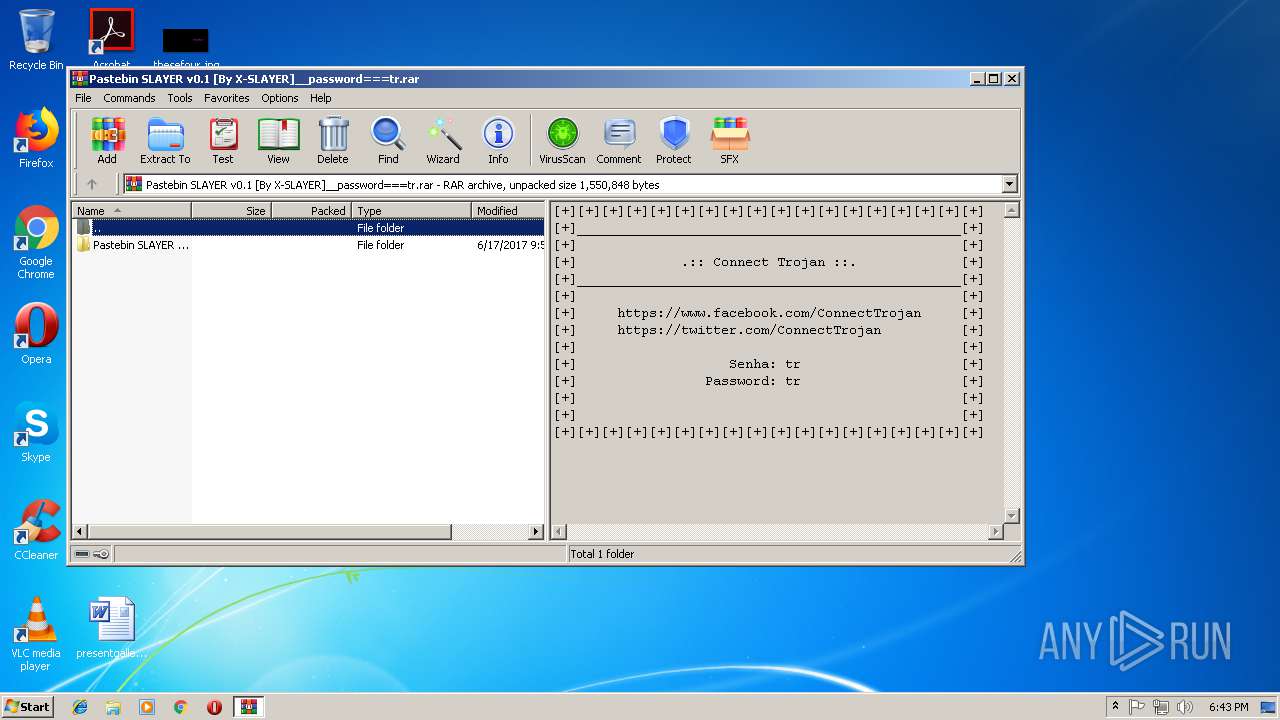
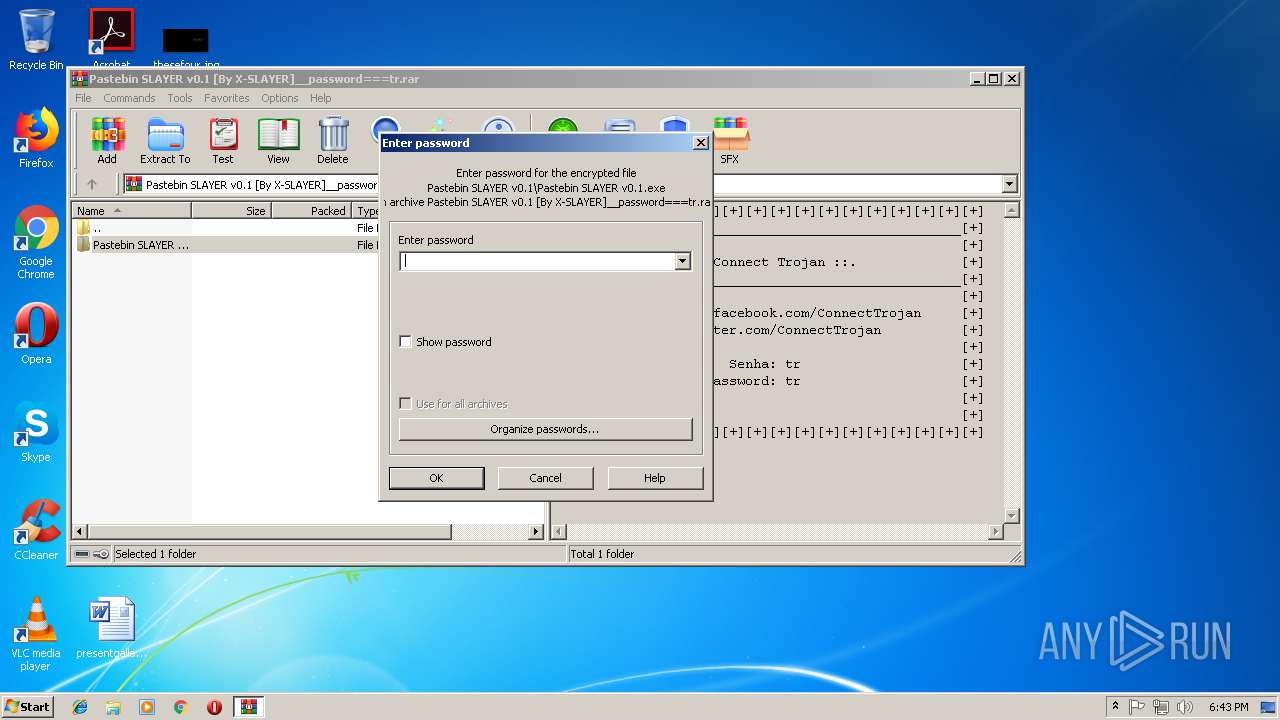
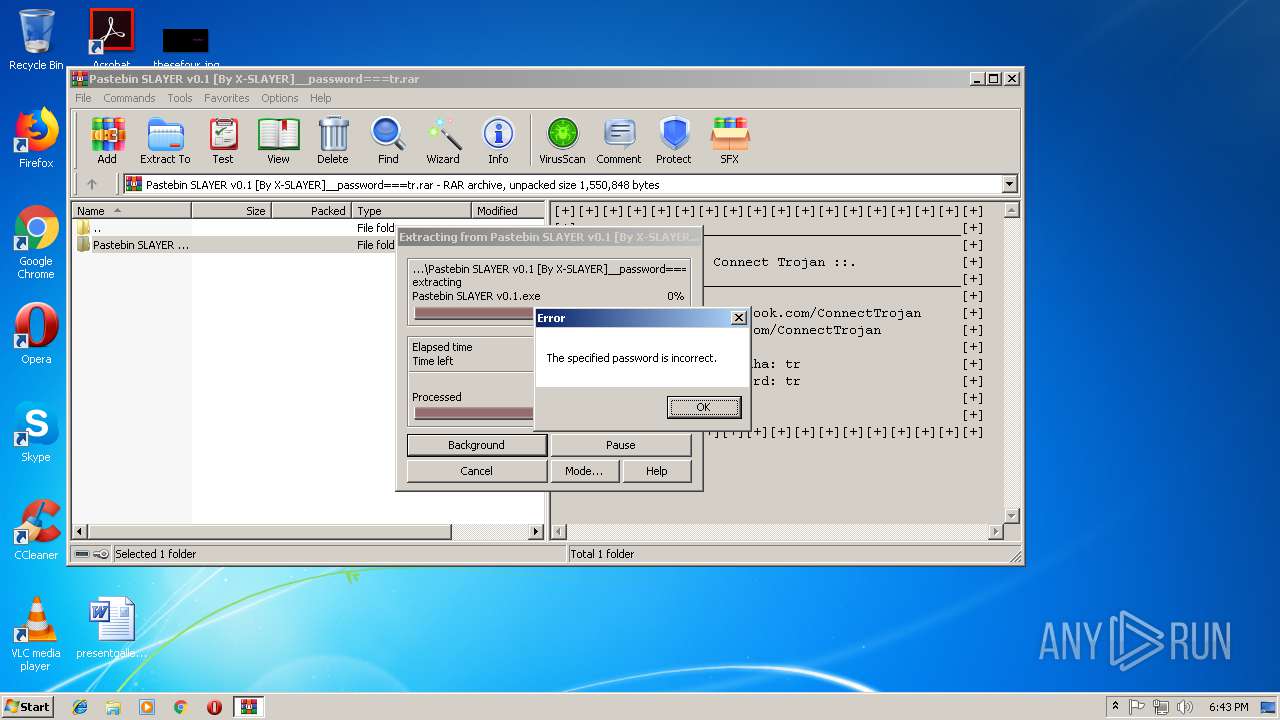
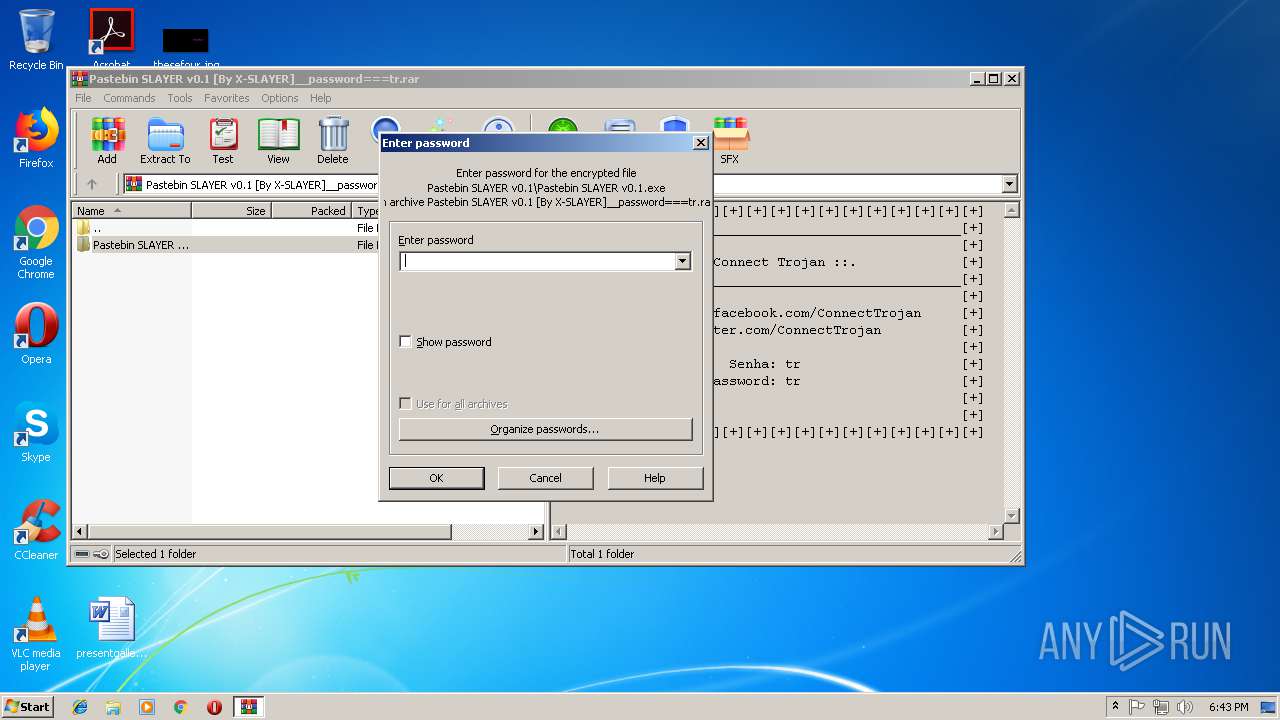
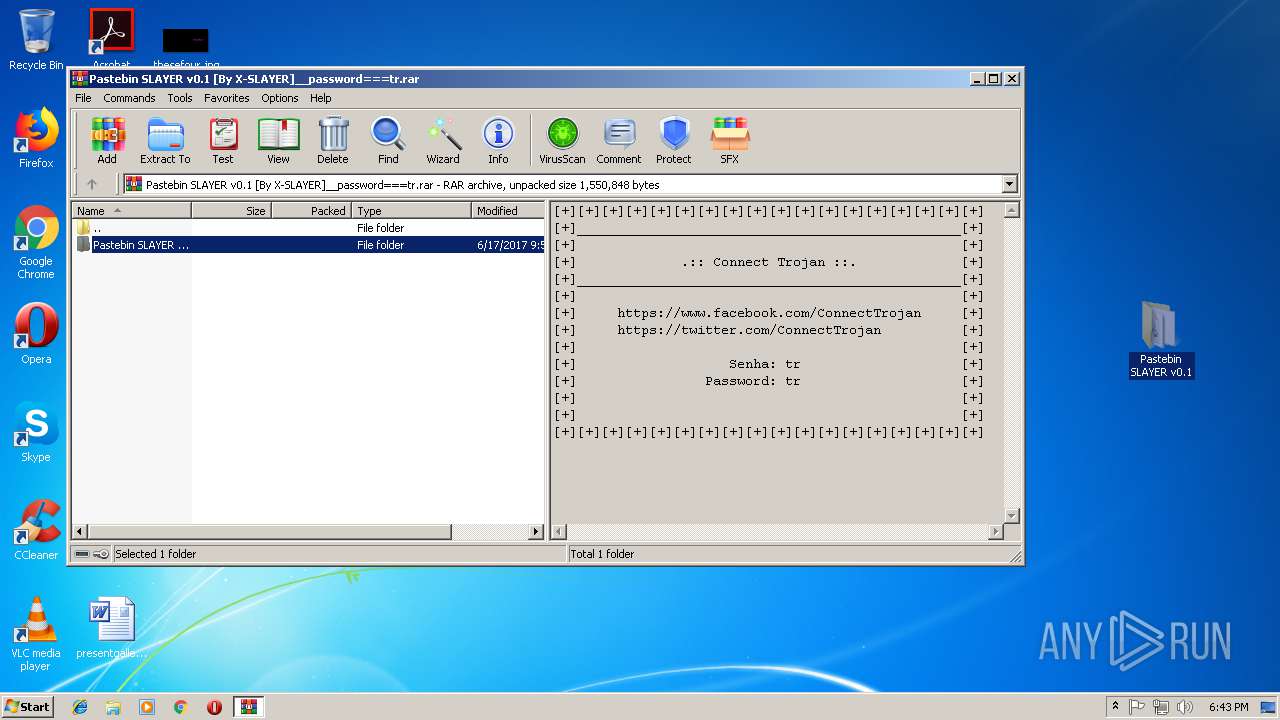
| File name: | Pastebin SLAYER v0.1 [By X-SLAYER]__password===tr.rar |
| Full analysis: | https://app.any.run/tasks/ce95af3d-0dc5-44ed-a0a9-8a62e84e2f1f |
| Verdict: | No threats detected |
| Analysis date: | November 14, 2018, 18:43:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 3550423FD1CF2277A6D820D84868E2C0 |
| SHA1: | 0B4861233BDE5B94FF4331F88236A32A822F422F |
| SHA256: | 19B5F3890282DC3A96A59144D32A09A7A47978239B440495F2F8CECEDE25851E |
| SSDEEP: | 12288:2zV6A4yJlnAMirZ5q8Pu4rn6m6ihyvrxBgJUUHSBlETnn3P0W1:MZ4yJlAlusu+6RihyY+UHOET3Mw |
MALICIOUS
Loads dropped or rewritten executable
- Pastebin SLAYER v0.1.exe (PID: 3556)
SUSPICIOUS
Reads Environment values
- Pastebin SLAYER v0.1.exe (PID: 3556)
Executable content was dropped or overwritten
- Pastebin SLAYER v0.1.exe (PID: 3556)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
33
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1364 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Pastebin SLAYER v0.1 [By X-SLAYER]__password===tr.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
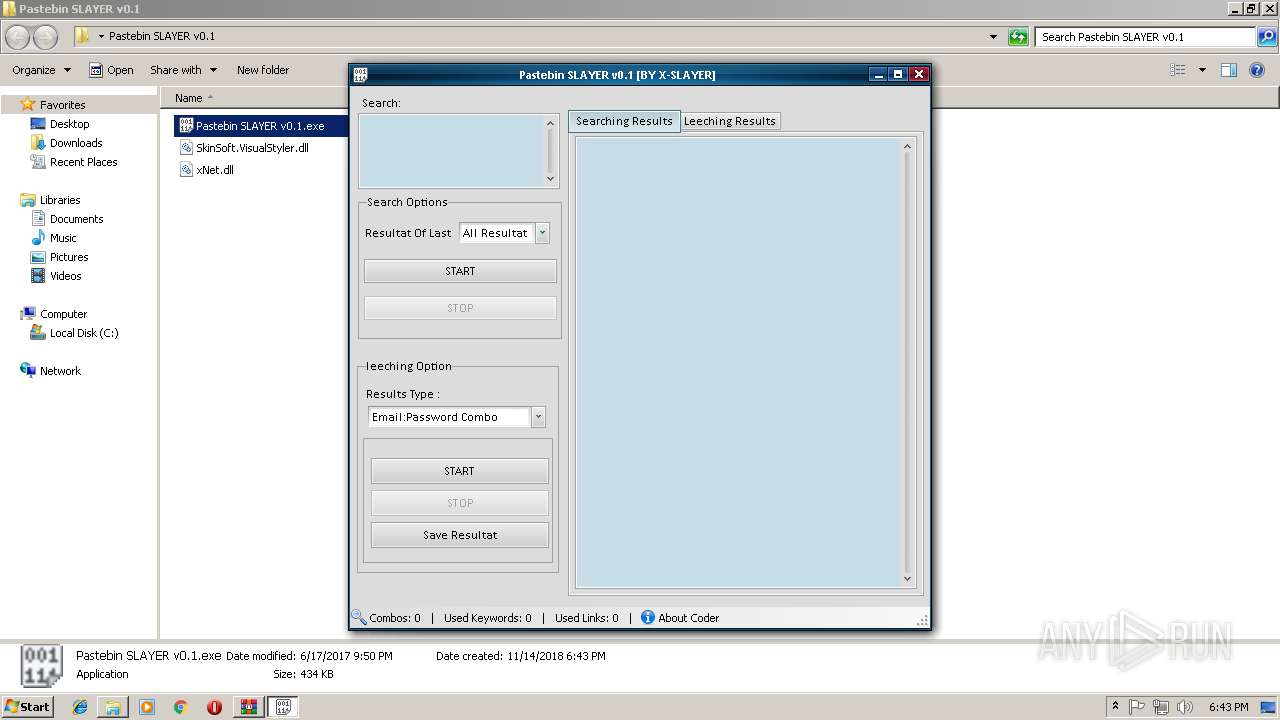
| 3556 | "C:\Users\admin\Desktop\Pastebin SLAYER v0.1\Pastebin SLAYER v0.1.exe" | C:\Users\admin\Desktop\Pastebin SLAYER v0.1\Pastebin SLAYER v0.1.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Pastebin SLAYER v0.1 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
461
Read events
441
Write events
20
Delete events
0
Modification events
| (PID) Process: | (1364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1364) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Pastebin SLAYER v0.1 [By X-SLAYER]__password===tr.rar | |||
| (PID) Process: | (1364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3556) Pastebin SLAYER v0.1.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
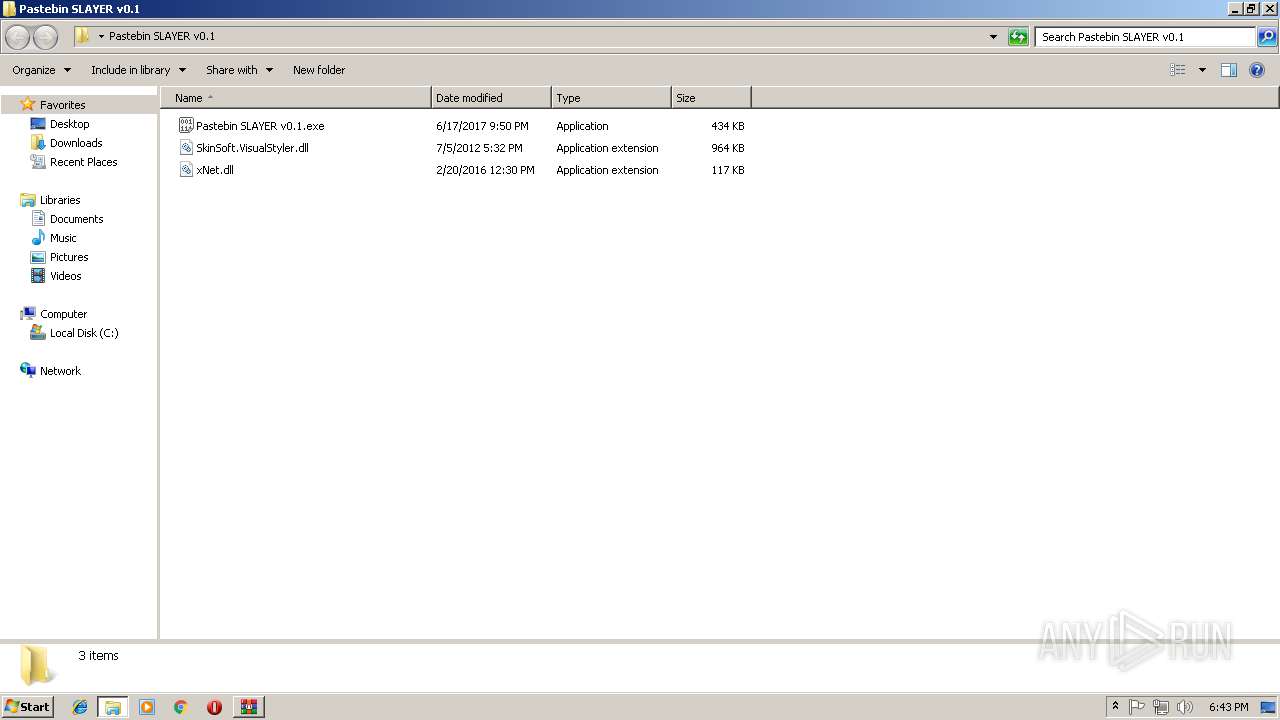
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1364.2155\Pastebin SLAYER v0.1\Pastebin SLAYER v0.1.exe | — | |
MD5:— | SHA256:— | |||
| 1364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1364.2155\Pastebin SLAYER v0.1\SkinSoft.VisualStyler.dll | — | |
MD5:— | SHA256:— | |||
| 1364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1364.2155\Pastebin SLAYER v0.1\xNet.dll | — | |
MD5:— | SHA256:— | |||
| 3556 | Pastebin SLAYER v0.1.exe | C:\Users\admin\AppData\Local\SkinSoft\VisualStyler\2.3.5.0\x86\ssapihook.dll | executable | |
MD5:D7F644C06B4CDE60651D02AED6B4174D | SHA256:A99EA2F5759B34859B484AFA3A58CE82A7F3BF792886A6C838DB852D517D9C0D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3556 | Pastebin SLAYER v0.1.exe | 172.217.168.3:443 | www.google.ru | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.ru |
| whitelisted |
www.google.tn |
| whitelisted |