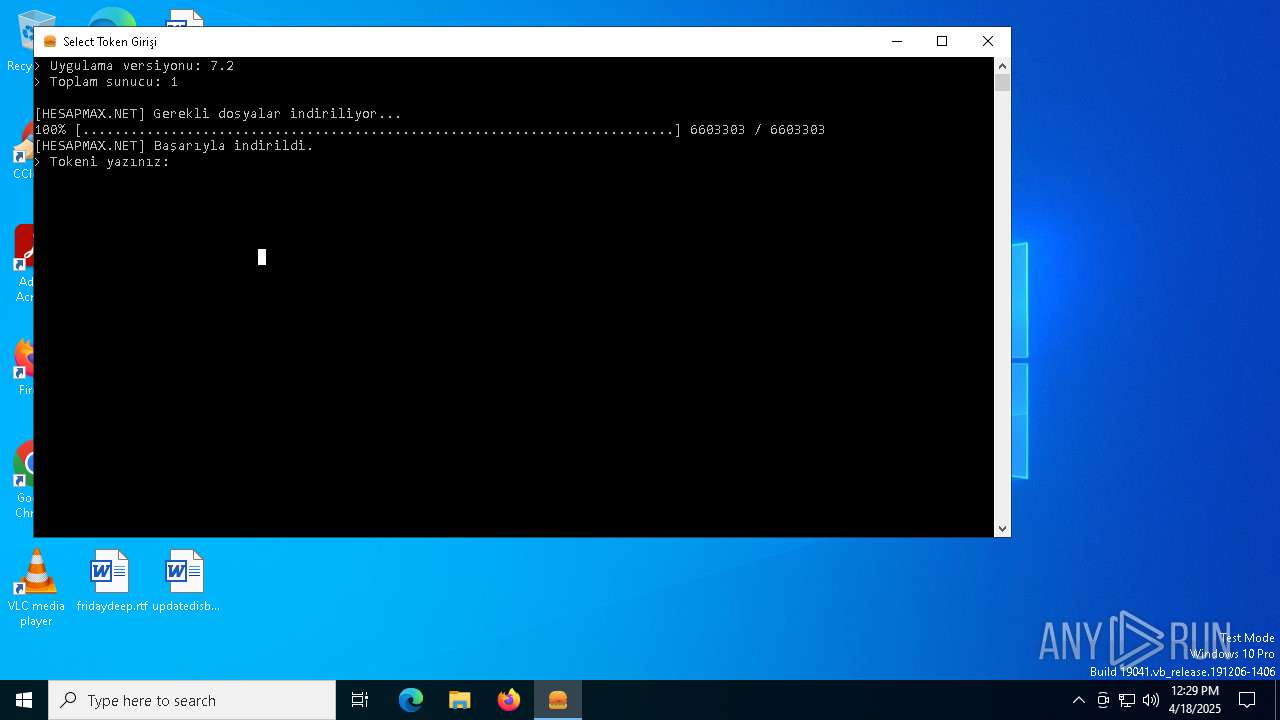
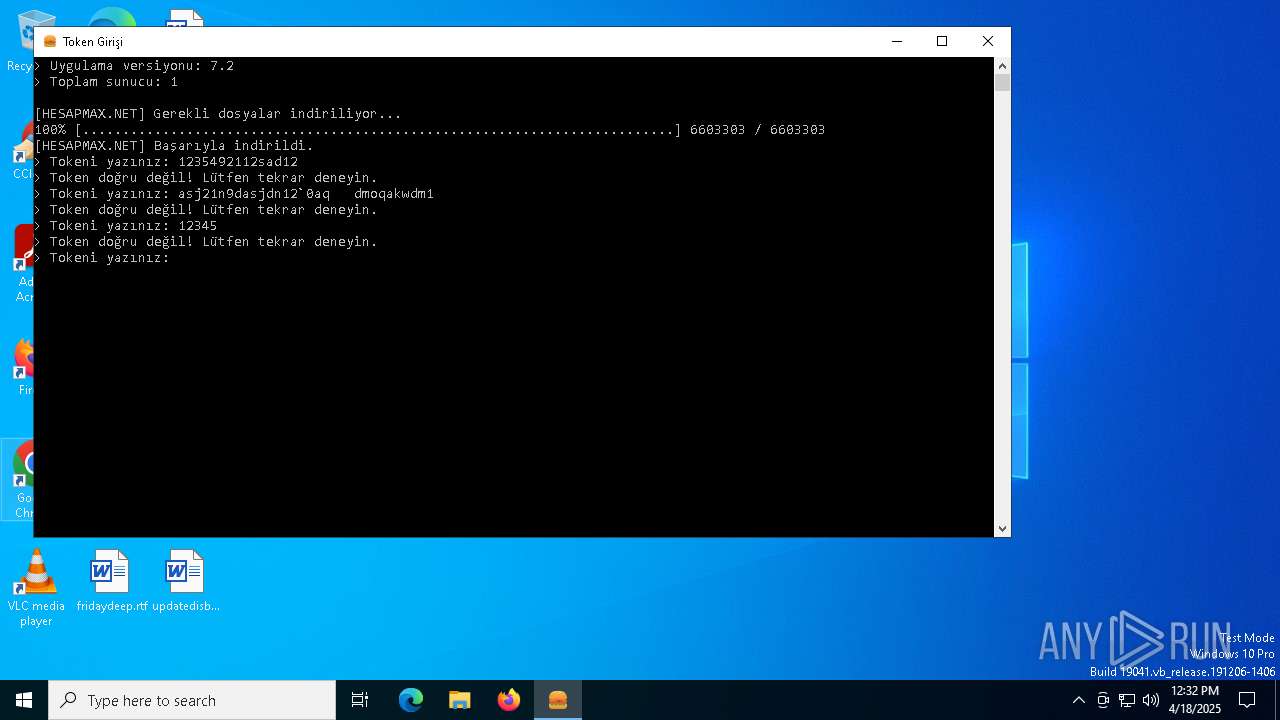
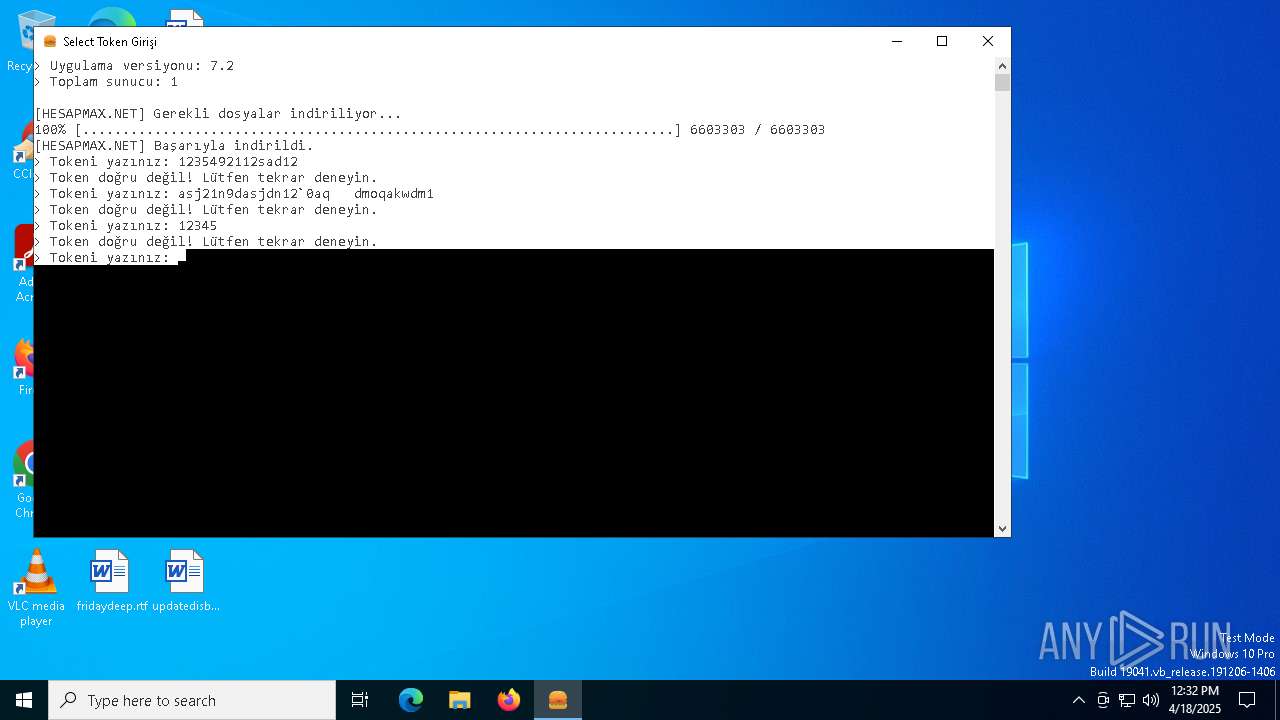
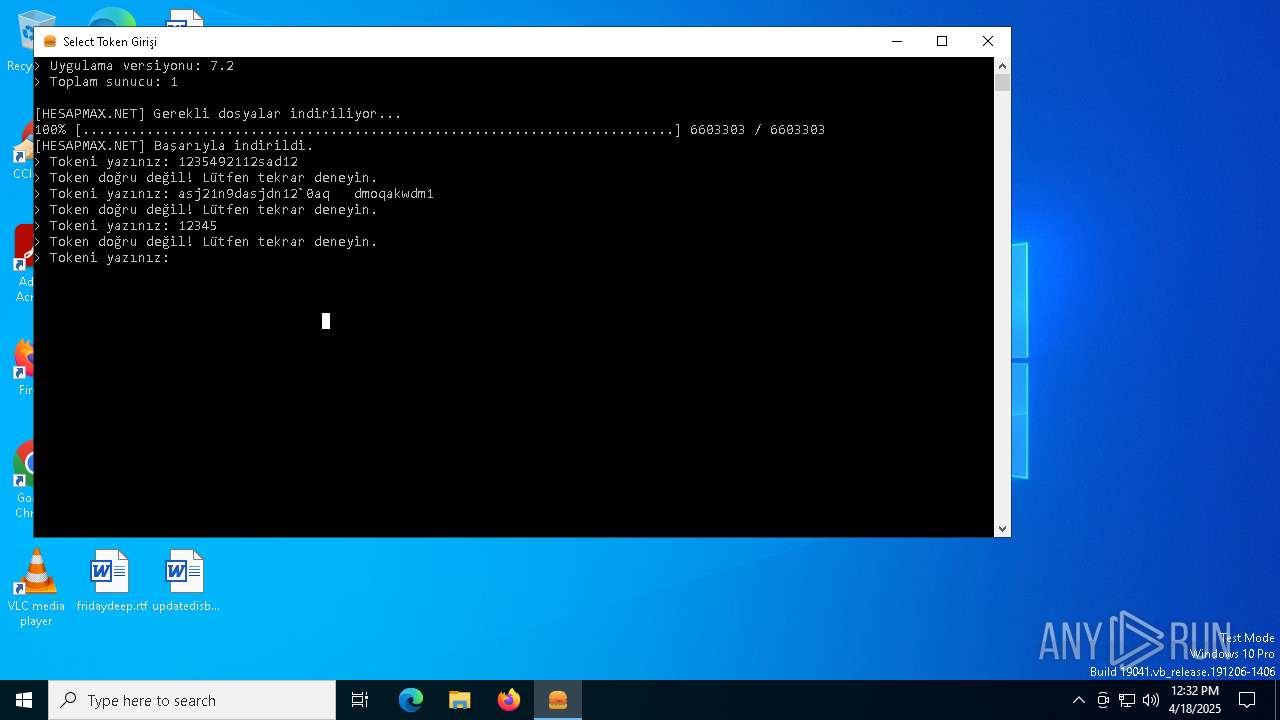
| File name: | AbiHesap.exe |
| Full analysis: | https://app.any.run/tasks/f876e4f6-5cd8-4eea-a78b-9598b21636e0 |
| Verdict: | Malicious activity |
| Analysis date: | April 18, 2025, 12:28:28 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 7 sections |
| MD5: | FE66AC54C847B7B036E8E46AF6E81BA7 |
| SHA1: | 5139FA4E5715A2BDE2F0ACC094D15955334572B1 |
| SHA256: | 195986D466C046C97F524DC67269DB0A4F4172B7EC2A83310DB31F10DAD2C09B |
| SSDEEP: | 98304:TdJ5MYL9m/LZl7dukTHDauUk/o5QgSZ1Um7KunZM9HwGBWJFZSy9l57OaYDIA5zm:w2u9y0l1x6mDYtSXBrwd0jZS |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops python dynamic module
- AbiHesap.exe (PID: 4108)
Application launched itself
- AbiHesap.exe (PID: 4108)
Process drops legitimate windows executable
- AbiHesap.exe (PID: 4108)
The process drops C-runtime libraries
- AbiHesap.exe (PID: 4108)
Executable content was dropped or overwritten
- AbiHesap.exe (PID: 4108)
- AbiHesap.exe (PID: 4812)
Loads Python modules
- AbiHesap.exe (PID: 4812)
Starts CMD.EXE for commands execution
- AbiHesap.exe (PID: 4812)
INFO
Reads the computer name
- AbiHesap.exe (PID: 4108)
- AbiHesap.exe (PID: 4812)
Checks supported languages
- AbiHesap.exe (PID: 4108)
- AbiHesap.exe (PID: 4812)
Create files in a temporary directory
- AbiHesap.exe (PID: 4108)
- AbiHesap.exe (PID: 4812)
The sample compiled with english language support
- AbiHesap.exe (PID: 4108)
Reads the machine GUID from the registry
- AbiHesap.exe (PID: 4812)
Checks proxy server information
- AbiHesap.exe (PID: 4812)
- slui.exe (PID: 6272)
Creates files or folders in the user directory
- AbiHesap.exe (PID: 4812)
PyInstaller has been detected (YARA)
- AbiHesap.exe (PID: 4108)
- AbiHesap.exe (PID: 4812)
Reads the software policy settings
- slui.exe (PID: 6640)
- slui.exe (PID: 6272)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2023:07:12 13:34:08+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.32 |
| CodeSize: | 165888 |
| InitializedDataSize: | 199168 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa330 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows command line |
Total processes
137
Monitored processes
8
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1072 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | AbiHesap.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1280 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | AbiHesap.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1452 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4108 | "C:\Users\admin\AppData\Local\Temp\AbiHesap.exe" | C:\Users\admin\AppData\Local\Temp\AbiHesap.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 4812 | "C:\Users\admin\AppData\Local\Temp\AbiHesap.exe" | C:\Users\admin\AppData\Local\Temp\AbiHesap.exe | AbiHesap.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 6272 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6640 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7148 | C:\WINDOWS\system32\cmd.exe /c @echo off | C:\Windows\System32\cmd.exe | — | AbiHesap.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 215
Read events
4 215
Write events
0
Delete events
0
Modification events
Executable files
77
Suspicious files
9
Text files
38
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4108 | AbiHesap.exe | C:\Users\admin\AppData\Local\Temp\_MEI41082\Crypto\Cipher\_ARC4.pyd | executable | |
MD5:B8CE6246C867FA4D9A97C8C0ABD86162 | SHA256:3BFCEEF9B2A31336876A2A6BE63891FDA68BA30AC37EFCB94A4CED10A6E6C23D | |||
| 4108 | AbiHesap.exe | C:\Users\admin\AppData\Local\Temp\_MEI41082\Crypto\Cipher\_raw_arc2.pyd | executable | |
MD5:9CE1EC6C375848D729C99AA19B04AC4A | SHA256:119ED08B30A011FB067BE66BAD5CA7BE9910632583AB0C723ED770A38DD99212 | |||
| 4108 | AbiHesap.exe | C:\Users\admin\AppData\Local\Temp\_MEI41082\Crypto\Cipher\_chacha20.pyd | executable | |
MD5:5CAD133D9824EBFAAAF6C23FD7117775 | SHA256:B80E579CEB9902DE24B6B0794D9169B0248C01FD539003F21E92655920EBA461 | |||
| 4108 | AbiHesap.exe | C:\Users\admin\AppData\Local\Temp\_MEI41082\Crypto\Cipher\_raw_aes.pyd | executable | |
MD5:ABBE9B2424566E107CB05D0DDA0AA636 | SHA256:C438DD66FA669430CCE11B2ACB7DC0EE72B7953B07013FDA6BF6B803C2C961F9 | |||
| 4108 | AbiHesap.exe | C:\Users\admin\AppData\Local\Temp\_MEI41082\Crypto\Cipher\_raw_aesni.pyd | executable | |
MD5:DD3143D155A6D8A1C9F12CAE6E86484A | SHA256:90ED3206CA3D7248B5152B500A9D48BD55E1D178AED26214CE351090342260D1 | |||
| 4108 | AbiHesap.exe | C:\Users\admin\AppData\Local\Temp\_MEI41082\Crypto\Cipher\_raw_cbc.pyd | executable | |
MD5:FF2C1C4A7AE46C12EB3963F508DAD30F | SHA256:73CF4155DF136DB24C2240E8DB0C76BEDCBB721E910558512D6008ADAF7EED50 | |||
| 4108 | AbiHesap.exe | C:\Users\admin\AppData\Local\Temp\_MEI41082\Crypto\Cipher\_raw_cast.pyd | executable | |
MD5:92FE77E205F6DB73E0676081E95340B0 | SHA256:46BA53DEB7E77D5BD5A384ACDF5BFB01814892236F98390EC9A6717F98760CFE | |||
| 4108 | AbiHesap.exe | C:\Users\admin\AppData\Local\Temp\_MEI41082\Crypto\Cipher\_raw_cfb.pyd | executable | |
MD5:FE489576D8950611C13E6CD1D682BC3D | SHA256:BB79A502ECA26D3418B49A47050FB4015FDB24BEE97CE56CDD070D0FCEB96CCD | |||
| 4108 | AbiHesap.exe | C:\Users\admin\AppData\Local\Temp\_MEI41082\Crypto\Cipher\_Salsa20.pyd | executable | |
MD5:E598D24941E68620AEF43723B239E1C5 | SHA256:E63D4123D894B61E0242D53813307FA1FF3B7B60818827520F7FF20CABCD8904 | |||
| 4108 | AbiHesap.exe | C:\Users\admin\AppData\Local\Temp\_MEI41082\Crypto\Hash\_BLAKE2b.pyd | executable | |
MD5:519B19AE9AECFABA15A9C92C9A0F5F9E | SHA256:CA7A058D5D10F5F136A6A19758F3FB9C822499700243D78034E9471A5B236467 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
26
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5056 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5056 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.1:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4812 | AbiHesap.exe | 188.114.96.3:443 | sunucu.abihesap.com | CLOUDFLARENET | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
sunucu.abihesap.com |
| unknown |
chromedriver.storage.googleapis.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |