| File name: | message_zdm.html |
| Full analysis: | https://app.any.run/tasks/be1632fe-1f16-4dcb-b96d-bd400e0ca304 |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2020, 03:40:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | F567CEB56E93F1574D50BAF0EC2B75DF |
| SHA1: | 8691502103334B1A9FB3F241A34F70B5357B7732 |
| SHA256: | 1995795C8207E22EFB585E7186D62890C4F4DB48B2E9212EFBB9D30328232E1B |
| SSDEEP: | 384:MPwXsoQszIQh/+L9eSITeCGyzdWJRYCY624FWH/zRClI3jMWcEaV2:M6J/NSITNWJ9Y624FM/zRClI3jMWcE02 |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 3072)
- iexplore.exe (PID: 2780)
Changes internet zones settings
- iexplore.exe (PID: 3072)
Application launched itself
- iexplore.exe (PID: 2888)
- iexplore.exe (PID: 3072)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2888)
- iexplore.exe (PID: 3072)
Changes settings of System certificates
- iexplore.exe (PID: 2888)
- iexplore.exe (PID: 3072)
Reads settings of System Certificates
- iexplore.exe (PID: 3072)
- iexplore.exe (PID: 2888)
Reads internet explorer settings
- iexplore.exe (PID: 2888)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .htm/html | | | HyperText Markup Language with DOCTYPE (80.6) |
|---|---|---|
| .html | | | HyperText Markup Language (19.3) |
EXIF
HTML
| ContentType: | text/html;charset=UTF-8 |
|---|---|
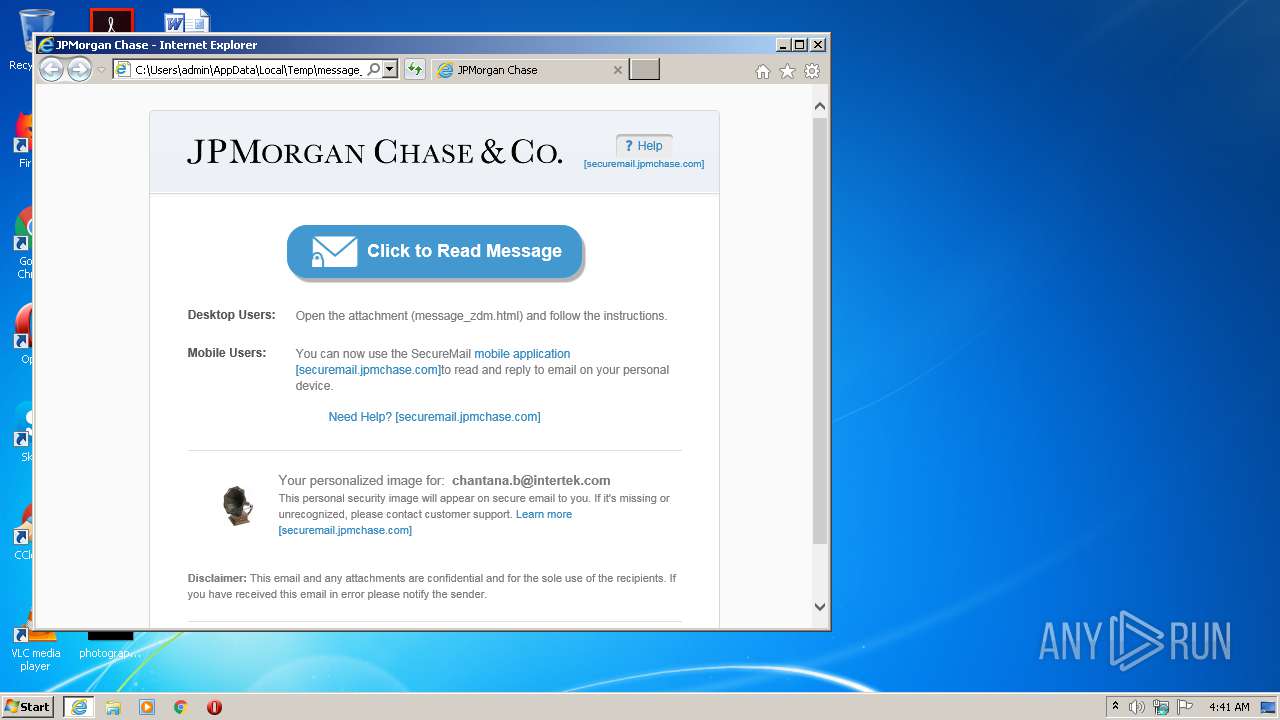
| Description: | SecureMail |
| Robots: | noindex, nofollow |
| viewport: | width=device-width, initial-scale=1.0, maximum-scale=1.0 |
| VoltageZFRVersion: | 3 |
| VoltageZFRType: | VoltageZFRMsg |
| Title: | JPMorgan Chase |
Total processes
37
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2780 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3072 CREDAT:333057 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2888 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3072 CREDAT:144385 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3072 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\message_zdm.html | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
2 255
Read events
2 164
Write events
88
Delete events
3
Modification events
| (PID) Process: | (3072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 3964329398 | |||
| (PID) Process: | (3072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30844562 | |||
| (PID) Process: | (3072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
45
Text files
9
Unknown types
21
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2888 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab6007.tmp | — | |
MD5:— | SHA256:— | |||
| 2888 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Tar6008.tmp | — | |
MD5:— | SHA256:— | |||
| 3072 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2888 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\verC904.tmp | — | |
MD5:— | SHA256:— | |||
| 3072 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\CabDD07.tmp | — | |
MD5:— | SHA256:— | |||
| 3072 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\TarDD08.tmp | — | |
MD5:— | SHA256:— | |||
| 2888 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A37B8BA80004D3266CB4D93B2052DC10_994B5C515D64A296EABD42B0A2E46349 | der | |
MD5:— | SHA256:— | |||
| 2888 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D8A5A4A0441F7653C3609E0E2DE6769F_A436E92D0CB7B112AA6C185BAF9AF147 | der | |
MD5:— | SHA256:— | |||
| 2888 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D8A5A4A0441F7653C3609E0E2DE6769F_A436E92D0CB7B112AA6C185BAF9AF147 | binary | |
MD5:— | SHA256:— | |||
| 2888 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_D9817BD5013875AD517DA73475345203 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
31
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2888 | iexplore.exe | GET | 200 | 104.108.66.215:80 | http://ocsp.entrust.net/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBTLXNCzDvBhHecWjg70iJhBW0InywQUanImetAe733nO2lR1GyNn5ASZqsCDGGh59IAAAAAUdNmpg%3D%3D | NL | der | 1.55 Kb | whitelisted |
2888 | iexplore.exe | GET | 200 | 104.108.66.215:80 | http://ocsp.entrust.net/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBTLXNCzDvBhHecWjg70iJhBW0InywQUanImetAe733nO2lR1GyNn5ASZqsCDGGh59IAAAAAUdNmpg%3D%3D | NL | der | 1.55 Kb | whitelisted |
2888 | iexplore.exe | GET | 200 | 104.108.66.215:80 | http://ocsp.entrust.net/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBTLXNCzDvBhHecWjg70iJhBW0InywQUanImetAe733nO2lR1GyNn5ASZqsCDGGh59IAAAAAUdNmpg%3D%3D | NL | der | 1.55 Kb | whitelisted |
2888 | iexplore.exe | GET | 200 | 104.108.66.215:80 | http://ocsp.entrust.net/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBTLXNCzDvBhHecWjg70iJhBW0InywQUanImetAe733nO2lR1GyNn5ASZqsCDGGh59IAAAAAUdNmpg%3D%3D | NL | der | 1.55 Kb | whitelisted |
2888 | iexplore.exe | GET | 200 | 104.108.66.215:80 | http://ocsp.entrust.net/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBTLXNCzDvBhHecWjg70iJhBW0InywQUanImetAe733nO2lR1GyNn5ASZqsCDGGh59IAAAAAUdNmpg%3D%3D | NL | der | 1.55 Kb | whitelisted |
2888 | iexplore.exe | GET | 200 | 104.108.66.215:80 | http://ocsp.entrust.net/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBTLXNCzDvBhHecWjg70iJhBW0InywQUanImetAe733nO2lR1GyNn5ASZqsCDGGh59IAAAAAUdNmpg%3D%3D | NL | der | 1.55 Kb | whitelisted |
2888 | iexplore.exe | GET | 200 | 104.108.66.215:80 | http://ocsp.entrust.net/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBTLXNCzDvBhHecWjg70iJhBW0InywQUanImetAe733nO2lR1GyNn5ASZqsCDGGh59IAAAAAUdNmpg%3D%3D | NL | der | 1.55 Kb | whitelisted |
2888 | iexplore.exe | GET | 200 | 104.108.66.215:80 | http://ocsp.entrust.net/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBTLXNCzDvBhHecWjg70iJhBW0InywQUanImetAe733nO2lR1GyNn5ASZqsCDGGh59IAAAAAUdNmpg%3D%3D | NL | der | 1.55 Kb | whitelisted |
2888 | iexplore.exe | GET | 200 | 104.108.66.215:80 | http://ocsp.entrust.net/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBTLXNCzDvBhHecWjg70iJhBW0InywQUanImetAe733nO2lR1GyNn5ASZqsCDGGh59IAAAAAUdNmpg%3D%3D | NL | der | 1.55 Kb | whitelisted |
2888 | iexplore.exe | GET | 200 | 104.108.66.215:80 | http://ocsp.entrust.net/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBTLXNCzDvBhHecWjg70iJhBW0InywQUanImetAe733nO2lR1GyNn5ASZqsCDGGh59IAAAAAUdNmpg%3D%3D | NL | der | 1.55 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2888 | iexplore.exe | 104.108.66.215:80 | ocsp.entrust.net | Akamai Technologies, Inc. | NL | unknown |
2888 | iexplore.exe | 159.53.113.132:443 | securemail.jpmchase.com | JPMorgan Chase & Co. | US | suspicious |
2888 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3072 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3072 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
— | — | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2888 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
securemail.jpmchase.com |
| whitelisted |
ocsp.entrust.net |
| whitelisted |
www.bing.com |
| whitelisted |
api.bing.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |