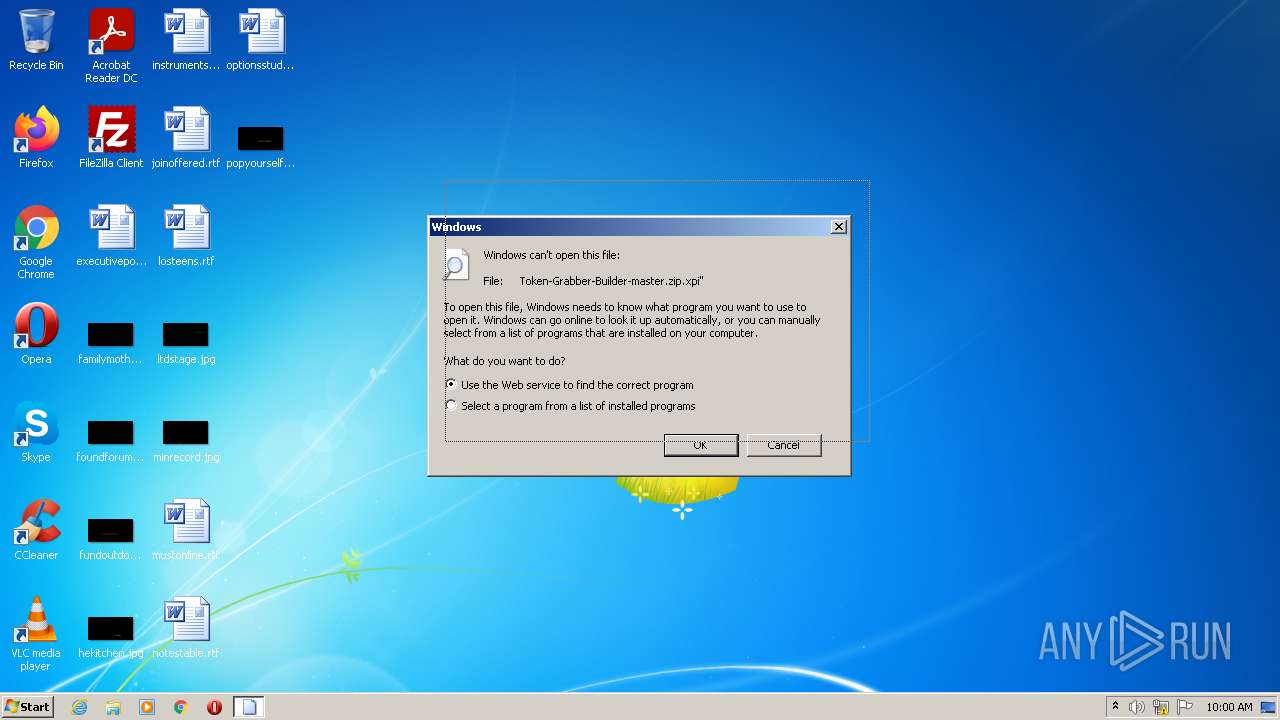
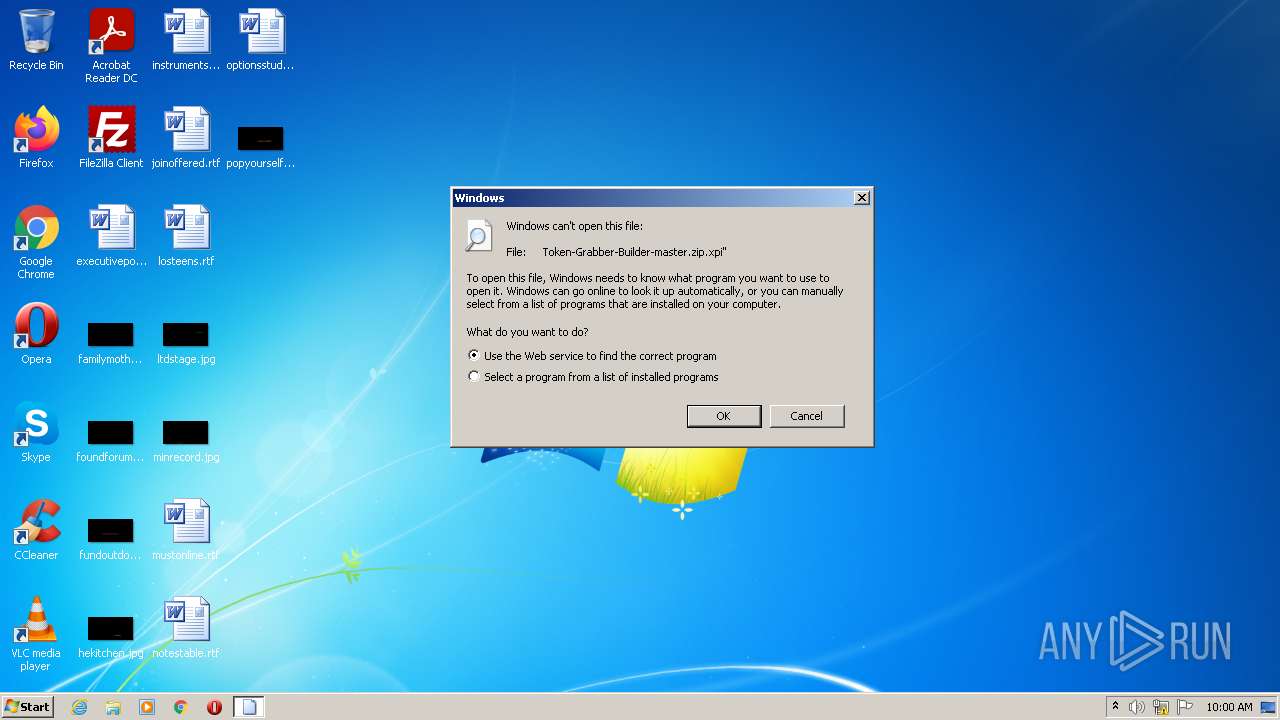
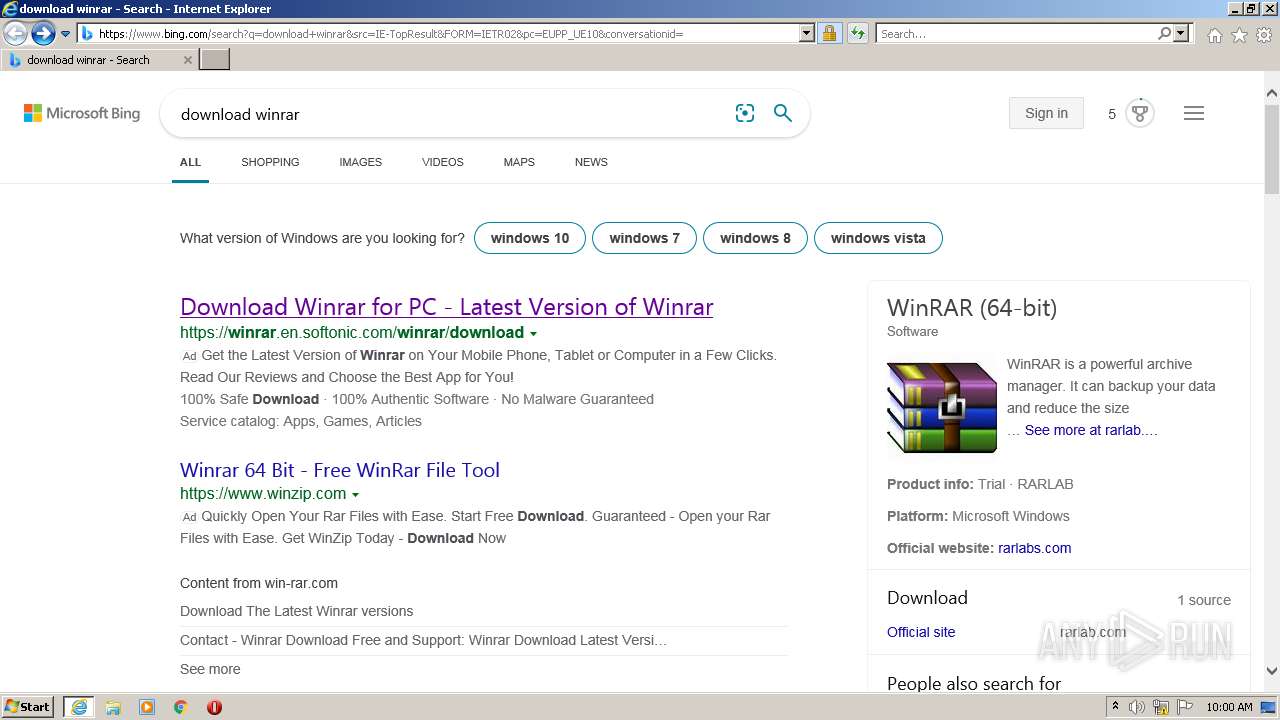
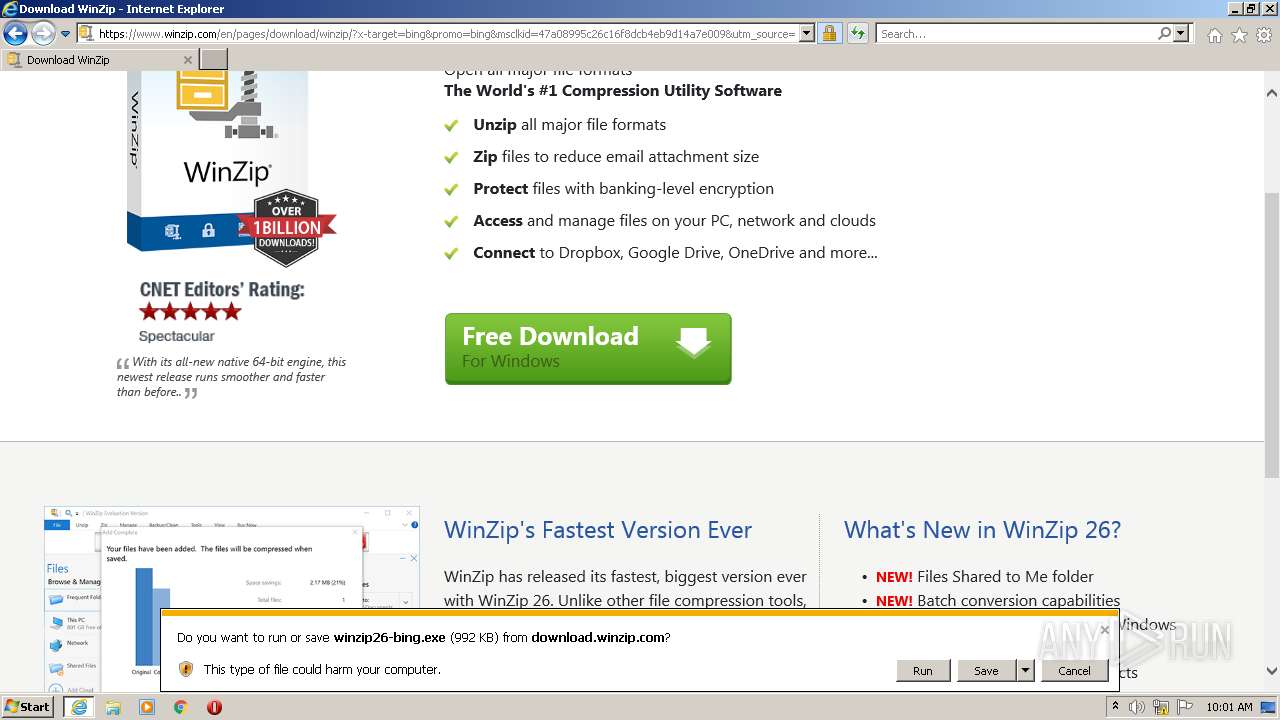
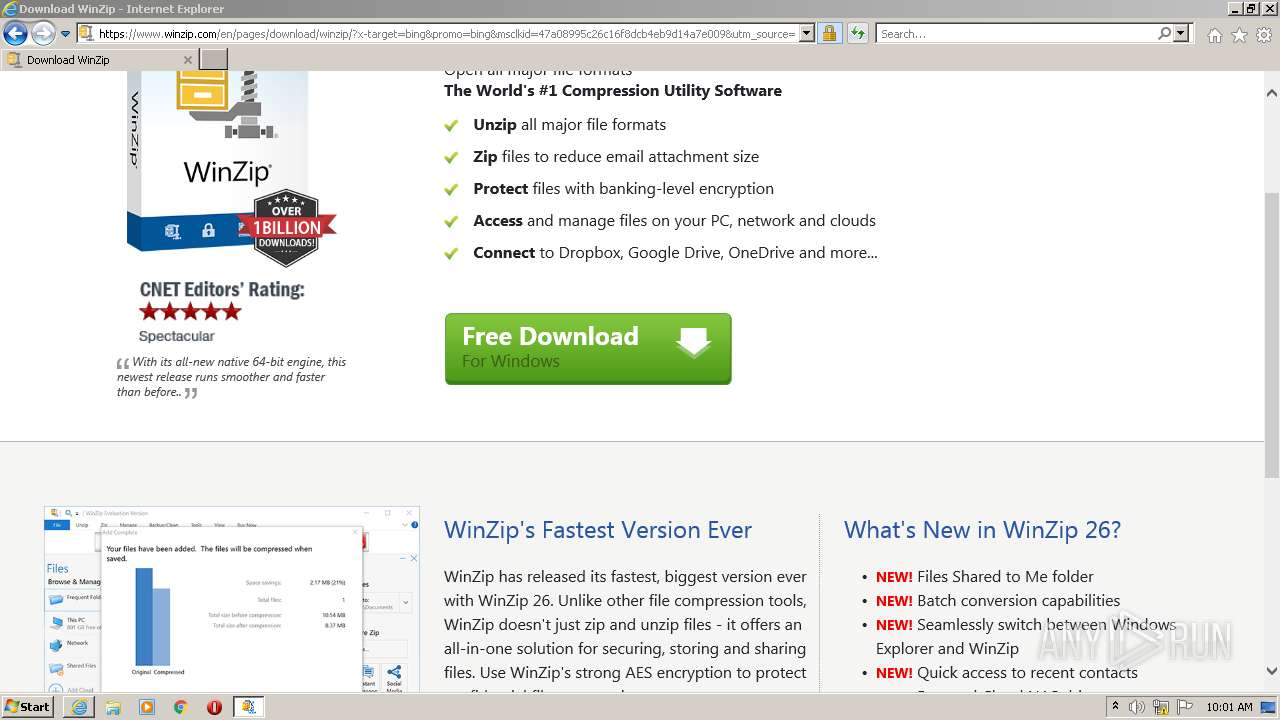
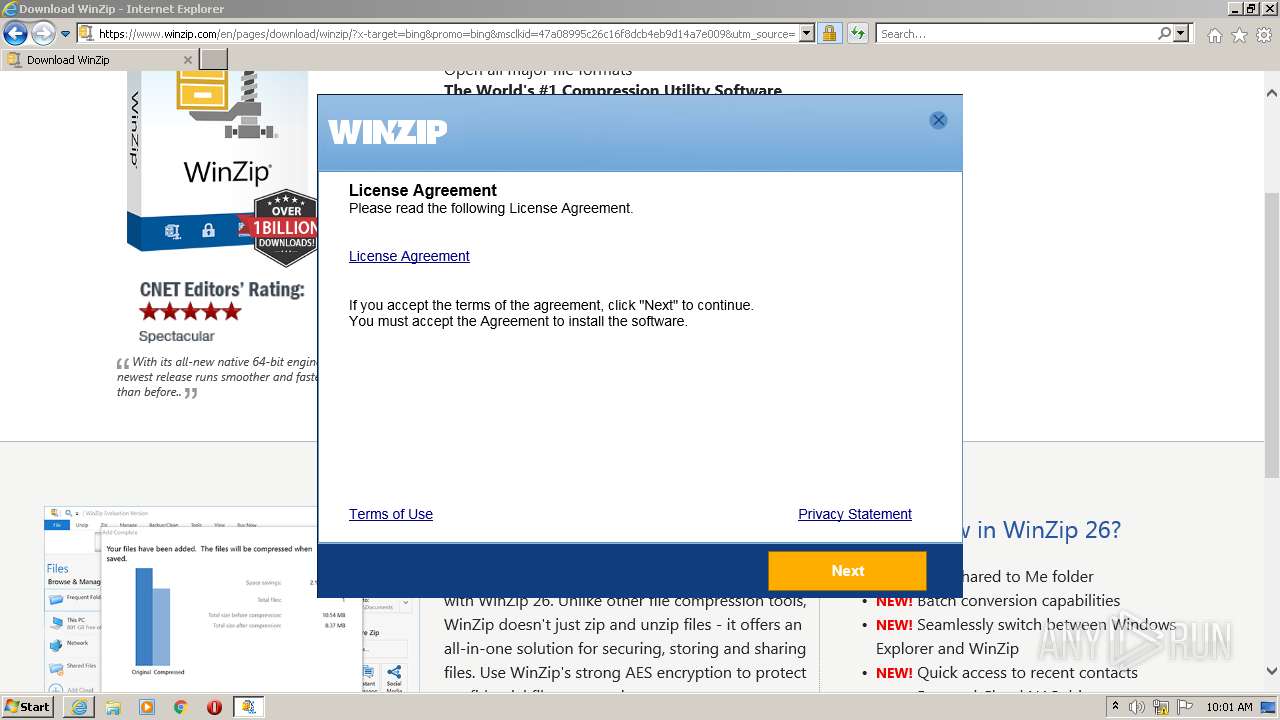
| File name: | Token-Grabber-Builder-master.zip |
| Full analysis: | https://app.any.run/tasks/c14200c8-1a7a-451b-8b85-ed11012b3dd0 |
| Verdict: | Malicious activity |
| Analysis date: | February 13, 2022, 10:00:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 945332DEB05856B3BBB8264C71895E3E |
| SHA1: | 8BE40DA147243B5628AF3988254F53666FB58956 |
| SHA256: | 19F3B2CA31B3947537208F640E31A3CF29B1898A03E2B950926A3163DF18619A |
| SSDEEP: | 768:U6AMCDkppk7RV/BIRb/gBQ1p9nhTn84GN7GBSAl7wU9g7rJppn+DM0RkouCol71G:ZC9qRTgB6nNYuNl7wU96rJpFakouFr3y |
MALICIOUS
Application was dropped or rewritten from another process
- winzip26-bing.exe (PID: 3932)
- winzip26-bing.exe (PID: 3812)
- winzip26-bing.exe (PID: 736)
- FAHWindow32.exe (PID: 3044)
- adxregistrator.exe (PID: 3836)
- FAHConsole.exe (PID: 1424)
- CloseFAH.exe (PID: 2324)
- WzPreloader.exe (PID: 2796)
- adxregistrator.exe (PID: 3304)
- WzPreviewer32.exe (PID: 3792)
- WZUpdateNotifier.exe (PID: 2572)
- WzBGTComServer32.exe (PID: 348)
- WzBGTools32.exe (PID: 3508)
- WzCABCacheSyncHelper32.exe (PID: 2720)
Drops executable file immediately after starts
- winzip26-bing.exe (PID: 3932)
Changes the autorun value in the registry
- msiexec.exe (PID: 2372)
Changes settings of System certificates
- MsiExec.exe (PID: 1176)
Loads dropped or rewritten executable
- csrss.exe (PID: 668)
- msiexec.exe (PID: 2372)
- WzCABCacheSyncHelper32.exe (PID: 2720)
- svchost.exe (PID: 876)
- FAHWindow32.exe (PID: 3044)
- adxregistrator.exe (PID: 3836)
- MsiExec.exe (PID: 1176)
- winzip32.exe (PID: 1808)
Writes to a start menu file
- msiexec.exe (PID: 2372)
Runs injected code in another process
- FAHWindow32.exe (PID: 3044)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2896)
- schtasks.exe (PID: 3004)
- schtasks.exe (PID: 3944)
Application was injected by another process
- Explorer.EXE (PID: 612)
Uses Task Scheduler to run other applications
- MsiExec.exe (PID: 3260)
SUSPICIOUS
Uses RUNDLL32.EXE to load library
- Explorer.EXE (PID: 612)
Starts Internet Explorer
- rundll32.exe (PID: 492)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2764)
- iexplore.exe (PID: 1344)
- iexplore.exe (PID: 1492)
- winzip26-bing.exe (PID: 3812)
- MsiExec.exe (PID: 1176)
- winzip32.exe (PID: 1808)
Executable content was dropped or overwritten
- iexplore.exe (PID: 1492)
- iexplore.exe (PID: 1344)
- winzip26-bing.exe (PID: 3932)
- MsiExec.exe (PID: 3260)
- msiexec.exe (PID: 2372)
- MsiExec.exe (PID: 1176)
Starts itself from another location
- winzip26-bing.exe (PID: 3932)
Checks supported languages
- winzip26-bing.exe (PID: 3812)
- winzip26-bing.exe (PID: 3932)
- CloseFAH.exe (PID: 2324)
- WzPreviewer32.exe (PID: 3792)
- WzPreloader.exe (PID: 2796)
- winzip32.exe (PID: 1808)
- WzCABCacheSyncHelper32.exe (PID: 2720)
- FAHConsole.exe (PID: 1424)
- FAHWindow32.exe (PID: 3044)
- adxregistrator.exe (PID: 3836)
- adxregistrator.exe (PID: 3304)
- WzBGTComServer32.exe (PID: 348)
- WZUpdateNotifier.exe (PID: 2572)
- WzBGTools32.exe (PID: 3508)
Reads internet explorer settings
- winzip26-bing.exe (PID: 3812)
Creates files in the program directory
- winzip26-bing.exe (PID: 3812)
- msiexec.exe (PID: 2372)
- winzip32.exe (PID: 1808)
- MsiExec.exe (PID: 1176)
Searches for installed software
- msiexec.exe (PID: 2372)
- MsiExec.exe (PID: 1176)
- winzip32.exe (PID: 1808)
Reads the computer name
- winzip26-bing.exe (PID: 3812)
- WzPreloader.exe (PID: 2796)
- winzip32.exe (PID: 1808)
- WzCABCacheSyncHelper32.exe (PID: 2720)
- FAHWindow32.exe (PID: 3044)
- adxregistrator.exe (PID: 3304)
- WzBGTools32.exe (PID: 3508)
- adxregistrator.exe (PID: 3836)
Reads Environment values
- vssvc.exe (PID: 848)
- WzCABCacheSyncHelper32.exe (PID: 2720)
Reads Windows owner or organization settings
- winzip26-bing.exe (PID: 3812)
- msiexec.exe (PID: 2372)
Executed as Windows Service
- msiexec.exe (PID: 2372)
- vssvc.exe (PID: 848)
Reads the Windows organization settings
- winzip26-bing.exe (PID: 3812)
- msiexec.exe (PID: 2372)
Application launched itself
- msiexec.exe (PID: 2372)
Drops a file that was compiled in debug mode
- MsiExec.exe (PID: 3260)
- MsiExec.exe (PID: 1176)
- msiexec.exe (PID: 2372)
Creates a directory in Program Files
- msiexec.exe (PID: 2372)
Drops a file with too old compile date
- msiexec.exe (PID: 2372)
Drops a file with a compile date too recent
- msiexec.exe (PID: 2372)
- MsiExec.exe (PID: 1176)
Executed via COM
- DllHost.exe (PID: 3236)
Creates a software uninstall entry
- msiexec.exe (PID: 2372)
- winzip32.exe (PID: 1808)
Creates files in the Windows directory
- MsiExec.exe (PID: 1176)
- svchost.exe (PID: 876)
Changes IE settings (feature browser emulation)
- msiexec.exe (PID: 2372)
- MsiExec.exe (PID: 1176)
Adds / modifies Windows certificates
- MsiExec.exe (PID: 1176)
Changes default file association
- msiexec.exe (PID: 2372)
- winzip32.exe (PID: 1808)
Creates files in the user directory
- winzip32.exe (PID: 1808)
Reads default file associations for system extensions
- Explorer.EXE (PID: 612)
Loads DLL from Mozilla Firefox
- csrss.exe (PID: 668)
Creates/Modifies COM task schedule object
- winzip32.exe (PID: 1808)
- adxregistrator.exe (PID: 3304)
- MsiExec.exe (PID: 1176)
- adxregistrator.exe (PID: 3836)
INFO
Reads the computer name
- iexplore.exe (PID: 1344)
- rundll32.exe (PID: 492)
- iexplore.exe (PID: 2764)
- iexplore.exe (PID: 1492)
- msiexec.exe (PID: 2372)
- vssvc.exe (PID: 848)
- MsiExec.exe (PID: 3260)
- MsiExec.exe (PID: 1176)
- DllHost.exe (PID: 3236)
- schtasks.exe (PID: 2896)
- schtasks.exe (PID: 3004)
- schtasks.exe (PID: 3944)
- explorer.exe (PID: 2824)
Changes internet zones settings
- iexplore.exe (PID: 1344)
Checks supported languages
- rundll32.exe (PID: 492)
- iexplore.exe (PID: 1344)
- iexplore.exe (PID: 2764)
- iexplore.exe (PID: 1492)
- vssvc.exe (PID: 848)
- msiexec.exe (PID: 2372)
- MsiExec.exe (PID: 3260)
- MsiExec.exe (PID: 1176)
- DllHost.exe (PID: 3236)
- schtasks.exe (PID: 2896)
- svchost.exe (PID: 876)
- schtasks.exe (PID: 3004)
- schtasks.exe (PID: 3944)
- explorer.exe (PID: 2824)
Application launched itself
- iexplore.exe (PID: 1344)
Reads settings of System Certificates
- iexplore.exe (PID: 2764)
- iexplore.exe (PID: 1344)
- iexplore.exe (PID: 1492)
- winzip26-bing.exe (PID: 3812)
- msiexec.exe (PID: 2372)
- MsiExec.exe (PID: 1176)
- winzip32.exe (PID: 1808)
Checks Windows Trust Settings
- iexplore.exe (PID: 1344)
- iexplore.exe (PID: 1492)
- iexplore.exe (PID: 2764)
- winzip26-bing.exe (PID: 3812)
- MsiExec.exe (PID: 1176)
- msiexec.exe (PID: 2372)
- winzip32.exe (PID: 1808)
Creates files in the user directory
- iexplore.exe (PID: 2764)
- iexplore.exe (PID: 1344)
Reads internet explorer settings
- iexplore.exe (PID: 2764)
- iexplore.exe (PID: 1492)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1344)
Changes settings of System certificates
- iexplore.exe (PID: 1344)
Modifies the phishing filter of IE
- iexplore.exe (PID: 1344)
Dropped object may contain Bitcoin addresses
- msiexec.exe (PID: 2372)
Reads Microsoft Office registry keys
- adxregistrator.exe (PID: 3836)
- adxregistrator.exe (PID: 3304)
Manual execution by user
- explorer.exe (PID: 2824)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipFileName: | Token-Grabber-Builder-master/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2021:05:13 19:57:19 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 10 |
Total processes
76
Monitored processes
31
Malicious processes
15
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 348 | "C:\Program Files\WinZip\WzBGTComServer32.exe" /REGSERVER | C:\Program Files\WinZip\WzBGTComServer32.exe | — | msiexec.exe |
User: admin Company: WinZip Computing Integrity Level: HIGH Description: WinZip Background Tool Exit code: 0 Version: 26.0.14596.0 | ||||
| 492 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL "C:\Users\admin\AppData\Local\Temp\Token-Grabber-Builder-master.zip.xpi" | C:\Windows\system32\rundll32.exe | — | Explorer.EXE |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 612 | C:\Windows\Explorer.EXE | C:\Windows\Explorer.EXE | — | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 668 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,12288,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\system32\csrss.exe | — | — |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 736 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\winzip26-bing.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\winzip26-bing.exe | — | iexplore.exe |
User: admin Company: WinZip Computing Integrity Level: MEDIUM Description: WinZipStub Installer Exit code: 3221226540 Version: 26.0.14575.0 | ||||
| 848 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft� Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 876 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\system32\svchost.exe | — | services.exe |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 1176 | C:\Windows\system32\MsiExec.exe -Embedding D0058C9A1B434D99242BCF6E9DA789A1 E Global\MSI0000 | C:\Windows\system32\MsiExec.exe | msiexec.exe | |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows� installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) | ||||
| 1344 | "C:\Program Files\Internet Explorer\iexplore.exe" http://go.microsoft.com/fwlink/?LinkId=57426&Ext=xpi" | C:\Program Files\Internet Explorer\iexplore.exe | rundll32.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) | ||||
| 1424 | "C:\Program Files\WinZip\FAHConsole.exe" | C:\Program Files\WinZip\FAHConsole.exe | — | MsiExec.exe |
User: SYSTEM Company: WinZip Computing, S.L. Integrity Level: SYSTEM Description: File Association Helper Exit code: 0 Version: 3.0.0.11 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
316
Suspicious files
73
Text files
495
Unknown types
96
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2764 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\9UWBIILA.txt | text | |
MD5:— | SHA256:— | |||
| 2764 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\0DO42GBG.txt | text | |
MD5:— | SHA256:— | |||
| 2764 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\G178016G.txt | text | |
MD5:— | SHA256:— | |||
| 2764 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\WO14LXXM.txt | text | |
MD5:— | SHA256:— | |||
| 2764 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\qsml[1].xml | xml | |
MD5:— | SHA256:— | |||
| 2764 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\B9GZN1CQ.txt | text | |
MD5:— | SHA256:— | |||
| 2764 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\qsml[1].xml | xml | |
MD5:— | SHA256:— | |||
| 2764 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\qsml[1].htm | xml | |
MD5:— | SHA256:— | |||
| 2764 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\KP908ZON.txt | text | |
MD5:— | SHA256:— | |||
| 1344 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\StructuredQuery.log | text | |
MD5:32418AAD6A59377813B0DCA5B0B79EDB | SHA256:D9E699252C740D93344BCC332D739B13FB6B5261F3430ACB75D5E19ED7638D06 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
53
TCP/UDP connections
234
DNS requests
82
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2764 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
2764 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
2764 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
2764 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
2764 | iexplore.exe | GET | 200 | 65.9.84.221:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
2764 | iexplore.exe | GET | 200 | 104.18.30.182:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQC0eKdRMTzmwh4ySFgYIPuD | US | der | 472 b | whitelisted |
2764 | iexplore.exe | GET | 200 | 192.124.249.24:80 | http://ocsp.godaddy.com//MEQwQjBAMD4wPDAJBgUrDgMCGgUABBTkIInKBAzXkF0Qh0pel3lfHJ9GPAQU0sSw0pHUTBFxs2HLPaH%2B3ahq1OMCAxvnFQ%3D%3D | US | der | 1.66 Kb | whitelisted |
2764 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
2764 | iexplore.exe | GET | 200 | 18.66.242.58:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
2764 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEH8SKh5qcwxcCgAAAAEvj7Q%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2764 | iexplore.exe | 104.89.38.104:443 | go.microsoft.com | Akamai Technologies, Inc. | NL | malicious |
2764 | iexplore.exe | 92.123.224.107:80 | shell.windows.com | Akamai International B.V. | — | suspicious |
2764 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2764 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2764 | iexplore.exe | 13.107.5.80:443 | api.bing.com | Microsoft Corporation | US | whitelisted |
1344 | iexplore.exe | 13.107.22.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2764 | iexplore.exe | 13.107.22.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2764 | iexplore.exe | 20.190.151.68:443 | login.microsoftonline.com | Microsoft Corporation | US | suspicious |
2764 | iexplore.exe | 35.227.233.104:443 | winrar.en.softonic.com | — | US | malicious |
2764 | iexplore.exe | 18.64.79.9:443 | sdk.privacy-center.org | Massachusetts Institute of Technology | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
shell.windows.com |
| whitelisted |
login.microsoftonline.com |
| whitelisted |
login.live.com |
| whitelisted |
winrar.en.softonic.com |
| malicious |
ocsp.comodoca.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2764 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2764 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2764 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2764 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2764 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2764 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2764 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2764 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
1176 | MsiExec.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
1808 | winzip32.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |