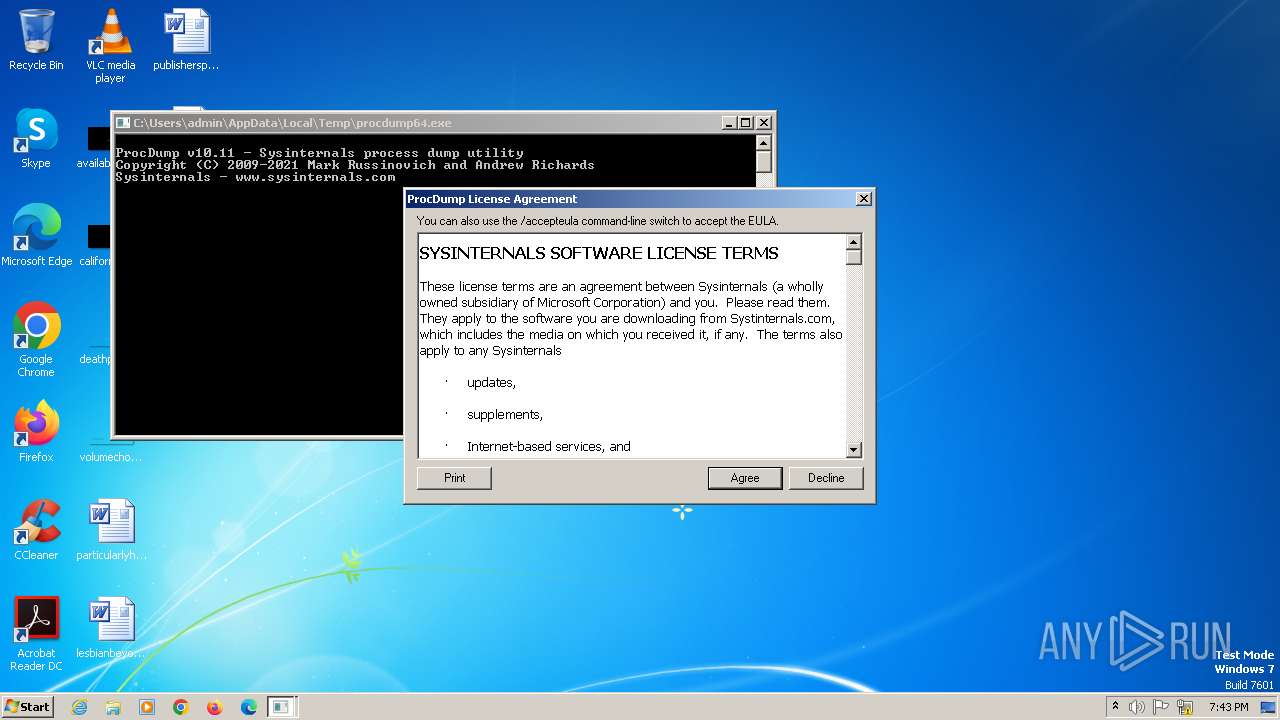
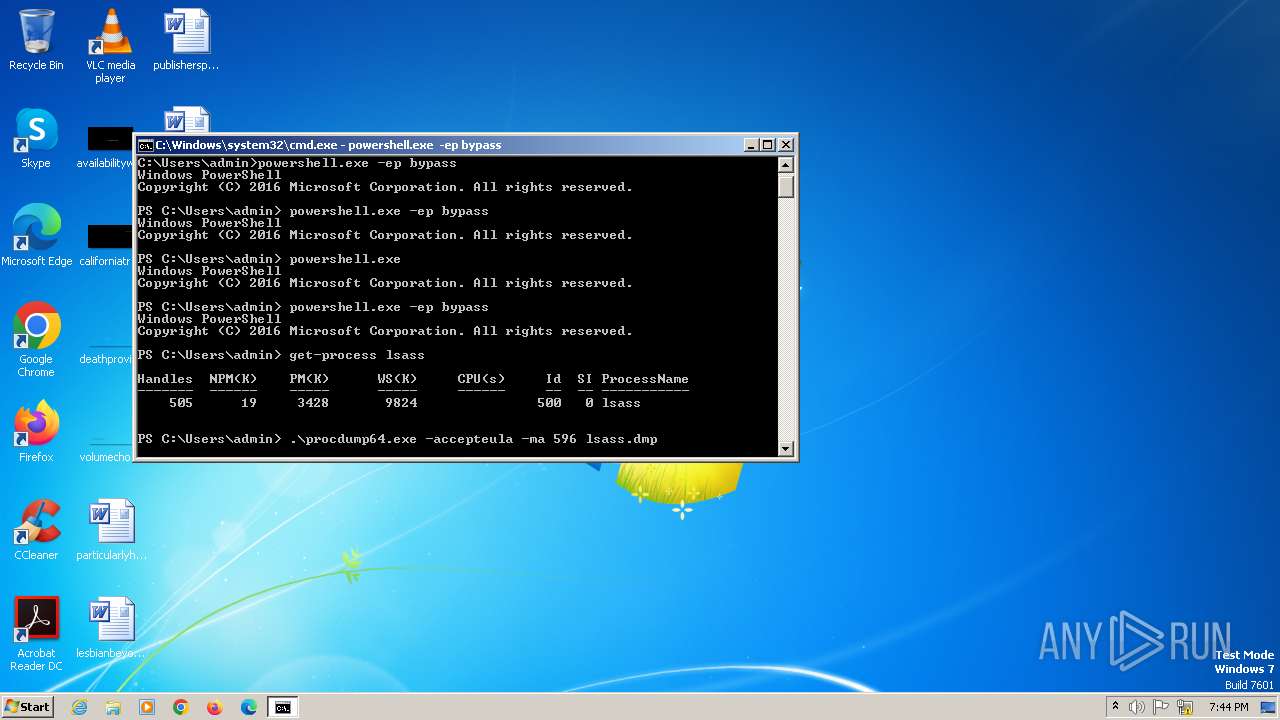
| File name: | procdump64.exe |
| Full analysis: | https://app.any.run/tasks/fee11d88-dccd-4f74-9d72-a6148502cb4b |
| Verdict: | Malicious activity |
| Analysis date: | July 16, 2024, 19:43:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64, for MS Windows |
| MD5: | 8CC9C90598900CECB00192DA74163250 |
| SHA1: | 8F7E488CE09CC8E1DB28E1A2A075EA59104B1978 |
| SHA256: | 1A107C3ECE1880CBBDC0A6C0817624B0DD033B02EBAF7FA366306AACA22C103D |
| SSDEEP: | 6144:reS/hL0JsERc5eRKov5CvG4pMaBN4m01BVUQ+qupTR:reS/hL0JR65ov5Ce4zz |
MALICIOUS
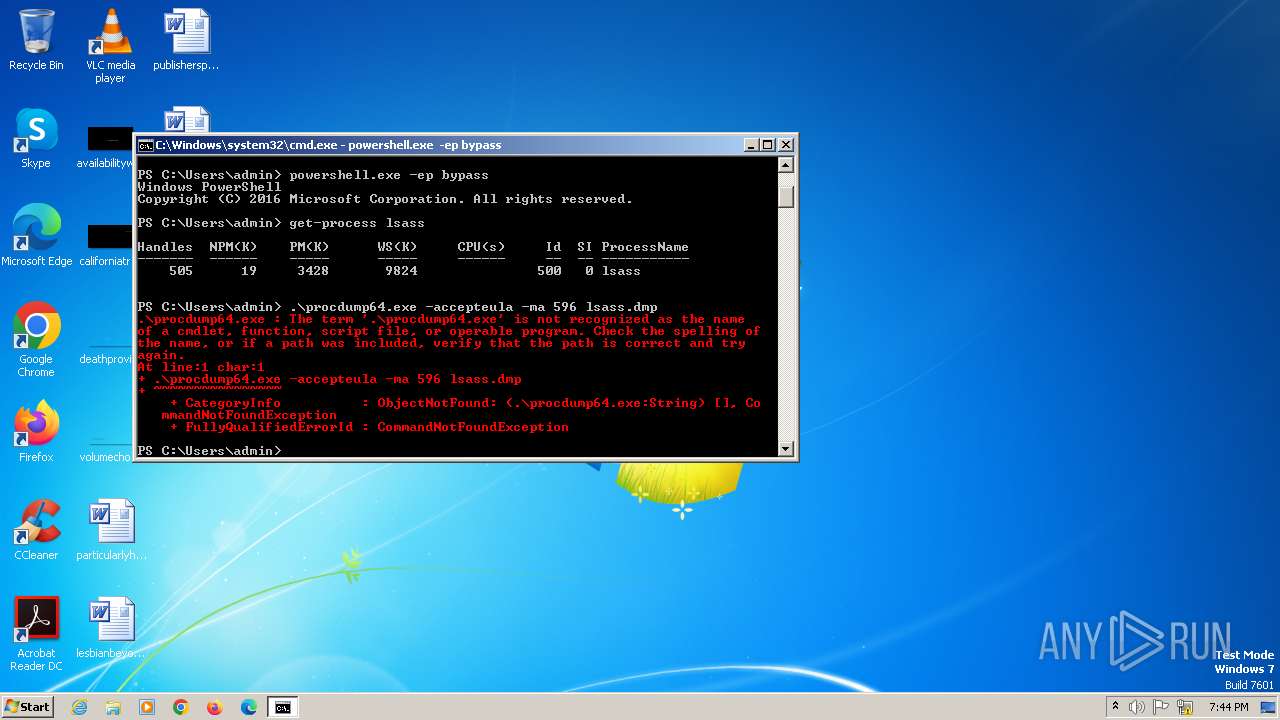
Drops the executable file immediately after the start
- procdump64.exe (PID: 1596)
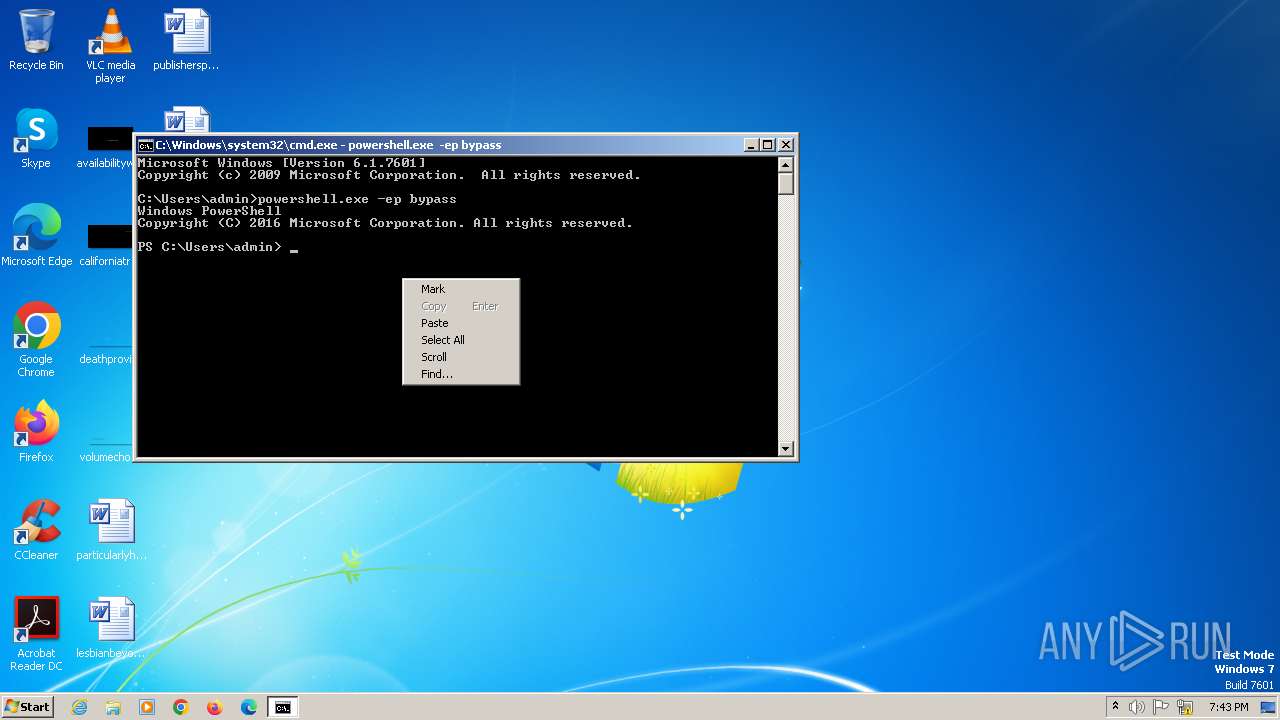
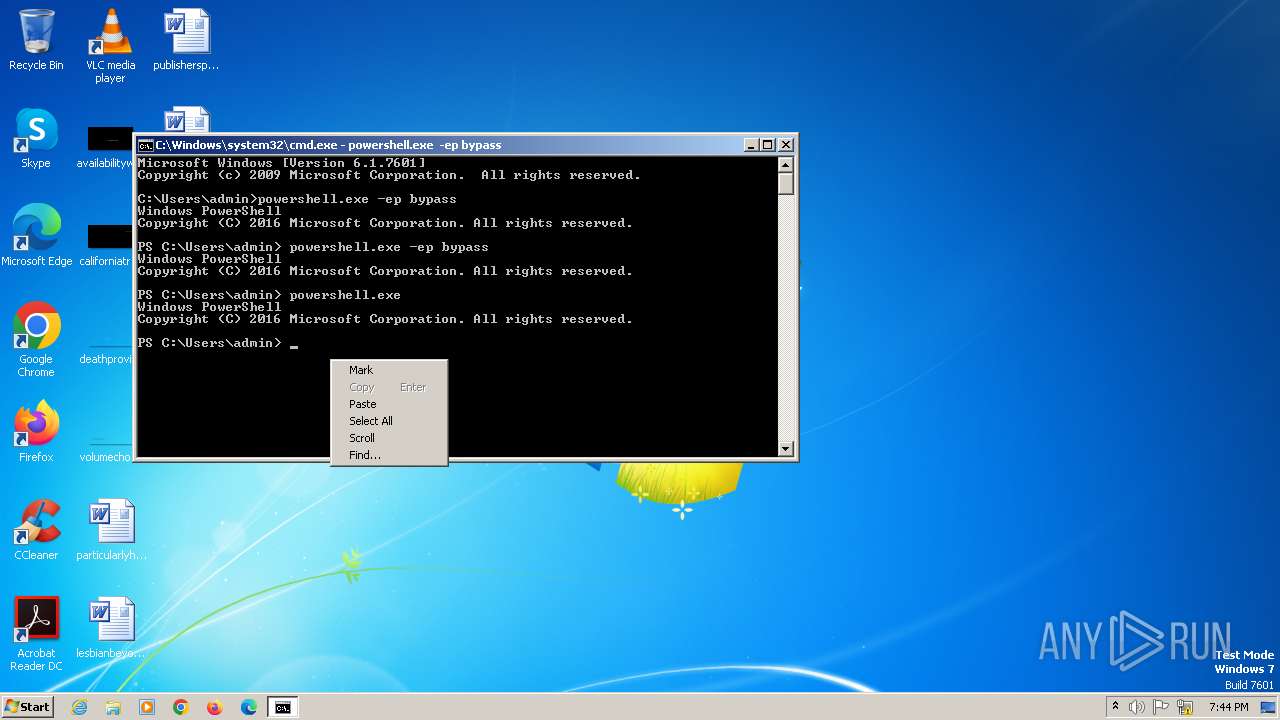
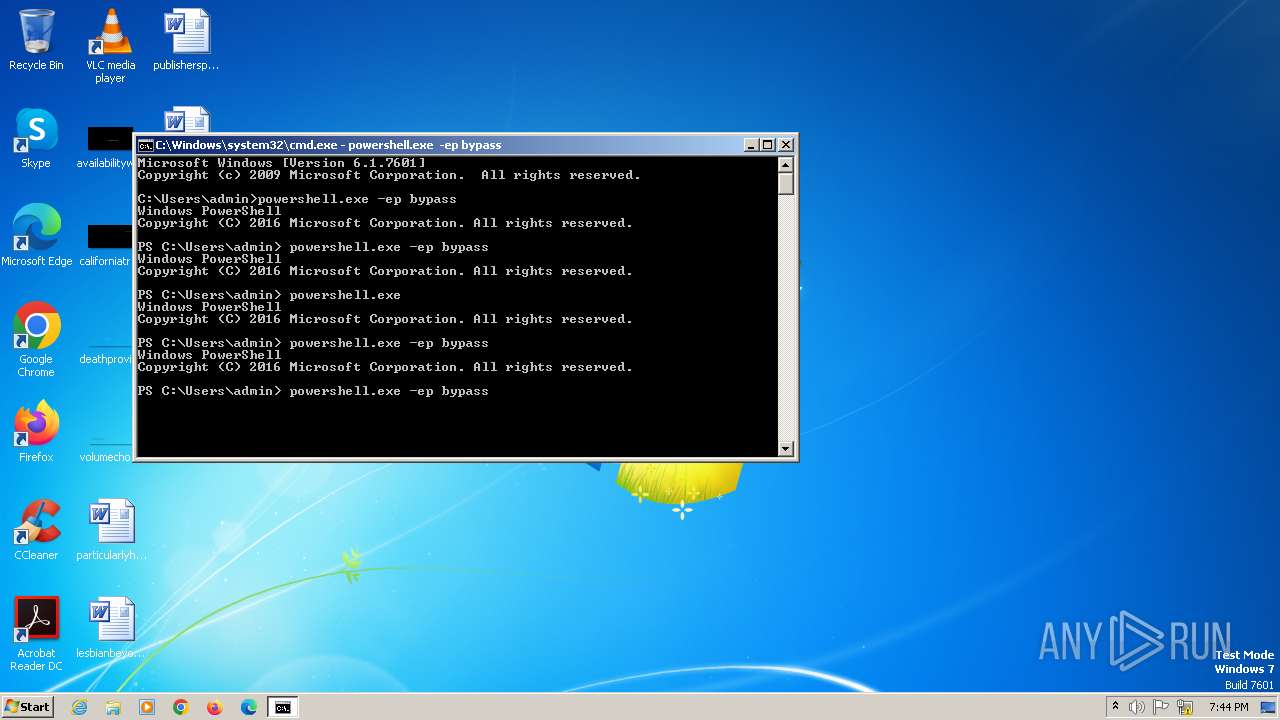
Bypass execution policy to execute commands
- powershell.exe (PID: 308)
- powershell.exe (PID: 2084)
- powershell.exe (PID: 2252)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 284)
- powershell.exe (PID: 2168)
- powershell.exe (PID: 308)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 284)
- powershell.exe (PID: 2084)
- powershell.exe (PID: 308)
- powershell.exe (PID: 2168)
Application launched itself
- powershell.exe (PID: 308)
- powershell.exe (PID: 2168)
- powershell.exe (PID: 2084)
INFO
Manual execution by a user
- cmd.exe (PID: 284)
Reads Environment values
- procdump64.exe (PID: 1596)
Checks supported languages
- procdump64.exe (PID: 1596)
Reads product name
- procdump64.exe (PID: 1596)
Reads the computer name
- procdump64.exe (PID: 1596)
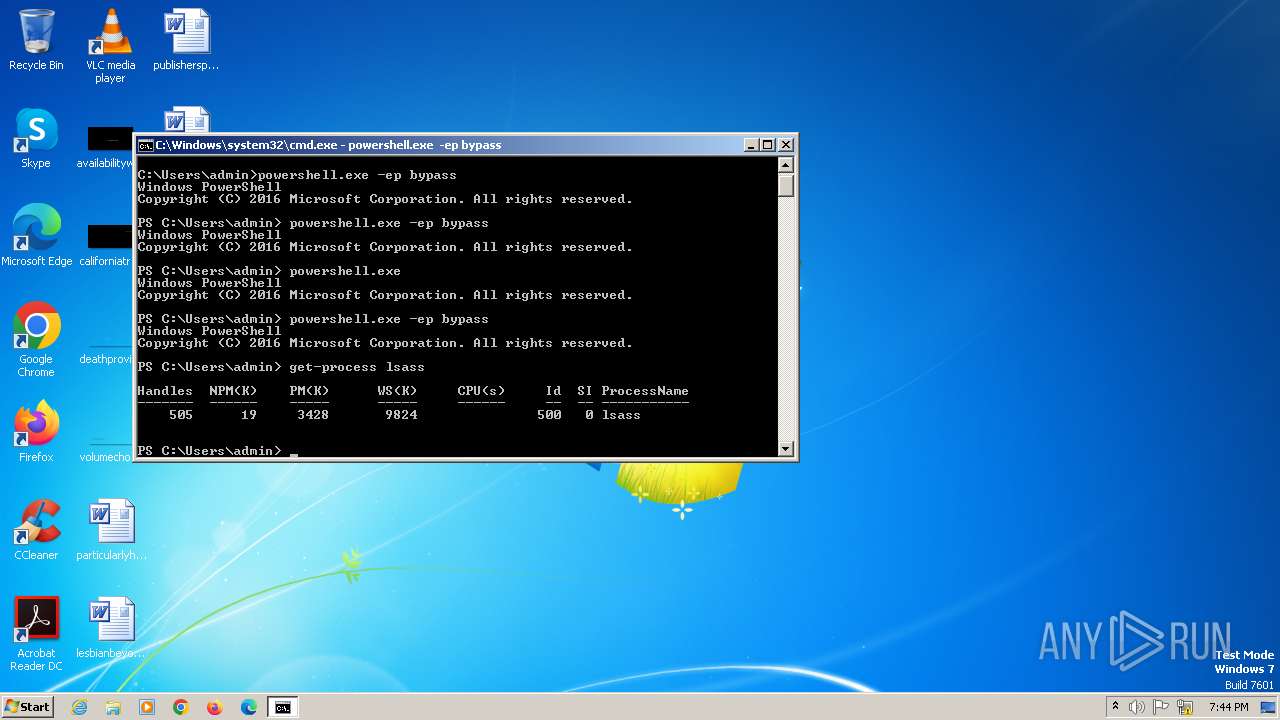
Checks current location (POWERSHELL)
- powershell.exe (PID: 308)
- powershell.exe (PID: 2084)
- powershell.exe (PID: 2252)
- powershell.exe (PID: 2168)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2252)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2021:08:16 12:54:28+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.29 |
| CodeSize: | 230912 |
| InitializedDataSize: | 172032 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1698c |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 10.1.1.0 |
| ProductVersionNumber: | 10.1.1.0 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Sysinternals - www.sysinternals.com |
| FileDescription: | Sysinternals process dump utility |
| FileVersion: | 10.11 |
| InternalName: | ProcDump |
| LegalCopyright: | Copyright (C) 2009-2021 Mark Russinovich and Andrew Richards |
| OriginalFileName: | procdump |
| ProductName: | ProcDump |
| ProductVersion: | 10.11 |
Total processes
38
Monitored processes
6
Malicious processes
1
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 308 | powershell.exe -ep bypass | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1596 | "C:\Users\admin\AppData\Local\Temp\procdump64.exe" | C:\Users\admin\AppData\Local\Temp\procdump64.exe | — | explorer.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Sysinternals process dump utility Exit code: 4294967295 Version: 10.11 Modules
| |||||||||||||||
| 2084 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2168 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2252 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
7 274
Read events
7 273
Write events
1
Delete events
0
Modification events
| (PID) Process: | (1596) procdump64.exe | Key: | HKEY_CURRENT_USER\Software\Sysinternals\ProcDump |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
Executable files
0
Suspicious files
8
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 308 | powershell.exe | C:\Users\admin\AppData\Local\Temp\eevumepu.tkp.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 308 | powershell.exe | C:\Users\admin\AppData\Local\Temp\gf4u21so.bwp.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2252 | powershell.exe | C:\Users\admin\AppData\Local\Temp\xxqvqplj.b0b.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2084 | powershell.exe | C:\Users\admin\AppData\Local\Temp\nulzc5mc.tpj.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2252 | powershell.exe | C:\Users\admin\AppData\Local\Temp\mrc0iztz.kqv.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2084 | powershell.exe | C:\Users\admin\AppData\Local\Temp\dguv3wzi.3wu.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2168 | powershell.exe | C:\Users\admin\AppData\Local\Temp\c2k1pyz4.14p.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2168 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ov2qt22l.zdq.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
360 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |