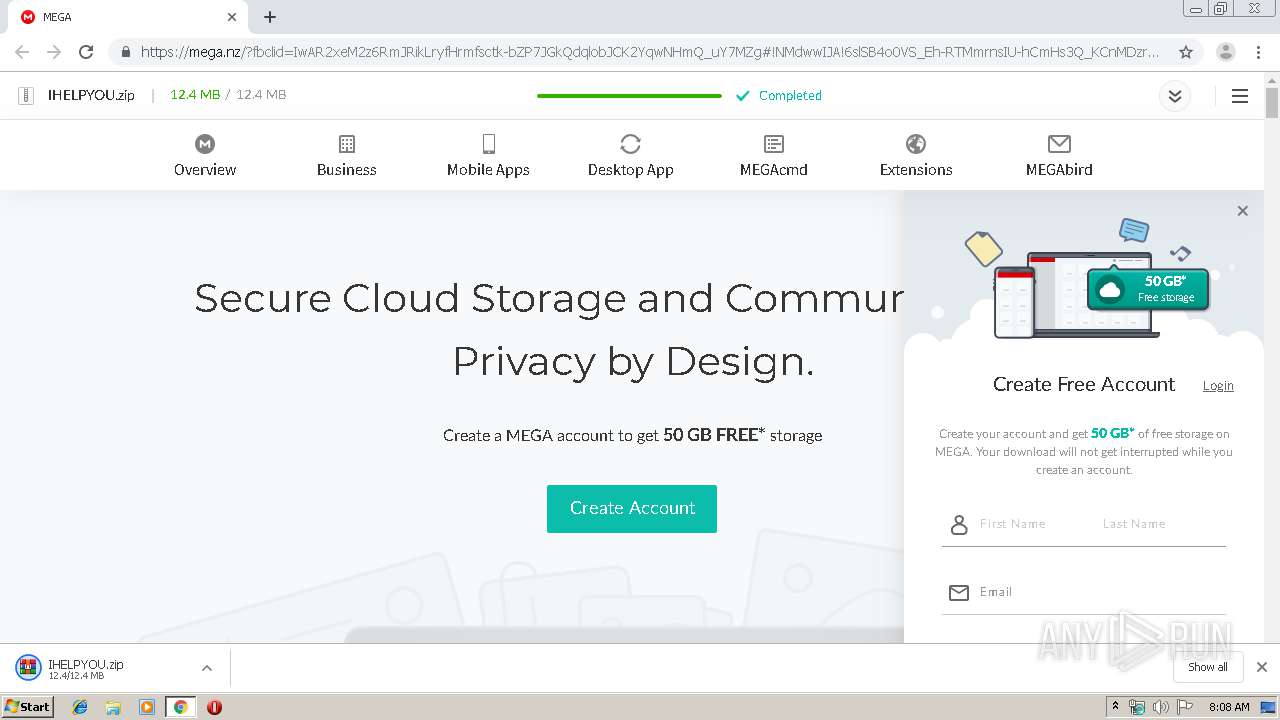
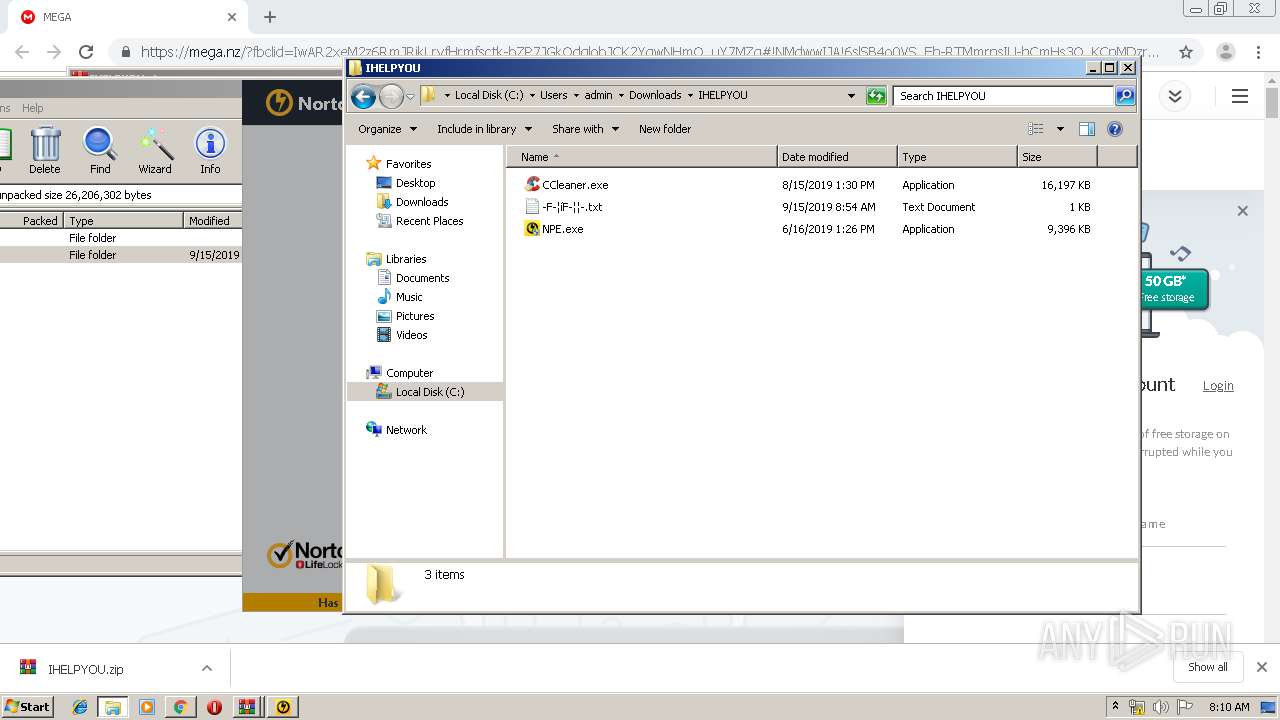
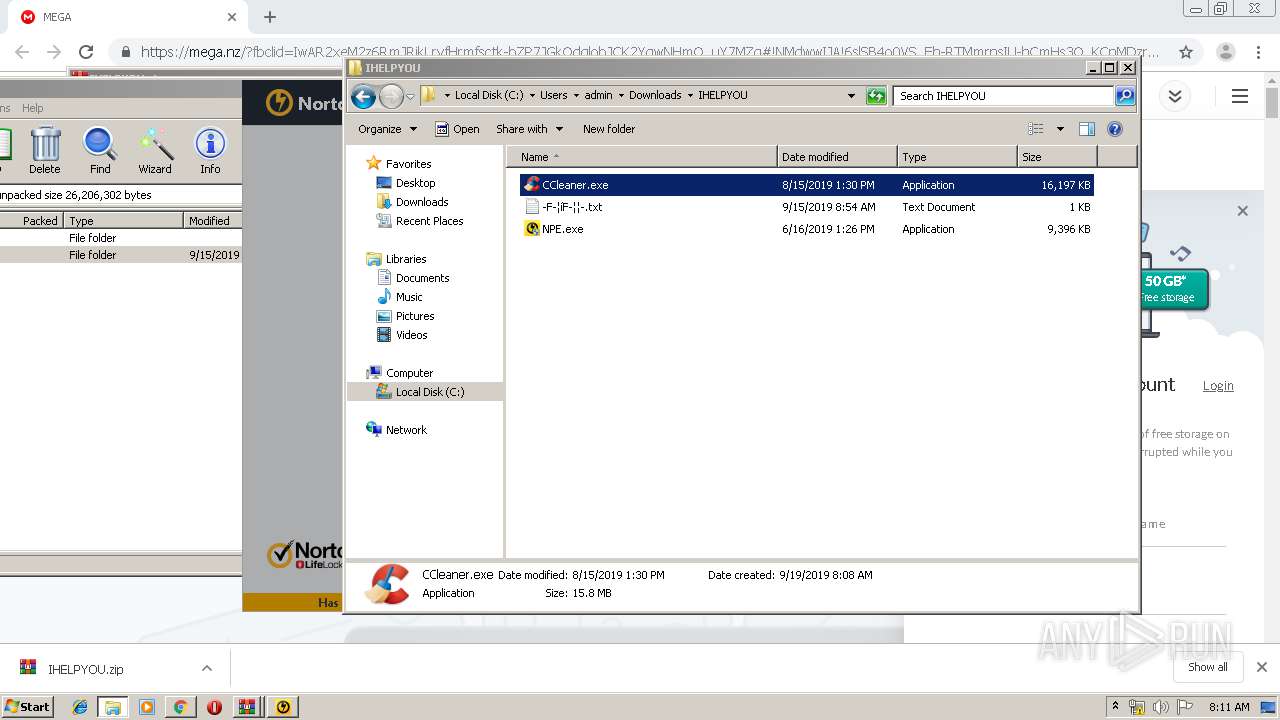
| URL: | https://mega.nz/?fbclid=IwAR2xeM2z6RmJRikLryfHrmfsctk-bZP7JGkQdqlobJCK2YqwNHmQ_uY7MZg#!NMdwwIJA!6slSB4o0VS_Eh-RTMmrnsIU-hCmHs3Q_KCnMDzr3D_Q |
| Full analysis: | https://app.any.run/tasks/4cba808e-5574-4adb-8f9e-829462a2a37e |
| Verdict: | Malicious activity |
| Analysis date: | September 19, 2019, 07:07:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 216D34857F5AB87AB365E7A95AA0F813 |
| SHA1: | 7C654527AFBC763098045FEAF4679039A19BF303 |
| SHA256: | 1A36ACD95E1ED4FCFB3C11D42D7D15BF7AB05B585268C056A50CDC06F47E23CC |
| SSDEEP: | 3:N8X/iabGJOSkdF7VOCuDBoI6TJKHRXort0Q8bKGrB689J20aw7WlQR0FmcJGh60:2hbj72doIQcart0Q8mcPTL7iK0F5JGs0 |
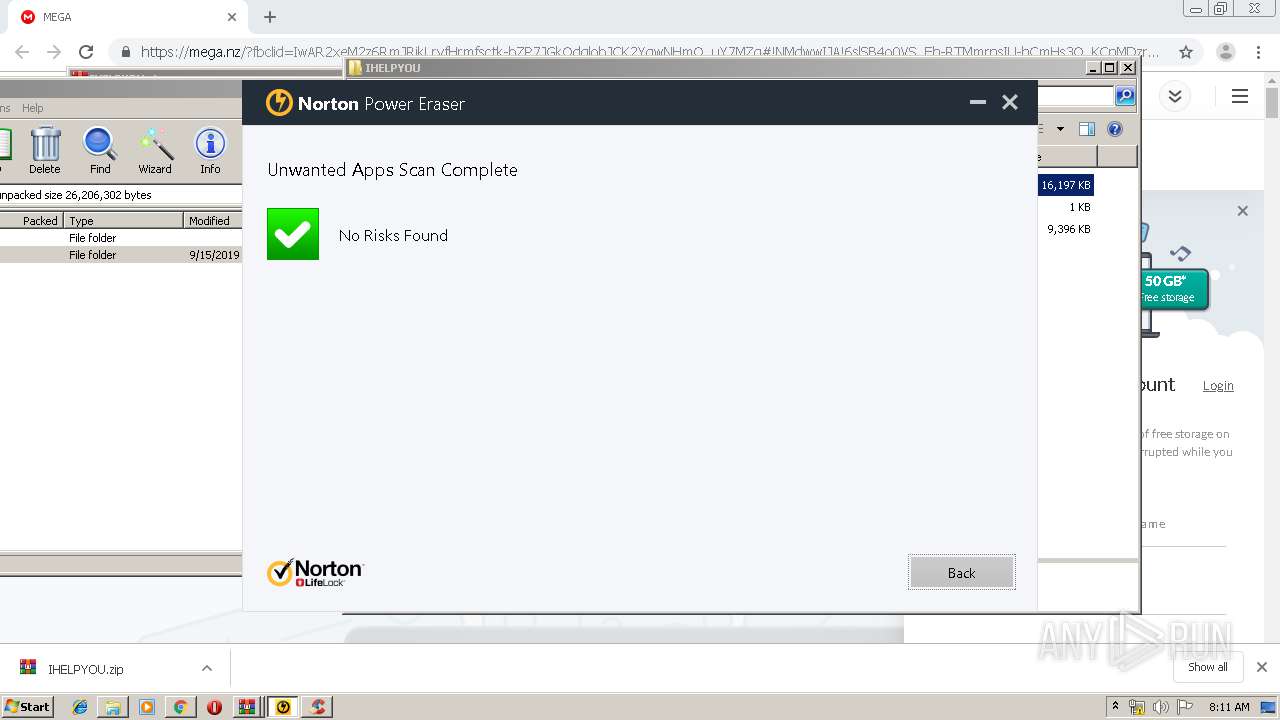
MALICIOUS
No malicious indicators.SUSPICIOUS
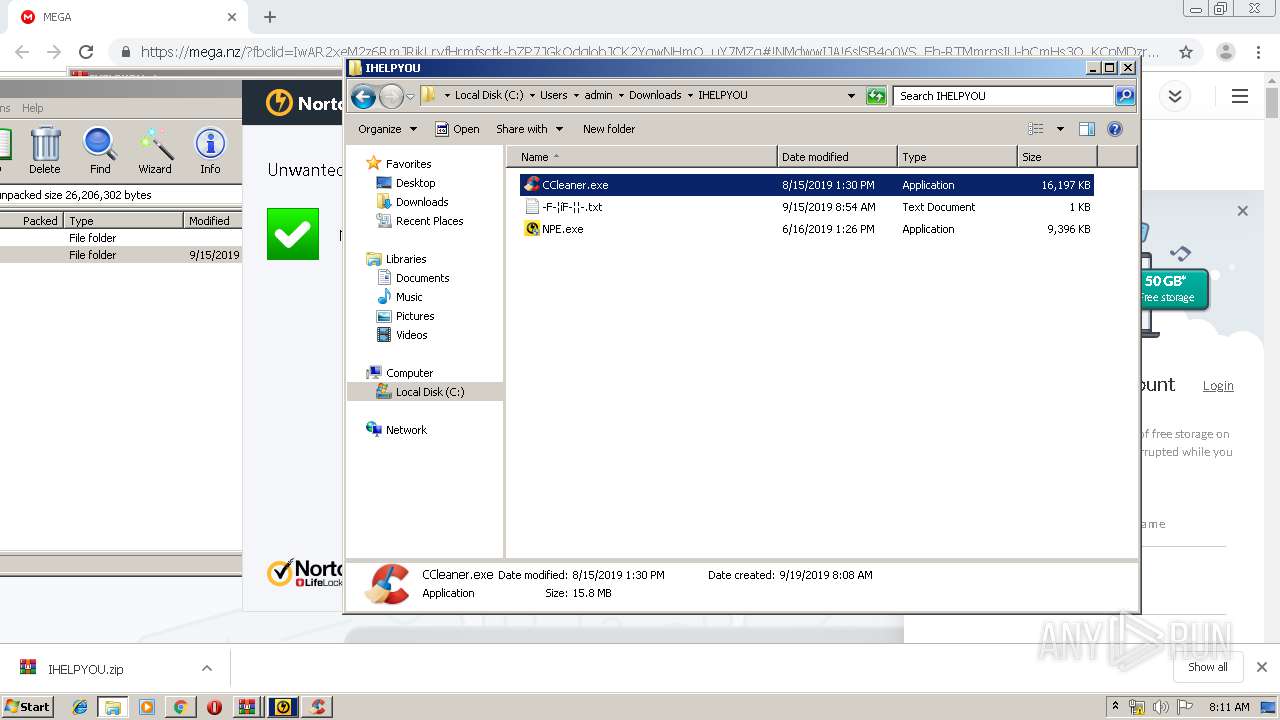
Creates files in the Windows directory
- NPE.exe (PID: 2948)
Creates files in the driver directory
- NPE.exe (PID: 2948)
Creates files in the program directory
- NPE.exe (PID: 2948)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2812)
Executable content was dropped or overwritten
- NPE.exe (PID: 2948)
Removes files from Windows directory
- NPE.exe (PID: 2948)
INFO
Manual execution by user
- NOTEPAD.EXE (PID: 3420)
- NPE.exe (PID: 2948)
- WinRAR.exe (PID: 3844)
- WinRAR.exe (PID: 3836)
- NPE.exe (PID: 3200)
Reads the hosts file
- chrome.exe (PID: 2376)
- chrome.exe (PID: 2812)
- NPE.exe (PID: 2948)
Application launched itself
- chrome.exe (PID: 2812)
Reads settings of System Certificates
- NPE.exe (PID: 2948)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
66
Monitored processes
27
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2376 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,4756398656555230842,14661670697041074113,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=18147687699976492502 --mojo-platform-channel-handle=1640 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2584 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,4756398656555230842,14661670697041074113,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=10264212087423042207 --mojo-platform-channel-handle=3428 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2720 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,4756398656555230842,14661670697041074113,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=696085173335714024 --mojo-platform-channel-handle=3492 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2756 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,4756398656555230842,14661670697041074113,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=18257966198747632580 --mojo-platform-channel-handle=3564 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2784 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,4756398656555230842,14661670697041074113,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=11826672243152545657 --mojo-platform-channel-handle=3532 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2812 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "https://mega.nz/?fbclid=IwAR2xeM2z6RmJRikLryfHrmfsctk-bZP7JGkQdqlobJCK2YqwNHmQ_uY7MZg#!NMdwwIJA!6slSB4o0VS_Eh-RTMmrnsIU-hCmHs3Q_KCnMDzr3D_Q" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2876 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2816 --on-initialized-event-handle=312 --parent-handle=316 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
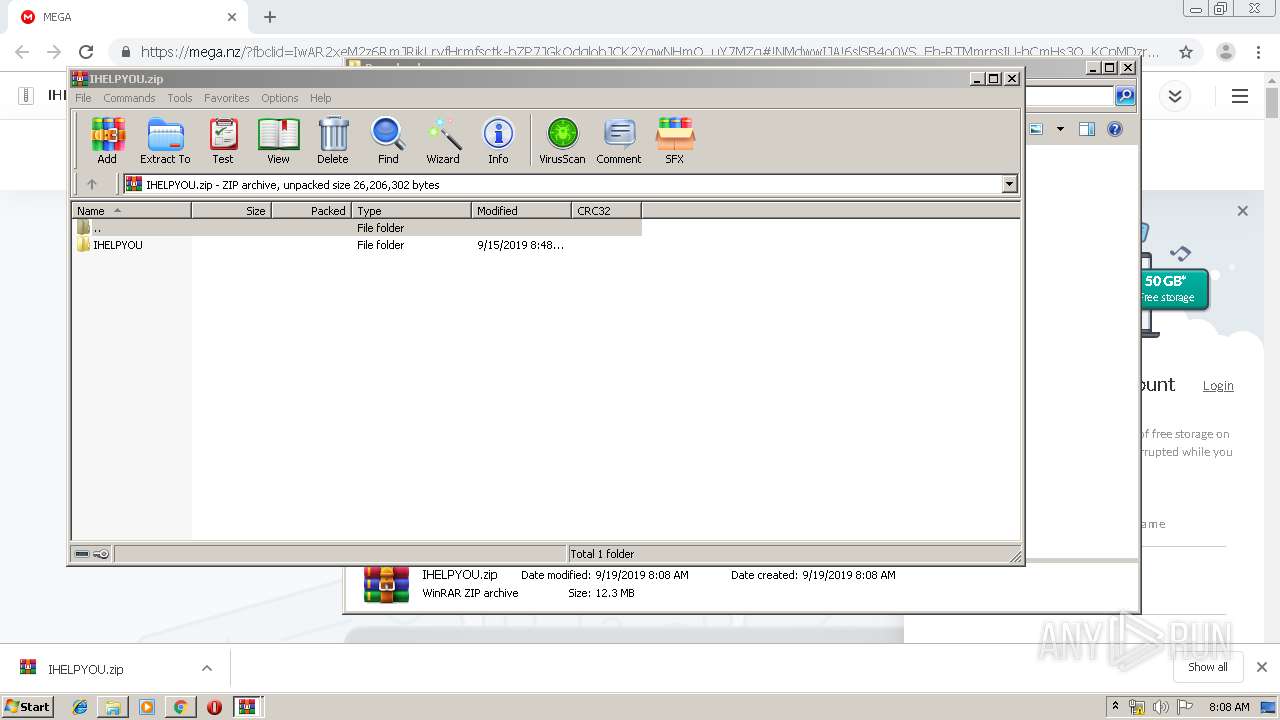
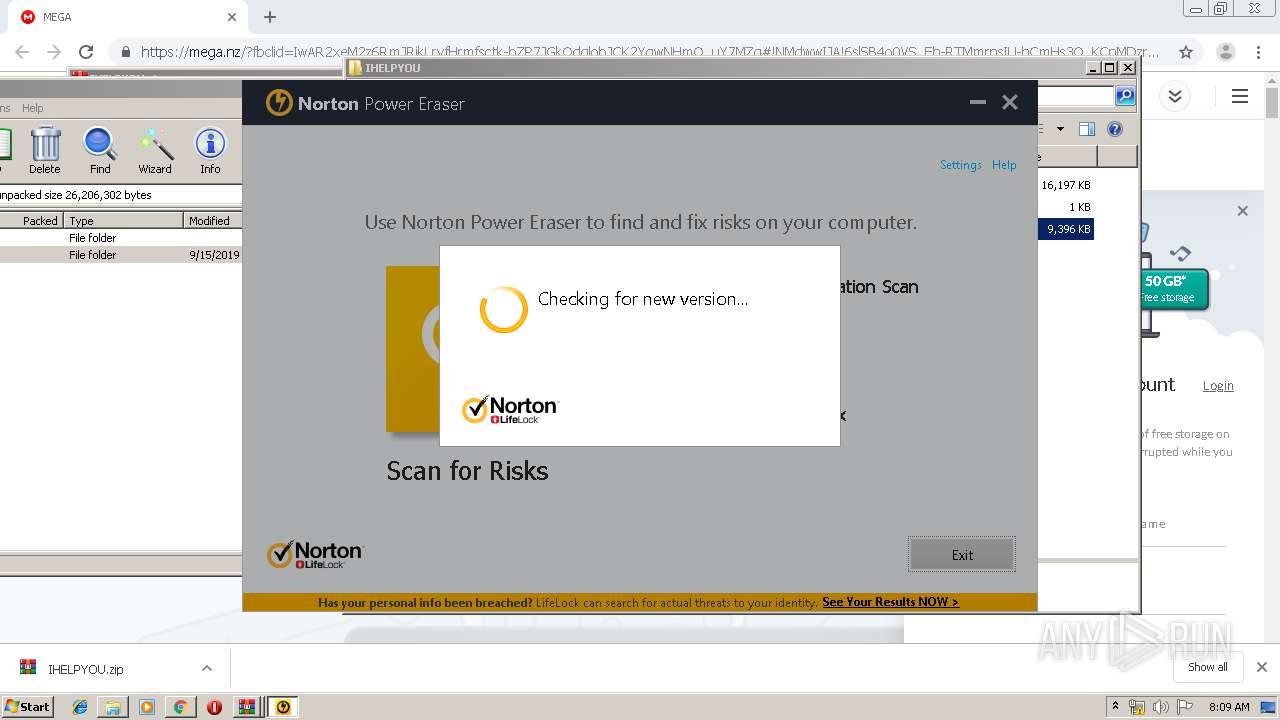
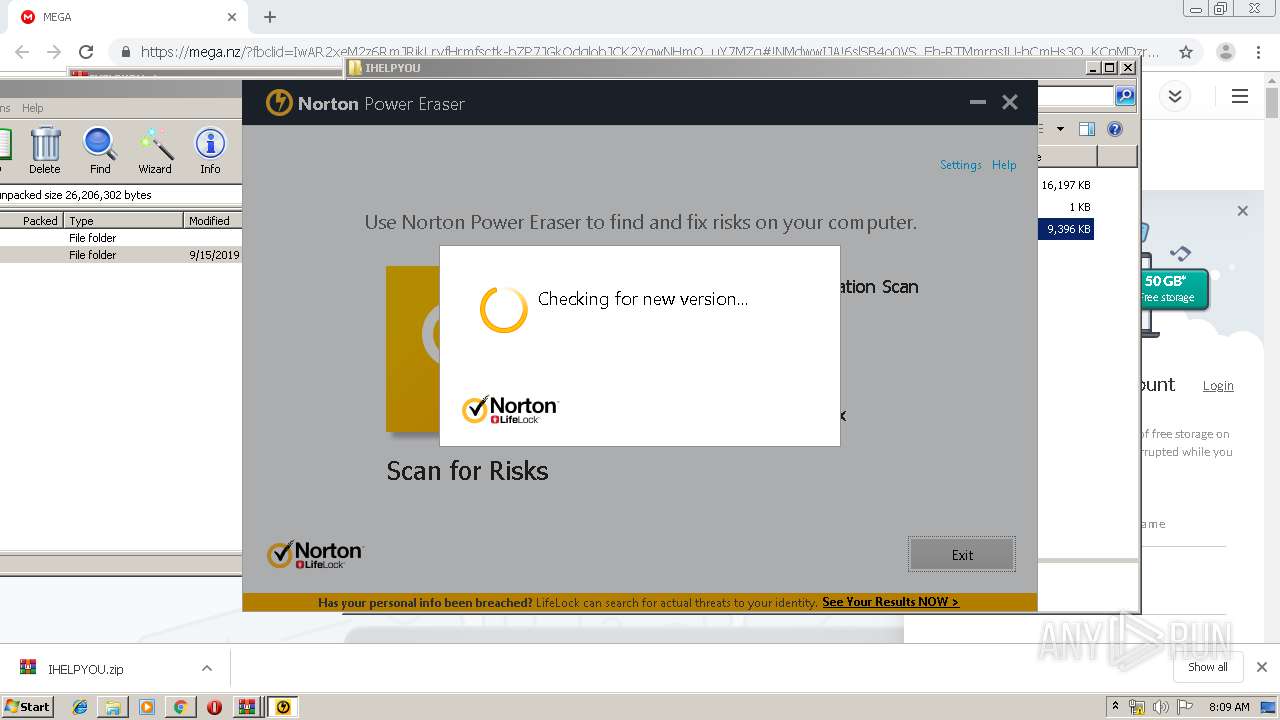
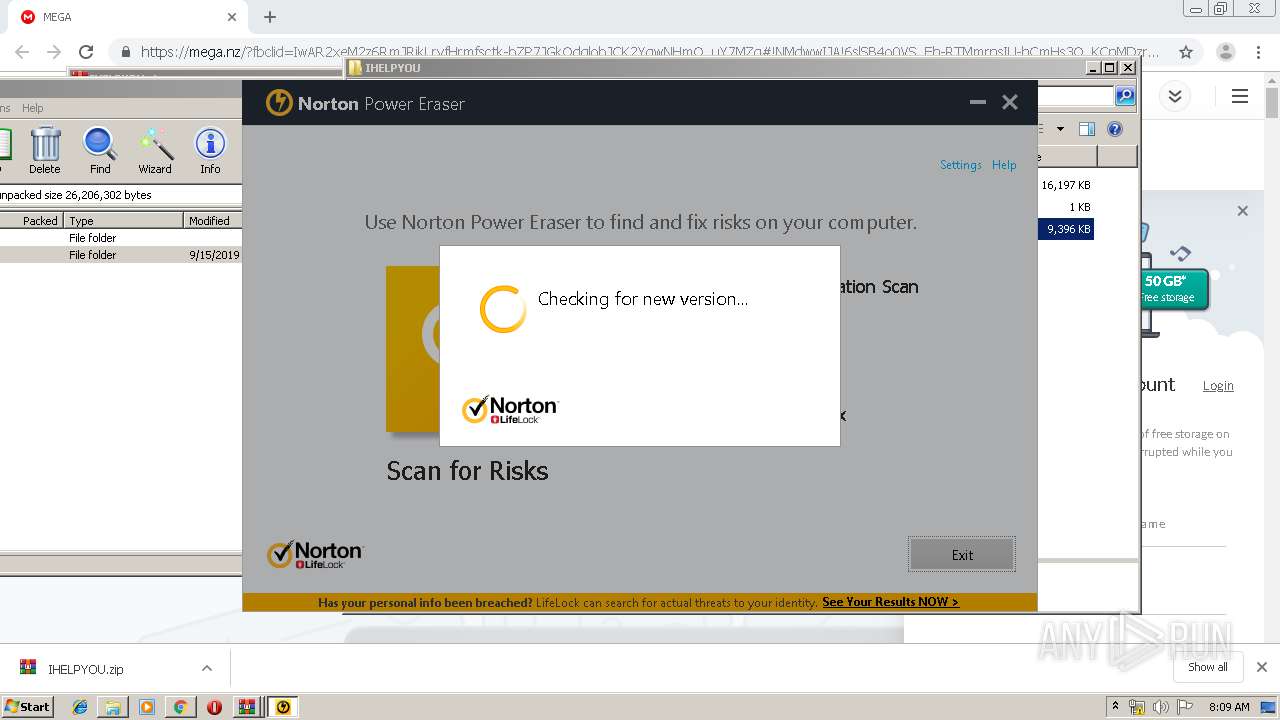
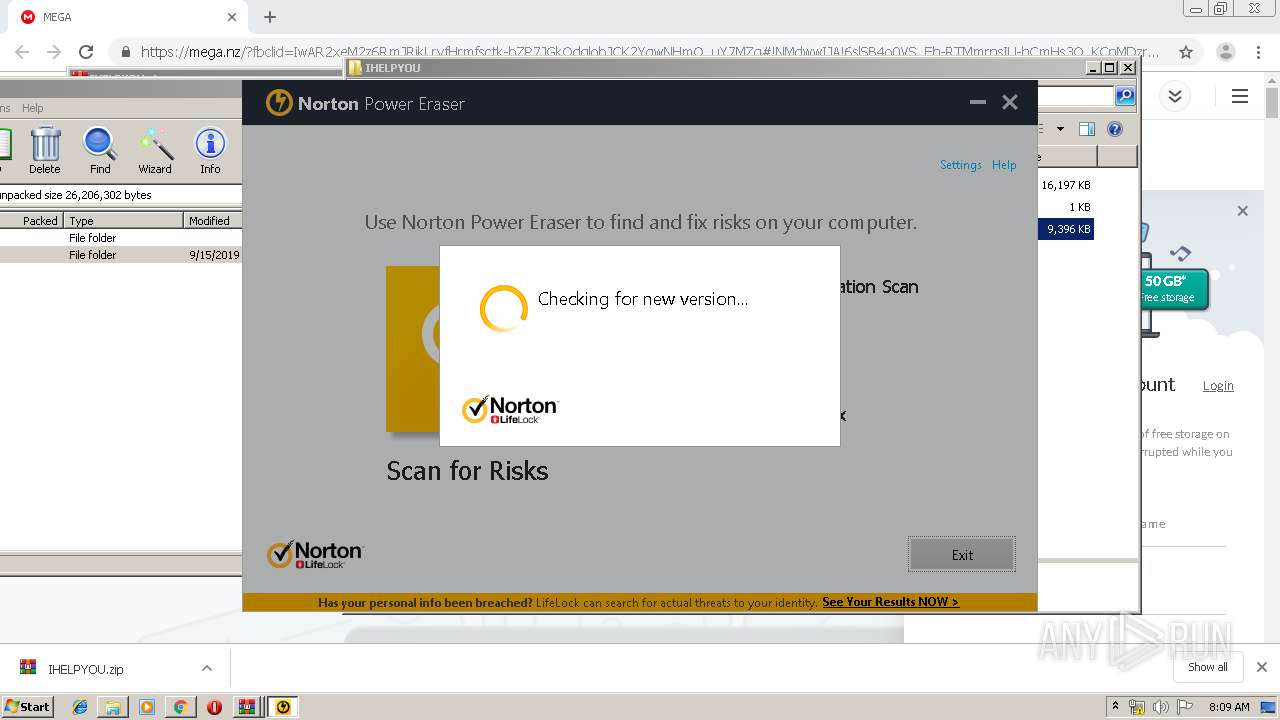
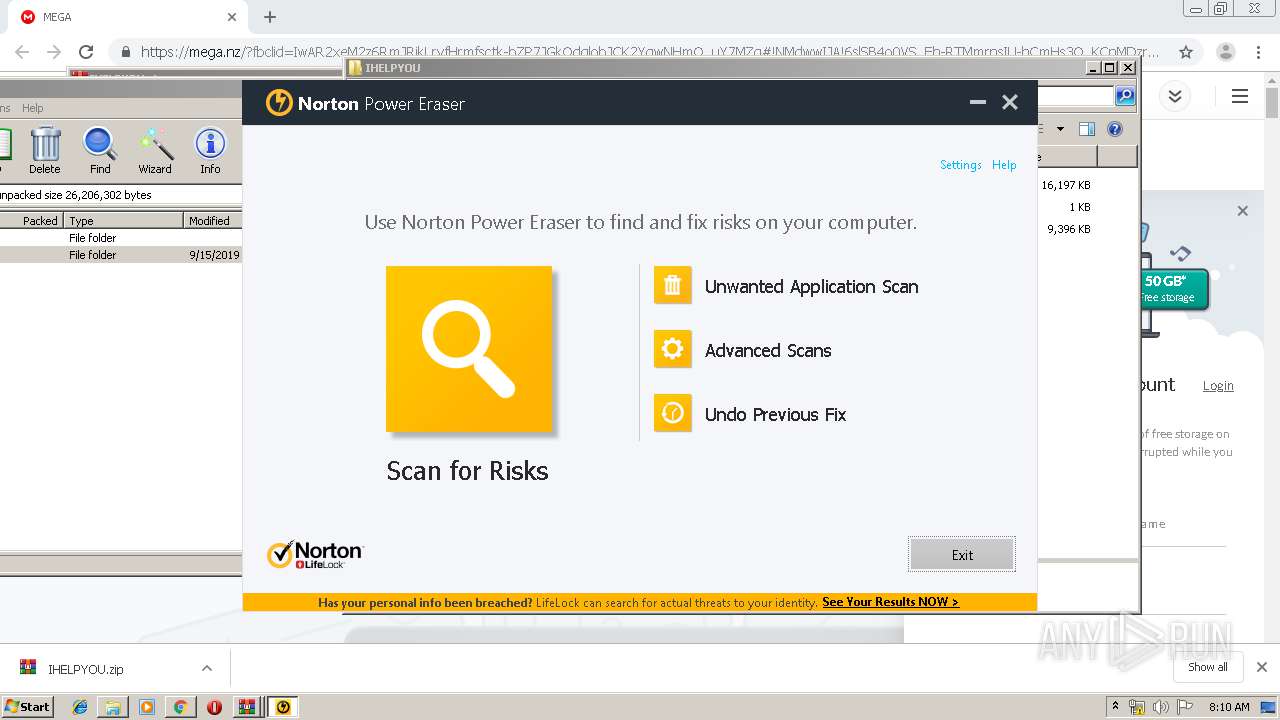
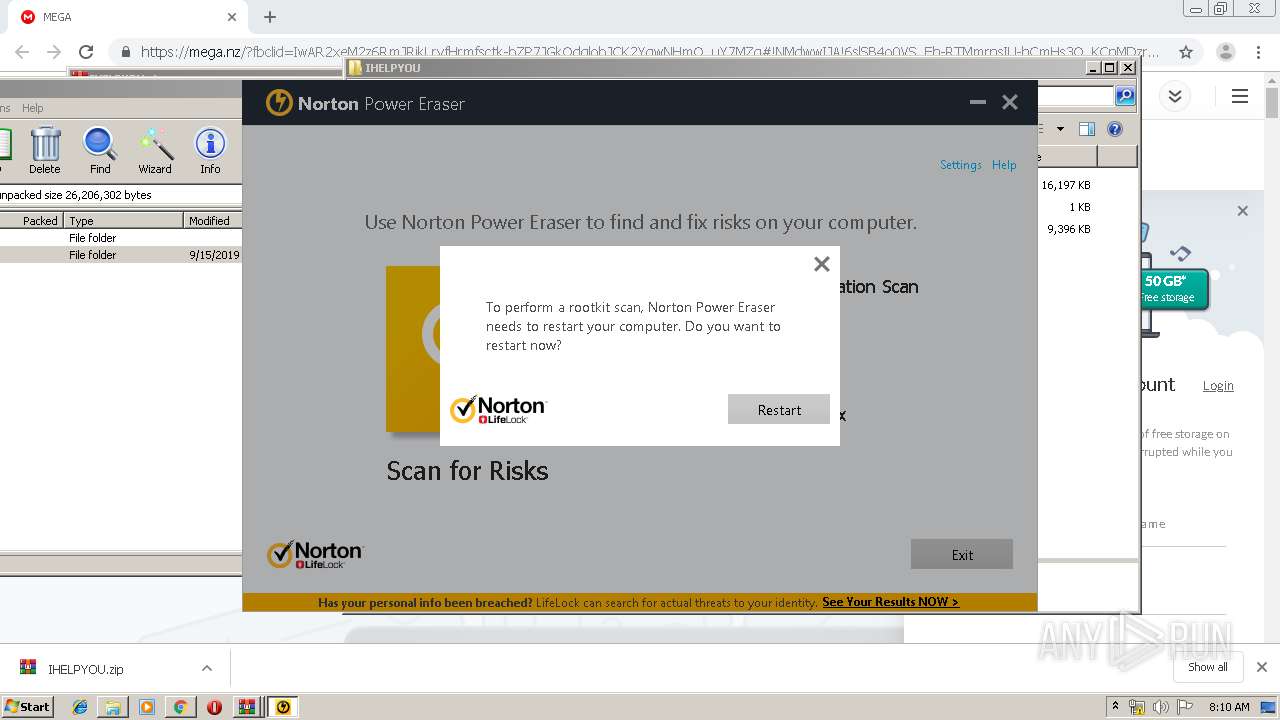
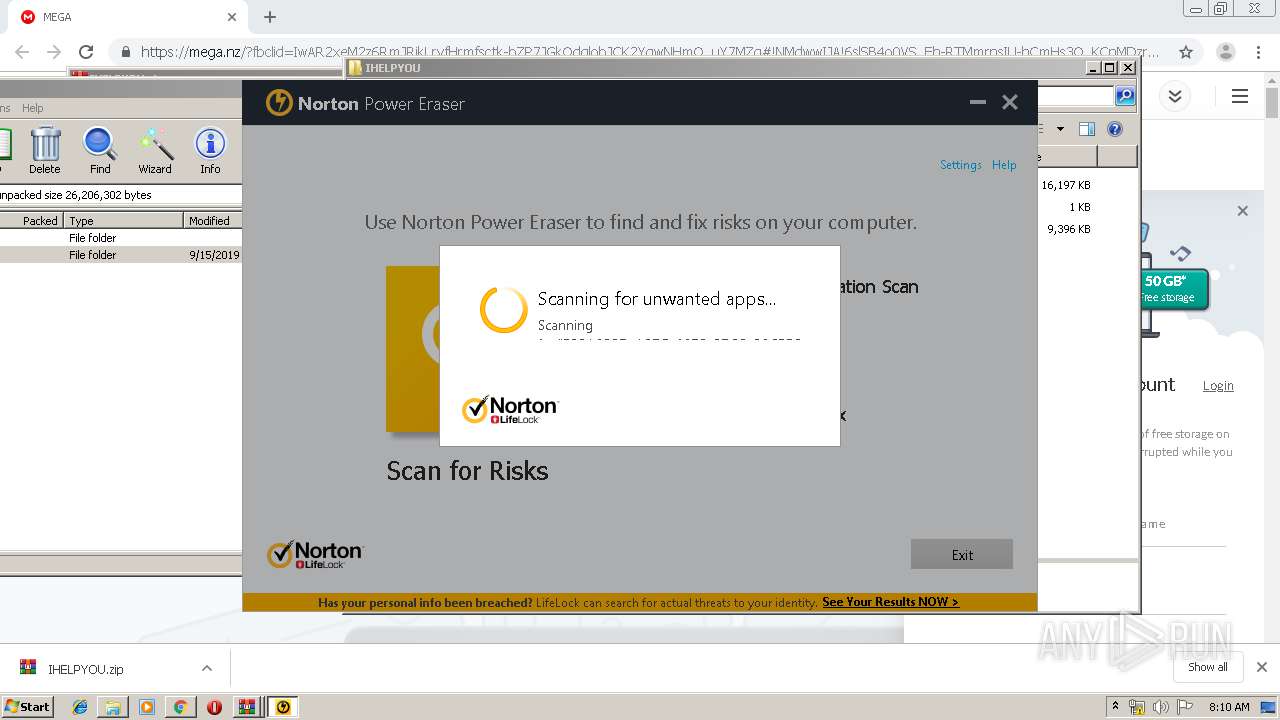
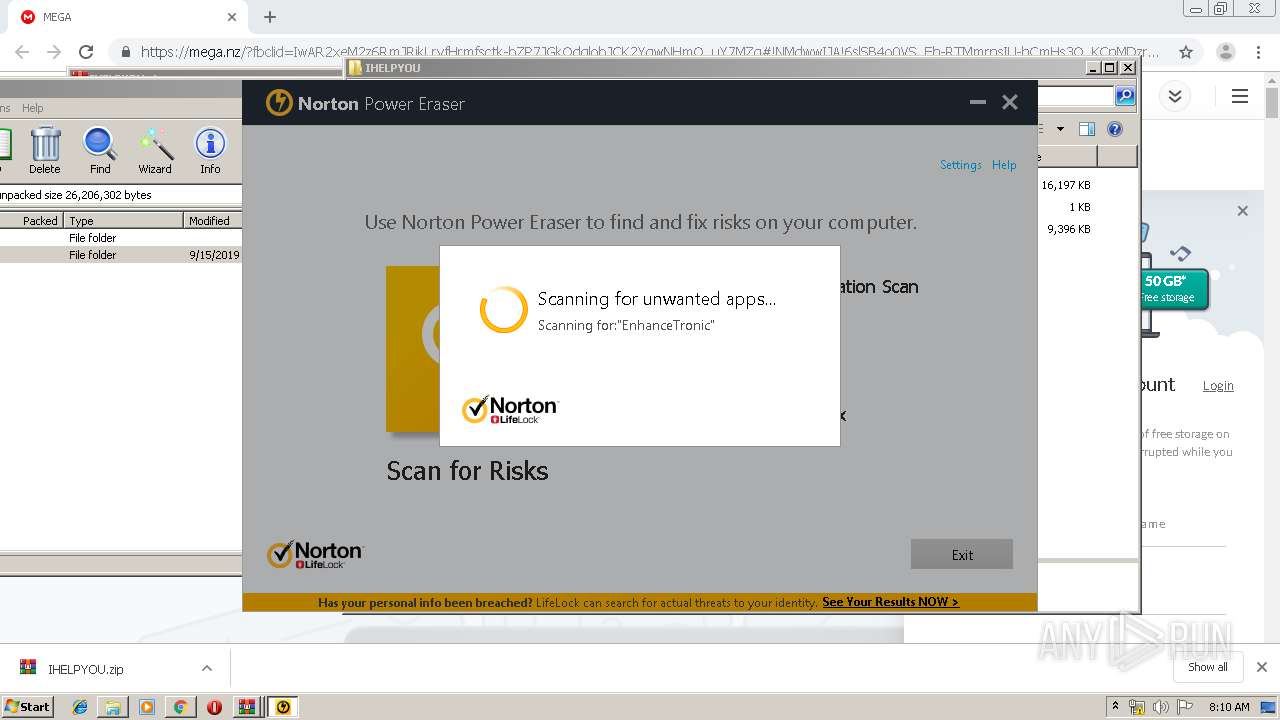
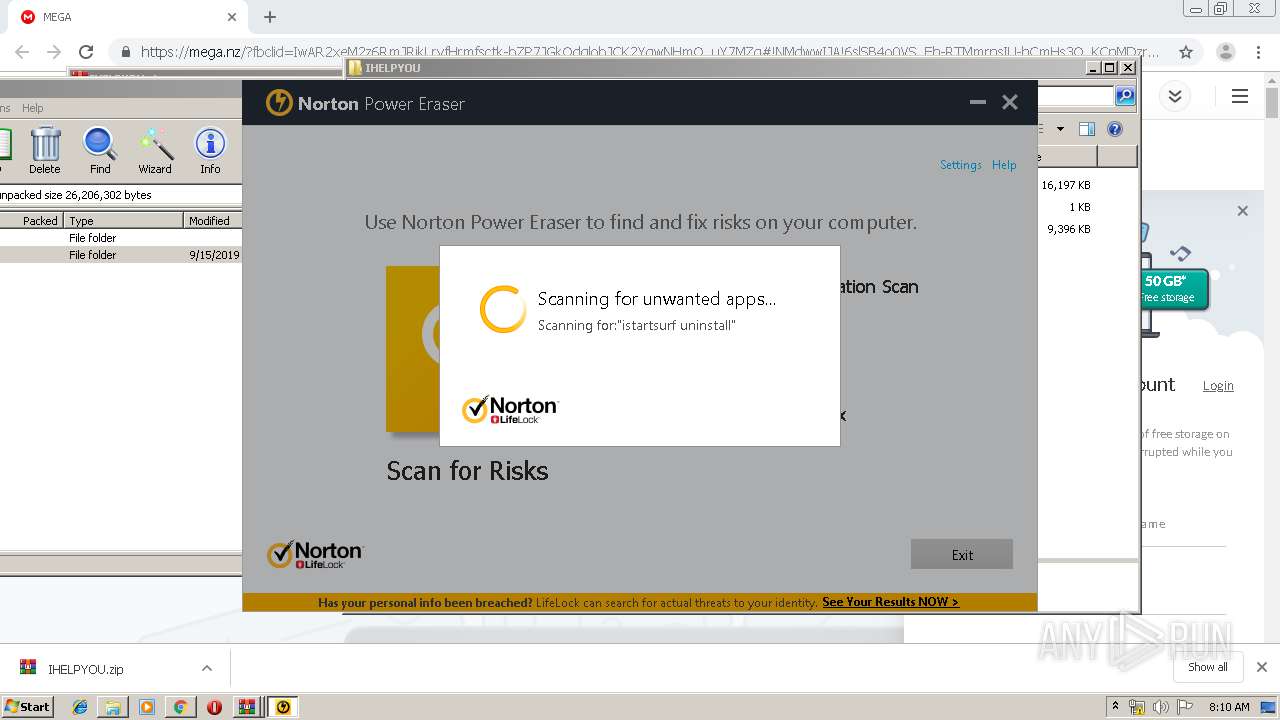
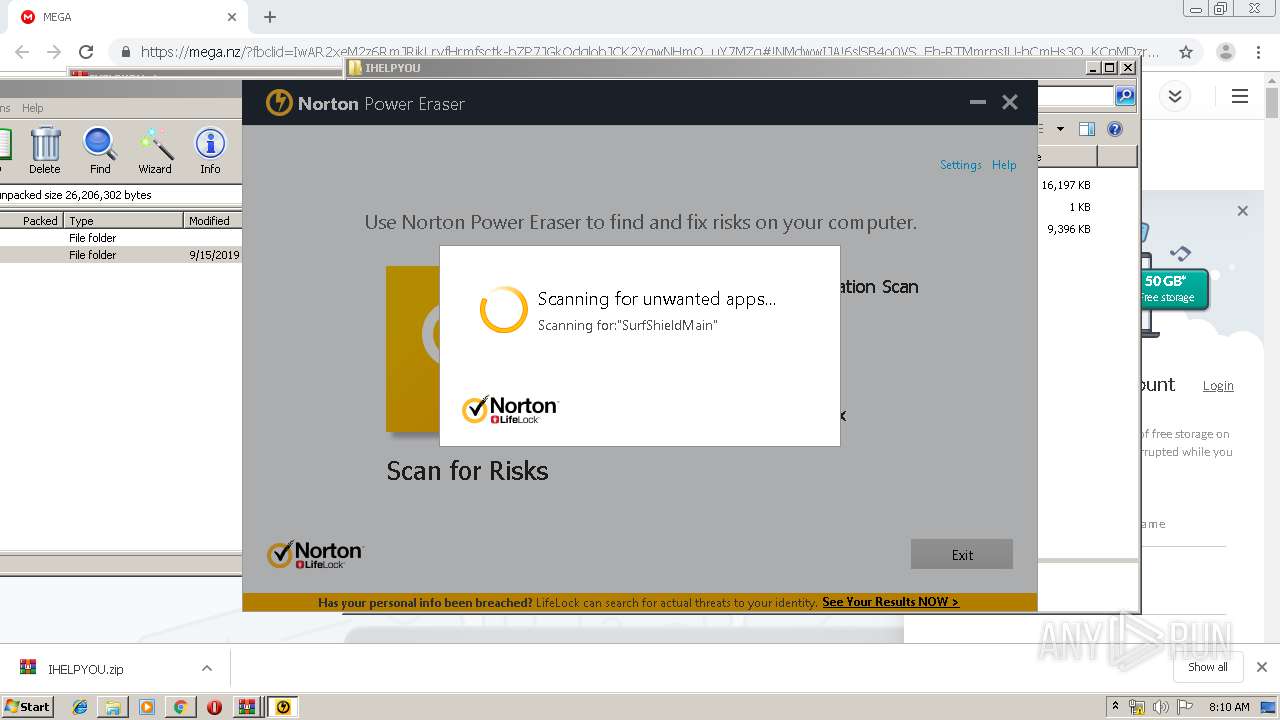
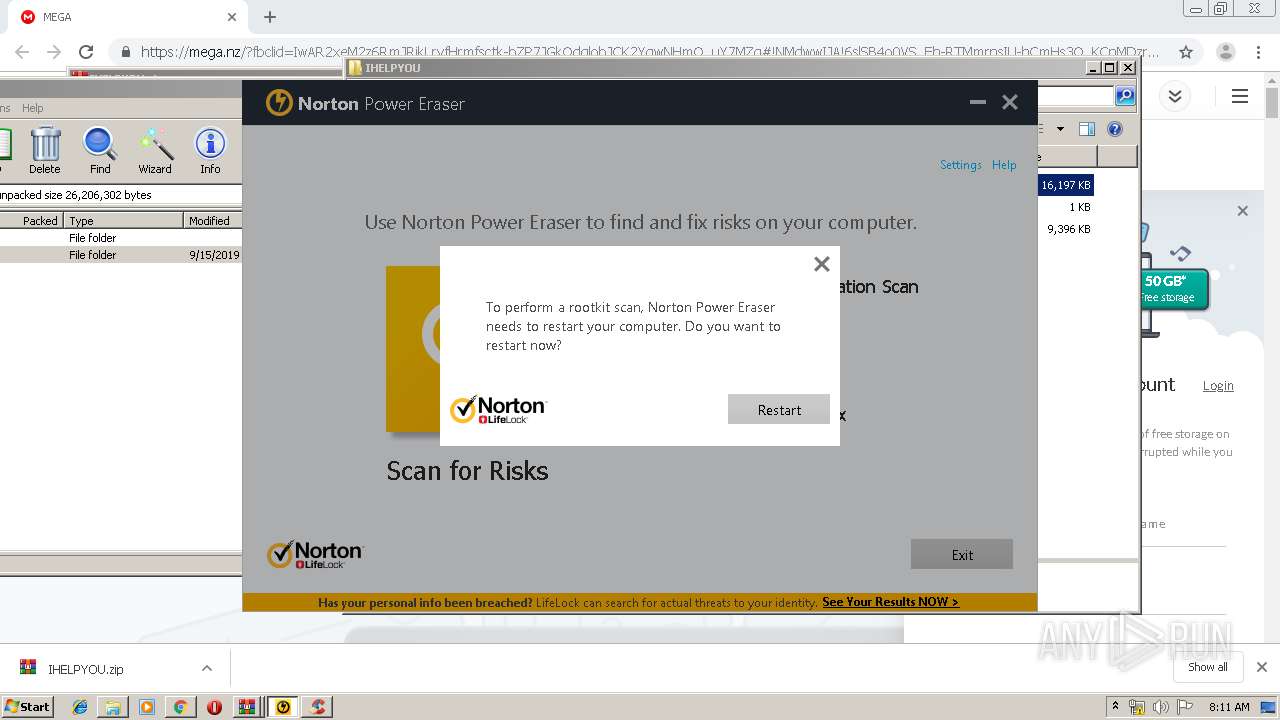
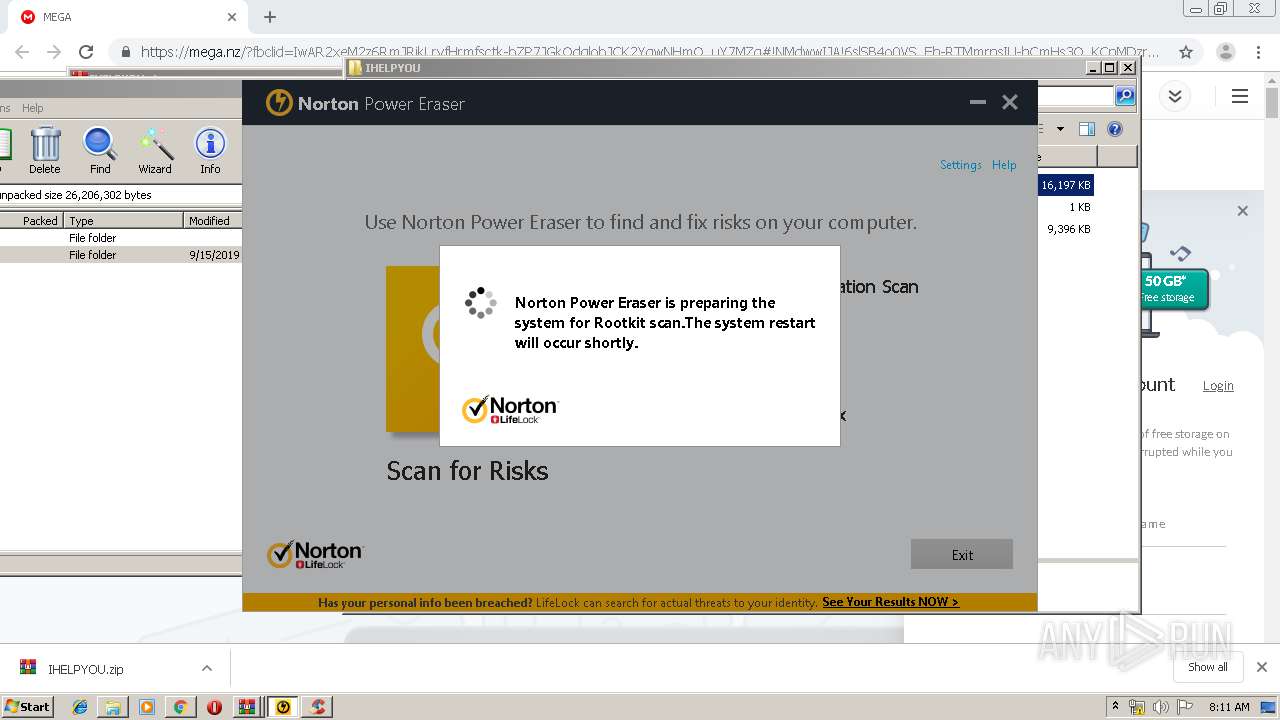
| 2948 | "C:\Users\admin\Downloads\IHELPYOU\NPE.exe" | C:\Users\admin\Downloads\IHELPYOU\NPE.exe | explorer.exe | ||||||||||||
User: admin Company: Symantec Corporation Integrity Level: HIGH Description: Norton Power Eraser Exit code: 0 Version: 5.3.0.47 Modules
| |||||||||||||||
| 3060 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,4756398656555230842,14661670697041074113,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=2299842080128737771 --mojo-platform-channel-handle=3912 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 3080 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1008,4756398656555230842,14661670697041074113,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=1849539481011758858 --renderer-client-id=17 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2776 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
1 954
Read events
1 797
Write events
151
Delete events
6
Modification events
| (PID) Process: | (2812) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2812) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2812) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2812) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2812) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2876) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2812-13213350465038250 |
Value: 259 | |||
| (PID) Process: | (2812) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2812) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2812) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 1512-13197841398593750 |
Value: 0 | |||
| (PID) Process: | (2812) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
1
Suspicious files
78
Text files
271
Unknown types
20
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2812 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2812 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2812 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2812 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF16a117.TMP | — | |
MD5:— | SHA256:— | |||
| 2812 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\9659559e-e739-4ee9-848f-f7c70a208843.tmp | — | |
MD5:— | SHA256:— | |||
| 2812 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000020.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2812 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2812 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 2812 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF16a155.TMP | text | |
MD5:— | SHA256:— | |||
| 2812 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old~RF16a1a3.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
71
DNS requests
34
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 151.101.2.109:80 | http://license.piriform.com/verify/?p=ccpro&c=cc&cv=5.61.7392&l=1033&lk=CJ9T-J7CU-SPNV-GWMB-WBEC&mk=IJR6-W5SV-5KYR-QBZD-6BY4-RN5Z-WAV9-RVK2-VJCA&mx=97B7721C4994E2556FF6A439510F665DB45337A341A47E15F4997584423BF714&gd=b72fc9d0-e691-4d02-bf89-b669089e91d3 | US | html | 5.58 Kb | whitelisted |
2948 | NPE.exe | GET | 200 | 152.195.132.112:80 | http://definitions.symantec.com/defs/dm/smrscd.7z | US | compressed | 6.36 Kb | malicious |
— | — | GET | 200 | 151.101.2.202:80 | http://www.ccleaner.com/auto?a=0&p=cc&v=5.61.7392&l=1033&lk=&mk=IJR6-W5SV-5KYR-QBZD-6BY4-RN5Z-WAV9-RVK2-VJCA&o=6.1W3&au=1&mx=97B7721C4994E2556FF6A439510F665DB45337A341A47E15F4997584423BF714&gd=b72fc9d0-e691-4d02-bf89-b669089e91d3 | US | text | 23 b | whitelisted |
— | — | GET | 200 | 152.195.132.112:80 | http://definitions.symantec.com/defs/dm/smrscd.7z | US | compressed | 6.36 Kb | malicious |
2376 | chrome.exe | GET | 302 | 216.58.208.46:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 516 b | whitelisted |
2376 | chrome.exe | GET | 200 | 84.15.64.141:80 | http://r2---sn-cpux-8ov6.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=85.206.166.82&mm=28&mn=sn-cpux-8ov6&ms=nvh&mt=1568876591&mv=u&mvi=1&pl=20&shardbypass=yes | LT | crx | 862 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2376 | chrome.exe | 89.44.169.132:443 | eu.static.mega.co.nz | Datacenter Luxembourg S.A. | LU | suspicious |
2376 | chrome.exe | 172.217.18.3:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2376 | chrome.exe | 31.216.148.10:443 | mega.nz | Datacenter Luxembourg S.A. | LU | unknown |
2376 | chrome.exe | 172.217.21.196:443 | www.google.com | Google Inc. | US | whitelisted |
2376 | chrome.exe | 172.217.22.1:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
2376 | chrome.exe | 89.44.168.73:443 | gfs270n363.userstorage.mega.co.nz | Datacenter Luxembourg S.A. | LU | unknown |
2376 | chrome.exe | 172.217.21.227:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2376 | chrome.exe | 172.217.18.110:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
2948 | NPE.exe | 2.20.20.197:443 | support.norton.com | Akamai International B.V. | — | whitelisted |
2376 | chrome.exe | 216.58.206.3:443 | www.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
mega.nz |
| whitelisted |
accounts.google.com |
| shared |
safebrowsing.googleapis.com |
| whitelisted |
clients1.google.com |
| whitelisted |
eu.static.mega.co.nz |
| shared |
g.api.mega.co.nz |
| shared |
www.google.com |
| malicious |
clients2.google.com |
| whitelisted |
clients2.googleusercontent.com |
| whitelisted |