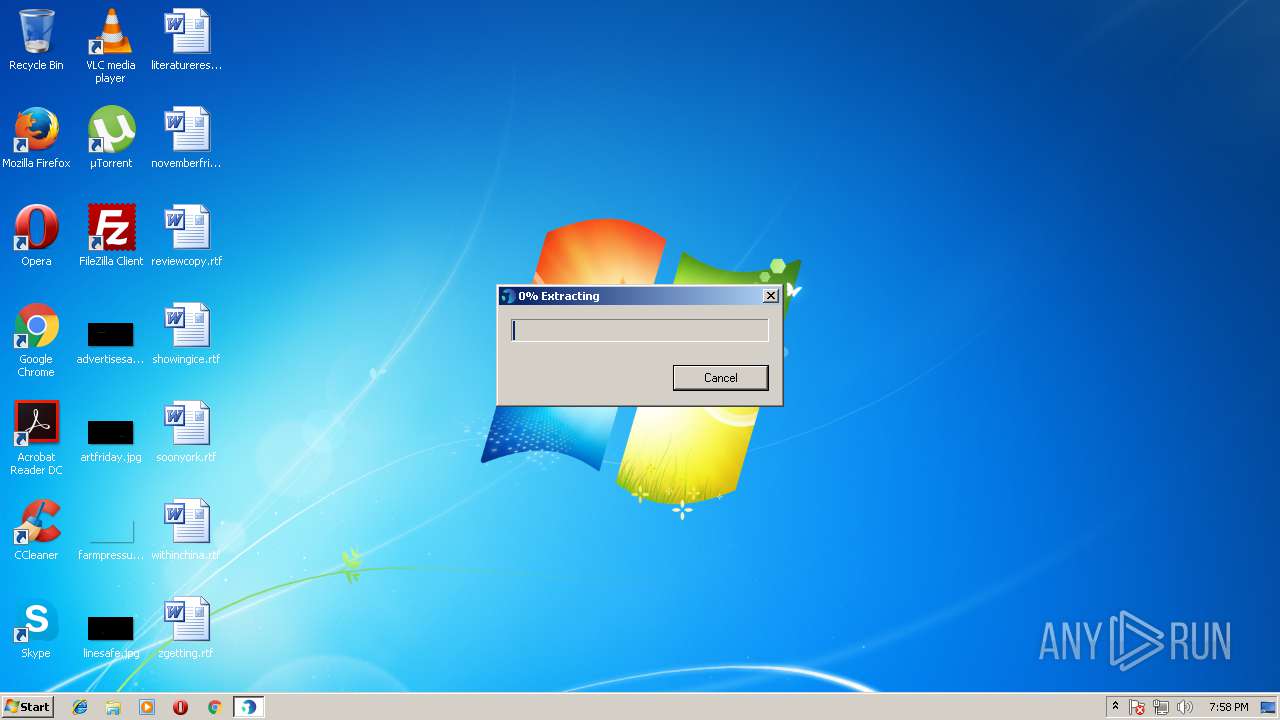
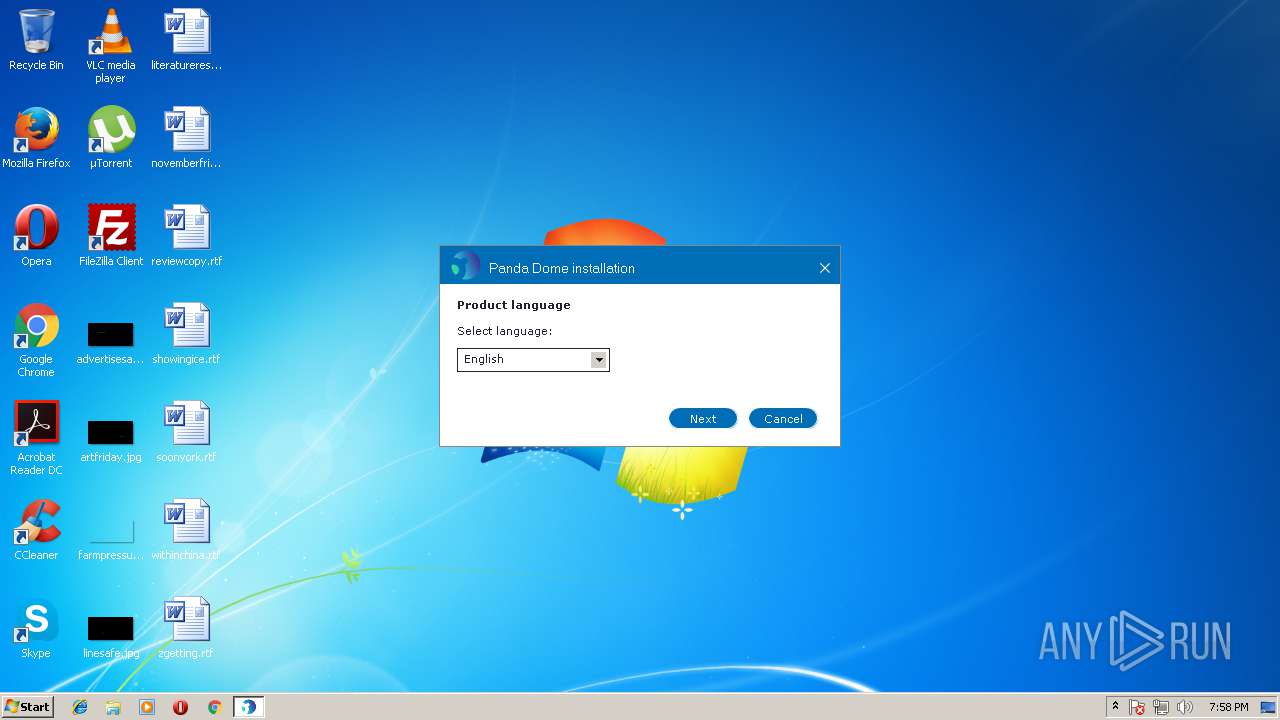
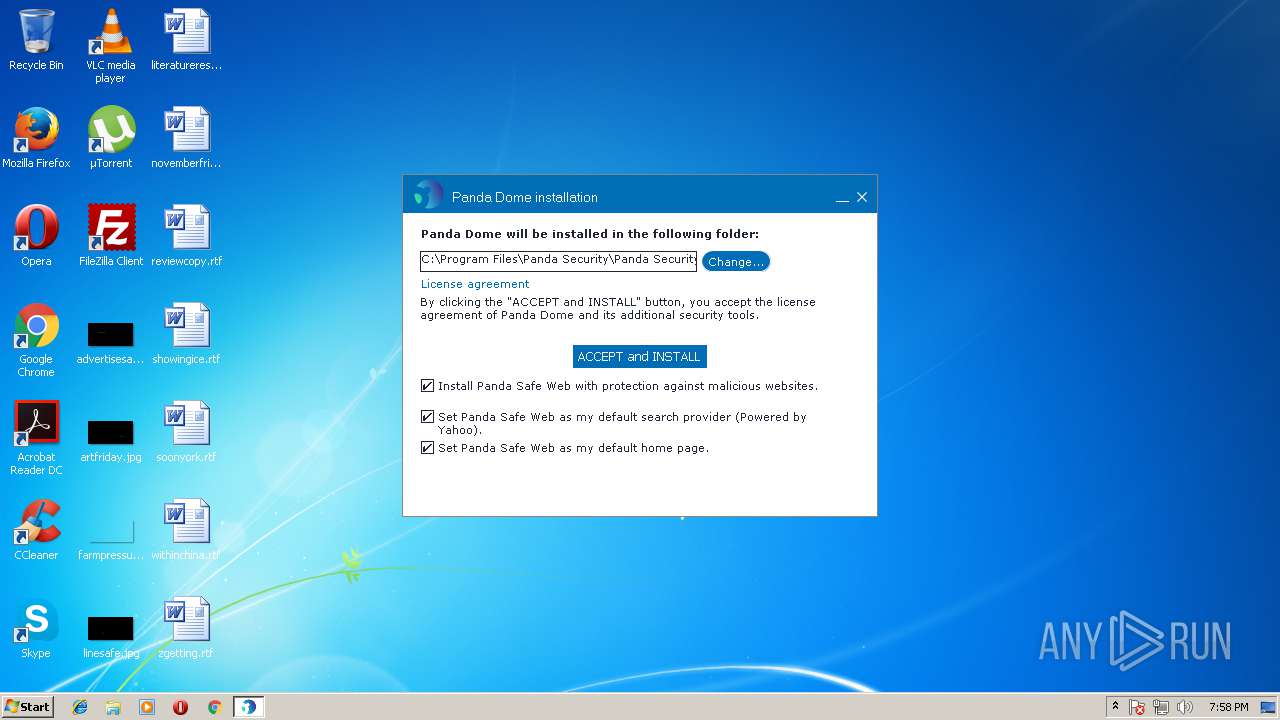
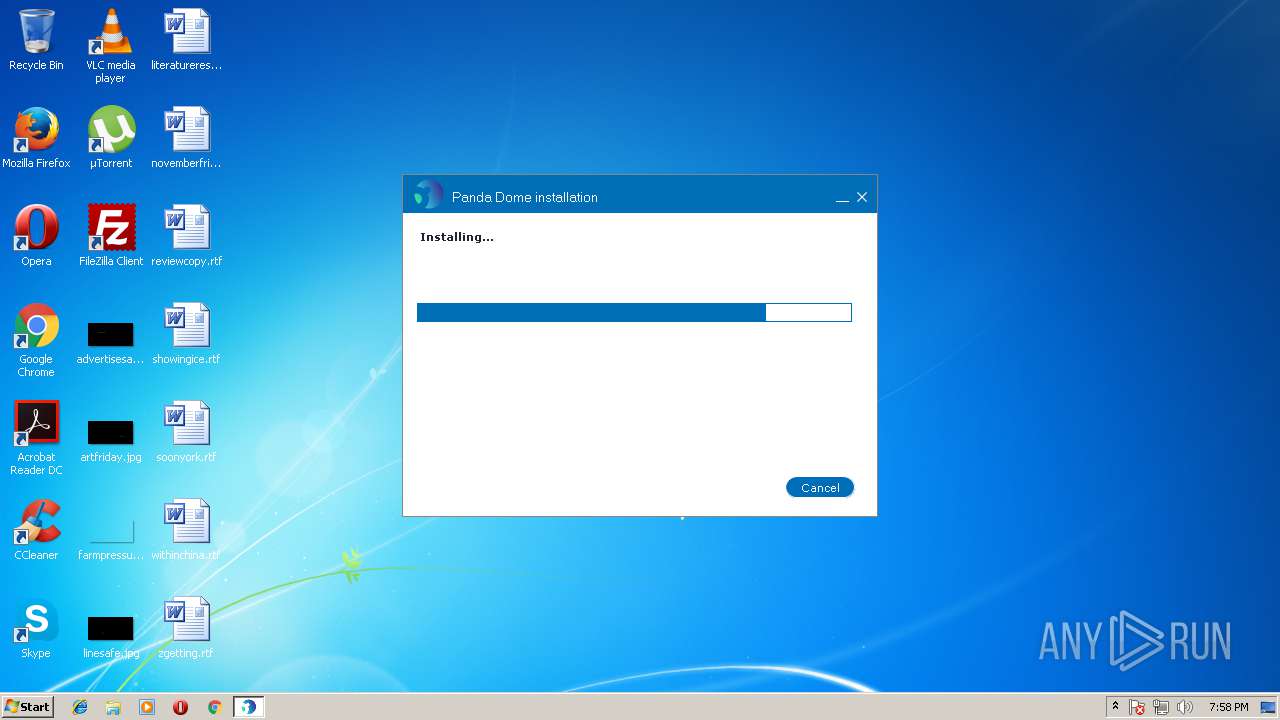
| URL: | http://acs.pandasoftware.com/Panda/FREEAV/181305/FREEAV.exe |
| Full analysis: | https://app.any.run/tasks/92e09630-5373-4c24-8186-ccb10d446c9f |
| Verdict: | Malicious activity |
| Analysis date: | May 30, 2018, 18:57:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | A3283C59F7C3252993FE87A121EA38EE |
| SHA1: | 89DBB2D226C767FD5B832981B3DD2298DA9A05B8 |
| SHA256: | 198D2115F0DCEAB399F540BE638574BB8CDFA693E70B4156C49D17EAD3DB0D70 |
| SSDEEP: | 3:N1Kf05FJLghxUknACn:Cs9U3UknAC |
MALICIOUS
Changes settings of System certificates
- setup.exe (PID: 1620)
Loads dropped or rewritten executable
- setup.exe (PID: 1620)
- PSANCU.exe (PID: 2684)
- csrss.exe (PID: 400)
- PSANCU.exe (PID: 3976)
- Hydra.Sdk.Windows.Service.exe (PID: 3984)
Application was dropped or rewritten from another process
- PSINAN~1.EXE (PID: 900)
- tracelog.exe (PID: 2952)
- PSANCU.exe (PID: 2684)
- PSANCU.exe (PID: 3976)
- Hydra.Sdk.Windows.Service.exe (PID: 3984)
SUSPICIOUS
Creates files in the program directory
- tracelog.exe (PID: 2952)
- setup.exe (PID: 1620)
- PSINAN~1.EXE (PID: 900)
- FREEAV[1].exe (PID: 3056)
- PSANCU.exe (PID: 3976)
- Hydra.Sdk.Windows.Service.exe (PID: 3984)
Adds / modifies Windows certificates
- setup.exe (PID: 1620)
Creates files in the user directory
- PSANCU.exe (PID: 2684)
Reads Internet Cache Settings
- setup.exe (PID: 1620)
Executable content was dropped or overwritten
- MsiExec.exe (PID: 2828)
- msiexec.exe (PID: 3932)
- FREEAV[1].exe (PID: 3056)
Creates files in the driver directory
- msiexec.exe (PID: 3932)
Modifies the open verb of a shell class
- msiexec.exe (PID: 3932)
Changes the autorun value in the registry
- msiexec.exe (PID: 3932)
Creates COM task schedule object
- MsiExec.exe (PID: 2684)
Changes IE settings (feature browser emulation)
- MsiExec.exe (PID: 2684)
Creates files in the Windows directory
- msiexec.exe (PID: 3932)
Creates or modifies windows services
- Hydra.Sdk.Windows.Service.exe (PID: 3984)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 2912)
Dropped object may contain URL's
- iexplore.exe (PID: 2912)
- iexplore.exe (PID: 2884)
- MsiExec.exe (PID: 2828)
- msiexec.exe (PID: 3932)
- FREEAV[1].exe (PID: 3056)
Changes internet zones settings
- iexplore.exe (PID: 2884)
Dropped object may contain Bitcoin addresses
- FREEAV[1].exe (PID: 3056)
- msiexec.exe (PID: 3932)
Application launched itself
- msiexec.exe (PID: 3932)
Creates files in the program directory
- MsiExec.exe (PID: 2828)
- msiexec.exe (PID: 3932)
- MsiExec.exe (PID: 2684)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 2684)
- MsiExec.exe (PID: 2828)
Creates a software uninstall entry
- msiexec.exe (PID: 3932)
Creates or modifies windows services
- msiexec.exe (PID: 3932)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
48
Monitored processes
14
Malicious processes
8
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 400 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,12288,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\System32\csrss.exe | — | — | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 900 | "C:\Users\admin\AppData\Local\Temp\{A7289~1\PSINAN~1.EXE" /LogFile:"C:\ProgramData\Panda Security\PSLogs\PSINanoRun.exe_7242.Log"| /GetSO:"C:\Users\admin\AppData\Local\Temp\{A72890C6-04C4-4B0B-BC93-2F6C70B3F157}\SO.ini"| | C:\Users\admin\AppData\Local\Temp\{A7289~1\PSINAN~1.EXE | — | MsiExec.exe | |||||||||||
User: admin Company: Panda Security, S.L. Integrity Level: HIGH Description: Panda Setup Bootstrap Run Utilities Exit code: 0 Version: 7.7.5.0 Modules
| |||||||||||||||
| 1568 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LM4BD81N\FREEAV[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LM4BD81N\FREEAV[1].exe | — | iexplore.exe | |||||||||||
User: admin Company: Panda Security, S.L. Integrity Level: MEDIUM Description: Panda Security SFX Exit code: 3221226540 Version: 15.14.4.0 Modules
| |||||||||||||||
| 1620 | ".\setup.exe" | C:\Users\admin\AppData\Local\Temp\7zS0FBF3E14\setup.exe | FREEAV[1].exe | ||||||||||||
User: admin Company: Panda Security, S.L. Integrity Level: HIGH Description: Setup Application Exit code: 0 Version: 7.7.20.0 Modules
| |||||||||||||||
| 2684 | "C:\Users\admin\AppData\Local\Temp\7zS0FBF3E14\Program Files\Panda Security\Panda Cloud Antivirus\PSANCU.exe" /applycustom /wd:"C:\Users\admin\AppData\Local\Temp\7zS0FBF3E14\" | C:\Users\admin\AppData\Local\Temp\7zS0FBF3E14\Program Files\Panda Security\Panda Cloud Antivirus\PSANCU.exe | — | setup.exe | |||||||||||
User: admin Company: Panda Security, S.L. Integrity Level: HIGH Description: Panda Security Application CU Exit code: 0 Version: 4.0.3.2 Modules
| |||||||||||||||
| 2684 | C:\Windows\system32\MsiExec.exe -Embedding CF86D789DFF3461C624DB2334627F581 M Global\MSI0000 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2828 | C:\Windows\system32\MsiExec.exe -Embedding DD226E9624A1BB47B25151F49985B198 | C:\Windows\system32\MsiExec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2884 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2912 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2884 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2952 | "C:\Users\admin\AppData\Local\Temp\7zS0FBF3E14\Temp\tracelog.exe" -start "InstAppLog_4600.etl" -rt -guid "C:\Users\admin\AppData\Local\Temp\7zS0FBF3E14\Temp\GUIDs.txt" -f "C:\ProgramData\Panda Security\PSLogs\InstAppLog_4600.etl" -level 5 -flags 255 -UseCPUCycle -gs -seq 5 | C:\Users\admin\AppData\Local\Temp\7zS0FBF3E14\Temp\tracelog.exe | — | setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
2 070
Read events
915
Write events
1 151
Delete events
4
Modification events
| (PID) Process: | (2884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000006B000000010000000000000000000000000000000000000000000000400C35B347C7D301000000000000000000000000020000001700000000000000FE80000000000000D45917EAB3ED3D860B000000000000001700000000000000FE80000000000000D45917EAB3ED3D860B000000000000001C00000000000000000000000000000000000000000000000000000000000000170000000000000000000000000000000000FFFFC0A8640B000000000000000002000000C0A801640000000000000000000000000000000000000000000000000C00000C37D0000010A73800D8703600000000000000000000000000000000000000000000000000000000000000000000000000000000000000000081F800009000230090002300380023000000000000702C000A00000000000000F8412C00 | |||
| (PID) Process: | (2884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {5B502FF3-643B-11E8-B27F-5254004AAD21} |
Value: 0 | |||
| (PID) Process: | (2884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 5 | |||
| (PID) Process: | (2884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E207050003001E00120039003600D201 | |||
Executable files
477
Suspicious files
229
Text files
122
Unknown types
131
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2884 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2LKO8ICX\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2884 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2884 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF73C1BC27A4151E85.TMP | — | |
MD5:— | SHA256:— | |||
| 2912 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\WF2FXMJU\FREEAV[1].exe | — | |
MD5:— | SHA256:— | |||
| 2884 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LM4BD81N\FREEAV[1].exe | — | |
MD5:— | SHA256:— | |||
| 3056 | FREEAV[1].exe | C:\Users\admin\AppData\Local\Temp\7zS0FBF3E14\CommonAppData\COMMONALLUSERNANO\CfgData\02012000.dat | binary | |
MD5:— | SHA256:— | |||
| 2912 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\MSHist012018053020180531\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2912 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2884 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{5B502FF4-643B-11E8-B27F-5254004AAD21}.dat | binary | |
MD5:— | SHA256:— | |||
| 3056 | FREEAV[1].exe | C:\Users\admin\AppData\Local\Temp\7zS0FBF3E14\CommonAppData\COMMONALLUSERNANO\CfgData\02005000.dat | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
2
Threats
985
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2912 | iexplore.exe | GET | — | 2.16.186.73:80 | http://acs.pandasoftware.com/Panda/FREEAV/181305/FREEAV.exe | unknown | — | — | whitelisted |
2884 | iexplore.exe | GET | 200 | 13.107.21.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2884 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2912 | iexplore.exe | 2.16.186.73:80 | acs.pandasoftware.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
acs.pandasoftware.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | A Network Trojan was detected | ET CNC Feodo Tracker Reported CnC Server group 9 |
— | — | A Network Trojan was detected | ET CNC Feodo Tracker Reported CnC Server group 1 |
— | — | A Network Trojan was detected | [PT MALWARE] Feodo HTTP header Cookie Check-in |
— | — | A Network Trojan was detected | [PT MALWARE] Feodo HTTP header Cookie Check-in |
— | — | A Network Trojan was detected | ET CNC Feodo Tracker Reported CnC Server group 3 |
— | — | A Network Trojan was detected | [PT MALWARE] Feodo HTTP header Cookie Check-in |
— | — | A Network Trojan was detected | ET CNC Feodo Tracker Reported CnC Server group 21 |
— | — | A Network Trojan was detected | [PT MALWARE] Feodo HTTP header Cookie Check-in |
— | — | A Network Trojan was detected | ET CNC Feodo Tracker Reported CnC Server group 16 |
— | — | A Network Trojan was detected | [PT MALWARE] Feodo HTTP header Cookie Check-in |
Process | Message |
|---|---|
setup.exe | Cancel |
setup.exe | Cancel |
setup.exe | Cancel |
setup.exe | Next |
setup.exe | Next |
setup.exe | Next |
setup.exe | Next |
setup.exe | Next |
setup.exe | Next |
setup.exe | Next |