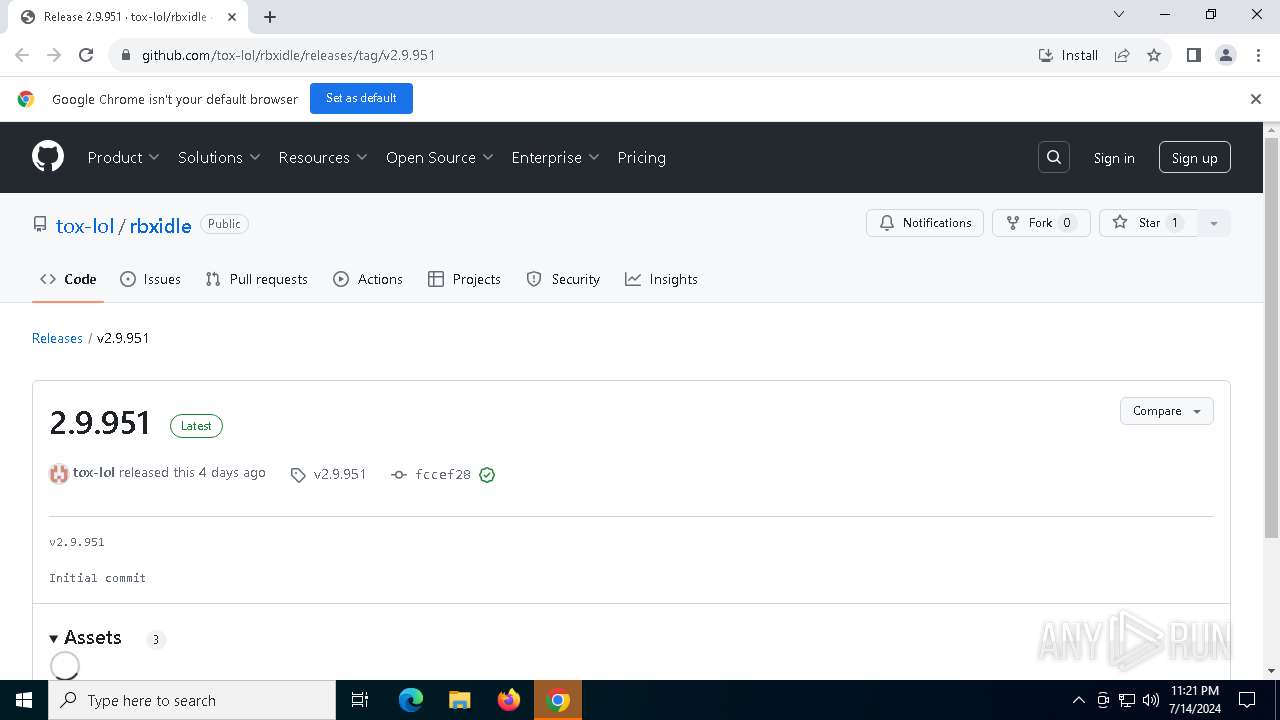
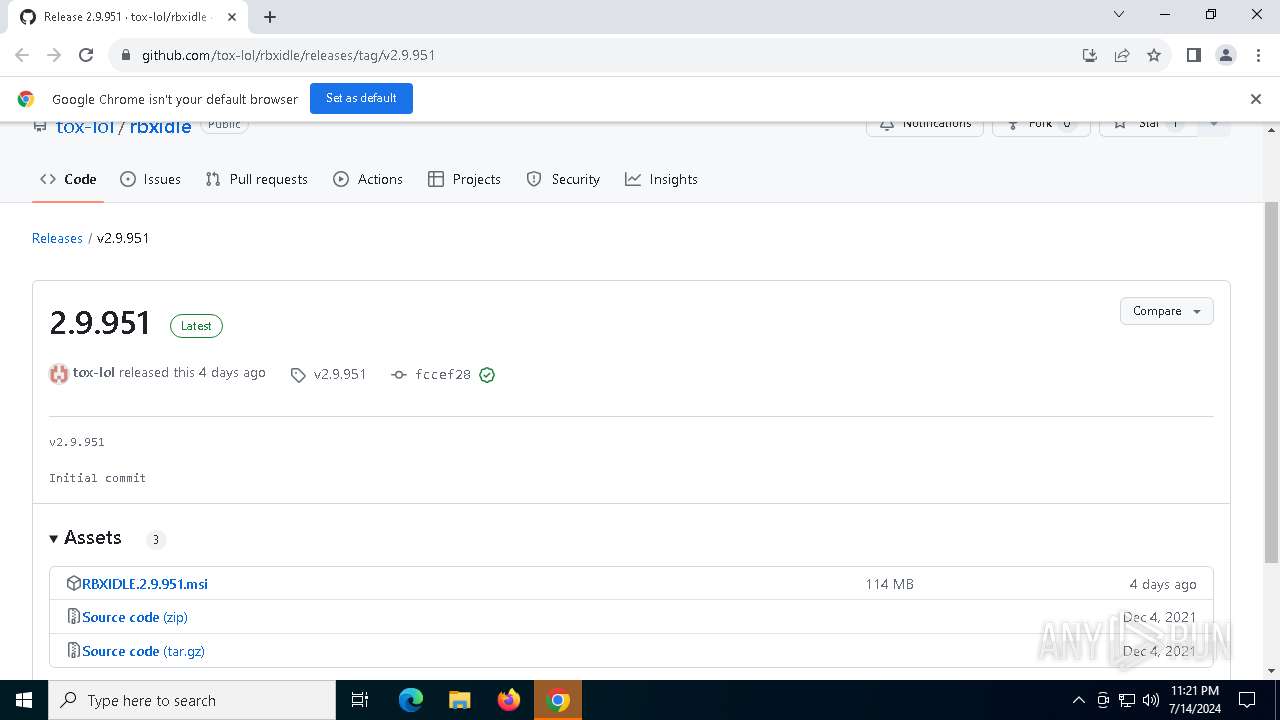
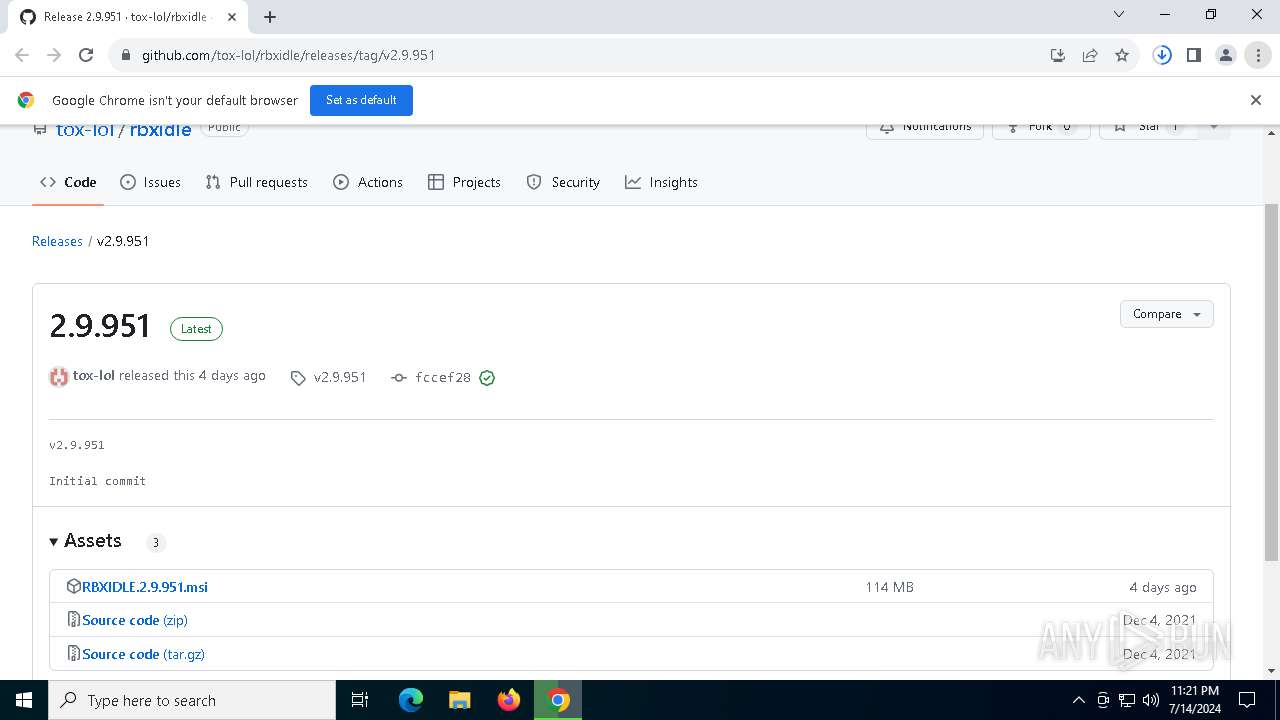
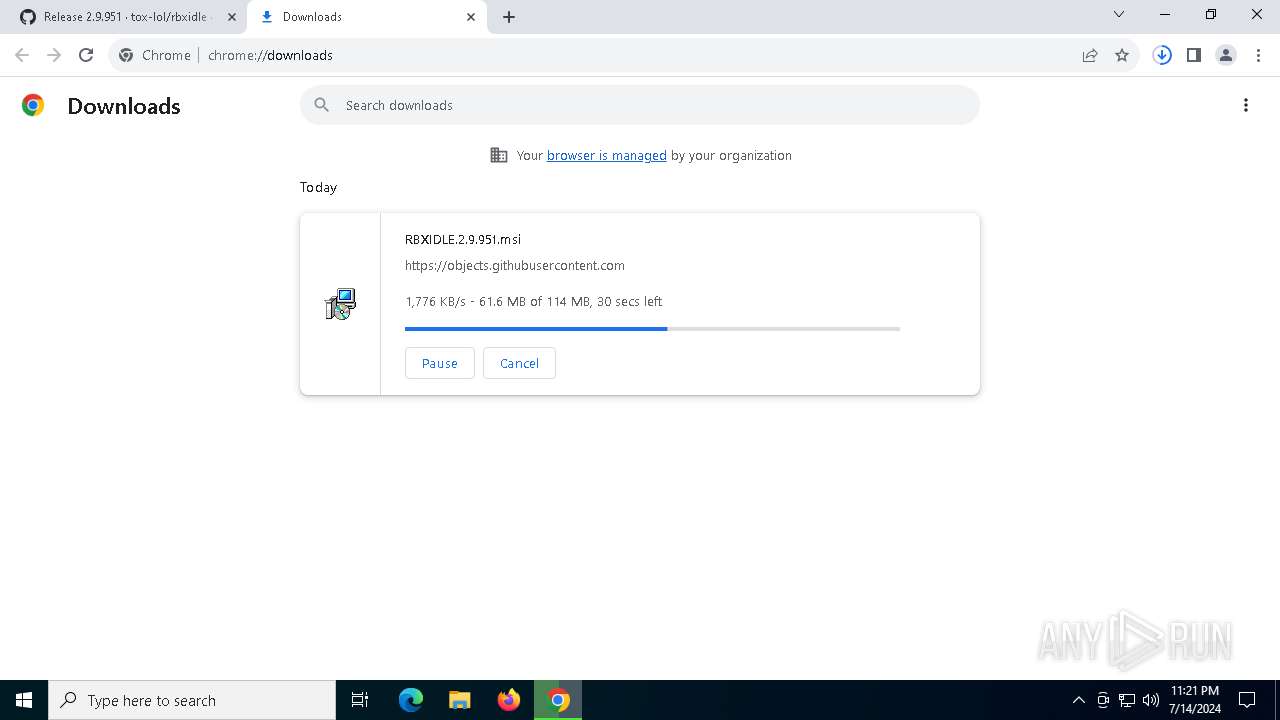
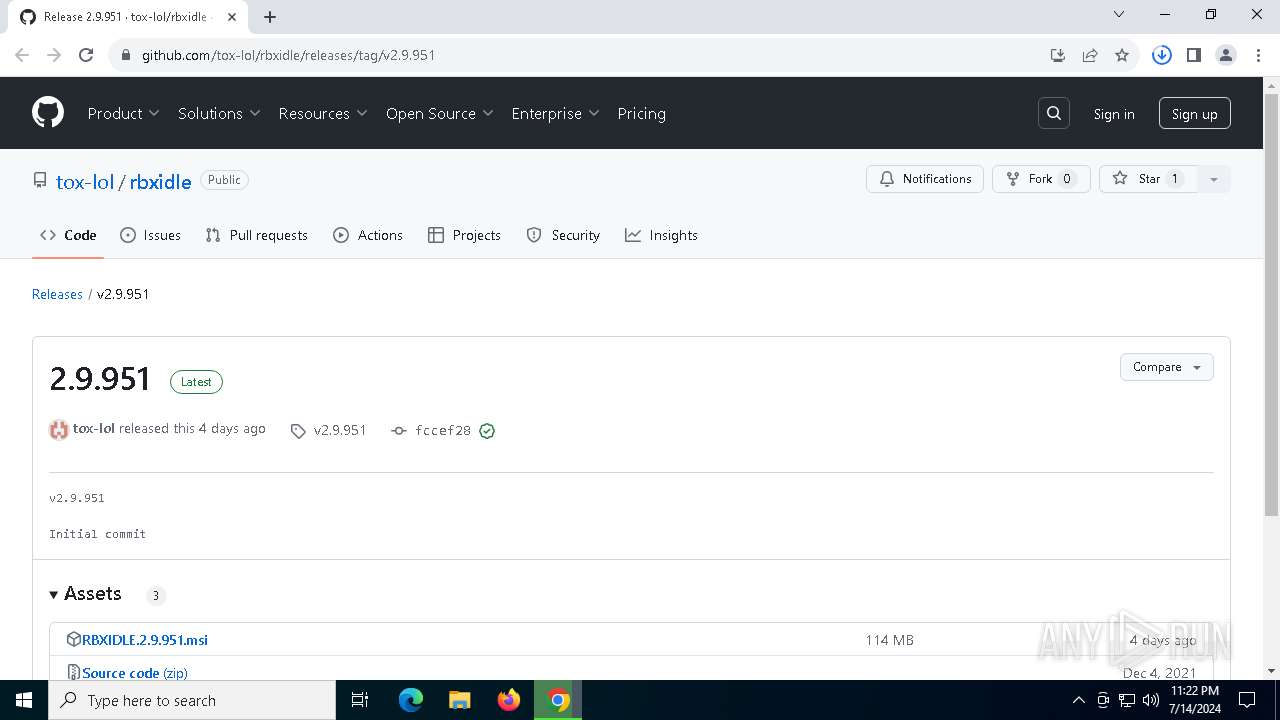
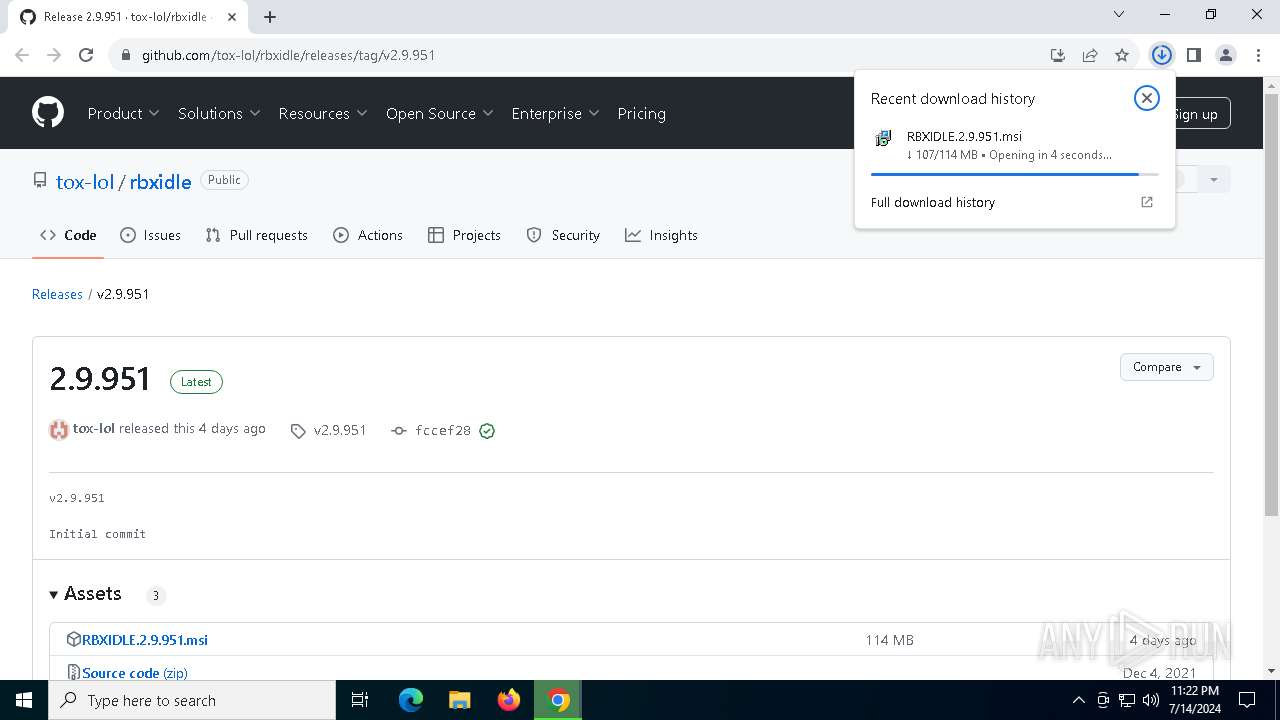
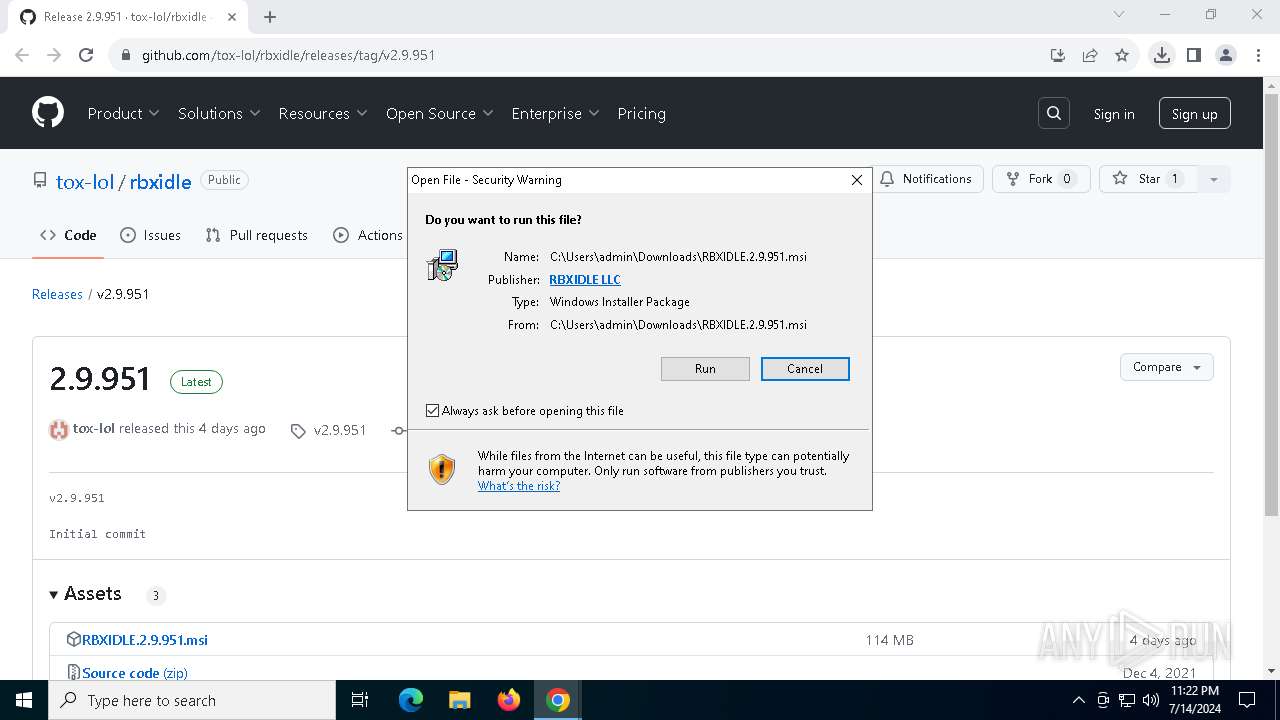
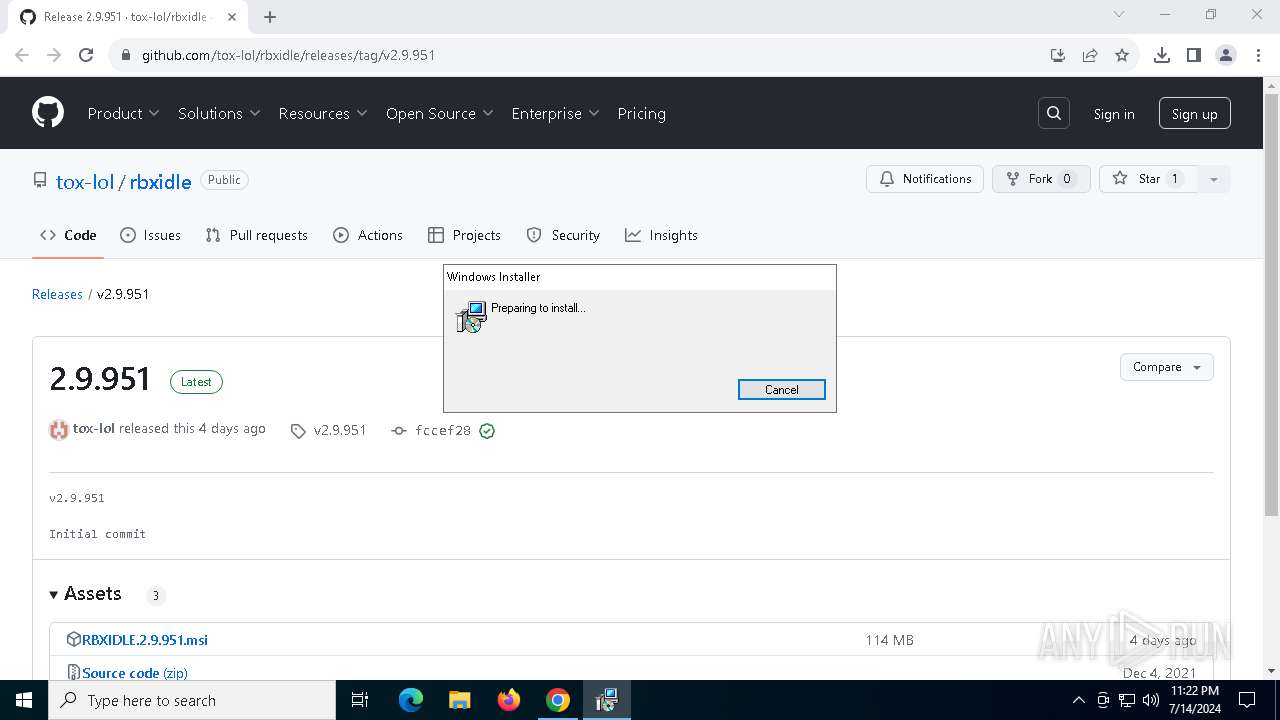
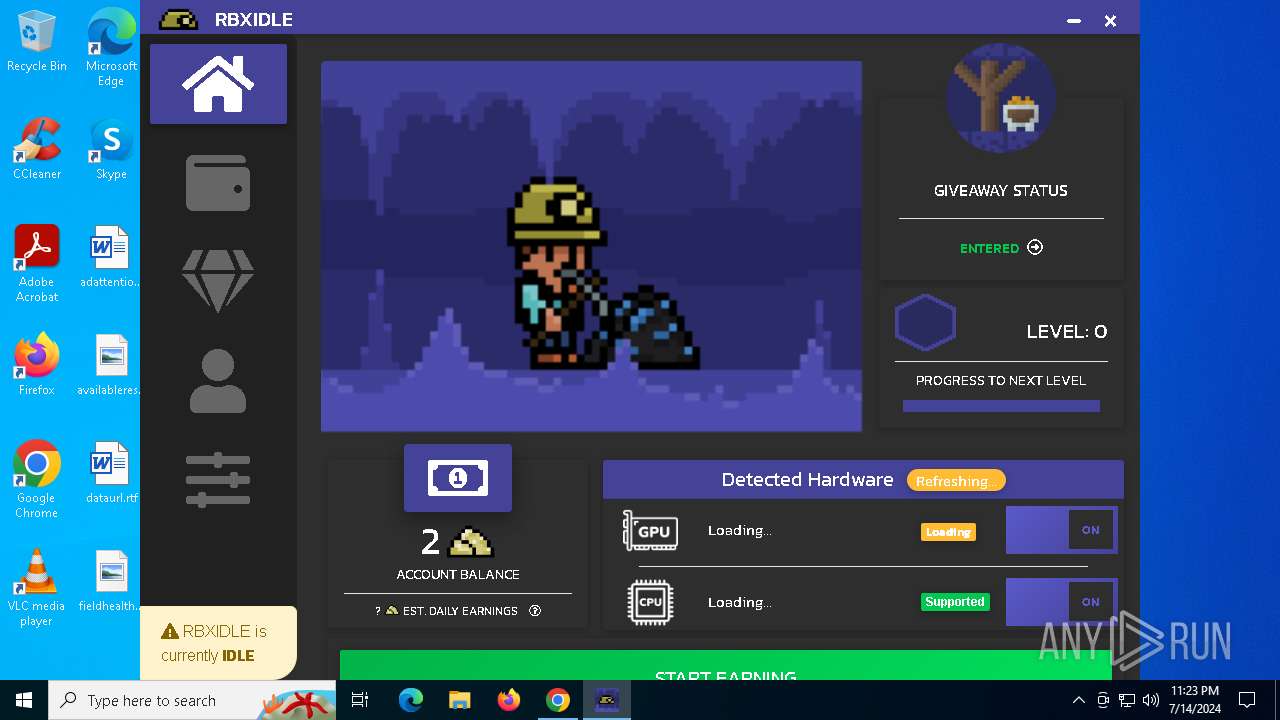
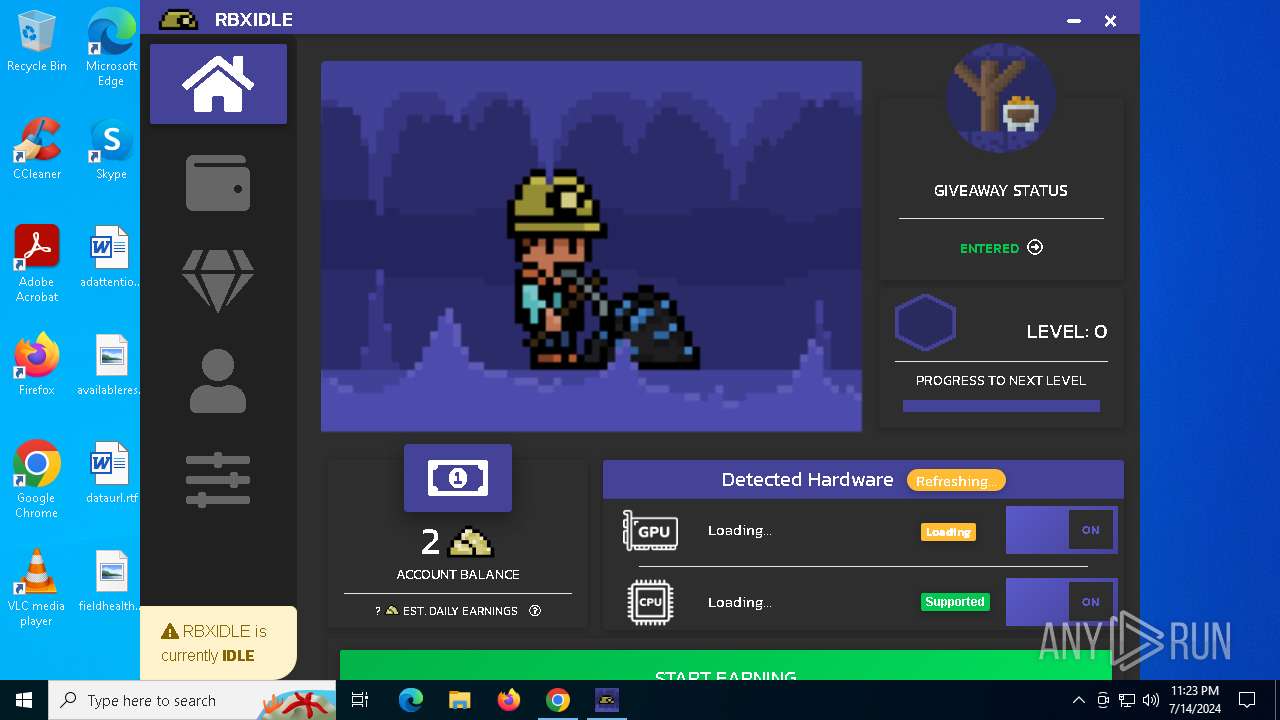
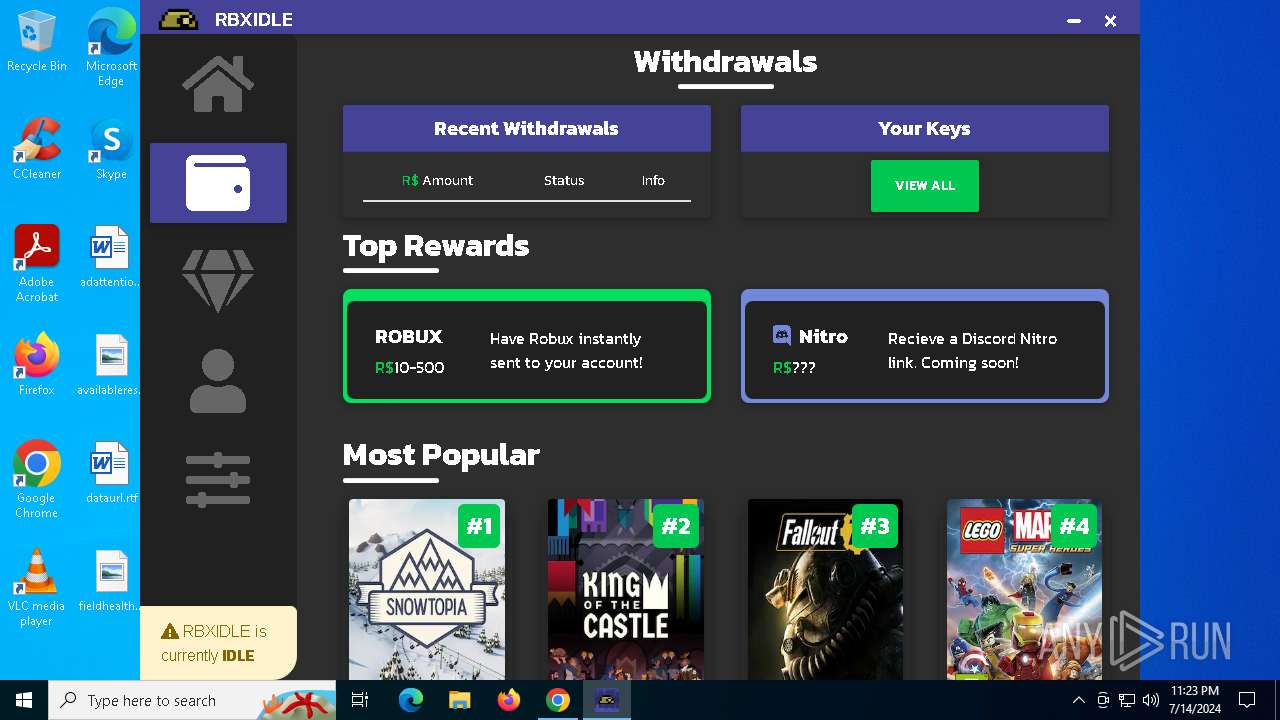
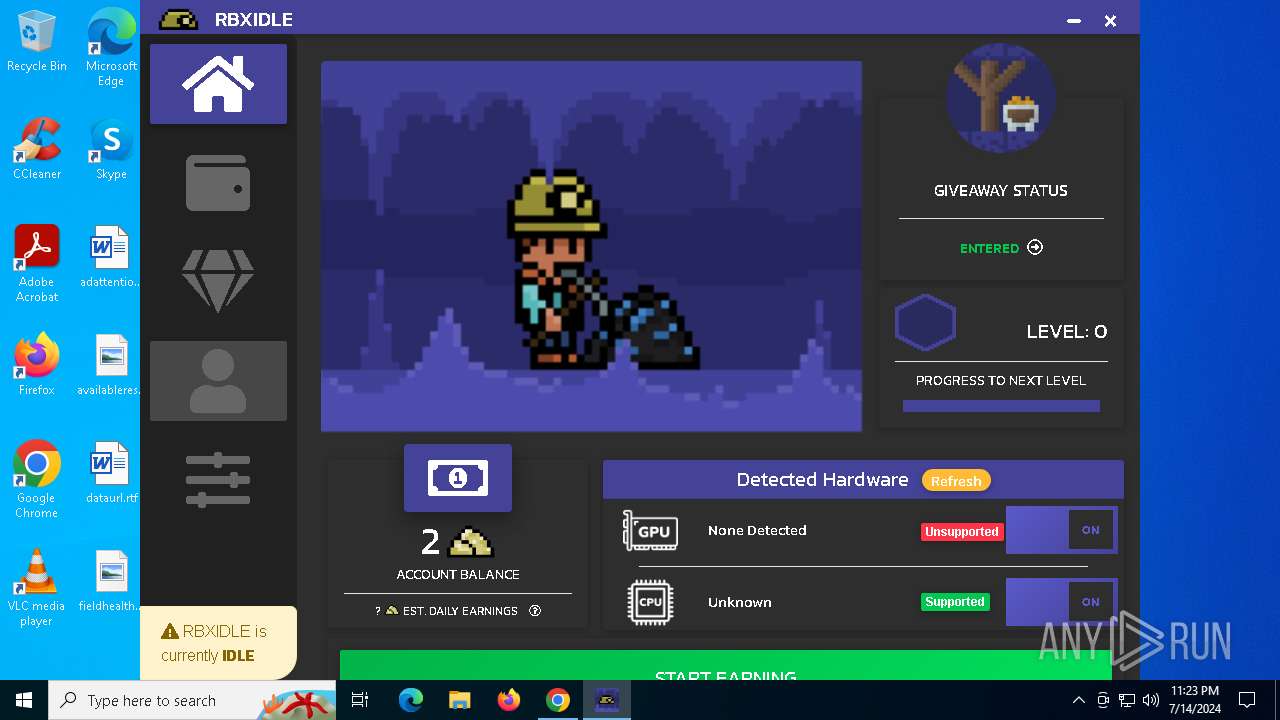
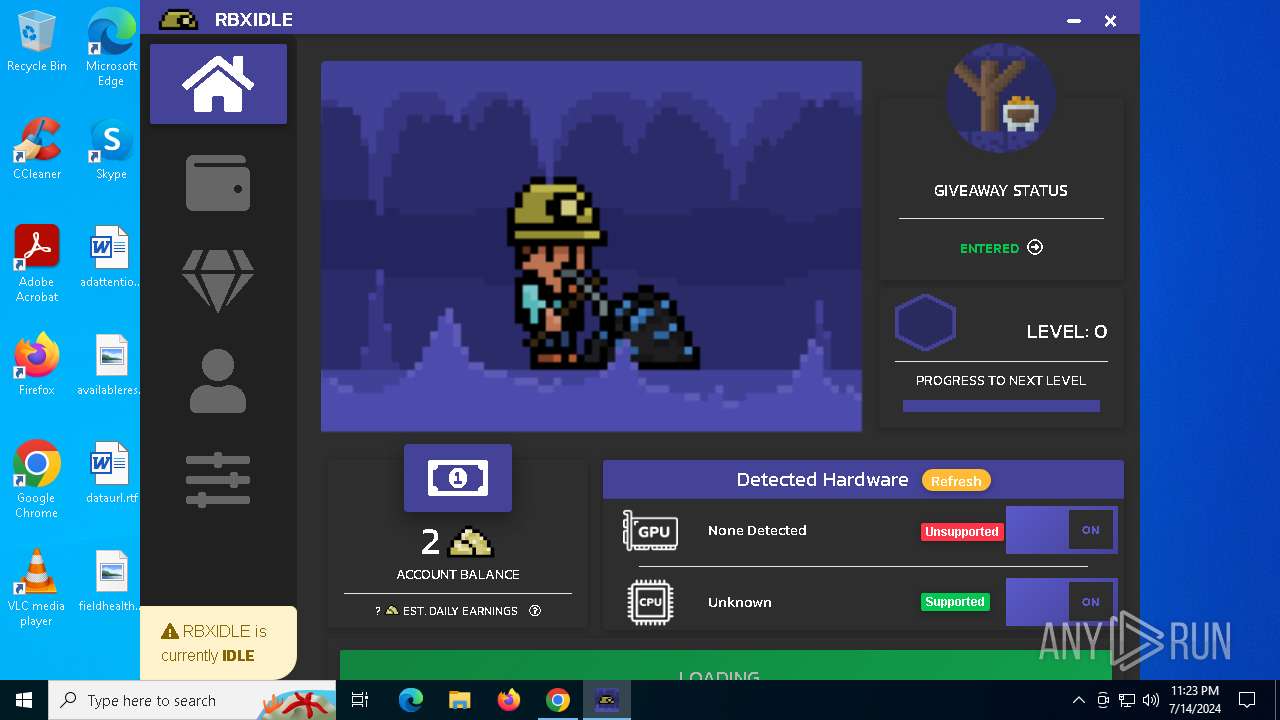
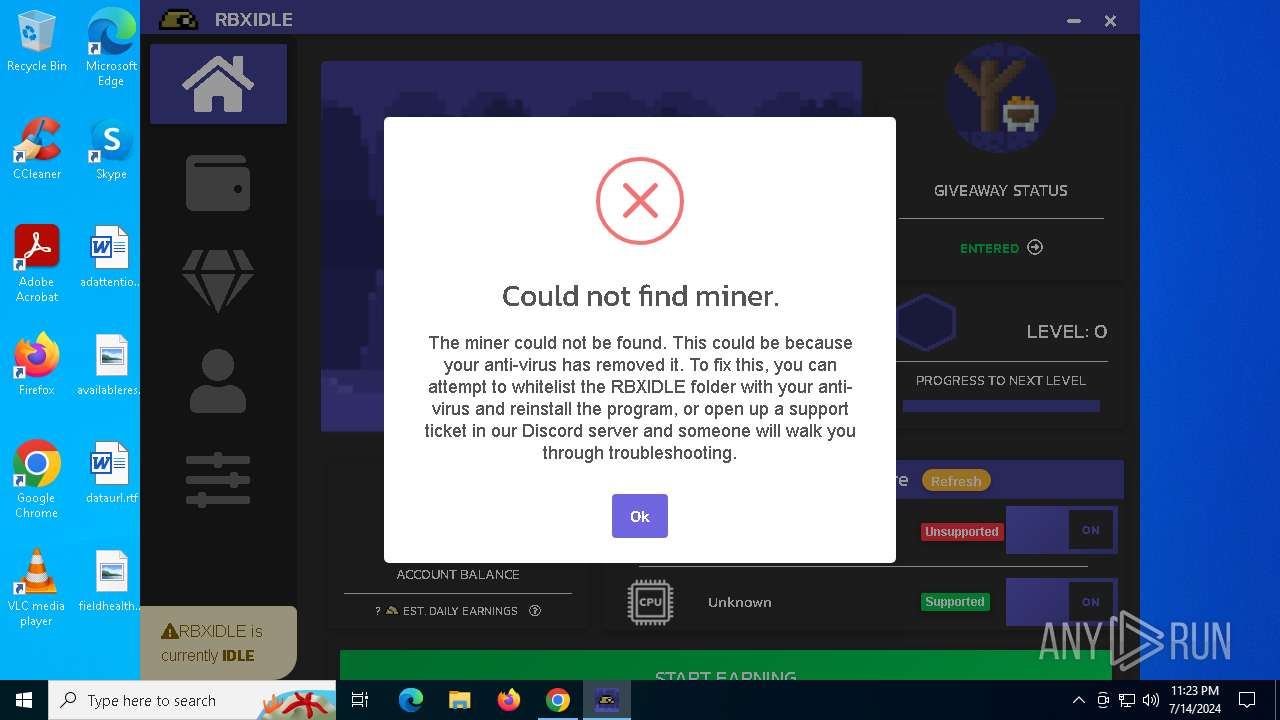
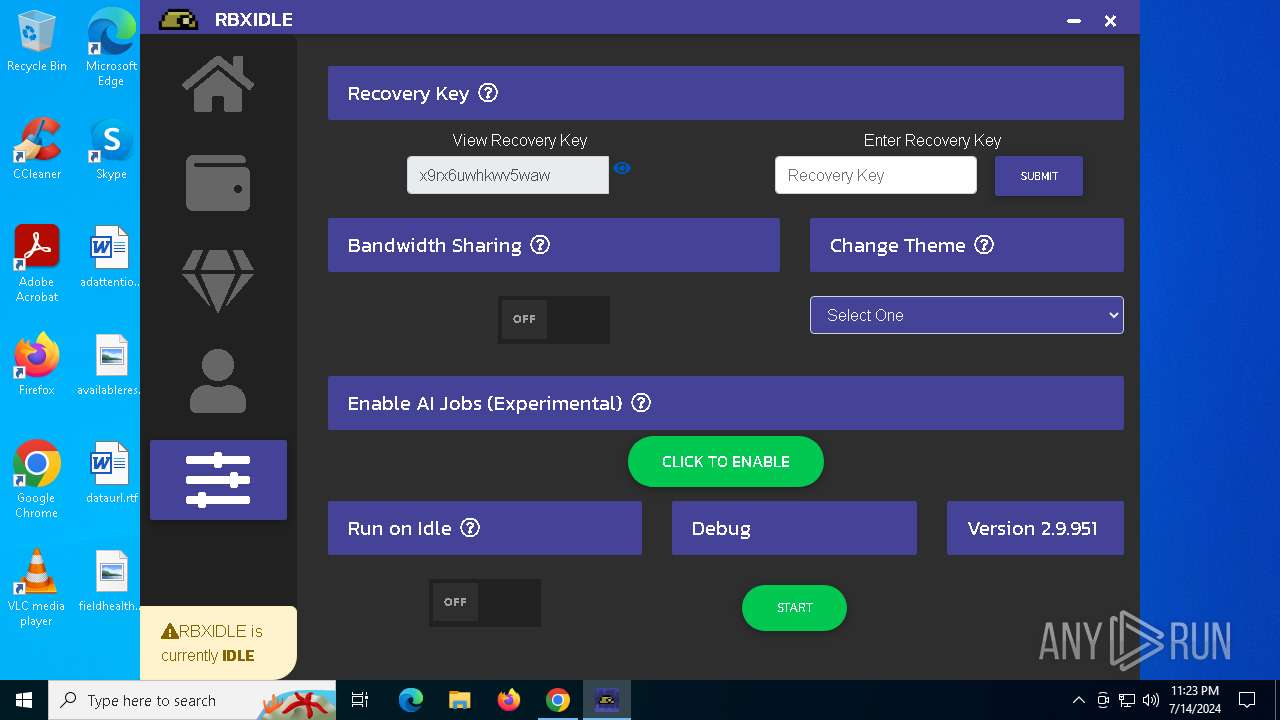
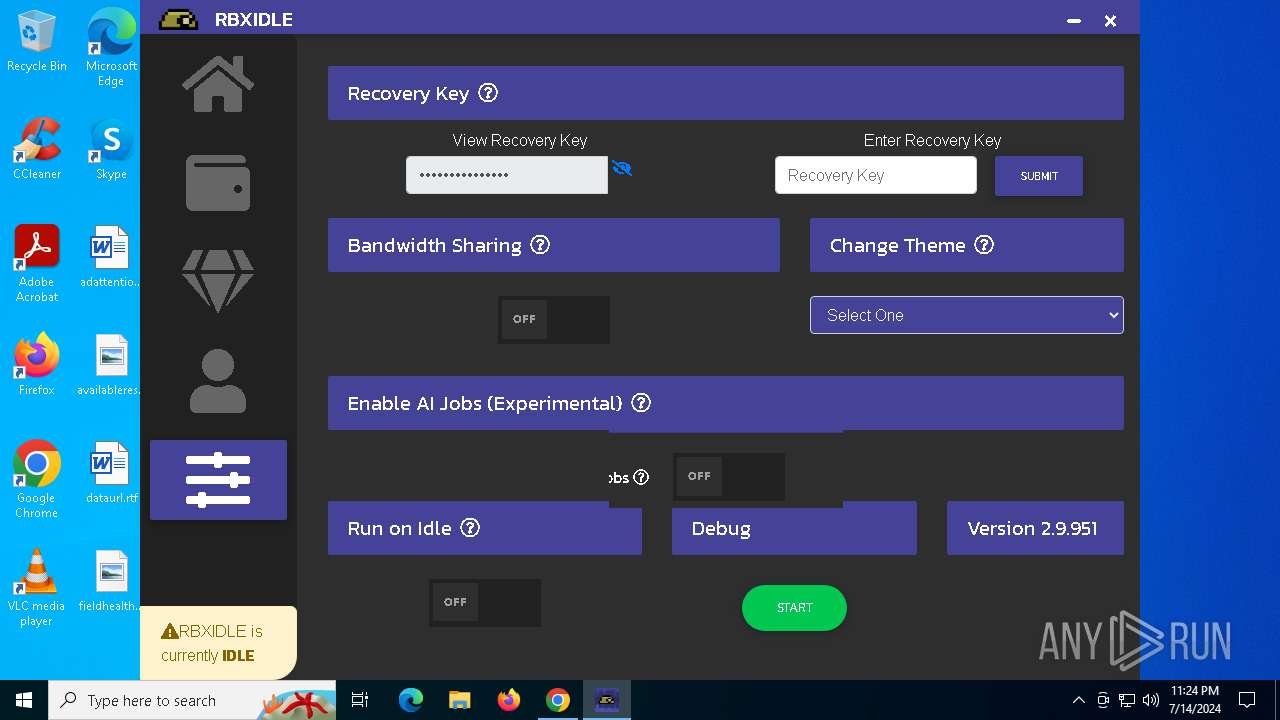
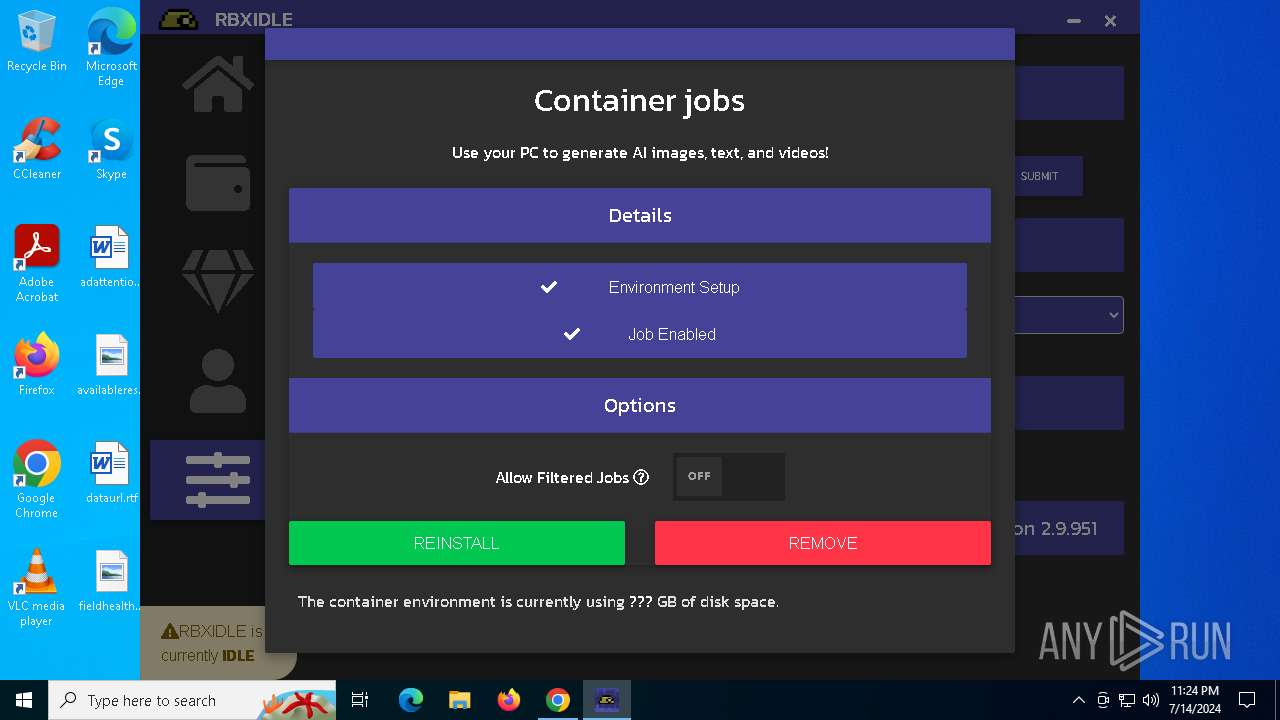
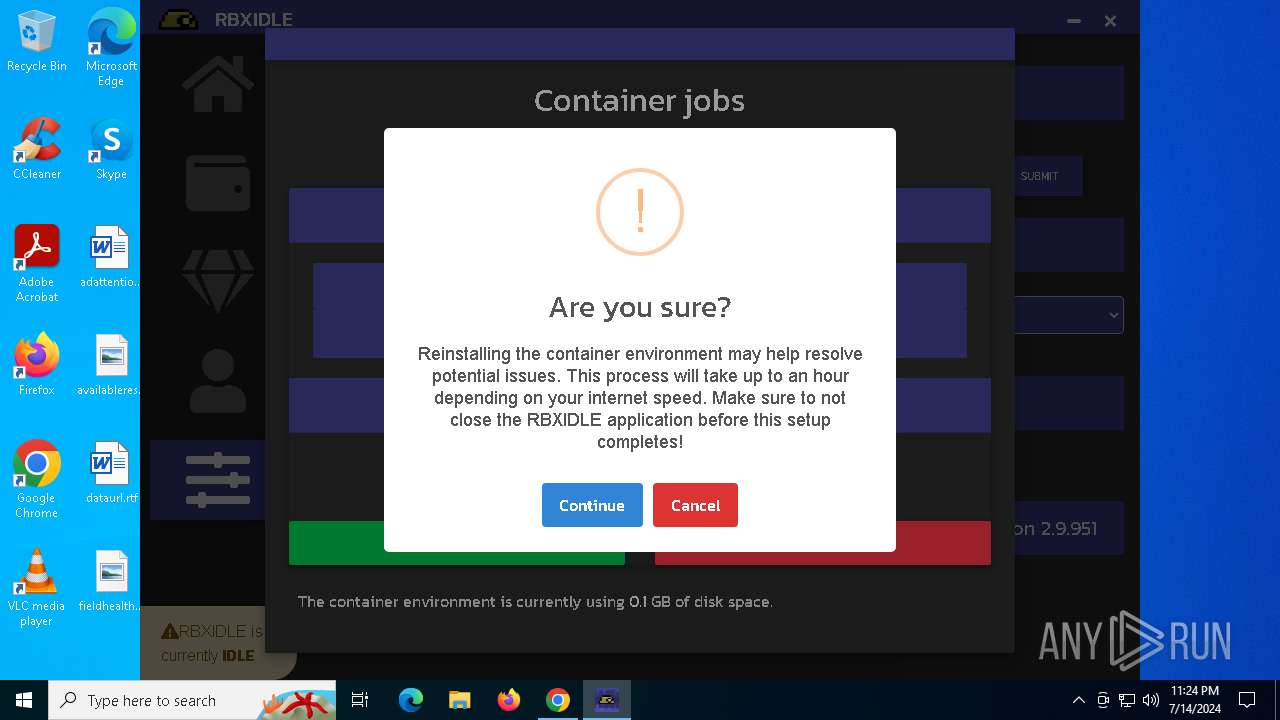
| URL: | https://github.com/tox-lol/rbxidle/releases/tag/v2.9.951 |
| Full analysis: | https://app.any.run/tasks/c1bf00f7-9ebf-447d-8453-ae47d2654619 |
| Verdict: | Malicious activity |
| Analysis date: | July 14, 2024, 23:20:57 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 24BBFEC39CB72A16992F2DA468A0DF7D |
| SHA1: | A7C0437E1A5192B47E0F15C5932D1369F2720D5A |
| SHA256: | 1A153C8ED7D2C852EA1B2CA66CACB3DD180C67A7DEA4B59CF68D95EAB16EF39A |
| SSDEEP: | 3:N8tEdhKSJHdASOrqKv6C:2u6SJEx5 |
MALICIOUS
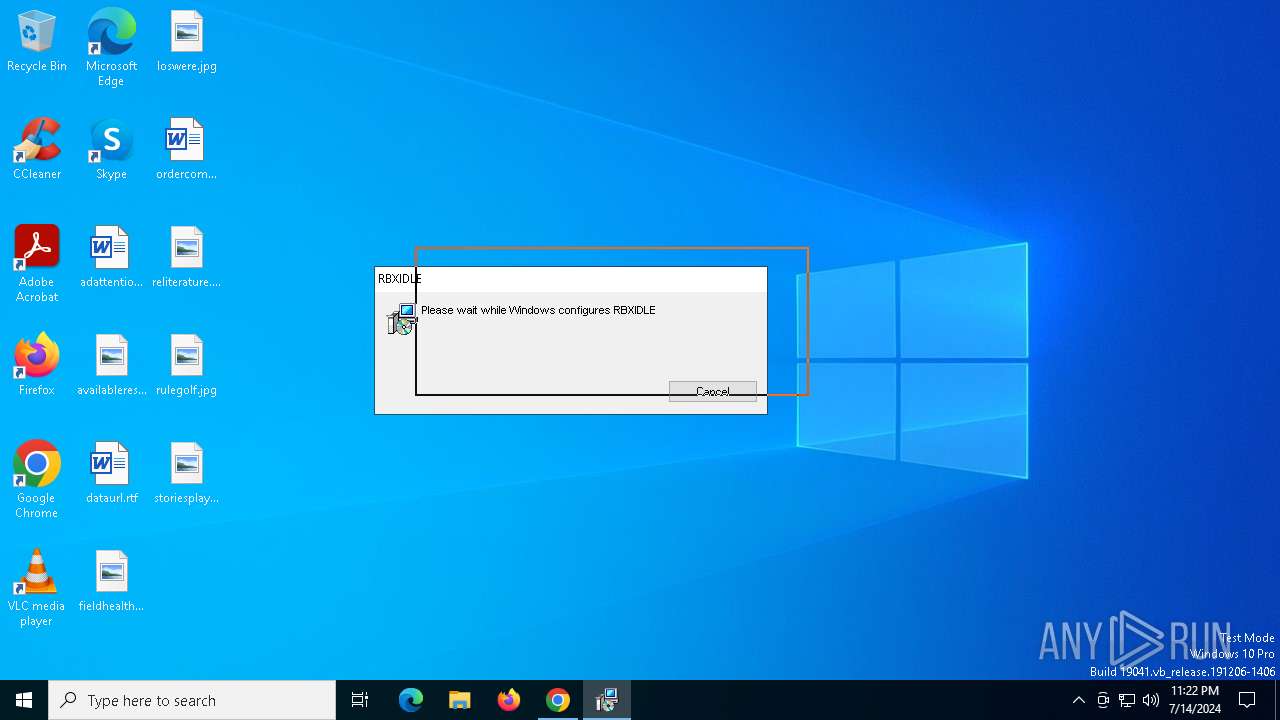
Drops the executable file immediately after the start
- msiexec.exe (PID: 2588)
Changes powershell execution policy (Unrestricted)
- RBXIDLE.exe (PID: 6848)
Run PowerShell with an invisible window
- powershell.exe (PID: 7360)
SUSPICIOUS
Reads the date of Windows installation
- SystemSettings.exe (PID: 3848)
Checks Windows Trust Settings
- msiexec.exe (PID: 2588)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 2588)
Process drops legitimate windows executable
- msiexec.exe (PID: 2588)
Starts CMD.EXE for commands execution
- RBXIDLE.exe (PID: 6848)
- powershell.exe (PID: 7360)
Starts application with an unusual extension
- cmd.exe (PID: 1064)
- cmd.exe (PID: 10144)
Application launched itself
- RBXIDLE.exe (PID: 6848)
The process creates files with name similar to system file names
- msiexec.exe (PID: 2588)
Adds/modifies Windows certificates
- RBXIDLE.exe (PID: 6848)
Powershell scripting: start process
- cmd.exe (PID: 7312)
Executing commands from a ".bat" file
- RBXIDLE.exe (PID: 6848)
- powershell.exe (PID: 7360)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7312)
- RBXIDLE.exe (PID: 6848)
- cmd.exe (PID: 8948)
Detected use of alternative data streams (AltDS)
- powershell.exe (PID: 7360)
The process hides Powershell's copyright startup banner
- RBXIDLE.exe (PID: 6848)
The process bypasses the loading of PowerShell profile settings
- RBXIDLE.exe (PID: 6848)
- cmd.exe (PID: 8948)
The process deletes folder without confirmation
- RBXIDLE.exe (PID: 6848)
Creates/Modifies COM task schedule object
- dxdiag.exe (PID: 9192)
- dxdiag.exe (PID: 6876)
Executes as Windows Service
- VSSVC.exe (PID: 2632)
INFO
Reads the computer name
- SystemSettings.exe (PID: 3848)
- msiexec.exe (PID: 2588)
- RBXIDLE.exe (PID: 6848)
- RBXIDLE.exe (PID: 4400)
- RBXIDLE.exe (PID: 4796)
- identity_helper.exe (PID: 8604)
Reads Microsoft Office registry keys
- SystemSettings.exe (PID: 3848)
- explorer.exe (PID: 7480)
- explorer.exe (PID: 8336)
- msedge.exe (PID: 7084)
- msedge.exe (PID: 9076)
- chrome.exe (PID: 244)
Reads the machine GUID from the registry
- SystemSettings.exe (PID: 3848)
- RBXIDLE.exe (PID: 6848)
- msiexec.exe (PID: 2588)
Reads the software policy settings
- slui.exe (PID: 5888)
- msiexec.exe (PID: 2060)
- SystemSettings.exe (PID: 3848)
- RBXIDLE.exe (PID: 6848)
- slui.exe (PID: 2668)
- dxdiag.exe (PID: 6876)
- dxdiag.exe (PID: 9192)
- msiexec.exe (PID: 2588)
The process uses the downloaded file
- chrome.exe (PID: 5652)
- chrome.exe (PID: 244)
Checks supported languages
- msiexec.exe (PID: 2588)
- RBXIDLE.exe (PID: 6848)
- chcp.com (PID: 5908)
- RBXIDLE.exe (PID: 4796)
- RBXIDLE.exe (PID: 4400)
- RBXIDLE.exe (PID: 3052)
- RBXIDLE.exe (PID: 7252)
- chcp.com (PID: 9312)
- identity_helper.exe (PID: 8604)
- SystemSettings.exe (PID: 3848)
Application launched itself
- chrome.exe (PID: 244)
- msedge.exe (PID: 9076)
- msedge.exe (PID: 7084)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 2060)
- Taskmgr.exe (PID: 5872)
- explorer.exe (PID: 7480)
- explorer.exe (PID: 8336)
- dxdiag.exe (PID: 6876)
- dxdiag.exe (PID: 9192)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2588)
Creates files or folders in the user directory
- msiexec.exe (PID: 2588)
- RBXIDLE.exe (PID: 4400)
- RBXIDLE.exe (PID: 6848)
- dxdiag.exe (PID: 6876)
Manual execution by a user
- Taskmgr.exe (PID: 2108)
- Taskmgr.exe (PID: 5872)
- RBXIDLE.exe (PID: 3088)
- RBXIDLE.exe (PID: 6848)
Creates a software uninstall entry
- msiexec.exe (PID: 2588)
Reads product name
- RBXIDLE.exe (PID: 6848)
Reads Environment values
- RBXIDLE.exe (PID: 6848)
Checks proxy server information
- RBXIDLE.exe (PID: 6848)
- slui.exe (PID: 2668)
- dxdiag.exe (PID: 6876)
Create files in a temporary directory
- RBXIDLE.exe (PID: 6848)
Process checks computer location settings
- RBXIDLE.exe (PID: 6848)
- RBXIDLE.exe (PID: 3052)
- RBXIDLE.exe (PID: 7252)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7552)
- powershell.exe (PID: 7684)
- powershell.exe (PID: 7716)
- powershell.exe (PID: 7520)
Attempting to use instant messaging service
- msedge.exe (PID: 9236)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
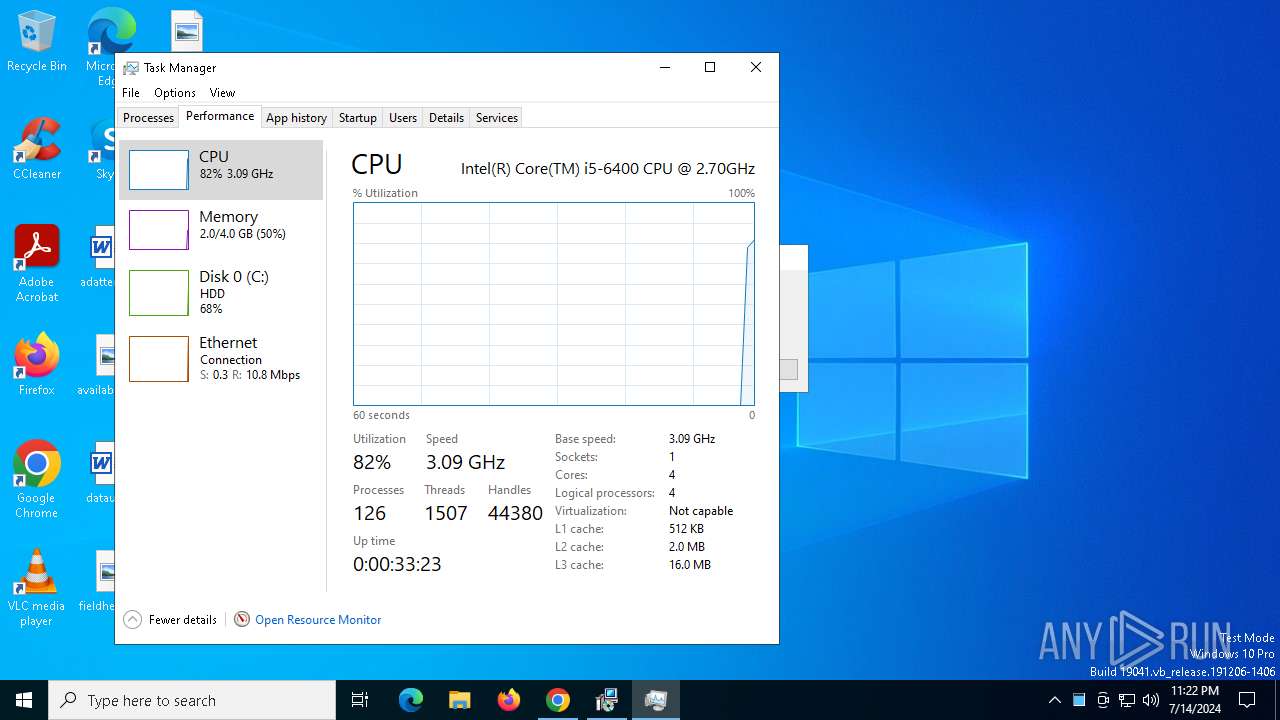
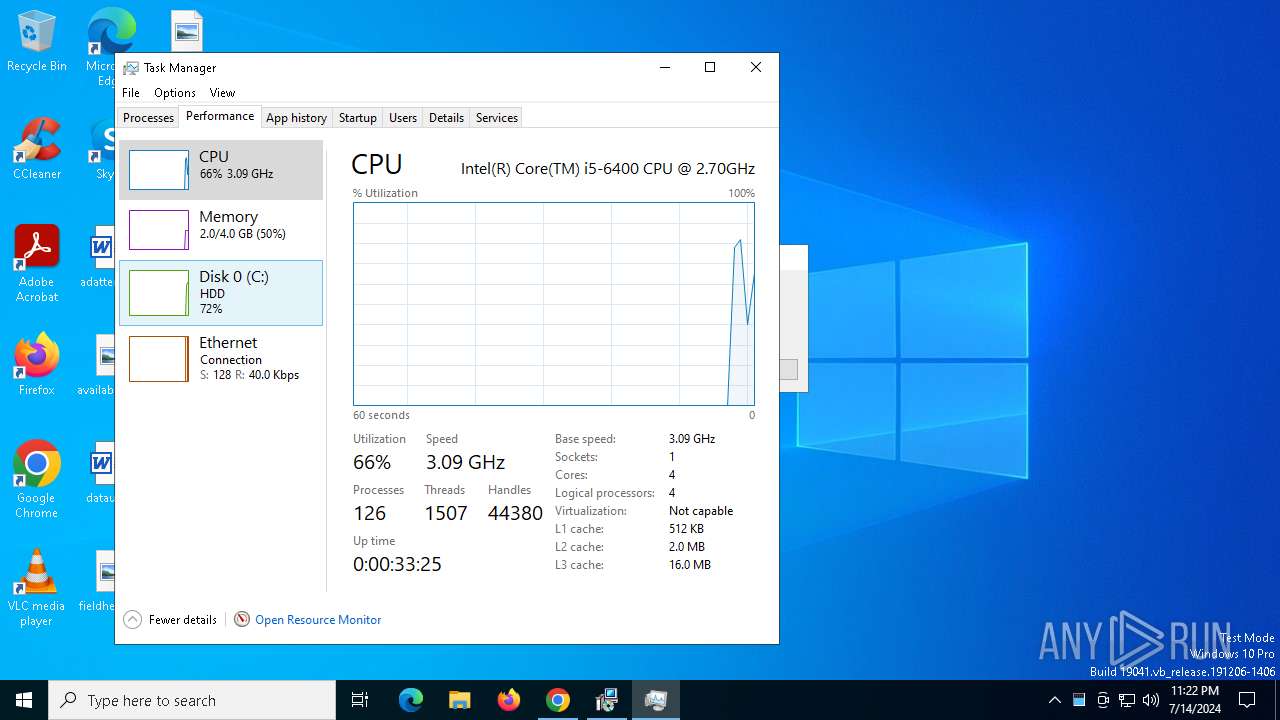
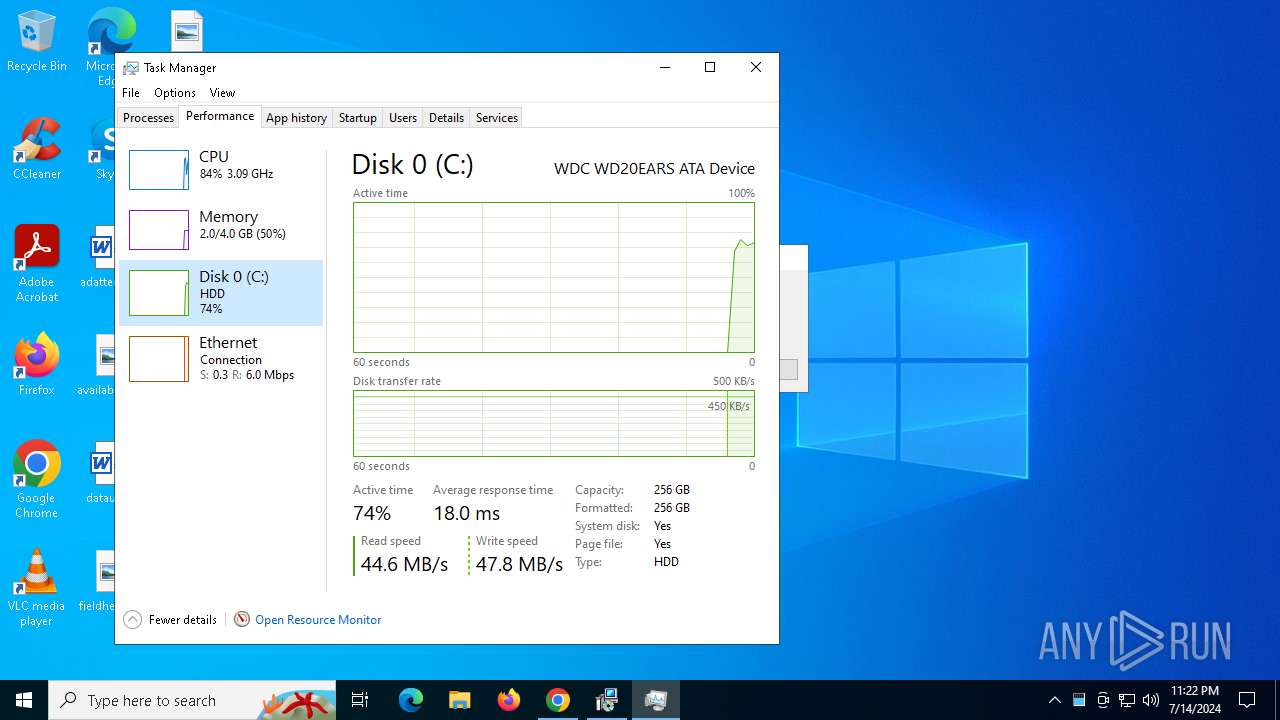
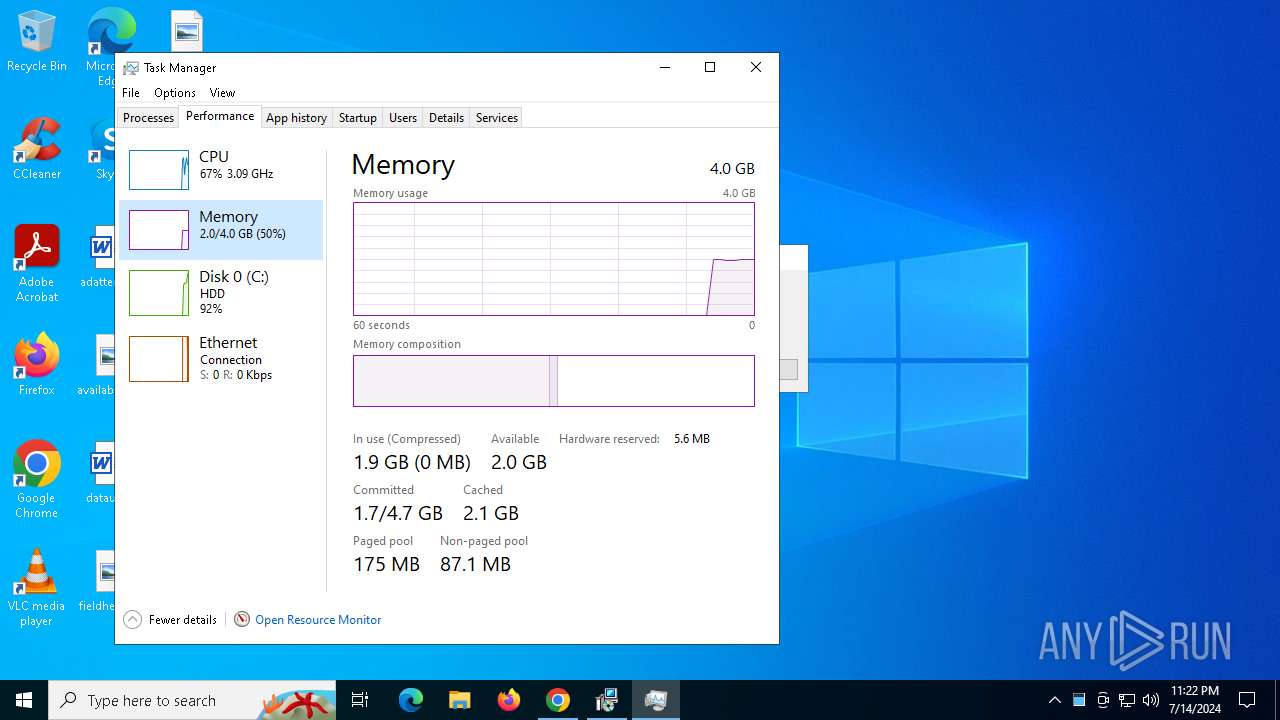
Total processes
280
Monitored processes
129
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 244 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "https://github.com/tox-lol/rbxidle/releases/tag/v2.9.951" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 836 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4428 --field-trial-handle=1848,i,18202946253778289822,16693785211582072068,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 992 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{60A90A2F-858D-42AF-8929-82BE9D99E8A1} | C:\Windows\SysWOW64\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1064 | C:\WINDOWS\system32\cmd.exe /d /s /c "chcp" | C:\Windows\System32\cmd.exe | — | RBXIDLE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1220 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=14 --mojo-platform-channel-handle=3148 --field-trial-handle=1848,i,18202946253778289822,16693785211582072068,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1596 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1992 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2032 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5728 --field-trial-handle=1848,i,18202946253778289822,16693785211582072068,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2060 | "C:\WINDOWS\System32\msiexec.exe" /i "C:\Users\admin\Downloads\RBXIDLE.2.9.951.msi" | C:\Windows\System32\msiexec.exe | — | chrome.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2100 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5196 --field-trial-handle=1848,i,18202946253778289822,16693785211582072068,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
164 905
Read events
163 794
Write events
1 030
Delete events
81
Modification events
| (PID) Process: | (244) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (244) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (244) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (244) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (244) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (244) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (244) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (244) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (244) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (244) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
216
Suspicious files
527
Text files
213
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1cf823.TMP | — | |
MD5:— | SHA256:— | |||
| 244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF1cf832.TMP | — | |
MD5:— | SHA256:— | |||
| 244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 244 | chrome.exe | C:\USERS\ADMIN\APPDATA\LOCAL\GOOGLE\CHROME\USER DATA\LAST VERSION | text | |
MD5:FCE53E052E5CF7C20819320F374DEA88 | SHA256:CD95DE277E746E92CC2C53D9FC92A8F6F0C3EDFB7F1AD9A4E9259F927065BC89 | |||
| 244 | chrome.exe | C:\USERS\ADMIN\APPDATA\LOCAL\GOOGLE\CHROME\USER DATA\CRASHPAD\SETTINGS.DAT | binary | |
MD5:FC81892AC822DCBB09441D3B58B47125 | SHA256:FB077C966296D02D50CCBF7F761D2A3311A206A784A7496F331C2B0D6AD205C8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
32
TCP/UDP connections
235
DNS requests
203
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1972 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6292 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6284 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1972 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5600 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6328 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6328 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4016 | SystemSettings.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4016 | SystemSettings.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4752 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1972 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1972 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4656 | SearchApp.exe | 104.126.37.145:443 | www.bing.com | Akamai International B.V. | DE | unknown |
4656 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5600 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
github.com |
| shared |
accounts.google.com |
| whitelisted |
github.githubassets.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
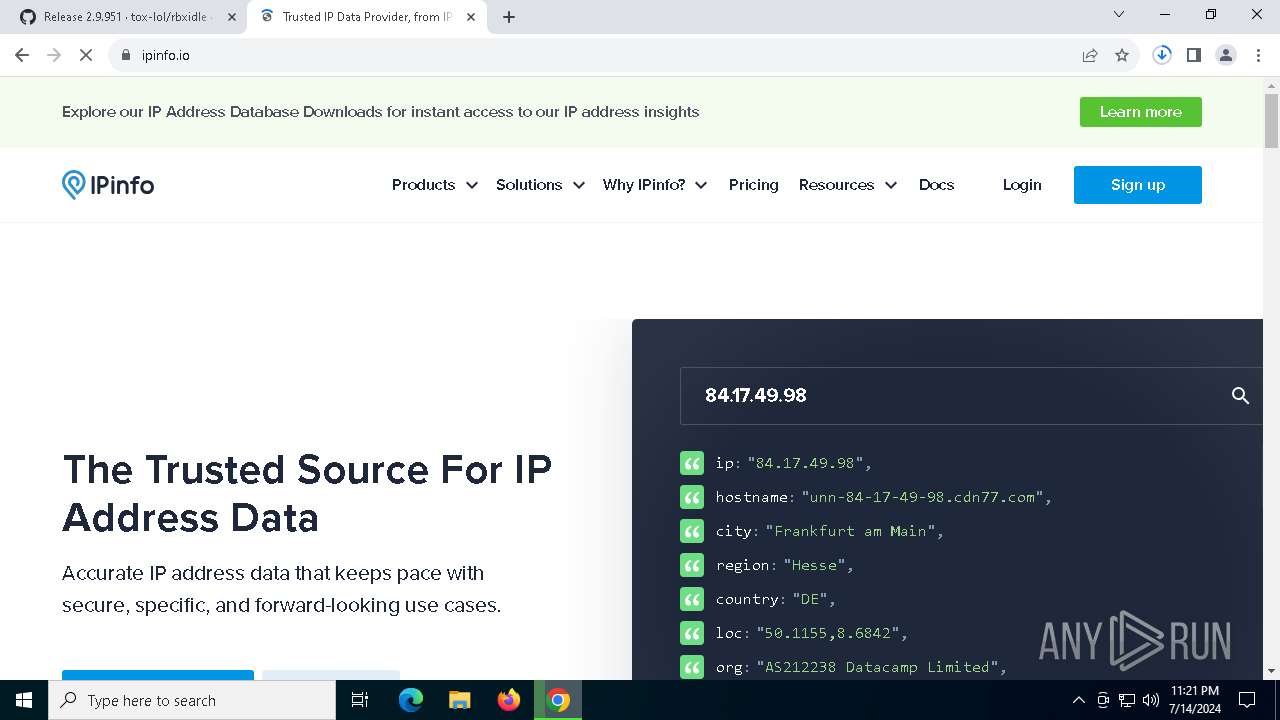
6556 | chrome.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
6556 | chrome.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
6556 | chrome.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ipinfo .io) |
6556 | chrome.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ipinfo .io) |
2168 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2168 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2168 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
9236 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
9236 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
9236 | msedge.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |