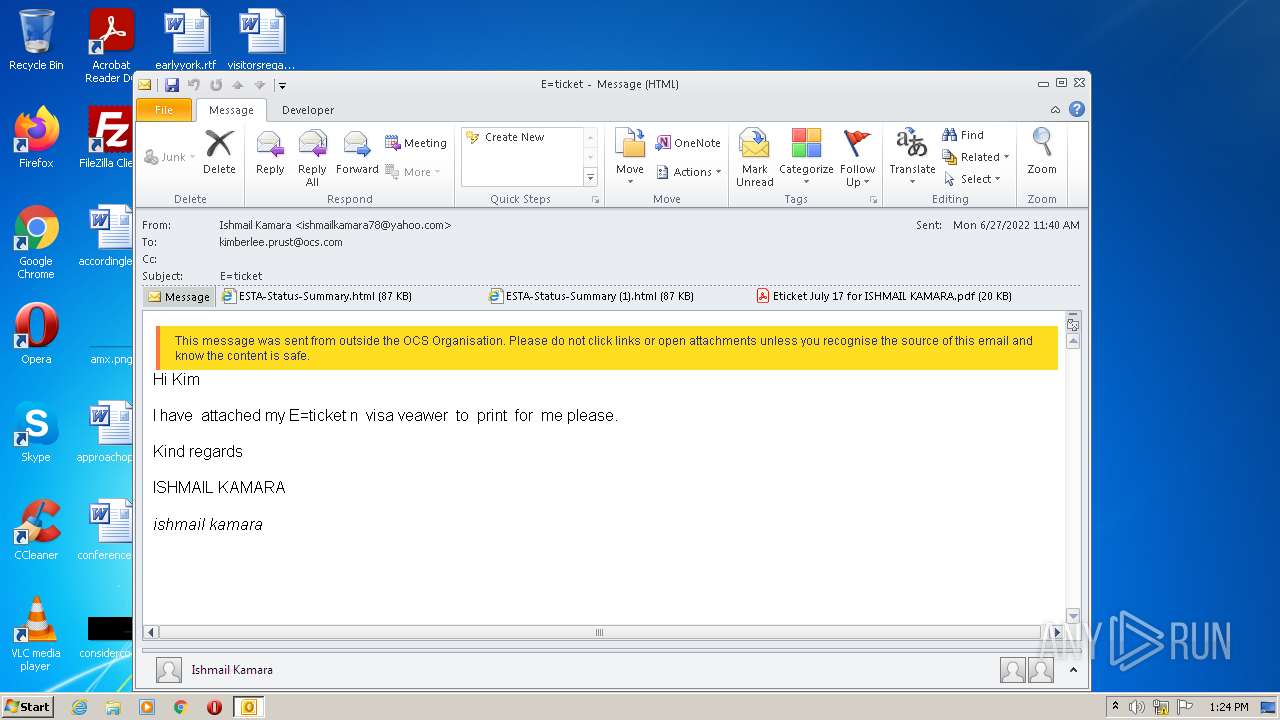
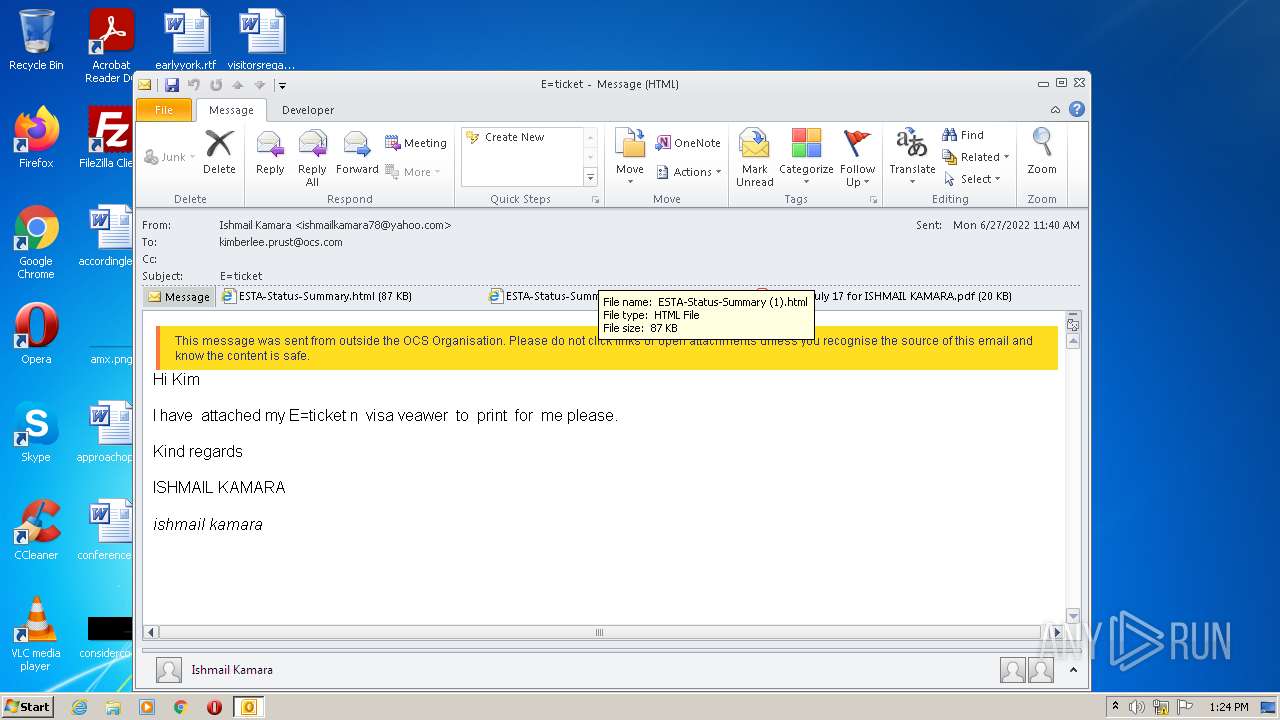
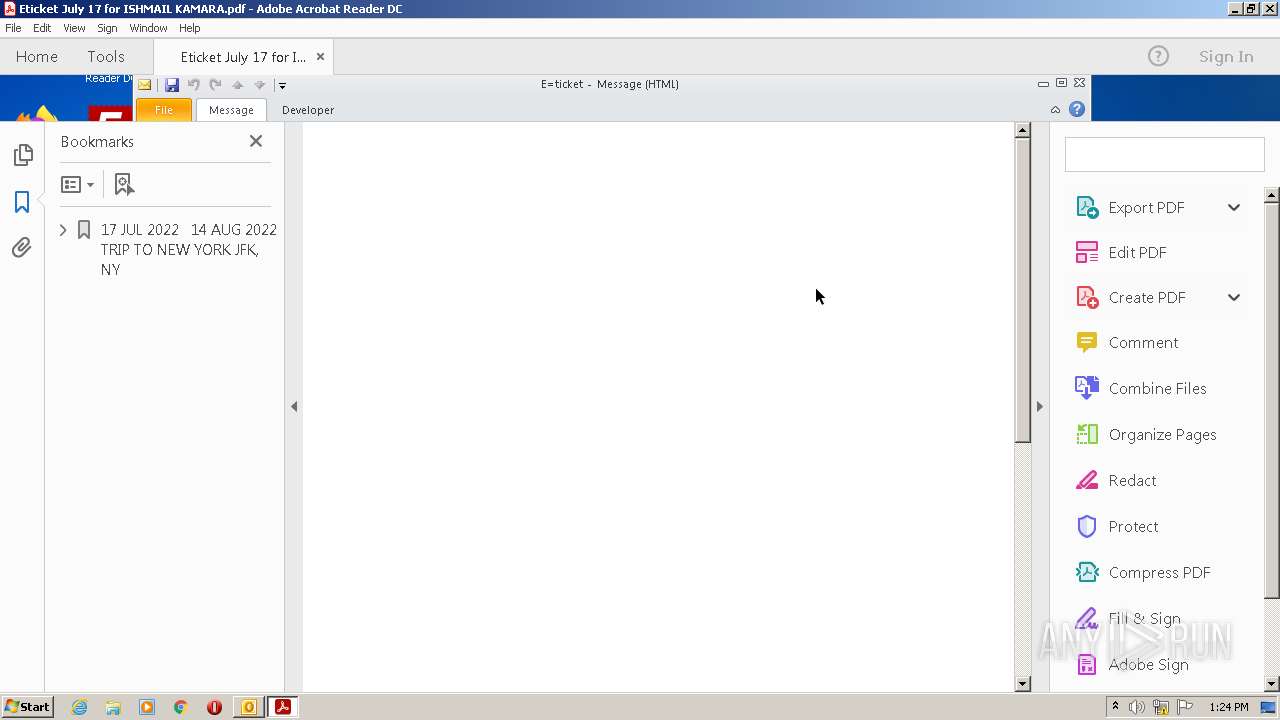
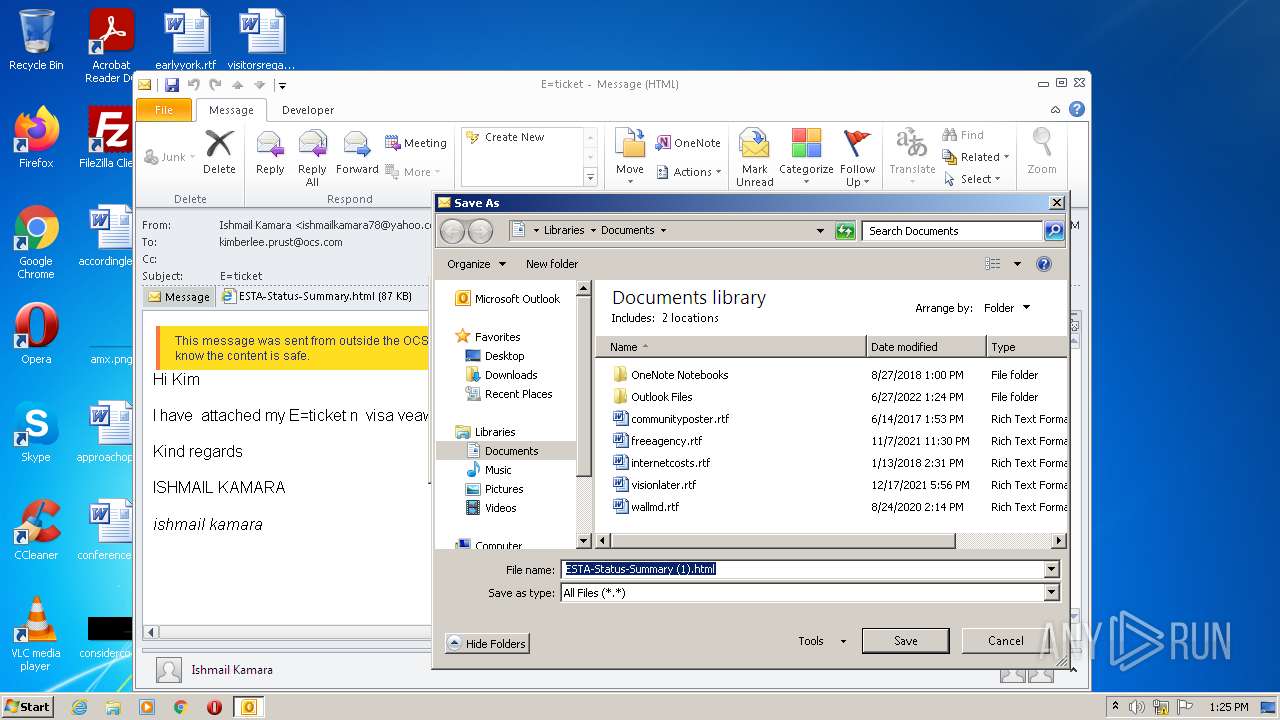
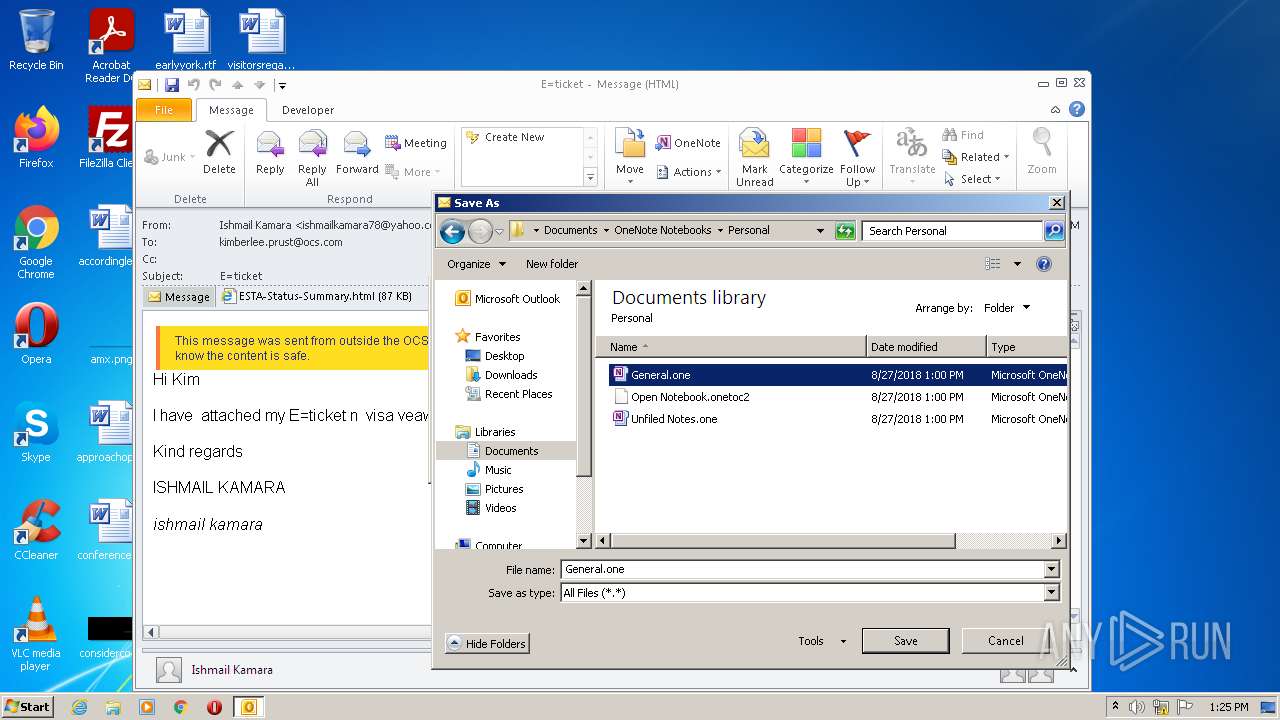
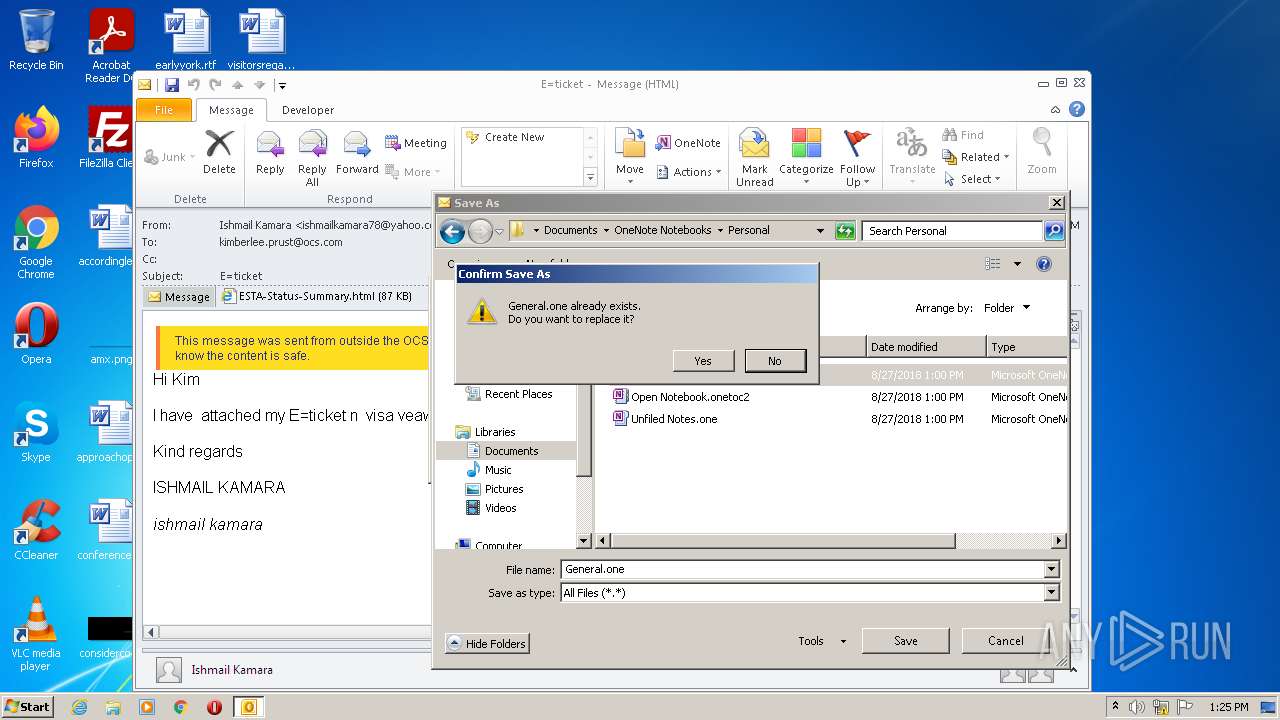
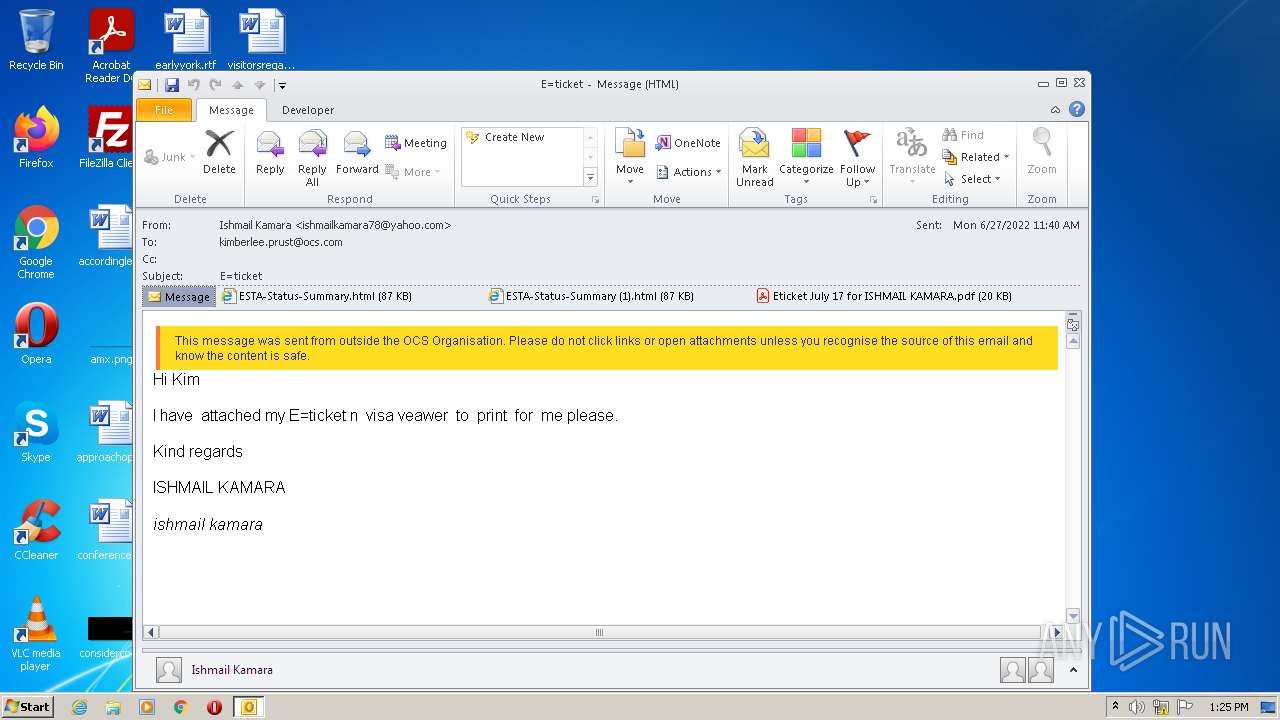
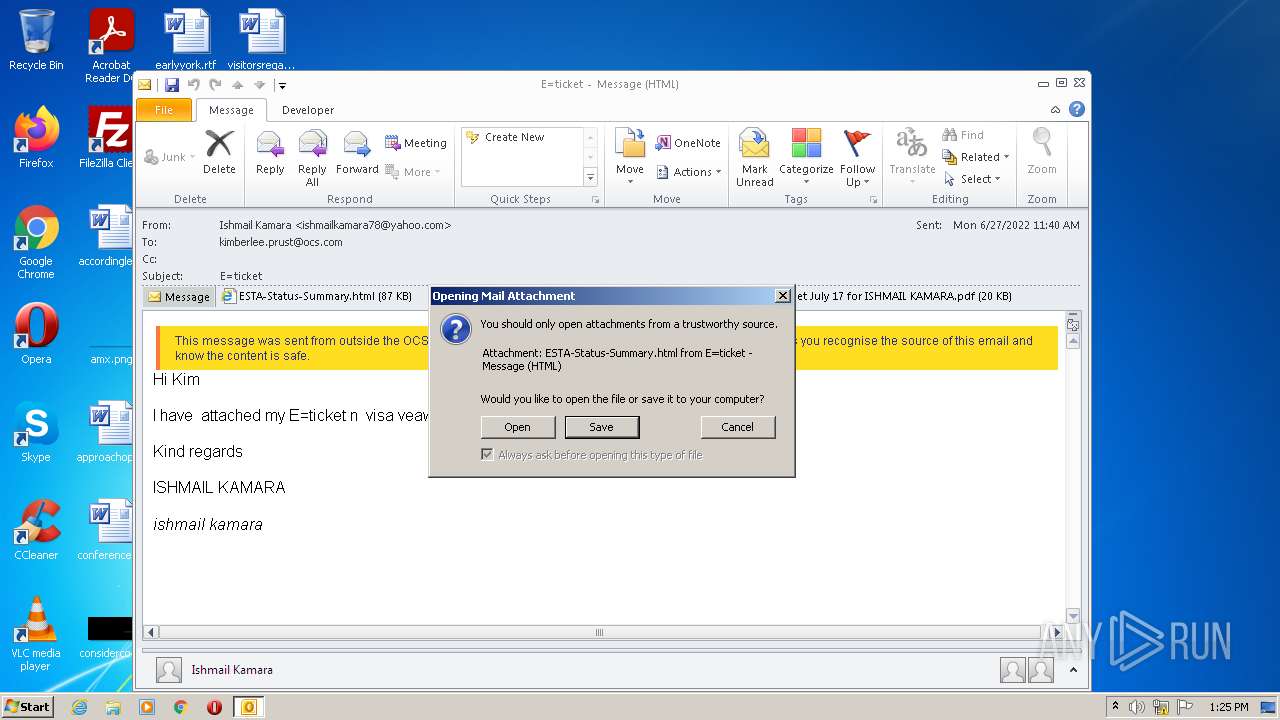
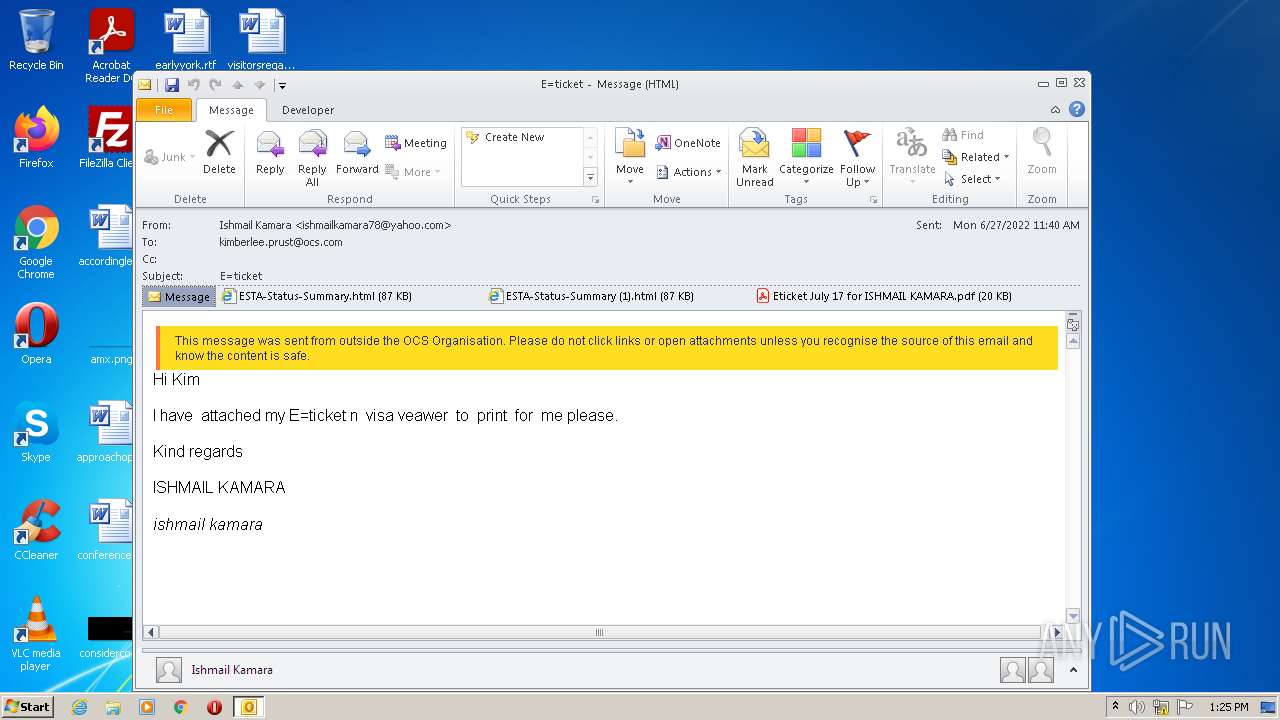
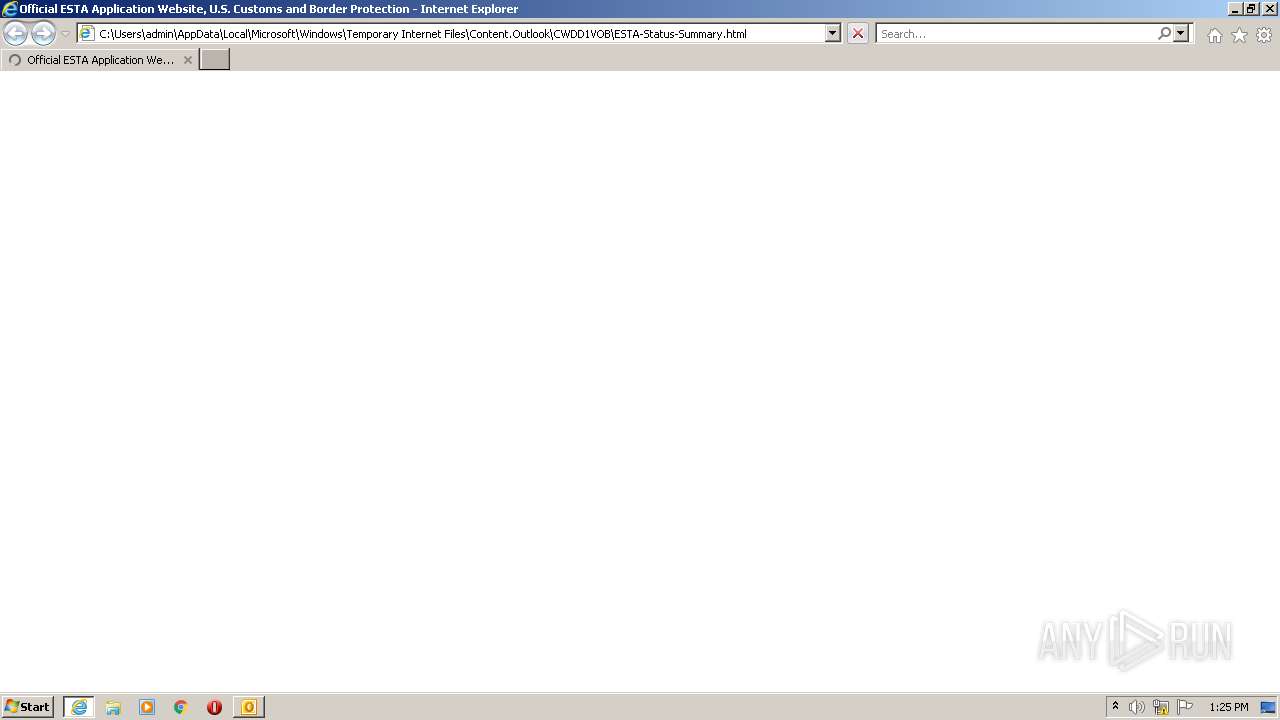
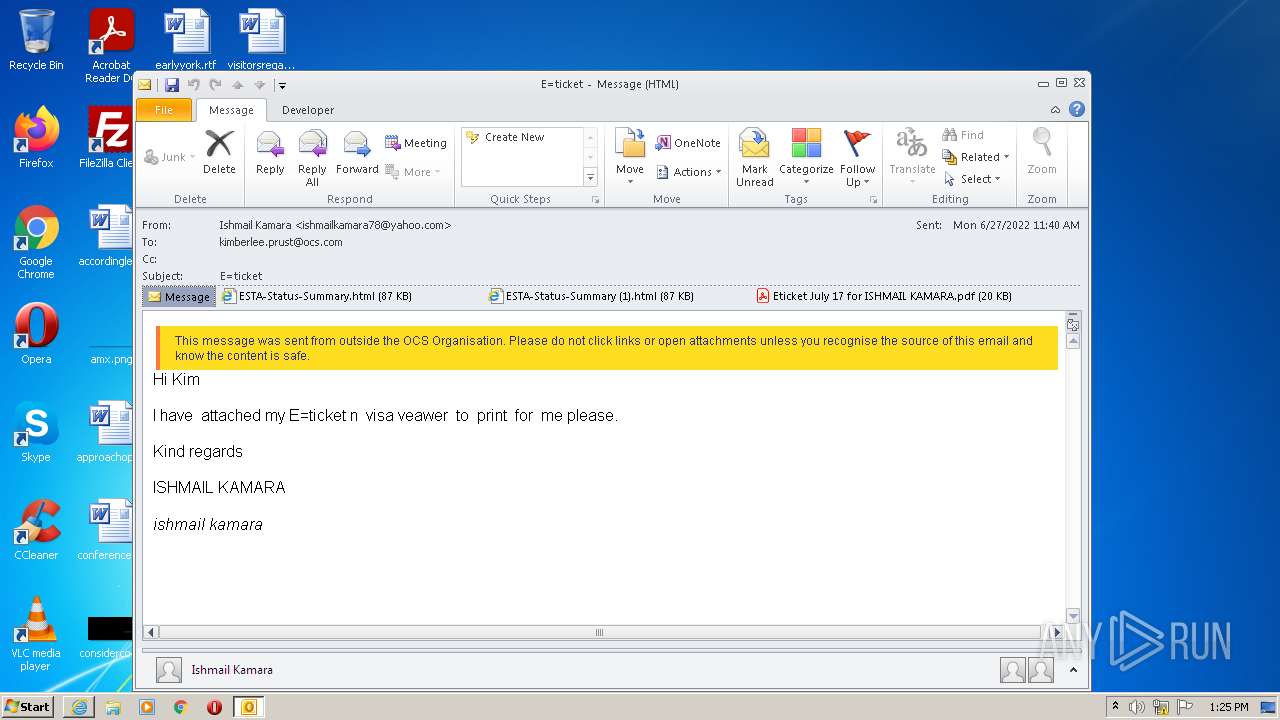
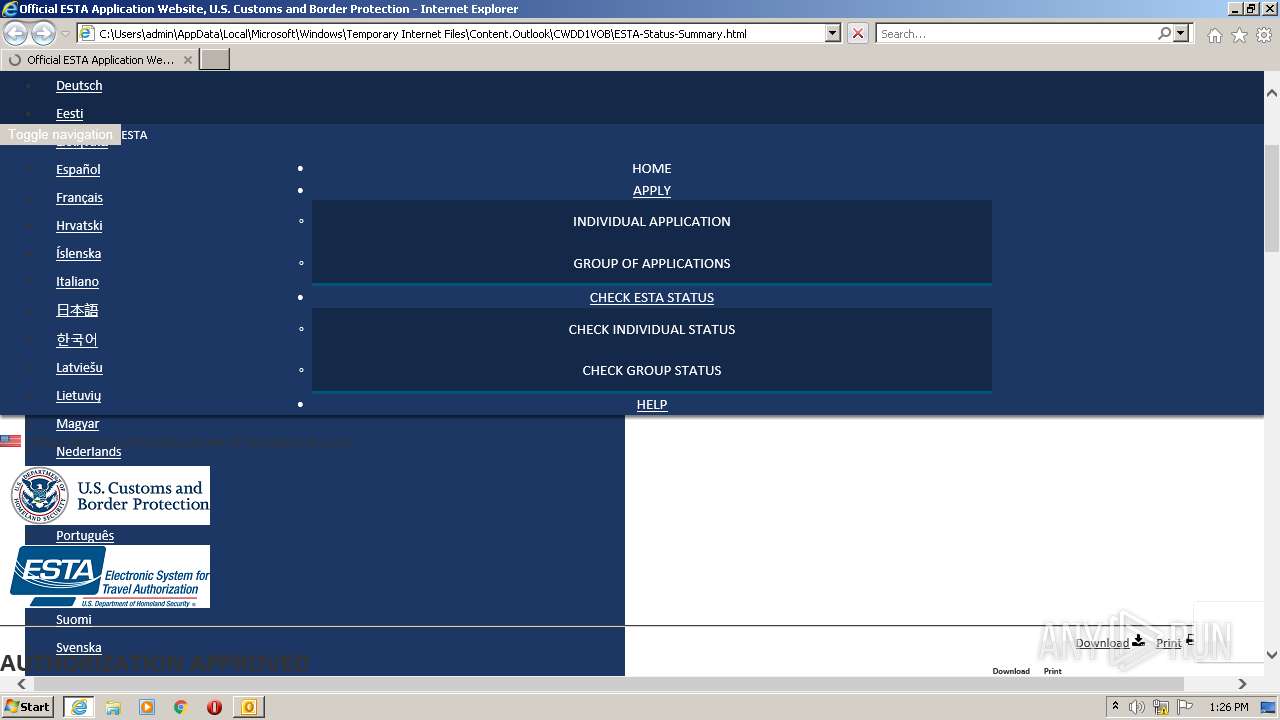
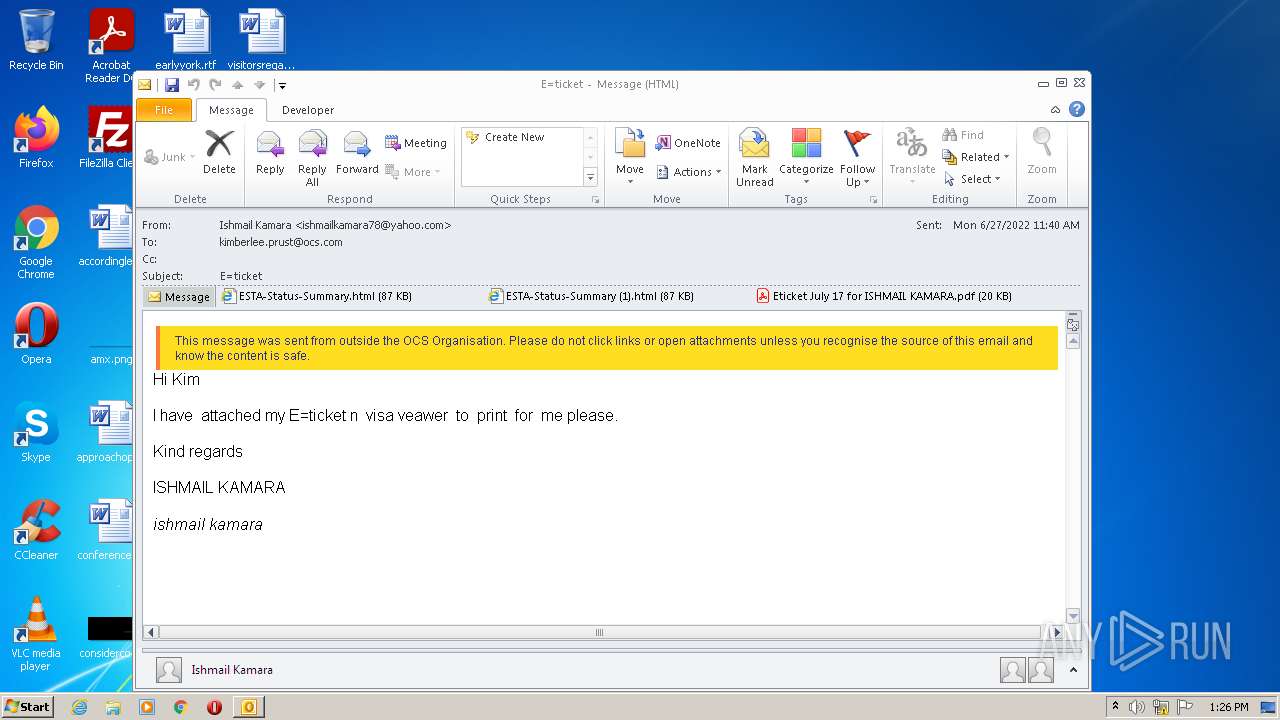
| File name: | 3F64A310-A502-4DE1-AA8E-8A21F6BE1C62.1_originalmail.eml |
| Full analysis: | https://app.any.run/tasks/66c261ed-3e30-4f09-bc35-1977b8bf5f90 |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 12:23:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 1ED25095752F8E9DF271FB44F3846069 |
| SHA1: | 5BA050AB73692E15182D57F75D62E3FA331FCFE7 |
| SHA256: | 19379A2C57DC0E687828A06FDD614905AFADAB40615B5090F99EBE8F0CCB77FB |
| SSDEEP: | 6144:5gtmLwkFM/c2iEbBuHhHZ10svwcHmePHabs+70veHZ10svwcHmePHabs+70vEGA:5gtmLwOM/c2ikBuH1f0DqybaQf0Dqybt |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks supported languages
- OUTLOOK.EXE (PID: 3284)
Reads the computer name
- OUTLOOK.EXE (PID: 3284)
Searches for installed software
- OUTLOOK.EXE (PID: 3284)
Creates files in the user directory
- OUTLOOK.EXE (PID: 3284)
Starts Internet Explorer
- OUTLOOK.EXE (PID: 3284)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 356)
INFO
Checks supported languages
- AcroRd32.exe (PID: 1432)
- AcroRd32.exe (PID: 4080)
- RdrCEF.exe (PID: 3492)
- RdrCEF.exe (PID: 2812)
- RdrCEF.exe (PID: 3504)
- RdrCEF.exe (PID: 2272)
- RdrCEF.exe (PID: 1884)
- RdrCEF.exe (PID: 3640)
- RdrCEF.exe (PID: 2744)
- iexplore.exe (PID: 356)
- RdrCEF.exe (PID: 1672)
- iexplore.exe (PID: 3336)
Reads the computer name
- AcroRd32.exe (PID: 1432)
- RdrCEF.exe (PID: 2812)
- AcroRd32.exe (PID: 4080)
- iexplore.exe (PID: 356)
- iexplore.exe (PID: 3336)
Searches for installed software
- AcroRd32.exe (PID: 4080)
- AcroRd32.exe (PID: 1432)
Application launched itself
- RdrCEF.exe (PID: 2812)
- AcroRd32.exe (PID: 4080)
- iexplore.exe (PID: 3336)
Reads CPU info
- AcroRd32.exe (PID: 1432)
Reads the hosts file
- RdrCEF.exe (PID: 2812)
Reads Microsoft Office registry keys
- AcroRd32.exe (PID: 1432)
- OUTLOOK.EXE (PID: 3284)
Changes internet zones settings
- iexplore.exe (PID: 3336)
Reads settings of System Certificates
- RdrCEF.exe (PID: 2812)
- AcroRd32.exe (PID: 4080)
- iexplore.exe (PID: 356)
- iexplore.exe (PID: 3336)
Checks Windows Trust Settings
- AcroRd32.exe (PID: 4080)
- iexplore.exe (PID: 356)
- iexplore.exe (PID: 3336)
Reads internet explorer settings
- iexplore.exe (PID: 356)
Creates files in the user directory
- iexplore.exe (PID: 356)
- iexplore.exe (PID: 3336)
Reads the date of Windows installation
- iexplore.exe (PID: 3336)
Changes settings of System certificates
- iexplore.exe (PID: 3336)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3336)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
50
Monitored processes
13
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 356 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3336 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1432 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\CWDD1VOB\Eticket July 17 for ISHMAIL KAMARA.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1672 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1072,16407387436179483206,11451747103391502520,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=10090636110774401475 --renderer-client-id=8 --mojo-platform-channel-handle=1816 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1884 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1072,16407387436179483206,11451747103391502520,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=12940004947864142770 --renderer-client-id=7 --mojo-platform-channel-handle=1516 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2272 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1072,16407387436179483206,11451747103391502520,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=6187880737423659734 --mojo-platform-channel-handle=1388 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2744 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1072,16407387436179483206,11451747103391502520,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=4588392276419534872 --mojo-platform-channel-handle=1220 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2812 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
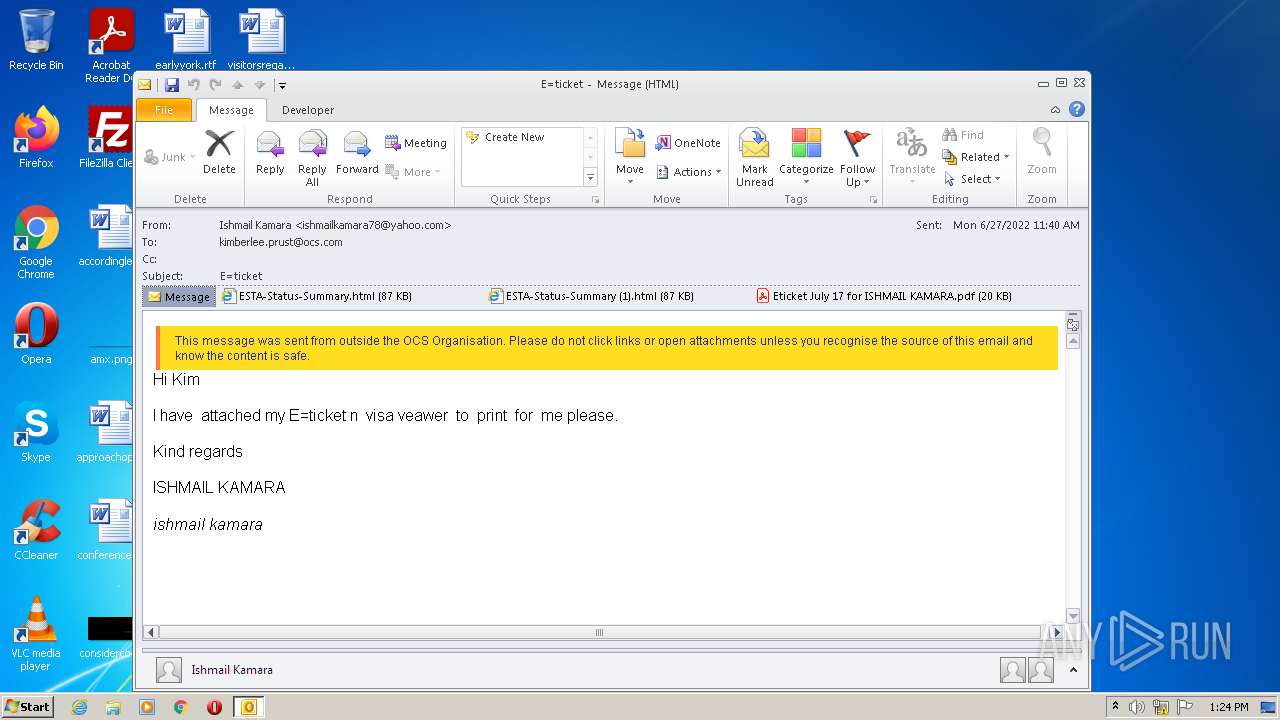
| 3284 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\3F64A310-A502-4DE1-AA8E-8A21F6BE1C62.1_originalmail.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
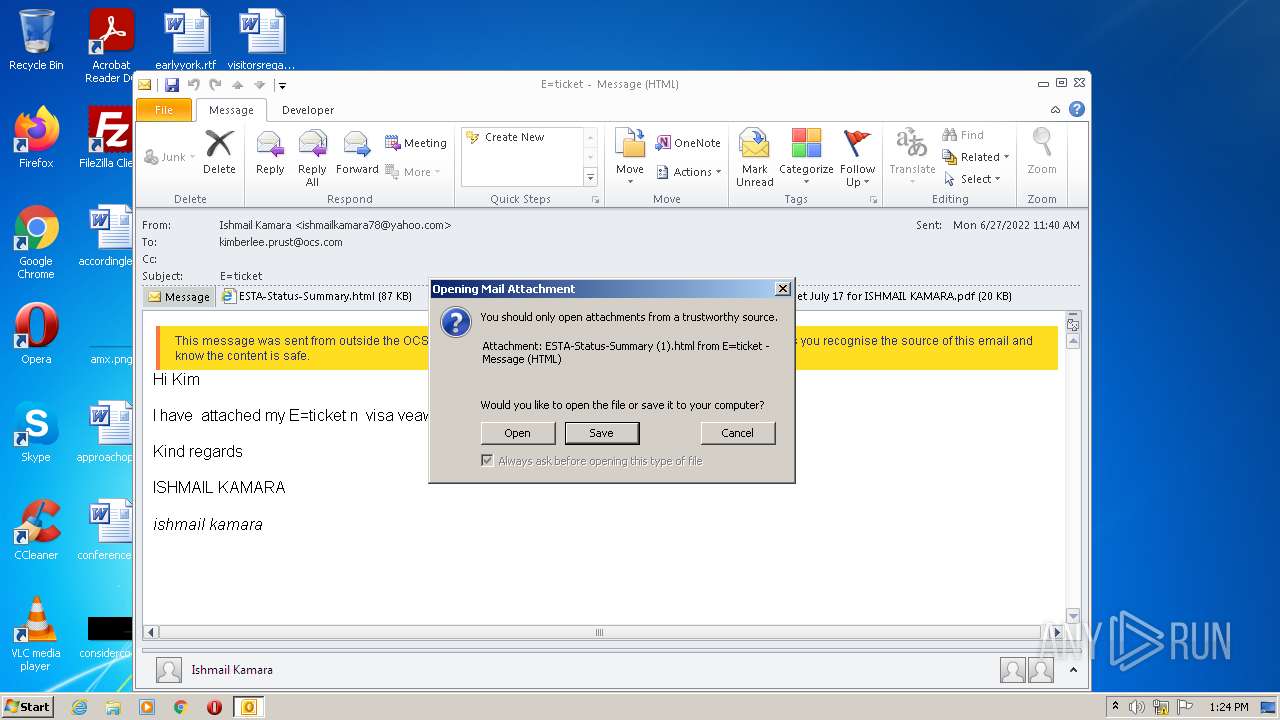
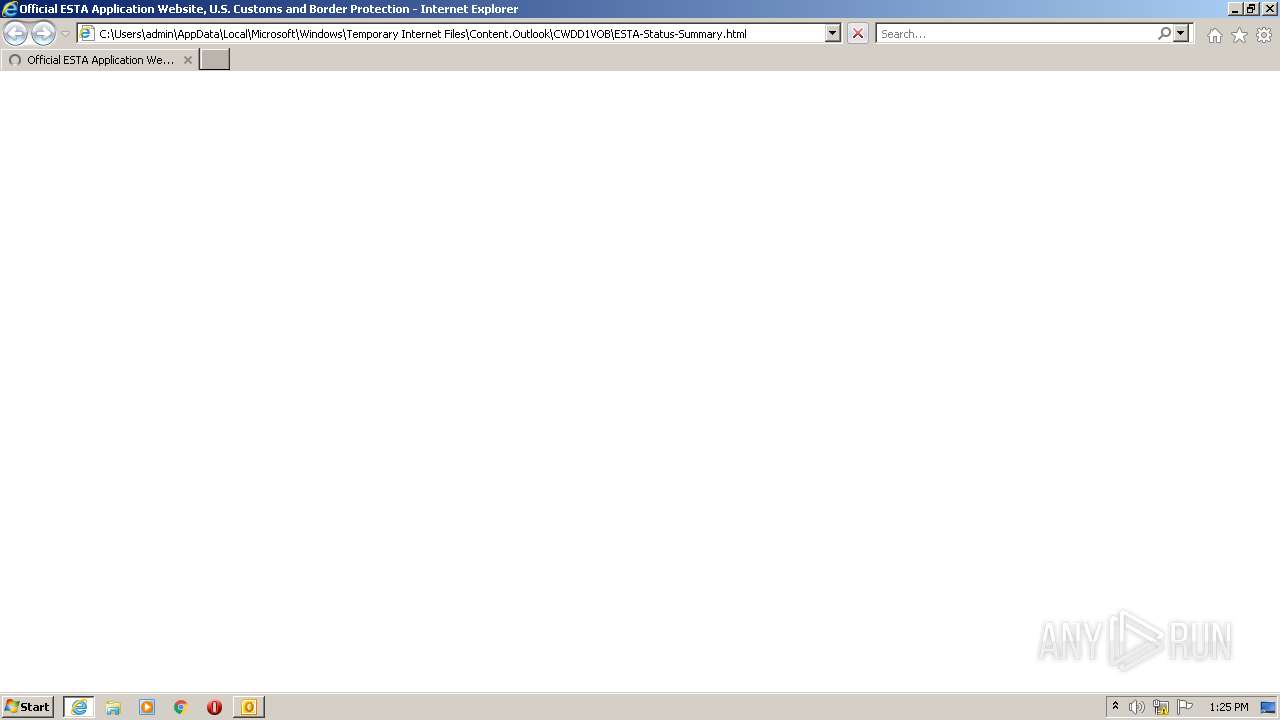
| 3336 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\CWDD1VOB\ESTA-Status-Summary.html | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3492 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1072,16407387436179483206,11451747103391502520,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=9365325646964415184 --mojo-platform-channel-handle=1212 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
Total events
37 613
Read events
36 629
Write events
953
Delete events
31
Modification events
| (PID) Process: | (3284) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3284) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3284) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3284) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3284) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3284) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3284) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3284) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3284) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (3284) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
168
Text files
42
Unknown types
18
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3284 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR8743.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3284 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 3284 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
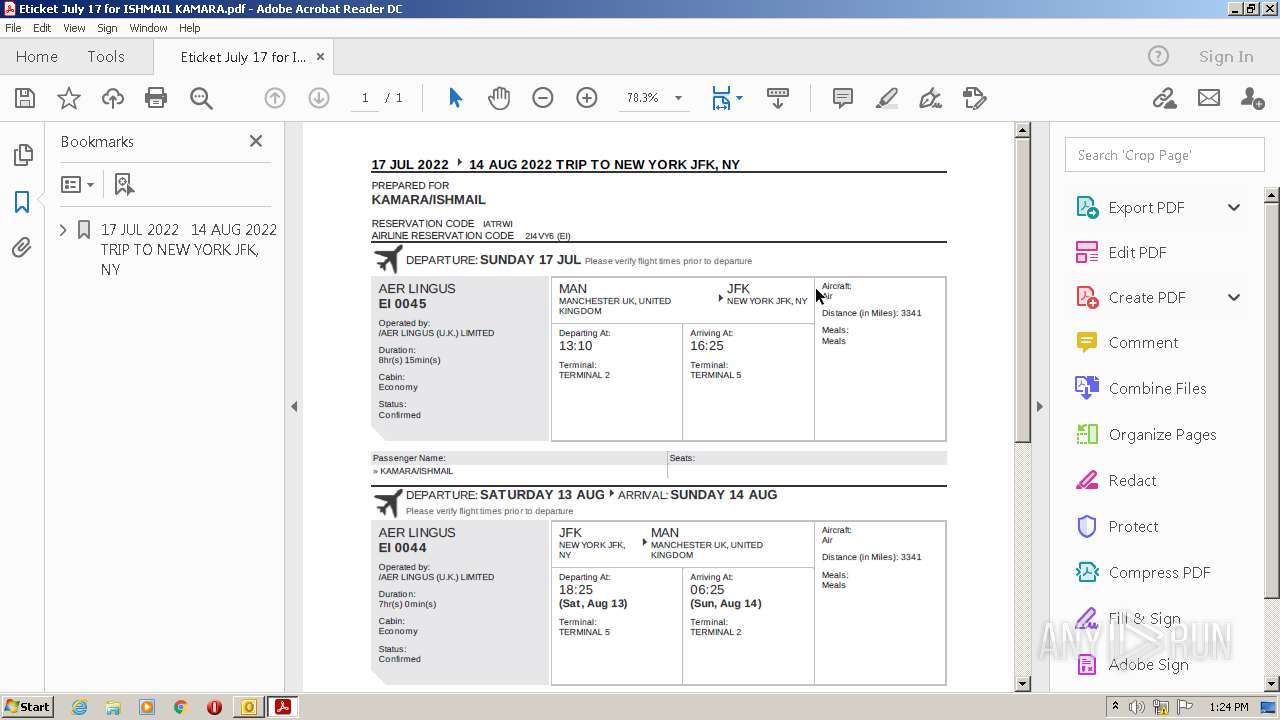
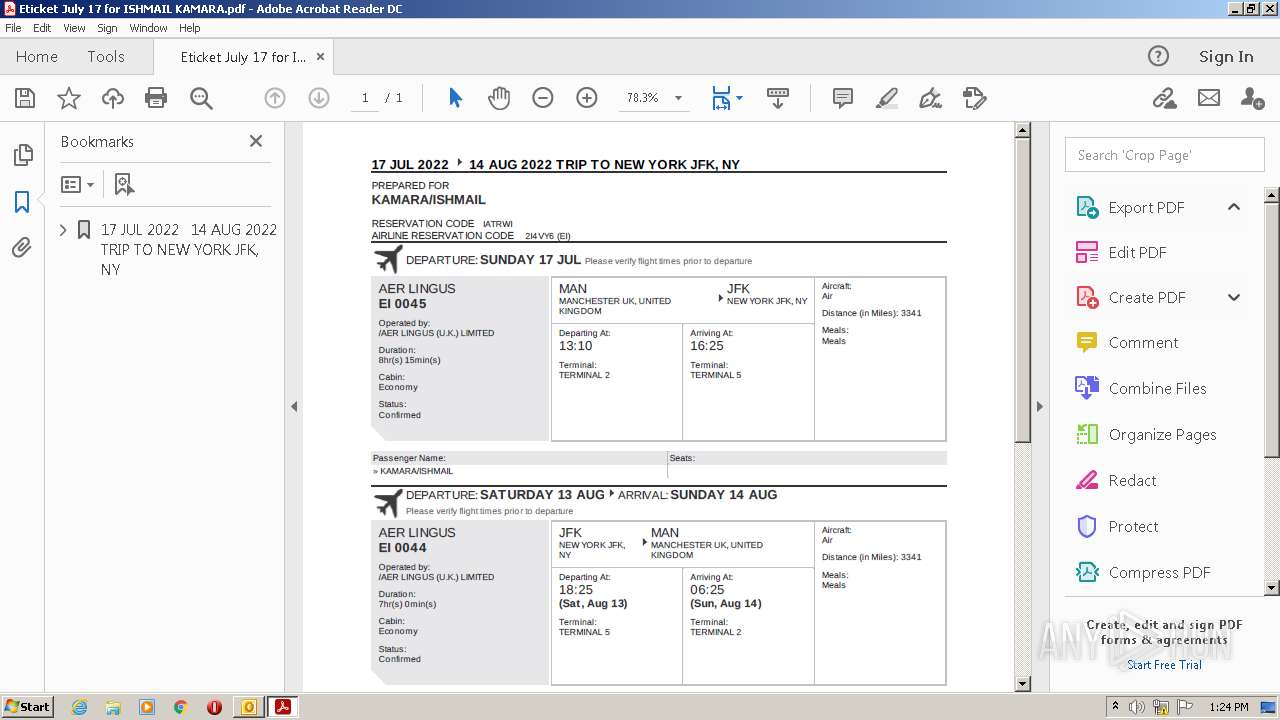
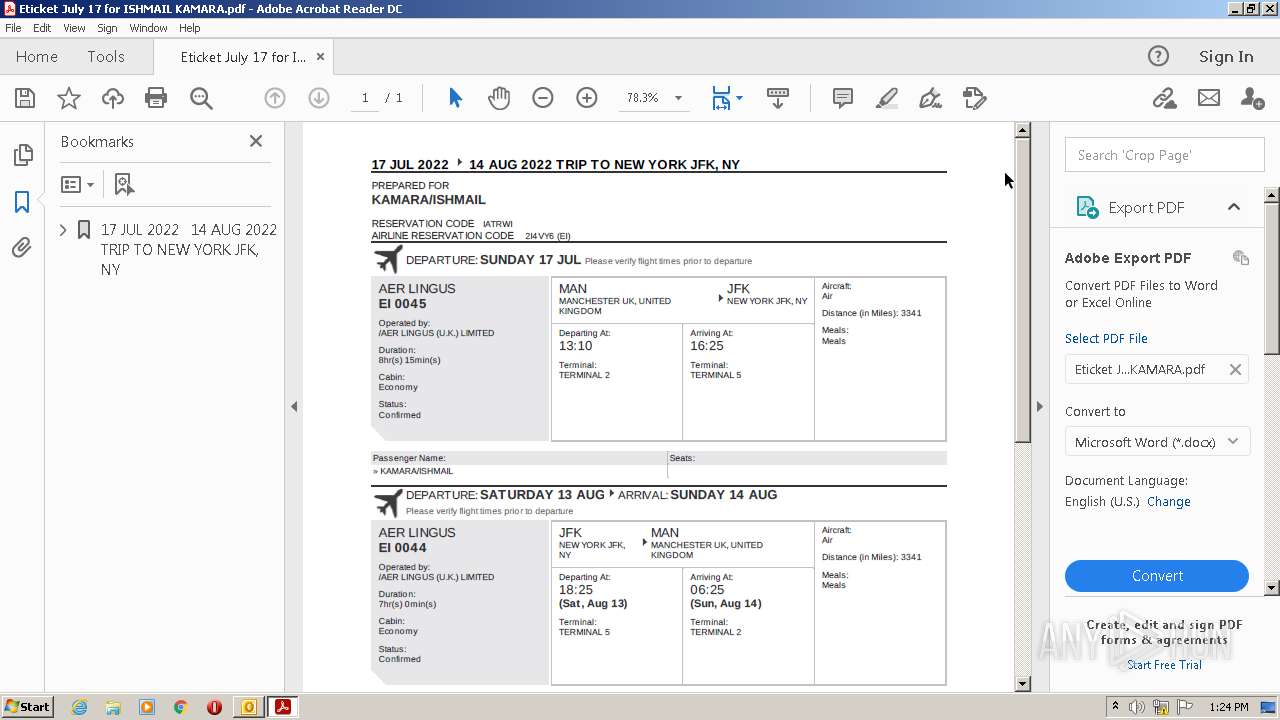
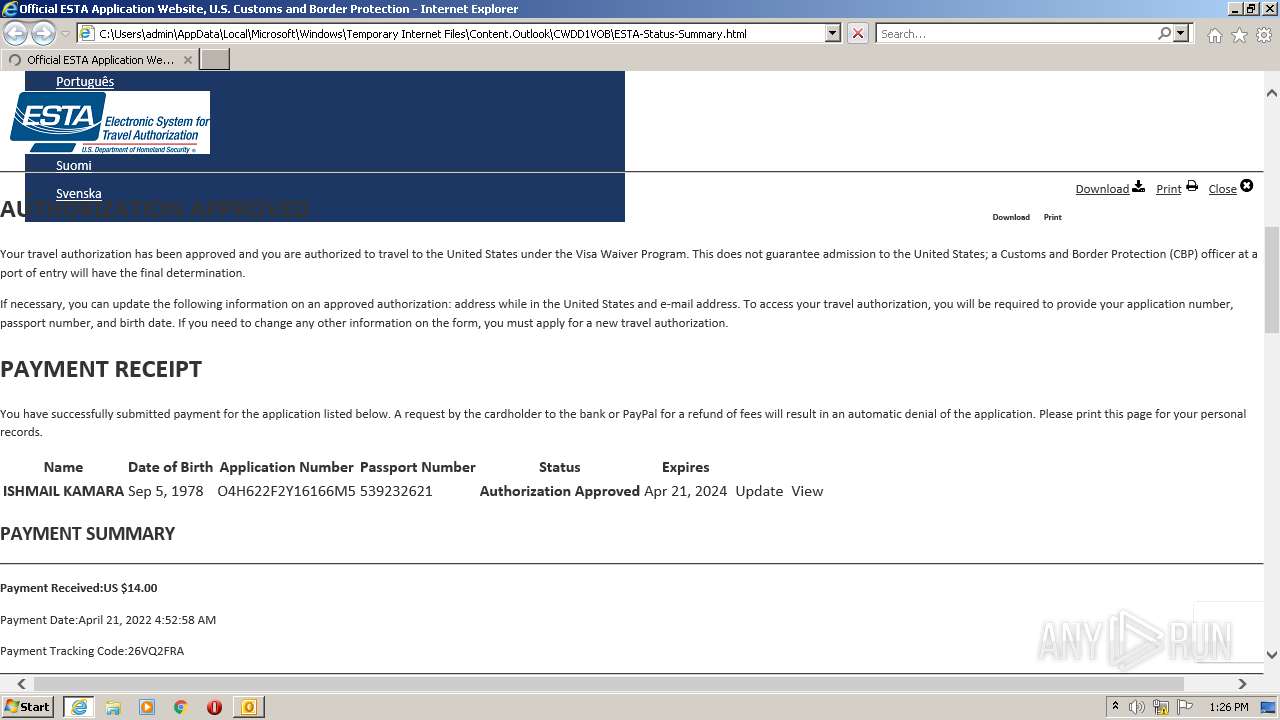
| 3284 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\CWDD1VOB\Eticket July 17 for ISHMAIL KAMARA.pdf | ||
MD5:— | SHA256:— | |||
| 3284 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\CWDD1VOB\Eticket July 17 for ISHMAIL KAMARA (2).pdf | ||
MD5:— | SHA256:— | |||
| 2812 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\aba6710fde0876af_0 | binary | |
MD5:— | SHA256:— | |||
| 2812 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\2a426f11fd8ebe18_0 | binary | |
MD5:— | SHA256:— | |||
| 3284 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2812 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\0786087c3c360803_0 | binary | |
MD5:— | SHA256:— | |||
| 2812 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\bba29d2e6197e2f4_0 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
57
DNS requests
68
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3284 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
356 | iexplore.exe | GET | — | 142.251.36.3:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | — | — | whitelisted |
356 | iexplore.exe | GET | — | 65.9.84.150:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | — | — | whitelisted |
356 | iexplore.exe | GET | — | 142.251.36.3:80 | http://crl.pki.goog/gtsr1/gtsr1.crl | US | — | — | whitelisted |
356 | iexplore.exe | GET | — | 65.9.84.167:80 | http://crl.rootg2.amazontrust.com/rootg2.crl | US | — | — | whitelisted |
356 | iexplore.exe | GET | — | 65.9.84.140:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | — | — | shared |
356 | iexplore.exe | GET | 200 | 142.251.36.46:80 | http://crls.pki.goog/gts1c3/moVDfISia2k.crl | US | der | 12.4 Kb | whitelisted |
3336 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
356 | iexplore.exe | GET | 200 | 142.251.36.3:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
356 | iexplore.exe | GET | 200 | 142.251.36.3:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCfB0sRdF8W%2FBIjdfpYeZPw | US | der | 472 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3284 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
2812 | RdrCEF.exe | 104.85.0.137:443 | geo2.adobe.com | Time Warner Cable Internet LLC | US | suspicious |
2812 | RdrCEF.exe | 54.227.187.23:443 | p13n.adobe.io | Amazon.com, Inc. | US | suspicious |
356 | iexplore.exe | 216.58.208.100:443 | www.google.com | Google Inc. | US | whitelisted |
— | — | 23.217.99.144:443 | acroipm2.adobe.com | Akamai Technologies, Inc. | US | suspicious |
356 | iexplore.exe | 65.9.86.93:443 | dap.digitalgov.gov | AT&T Services, Inc. | US | unknown |
356 | iexplore.exe | 142.250.179.142:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
356 | iexplore.exe | 88.221.255.138:80 | ctldl.windowsupdate.com | Akamai International B.V. | — | unknown |
3336 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
356 | iexplore.exe | 142.251.36.3:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dns.msftncsi.com |
| shared |
config.messenger.msn.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
dap.digitalgov.gov |
| whitelisted |
www.google.com |
| malicious |