| File name: | satan.exe |
| Full analysis: | https://app.any.run/tasks/6111a7a0-53bb-4637-b378-eb7ff1574a1f |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 16:22:34 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | C9C341EAF04C89933ED28CBC2739D325 |
| SHA1: | C5B7D47AEF3BD33A24293138FCBA3A5FF286C2A8 |
| SHA256: | 1A0A2FD546E3C05E15B2DB3B531CB8E8755641F5F1C17910CE2FB7BBCE2A05B7 |
| SSDEEP: | 3072:H8SIBtQnE7OhssdWJ5jy392aCmCbBq0ryEbh/Wl7hqU6Q4NJ15xgDbvSY5thfRb3:c7qvhssdu5jyYaCmCQVE6hqUI5sb9Rb3 |
MALICIOUS
Runs injected code in another process
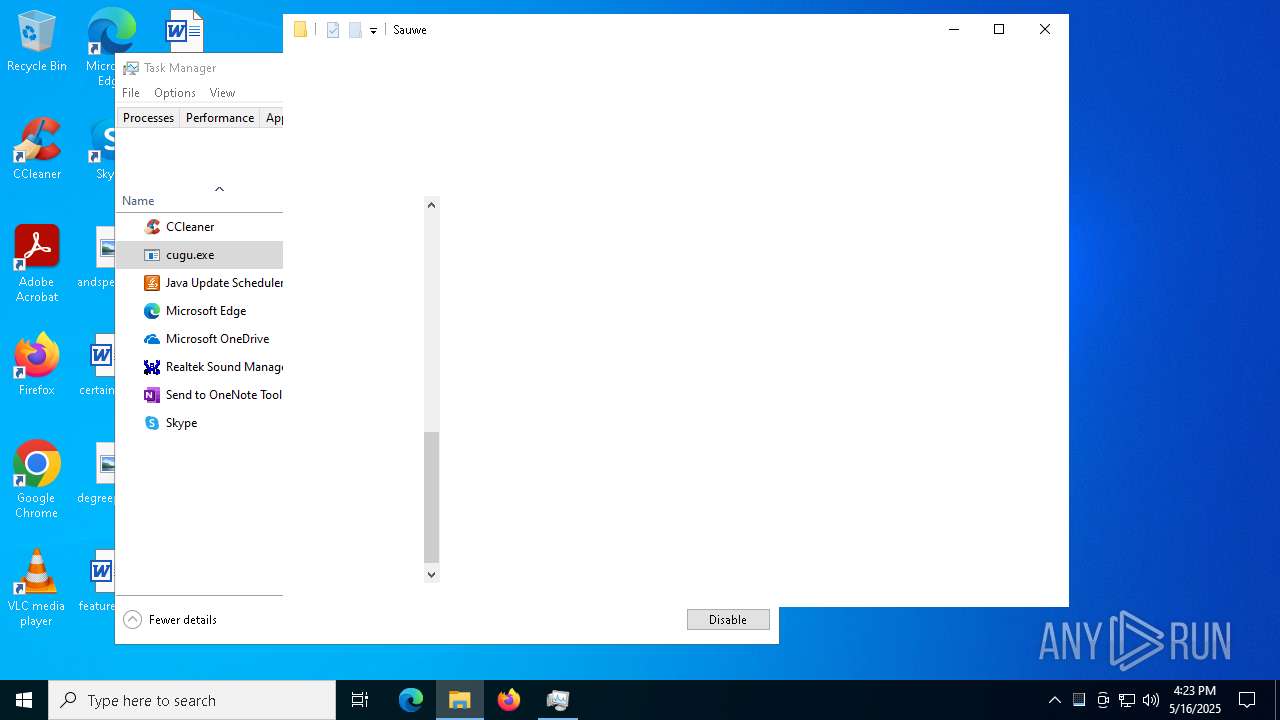
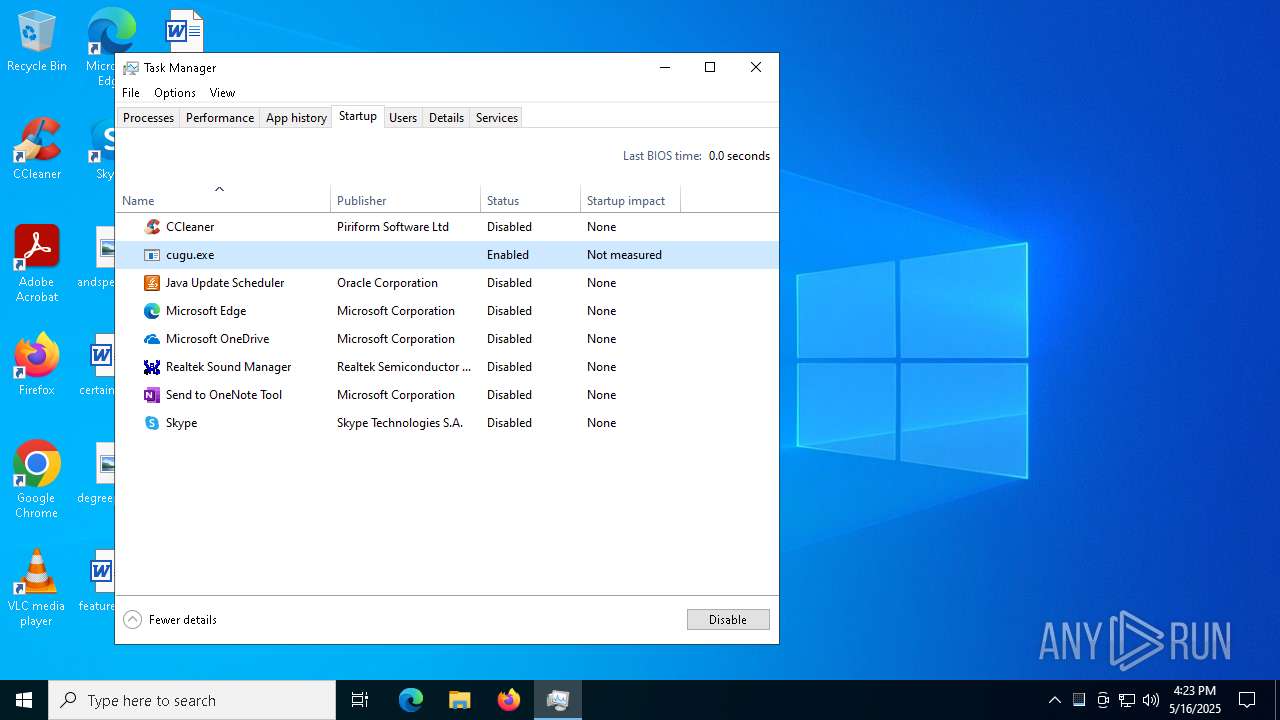
- cugu.exe (PID: 7448)
Application was injected by another process
- RuntimeBroker.exe (PID: 6160)
- svchost.exe (PID: 4544)
- sihost.exe (PID: 4984)
- svchost.exe (PID: 6608)
- StartMenuExperienceHost.exe (PID: 1968)
- explorer.exe (PID: 5492)
- SearchApp.exe (PID: 2924)
- dllhost.exe (PID: 6896)
- RuntimeBroker.exe (PID: 5368)
- ApplicationFrameHost.exe (PID: 6952)
- backgroundTaskHost.exe (PID: 2040)
- dllhost.exe (PID: 6176)
- TextInputHost.exe (PID: 6864)
- UserOOBEBroker.exe (PID: 1248)
- backgroundTaskHost.exe (PID: 3008)
- RuntimeBroker.exe (PID: 3032)
- RuntimeBroker.exe (PID: 1036)
- svchost.exe (PID: 4684)
- RuntimeBroker.exe (PID: 4528)
- svchost.exe (PID: 4952)
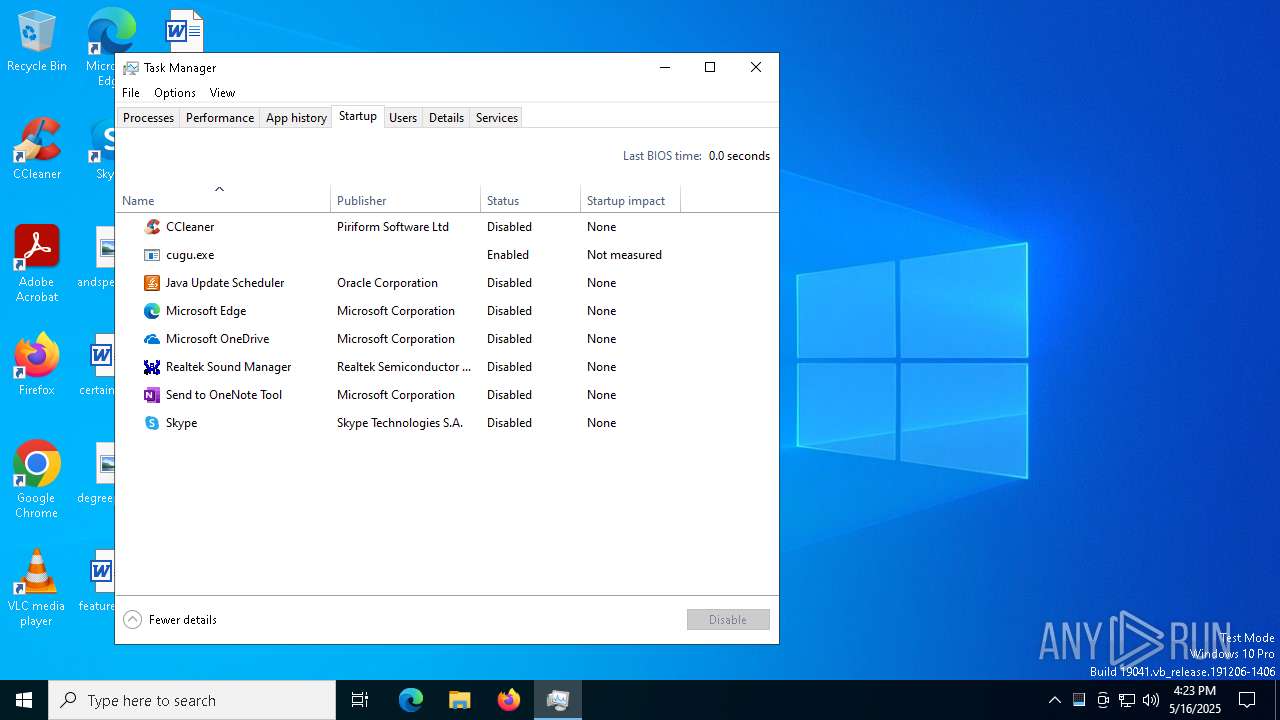
Changes the autorun value in the registry
- explorer.exe (PID: 5492)
Deletes shadow copies
- explorer.exe (PID: 5492)
Connects to the CnC server
- explorer.exe (PID: 5492)
SUSPICIOUS
Application launched itself
- satan.exe (PID: 7324)
- cugu.exe (PID: 7372)
- cugu.exe (PID: 1164)
Executable content was dropped or overwritten
- satan.exe (PID: 7344)
Starts CMD.EXE for commands execution
- satan.exe (PID: 7344)
Executing commands from a ".bat" file
- satan.exe (PID: 7344)
Contacting a server suspected of hosting an CnC
- explorer.exe (PID: 5492)
Block-list domains
- explorer.exe (PID: 5492)
INFO
Checks supported languages
- satan.exe (PID: 7344)
- satan.exe (PID: 7324)
- cugu.exe (PID: 7372)
- cugu.exe (PID: 7448)
- SearchApp.exe (PID: 2924)
- cugu.exe (PID: 1164)
- cugu.exe (PID: 4408)
Reads the machine GUID from the registry
- satan.exe (PID: 7324)
- satan.exe (PID: 7344)
- cugu.exe (PID: 7372)
- cugu.exe (PID: 7448)
- SearchApp.exe (PID: 2924)
- cugu.exe (PID: 1164)
- cugu.exe (PID: 4408)
Reads the computer name
- satan.exe (PID: 7344)
- satan.exe (PID: 7324)
- cugu.exe (PID: 7448)
- cugu.exe (PID: 7372)
- cugu.exe (PID: 1164)
- cugu.exe (PID: 4408)
Creates files or folders in the user directory
- satan.exe (PID: 7344)
Create files in a temporary directory
- satan.exe (PID: 7344)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5492)
- RuntimeBroker.exe (PID: 5368)
- Taskmgr.exe (PID: 7256)
Process checks computer location settings
- SearchApp.exe (PID: 2924)
Manual execution by a user
- vssadmin.exe (PID: 7596)
Reads the software policy settings
- SearchApp.exe (PID: 2924)
- slui.exe (PID: 7704)
Checks proxy server information
- explorer.exe (PID: 5492)
Local mutex for internet shortcut management
- RuntimeBroker.exe (PID: 5368)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:02:23 19:28:24+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 18432 |
| InitializedDataSize: | 84992 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x13b9 |
| OSVersion: | 5.1 |
| ImageVersion: | 1 |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
138
Monitored processes
36
Malicious processes
5
Suspicious processes
19
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1036 | C:\Windows\System32\RuntimeBroker.exe -Embedding | C:\Windows\System32\RuntimeBroker.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Runtime Broker Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
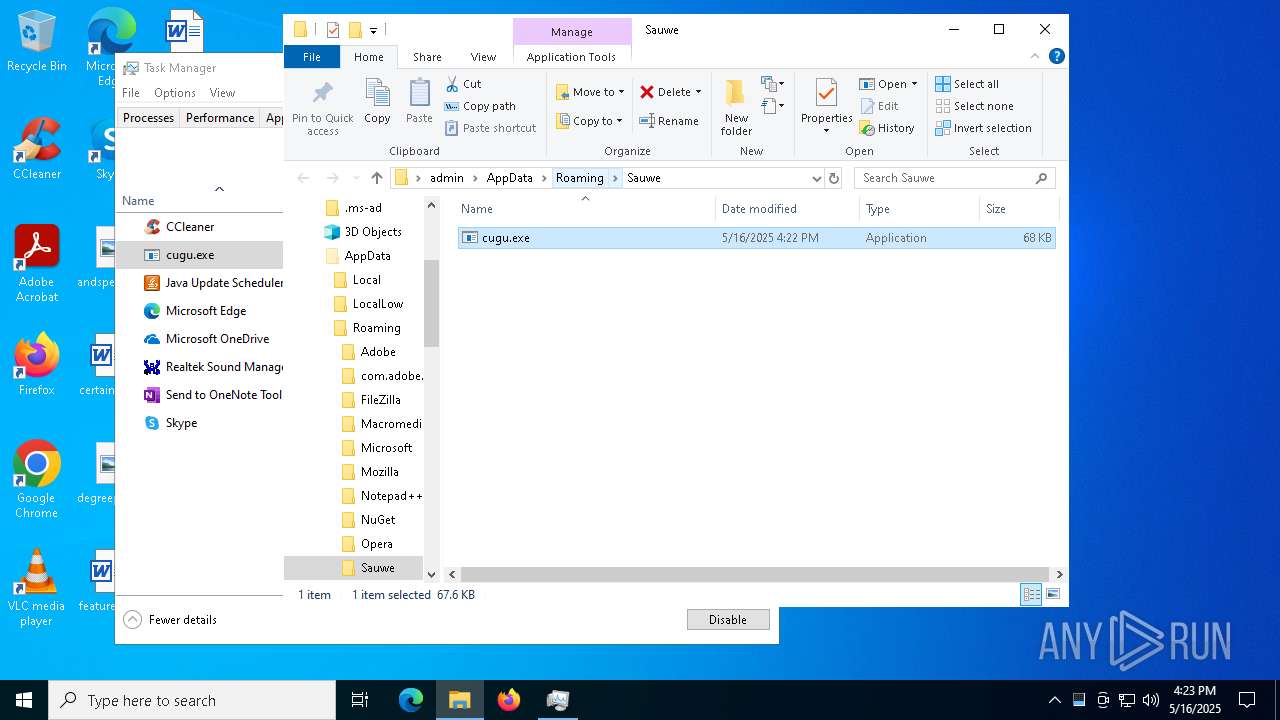
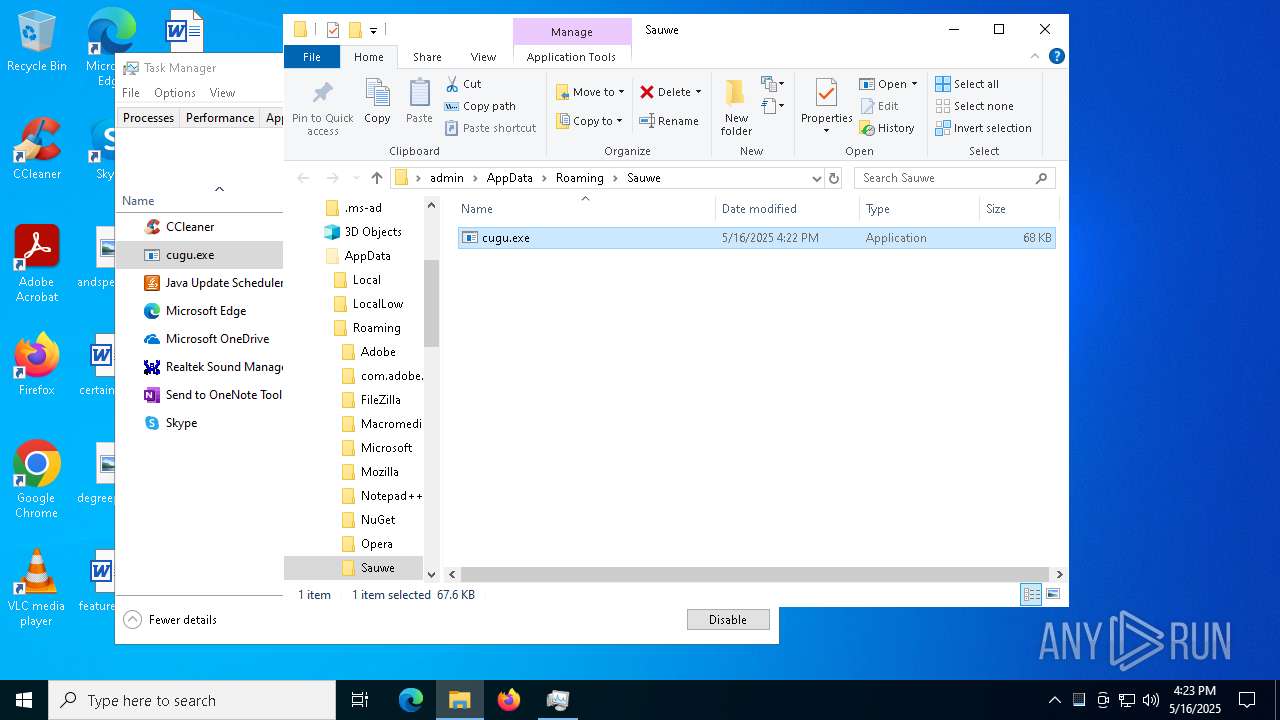
| 1164 | "C:\Users\admin\AppData\Roaming\Sauwe\cugu.exe" | C:\Users\admin\AppData\Roaming\Sauwe\cugu.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1248 | C:\Windows\System32\oobe\UserOOBEBroker.exe -Embedding | C:\Windows\System32\oobe\UserOOBEBroker.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: User OOBE Broker Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1968 | "C:\WINDOWS\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe" -ServerName:App.AppXywbrabmsek0gm3tkwpr5kwzbs55tkqay.mca | C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe | svchost.exe | ||||||||||||
User: admin Integrity Level: LOW Modules
| |||||||||||||||
| 2040 | "C:\WINDOWS\system32\backgroundTaskHost.exe" -ServerName:Global.IrisService.AppXwt29n3t7x7q6fgyrrbbqxwzkqjfjaw4y.mca | C:\Windows\System32\backgroundTaskHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Background Task Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2924 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3008 | "C:\WINDOWS\system32\backgroundTaskHost.exe" -ServerName:CortanaUI.AppX3bn25b6f886wmg6twh46972vprk9tnbf.mca | C:\Windows\System32\backgroundTaskHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Background Task Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3032 | C:\Windows\System32\RuntimeBroker.exe -Embedding | C:\Windows\System32\RuntimeBroker.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Runtime Broker Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3100 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3888 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
26 811
Read events
26 395
Write events
410
Delete events
6
Modification events
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | {DD57EE79-A67A-65F0-C4FE-C3891FCDB02A} |
Value: C:\Users\admin\AppData\Roaming\Sauwe\cugu.exe | |||
| (PID) Process: | (4984) sihost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppModel\SystemAppData\Microsoft.Windows.Search_cw5n1h2txyewy |
| Operation: | write | Name: | WasEverActivated |
Value: 1 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search |
| Operation: | write | Name: | TraySearchBoxVisible |
Value: 1 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search |
| Operation: | write | Name: | TraySearchBoxVisibleOnAnyMonitor |
Value: 1 | |||
| (PID) Process: | (4952) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Notifications\Settings |
| Operation: | write | Name: | QuietHoursTelemetryLastRun |
Value: 6966276800000000 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FeatureUsage\TrayButtonClicked |
| Operation: | write | Name: | StartButton |
Value: 149 | |||
| (PID) Process: | (1968) StartMenuExperienceHost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\CloudStore\Store\Cache\DefaultAccount\$de${c6a388c9-afd3-47e2-a46b-29cb43ad4323}$start.tilegrid$windows.data.curatedtilecollection.tilecollection\Current |
| Operation: | write | Name: | Data |
Value: 0200000060ABAECD7EC6DB0100000000434201000A0A00D0140CCA3200CB8C0A0212267B00410039003400310034003200440039002D0032003100350030002D0034003600380037002D0038003600390033002D003100450036003200320036003500390039003900430031007D000012267B00390033004600380044003900390046002D0036003500300041002D0034003100330035002D0038004200340043002D003200460046004100410041003300450046004600340039007D0000E22C01010000 | |||
| (PID) Process: | (2924) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Flighting |
| Operation: | delete value | Name: | CachedFeatureString |
Value: | |||
| (PID) Process: | (2924) SearchApp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.search_cw5n1h2txyewy\SOFTWARE\Microsoft\Speech_OneCore\Isolated\A1hdl50UVDh2ZbG324Nx-6fZgntcGnHOs5kHLdmaJYE\HKEY_CURRENT_USER\SOFTWARE\Microsoft\Speech_OneCore\Recognizers |
| Operation: | write | Name: | DefaultTokenId |
Value: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Speech_OneCore\Recognizers\Tokens\MS-1033-110-WINMO-DNN | |||
| (PID) Process: | (2924) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | IsMSACloudSearchEnabled |
Value: 0 | |||
Executable files
1
Suspicious files
3
Text files
72
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2924 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\TokenBroker\Cache\fbaf94e759052658216786bfbabcdced1b67a5c2.tbres | binary | |
MD5:E9F42156DC97F0EF7CE94A60F296E1D6 | SHA256:AB8916FE82D3A9D9C08330BE3C0070C59C609F4AFEA0831F8CB2868DE3841CFF | |||
| 2924 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\AppIconCache\100\https___java_com_ | image | |
MD5:83CA11E387A17C26A8F5D961F9C56B17 | SHA256:C22FAD60FEB2EFA565E07B0E75C7855F08333B0501956C84D2274E0BEE23C753 | |||
| 2924 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\AppIconCache\100\{1AC14E77-02E7-4E5D-B744-2EB1AE5198B7}_WindowsPowerShell_v1_0_PowerShell_ISE_exe | image | |
MD5:EB542559313A50C3BA5437B3A0E6C864 | SHA256:C1085B01B06F2612B284F1C0B4428827147108FFA08FC9474A8ACE2DF587884D | |||
| 2924 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\AppIconCache\100\Microsoft_Office_SETLANG_EXE_15 | image | |
MD5:666E2DA7AA58BB00CD3CFAE820917649 | SHA256:7D8CC9C51A193C088EE072F4F87D27D26402CF84CF51BCF0A9E221DE7C0DD17D | |||
| 2924 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\AppIconCache\100\Chrome | image | |
MD5:D25BE1489F9FF868F37AA5E3978C87D1 | SHA256:D360E5EE2B1A00A0052FBA05761FEA4C009963D656BC6D52947FC2D578AFF0E2 | |||
| 2924 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\Internet Explorer\DOMStore\ZWUI0EBX\www.bing[1].xml | text | |
MD5:89F44019F2BE1D5FC2A3802F7E4D7E34 | SHA256:29B081207109AD91906807D2BBE2210359E890CDEE3DFC1AC83E0AD300AA8840 | |||
| 7256 | Taskmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\3534848bb9f4cb71\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 2924 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\AppIconCache\100\MSEdge | image | |
MD5:D936BC59E11E91DAB4096D47FF5CA8D7 | SHA256:1A2348734A25E5DE91886BBD400D38ECCAB56157A2BBF86FE2140002769C012B | |||
| 2924 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\AppIconCache\100\http___www_ccleaner_com_ccleaner | image | |
MD5:D936BC59E11E91DAB4096D47FF5CA8D7 | SHA256:1A2348734A25E5DE91886BBD400D38ECCAB56157A2BBF86FE2140002769C012B | |||
| 2924 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\AppIconCache\100\Microsoft_AutoGenerated_{DAA168DE-4306-C8BC-8C11-B596240BDDED} | image | |
MD5:2B892F063231C9BA578162A23D97629C | SHA256:DCF367B1E19764053D11265ABD0C398B04E8B966BA92AC6D9DEACA59101A2574 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
54
DNS requests
15
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5492 | explorer.exe | POST | 404 | 144.202.70.158:80 | http://6pi3jrqjbssfh6gu.onion.pw/g.php | unknown | — | — | whitelisted |
5492 | explorer.exe | POST | 404 | 144.202.70.158:80 | http://6pi3jrqjbssfh6gu.onion.pw/g.php | unknown | — | — | whitelisted |
5492 | explorer.exe | POST | 404 | 144.202.70.158:80 | http://6pi3jrqjbssfh6gu.onion.pw/g.php | unknown | — | — | whitelisted |
5492 | explorer.exe | POST | 404 | 144.202.70.158:80 | http://6pi3jrqjbssfh6gu.onion.pw/g.php | unknown | — | — | whitelisted |
5492 | explorer.exe | POST | 404 | 144.202.70.158:80 | http://6pi3jrqjbssfh6gu.onion.pw/g.php | unknown | — | — | whitelisted |
5492 | explorer.exe | POST | 404 | 144.202.70.158:80 | http://6pi3jrqjbssfh6gu.onion.pw/g.php | unknown | — | — | whitelisted |
5492 | explorer.exe | POST | 404 | 144.202.70.158:80 | http://6pi3jrqjbssfh6gu.onion.pw/g.php | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
5492 | explorer.exe | 144.202.70.158:80 | 6pi3jrqjbssfh6gu.onion.pw | AS-CHOOPA | US | malicious |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2924 | SearchApp.exe | 2.23.227.215:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
6544 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
720 | SIHClient.exe | 20.12.23.50:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
720 | SIHClient.exe | 52.165.164.15:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2924 | SearchApp.exe | 204.79.197.222:443 | fp.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
6pi3jrqjbssfh6gu.onion.pw |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
15.164.165.52.in-addr.arpa |
| unknown |
6.0.1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.7.0.0.0.0.3.0.1.3.0.6.2.ip6.arpa |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
— | — | Potentially Bad Traffic | ET INFO DNS Query to .onion proxy Domain (onion. pw) |
5492 | explorer.exe | Malware Command and Control Activity Detected | ET MALWARE Zbot POST Request to C2 |
5492 | explorer.exe | Misc activity | ET INFO HTTP Request to a *.pw domain |
5492 | explorer.exe | Malware Command and Control Activity Detected | ET MALWARE Zbot POST Request to C2 |
5492 | explorer.exe | Misc activity | ET INFO HTTP Request to a *.pw domain |
5492 | explorer.exe | Malware Command and Control Activity Detected | ET MALWARE Zbot POST Request to C2 |
5492 | explorer.exe | Misc activity | ET INFO HTTP Request to a *.pw domain |
5492 | explorer.exe | Misc activity | ET INFO HTTP Request to a *.pw domain |
5492 | explorer.exe | Malware Command and Control Activity Detected | ET MALWARE Zbot POST Request to C2 |