| File name: | Spotify_Lite_v1.9.0.72404_MOD.apk |
| Full analysis: | https://app.any.run/tasks/f0b55c83-6f45-4722-8c44-5a57468a7d47 |
| Verdict: | Malicious activity |
| Analysis date: | July 04, 2025, 21:18:36 |
| OS: | Android 14 |
| MIME: | application/vnd.android.package-archive |
| File info: | Android package (APK), with AndroidManifest.xml |
| MD5: | 8FB64CBE84144E50D4C131E0239960DA |
| SHA1: | 2D5361457A53B66C8CA5BBDCA12F63AA833F4C69 |
| SHA256: | 1A4C1FACE42317F73DCA337B726FDA5C02279947B8B6D5075BC69A9F2E1F8EC8 |
| SSDEEP: | 98304:U5F1J3CHWQ26njl1AJsMU+yJzWGzCTJCEnd7gSKZrpNbVbgJWYSnR8YYNbwCLa82:xHfmwubvJuY8n71Q8cD3t10LsuVQSdh |
MALICIOUS
No malicious indicators.SUSPICIOUS
Establishing a connection
- app_process64 (PID: 2293)
- app_process64 (PID: 2561)
- app_process64 (PID: 2634)
- app_process64 (PID: 2398)
- app_process64 (PID: 2484)
- app_process64 (PID: 2784)
- app_process64 (PID: 2935)
- app_process64 (PID: 2712)
- app_process64 (PID: 3232)
- app_process64 (PID: 3082)
- app_process64 (PID: 3456)
- app_process64 (PID: 3012)
- app_process64 (PID: 3384)
- app_process64 (PID: 2862)
- app_process64 (PID: 3528)
- app_process64 (PID: 3693)
- app_process64 (PID: 3157)
- app_process64 (PID: 3305)
- app_process64 (PID: 3768)
Accesses system-level resources
- app_process64 (PID: 2398)
- app_process64 (PID: 2484)
- app_process64 (PID: 2634)
- app_process64 (PID: 2712)
- app_process64 (PID: 2561)
- app_process64 (PID: 2862)
- app_process64 (PID: 2935)
- app_process64 (PID: 3012)
- app_process64 (PID: 2784)
- app_process64 (PID: 3082)
- app_process64 (PID: 3157)
- app_process64 (PID: 3305)
- app_process64 (PID: 3232)
- app_process64 (PID: 3384)
- app_process64 (PID: 3456)
- app_process64 (PID: 3603)
- app_process64 (PID: 3528)
- app_process64 (PID: 3693)
- app_process64 (PID: 3768)
Updates data in the storage of application settings (SharedPreferences)
- app_process64 (PID: 2293)
- app_process64 (PID: 2398)
Collects data about the device's environment (JVM version)
- app_process64 (PID: 2398)
- app_process64 (PID: 2484)
- app_process64 (PID: 2561)
- app_process64 (PID: 2293)
- app_process64 (PID: 2634)
- app_process64 (PID: 2712)
- app_process64 (PID: 2784)
- app_process64 (PID: 2935)
- app_process64 (PID: 3012)
- app_process64 (PID: 2862)
- app_process64 (PID: 3157)
- app_process64 (PID: 3232)
- app_process64 (PID: 3305)
- app_process64 (PID: 3082)
- app_process64 (PID: 3384)
- app_process64 (PID: 3456)
- app_process64 (PID: 3528)
- app_process64 (PID: 3768)
- app_process64 (PID: 3603)
Retrieves a list of running application processes
- app_process64 (PID: 2293)
- app_process64 (PID: 2398)
INFO
Retrieves data from storage of application settings (SharedPreferences)
- app_process64 (PID: 2293)
- app_process64 (PID: 2398)
- app_process64 (PID: 2484)
- app_process64 (PID: 2634)
- app_process64 (PID: 2561)
- app_process64 (PID: 2712)
- app_process64 (PID: 2784)
- app_process64 (PID: 2935)
- app_process64 (PID: 2862)
- app_process64 (PID: 3157)
- app_process64 (PID: 3012)
- app_process64 (PID: 3232)
- app_process64 (PID: 3082)
- app_process64 (PID: 3528)
- app_process64 (PID: 3384)
- app_process64 (PID: 3456)
- app_process64 (PID: 3305)
- app_process64 (PID: 3603)
- app_process64 (PID: 3693)
Stores data using SQLite database
- app_process64 (PID: 2293)
- app_process64 (PID: 2398)
Retrieves the value of a secure system setting
- app_process64 (PID: 2293)
- app_process64 (PID: 2484)
- app_process64 (PID: 2634)
- app_process64 (PID: 2398)
- app_process64 (PID: 2712)
- app_process64 (PID: 2935)
- app_process64 (PID: 2561)
- app_process64 (PID: 3012)
- app_process64 (PID: 2784)
- app_process64 (PID: 2862)
- app_process64 (PID: 3157)
- app_process64 (PID: 3082)
- app_process64 (PID: 3232)
- app_process64 (PID: 3456)
- app_process64 (PID: 3305)
- app_process64 (PID: 3528)
- app_process64 (PID: 3603)
- app_process64 (PID: 3384)
- app_process64 (PID: 3693)
- app_process64 (PID: 3768)
Detects if debugger is connected
- app_process64 (PID: 2398)
- app_process64 (PID: 2484)
- app_process64 (PID: 2561)
- app_process64 (PID: 2634)
- app_process64 (PID: 2712)
- app_process64 (PID: 2935)
- app_process64 (PID: 3012)
- app_process64 (PID: 2784)
- app_process64 (PID: 2862)
- app_process64 (PID: 3157)
- app_process64 (PID: 3082)
- app_process64 (PID: 3305)
- app_process64 (PID: 3528)
- app_process64 (PID: 3232)
- app_process64 (PID: 3603)
- app_process64 (PID: 3384)
- app_process64 (PID: 3693)
- app_process64 (PID: 3456)
Gets file name without full path
- app_process64 (PID: 2293)
- app_process64 (PID: 2398)
- app_process64 (PID: 2484)
- app_process64 (PID: 2561)
- app_process64 (PID: 2634)
- app_process64 (PID: 2862)
- app_process64 (PID: 2712)
- app_process64 (PID: 2784)
- app_process64 (PID: 3082)
- app_process64 (PID: 2935)
- app_process64 (PID: 3232)
- app_process64 (PID: 3012)
- app_process64 (PID: 3384)
- app_process64 (PID: 3157)
- app_process64 (PID: 3603)
- app_process64 (PID: 3528)
- app_process64 (PID: 3456)
- app_process64 (PID: 3305)
Returns elapsed time since boot
- app_process64 (PID: 2398)
- app_process64 (PID: 2293)
Dynamically inspects or modifies classes, methods, and fields at runtime
- app_process64 (PID: 2398)
- app_process64 (PID: 2484)
- app_process64 (PID: 2561)
- app_process64 (PID: 2293)
- app_process64 (PID: 2634)
- app_process64 (PID: 2712)
- app_process64 (PID: 2784)
- app_process64 (PID: 2862)
- app_process64 (PID: 2935)
- app_process64 (PID: 3012)
- app_process64 (PID: 3082)
- app_process64 (PID: 3157)
- app_process64 (PID: 3232)
- app_process64 (PID: 3384)
- app_process64 (PID: 3305)
- app_process64 (PID: 3456)
- app_process64 (PID: 3528)
- app_process64 (PID: 3693)
- app_process64 (PID: 3768)
- app_process64 (PID: 3603)
Listens for changes in airplane mode status
- app_process64 (PID: 2398)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .oxt | | | OpenOffice Extension (53.7) |
|---|---|---|
| .jar | | | Java Archive (36.2) |
| .zip | | | ZIP compressed archive (10) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:08:27 12:38:04 |
| ZipCRC: | 0x15b348df |
| ZipCompressedSize: | 7636 |
| ZipUncompressedSize: | 37556 |
| ZipFileName: | AndroidManifest.xml |
Total processes
151
Monitored processes
27
Malicious processes
0
Suspicious processes
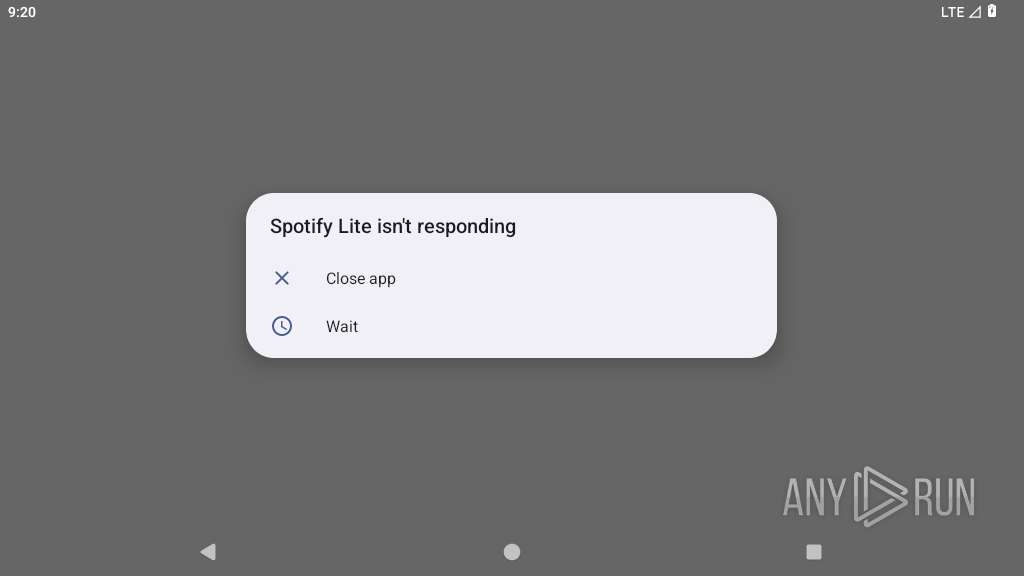
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 1795 | com.android.statementservice | /system/bin/app_process64 | — | app_process64 |
User: u0_a35 Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2293 | com.spotify.lite | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2398 | com.spotify.lite | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2484 | com.spotify.lite | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2561 | com.spotify.lite | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2634 | com.spotify.lite | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2712 | com.spotify.lite | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2784 | com.spotify.lite | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2861 | com.spotify.lite | /system/bin/app_process64 | — | app_process64 |
User: u0_a109 Integrity Level: UNKNOWN Exit code: 256 | ||||
| 2862 | com.spotify.lite | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
363
Text files
126
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2293 | app_process64 | /data/data/com.spotify.lite/files/PersistedInstallation8272997127740466087tmp | binary | |
MD5:— | SHA256:— | |||
| 2293 | app_process64 | /data/data/com.spotify.lite/files/PersistedInstallation.W0RFRkFVTFRd+MTo1MzExMzA3ODkxNzc6YW5kcm9pZDoyY2E5NzljYzMyODQ4NjBj.json | binary | |
MD5:— | SHA256:— | |||
| 2293 | app_process64 | /data/data/com.spotify.lite/files/.com.google.firebase.crashlytics/68684541007A-0001-08F5-9085D0FE082DBeginSession.cls_temp | binary | |
MD5:— | SHA256:— | |||
| 2293 | app_process64 | /data/data/com.spotify.lite/files/.com.google.firebase.crashlytics-ndk/68684541007A-0001-08F5-9085D0FE082D/session.json | binary | |
MD5:— | SHA256:— | |||
| 2293 | app_process64 | /data/data/com.spotify.lite/no_backup/androidx.work.workdb-journal | binary | |
MD5:— | SHA256:— | |||
| 2293 | app_process64 | /data/data/com.spotify.lite/no_backup/androidx.work.workdb-wal | binary | |
MD5:— | SHA256:— | |||
| 2293 | app_process64 | /data/data/com.spotify.lite/files/.com.google.firebase.crashlytics/68684541007A-0001-08F5-9085D0FE082DSessionApp.cls_temp | binary | |
MD5:— | SHA256:— | |||
| 2293 | app_process64 | /data/data/com.spotify.lite/files/.com.google.firebase.crashlytics-ndk/68684541007A-0001-08F5-9085D0FE082D/app.json | binary | |
MD5:— | SHA256:— | |||
| 2293 | app_process64 | /data/data/com.spotify.lite/shared_prefs/com.google.firebase.crashlytics.xml | xml | |
MD5:— | SHA256:— | |||
| 2293 | app_process64 | /data/data/com.spotify.lite/shared_prefs/com.facebook.sdk.appEventPreferences.xml | xml | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
112
TCP/UDP connections
102
DNS requests
20
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | — | 142.250.185.164:443 | https://www.google.com/generate_204 | unknown | — | — | unknown |
— | — | GET | 204 | 142.250.186.132:80 | http://www.google.com/gen_204 | unknown | — | — | whitelisted |
— | — | GET | 200 | 151.101.3.42:443 | https://open.spotify.com/.well-known/assetlinks.json | unknown | text | 2.86 Kb | whitelisted |
— | — | GET | 200 | 151.101.67.42:443 | https://spotify.link/.well-known/assetlinks.json | unknown | text | 2.07 Kb | unknown |
— | — | GET | 200 | 151.101.131.42:443 | https://spotify.test-app.link/.well-known/assetlinks.json | unknown | text | 1.65 Kb | unknown |
— | — | GET | 200 | 151.101.195.42:443 | https://spotify-alternate.test-app.link/.well-known/assetlinks.json | unknown | text | 1.65 Kb | unknown |
— | — | GET | 200 | 151.101.3.42:443 | https://spotify-alternate.app.link/.well-known/assetlinks.json | unknown | text | 2.07 Kb | whitelisted |
— | — | GET | 200 | 157.240.0.13:443 | https://graph.facebook.com/v15.0/app?access_token=174829003346%7C892e40f54a536e2df0041ee946fc5c7d&fields=supports_implicit_sdk_logging%2Cgdpv4_nux_content%2Cgdpv4_nux_enabled%2Candroid_dialog_configs%2Candroid_sdk_error_categories%2Capp_events_session_timeout%2Capp_events_feature_bitmask%2Cauto_event_mapping_android%2Cseamless_login%2Csmart_login_bookmark_icon_url%2Csmart_login_menu_icon_url%2Crestrictive_data_filter_params%2Caam_rules%2Csuggested_events_setting&format=json&sdk=android | unknown | binary | 2.34 Kb | whitelisted |
— | — | POST | 200 | 142.250.185.170:443 | https://firebaseinstallations.googleapis.com/v1/projects/spotify-lite/installations | unknown | binary | 622 b | whitelisted |
— | — | GET | 200 | 157.240.0.13:443 | https://graph.facebook.com/v15.0/app/mobile_sdk_gk?access_token=174829003346%7C892e40f54a536e2df0041ee946fc5c7d&fields=gatekeepers&format=json&sdk_version=15.0.1&sdk=android&platform=android | unknown | binary | 3.23 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
451 | mdnsd | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 142.250.185.99:80 | connectivitycheck.gstatic.com | GOOGLE | US | whitelisted |
— | — | 142.250.186.132:443 | www.google.com | GOOGLE | US | whitelisted |
— | — | 142.250.186.132:80 | www.google.com | GOOGLE | US | whitelisted |
574 | app_process64 | 216.239.35.12:123 | time.android.com | — | — | whitelisted |
1755 | app_process64 | 108.177.15.81:443 | staging-remoteprovisioning.sandbox.googleapis.com | GOOGLE | US | whitelisted |
1795 | app_process64 | 3.171.214.95:443 | spotify.app.link | — | US | whitelisted |
1795 | app_process64 | 151.101.3.42:443 | open.spotify.com | FASTLY | US | whitelisted |
1795 | app_process64 | 3.171.214.49:443 | spotify.test-app.link | — | US | unknown |
1795 | app_process64 | 52.8.7.198:443 | spotify.link | AMAZON-02 | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| whitelisted |
connectivitycheck.gstatic.com |
| whitelisted |
google.com |
| whitelisted |
time.android.com |
| whitelisted |
staging-remoteprovisioning.sandbox.googleapis.com |
| whitelisted |
spotify.app.link |
| whitelisted |
open.spotify.com |
| whitelisted |
spotify.test-app.link |
| unknown |
spotify-alternate.test-app.link |
| unknown |
spotify.link |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Android Device Connectivity Check |
— | — | Misc activity | ET INFO Android Device Connectivity Check |