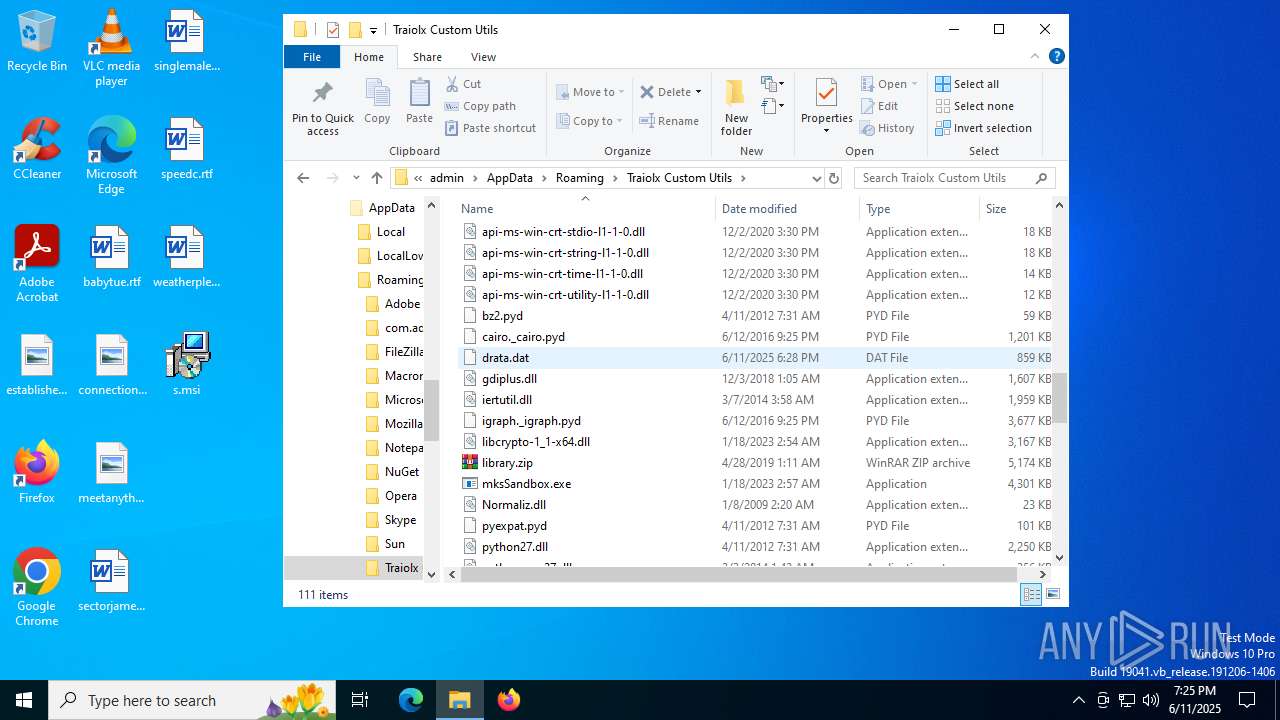
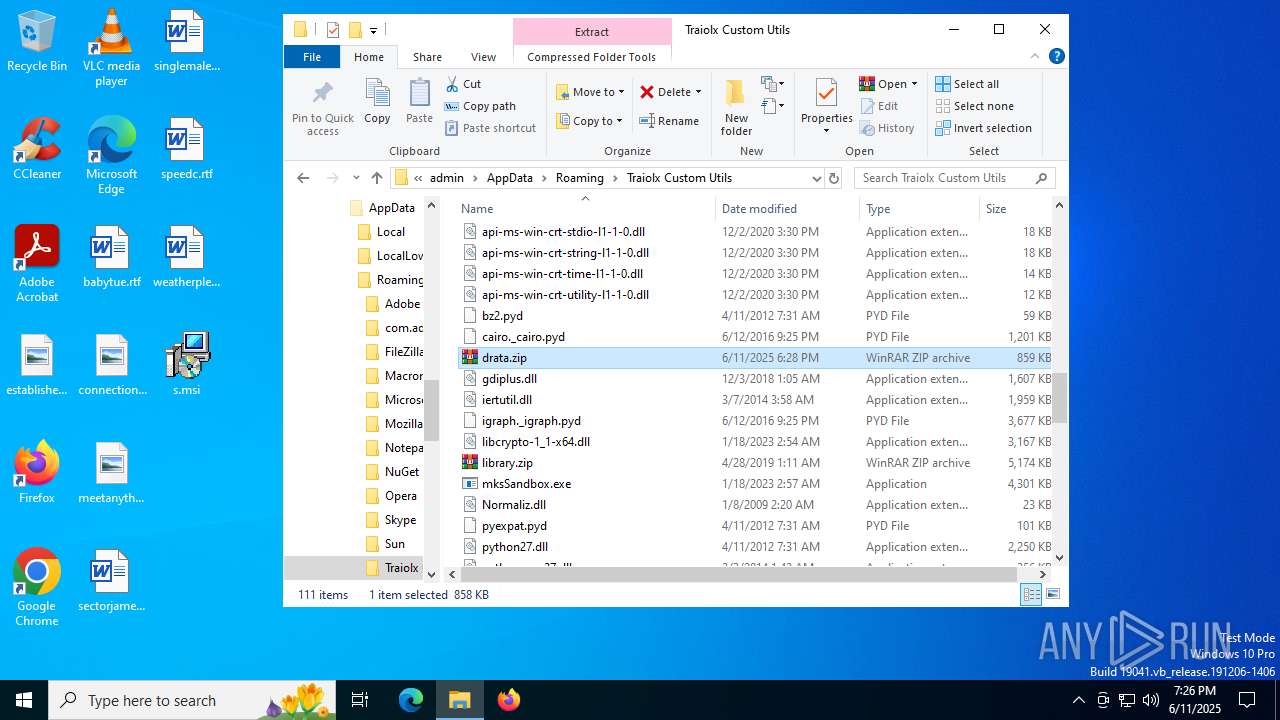
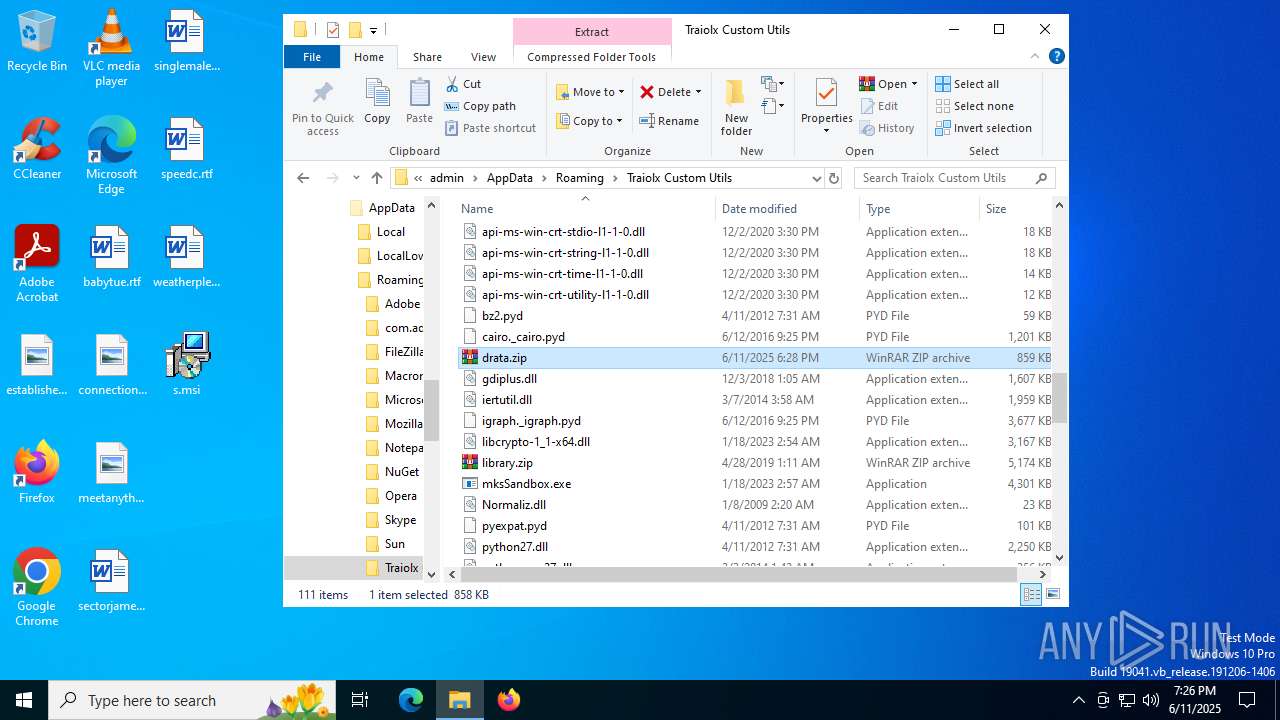
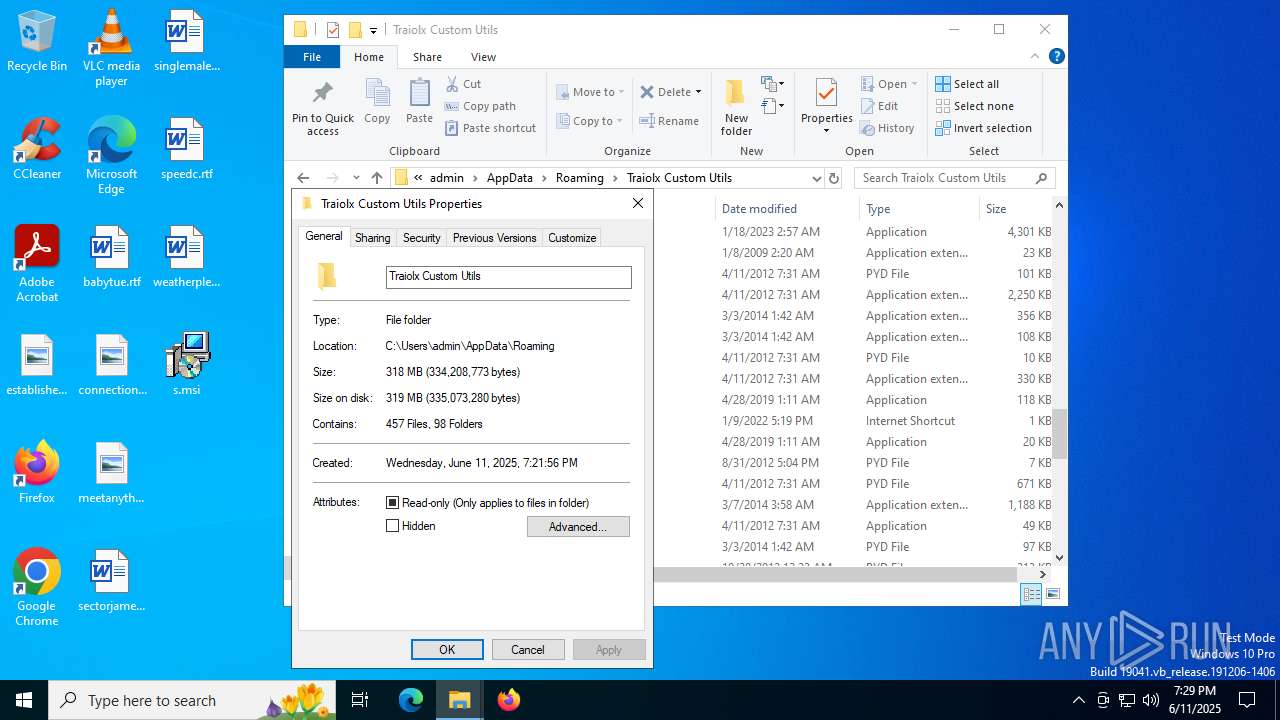
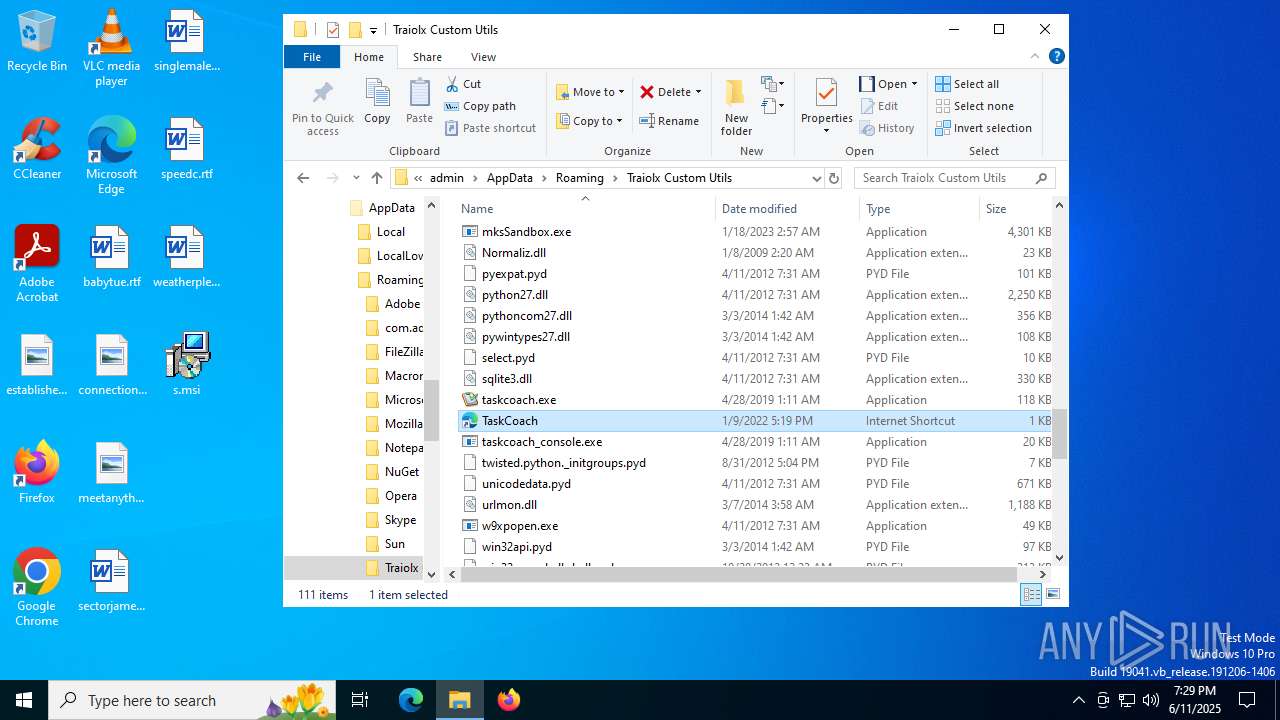
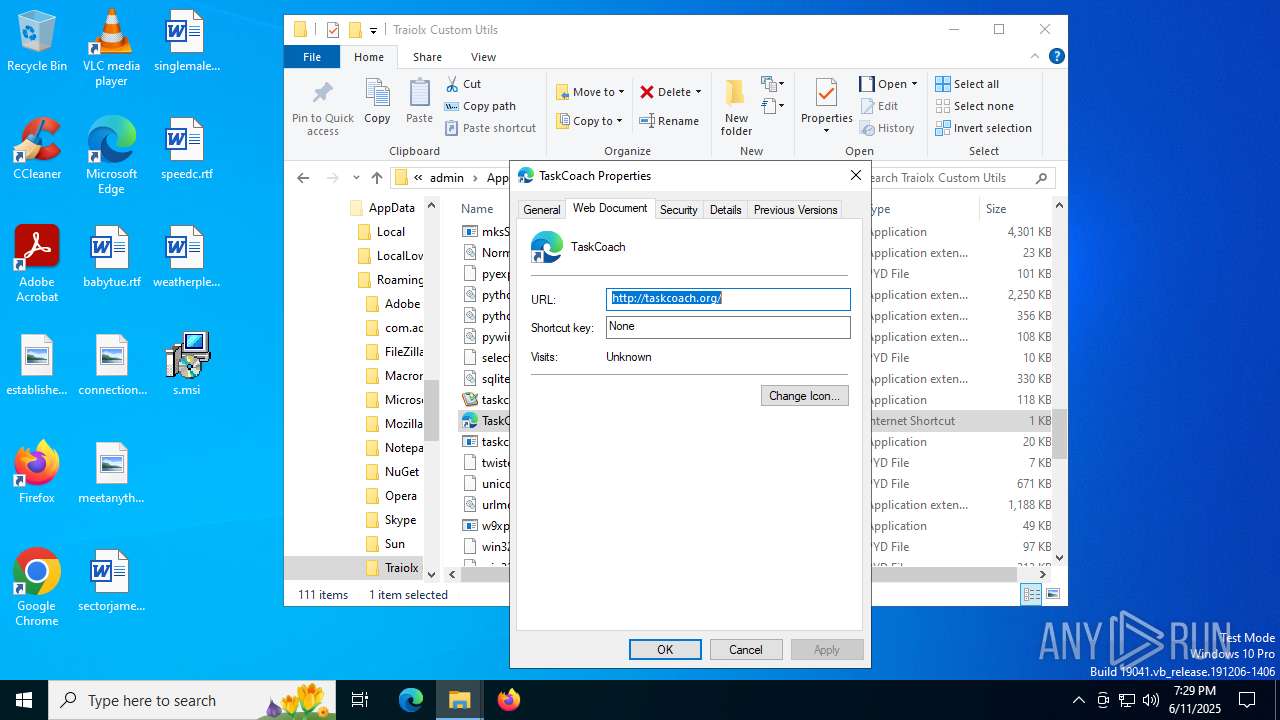
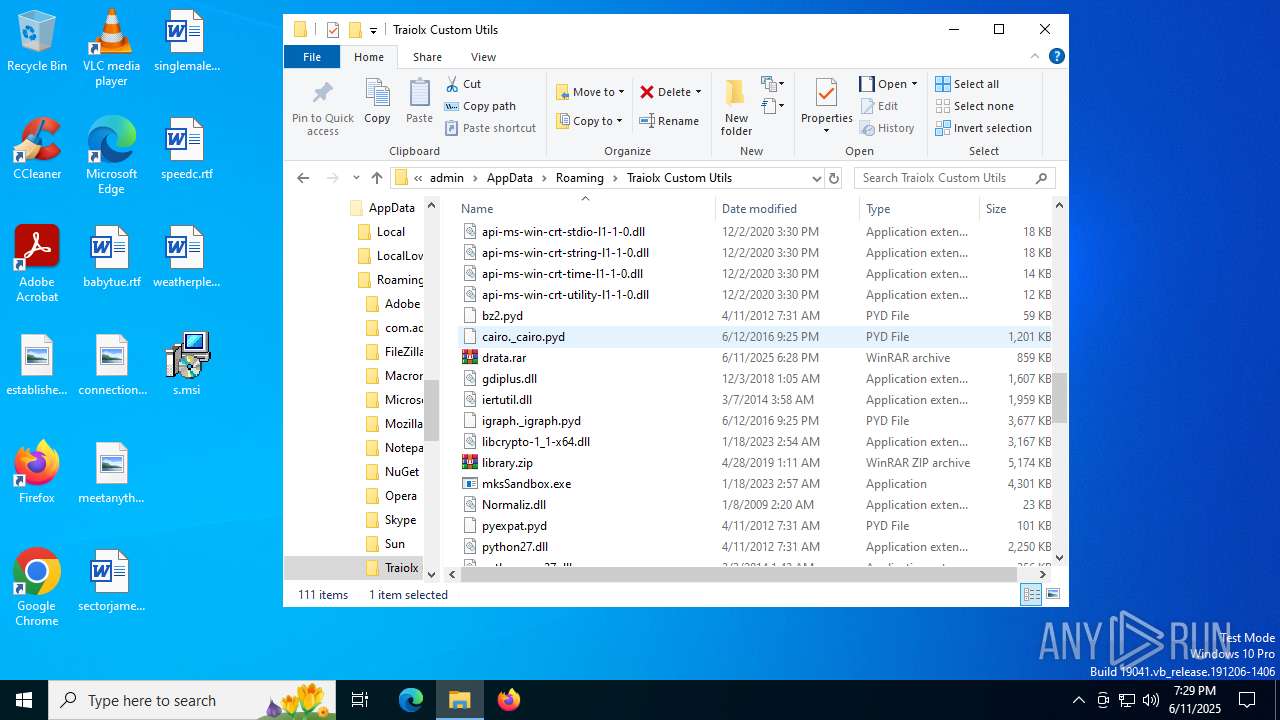
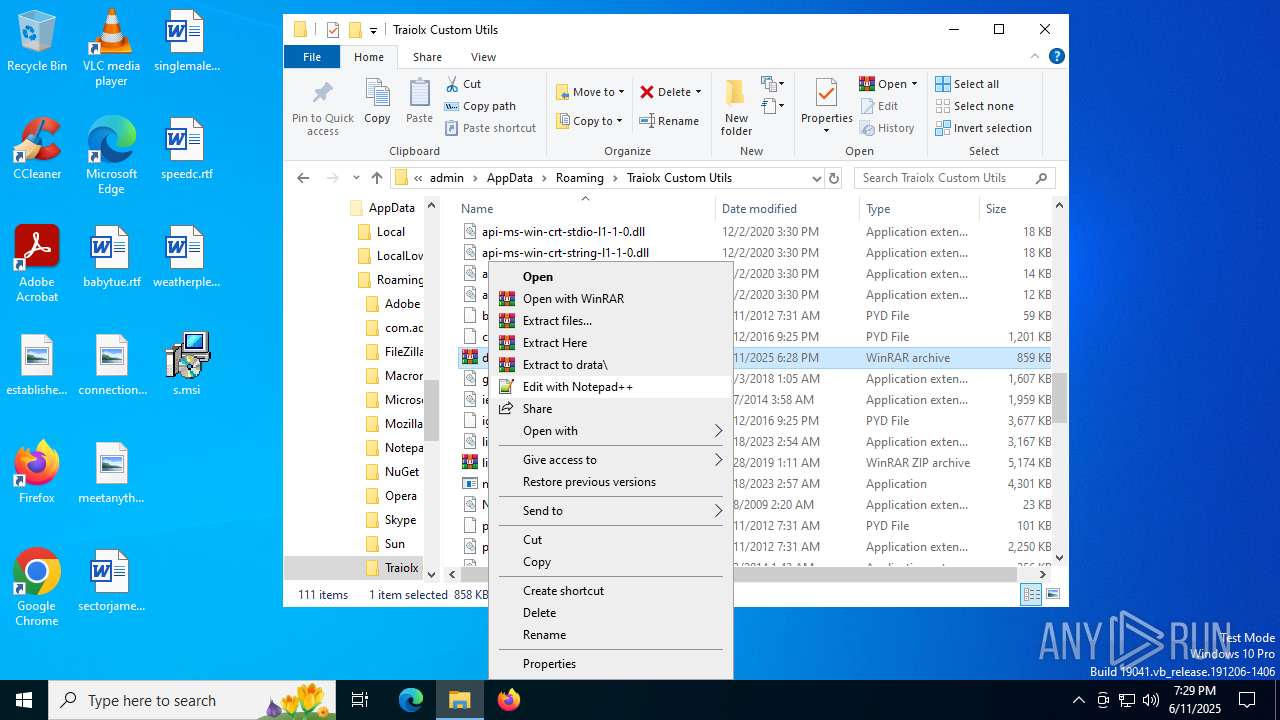
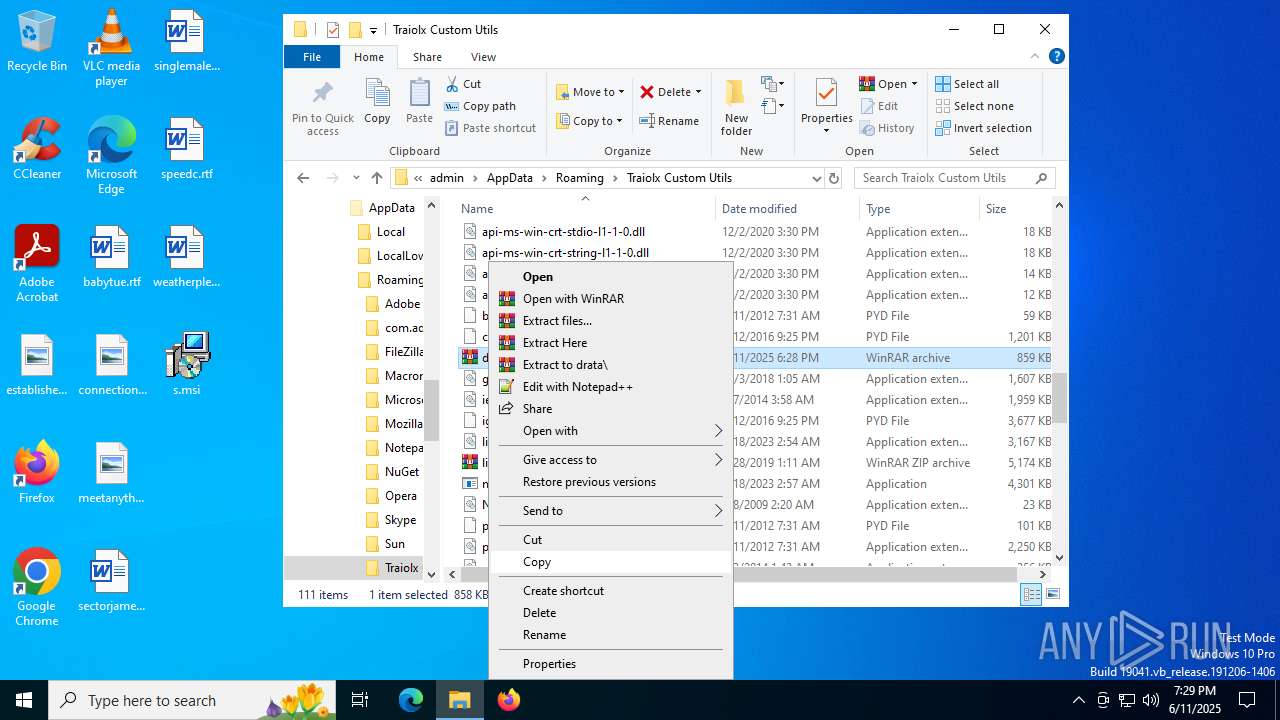
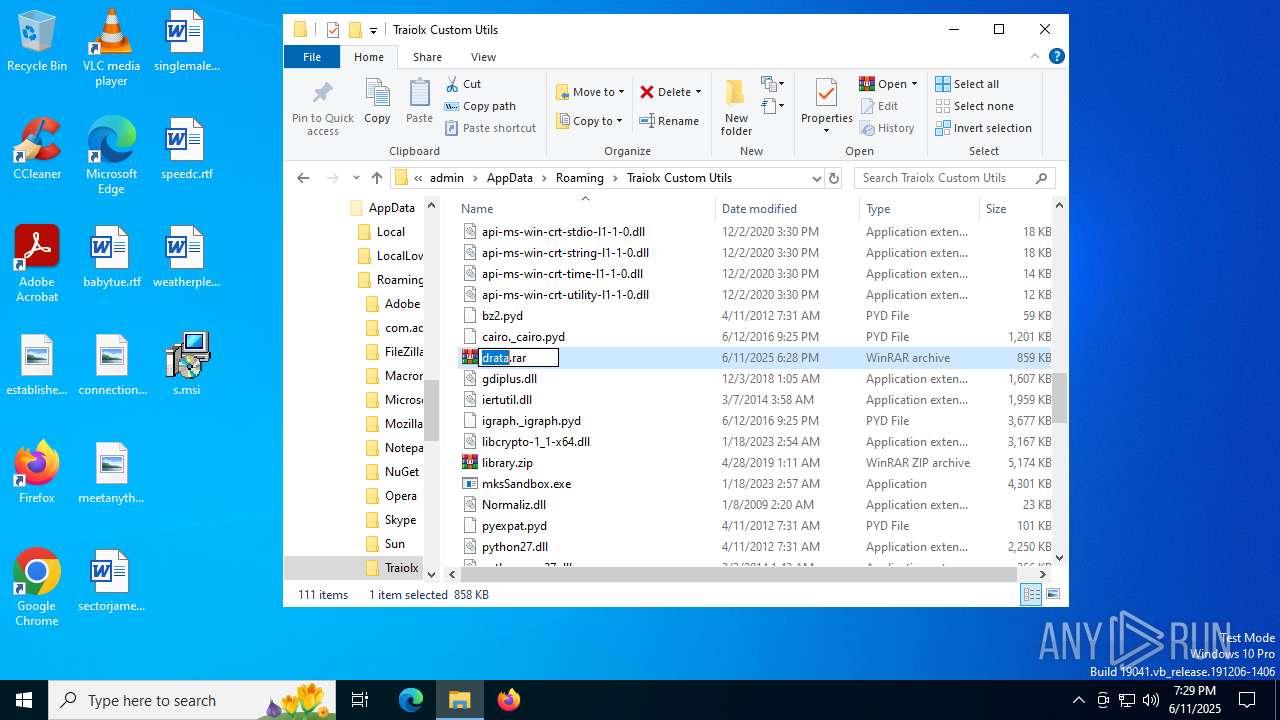
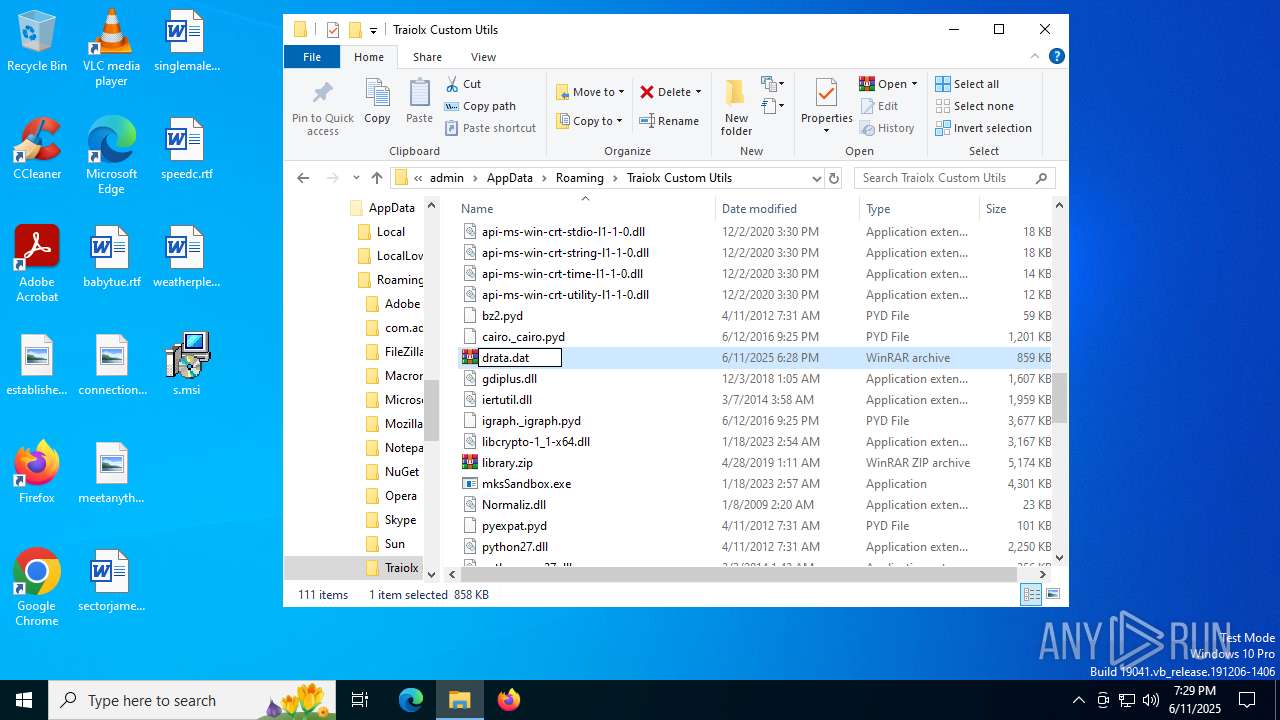
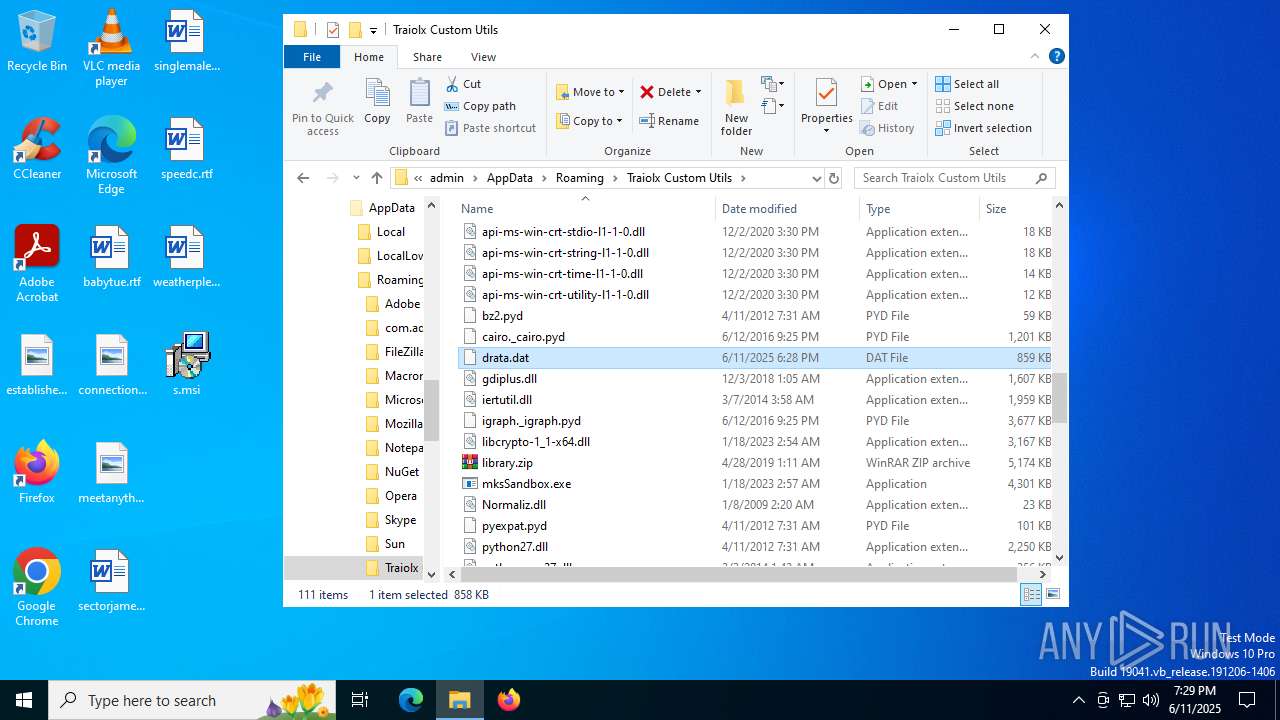
| File name: | s.msi |
| Full analysis: | https://app.any.run/tasks/5860243f-5400-44dc-95a6-bac5e0d24e7f |
| Verdict: | Malicious activity |
| Analysis date: | June 11, 2025, 19:21:36 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Security: 0, Code page: 1252, Revision Number: {ADBD41DF-2756-4AB0-ACDA-AC75FD96ABC1}, Number of Words: 10, Subject: Traiolx Custom Utils, Author: Viwaso Loqpol, Name of Creating Application: Traiolx Custom Utils, Template: x64;1033, Comments: This installer database contains the logic and data required to install Traiolx Custom Utils., Title: Installation Database, Keywords: Installer, MSI, Database, Create Time/Date: Wed Jun 11 15:29:03 2025, Last Saved Time/Date: Wed Jun 11 15:29:03 2025, Last Printed: Wed Jun 11 15:29:03 2025, Number of Pages: 450 |
| MD5: | FC0265A960F4A205E76313A9151077C0 |
| SHA1: | 0C9CBF3AC5FEDAD364E7AB623850AB62718A1EF6 |
| SHA256: | 1A7EAA4BD75D0D8EFABB4C33940918BA0E87468C239F52C9E540B14EDCB62617 |
| SSDEEP: | 393216:1xmhndyL/8/aDzj9U82/PVoATjN2h0objZMdmYxIg2AZkygH:Qdij9RcVoATjN2h0objZB2Ifl |
MALICIOUS
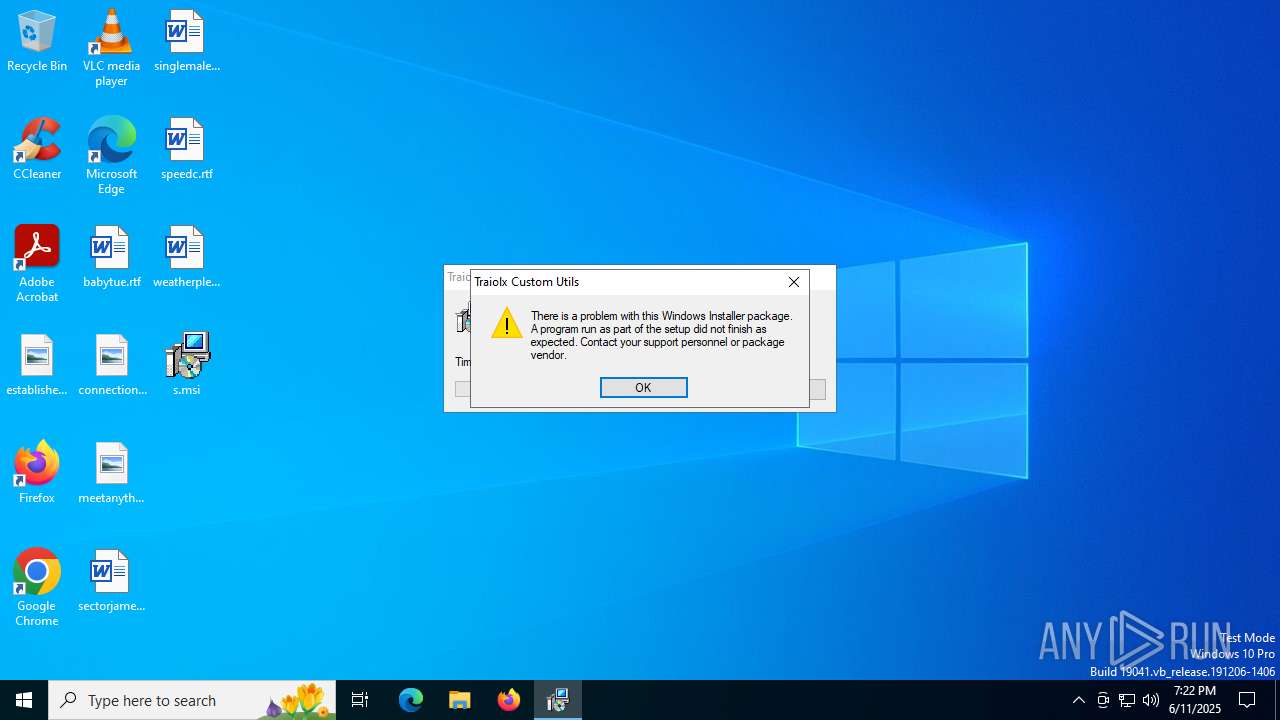
No malicious indicators.SUSPICIOUS
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6876)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 5232)
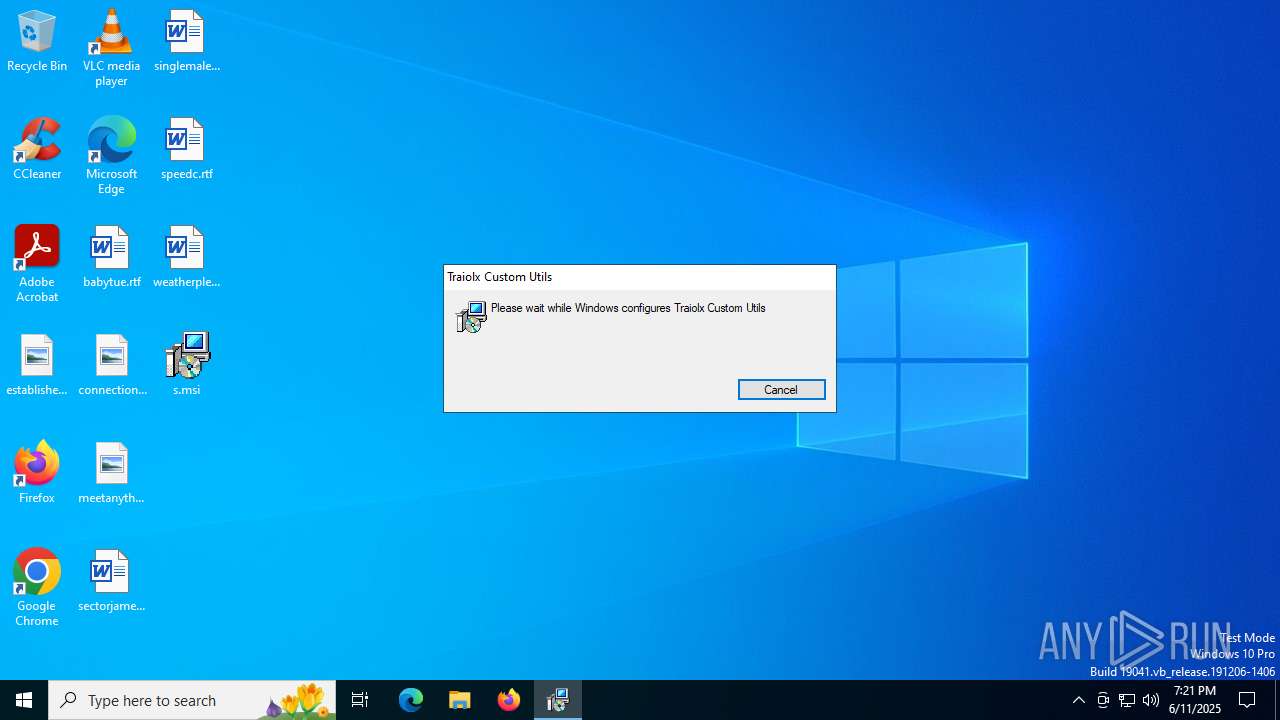
Process drops python dynamic module
- msiexec.exe (PID: 6876)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 6876)
Executing commands from a ".bat" file
- msiexec.exe (PID: 6876)
The executable file from the user directory is run by the CMD process
- 7z.exe (PID: 5124)
The process executes via Task Scheduler
- updater.exe (PID: 2324)
Application launched itself
- updater.exe (PID: 2324)
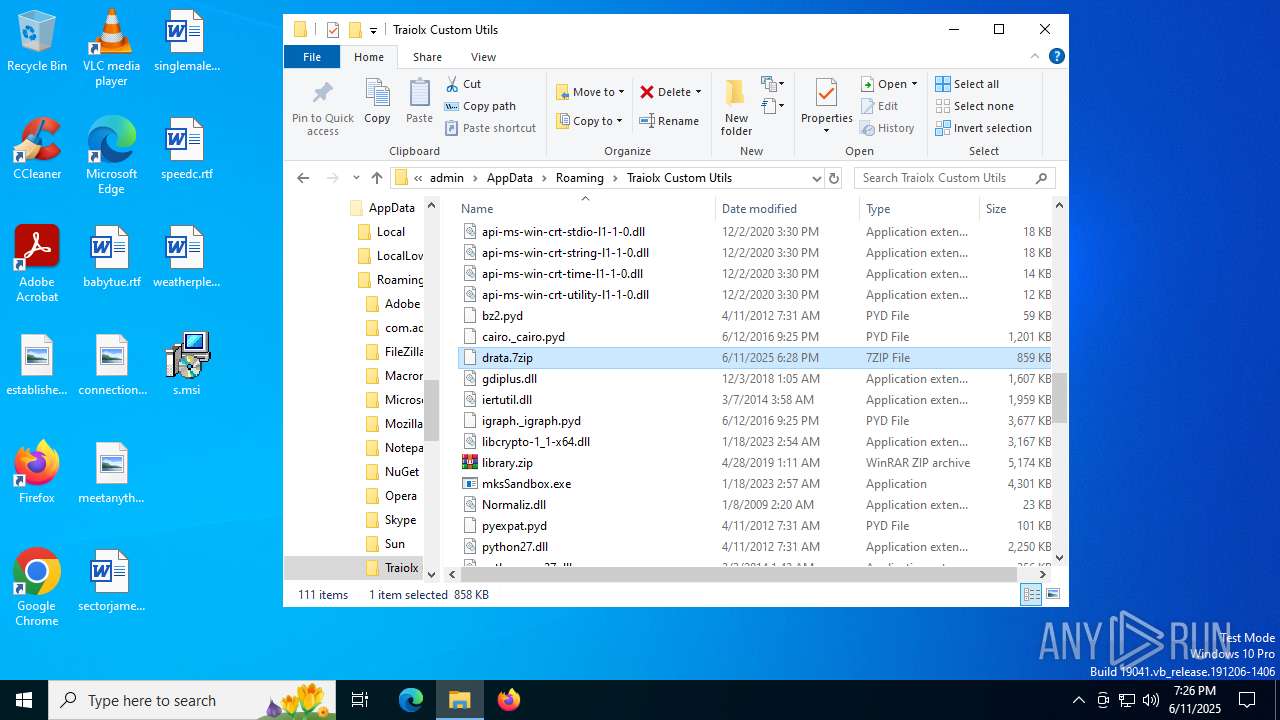
Drops 7-zip archiver for unpacking
- msiexec.exe (PID: 6876)
Process drops legitimate windows executable
- msiexec.exe (PID: 6876)
The process drops C-runtime libraries
- msiexec.exe (PID: 6876)
INFO
Reads Environment values
- msiexec.exe (PID: 5232)
Checks supported languages
- msiexec.exe (PID: 5232)
- msiexec.exe (PID: 6876)
- 7z.exe (PID: 5124)
- updater.exe (PID: 2324)
- updater.exe (PID: 6492)
Reads the computer name
- msiexec.exe (PID: 6876)
- msiexec.exe (PID: 5232)
- 7z.exe (PID: 5124)
- updater.exe (PID: 2324)
An automatically generated document
- msiexec.exe (PID: 7164)
Checks proxy server information
- msiexec.exe (PID: 5232)
- slui.exe (PID: 5896)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6876)
Reads the machine GUID from the registry
- msiexec.exe (PID: 5232)
Reads the software policy settings
- msiexec.exe (PID: 5232)
- slui.exe (PID: 5896)
Creates files or folders in the user directory
- msiexec.exe (PID: 5232)
- msiexec.exe (PID: 6876)
The sample compiled with english language support
- msiexec.exe (PID: 6876)
Create files in a temporary directory
- msiexec.exe (PID: 7164)
Process checks whether UAC notifications are on
- updater.exe (PID: 2324)
Manual execution by a user
- cmd.exe (PID: 5772)
- cmd.exe (PID: 6672)
- cmd.exe (PID: 3672)
- WinRAR.exe (PID: 4104)
- WinRAR.exe (PID: 4456)
Creates a software uninstall entry
- msiexec.exe (PID: 6876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (88.6) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (10) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| Security: | None |
|---|---|
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {ADBD41DF-2756-4AB0-ACDA-AC75FD96ABC1} |
| Words: | 10 |
| Subject: | Traiolx Custom Utils |
| Author: | Viwaso Loqpol |
| LastModifiedBy: | - |
| Software: | Traiolx Custom Utils |
| Template: | x64;1033 |
| Comments: | This installer database contains the logic and data required to install Traiolx Custom Utils. |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| CreateDate: | 2025:06:11 15:29:03 |
| ModifyDate: | 2025:06:11 15:29:03 |
| LastPrinted: | 2025:06:11 15:29:03 |
| Pages: | 450 |
Total processes
160
Monitored processes
21
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 432 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
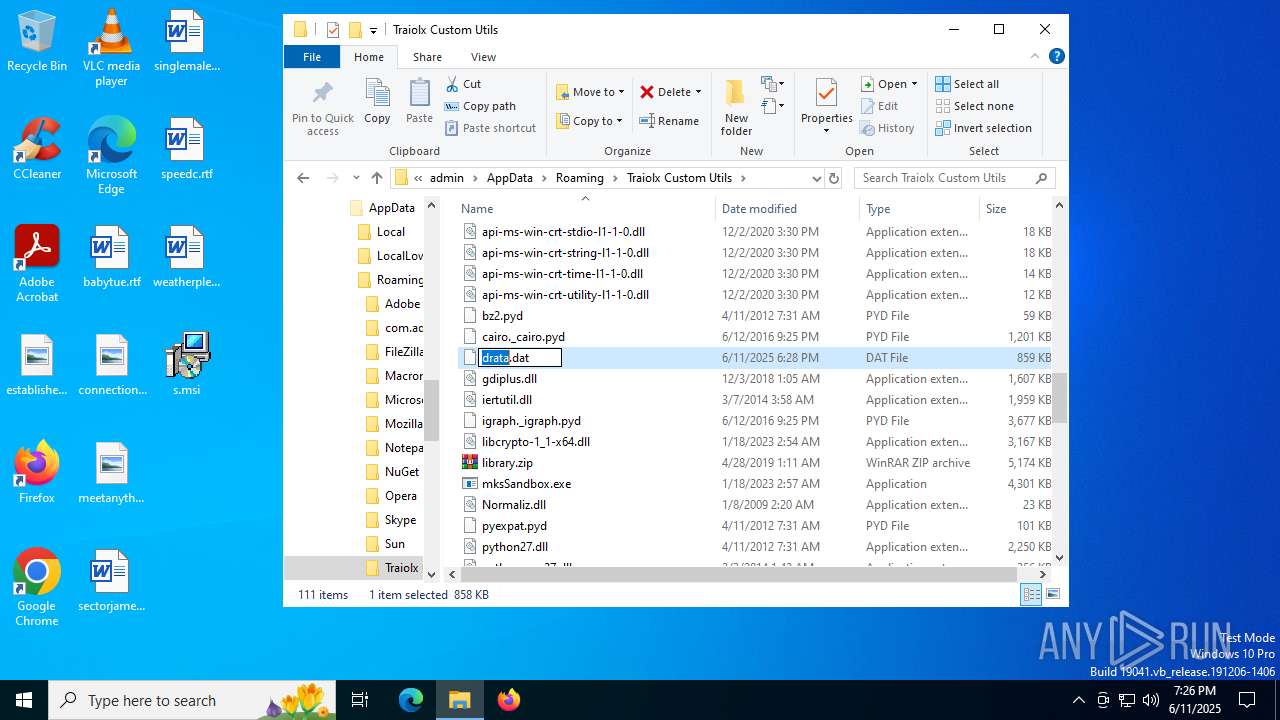
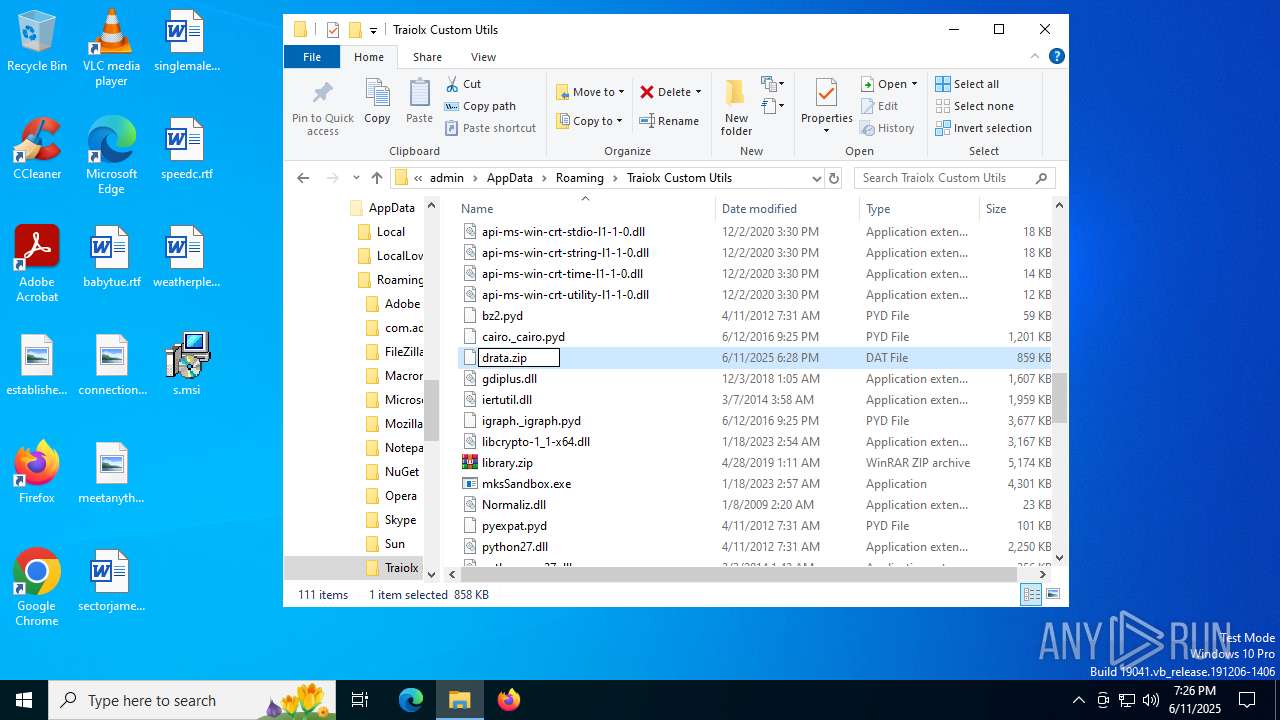
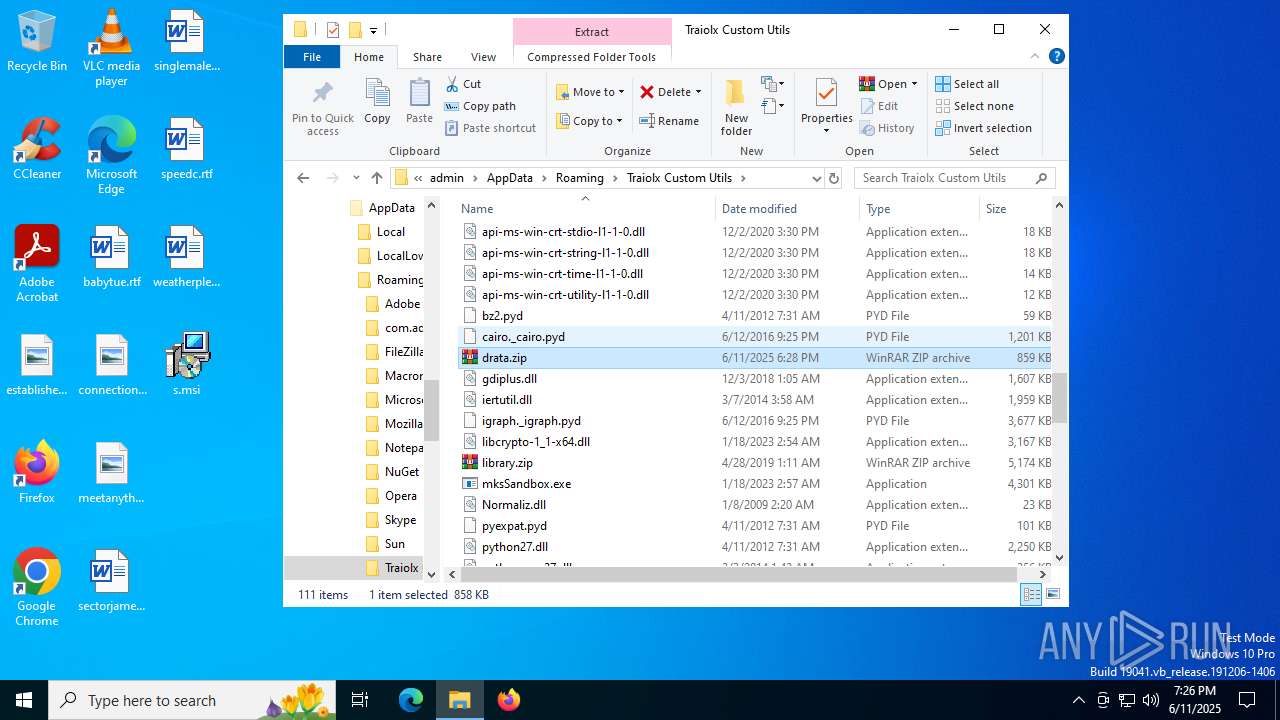
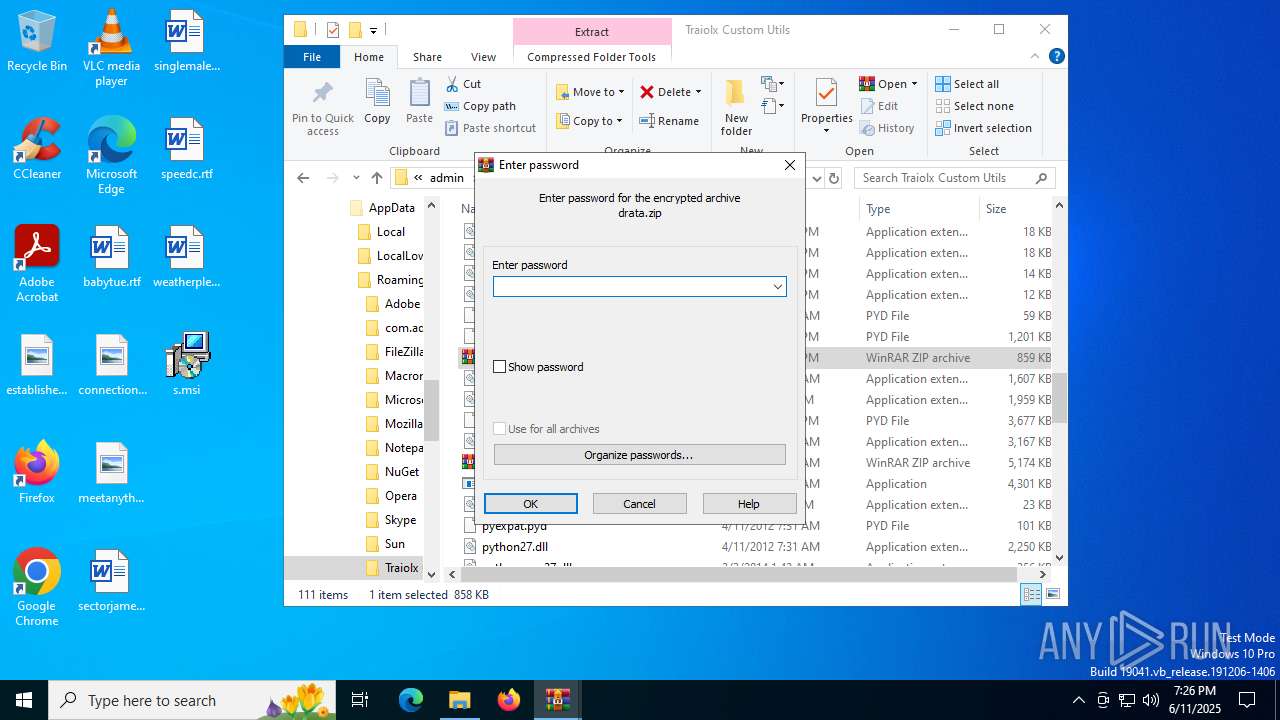
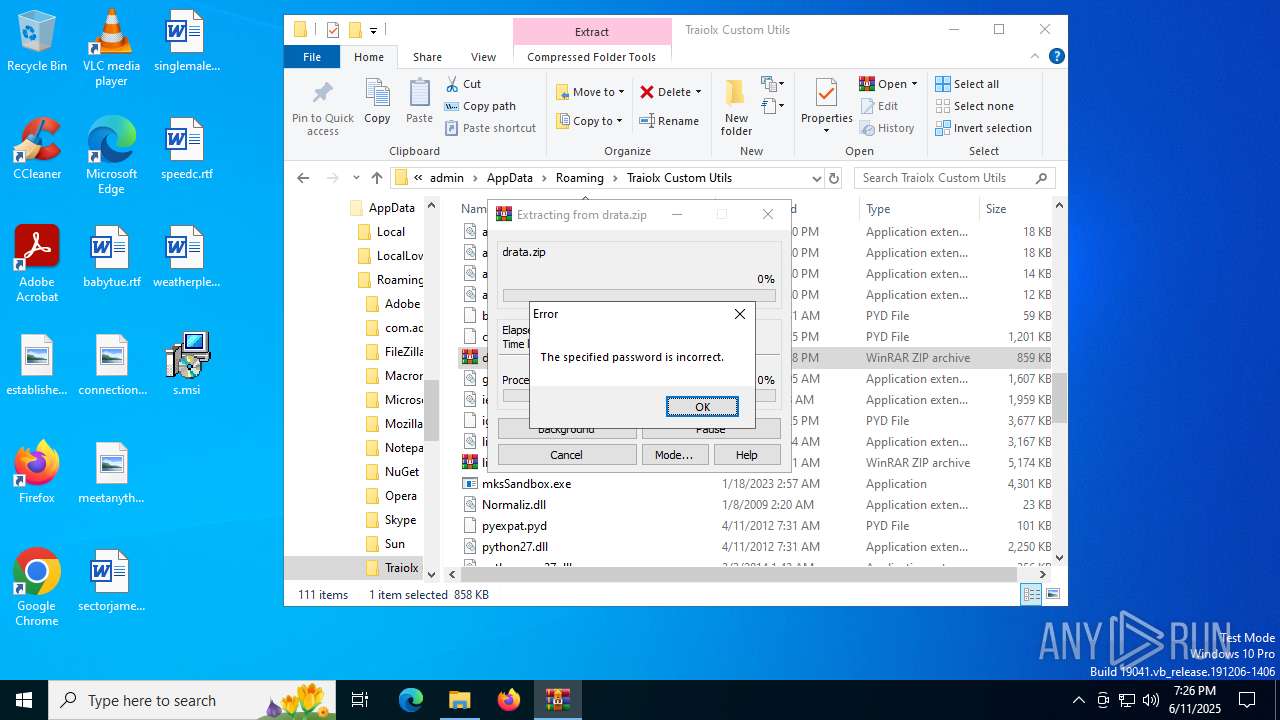
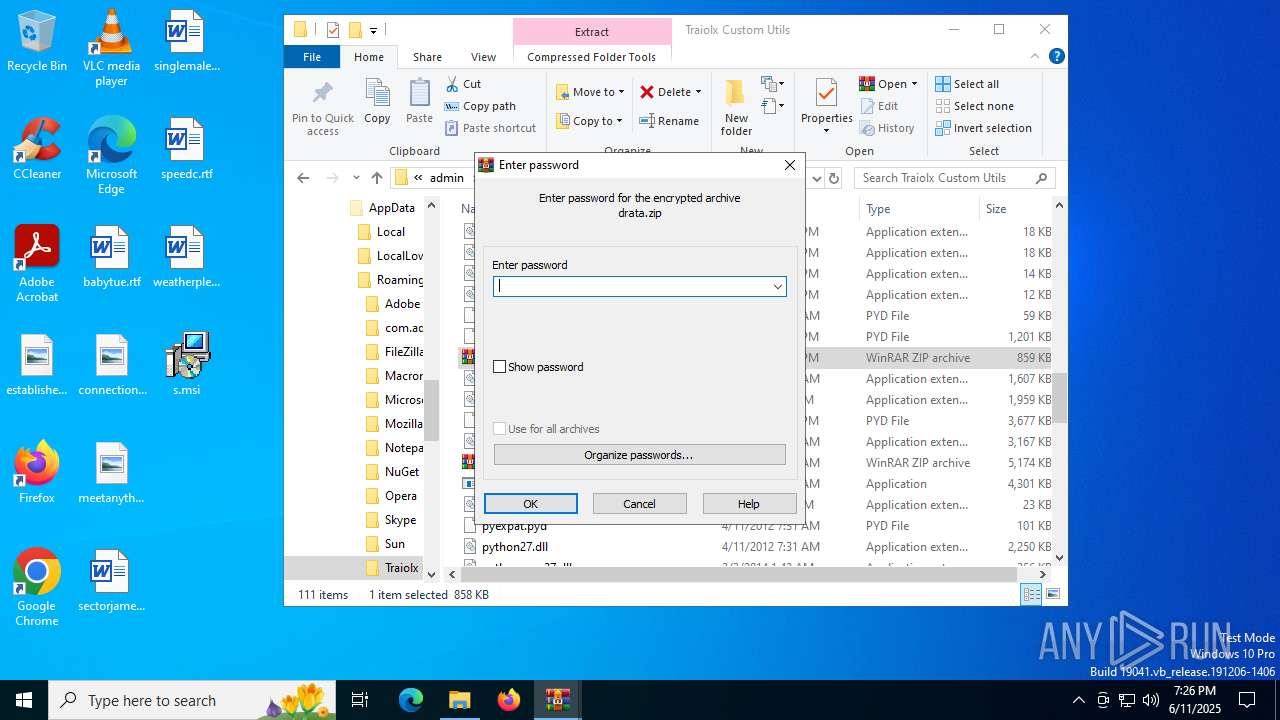
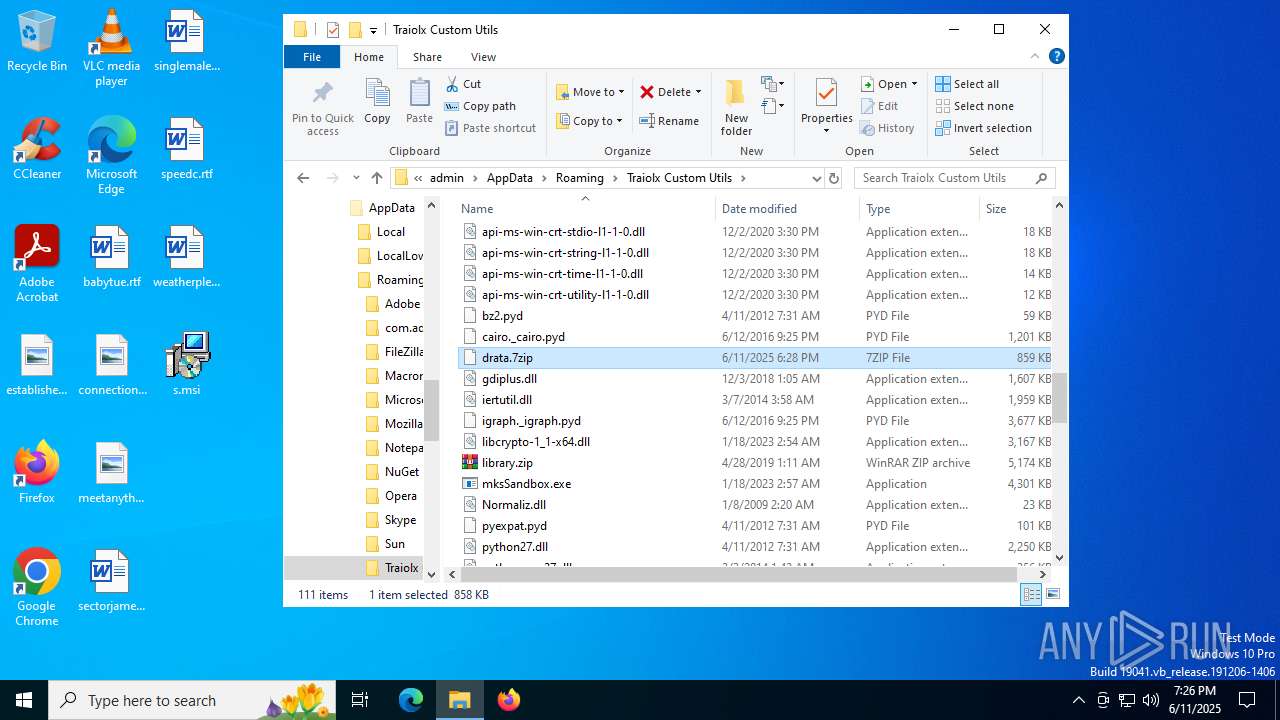
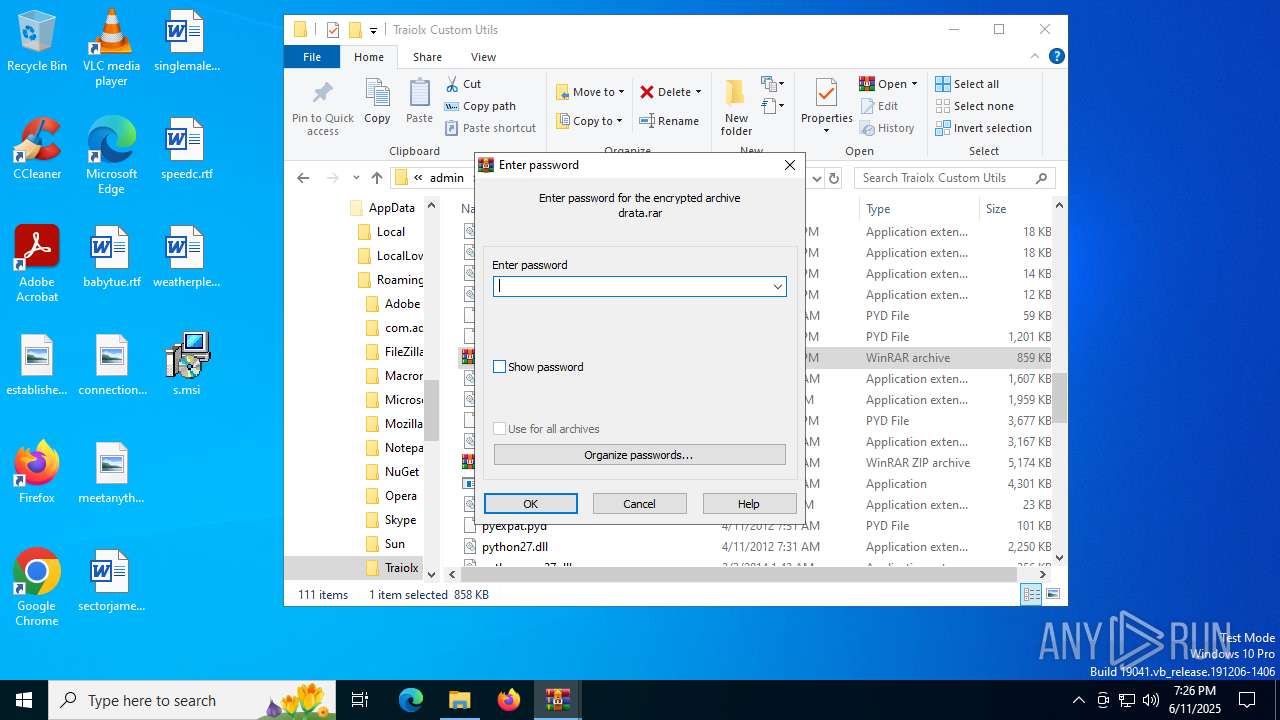
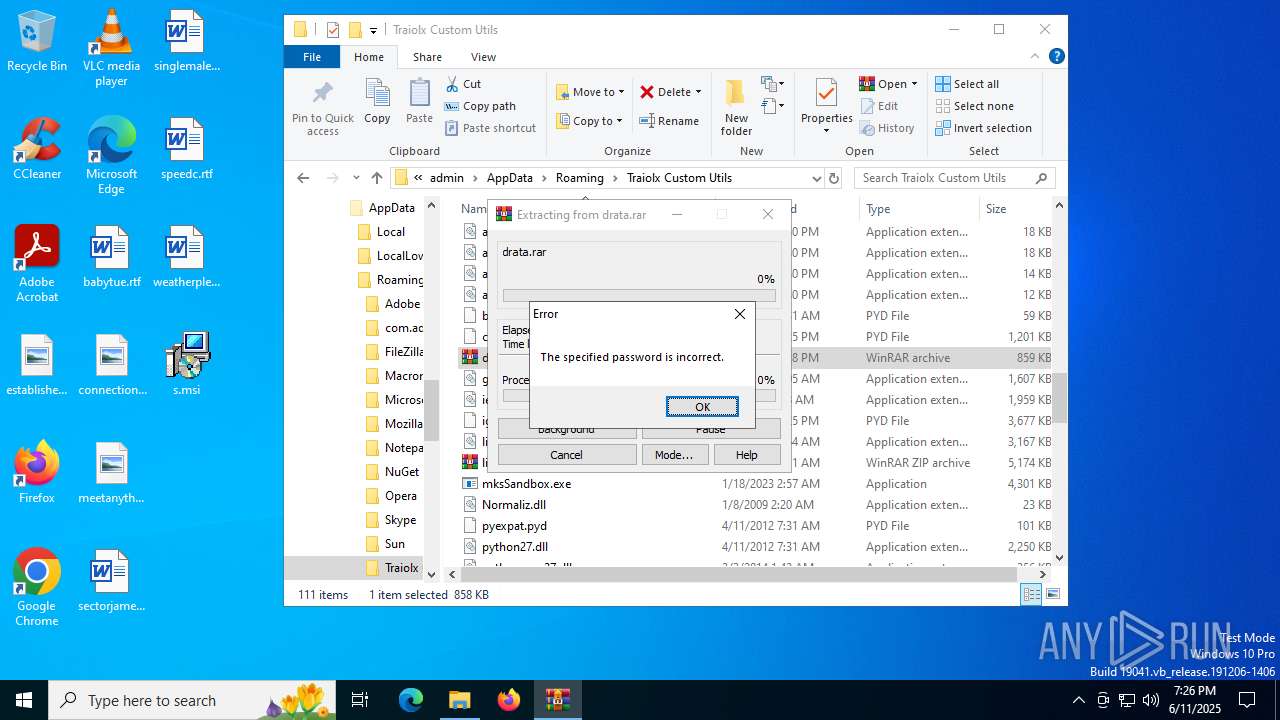
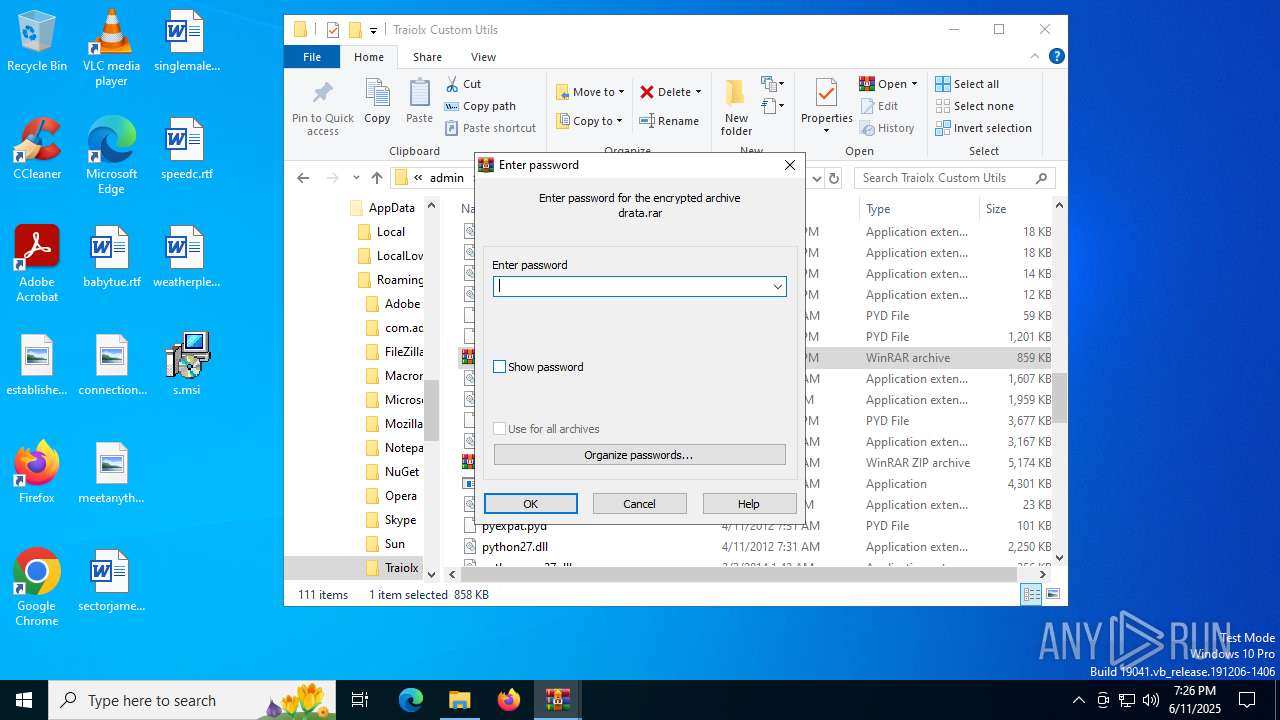
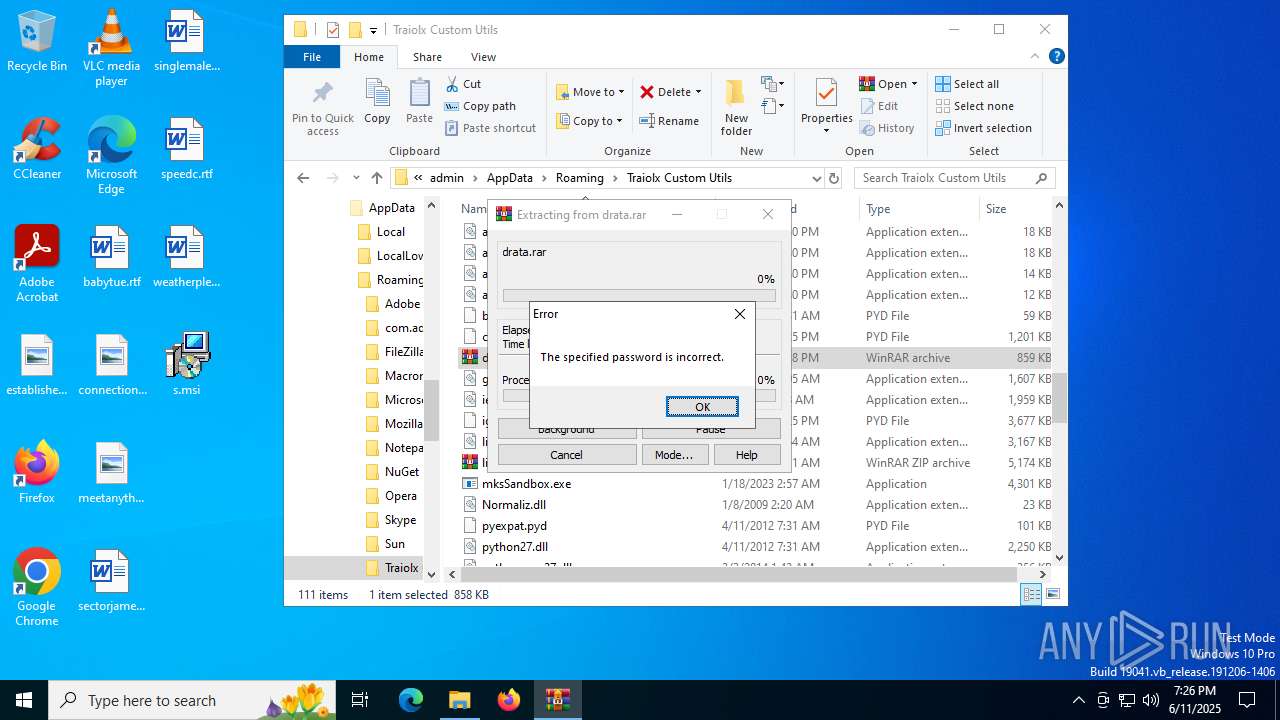
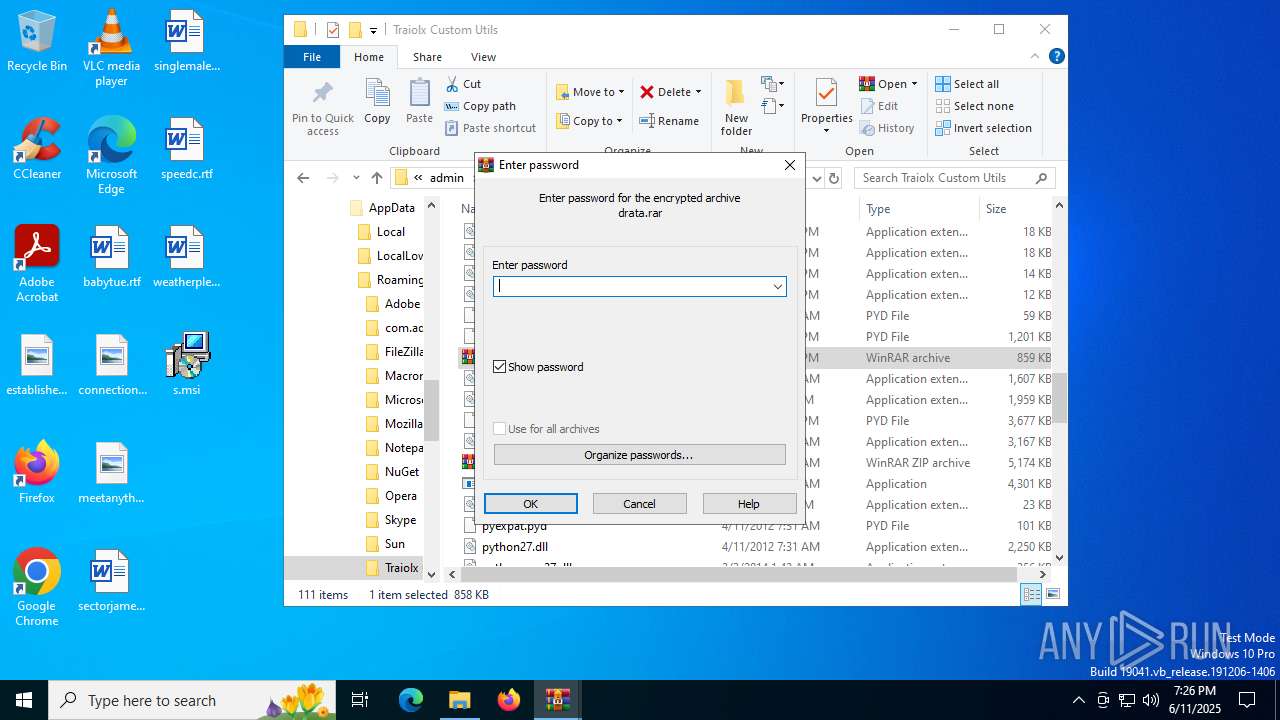
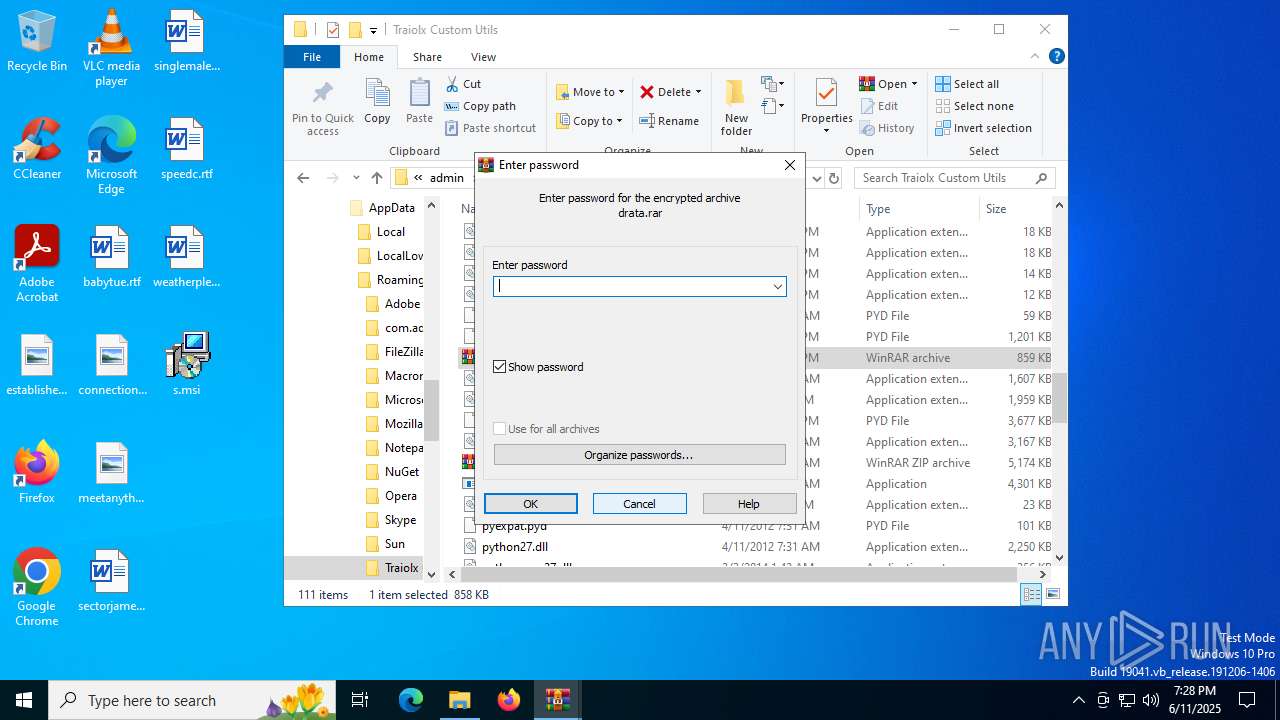
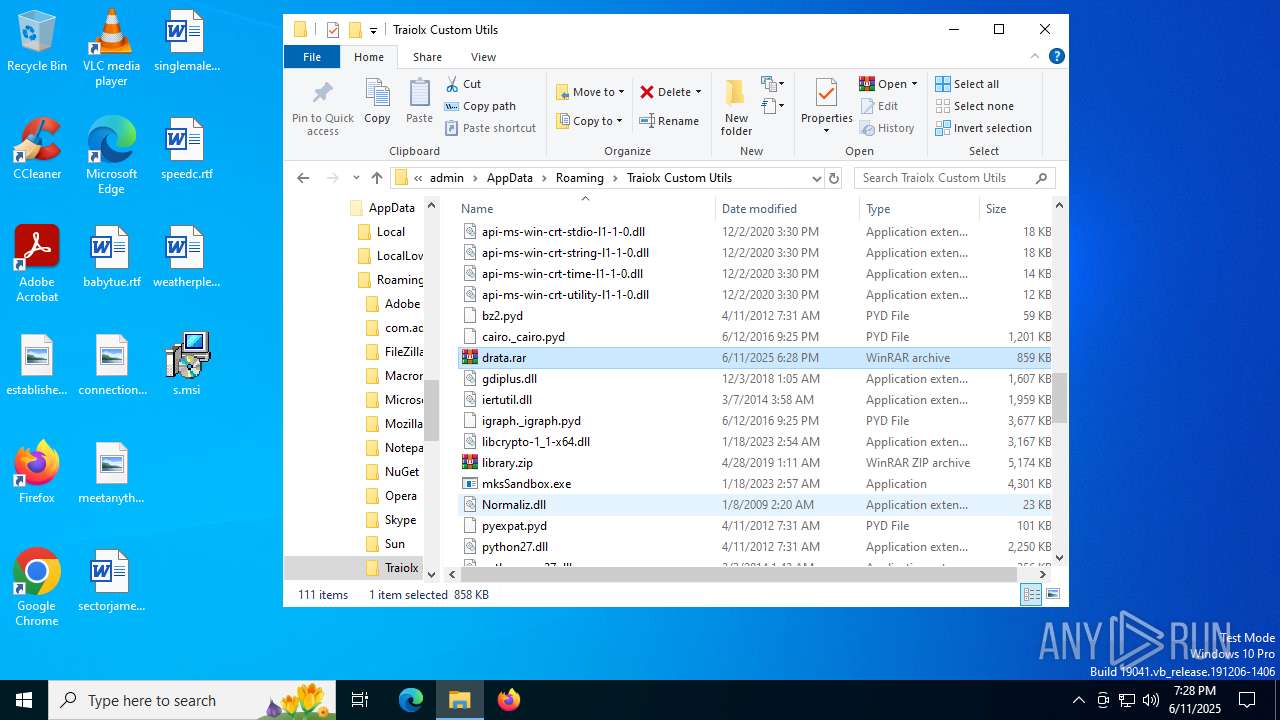
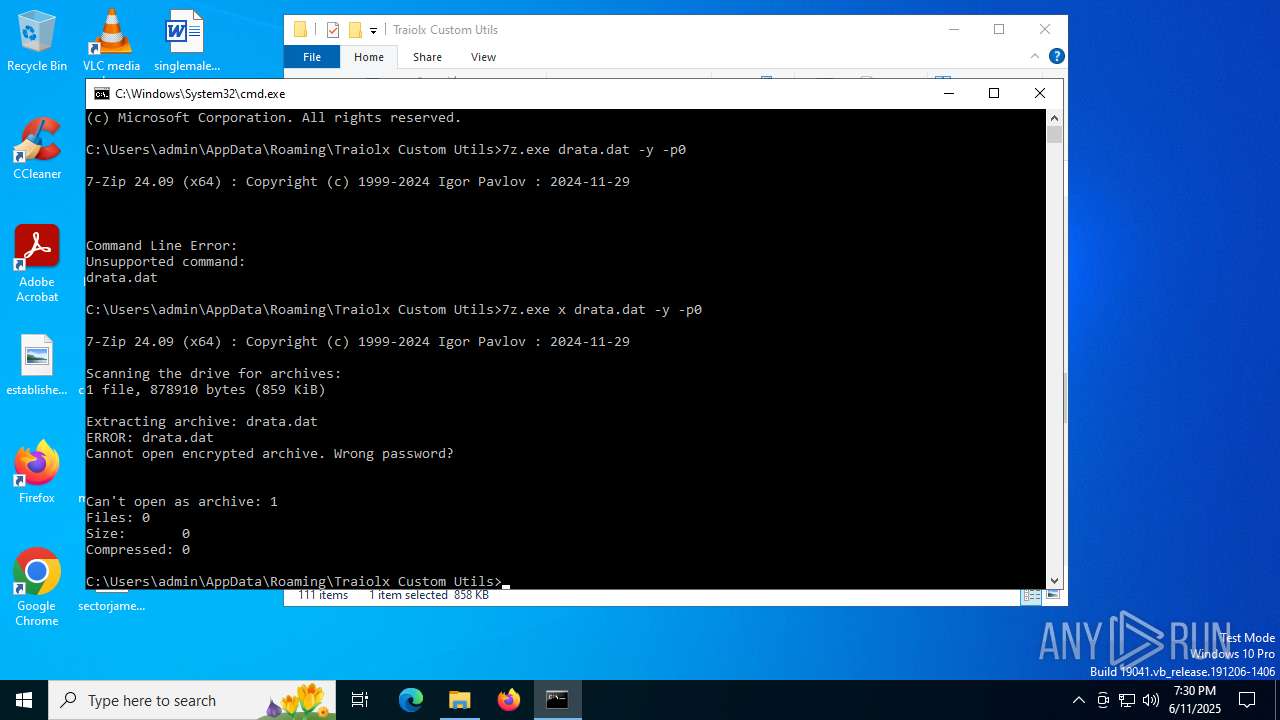
| 1044 | 7z.exe drata.dat -y -p0 | C:\Users\admin\AppData\Roaming\Traiolx Custom Utils\7z.exe | — | cmd.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Console Exit code: 7 Version: 24.09 Modules
| |||||||||||||||
| 2072 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2324 | "C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe" --wake --system | C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Updater Exit code: 0 Version: 134.0.6985.0 Modules
| |||||||||||||||
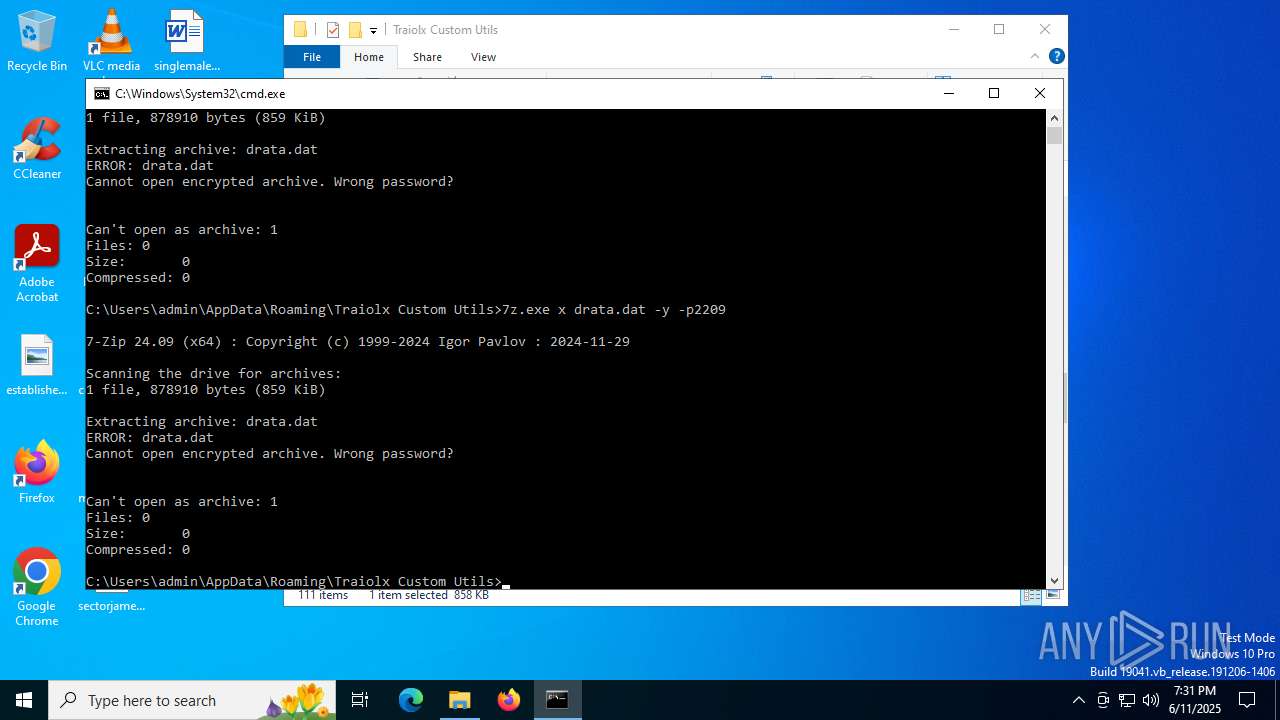
| 2520 | 7z.exe x drata.dat -y -p2209 | C:\Users\admin\AppData\Roaming\Traiolx Custom Utils\7z.exe | — | cmd.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Console Exit code: 2 Version: 24.09 Modules
| |||||||||||||||
| 3672 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4072 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
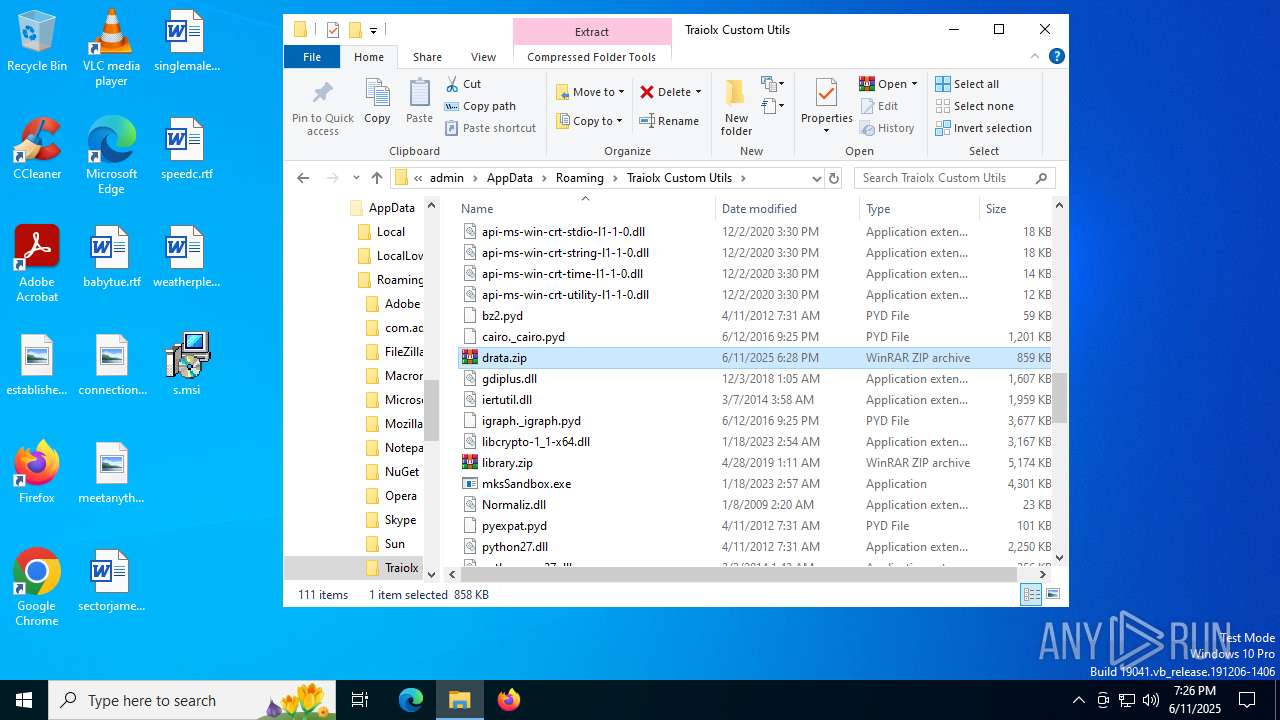
| 4104 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\AppData\Roaming\Traiolx Custom Utils\drata.zip" "C:\Users\admin\AppData\Roaming\Traiolx Custom Utils\" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 255 Version: 5.91.0 Modules
| |||||||||||||||
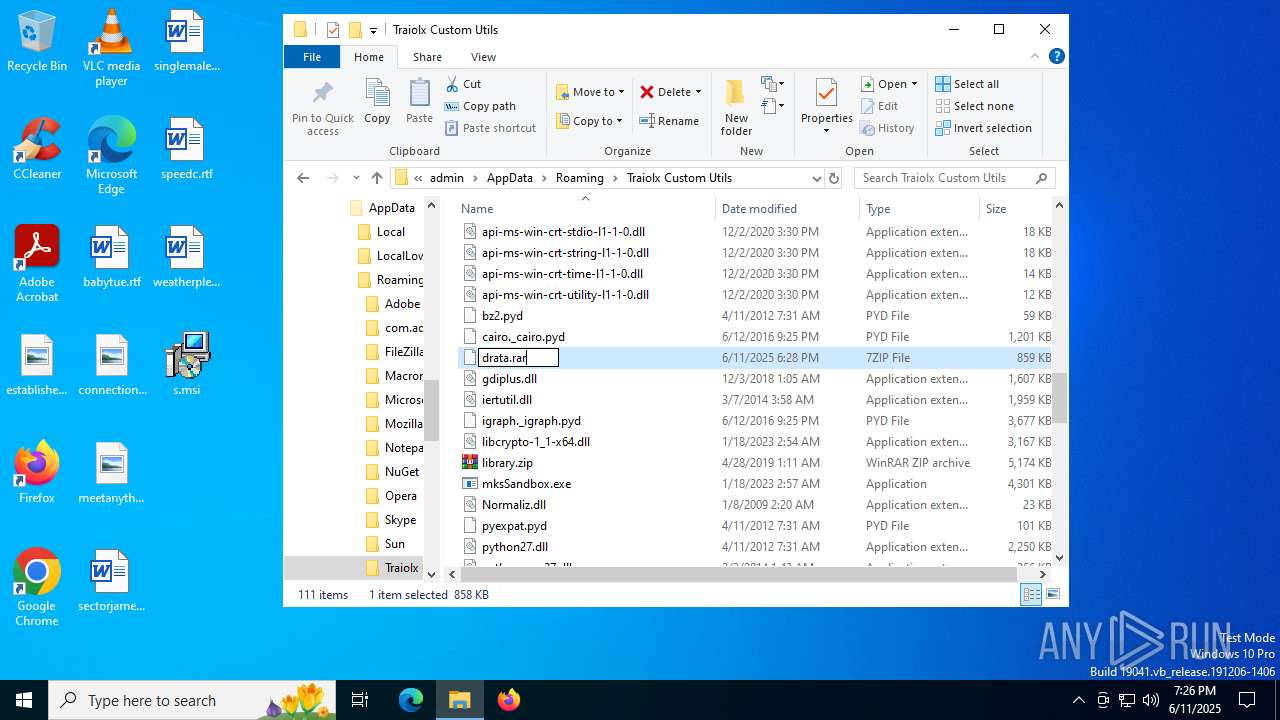
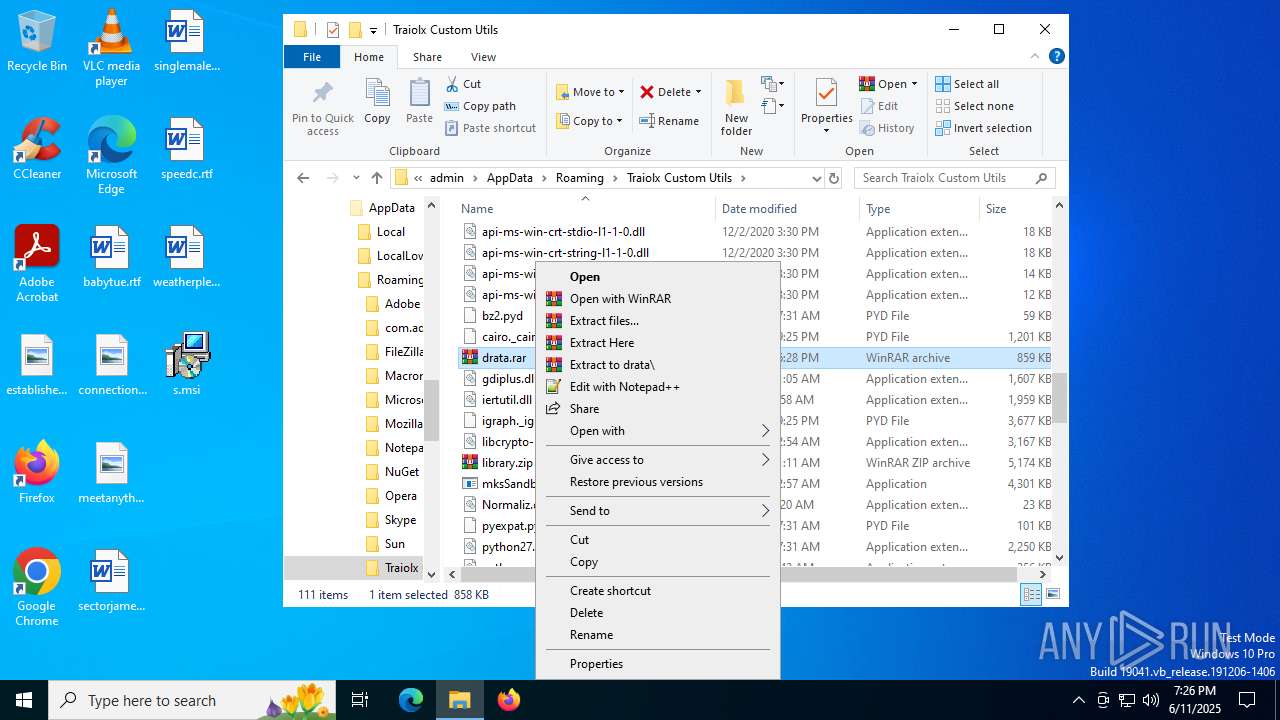
| 4456 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\AppData\Roaming\Traiolx Custom Utils\drata.rar" "C:\Users\admin\AppData\Roaming\Traiolx Custom Utils\drata\" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 255 Version: 5.91.0 Modules
| |||||||||||||||
| 4960 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 163
Read events
3 825
Write events
329
Delete events
9
Modification events
| (PID) Process: | (6876) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: DC1A00003A4EC71606DBDB01 | |||
| (PID) Process: | (6876) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: A8DC793E87C746CC6D273960EE45BFF91E8C4A7F1E0DEF79668242C463A982EC | |||
| (PID) Process: | (6876) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (5232) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5232) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5232) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6876) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\297BB0845463FC14D9BF829CFA0204A1 |
| Operation: | write | Name: | 514771724BF65274AA892B8EDA8BB3F8 |
Value: C:\Users\admin\AppData\Roaming\Traiolx Custom Utils\locale\fr\LC_MESSAGES\wxstd.mo | |||
| (PID) Process: | (6876) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\D7A88B54480B0684D8E004188AB0804A |
| Operation: | write | Name: | 514771724BF65274AA892B8EDA8BB3F8 |
Value: C:\Users\admin\AppData\Roaming\Traiolx Custom Utils\locale\gl_ES\LC_MESSAGES\wxstd.mo | |||
| (PID) Process: | (6876) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\95B92E541618FC24997C091E51D1FCBC |
| Operation: | write | Name: | 514771724BF65274AA892B8EDA8BB3F8 |
Value: C:\Users\admin\AppData\Roaming\Traiolx Custom Utils\locale\hi\LC_MESSAGES\wxstd.mo | |||
| (PID) Process: | (6876) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\99FE6F3F0A930974C8DF694CC11975AC |
| Operation: | write | Name: | 514771724BF65274AA892B8EDA8BB3F8 |
Value: C:\Users\admin\AppData\Roaming\Traiolx Custom Utils\locale\hu\LC_MESSAGES\wxstd.mo | |||
Executable files
117
Suspicious files
165
Text files
101
Unknown types
99
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6876 | msiexec.exe | C:\Windows\Installer\177520.msi | — | |
MD5:— | SHA256:— | |||
| 6876 | msiexec.exe | C:\Windows\Installer\MSI7649.tmp | executable | |
MD5:B717117EB31436F2FBD8182C3AAB267A | SHA256:4516899C2D5369CAC039258668E5AEF2651B33502849C1FA0778D3D63654CE9E | |||
| 6876 | msiexec.exe | C:\Windows\Installer\MSI7726.tmp | executable | |
MD5:B717117EB31436F2FBD8182C3AAB267A | SHA256:4516899C2D5369CAC039258668E5AEF2651B33502849C1FA0778D3D63654CE9E | |||
| 6876 | msiexec.exe | C:\Windows\Installer\MSI7765.tmp | executable | |
MD5:B717117EB31436F2FBD8182C3AAB267A | SHA256:4516899C2D5369CAC039258668E5AEF2651B33502849C1FA0778D3D63654CE9E | |||
| 6876 | msiexec.exe | C:\Windows\Installer\MSI76D7.tmp | executable | |
MD5:B717117EB31436F2FBD8182C3AAB267A | SHA256:4516899C2D5369CAC039258668E5AEF2651B33502849C1FA0778D3D63654CE9E | |||
| 6876 | msiexec.exe | C:\Windows\Installer\MSI7C3A.tmp | executable | |
MD5:B717117EB31436F2FBD8182C3AAB267A | SHA256:4516899C2D5369CAC039258668E5AEF2651B33502849C1FA0778D3D63654CE9E | |||
| 5232 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37B114A7D931F8A326F0586E65C5BE9D | binary | |
MD5:4ACACD1D65AC1E7C06C70787BAAEDD8D | SHA256:5081780A9808E7783305A97F4289404DE7D4F08AE9E664E7B4F9895991BD14AA | |||
| 5232 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37B114A7D931F8A326F0586E65C5BE9D | binary | |
MD5:39E3F513A10544388A829D4CEBB6BC1F | SHA256:4B942BF779BD866AA051ECB8E7013011566E05C9F98539790DB96936E6D3194E | |||
| 5232 | msiexec.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\diagnostics[1].htm | binary | |
MD5:CFCD208495D565EF66E7DFF9F98764DA | SHA256:5FECEB66FFC86F38D952786C6D696C79C2DBC239DD4E91B46729D73A27FB57E9 | |||
| 6876 | msiexec.exe | C:\Windows\Installer\MSI77C4.tmp | executable | |
MD5:805680BE3B2F96DDD652257156481EBB | SHA256:B5D0C2958F7C59410EB7E255E978563403A71B17D2105498005E1CED7F643489 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
26
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.24.77.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 184.24.77.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5232 | msiexec.exe | GET | 200 | 65.9.66.40:80 | http://r11.c.lencr.org/119.crl | unknown | — | — | whitelisted |
1212 | backgroundTaskHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
480 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
480 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.35.233.46:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5944 | MoUsoCoreWorker.exe | 184.24.77.9:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.24.77.9:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5232 | msiexec.exe | 169.150.247.36:443 | birdeemusic.com | — | GB | unknown |
5232 | msiexec.exe | 65.9.66.40:80 | r11.c.lencr.org | AMAZON-02 | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
birdeemusic.com |
| unknown |
r11.c.lencr.org |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |