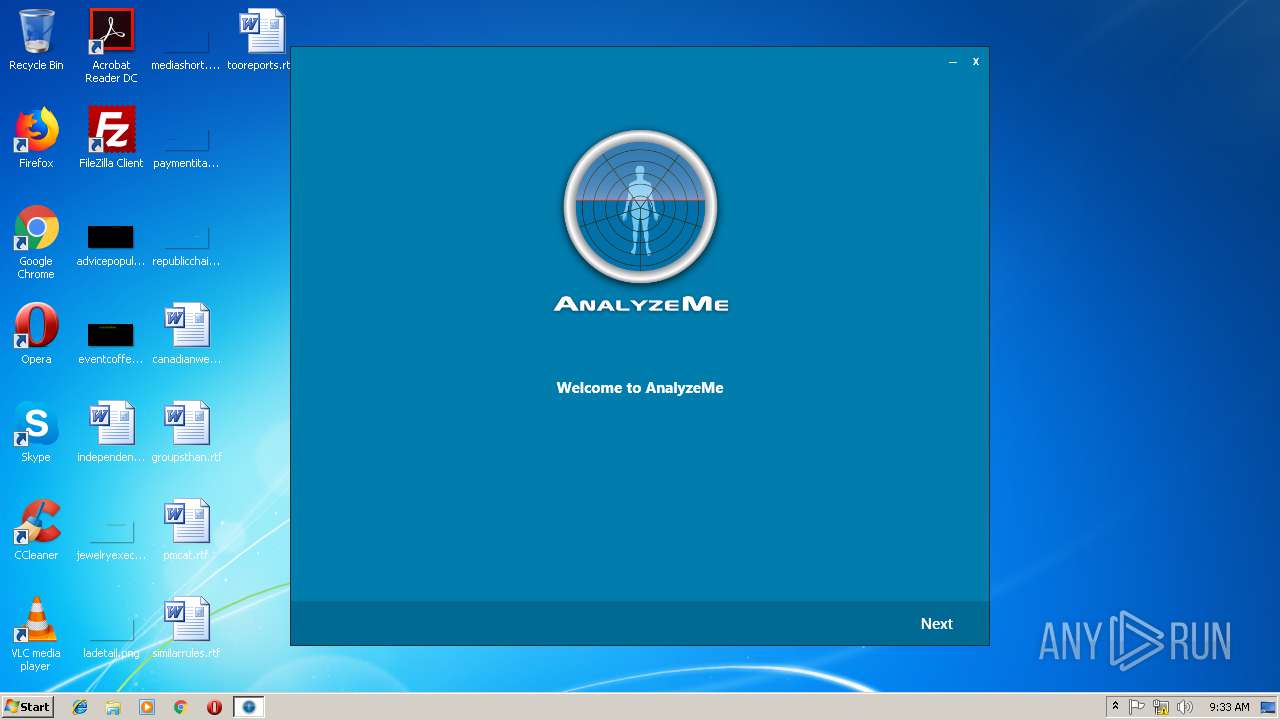
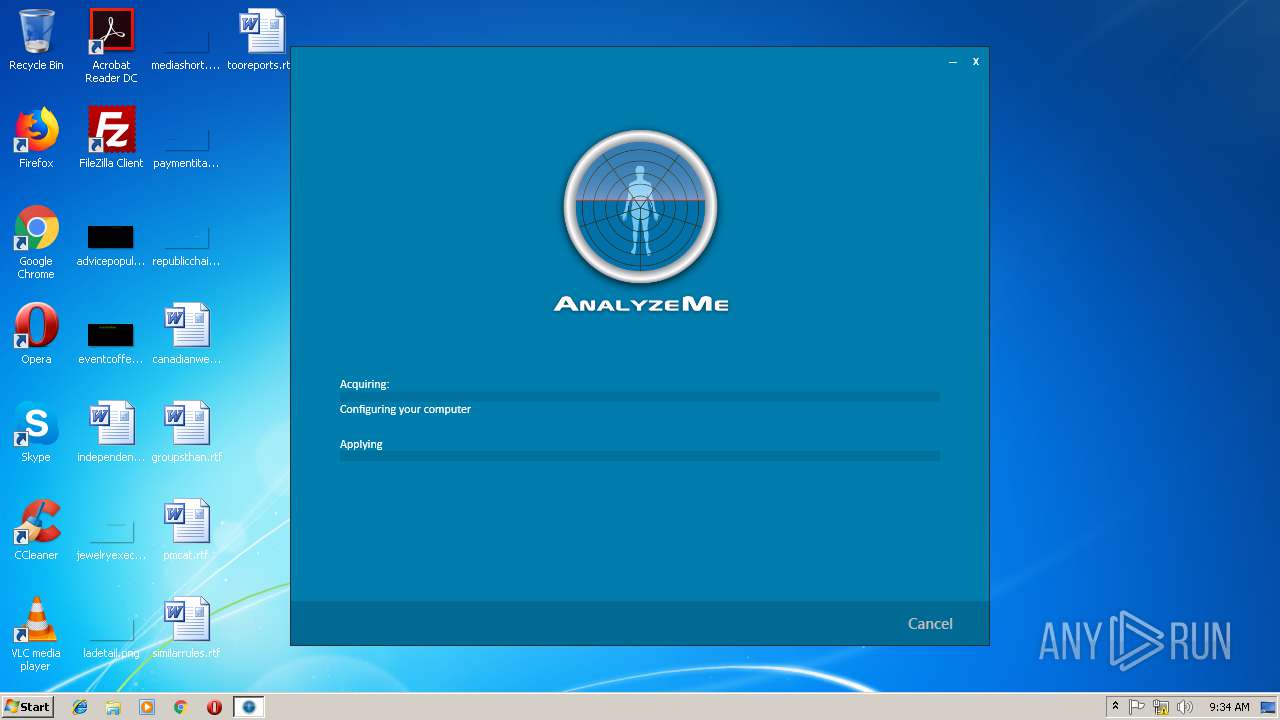
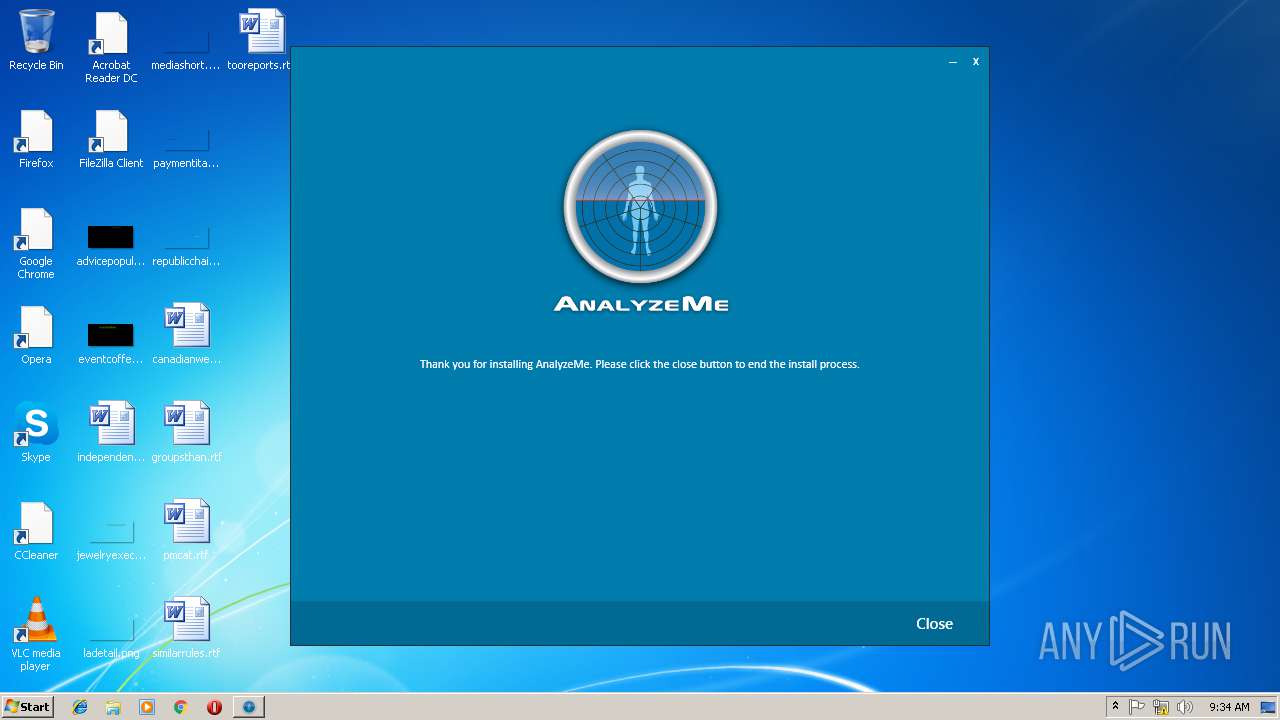
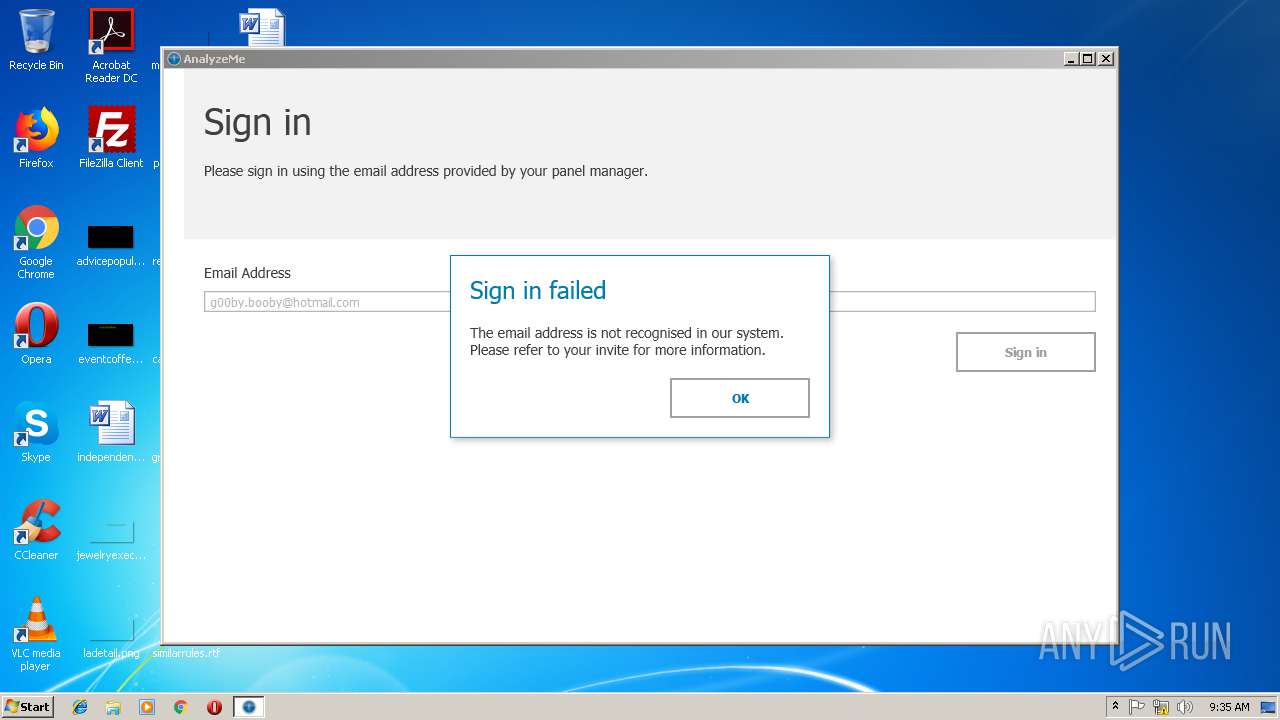
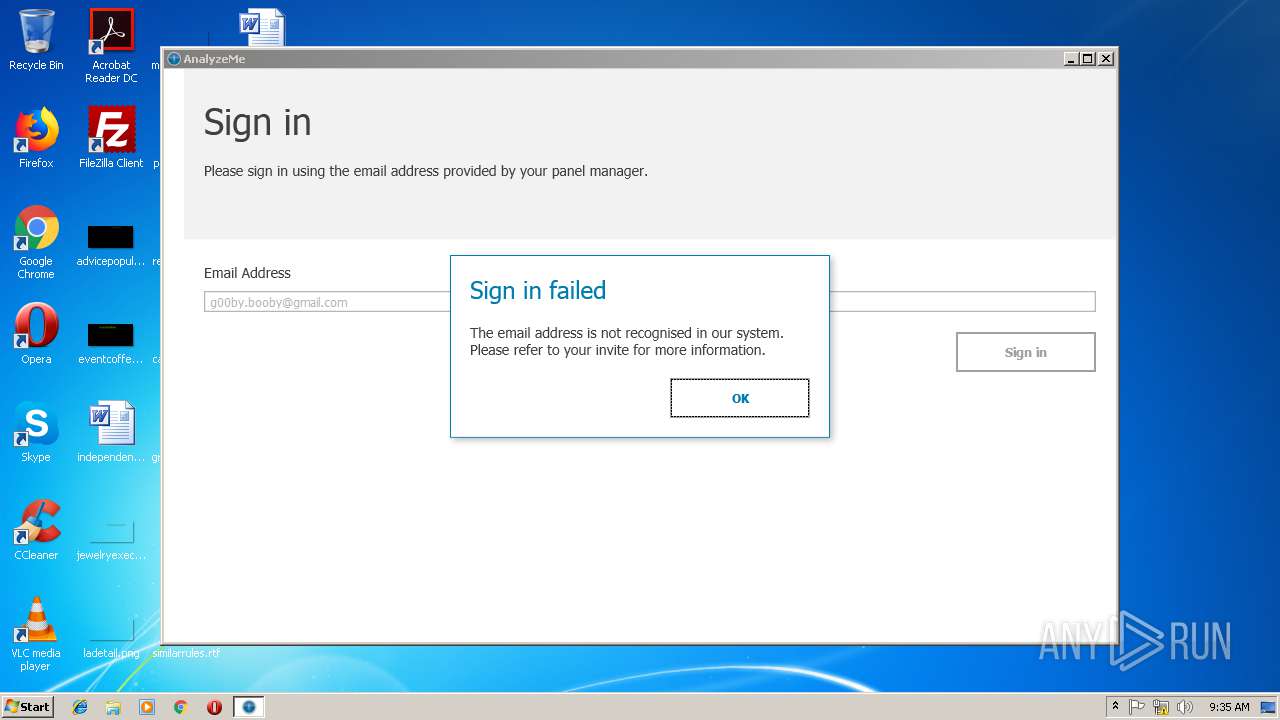
| URL: | https://q.rmine.co/p/?p=4qrq3v1k |
| Full analysis: | https://app.any.run/tasks/5d416a47-e3ee-4c07-a882-5332b3fec814 |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2018, 09:30:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | FCD28B2230CF9DBC1017283BEAE2EC3B |
| SHA1: | B20B96EE1AAE465A86619EF1ADC1C1917CC20300 |
| SHA256: | 195E728E3C1845AEA6289B9E018FF8BC89C3166F558ED45841F3365E50318A02 |
| SSDEEP: | 3:N8IiRUwO:2IivO |
MALICIOUS
Application was dropped or rewritten from another process
- serveFile[1].exe (PID: 3044)
- Setup.exe (PID: 2892)
- UsageMonitor.WindowsService.exe (PID: 4076)
- UsageMonitor.UI.App.exe (PID: 1888)
- UsageMonitor.HealthCheck.exe (PID: 3096)
Loads dropped or rewritten executable
- serveFile[1].exe (PID: 3044)
- UsageMonitor.WindowsService.exe (PID: 4076)
- UsageMonitor.HealthCheck.exe (PID: 3096)
- UsageMonitor.UI.App.exe (PID: 1888)
Changes the autorun value in the registry
- Setup.exe (PID: 2892)
SUSPICIOUS
Executable content was dropped or overwritten
- iexplore.exe (PID: 2952)
- iexplore.exe (PID: 3232)
- serveFile[1].exe (PID: 3044)
- Setup.exe (PID: 2892)
- msiexec.exe (PID: 2764)
Searches for installed software
- Setup.exe (PID: 2892)
Changes the autorun value in the registry
- msiexec.exe (PID: 2764)
Creates files in the user directory
- serveFile[1].exe (PID: 3044)
Creates files in the program directory
- Setup.exe (PID: 2892)
Creates a software uninstall entry
- Setup.exe (PID: 2892)
Uses RUNDLL32.EXE to load library
- UsageMonitor.UI.App.exe (PID: 1888)
Reads Internet Cache Settings
- rundll32.exe (PID: 2804)
- UsageMonitor.UI.App.exe (PID: 1888)
Reads Environment values
- UsageMonitor.UI.App.exe (PID: 1888)
INFO
Creates files in the user directory
- iexplore.exe (PID: 2952)
- iexplore.exe (PID: 3232)
Application launched itself
- iexplore.exe (PID: 2952)
- msiexec.exe (PID: 2764)
Changes internet zones settings
- iexplore.exe (PID: 2952)
Reads Internet Cache Settings
- iexplore.exe (PID: 3232)
- iexplore.exe (PID: 2952)
Creates files in the program directory
- msiexec.exe (PID: 2764)
Creates a software uninstall entry
- msiexec.exe (PID: 2764)
Low-level read access rights to disk partition
- vssvc.exe (PID: 3424)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
50
Monitored processes
13
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1888 | "C:\Program Files\AnalyzeMe\UsageMonitor.UI.App.exe" /FirstTime | C:\Program Files\AnalyzeMe\UsageMonitor.UI.App.exe | serveFile[1].exe | ||||||||||||
User: admin Company: RealityMine Ltd Integrity Level: MEDIUM Description: UsageMonitor.UI.App Exit code: 0 Version: 2.0.3.0 Modules
| |||||||||||||||
| 2072 | C:\Windows\system32\MsiExec.exe -Embedding AA816EE30ED9F1FCC222C0563457B1D0 M Global\MSI0000 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2740 | DrvInst.exe "1" "200" "STORAGE\VolumeSnapshot\HarddiskVolumeSnapshot18" "" "" "6792c44eb" "00000000" "00000574" "000002D0" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2764 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2804 | "C:\Windows\system32\rundll32.exe" "C:\Windows\system32\WININET.dll",DispatchAPICall 1 | C:\Windows\system32\rundll32.exe | — | UsageMonitor.UI.App.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2892 | "C:\Users\admin\AppData\Local\Temp\{c246614a-ee40-4deb-a5bc-b0878350f06f}\.be\Setup.exe" -q -burn.elevated BurnPipe.{61719E4B-CB17-4E5F-808C-5BA891C0A270} {5249558B-3BBB-4014-85AB-36F2B58643D0} 3044 | C:\Users\admin\AppData\Local\Temp\{c246614a-ee40-4deb-a5bc-b0878350f06f}\.be\Setup.exe | serveFile[1].exe | ||||||||||||
User: admin Company: RealityMine Ltd Integrity Level: HIGH Description: AnalyzeMe Exit code: 0 Version: 2.0.3.0 Modules
| |||||||||||||||
| 2952 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
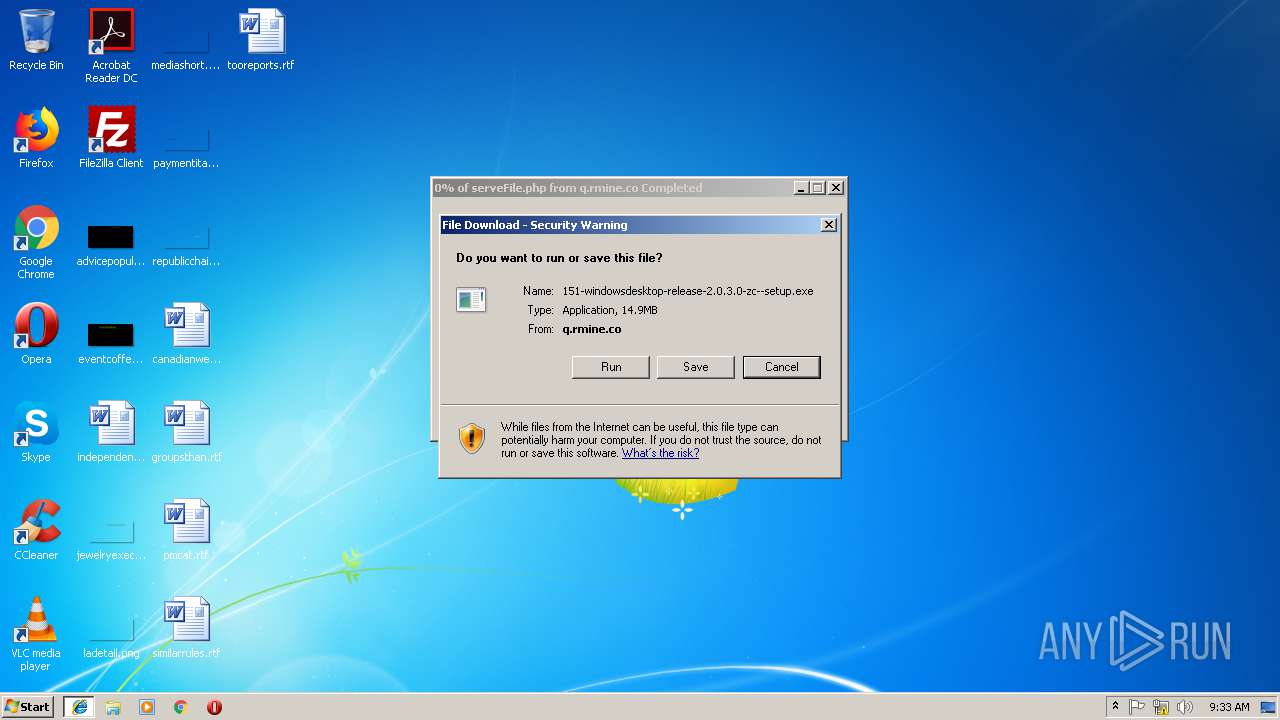
| 3044 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\serveFile[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\serveFile[1].exe | iexplore.exe | ||||||||||||
User: admin Company: RealityMine Ltd Integrity Level: MEDIUM Description: AnalyzeMe Exit code: 0 Version: 2.0.3.0 Modules
| |||||||||||||||
| 3096 | "C:\Program Files\AnalyzeMe\UsageMonitor.HealthCheck.exe" | C:\Program Files\AnalyzeMe\UsageMonitor.HealthCheck.exe | — | serveFile[1].exe | |||||||||||
User: admin Company: RealityMine Ltd Integrity Level: MEDIUM Description: UsageMonitor.HealthCheck Exit code: 4294967295 Version: 2.0.3.0 Modules
| |||||||||||||||
| 3232 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2952 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 853
Read events
1 455
Write events
381
Delete events
17
Modification events
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {A414E9ED-F939-11E8-BAD8-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E2070C000400060009001F000100DA00 | |||
Executable files
39
Suspicious files
9
Text files
135
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2952 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF78A123196C332999.TMP | — | |
MD5:— | SHA256:— | |||
| 3044 | serveFile[1].exe | C:\Users\admin\AppData\Local\Temp\{c246614a-ee40-4deb-a5bc-b0878350f06f}\.ba1\Installer.BootstrapperApplication.dll | executable | |
MD5:— | SHA256:— | |||
| 2952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\serveFile[1].exe | executable | |
MD5:— | SHA256:— | |||
| 3044 | serveFile[1].exe | C:\Users\admin\AppData\Local\Temp\{c246614a-ee40-4deb-a5bc-b0878350f06f}\.ba1\LogoTitle.png | image | |
MD5:— | SHA256:— | |||
| 3232 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\151-windowsdesktop-release-2.0.3.0-zc--setup[1].exe | executable | |
MD5:— | SHA256:— | |||
| 3232 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\MSHist012018120620181207\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{A414E9EE-F939-11E8-BAD8-5254004A04AF}.dat | binary | |
MD5:— | SHA256:— | |||
| 2952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\History.IE5\MSHist012018120620181207\index.dat | dat | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
6
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3232 | iexplore.exe | GET | 302 | 52.211.91.170:80 | http://q.rmine.co/p/serveBinary.php?platform=windowsDesktop&version=2.0.3.0&brandId=151&status=release&update=true | IE | — | — | unknown |
2952 | iexplore.exe | GET | 200 | 13.107.21.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2952 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3232 | iexplore.exe | 52.211.91.170:443 | q.rmine.co | Amazon.com, Inc. | IE | unknown |
3232 | iexplore.exe | 52.211.91.170:80 | q.rmine.co | Amazon.com, Inc. | IE | unknown |
1888 | UsageMonitor.UI.App.exe | 54.77.147.229:443 | www.analyzeme.net | Amazon.com, Inc. | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
q.rmine.co |
| unknown |
www.analyzeme.net |
| unknown |