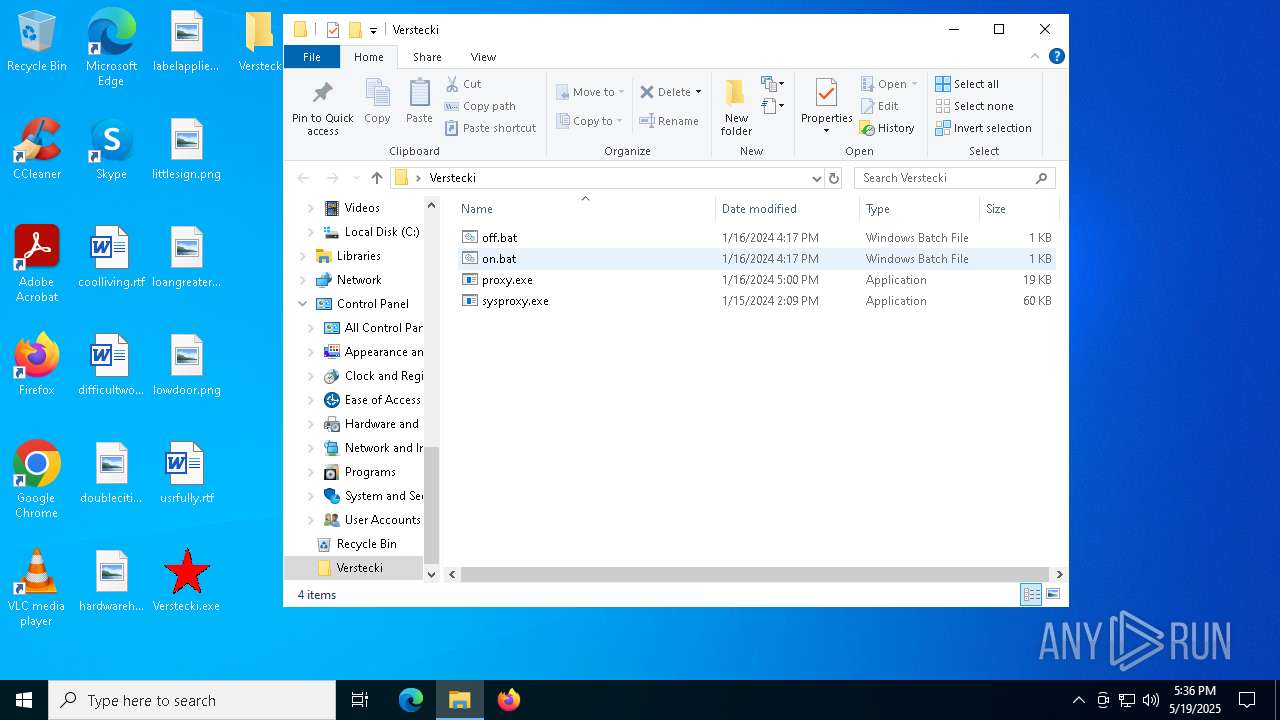
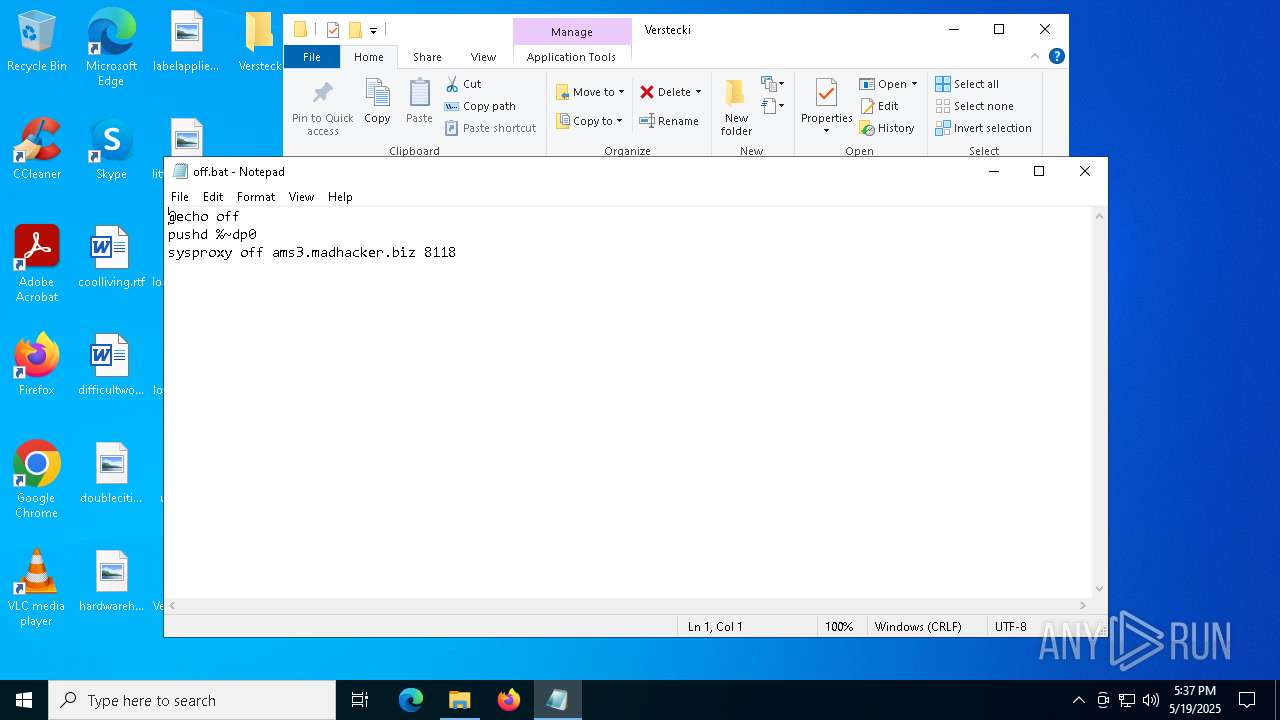
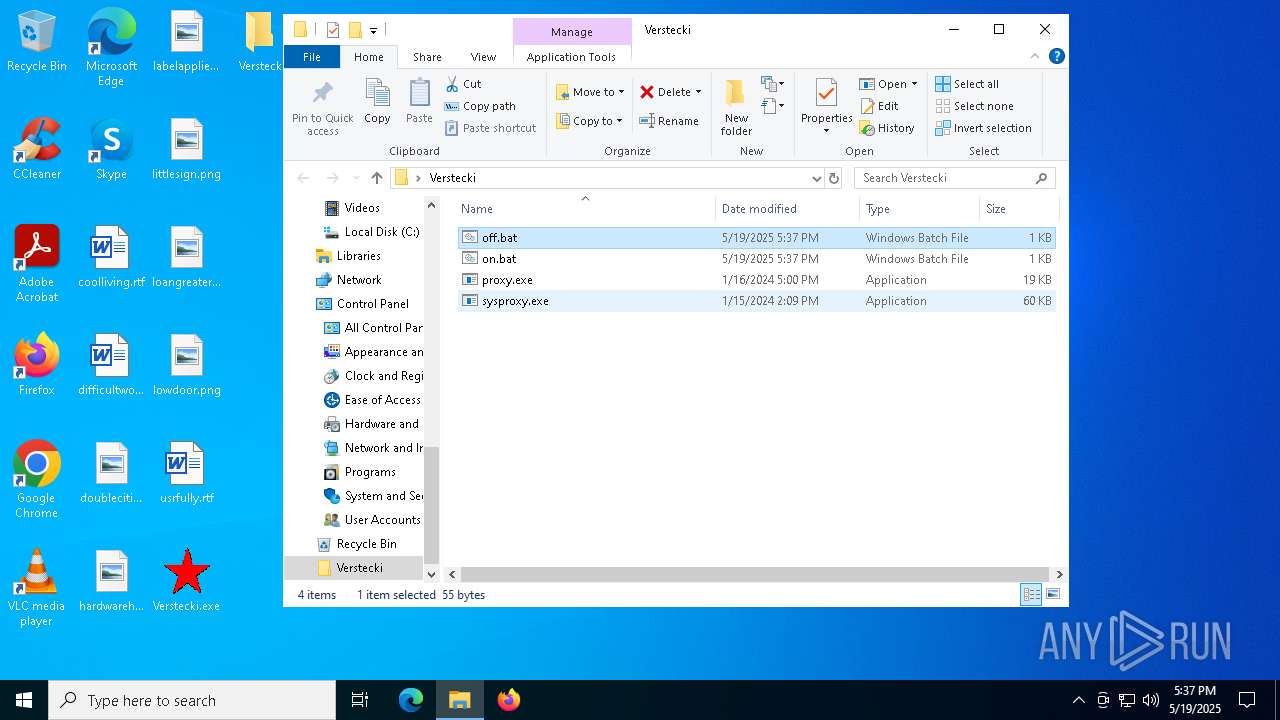
| 6668 | Verstecki.exe | C:\Users\admin\AppData\Local\Temp\Verstecki\off.bat | text | |
MD5:D6A72512B7299CD617C46921DE2E3E57 | SHA256:839B3CC35C26B6BD03A15A1CB9DCD663CF18E40408233270F609C87DB40A1BB4 | |||
| 6668 | Verstecki.exe | C:\Users\admin\AppData\Local\Temp\Verstecki\sysproxy.exe | executable | |
MD5:380D58A33FAF71547FB97C3FC12A38A9 | SHA256:A918AA182DD57A545B0416E406432A6D09D1232AA0C33A0969DCD39A432D0D6B | |||
| 6668 | Verstecki.exe | C:\Users\admin\AppData\Local\Temp\Verstecki\proxy.exe | executable | |
MD5:E54AE14A6A56FD181A3D46CAC0FFEAF6 | SHA256:0A758D1B371979D5B53DC9A5D566F756BB52BC7B4AAD22A851CEE11AC2DCC906 | |||
| 2552 | proxy.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\line[1].txt | text | |
MD5:A39AAE7B7D3FEBB7A7454F93AE1C3702 | SHA256:14C5EE1E0802556D3D1C4BE8E60C9AF27624561F5B5461E21C2D66D52D445510 | |||
| 6540 | WinRAR.exe | C:\Users\admin\Desktop\Verstecki\sysproxy.exe | executable | |
MD5:380D58A33FAF71547FB97C3FC12A38A9 | SHA256:A918AA182DD57A545B0416E406432A6D09D1232AA0C33A0969DCD39A432D0D6B | |||
| 2552 | proxy.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\line[2].txt | text | |
MD5:A39AAE7B7D3FEBB7A7454F93AE1C3702 | SHA256:14C5EE1E0802556D3D1C4BE8E60C9AF27624561F5B5461E21C2D66D52D445510 | |||
| 2552 | proxy.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\line[1].txt | text | |
MD5:A39AAE7B7D3FEBB7A7454F93AE1C3702 | SHA256:14C5EE1E0802556D3D1C4BE8E60C9AF27624561F5B5461E21C2D66D52D445510 | |||
| 6668 | Verstecki.exe | C:\Users\admin\AppData\Local\Temp\Verstecki\on.bat | text | |
MD5:829C4553AC0215C7CC76BB5FA9C01B26 | SHA256:7E225A2D5C51769C400CCD13B75F01C675317CE560F662699121D60160E5A110 | |||
| 6540 | WinRAR.exe | C:\Users\admin\Desktop\Verstecki\off.bat | text | |
MD5:D6A72512B7299CD617C46921DE2E3E57 | SHA256:839B3CC35C26B6BD03A15A1CB9DCD663CF18E40408233270F609C87DB40A1BB4 | |||
| 6540 | WinRAR.exe | C:\Users\admin\Desktop\Verstecki\on.bat | text | |
MD5:829C4553AC0215C7CC76BB5FA9C01B26 | SHA256:7E225A2D5C51769C400CCD13B75F01C675317CE560F662699121D60160E5A110 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
47
DNS requests
19
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.22:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4424 | proxy.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=8721 | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5376 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5376 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2552 | proxy.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=8721 | unknown | — | — | whitelisted |
2552 | proxy.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=8721 | unknown | — | — | whitelisted |
2552 | proxy.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=8721 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.22:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4424 | proxy.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ip-api.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
4424 | proxy.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2552 | proxy.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
2552 | proxy.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
2552 | proxy.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |