| File name: | TeamViewer11_Exit.hta |
| Full analysis: | https://app.any.run/tasks/dee0895d-1b9e-4037-9236-70c3d1c850a2 |
| Verdict: | Malicious activity |
| Analysis date: | March 18, 2024, 05:55:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | data |
| MD5: | 2703F13A3876449D71A78182793D883A |
| SHA1: | 90D25BA6E6F61FE9A1A8AF67444021A415C30FEF |
| SHA256: | 1A1FF5EC6C6C7150124555B7714A4BD62C8C9BF96FECF1931EE20891DA06BEF4 |
| SSDEEP: | 24:p37rysGWgjN9TLk/4TolcTCTVcxBOU9m9TnG10taZl5B1S:pf1GVN9Hkq4mCTVPtGitab5BE |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Internet Settings
- mshta.exe (PID: 4008)
- mshta.exe (PID: 2088)
- mshta.exe (PID: 1784)
- mshta.exe (PID: 552)
Adds/modifies Windows certificates
- mshta.exe (PID: 552)
- mshta.exe (PID: 1784)
- mshta.exe (PID: 2088)
- mshta.exe (PID: 4008)
INFO
Reads Internet Explorer settings
- mshta.exe (PID: 552)
- mshta.exe (PID: 2088)
- mshta.exe (PID: 4008)
- mshta.exe (PID: 1784)
Application launched itself
- iexplore.exe (PID: 3100)
Manual execution by a user
- mshta.exe (PID: 2088)
- mshta.exe (PID: 1784)
- mshta.exe (PID: 552)
Checks proxy server information
- mshta.exe (PID: 2088)
- mshta.exe (PID: 552)
- mshta.exe (PID: 4008)
- mshta.exe (PID: 1784)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
47
Monitored processes
7
Malicious processes
0
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 548 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3100 CREDAT:2233609 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 552 | "C:\Windows\System32\mshta.exe" "C:\Users\admin\Desktop\TeamViewer11_Exit.hta" | C:\Windows\System32\mshta.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1784 | "C:\Windows\System32\mshta.exe" "C:\Users\admin\AppData\Local\Temp\TeamViewer11_Exit.hta" | C:\Windows\System32\mshta.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2088 | "C:\Windows\System32\mshta.exe" "C:\Users\admin\Desktop\TeamViewer11_Exit.hta" | C:\Windows\System32\mshta.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3100 | "C:\Program Files\Internet Explorer\iexplore.exe" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3780 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3100 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 4008 | "C:\Windows\System32\mshta.exe" "C:\Users\admin\AppData\Local\Temp\TeamViewer11_Exit.hta" | C:\Windows\System32\mshta.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
29 724
Read events
29 029
Write events
464
Delete events
231
Modification events
| (PID) Process: | (4008) mshta.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4008) mshta.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4008) mshta.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4008) mshta.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4008) mshta.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (4008) mshta.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyServer |
Value: | |||
| (PID) Process: | (4008) mshta.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyOverride |
Value: | |||
| (PID) Process: | (4008) mshta.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoConfigURL |
Value: | |||
| (PID) Process: | (4008) mshta.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoDetect |
Value: | |||
| (PID) Process: | (4008) mshta.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005C010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
0
Suspicious files
7
Text files
8
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1784 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | der | |
MD5:C4589D928BDE093A8B3C4AC1B2E9A472 | SHA256:C04B0BCC650D2A58D5F3846C775FDD29C4257063540FC79AC1C5043AEEE22FE1 | |||
| 1784 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\index[1].htm | html | |
MD5:2D21874099B2E58A5A18B7098FF80F36 | SHA256:2236DAAB42DD69551AAC36CE3BC90F1AB0DE9A6457BD652CE730A6D46B19DEF0 | |||
| 1784 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:65DC821FDDBE67920385ACBAD8827260 | SHA256:FA7F499ADFB3A4B12FFEB3A38DBE0ED7CE8B23DF7BA3FCC10DDBC71DE58D5EB2 | |||
| 1784 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:94C20CE605229FE43B3B3589432E48F0 | SHA256:5DCC71E9B3FAD70B52F7270C105535D82B475773BE2B0DC10DA3BD704436E807 | |||
| 3100 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFC7B2957446D10D16.TMP | gmc | |
MD5:F24C332BDF453E10017C5DD097434ADE | SHA256:849C75460C81C9D5A9857D89506AB52663F3BFC1A39E4F362904735DEDC6733A | |||
| 3100 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | binary | |
MD5:1CF25301F44CF779F956F1E1BAC39F23 | SHA256:5EEE1DA2EFF1EE6C4B3C8CF2B35E4297EA6F10558DF7C182974B01AA00C04C7C | |||
| 3100 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\favicon[3].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3100 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | der | |
MD5:03286F86A6340EF1EB71162CA877B4CA | SHA256:F6E395EAB531C2331F213B764ECB38E1B4A1E883299D15C1D8B688291E26F20A | |||
| 4008 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C5EF16D6DA310F726628BDE0AA98666C | binary | |
MD5:5C6D7AB3EE45C02C8ADEAFFB2C66275D | SHA256:4F496994D42376F7DA7CB1A6BCE3632BC3A7010540615CA97682CD80C396A9C7 | |||
| 3100 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
41
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1784 | mshta.exe | GET | 304 | 87.248.205.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?95686c55b05a20ca | unknown | — | — | unknown |
1784 | mshta.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | binary | 2.18 Kb | unknown |
4008 | mshta.exe | GET | 301 | 104.16.62.16:80 | http://www.teamviewer.com/favicon.ico | unknown | — | — | unknown |
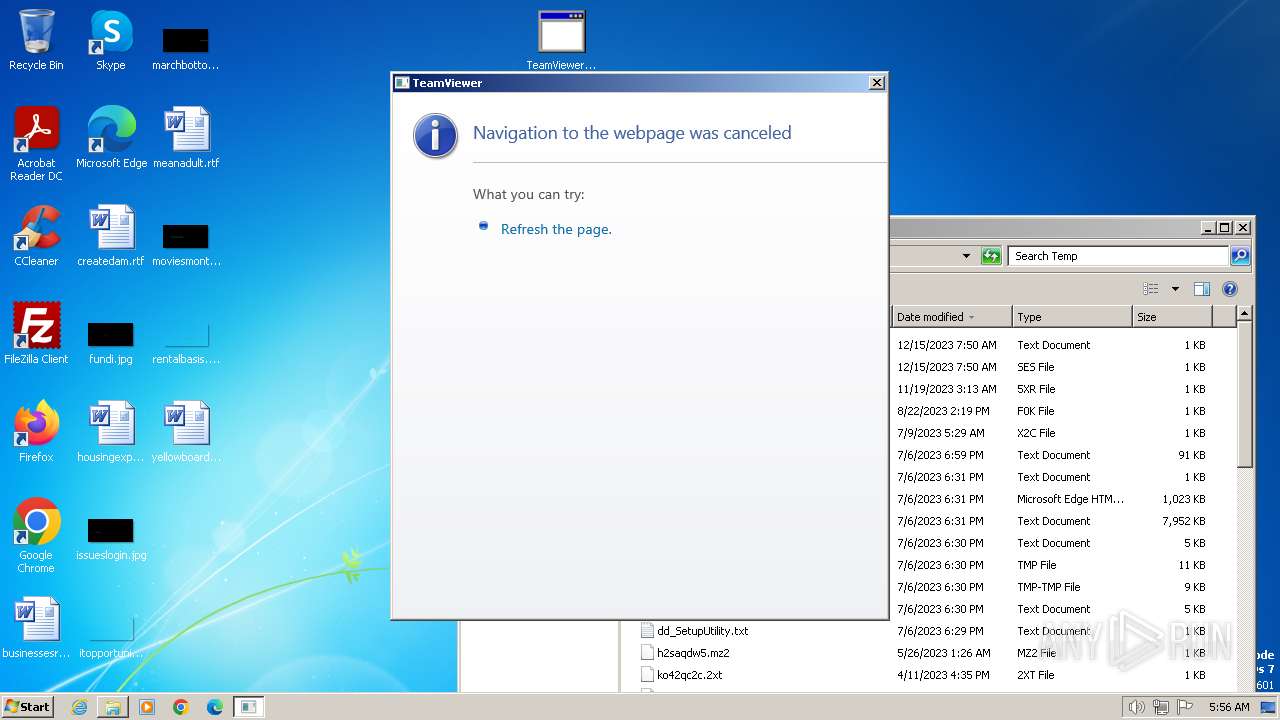
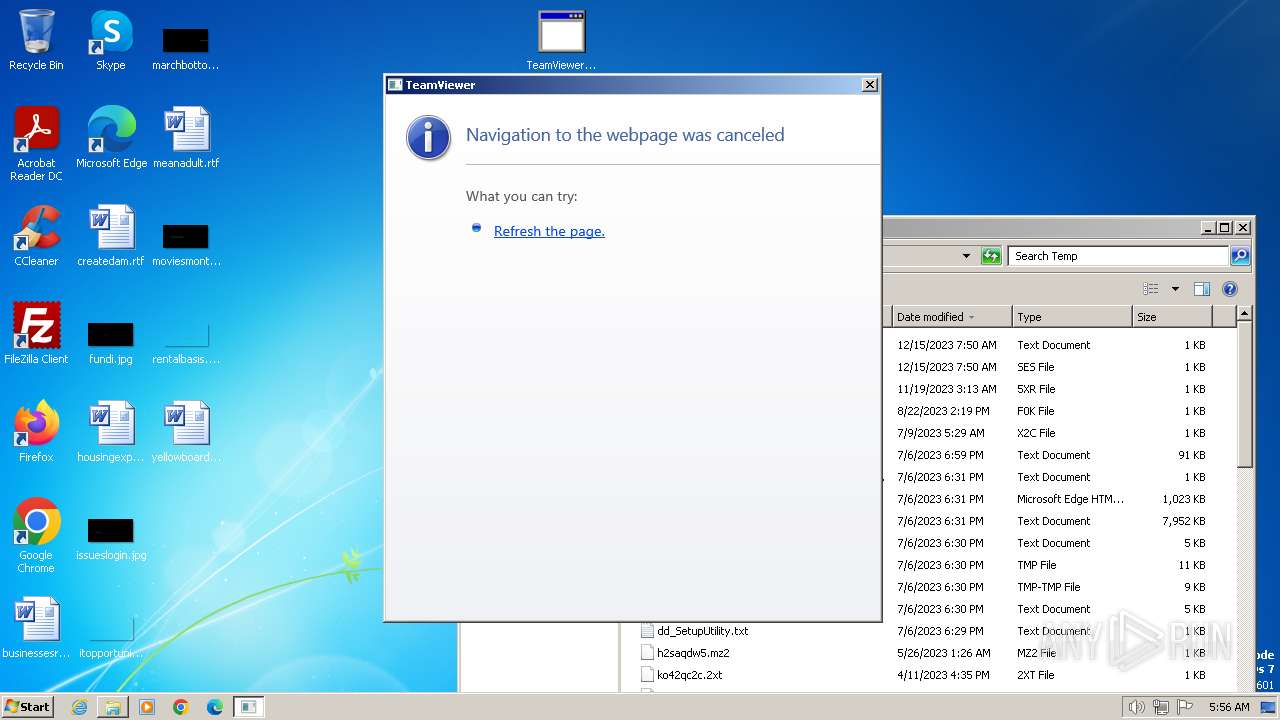
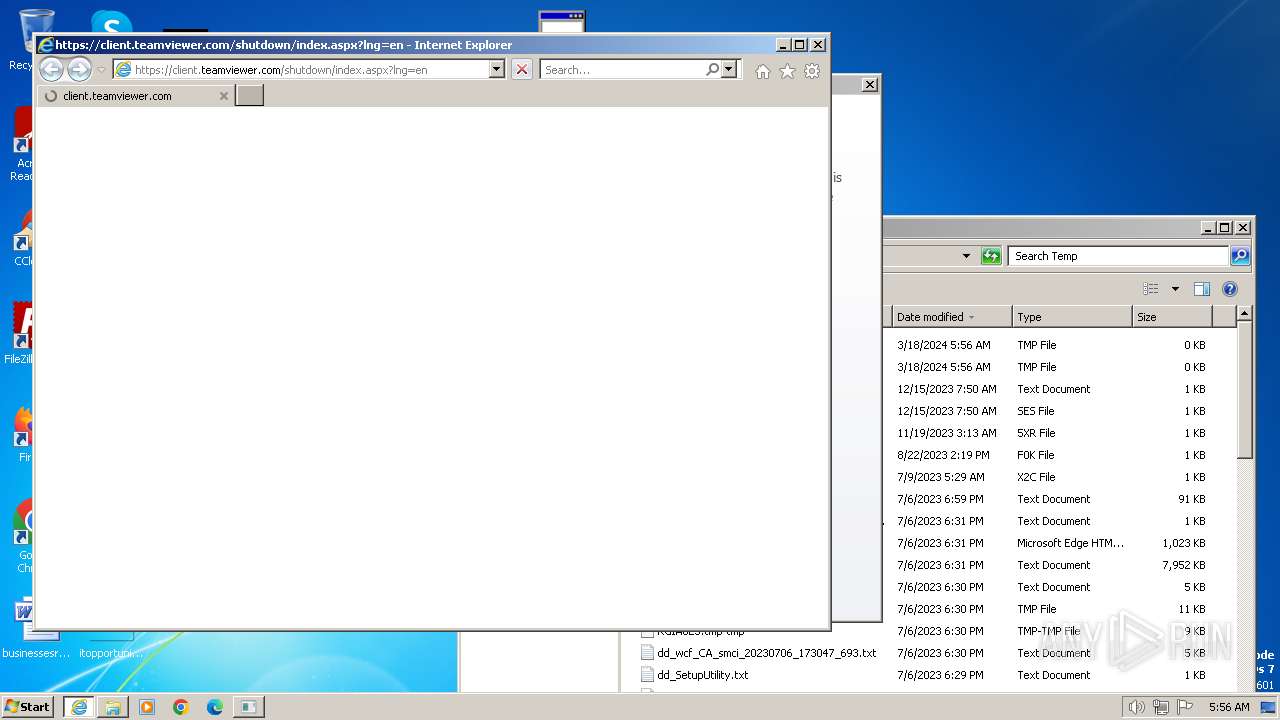
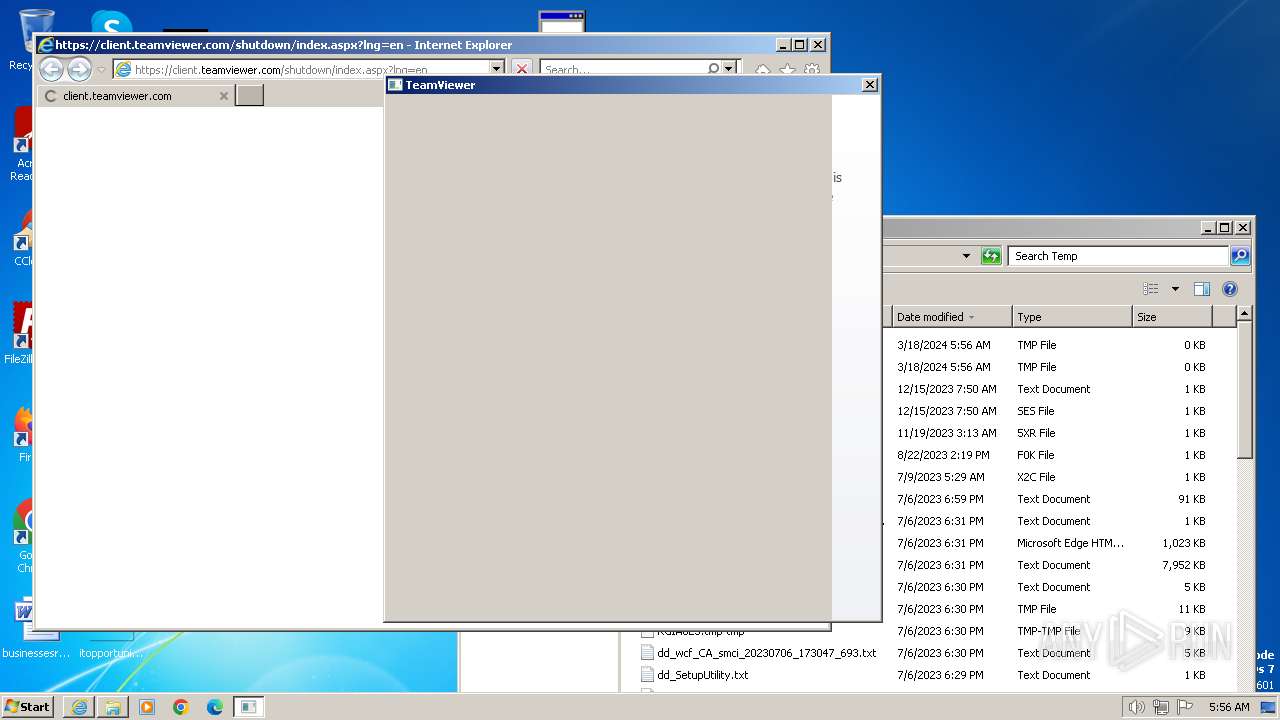
552 | mshta.exe | GET | 307 | 20.50.2.7:80 | http://client.teamviewer.com/shutdown/index.aspx?lng=en | unknown | — | — | unknown |
1784 | mshta.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | binary | 1.42 Kb | unknown |
4008 | mshta.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEBQhuWUyZF1LyUFQW83cEvI%3D | unknown | binary | 471 b | unknown |
4008 | mshta.exe | GET | 307 | 20.50.2.7:80 | http://client.teamviewer.com/shutdown/index.aspx?lng=en | unknown | — | — | unknown |
1080 | svchost.exe | GET | 200 | 87.248.205.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?07f4511d6423f7b6 | unknown | compressed | 67.5 Kb | unknown |
3100 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 314 b | unknown |
2088 | mshta.exe | GET | 307 | 20.50.2.7:80 | http://client.teamviewer.com/shutdown/index.aspx?lng=en | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4008 | mshta.exe | 104.16.62.16:80 | www.teamviewer.com | CLOUDFLARENET | — | shared |
4008 | mshta.exe | 104.16.62.16:443 | www.teamviewer.com | CLOUDFLARENET | — | shared |
4008 | mshta.exe | 20.50.2.7:80 | client.teamviewer.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
4008 | mshta.exe | 104.16.63.16:443 | www.teamviewer.com | CLOUDFLARENET | — | shared |
1784 | mshta.exe | 104.16.62.16:443 | www.teamviewer.com | CLOUDFLARENET | — | shared |
1784 | mshta.exe | 20.50.2.7:80 | client.teamviewer.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
1784 | mshta.exe | 20.50.2.7:443 | client.teamviewer.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.teamviewer.com |
| shared |
client.teamviewer.com |
| shared |
dns.msftncsi.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |