| File name: | TeraCopy.exe |
| Full analysis: | https://app.any.run/tasks/9018c000-98b7-46b5-a46a-62701738cc3e |
| Verdict: | Suspicious activity |
| Analysis date: | February 07, 2019, 07:45:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 3130E763ADAF55BC94694EB71459668D |
| SHA1: | 1E41DB86D44EEACCE2947E4FA384AB9B58601D75 |
| SHA256: | 19E6A69B7F10D8342DA2172D683F87664B8DCD0D28F80ADE3E8357AEC9BB1314 |
| SSDEEP: | 98304:2OYYYYYYYYYYYRYYYYYYYYYYB6adUmTviCJ:m6aCmTvia |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates files in the user directory
- TeraCopy.exe (PID: 3040)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | DOS Executable Generic (100) |
|---|
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:10:16 12:56:30+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 2832384 |
| InitializedDataSize: | 2555392 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x748000 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.2.6.0 |
| ProductVersionNumber: | 3.2.6.0 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | Debug |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Unknown (0009) |
| CharacterSet: | Unicode |
| CompanyName: | Code Sector |
| FileDescription: | TeraCopy |
| FileVersion: | 3.2.6.0 |
| InternalName: | TeraCopy |
| LegalCopyright: | (C) 2007-2017 Code Sector |
| OriginalFileName: | TeraCopy.exe |
| ProductName: | TeraCopy |
| ProductVersion: | 3.2.6.0 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 16-Oct-2017 10:56:30 |
| Detected languages: |
|
| CompanyName: | Code Sector |
| FileDescription: | TeraCopy |
| FileVersion: | 3.2.6.0 |
| InternalName: | TeraCopy |
| LegalCopyright: | (C) 2007-2017 Code Sector |
| OriginalFilename: | TeraCopy.exe |
| ProductName: | TeraCopy |
| ProductVersion: | 3.2.6.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x9E71 |
| Pages in file: | 0x73C1 |
| Relocations: | 0x08D3 |
| Size of header: | 0xA3F2 |
| Min extra paragraphs: | 0x8DD3 |
| Max extra paragraphs: | 0x0195 |
| Initial SS value: | 0x152C |
| Initial SP value: | 0x9E1E |
| Checksum: | 0x5DE5 |
| Initial IP value: | 0x28DB |
| Initial CS value: | 0xDEC7 |
| Overlay number: | 0x673A |
| OEM identifier: | 0xC6FC |
| OEM information: | 0x3274 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 7 |
| Time date stamp: | 16-Oct-2017 10:56:30 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
0x00748000 | 0x00019000 | 0x00018FBD | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.99719 | |
.rsrc | 0x00538000 | 0x0020C2C4 | 0x00204435 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.62454 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.89226 | 1984 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 5.91015 | 4264 | UNKNOWN | Russian - Russia | RT_ICON |
3 | 5.89209 | 16936 | UNKNOWN | Russian - Russia | RT_ICON |
4 | 5.55477 | 270376 | UNKNOWN | Russian - Russia | RT_ICON |
5 | 5.50222 | 1081384 | UNKNOWN | Russian - Russia | RT_ICON |
6 | 4.01522 | 4264 | UNKNOWN | Russian - Russia | RT_ICON |
7 | 3.84432 | 1128 | UNKNOWN | Russian - Russia | RT_ICON |
8 | 3.73224 | 4264 | UNKNOWN | Russian - Russia | RT_ICON |
9 | 3.9728 | 1128 | UNKNOWN | Russian - Russia | RT_ICON |
10 | 3.03844 | 1128 | UNKNOWN | Russian - Russia | RT_ICON |
Imports
advapi32.dll |
comctl32.dll |
kernel32.dll |
user32.dll |
Exports
Title | Ordinal | Address |
|---|---|---|
dbkFCallWrapperAddr | 1 | 0x002E95A8 |
__dbk_fcall_wrapper | 2 | 0x00011658 |
madTraceProcess | 3 | 0x000A59F0 |
TMethodImplementationIntercept | 4 | 0x000D2CE0 |
Total processes
30
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3040 | "C:\Users\admin\AppData\Local\Temp\TeraCopy.exe" | C:\Users\admin\AppData\Local\Temp\TeraCopy.exe | explorer.exe | ||||||||||||
User: admin Company: Code Sector Integrity Level: MEDIUM Description: TeraCopy Exit code: 0 Version: 3.2.6.0 Modules
| |||||||||||||||
Total events
33
Read events
32
Write events
1
Delete events
0
Modification events
| (PID) Process: | (3040) TeraCopy.exe | Key: | HKEY_CURRENT_USER\Software\Obsidium\{3A180837-4BE9D673-B31A4BA0-7700D3BD} |
| Operation: | write | Name: | 1894784316145562426 |
Value: 9F2BC2416F88A54931A3B9CA8D4DF51C23DC900DB1EBB25F0CAA14A659E4362C4EC812770C12537AFA81B77561DC9BBC289B417E2F834A5840B55B20BB159AB5DB53450E4D0293C0D65F8BE81667CE4CB7B37788B18935A4BC2ACB37228848FFA9300FB2B8A57E11D0F683CB1D9E087AACF59B9B4FB0D7D998D7E31544ACC7286248A08FC7D9AACF9FD0FC53CC38A9C55B4D4B179D30A3AEFD1E9BC26D2BF409B63D786423CD17FF84F117652D395D09186E316DFCA23AFB666900850C2C2A77D816155A8B4ACAA695B6EF634450F4BC05510C3B0D2D835A3B6AAC5D2B11CAF5A080B9A81920937FE12FB76B0D7753B3124E44924074877BD411CFD12BDA65EA593EEC21626C568922EAC61E1E4D1155E67D1E0C8682720A32417CD1E125D874AB754AE9F47145EC1FD3606F874875CA3E12138C1674BC81ACC57A76226993515759163926341D73D373D7785630A4EC2DAF0E2368C7EEADE233AE5F8B0073D123114E3DDBC1C5BF7F486653246B774A124DDF8C0D78B5A4668134D6689C31E084FB5AE86C344C05CC5FAE77650FAF04DAB0E4E7B7683CA38332B483756D88654E6B8E88F47E57F77850242D8D19F2782C58D4A853A6577C53A45D7A973445878DA98085033F79B6187A615CED31D470D9838A8CF048E1BE530FDE80A39F3B853BA1A36F15305A09EC82025369CFF53DF5B638F1FDEF26CBAE92E4D47E11007BB25CEDD4E6813D167EE2FC8846179116DEF973B834D3B261AD2F3C9B09CEAE2BDC433FE42EB3EC599676997B957C90FD709F5D1F558F12D94056264C06AF37DED4D57AAA1EAEFF5DB5927D407A2436629B6F7AAE975529DF00E8C9233E74C077E6556508BD67B58599DCDB94770C063C961204315470FDB93082EA233C160A795663488125CAF1F6231DD0C3362DA7AEA4F661214F2F990D665E8BF9F4A48AC7FA5DD7F3B4CF88DFE0A652D0564A806C924415E0A0DEFCB86FDE5D65C35306BEA87FC7EB55BA1832D11DE3789B372F657D70FA681D21DA3204A8610595AFAF2FAD96DFBB6611138CED6AE3DC52BAD31C2F075A644E68F5F0CA908EE3BE157FE062A44E31C0DF260D094A1DAF56CE01A0E04077C1F70E6CF781C57A7402284A624333C4726EB2ECFC3D22E0319466ED2E7E0448E5E19BA560FCFFD66E626E8753501125127CD1B33043E35FBEE4145B11F1430C56EE78B34F1BE58D3D5E678A6A25E8D2A96ABDA9BA360F9FAA93BC567065E82B16CFA117C64A6934B307B383A90A332D6282B131FE9FAAB62CC403F24B265CE18D83CA59747E5110B8BF1CE61F660474B9E02751F61F80E8D15C545A87808B3F21703CD76294C1B30280965C1F51362DDA2912DC630D38815FB173C4A98530AC6CA2B611CFD6078EA14291F16B15270F82CC89EAE28F512C87297C855490D7A9334CECCAB9FEEBC296EDA5F10D3A85BC1E1385AEE2F14255781AC8F0A6AAC49EAE90D812D54CDB3EC8B76C2D64C526337BEE6AB3A9BCAC9C0792EB65BAC7727EC04F4A3DF68462A5F8A9FDA40D3982407CBA322BAF8F4455FEDBAE2A2B6E6CA52872DA7E51FF0C3BB8593549FC6C5A95361F0B0D8D67D085DF8A717B01F537D219C9BBF741A287975CB8BC666EC251685F87E524EDED037DB3C640542606EA0E459A7DC43AEC68D47C59CDDEC8DBFCAF28AA1A1159A0EDD3D8D69CF0970B9115C084F30B97CB2DBD66D167A6D43D16CCA62439E44F99971B01661D4725D8D530C226010F35699B78D40950F8EC | |||
Executable files
0
Suspicious files
2
Text files
0
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3040 | TeraCopy.exe | C:\Users\admin\AppData\Roaming\TeraCopy\main.db-journal | — | |
MD5:— | SHA256:— | |||
| 3040 | TeraCopy.exe | C:\Users\admin\AppData\Roaming\TeraCopy\History\190207-074625.db-journal | — | |
MD5:— | SHA256:— | |||
| 3040 | TeraCopy.exe | C:\Users\admin\AppData\Roaming\TeraCopy\History\190207-074716.db-journal | — | |
MD5:— | SHA256:— | |||
| 3040 | TeraCopy.exe | C:\Users\admin\AppData\Roaming\Obsidium\{3A180837-4BE9D673-B31A4BA0-7700D3BD}.1894784316145562426 | binary | |
MD5:— | SHA256:— | |||
| 3040 | TeraCopy.exe | C:\Users\admin\AppData\Roaming\TeraCopy\History\190207-074716.db | sqlite | |
MD5:— | SHA256:— | |||
| 3040 | TeraCopy.exe | C:\Users\admin\AppData\Roaming\TeraCopy\History\190207-074625.db | sqlite | |
MD5:— | SHA256:— | |||
| 3040 | TeraCopy.exe | C:\Users\admin\.obs32\{3A180837-4BE9D673-B31A4BA0-7700D3BD}.Metrics | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
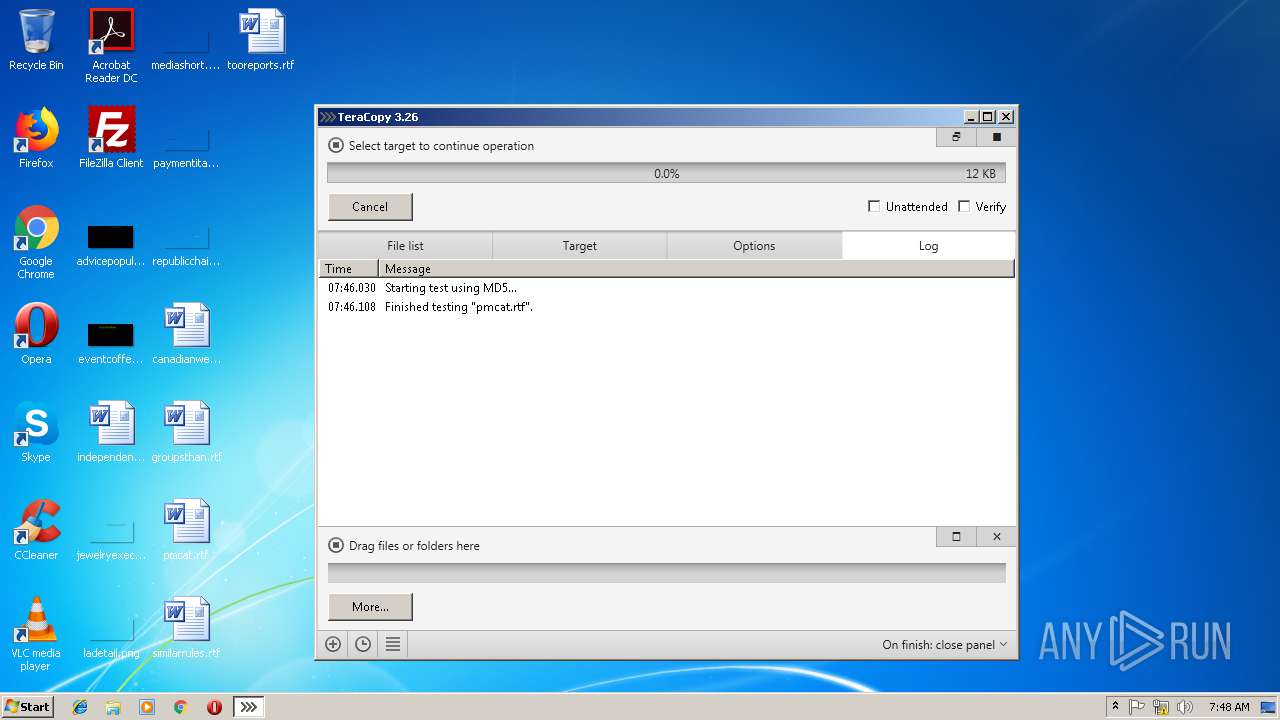
Process | Message |
|---|---|
TeraCopy.exe | 1695656 : Starting test using MD5... |
TeraCopy.exe | 1695734 : Finished testing "pmcat.rtf". |