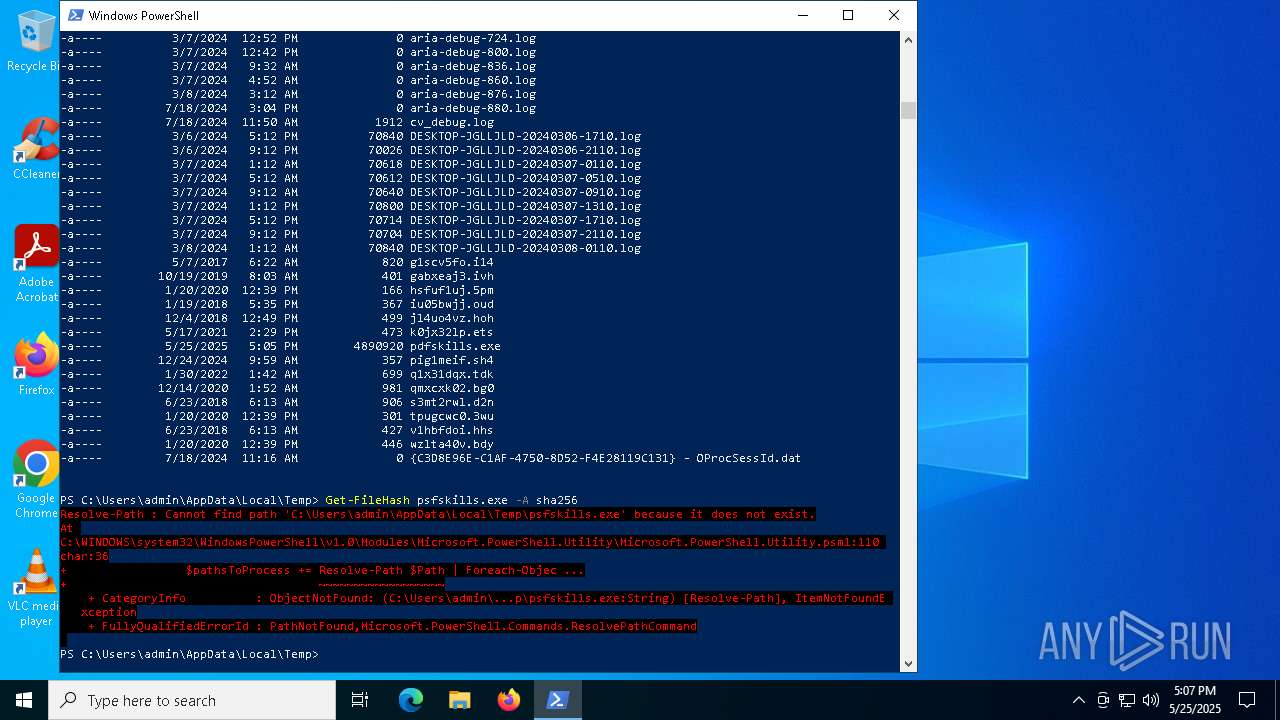
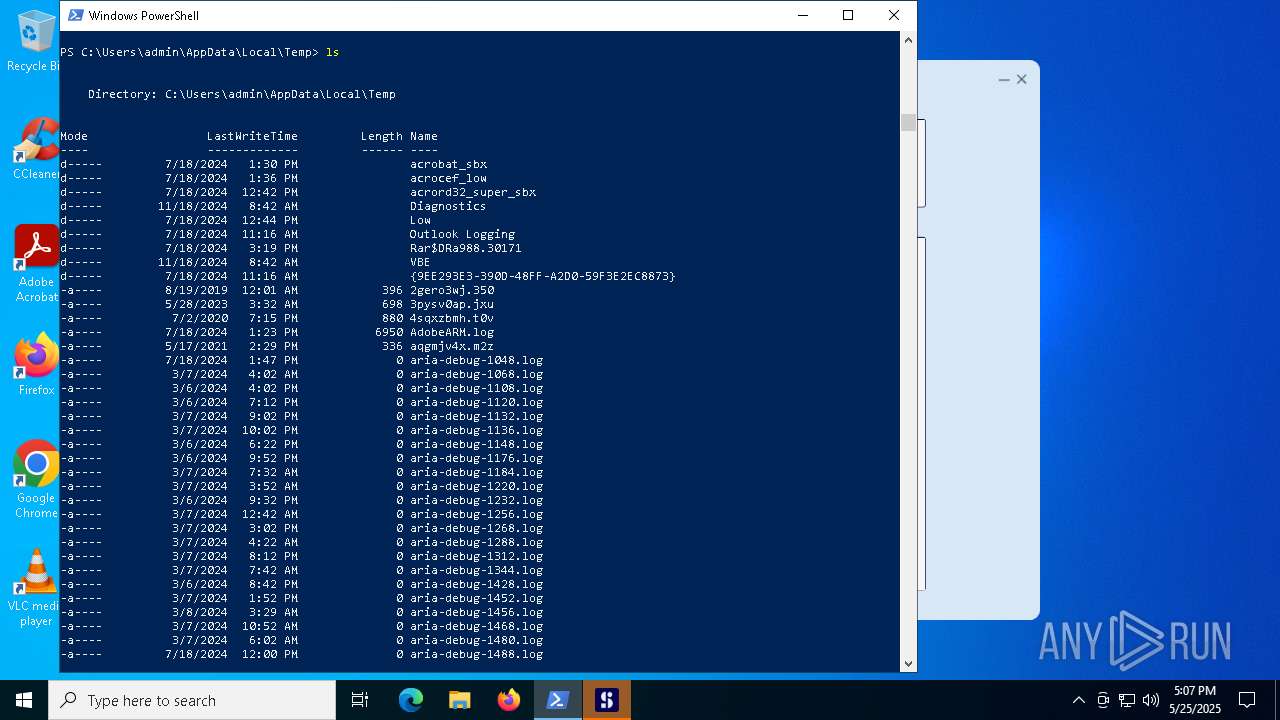
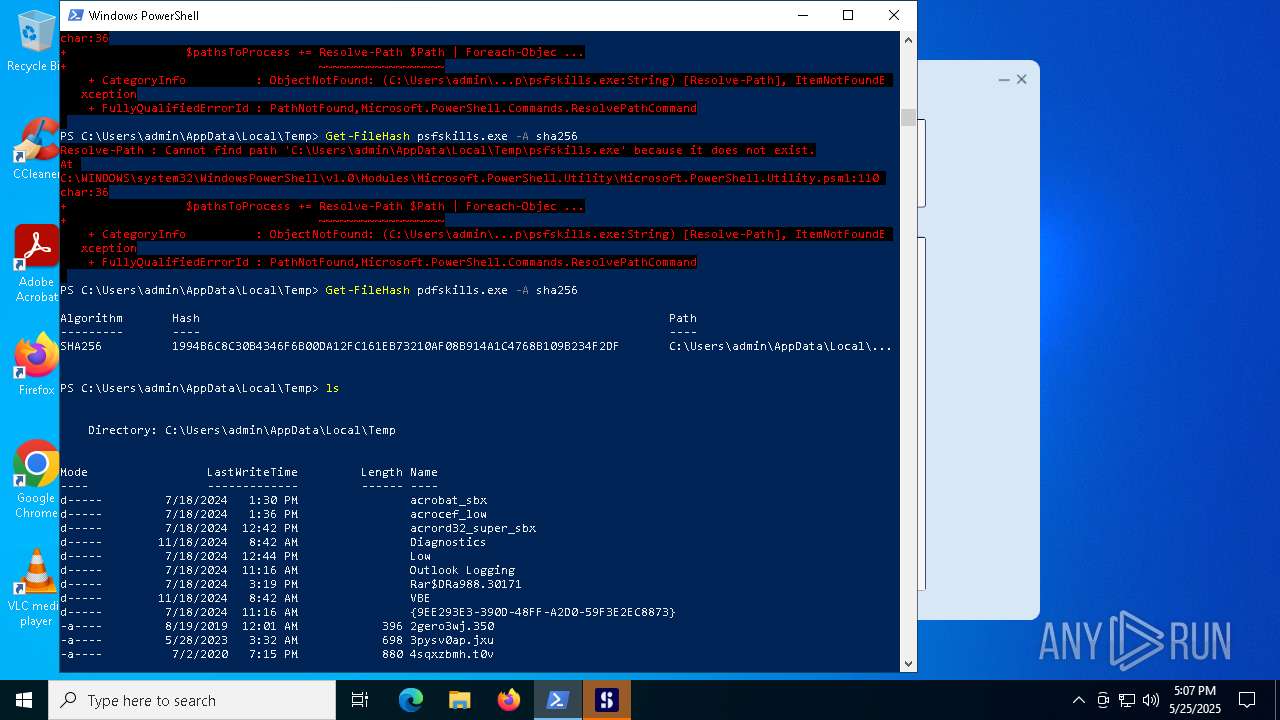
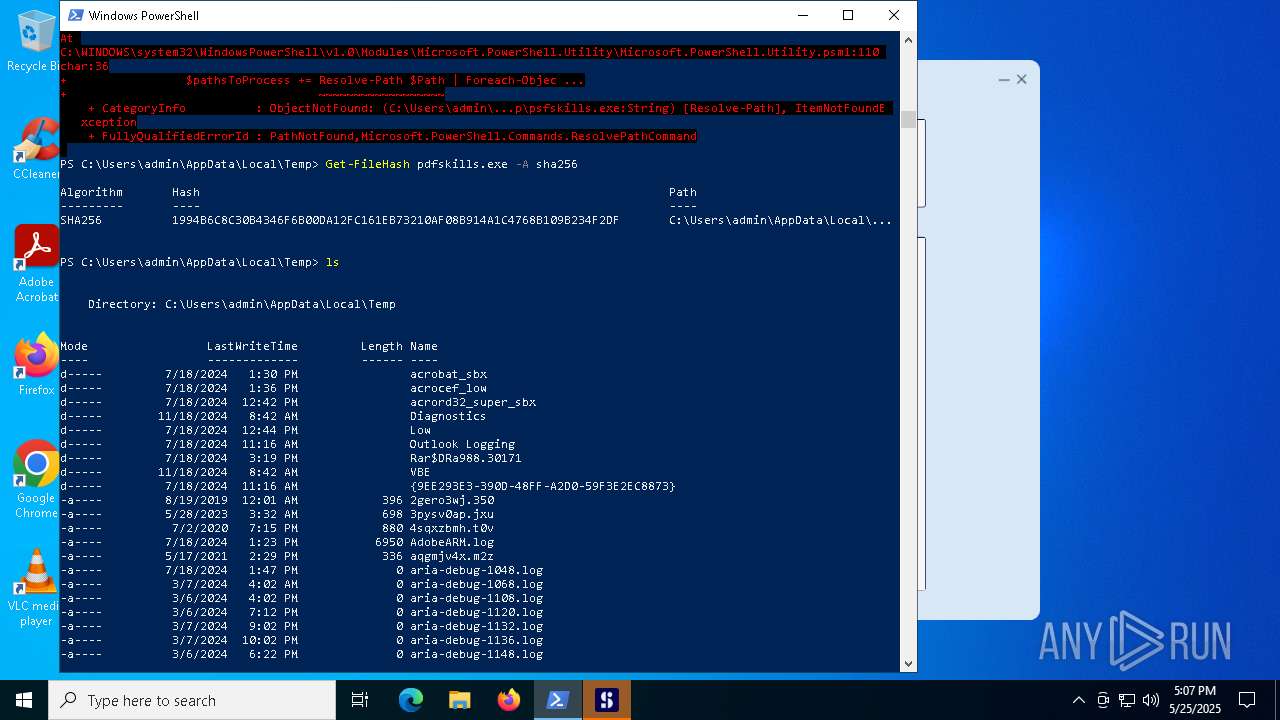
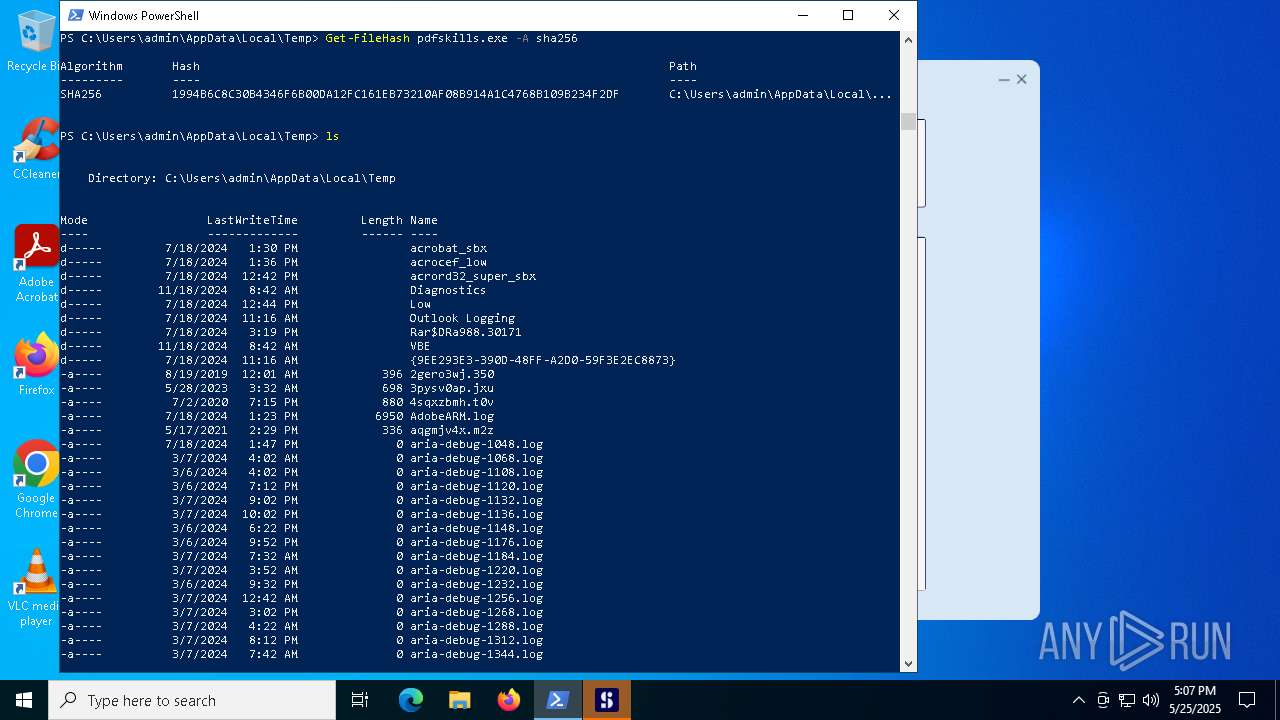
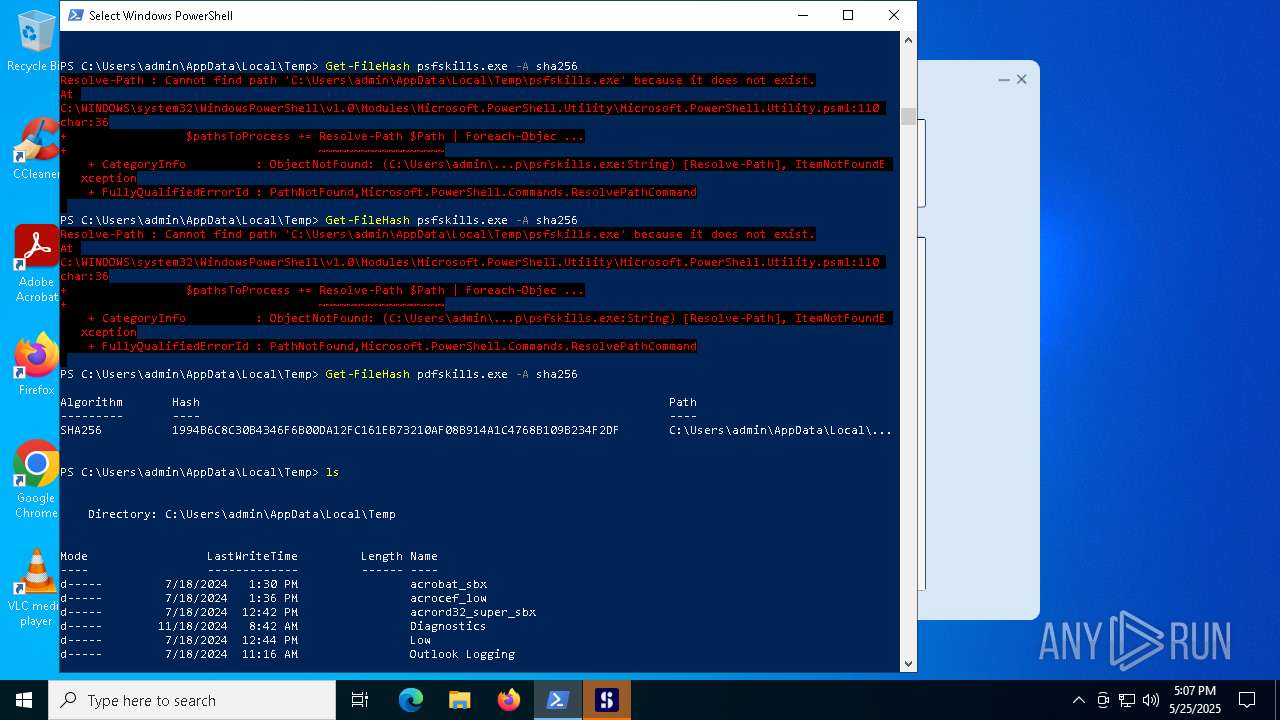
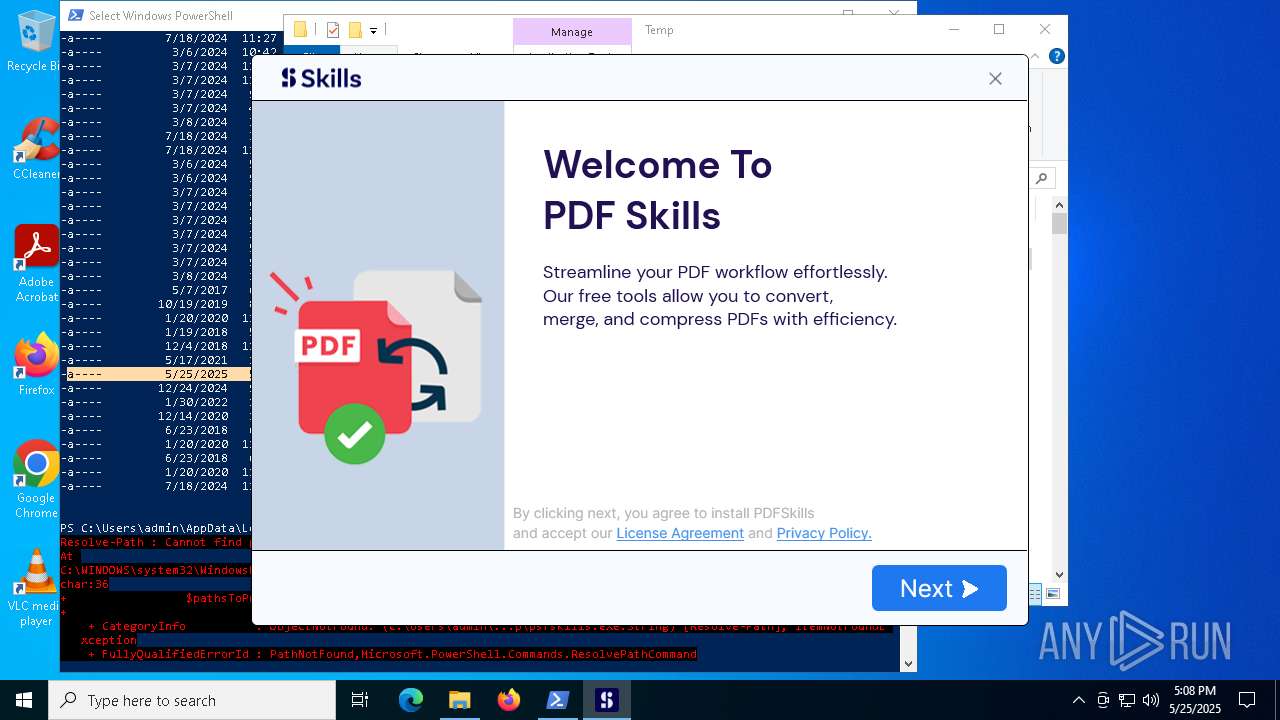
| File name: | pdfskills.exe |
| Full analysis: | https://app.any.run/tasks/b5bfc043-0559-4030-b173-7662a300e089 |
| Verdict: | Malicious activity |
| Analysis date: | May 25, 2025, 17:05:45 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64 Mono/.Net assembly, for MS Windows, 2 sections |
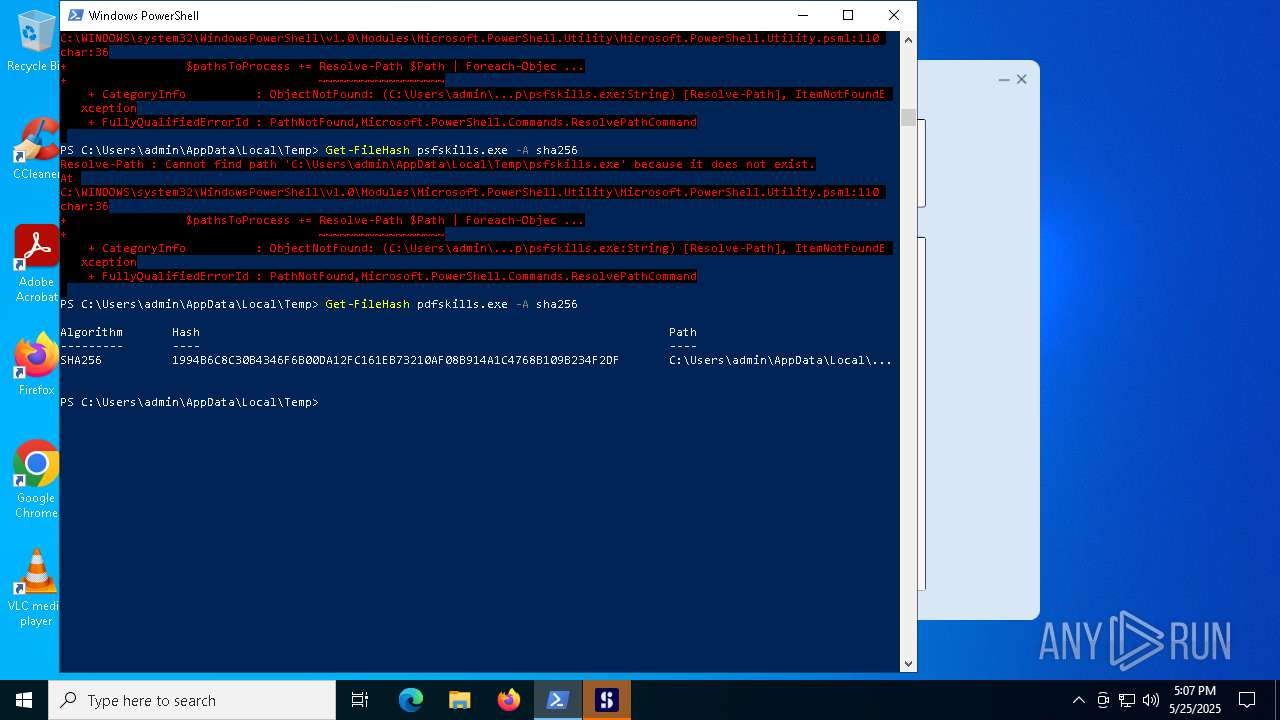
| MD5: | 6993F5E370CA16EF520108FC8E24ECF5 |
| SHA1: | 6C90CAE62C6E4B5C7FBED2AC13252410AF0132BC |
| SHA256: | 1994B6C8C30B4346F6B00DA12FC161EB73210AF08B914A1C4768B109B234F2DF |
| SSDEEP: | 98304:Rw4DuwYxT2ZyydrgUleLSzW8vdj2iXrVfY1c75uzdFhb4PyH1ZH30kMhvXHDnBXj:3KBRdnefCjO |
MALICIOUS
GENERIC has been found (auto)
- pdfskills.exe (PID: 7548)
SUSPICIOUS
Reads security settings of Internet Explorer
- pdfskills.exe (PID: 7548)
- PDFSkillsApp.exe (PID: 7224)
- pdfskills.exe (PID: 5064)
Executable content was dropped or overwritten
- pdfskills.exe (PID: 7548)
Reads the date of Windows installation
- pdfskills.exe (PID: 7548)
Creates a software uninstall entry
- pdfskills.exe (PID: 7548)
Searches for installed software
- pdfskills.exe (PID: 7548)
INFO
Creates files or folders in the user directory
- pdfskills.exe (PID: 7548)
Disables trace logs
- pdfskills.exe (PID: 7548)
- pdfskills.exe (PID: 5064)
Checks supported languages
- pdfskills.exe (PID: 7548)
- PDFSkillsApp.exe (PID: 7224)
- pdfskills.exe (PID: 5064)
Reads the computer name
- pdfskills.exe (PID: 7548)
- PDFSkillsApp.exe (PID: 7224)
- pdfskills.exe (PID: 5064)
Checks proxy server information
- pdfskills.exe (PID: 7548)
- pdfskills.exe (PID: 5064)
- slui.exe (PID: 5592)
Reads the software policy settings
- pdfskills.exe (PID: 7548)
- pdfskills.exe (PID: 5064)
- slui.exe (PID: 5592)
Reads Environment values
- pdfskills.exe (PID: 7548)
- pdfskills.exe (PID: 5064)
Reads the machine GUID from the registry
- pdfskills.exe (PID: 7548)
- PDFSkillsApp.exe (PID: 7224)
- pdfskills.exe (PID: 5064)
Manual execution by a user
- powershell.exe (PID: 7792)
- pdfskills.exe (PID: 5064)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 7792)
Gets or sets the time when the file was last written to (POWERSHELL)
- powershell.exe (PID: 7792)
Checks current location (POWERSHELL)
- powershell.exe (PID: 7792)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7792)
Process checks computer location settings
- pdfskills.exe (PID: 7548)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7792)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2074:07:23 17:41:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 48 |
| CodeSize: | 4860928 |
| InitializedDataSize: | 17408 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x0000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 247.8.44.101 |
| ProductVersionNumber: | 247.8.44.101 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | PDFSkills |
| FileVersion: | 247.8.44.101 |
| InternalName: | PDFSkills.exe |
| LegalCopyright: | Copyright © 2015-2023 BLACK INDIGO All rights reserved |
| LegalTrademarks: | - |
| OriginalFileName: | PDFSkills.exe |
| ProductName: | PDFSkills |
| ProductVersion: | 247.8.44.101 |
| AssemblyVersion: | 247.8.44.101 |
Total processes
142
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 4696 | "C:\Users\admin\AppData\Local\PDFSkills\PDFSkillsApp.exe" | C:\Users\admin\AppData\Local\PDFSkills\PDFSkillsApp.exe | — | pdfskills.exe |
User: admin Integrity Level: MEDIUM Description: NativeTemplate Version: 4.0.0.0 | ||||
| 5064 | "C:\Users\admin\AppData\Local\Temp\pdfskills.exe" | C:\Users\admin\AppData\Local\Temp\pdfskills.exe | explorer.exe | |
User: admin Integrity Level: MEDIUM Description: PDFSkills Exit code: 0 Version: 247.8.44.101 | ||||
| 5592 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 7224 | "C:\Users\admin\AppData\Local\PDFSkills\PDFSkillsApp.exe" | C:\Users\admin\AppData\Local\PDFSkills\PDFSkillsApp.exe | — | pdfskills.exe |
User: admin Integrity Level: MEDIUM Description: NativeTemplate Exit code: 0 Version: 4.0.0.0 | ||||
| 7548 | "C:\Users\admin\AppData\Local\Temp\pdfskills.exe" | C:\Users\admin\AppData\Local\Temp\pdfskills.exe | explorer.exe | |
User: admin Integrity Level: MEDIUM Description: PDFSkills Exit code: 0 Version: 247.8.44.101 | ||||
| 7792 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 7800 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 7884 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
2
Suspicious files
5
Text files
8
Unknown types
0
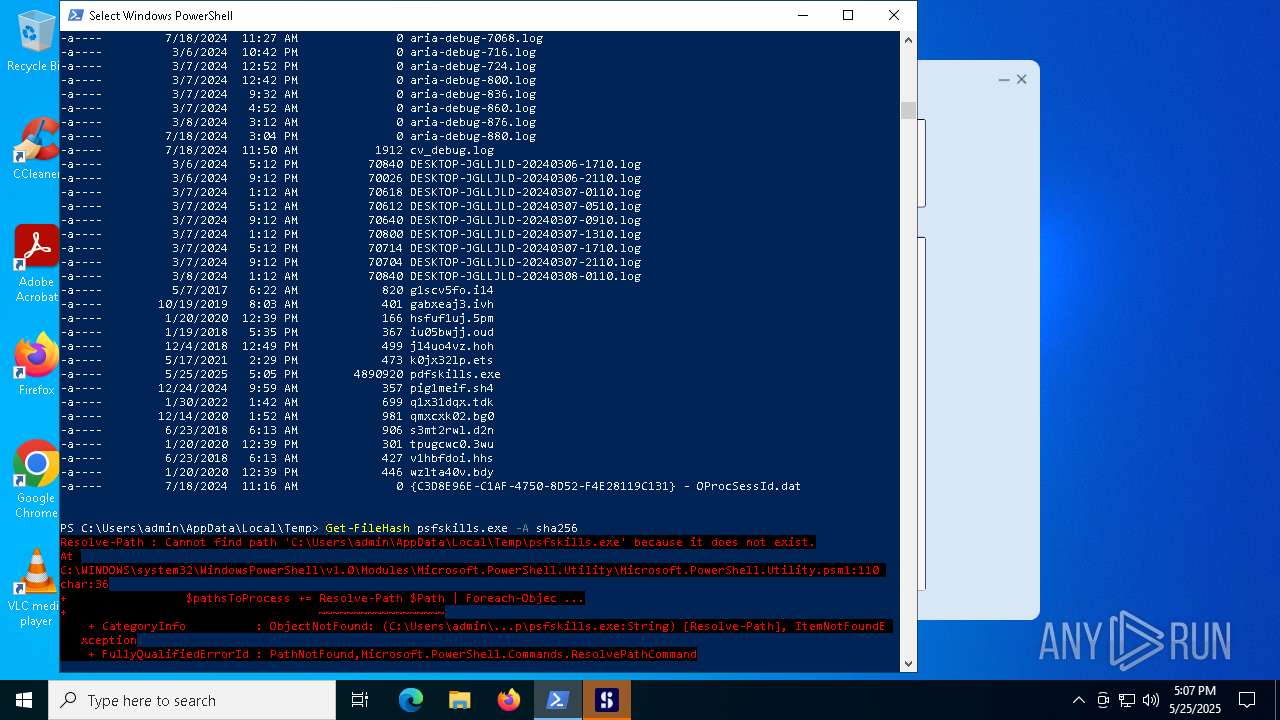
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7548 | pdfskills.exe | C:\Users\admin\AppData\Roaming\SMCR\userId.txt | text | |
MD5:0001647F38CDF7A0D13313E5619C13B0 | SHA256:C64D1BFC322E2FC3E6A41BD661A34227592DF5C0E5EC8E2A393AD28F04CFB616 | |||
| 7792 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_t0lblmpw.hgj.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7792 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_v0q3orwm.wiw.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7792 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:3F95A05381C6D14195F6A1538F5FBADE | SHA256:0E753E9AD3EDE811C17D076B462F85321B8F559C2E462AF0990A1653573A525F | |||
| 7548 | pdfskills.exe | C:\Users\admin\AppData\Local\PDFSkills\Uninstall.exe | executable | |
MD5:2368A9422D855316695A77C1140AEA2C | SHA256:E6696F2BE034E1D113FABEC1C3843704EE7CC88CE0624BBA3E942E32DD7E99C5 | |||
| 7792 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:45AE9969D8B7153A6B63873330ACE679 | SHA256:83501B37DB562B05F2C6E2EA5566956559D437351227FEBC75A415E17B7DFCF9 | |||
| 7548 | pdfskills.exe | C:\Users\admin\AppData\Local\PDFSkills\skillsUserId.txt | text | |
MD5:0001647F38CDF7A0D13313E5619C13B0 | SHA256:C64D1BFC322E2FC3E6A41BD661A34227592DF5C0E5EC8E2A393AD28F04CFB616 | |||
| 7792 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ffbeu0lb.snc.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7548 | pdfskills.exe | C:\Users\admin\AppData\Local\PDFSkills\PDFSkills.Belongings.favicon.ico | image | |
MD5:FC5F48AAF4694FABB338180E78FCFDCB | SHA256:575233647D440DF001566E8092FD408E1F3C840BC3991A1866408AFDA3DC6F99 | |||
| 7792 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF10cf96.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
32
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8064 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7424 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
8064 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5796 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3272 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
7548 | pdfskills.exe | 198.71.59.132:443 | val.skillcli.com | IONOS SE | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 40.126.31.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
val.skillcli.com |
| unknown |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |