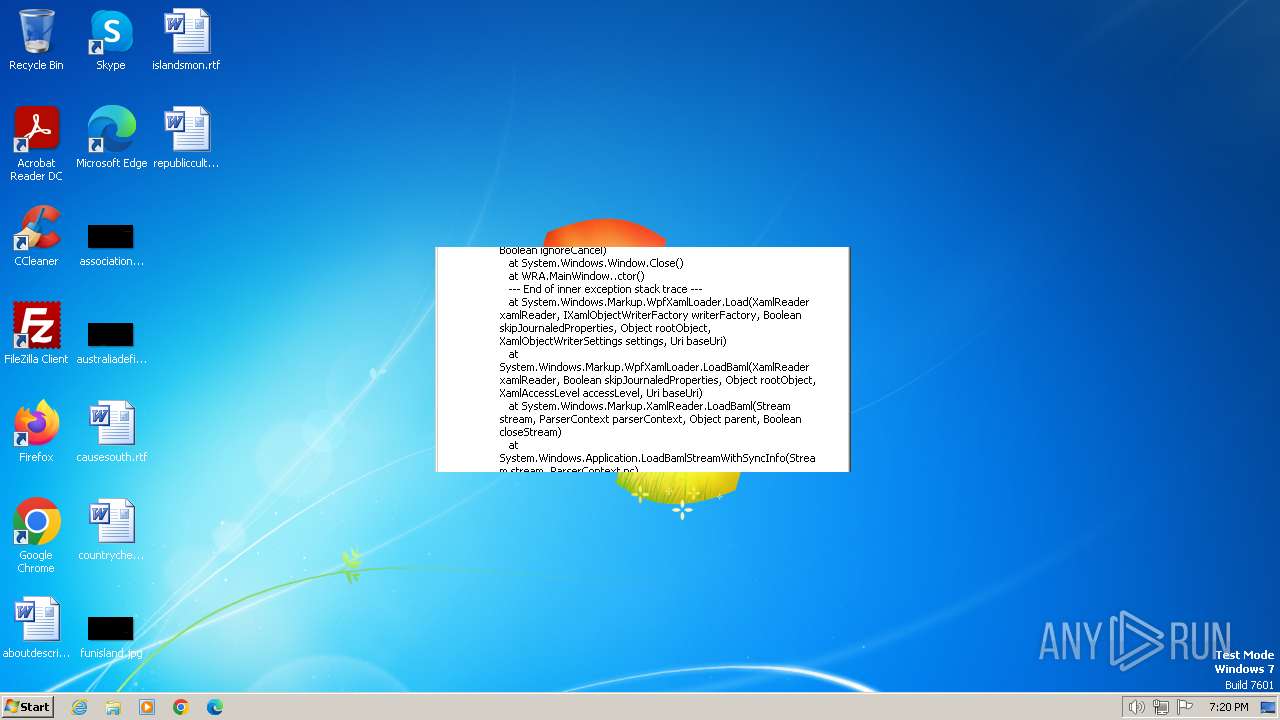
| File name: | WoT Replay Analyzer.exe |
| Full analysis: | https://app.any.run/tasks/0ed368f3-2906-4862-9bc8-8b8b791f0f54 |
| Verdict: | Malicious activity |
| Analysis date: | January 09, 2024, 19:20:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 793A29DBFB78E7470245104AF0C864A8 |
| SHA1: | AB31F7F8DF29386BD2D21B4430E86516BDCB6BB6 |
| SHA256: | 1931A9E8D9E5A1DEBE073A1BD2B03940EBB1EBA003A8B6CDF146E450341E4B7C |
| SSDEEP: | 98304:qe3qx0zRDLNTDs2ShPfSxvKKtPFQ8tQucgKK5UXGRHmehYKWQUz58rKBtG5g3Aj/:sd5PmC20 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Internet Settings
- WoT Replay Analyzer.exe (PID: 116)
Reads Microsoft Outlook installation path
- WoT Replay Analyzer.exe (PID: 116)
Checks Windows Trust Settings
- WoT Replay Analyzer.exe (PID: 116)
Reads settings of System Certificates
- WoT Replay Analyzer.exe (PID: 116)
Reads security settings of Internet Explorer
- WoT Replay Analyzer.exe (PID: 116)
INFO
Drops the executable file immediately after the start
- WoT Replay Analyzer.exe (PID: 116)
Checks supported languages
- WoT Replay Analyzer.exe (PID: 116)
Reads the computer name
- WoT Replay Analyzer.exe (PID: 116)
Create files in a temporary directory
- WoT Replay Analyzer.exe (PID: 116)
Checks proxy server information
- WoT Replay Analyzer.exe (PID: 116)
Reads the machine GUID from the registry
- WoT Replay Analyzer.exe (PID: 116)
Creates files or folders in the user directory
- WoT Replay Analyzer.exe (PID: 116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (56.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.3) |
| .scr | | | Windows screen saver (10.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:11:03 18:04:07+01:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 5252096 |
| InitializedDataSize: | 30720 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x50431e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.10.1.1 |
| ProductVersionNumber: | 1.10.1.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | World of Tanks Replay Analyzer |
| FileVersion: | 1.10.1.1 |
| InternalName: | WoT Replay Analyzer.exe |
| LegalCopyright: | Copyright © 2012-2020 by Aimdrol |
| LegalTrademarks: | - |
| OriginalFileName: | WoT Replay Analyzer.exe |
| ProductName: | World of Tanks Replay Analyzer |
| ProductVersion: | 1.10.1.1 |
| AssemblyVersion: | 1.10.1.1 |
Total processes
34
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Users\admin\AppData\Local\Temp\WoT Replay Analyzer.exe" | C:\Users\admin\AppData\Local\Temp\WoT Replay Analyzer.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: World of Tanks Replay Analyzer Exit code: 0 Version: 1.10.1.1 Modules
| |||||||||||||||
Total events
4 176
Read events
4 145
Write events
31
Delete events
0
Modification events
| (PID) Process: | (116) WoT Replay Analyzer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: Explorer.EXE | |||
| (PID) Process: | (116) WoT Replay Analyzer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (116) WoT Replay Analyzer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (116) WoT Replay Analyzer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (116) WoT Replay Analyzer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (116) WoT Replay Analyzer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (116) WoT Replay Analyzer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005B010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (116) WoT Replay Analyzer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (116) WoT Replay Analyzer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (116) WoT Replay Analyzer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
0
Suspicious files
5
Text files
1
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 116 | WoT Replay Analyzer.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\59D76868C250B3240414CE3EFBB12518_6B5A53AF835C2F7B0B0237F2381D4C41 | binary | |
MD5:311B7DCA1D599EB08128299536BD7621 | SHA256:ACDADFF0B31C1A97883C33FF1862AC9696780148839102D490C71AC8615DFB3D | |||
| 116 | WoT Replay Analyzer.exe | C:\Users\admin\AppData\Local\Temp\log.txt | text | |
MD5:A9B54A7F978998DCC30A022E4AD587BA | SHA256:0E0A3CB369CBBA34CB7277FEFBFE89250A985BB5682A6CBFE10B87B16B036D4A | |||
| 116 | WoT Replay Analyzer.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:85B241891F7A62305C4FB5A024C8F2D9 | SHA256:8822AFD30567423163844A06755BC3A64872FDDC5197773303B40D82C1FD8C17 | |||
| 116 | WoT Replay Analyzer.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_49536AB5156BDD74EFF881D01C36A419 | der | |
MD5:737C4492E3E888980EFA76B5BEF0ADEA | SHA256:1370E218BE96E86482CAE46B2EFD326036DFD55551C718F42B139857AB3E8643 | |||
| 116 | WoT Replay Analyzer.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_49536AB5156BDD74EFF881D01C36A419 | binary | |
MD5:84AC462E3B744D9482729D7CA64E119F | SHA256:9075C8FF3C475A10C530D005233ECD511DE2CC33474C7DC754561B0B9A7E5675 | |||
| 116 | WoT Replay Analyzer.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 116 | WoT Replay Analyzer.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\59D76868C250B3240414CE3EFBB12518_6B5A53AF835C2F7B0B0237F2381D4C41 | binary | |
MD5:FA361DA49ADC4F504213530BEFEC95D2 | SHA256:B490A22FF8F63A2ECA23705561D9FDBDF6FD53021C4E67BF7B86D9076387B81D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
9
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
116 | WoT Replay Analyzer.exe | GET | 301 | 92.223.22.85:80 | http://forum.worldoftanks.eu/index.php?/topic/185348-090-wot-replay-analyzer-wip-1-200414/page__pid__3454598 | unknown | html | 162 b | unknown |
116 | WoT Replay Analyzer.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?01e0fe98e502a2b0 | unknown | compressed | 4.66 Kb | unknown |
116 | WoT Replay Analyzer.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | binary | 471 b | unknown |
116 | WoT Replay Analyzer.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSnxLiz3Fu1WB6n1%2FE6xWn1b0jXiQQUdIWAwGbH3zfez70pN6oDHb7tzRcCEAiUzOhlFnt0DQf%2FoauArwQ%3D | unknown | binary | 471 b | unknown |
1080 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?85d4b5be3d25b038 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
116 | WoT Replay Analyzer.exe | 92.223.22.85:80 | forum.worldoftanks.eu | G-Core Labs S.A. | LU | unknown |
116 | WoT Replay Analyzer.exe | 92.223.22.85:443 | forum.worldoftanks.eu | G-Core Labs S.A. | LU | unknown |
116 | WoT Replay Analyzer.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
116 | WoT Replay Analyzer.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1080 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
forum.worldoftanks.eu |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |