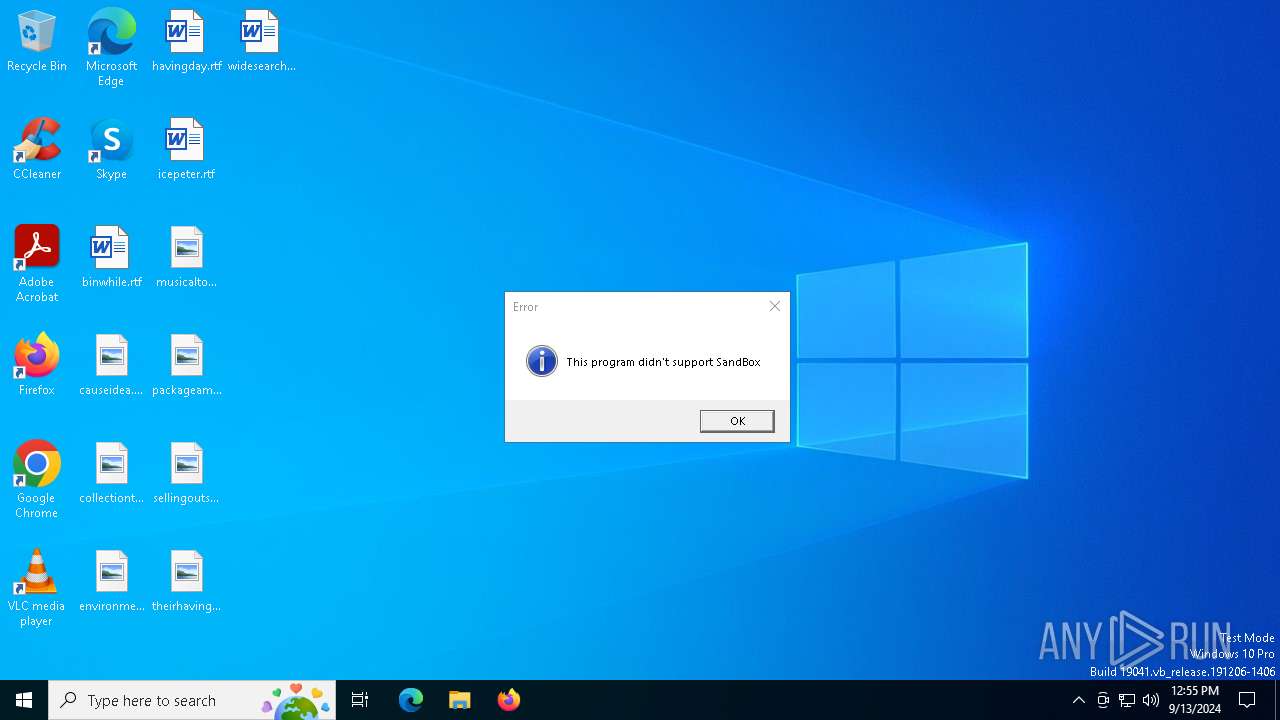
| File name: | EZHips - Copy.exe |
| Full analysis: | https://app.any.run/tasks/38601f03-e8d8-490f-b5a5-67af4c050178 |
| Verdict: | Malicious activity |
| Analysis date: | September 13, 2024, 12:55:06 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | 60A5559FE6D4DE7BB6ADFF0F2FDD3988 |
| SHA1: | 3329E9B878BD6FC257CE38011738AAC173292687 |
| SHA256: | 1969392BE892C6F256C6B860DB6D073FEBFF9C435412A81C1CA2BFD2CE59D2EC |
| SSDEEP: | 98304:tE9gdE+F+TviOsmwMz8avFuji0pEKXebgAVCPZwkD3Oe+R8RnSYenrtEriSK4DeP:FfMu8To |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks for Java to be installed
- EZHips - Copy.exe (PID: 6216)
Executable content was dropped or overwritten
- EZHips - Copy.exe (PID: 6216)
Uses WMIC.EXE to obtain CPU information
- EZHips - Copy.exe (PID: 6216)
Uses WMIC.EXE to obtain data on the base board management (motherboard or system board)
- EZHips - Copy.exe (PID: 6216)
Uses ATTRIB.EXE to modify file attributes
- EZHips - Copy.exe (PID: 6216)
Starts SC.EXE for service management
- EZHips - Copy.exe (PID: 6216)
Uses REG/REGEDIT.EXE to modify registry
- EZHips - Copy.exe (PID: 6216)
Starts CMD.EXE for commands execution
- EZHips - Copy.exe (PID: 6216)
INFO
Create files in a temporary directory
- EZHips - Copy.exe (PID: 6216)
- java.exe (PID: 5904)
Checks supported languages
- EZHips - Copy.exe (PID: 6216)
- java.exe (PID: 5904)
- i4jdel0.exe (PID: 1748)
Creates files in the program directory
- java.exe (PID: 5904)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 6880)
- WMIC.exe (PID: 5032)
- WMIC.exe (PID: 5656)
Reads Internet Explorer settings
- mshta.exe (PID: 6128)
Reads the computer name
- EZHips - Copy.exe (PID: 6216)
Reads the machine GUID from the registry
- EZHips - Copy.exe (PID: 6216)
Creates files or folders in the user directory
- EZHips - Copy.exe (PID: 6216)
The process uses the downloaded file
- mshta.exe (PID: 6128)
Checks proxy server information
- mshta.exe (PID: 6128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (57.6) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.9) |
| .exe | | | Generic Win/DOS Executable (2.6) |
| .exe | | | DOS Executable Generic (2.6) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2018:07:31 21:44:22+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 9 |
| CodeSize: | 186880 |
| InitializedDataSize: | 164352 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x18f28 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.0.1.1 |
| ProductVersionNumber: | 5.0.1.1 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | Debug |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | Beijing Huorong Network Technology Co., Ltd. |
| FileDescription: | Huorong Internet Security |
| FileVersion: | 5.0.1.1 |
| LegalCopyright: | Beijing Huorong Network Technology Co., Ltd. |
| ProductName: | Huorong Internet Security |
| ProductVersion: | 5.0.1.1 |
| OriginalFileName: | EZHips.exe |
| InternalName: | Huorong Internet Security |
Total processes
147
Monitored processes
28
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | reg query "SOFTWARE\VMware, Inc.\VMware Tools" | C:\Windows\System32\reg.exe | — | EZHips - Copy.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 872 | C:\WINDOWS\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1748 | C:\Users\admin\AppData\Local\Temp\i4jdel0.exe i4j9110981897799539405.tmp | C:\Users\admin\AppData\Local\Temp\i4jdel0.exe | — | EZHips - Copy.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2056 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2992 | attrib C:\Users\admin\AppData\Roaming\Windows +H | C:\Windows\System32\attrib.exe | — | EZHips - Copy.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3268 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3412 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3584 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4056 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5032 | wmic baseboard get SerialNumber | C:\Windows\System32\wbem\WMIC.exe | — | EZHips - Copy.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 971
Read events
1 965
Write events
6
Delete events
0
Modification events
| (PID) Process: | (6216) EZHips - Copy.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\ej-technologies\exe4j\pids |
| Operation: | write | Name: | c:\users\admin\appdata\local\temp\ezhips - copy.exe |
Value: 6216 | |||
| (PID) Process: | (6216) EZHips - Copy.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\ej-technologies\exe4j\jvms\c:/program files/java/jre1.8.0_271/bin/java.exe |
| Operation: | write | Name: | LastWriteTime |
Value: FE850DA0993CD901 | |||
| (PID) Process: | (6216) EZHips - Copy.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\ej-technologies\exe4j\jvms\c:/program files/java/jre1.8.0_271/bin/java.exe |
| Operation: | write | Name: | Version |
Value: 1.8.0_271 | |||
| (PID) Process: | (6128) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6128) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6128) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
3
Suspicious files
2
Text files
2
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5904 | java.exe | C:\ProgramData\Oracle\Java\.oracle_jre_usage\17dfc292991c8061.timestamp | text | |
MD5:0ED594CE59B4BD3B5DD65DCDEC71C364 | SHA256:4657420E3DDFE642AF0F465BC40E6D03773CBBA02339833E84BD31DC28A94F15 | |||
| 6216 | EZHips - Copy.exe | C:\Users\admin\AppData\Local\Temp\e4jB222.tmp_dir1726232116\exe4jlib.jar | java | |
MD5:35CDCD4A8A01AAA62DDE9A5F1B8702C9 | SHA256:99374E9B2E4B7402C278C41D2EEF5A50CA8A7B36DC61357D4C6A01D5076861AF | |||
| 6216 | EZHips - Copy.exe | C:\Users\admin\AppData\Local\Temp\e4jB222.tmp_dir1726232116\Client-1.0.0-jar-with-dependencies.jar | compressed | |
MD5:F5FB656D75C6B42F45270CCA6F9782E7 | SHA256:B13FBF0DAAD9FE5875CCF45B2CAB092741574A18D52F88A4D00B946FA68DAA76 | |||
| 6216 | EZHips - Copy.exe | C:\Users\admin\AppData\Local\Temp\i4jdel0.exe | executable | |
MD5:F3541C34A88F52C13D709AF62F000055 | SHA256:1C822B3773DA680B2575FE810E7880D4A6BF81A501E9100BBF951553A70B738F | |||
| 6216 | EZHips - Copy.exe | C:\Users\admin\AppData\Local\Temp\e4jB222.tmp_dir1726232116\i4jdel.exe | executable | |
MD5:F3541C34A88F52C13D709AF62F000055 | SHA256:1C822B3773DA680B2575FE810E7880D4A6BF81A501E9100BBF951553A70B738F | |||
| 6216 | EZHips - Copy.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1693682860-607145093-2874071422-1001\83aa4cc77f591dfc2374580bbd95f6ba_bb926e54-e3ca-40fd-ae90-2764341e7792 | dbf | |
MD5:C8366AE350E7019AEFC9D1E6E6A498C6 | SHA256:11E6ACA8E682C046C83B721EEB5C72C5EF03CB5936C60DF6F4993511DDC61238 | |||
| 6216 | EZHips - Copy.exe | C:\Users\admin\AppData\Local\Temp\e4jB33C.tmp | text | |
MD5:E293057450F58A86C057A66EF68BA694 | SHA256:298641C5A1DE57362FACB542457D295C3648DE04F07EDAC0D5B9642EE973D8CF | |||
| 6216 | EZHips - Copy.exe | C:\Users\admin\AppData\Local\Temp\i4j9110981897799539405.tmp | binary | |
MD5:F359DFE5BD4AB7F82D9C6AFCE35C96A6 | SHA256:3C6A361FA7AAB6DE92F0BBD51600E343200C88A51786930EA2EA0A2BC7306EE8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
22
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3424 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3448 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3448 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3424 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3424 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6232 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3448 | SIHClient.exe | 20.114.59.183:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |