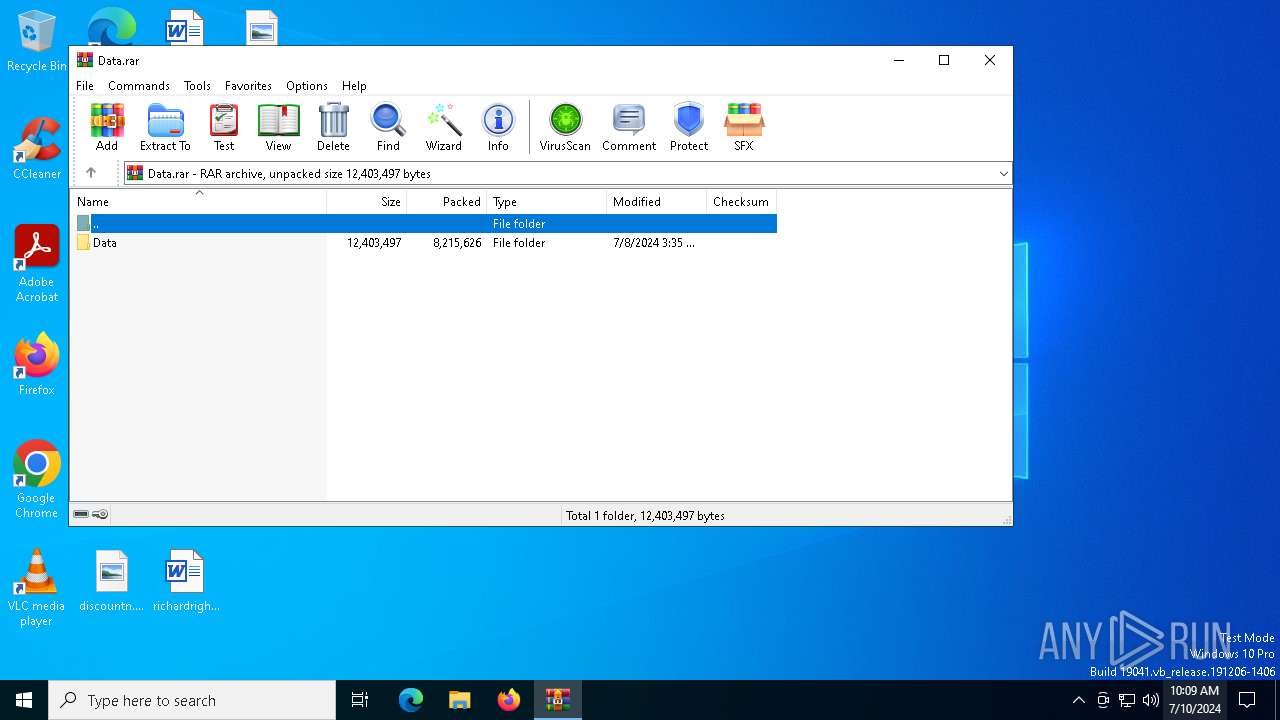
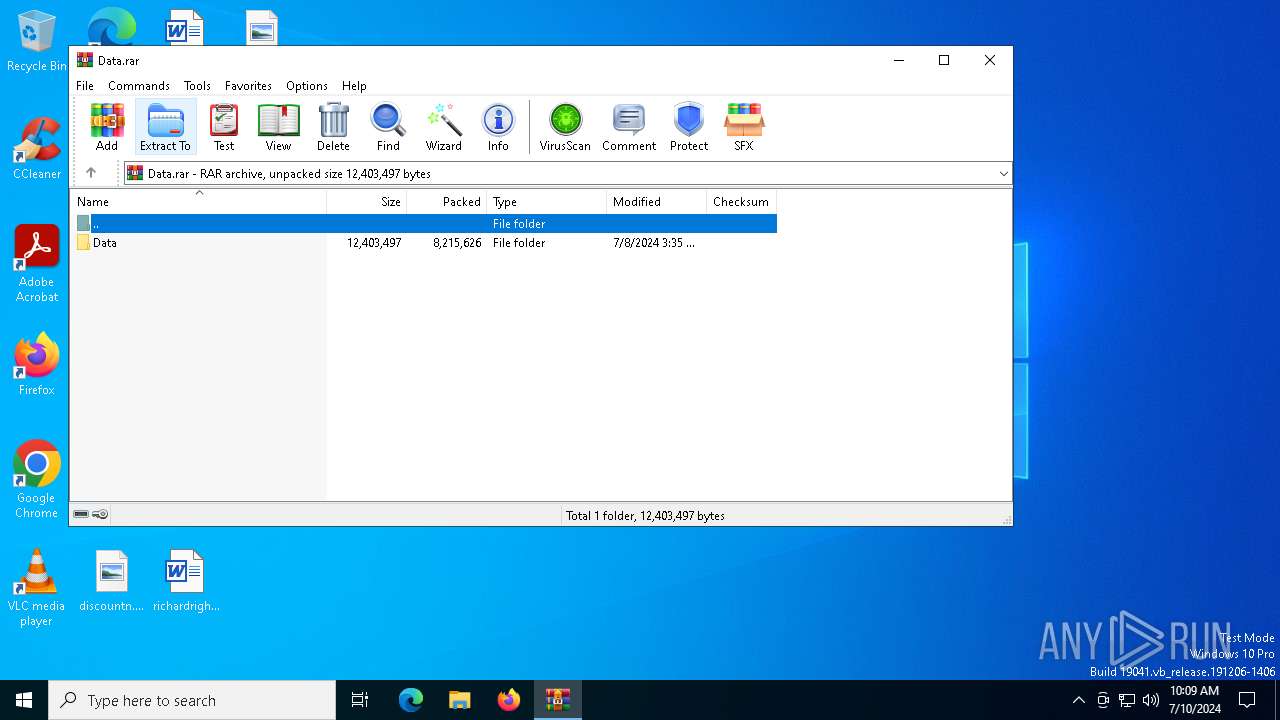
| File name: | Data.rar |
| Full analysis: | https://app.any.run/tasks/174e0594-8ae3-458a-8513-096e9210f9d7 |
| Verdict: | Malicious activity |
| Analysis date: | July 10, 2024, 10:09:34 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 6C601F323F0BE0CAF858C05D2CB5E457 |
| SHA1: | 99ABF21D0E4E93812836059F157C7841FDF3C097 |
| SHA256: | 1929125CA9D94A06BAC946F4ADB4CD96E0DEEAE5C1A3F85704F1760B8F3F5EE6 |
| SSDEEP: | 98304:KKLW+9ExNKGbOqVjk1xy8gZEV1gH6f2rajDXxX4cnJj8Lt+cRY51kwbcnh/3/Z0i:KxUbHrY9bWFuW+F1 |
MALICIOUS
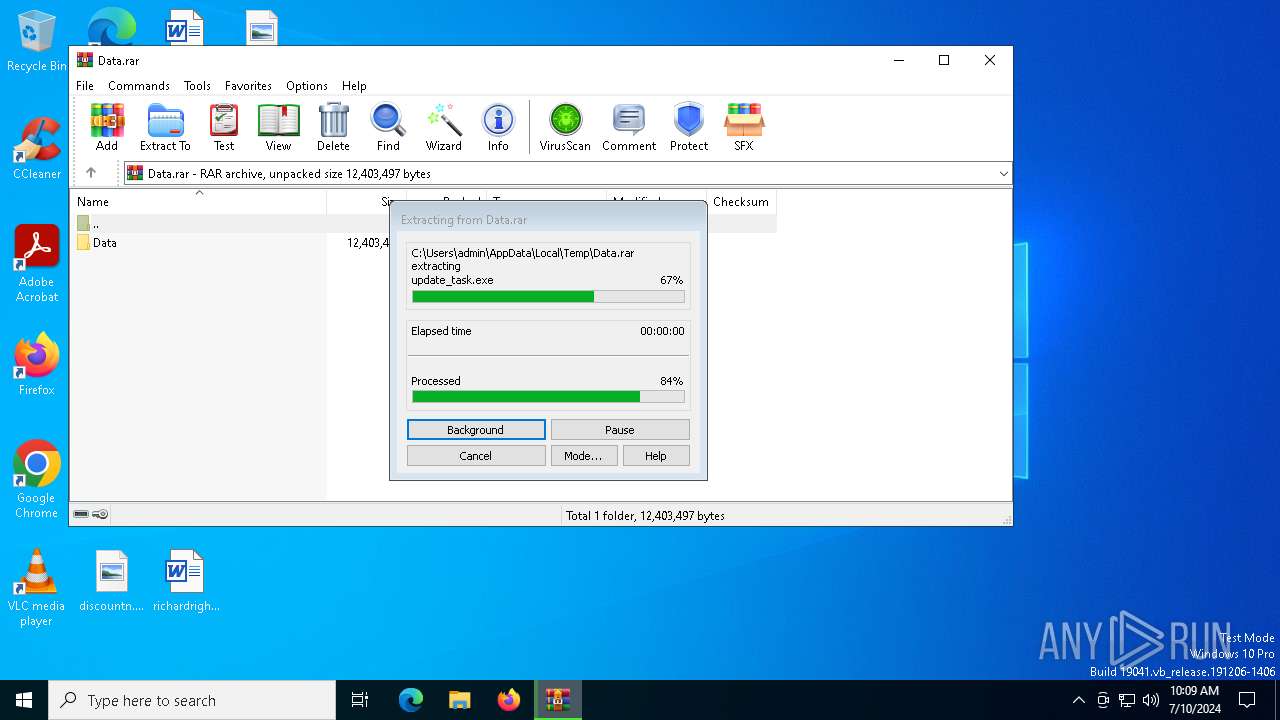
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6272)
Creates a writable file in the system directory
- WerFault.exe (PID: 5608)
SUSPICIOUS
The process creates files with name similar to system file names
- WinRAR.exe (PID: 6272)
Process drops legitimate windows executable
- WinRAR.exe (PID: 6272)
Reads security settings of Internet Explorer
- update_task.exe (PID: 3088)
- LockApp.exe (PID: 3872)
Reads the date of Windows installation
- update_task.exe (PID: 3088)
Executes as Windows Service
- wsc_proxy.exe (PID: 2104)
Executes application which crashes
- wsc_proxy.exe (PID: 2104)
INFO
Reads the computer name
- update_task.exe (PID: 3088)
- LockApp.exe (PID: 3872)
- SkypeApp.exe (PID: 1068)
- wsc_proxy.exe (PID: 2104)
Checks supported languages
- update_task.exe (PID: 3088)
- SkypeApp.exe (PID: 1068)
- LockApp.exe (PID: 3872)
- wsc_proxy.exe (PID: 2104)
Process checks computer location settings
- update_task.exe (PID: 3088)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6272)
Manual execution by a user
- update_task.exe (PID: 444)
- update_task.exe (PID: 3088)
- Taskmgr.exe (PID: 4180)
- Taskmgr.exe (PID: 6100)
- Taskmgr.exe (PID: 6796)
- Taskmgr.exe (PID: 6912)
Reads the machine GUID from the registry
- wsc_proxy.exe (PID: 2104)
Creates files in the program directory
- wsc_proxy.exe (PID: 2104)
Reads CPU info
- wsc_proxy.exe (PID: 2104)
Reads the software policy settings
- WerFault.exe (PID: 5608)
- slui.exe (PID: 3108)
- slui.exe (PID: 5324)
Checks proxy server information
- slui.exe (PID: 5324)
- update_task.exe (PID: 3088)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 6100)
- Taskmgr.exe (PID: 6912)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
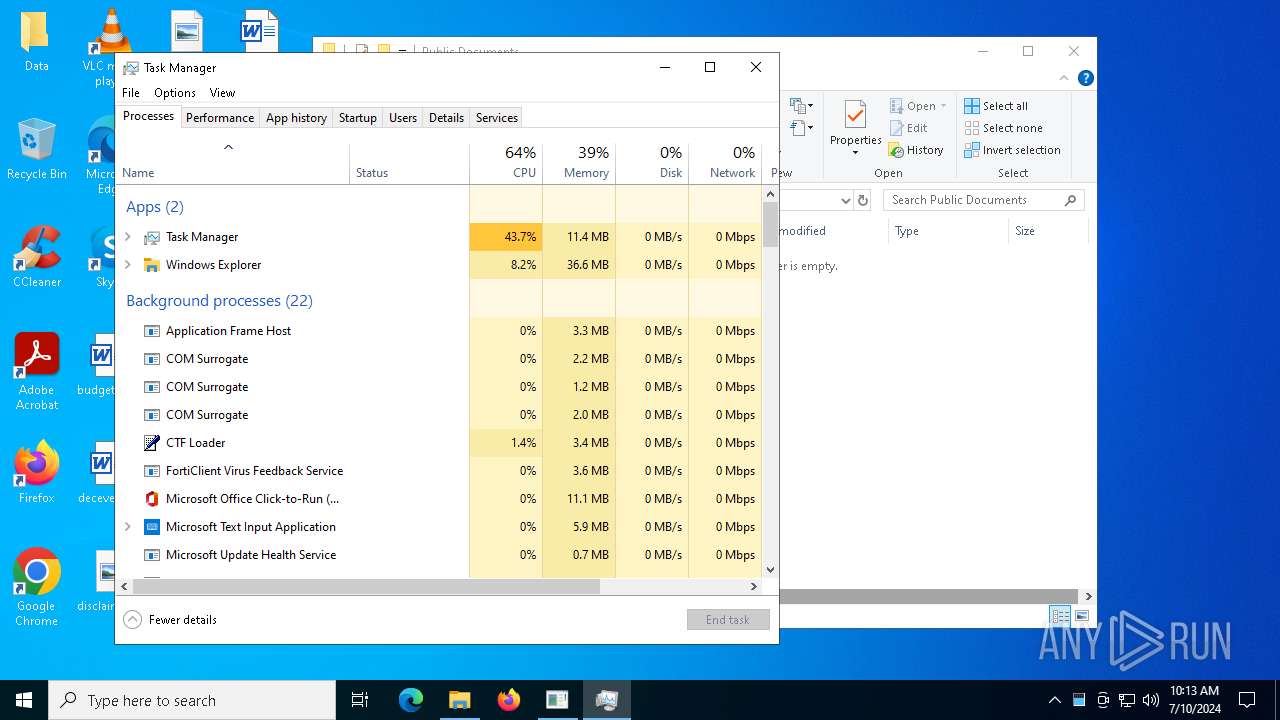
Total processes
169
Monitored processes
17
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 444 | "C:\Users\admin\Desktop\Data\update_task.exe" | C:\Users\admin\Desktop\Data\update_task.exe | — | explorer.exe | |||||||||||
User: admin Company: Fortinet Inc. Integrity Level: MEDIUM Description: FortiClient Virus Feedback Service Exit code: 3221226540 Version: 7.2.4.0972 Modules
| |||||||||||||||
| 1068 | "C:\Users\admin\Desktop\Data\SkypeApp.exe" | C:\Users\admin\Desktop\Data\SkypeApp.exe | — | update_task.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 2104 | "C:\Users\admin\Desktop\Data\wsc_proxy.exe" /runassvc /rpcserver /wsc_name:" " | C:\Users\admin\Desktop\Data\wsc_proxy.exe | services.exe | ||||||||||||
User: SYSTEM Company: AVAST Software Integrity Level: SYSTEM Description: Avast remediation exe Exit code: 3221226505 Version: 21.4.6162.0 Modules
| |||||||||||||||
| 2556 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | update_task.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3088 | "C:\Users\admin\Desktop\Data\update_task.exe" | C:\Users\admin\Desktop\Data\update_task.exe | explorer.exe | ||||||||||||
User: admin Company: Fortinet Inc. Integrity Level: HIGH Description: FortiClient Virus Feedback Service Version: 7.2.4.0972 Modules
| |||||||||||||||
| 3108 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3872 | "C:\WINDOWS\SystemApps\Microsoft.LockApp_cw5n1h2txyewy\LockApp.exe" -ServerName:WindowsDefaultLockScreen.AppX7y4nbzq37zn4ks9k7amqjywdat7d3j2z.mca | C:\Windows\SystemApps\Microsoft.LockApp_cw5n1h2txyewy\LockApp.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: LockApp.exe Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4180 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4800 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5324 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
18 952
Read events
18 881
Write events
63
Delete events
8
Modification events
| (PID) Process: | (6272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Data.rar | |||
| (PID) Process: | (6272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (6272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
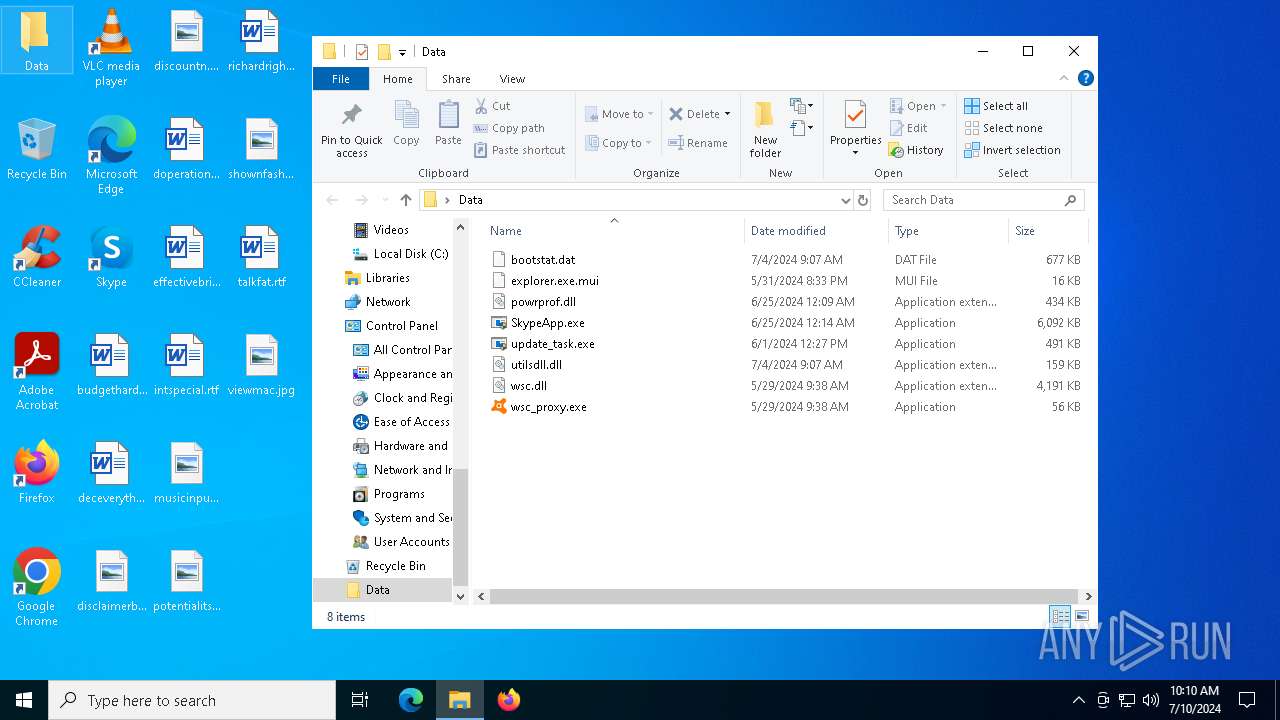
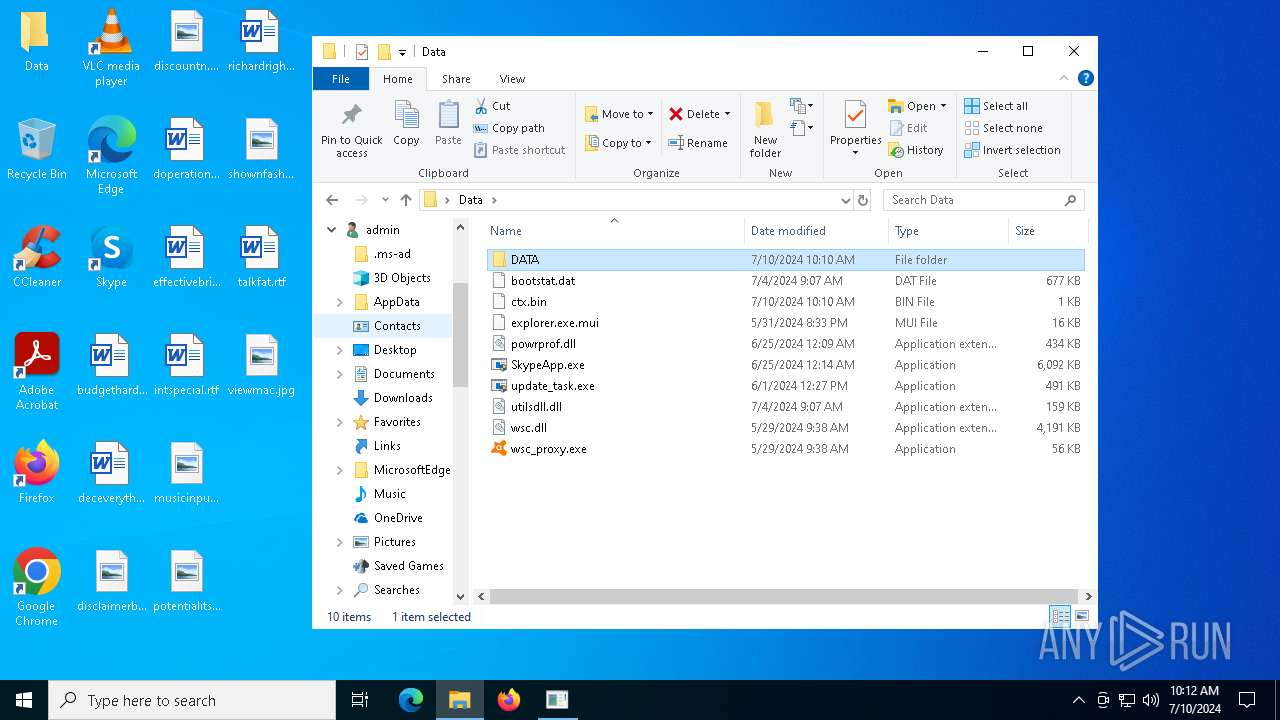
Executable files
7
Suspicious files
5
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5608 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_wsc_proxy.exe_8b25899f1fb3d5d2785872911ba1ea1fea2dfb1c_e2da83c0_cfb751e2-84e2-4244-8069-87b11d5207ed\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6272 | WinRAR.exe | C:\Users\admin\Desktop\Data\SkypeApp.exe | executable | |
MD5:C0DCAE518FE65E407FDBB6F2A71B35C7 | SHA256:CB2FF159566E5D73EC3DF5C12ED502648F0F35D1917BEFCE39E9569B09CA4DCD | |||
| 6272 | WinRAR.exe | C:\Users\admin\Desktop\Data\wsc_proxy.exe | executable | |
MD5:1B231B5C4D36DE4750A587F08338DEDE | SHA256:79E53D36A40951AB328E153BAC9C1E3ADF3330B45899345E645889B9046F06E0 | |||
| 1068 | SkypeApp.exe | C:\Users\admin\Desktop\Data\ctx.bin | pi2 | |
MD5:441077CC9E57554DD476BDFB8B8B8102 | SHA256:B413F47D13EE2FE6C845B2EE141AF81DE858DF4EC549A58B7970BB96645BC8D2 | |||
| 6272 | WinRAR.exe | C:\Users\admin\Desktop\Data\powrprof.dll | executable | |
MD5:E0B6BD1728237354A7FB60407ED098D0 | SHA256:0B8B72E4C1EA80AF57EE638BC8E65BA48550E716C77EB88EA319CC007C7C3B57 | |||
| 6272 | WinRAR.exe | C:\Users\admin\Desktop\Data\utilsdll.dll | executable | |
MD5:88118F697925A8DD74691B714AB8B4C9 | SHA256:E0EDE21DCEE0D47825D7B869395C0805EA9AF2797D1E7CED8F296D55E15DA9A0 | |||
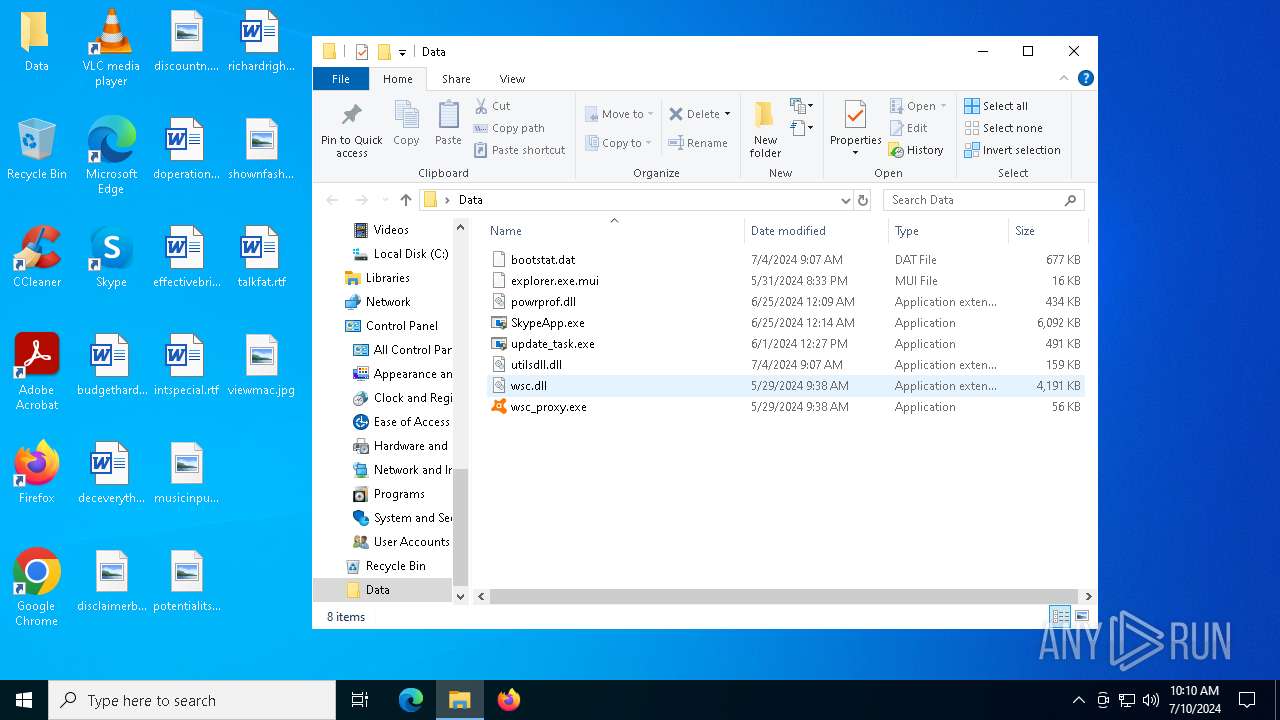
| 6272 | WinRAR.exe | C:\Users\admin\Desktop\Data\wsc.dll | executable | |
MD5:D60E8A632A3FF1F145F84C7231BAA6BD | SHA256:DE820B5E592CF456F6A4F8356195C4A335A51C6354CA7AC32CCD390E62D9BECC | |||
| 2104 | wsc_proxy.exe | C:\ProgramData\Avast Software\Avast\log\wsc.log | text | |
MD5:ECAA88F7FA0BF610A5A26CF545DCD3AA | SHA256:F1945CD6C19E56B3C1C78943EF5EC18116907A4CA1EFC40A57D48AB1DB7ADFC5 | |||
| 6272 | WinRAR.exe | C:\Users\admin\Desktop\Data\explorer.exe.mui | executable | |
MD5:F84FF7D56E9921D21522821BDE1D3228 | SHA256:429D4BC00F03A197300B1791444E47A5CD51AB14D2A35E31D1CB4F96CD555774 | |||
| 6272 | WinRAR.exe | C:\Users\admin\Desktop\Data\bootstat.dat | binary | |
MD5:CD92E4F79851F17ACF0719F3C9C12B39 | SHA256:7A510517252AA94DBD5E0C185F3B42C3AAA87292DA681ECF0B6B755B3C627754 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
72
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6612 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
6044 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
6044 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
6516 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
3652 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
4448 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
4448 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2224 | RUXIMICS.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5988 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4448 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 184.86.251.23:443 | www.bing.com | Akamai International B.V. | DE | unknown |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4656 | SearchApp.exe | 184.86.251.23:443 | www.bing.com | Akamai International B.V. | DE | unknown |
3652 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
wsc_proxy.exe | [2024-07-10 10:10:20.701] [error ] [crashguard ] [ 2104: 3836] [E9669F: 103] Dump path 'C:\ProgramData\Avast Software\Avast\log' does not exist. Directory should be already created.
|