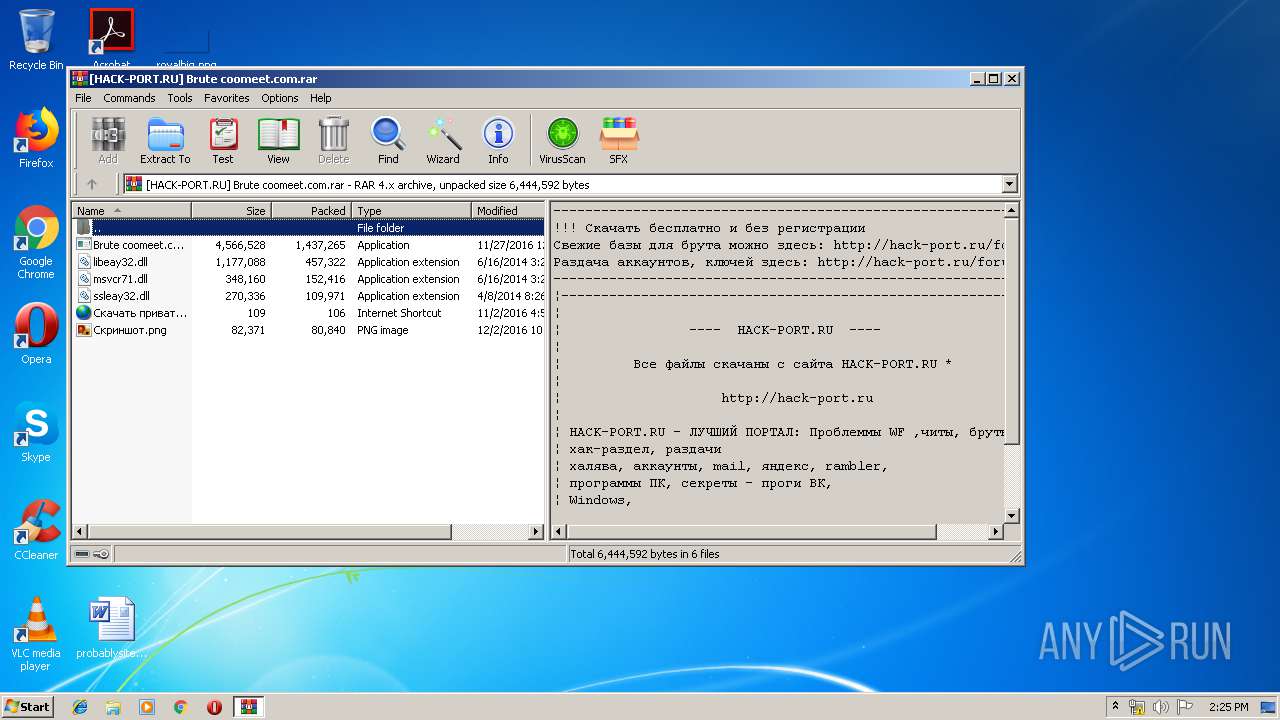
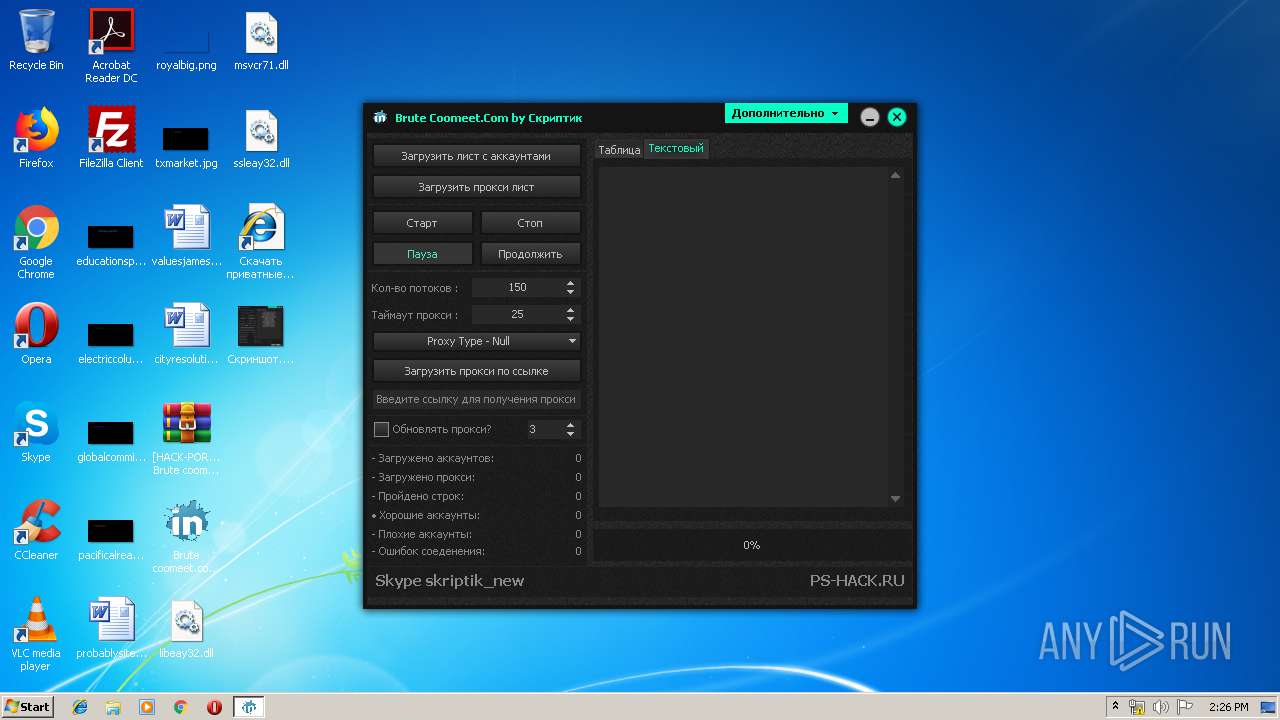
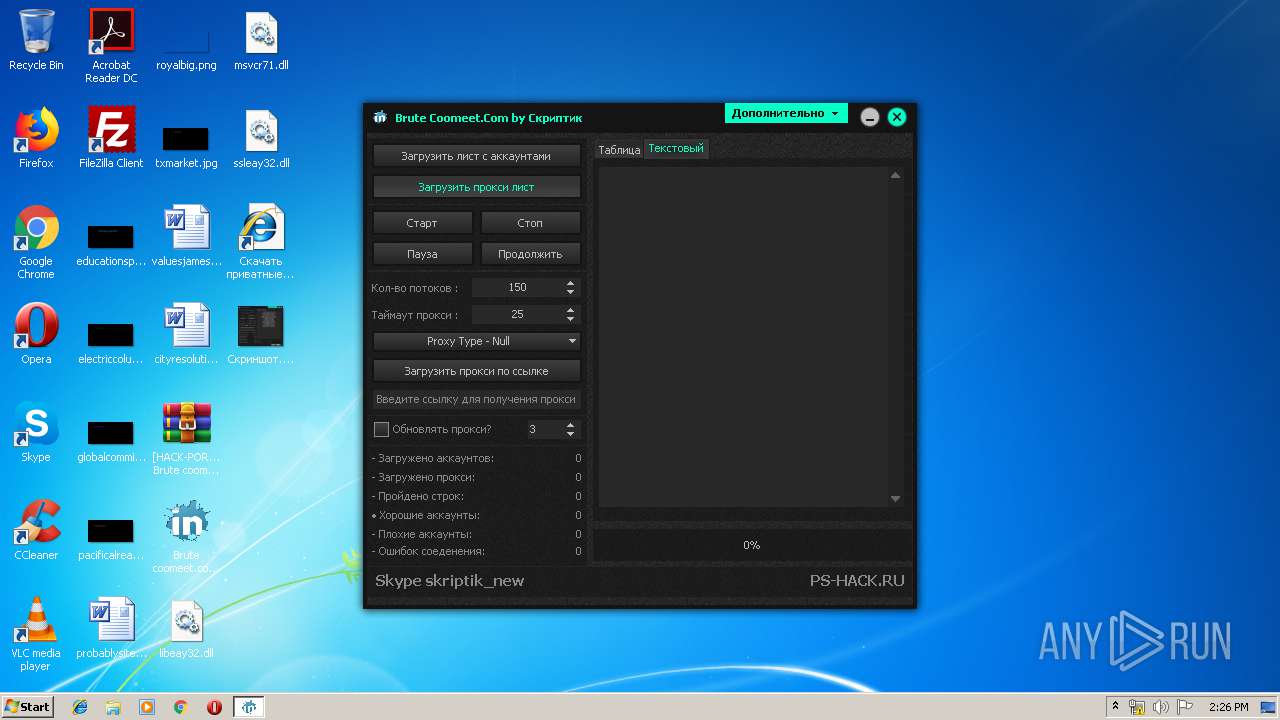
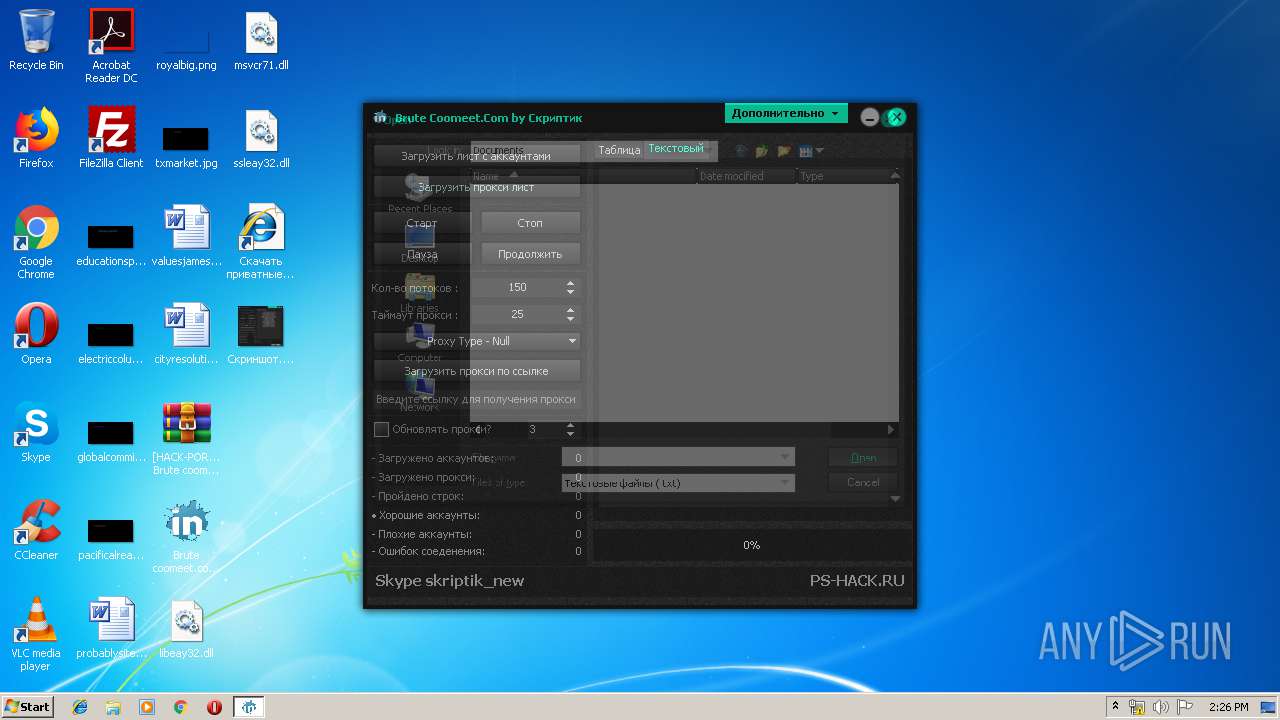
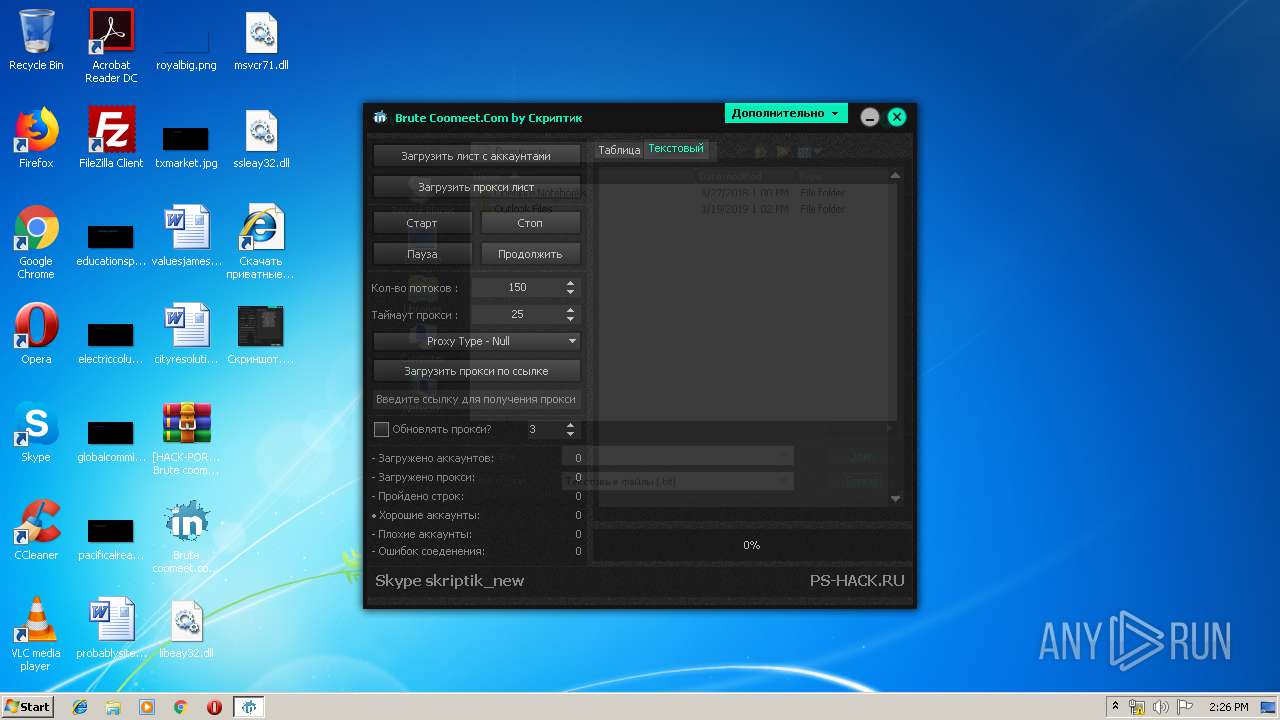
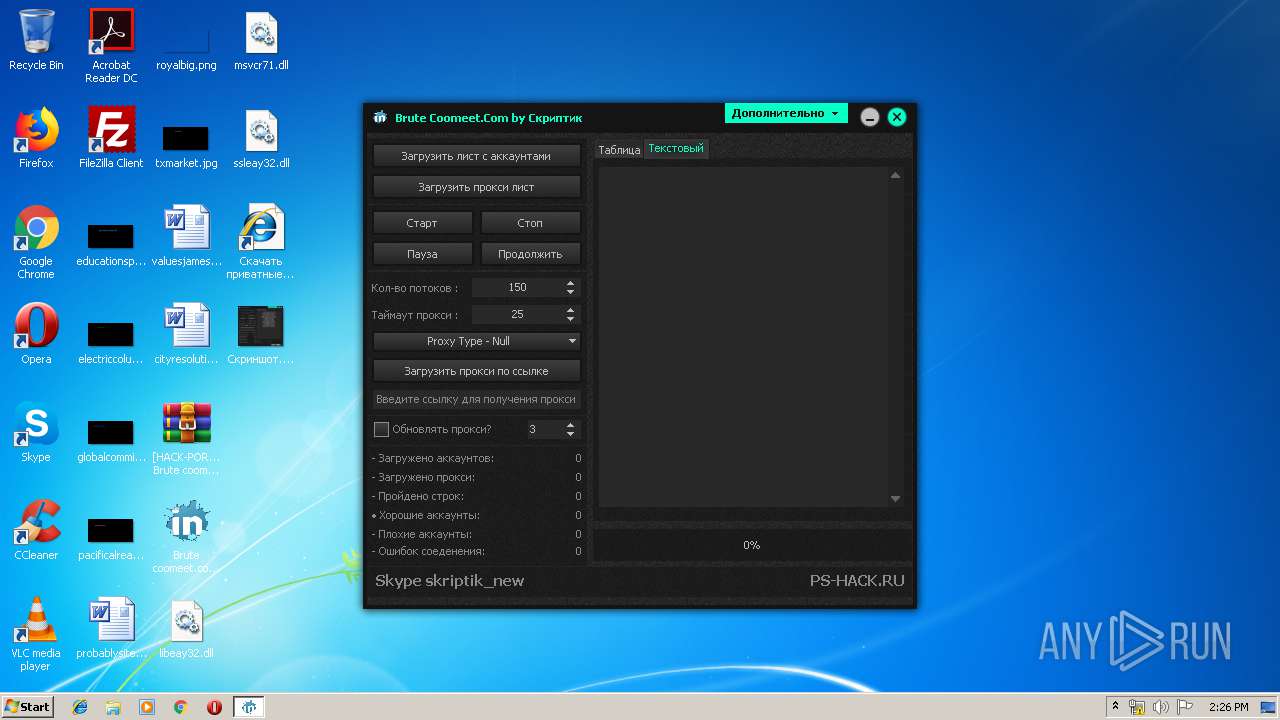
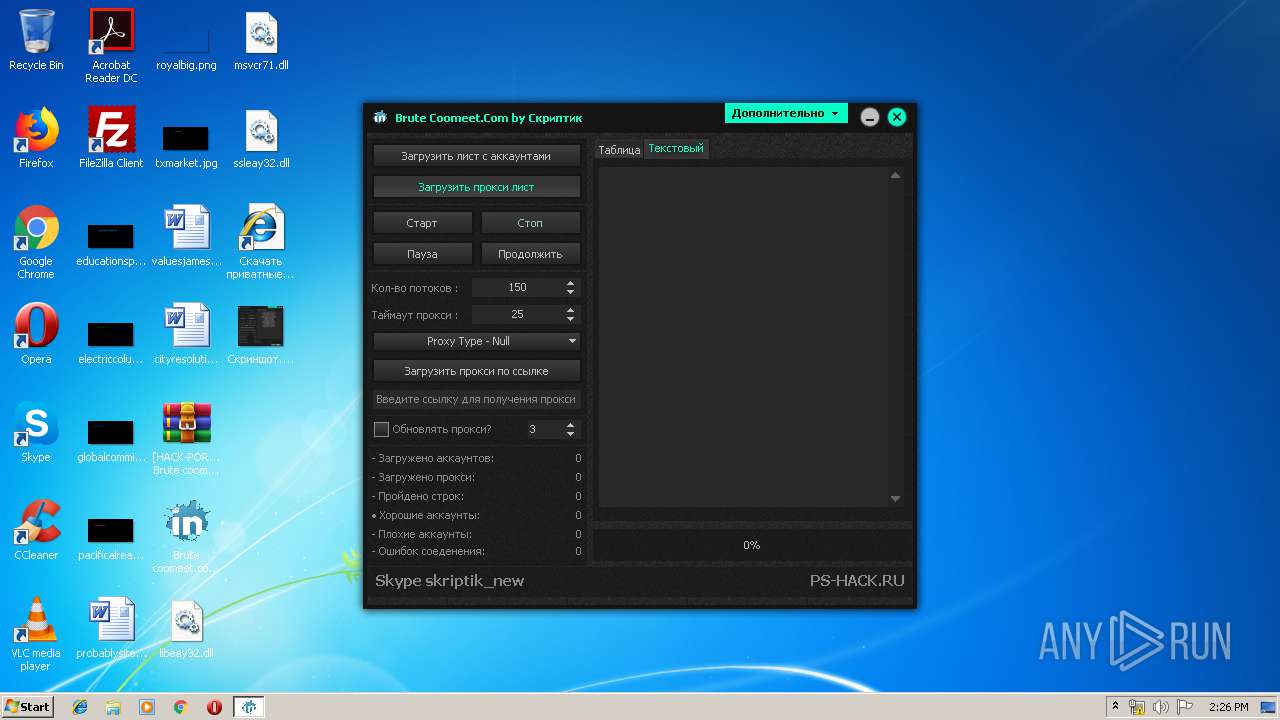
| File name: | [HACK-PORT.RU] Brute coomeet.com.rar |
| Full analysis: | https://app.any.run/tasks/3ae2efe4-f0cc-4f05-82a5-78fef659b454 |
| Verdict: | Malicious activity |
| Analysis date: | April 12, 2019, 13:25:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32, flags: Locked RecoveryRecordPresent |
| MD5: | 2C4AD63FE263A1D9F6C97117DC7438E6 |
| SHA1: | A30E0AE196CAA592B21947CE7C900E9D3F6A7DDA |
| SHA256: | 1AA89B2A533B2CD36C95458B086A0A9EB495CF654535BDC1274B6ACC4DBC8D96 |
| SSDEEP: | 49152:mLG2YyZB/Of0GK3IA5cqwCxp6DcJ3eI6nCiPPK6DJvRy/cpLO5Ihi:LMZVGFzdGQ2R6JBDJvs/cuIhi |
MALICIOUS
Loads dropped or rewritten executable
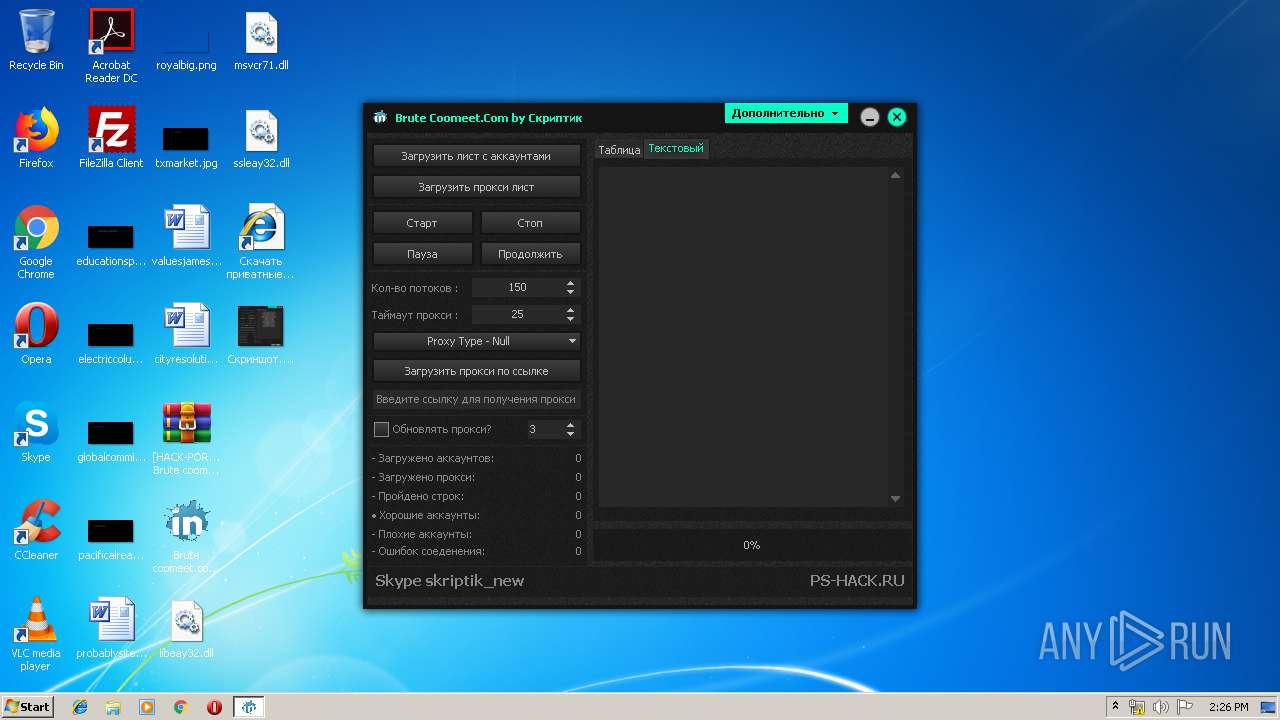
- Brute coomeet.com by Скриптик.exe (PID: 3604)
- SearchProtocolHost.exe (PID: 2584)
- Brute coomeet.com by Скриптик.exe (PID: 2036)
- WerFault.exe (PID: 692)
- WerFault.exe (PID: 1524)
Application was dropped or rewritten from another process
- Brute coomeet.com by Скриптик.exe (PID: 3604)
- Brute coomeet.com by Скриптик.exe (PID: 2036)
SUSPICIOUS
Reads Internet Cache Settings
- Brute coomeet.com by Скриптик.exe (PID: 3604)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3364)
INFO
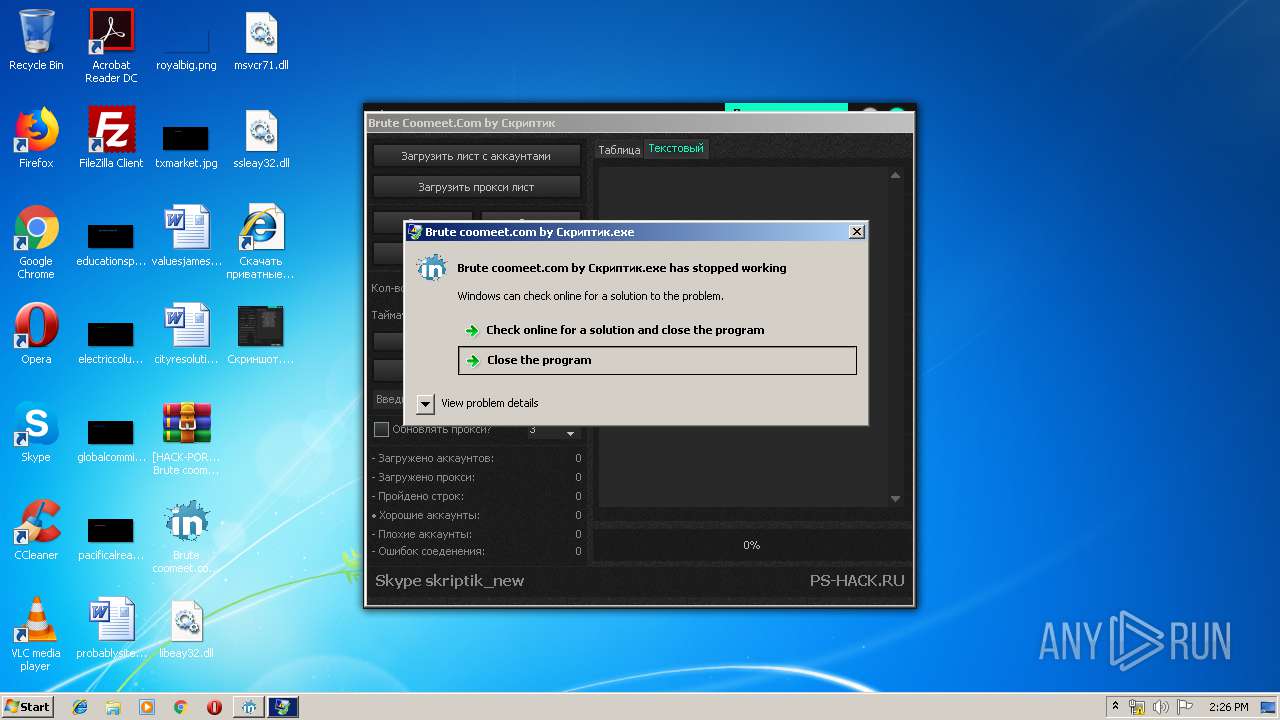
Application was crashed
- Brute coomeet.com by Скриптик.exe (PID: 3604)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 457360 |
|---|---|
| UncompressedSize: | 1177088 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2014:06:16 03:23:23 |
| PackingMethod: | Normal |
| ArchivedFileName: | libeay32.dll |
Total processes
43
Monitored processes
6
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 692 | C:\Windows\system32\WerFault.exe -u -p 3604 -s 692 | C:\Windows\system32\WerFault.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1524 | C:\Windows\system32\WerFault.exe -u -p 3604 -s 696 | C:\Windows\system32\WerFault.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2036 | "C:\Users\admin\Desktop\Brute coomeet.com by Скриптик.exe" | C:\Users\admin\Desktop\Brute coomeet.com by Скриптик.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2584 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3364 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\[HACK-PORT.RU] Brute coomeet.com.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3604 | "C:\Users\admin\Desktop\Brute coomeet.com by Скриптик.exe" | C:\Users\admin\Desktop\Brute coomeet.com by Скриптик.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
1 255
Read events
1 137
Write events
113
Delete events
5
Modification events
| (PID) Process: | (3364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3364) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\[HACK-PORT.RU] Brute coomeet.com.rar | |||
| (PID) Process: | (3364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3364) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\ieframe.dll,-10046 |
Value: Internet Shortcut | |||
| (PID) Process: | (3364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
Executable files
4
Suspicious files
2
Text files
2
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1524 | WerFault.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportArchive\AppCrash_Brute coomeet.co_2f41ad62419e89dd2a4a73c69f6afc17ee03bd5_05fb0bbe\Report.wer | binary | |
MD5:— | SHA256:— | |||
| 692 | WerFault.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportArchive\AppCrash_Brute coomeet.co_73c09b748d50f6126a217fa2dd6badecde1d8_02bb1350\Report.wer | binary | |
MD5:— | SHA256:— | |||
| 692 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\Brute coomeet.com by Скриптик.exe(1).3604.dmp | dmp | |
MD5:— | SHA256:— | |||
| 1524 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\Brute coomeet.com by Скриптик.exe.3604.dmp | dmp | |
MD5:— | SHA256:— | |||
| 3364 | WinRAR.exe | C:\Users\admin\Desktop\Скриншот.png | image | |
MD5:667B7D22DD1F81E60377889D893EAE4F | SHA256:CC3E5396C3A7F49C794BF3696586B6A42B2D37CE8857392D74052C01CCA7B69C | |||
| 3364 | WinRAR.exe | C:\Users\admin\Desktop\Brute coomeet.com by Скриптик.exe | executable | |
MD5:1FE6BDF036D0BD6ED5CBDBD0B8266F55 | SHA256:4C77869995527AD7F6322110D89A9E3C3096D2C702E9C4683FF1027318F14129 | |||
| 3364 | WinRAR.exe | C:\Users\admin\Desktop\libeay32.dll | executable | |
MD5:F361DF56A4D349DCE764BD1A51AEAD84 | SHA256:6731B8DEF903B56DC51DFDD24EF7550965E68B1D6547F379EE561E16EFAB1BA3 | |||
| 3364 | WinRAR.exe | C:\Users\admin\Desktop\Скачать приватные программы, постоянные раздачи, море халявы HACK-PORT.RU.url | text | |
MD5:B688C5423ACA0384835A9A2DE41AFCC4 | SHA256:EA28E210C4C8A42DFABFE1F6C17C1AA81C238ACAA620773EDF9FB9024FCFA378 | |||
| 3364 | WinRAR.exe | C:\Users\admin\Desktop\ssleay32.dll | executable | |
MD5:E0CD0800A00D51025968D778D0E6B2B3 | SHA256:B4434B408409D36D8E0D0BCF41AD804D02FDEE96BC7F8255105380BFCEC0D1F5 | |||
| 3364 | WinRAR.exe | C:\Users\admin\Desktop\msvcr71.dll | executable | |
MD5:5D70D744B237A3A1F57C475600764C3E | SHA256:525B896A6DE9D1C400A61D09CBD1248376F64559DA5EF22380600EFEFDD06078 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report