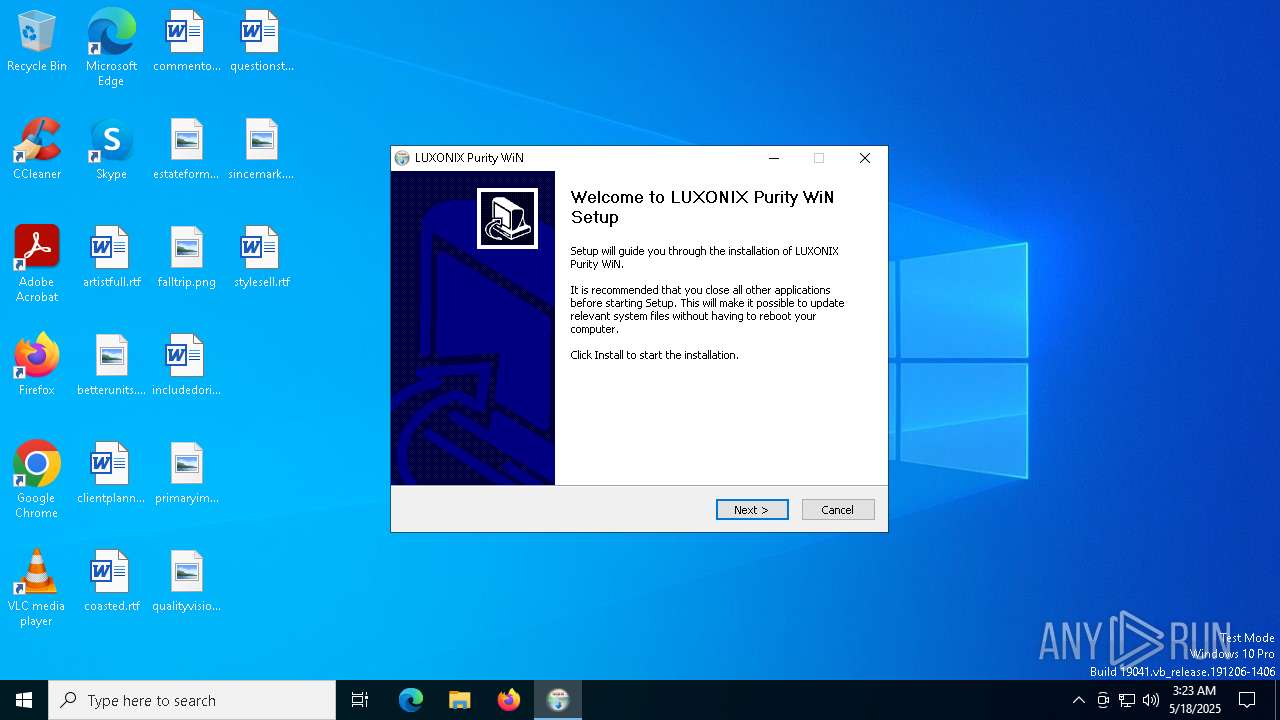
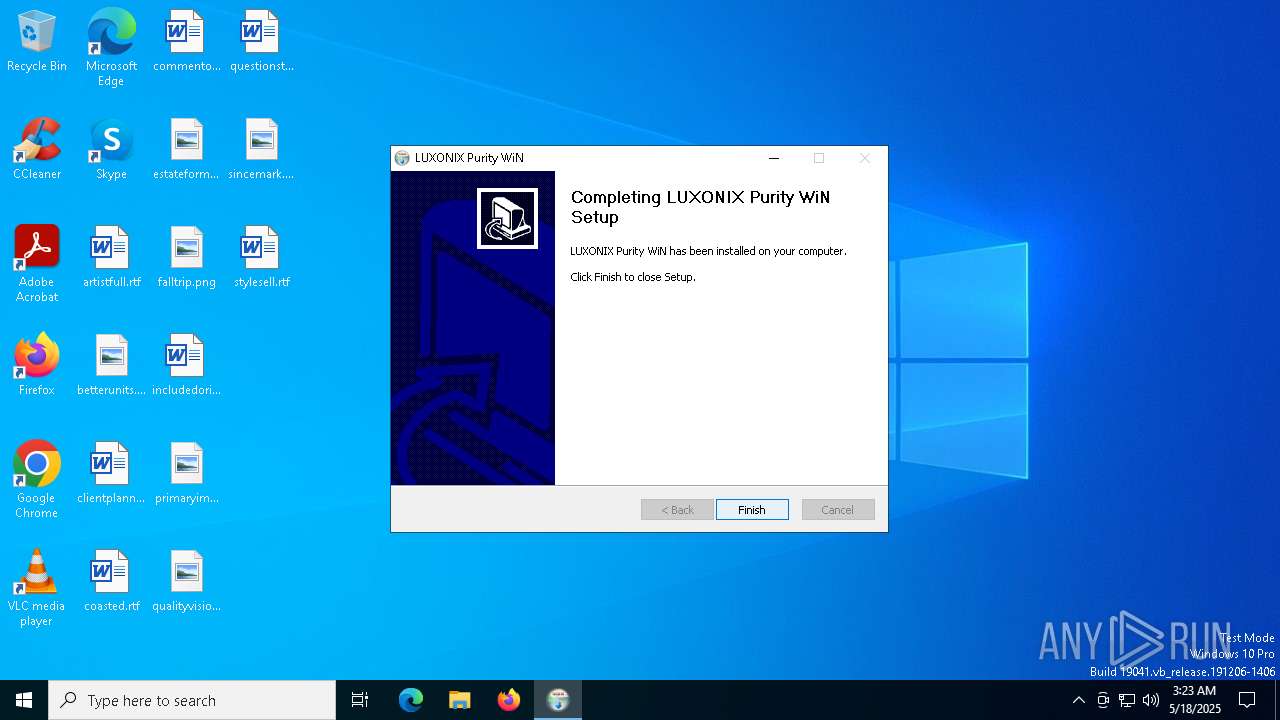
| File name: | LUXONIX Purity WiN.exe |
| Full analysis: | https://app.any.run/tasks/402fe1bd-e1b6-4224-be50-030bae3a025e |
| Verdict: | Malicious activity |
| Analysis date: | May 18, 2025, 03:23:16 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 9999D9C44547B31DBCD11F05022FA405 |
| SHA1: | D8F2EFED8C060B073C7A1FCA8707F90C6F0BA7D7 |
| SHA256: | 1ABE0D79D9B70043163C873024977DB0737B9582EC39891EB08B91A54D94082E |
| SSDEEP: | 1536:Pi37Ij8pGMuNpTUfzM74mVvtfsOBu8M0is+Fx3piW51ocj:WIYpGMuNpT+M7VVvtESZMQcx3pD5+4 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- LUXONIX Purity WiN.exe (PID: 7552)
Executable content was dropped or overwritten
- LUXONIX Purity WiN.exe (PID: 7552)
Reads security settings of Internet Explorer
- LUXONIX Purity WiN.exe (PID: 7552)
The process creates files with name similar to system file names
- LUXONIX Purity WiN.exe (PID: 7552)
INFO
Checks supported languages
- LUXONIX Purity WiN.exe (PID: 7552)
Reads the computer name
- LUXONIX Purity WiN.exe (PID: 7552)
The sample compiled with english language support
- LUXONIX Purity WiN.exe (PID: 7552)
Checks proxy server information
- LUXONIX Purity WiN.exe (PID: 7552)
Create files in a temporary directory
- LUXONIX Purity WiN.exe (PID: 7552)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:07:02 02:09:43+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 139776 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x3645 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
132
Monitored processes
6
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4932 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7468 | "C:\Users\admin\AppData\Local\Temp\LUXONIX Purity WiN.exe" | C:\Users\admin\AppData\Local\Temp\LUXONIX Purity WiN.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 7552 | "C:\Users\admin\AppData\Local\Temp\LUXONIX Purity WiN.exe" | C:\Users\admin\AppData\Local\Temp\LUXONIX Purity WiN.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 7612 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7644 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
749
Read events
746
Write events
3
Delete events
0
Modification events
| (PID) Process: | (7552) LUXONIX Purity WiN.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7552) LUXONIX Purity WiN.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7552) LUXONIX Purity WiN.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
3
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7552 | LUXONIX Purity WiN.exe | C:\Users\admin\AppData\Local\Temp\nsbB961.tmp\System.dll | executable | |
MD5:4ADD245D4BA34B04F213409BFE504C07 | SHA256:9111099EFE9D5C9B391DC132B2FAF0A3851A760D4106D5368E30AC744EB42706 | |||
| 7552 | LUXONIX Purity WiN.exe | C:\Users\admin\AppData\Local\Temp\nsbB961.tmp\nsDialogs.dll | executable | |
MD5:1D8F01A83DDD259BC339902C1D33C8F1 | SHA256:4B7D17DA290F41EBE244827CC295CE7E580DA2F7E9F7CC3EFC1ABC6898E3C9ED | |||
| 7552 | LUXONIX Purity WiN.exe | C:\Users\admin\AppData\Local\Temp\nsqB921.tmp | binary | |
MD5:60348A7665ADA781E211C1EEFD65F5C7 | SHA256:E349BC478DB240C0B9664ED4A4BB9DF7D4581490528FBC7F8D0260909C340C0B | |||
| 7552 | LUXONIX Purity WiN.exe | C:\Users\admin\AppData\Local\Temp\nsbB961.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
| 7552 | LUXONIX Purity WiN.exe | C:\Users\admin\AppData\Local\Temp\nsbB961.tmp\INetC.dll | executable | |
MD5:40D7ECA32B2F4D29DB98715DD45BFAC5 | SHA256:85E03805F90F72257DD41BFDAA186237218BBB0EC410AD3B6576A88EA11DCCB9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
22
DNS requests
16
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7552 | LUXONIX Purity WiN.exe | GET | 404 | 188.114.96.3:80 | http://truckobservation.icu/aar.php?pe=n&p=3942&t=53256548&title=TFVYT05JWCBQdXJpdHkgV2lO&sub= | unknown | — | — | unknown |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7552 | LUXONIX Purity WiN.exe | GET | 404 | 104.21.29.130:80 | http://shadeinsect.icu/aars.php?pe=n&p=3942&t=53256548&title=TFVYT05JWCBQdXJpdHkgV2lO&sub= | unknown | — | — | unknown |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6516 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6516 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7552 | LUXONIX Purity WiN.exe | 188.114.96.3:80 | truckobservation.icu | CLOUDFLARENET | NL | unknown |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7552 | LUXONIX Purity WiN.exe | 104.21.29.130:80 | shadeinsect.icu | CLOUDFLARENET | — | unknown |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
truckobservation.icu |
| unknown |
shadeinsect.icu |
| unknown |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .icu Domain |
7552 | LUXONIX Purity WiN.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
7552 | LUXONIX Purity WiN.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |